Image Based Password Authentication for Illiterate using Touch screen by Deepak Yadav
Download as PPTX, PDF5 likes8,789 views
Image based password authentication using touchscreen basically designed for illiterate for their security system.Since image are easily to recall than strings of character.
1 of 18
Downloaded 208 times

















Ad
Recommended
graphical password authentication



graphical password authenticationAkhil Kumar The document discusses and compares various authentication methods, including recognition-based, recall-based, and graphical password techniques. It provides an overview of common techniques such as Dhamija and Perrig's picture selection scheme, Sobrado and Birget's pass-object selection scheme, and Jermyn et al.'s Draw-A-Secret scheme. While graphical passwords may be easier for users to remember than text passwords, they have limitations such as taking longer to create and register, requiring more storage space, and not being very mature yet compared to traditional text-based passwords. The document evaluates the security and usability of different authentication methods.
Graphical Password Authentication



Graphical Password AuthenticationDhvani Shah This document discusses graphical passwords as an alternative to text-based passwords. It outlines the drawbacks of text-based passwords, such as being difficult to remember and vulnerable to brute force and dictionary attacks. The document then proposes a graphical password system that uses images and points of interest on images instead of text for password authentication. This approach aims to make passwords more secure and easier for users to remember.
Graphical Password Authentication



Graphical Password AuthenticationAbhijit Akotkar This document summarizes a thesis on graphical passwords as an alternative to text-based passwords. Graphical passwords use images instead of text and are easier for users to remember. They provide stronger security than text passwords since they are harder to guess via brute force or dictionary attacks. However, graphical passwords are vulnerable to "shoulder surfing" attacks where an observer watches the user enter their password. The document discusses recognition-based and recall-based graphical password techniques and proposes solutions like movable frames to mitigate shoulder surfing risks. It concludes that graphical passwords satisfy the conflicting needs of ease of use and security, but have not been widely adopted and current methods could still be improved.
Image based authentication



Image based authenticationأحلام انصارى Image-based authentication (IBA) uses a set of user-selected images rather than a password for authentication. The IBA system displays an image set including key images mixed with other images. The user is authenticated by correctly identifying their key images. The document discusses IBA in detail, including potential vulnerabilities and methods to counter threats like observation attacks, brute force attacks, and frequency analysis attacks. It also covers the use of CAPTCHAs to distinguish humans and machines.
Graphical password authentication system ppts



Graphical password authentication system pptsNimisha_Goel This document discusses different types of authentication systems including token-based, biometric-based, knowledge-based, recognition-based, pure recall-based, cued recall-based, and hybrid systems. It then focuses on graphical passwords, describing how they work by having users select images in a specific order. The document outlines a project to create an Android application for graphical password authentication to unlock private files using a cued recall system where users must select images in the correct sequence from a random grid. It discusses security considerations like guessing attacks and proposes that this approach provides stronger passwords while increasing the workload for attackers.
Graphical password authentication



Graphical password authenticationAsim Kumar Pathak This document discusses authentication methods and focuses on graphical passwords. It begins with an overview of common authentication methods like text passwords, tokens, and biometrics. It then discusses the drawbacks of text passwords and introduces graphical passwords as an alternative. The document surveys recall-based and recognition-based graphical password techniques and provides examples like Draw-A-Secret and Passfaces. It concludes by noting the advantages of graphical passwords in usability and security but also disadvantages like longer login times and storage requirements.
Graphical password



Graphical passwordvitam,berhampur This document discusses graphical passwords as an alternative to alphanumeric passwords. Graphical passwords work by having users select images or points on images in a specific order. They are generally easier for users to remember but harder for others to guess compared to alphanumeric passwords. The document compares graphical and alphanumeric passwords and describes some simple graphical password schemes, advantages like improved security, and disadvantages like longer login times and vulnerability to shoulder surfing. It proposes solutions like triangle-based and movable frame-based schemes to address the shoulder surfing issue.
Graphical password authentication



Graphical password authenticationshalini singh a study on various techniques on graphical password authentication.
A key area in security research is authentication. Access to system is mostly based on the use of alpha numeric passwords. User felt difficult in remembering the password as that is long and randomly selected and how many passwords will user remember?, it made a complex procedure.
It presents comparison between Persuasive Cued Click Point Graphical Password scheme and Improved Persuasive Cued Click Points. One such category is click-based graphical passwords where a password is composed of a series of clicks on one or more pixel-based images .To log in, user re-select their click-points in the correct order. Click-points that fall within some acceptable tolerance of the original points should be accepted by the system since it is unrealistic to expect users to accurately target individual pixels.
Biometric security system



Biometric security systemMithun Paul The document discusses biometric systems for security. It defines biometrics as measuring biological traits to identify individuals. It then discusses the history of biometrics using fingerprinting in China in the 14th century. It describes the main types of biometric devices as behavioral (e.g. voice, signature) or physical (e.g. fingerprint, face) and lists their common uses including banking, attendance tracking, and data security. Finally, it compares biometric security to other methods and outlines some limitations such as noise in data and variations over time.
Graphical password authentication



Graphical password authenticationSuraj Swarnakar This document discusses graphical password authentication as an alternative to text passwords. It provides an overview of different authentication methods before focusing on the drawbacks of text passwords. Graphical passwords are introduced as a way to make passwords more secure yet easier for users. The document then surveys two categories of graphical passwords - recall-based techniques which require reproducing a password and recognition-based techniques involving identifying pre-selected images. It concludes by discussing the advantages and disadvantages of graphical passwords.
Graphical password authentication



Graphical password authenticationanilaja Password is a secret word or string of characters used to authenticate identity and access resources like accounts, emails, apps, networks, websites and databases. Common types of authentication include token-based using keys or cards, biometric using fingerprints or facial recognition, and knowledge-based using text or graphical passwords, which are the most widely used. Graphical passwords present images and require the user to select or click points in a specific order for authentication. They provide more security than text passwords but also have drawbacks like taking more time and storage and being vulnerable to shoulder surfing.
Graphical Password Authentication



Graphical Password AuthenticationShobha Rani Hi guys , here is new presentation which is related to password authentication named as Graphical Password Authentication.Here i have covered all the topics which are related to GPA .I will also provide a documentation regarding this topic if u need .So please comment below for the document and fallow @shobha rani
Graphical password



Graphical passwordsowji888 This document discusses graphical passwords as an alternative to traditional alphanumeric passwords. It begins with an introduction and definitions of passwords and graphical passwords. It then compares the advantages of graphical passwords, such as being easier for users to remember and harder for attackers to guess. The document outlines a simple graphical password scheme using image click points. It also discusses issues like the shoulder surfing problem where passwords can be observed and solutions to increase security like using triangle shapes or movable frames.
SEMINAR REPORT ON 3D PASSWORD



SEMINAR REPORT ON 3D PASSWORDKarishma Khan This document discusses 3D passwords as a new authentication technique that combines existing methods like text passwords, graphical passwords, and biometrics into a single 3D virtual environment. The user interacts with various objects in the virtual world to create their unique 3D password. When logging in, they must recreate the same sequence of interactions. This makes 3D passwords more secure by increasing the number of possible passwords and making them difficult for attackers to guess. The document outlines how a 3D password system would work, including designing the virtual environment, recording the user's interactions as their password, and guidelines for the virtual world design like real-life similarity, unique distinguishable objects, and appropriate size.
Automatic Attendance system using Facial Recognition



Automatic Attendance system using Facial RecognitionNikyaa7 It is a boimetric based App,which is gradually evolving in the universal boimetric solution with a virtually zero effort from the user end when compared with other boimetric options.
3D Password PPT



3D Password PPTSeminar Links The 3-D password is a multifactor authentication scheme that combines these various authentication schemes into a single 3-D virtual environment. The virtual environment can contain any existing authentication scheme or even any upcoming authentication schemes by adding it as a response to actions performed on an object. Therefore, the resulted password space becomes very large compared to any existing authentication schemes.
Graphical password authentication using pccp with sound signature



Graphical password authentication using pccp with sound signatureeSAT Journals Abstract
Persuasive Cued-Click Point is an advanced method of cued click point of graphical password technique which includes usability and security evaluations. It also useful for reduces hotspot problem and hence it helps the user in selecting password of higher security. This paper includes the persuasion to influence user choice in click based graphical passwords, so that users select more desultory and more difficult to guess the passwords. In this paper includes sound signature for recover the password if user forgot password or click point ,then playing the sound signature which is selected at registration time then it set new password and access the account. This paper include dead zone new concept to avoiding Shoulder surfing attack in graphical password authentication.
Keywords: Graphical Password, Authentication, Password Images, and PCCP etc…
Biometrics Based Authentication AKASH



Biometrics Based Authentication AKASHAkash Deep Maurya This document outlines a presentation on biometric authentication. It discusses authentication and its types, biometrics and why they are used, the characteristics and modes of biometric systems, different biometric techniques including fingerprint, face, iris, hand geometry and voice recognition, a comparison of techniques, applications and limitations. The working process of a biometric system including enrollment, authentication, capturing, pre-processing, feature extraction and matching is also summarized.
Deepfake detection



Deepfake detectionWeverify Deepfake detection models require clean training data to generalize well. The document discusses preprocessing training data by filtering out false detections from face extraction. This improved log loss error on evaluation datasets for models trained with the preprocessed data. However, deepfake detection remains challenging due to limited generalization, overfitting, and the broad scope of possible manipulations. The importance of preprocessing training data and methods to address challenges are discussed.
Graphical password based hybrid authentication system for smart hand held dev...



Graphical password based hybrid authentication system for smart hand held dev...Alexander Decker The document proposes a new hybrid graphical password scheme for authentication on smart handheld devices. It combines recognition and recall-based techniques. During registration, the user selects objects as a graphical password and assigns digits to each object. For authentication, the user selects the objects in order and enters the corresponding digits. The scheme aims to improve usability and security over text passwords while addressing issues like shoulder surfing that graphical passwords often face. It is designed for smart devices like phones which are more convenient than desktop computers.
Graphical Password Authentication



Graphical Password AuthenticationAbha nandan note: A slide for any presentation should not contain more than 4-5 sentences but this presentation has more than the requirement.So, i suggest you to edit as per your requirement and to make it more effective, you can add animations as well.
Face detection and recognition



Face detection and recognitionPankaj Thakur Presentation on Face detection and recognition - Credits goes to Mr Shriram, "https://www.hackster.io/sriram17ei/facial-recognition-opencv-python-9bc724"
Security in Embedded systems 



Security in Embedded systems Naveen Jakhar, I.T.S Topics covered in this presentation:
What is an Embedded system ?
What are MISRA C rules ?
MISRA C conformance and deviations
Tools for MISRA C conformance
Embedded Security Rules
3D Password Presentation



3D Password PresentationSambit Mishra Users nowadays are provided with major password stereotypes such as textual passwords, biometric scanning, tokens or cards (such as an ATM) etc. Mostly textual passwords follow an encryption algorithm as mentioned aboveBiometric scanning is your "natural" signature and Cards or Tokens prove your validity. But some people hate the fact to carry around their cards, some refuse to undergo strong IR exposure to their retinas(Biometric scanning). Mostly textual passwords, nowadays, are kept very simple say a word from the dictionary or their pet names, girlfriends etc. Years back Klein performed such tests and he could crack 10-15 passwords per day. Now with the technology change, fast processors and many tools on the Internet this has become a Child's Play.
Face recognization



Face recognizationleenak770 This document provides an overview of face recognition technology. It discusses 2D and 3D facial recognition, how the technology works by measuring facial features to create a unique face print, hardware and software requirements, advantages like identifying repeat offenders, and applications in security, multimedia, and law enforcement. The conclusion states that while progress has been made, continued work is needed to develop more accurate systems.
Face recognition attendance system



Face recognition attendance systemNaomi Kulkarni This document summarizes a face recognition attendance system project. The project uses face recognition technology to take attendance by comparing captured images to stored student records. It has a completed status. The methodology follows a waterfall model. System diagrams include context, data flow, and architecture diagrams. The database stores student data like name, roll number, attendance, and captured images. The system allows for student registration by capturing images, training the model, and recognizing faces to mark attendance. Developing this project provided experience with real-world software development processes.
Atm using fingerprint



Atm using fingerprintAnIsh Kumar The document discusses using fingerprint biometrics for authentication in ATM machines. Fingerprints provide high universality, distinctiveness, permanence and performance making them suitable for biometric authentication. The technical processes of minutiae extraction from fingerprints and the biometric system workflow are described. Applications of fingerprint ATMs include added security for banking, membership verification, and food/ticket purchases. Potential disadvantages include false acceptance and rejection rates and issues with certain users. Future areas of development include improved matching algorithms and database security to further enhance fingerprint biometrics for ATM authentication.
Graphical User Authentication



Graphical User AuthenticationSarthak Gupta Graphical passwords are an alternative authentication method that uses images instead of text. They are easier for users to remember but take longer to set up and log in. While more secure than text passwords, most schemes are vulnerable to shoulder surfing. However, techniques like movable frames could add security by countering observation. Overall, graphical passwords balance usability and security but require more development to address issues and achieve widespread adoption.
Fingerprint base security system



Fingerprint base security systempraful borad This document describes a fingerprint-based security system project. The system uses a fingerprint sensor and microcontroller to scan fingerprints and compare them to registered fingerprints to grant access. It has two modes - master mode to add and delete users, and user mode to authenticate employees. If the scanned fingerprint matches a registered print, the microcontroller sends the user ID to the computer and activates devices like unlocking a door. The system aims to provide secure access control for organizations using biometric fingerprint identification.
Report (Electromagnetic Password Door Lock System)



Report (Electromagnetic Password Door Lock System)Siang Wei Lee This document describes a student's mini project to develop a microcontroller-based electronic door lock system. It includes chapters on the introduction, design and implementation, and software design. The introduction provides background on embedded systems and microcontrollers. It defines the problem of people forgetting door keys and outlines the project aims to create a cheaper digital door lock system. The design and implementation chapter describes the hardware design including schematic diagrams for the power supply, microcontroller, LCD display, buttons/buzzer/relay, and keypad units. It also includes PCB layout diagrams. The software design chapter discusses configuring the microcontroller ports and LCD, and scanning the keypad using functions to detect button presses and check the password.
Ad
More Related Content
What's hot (20)
Biometric security system



Biometric security systemMithun Paul The document discusses biometric systems for security. It defines biometrics as measuring biological traits to identify individuals. It then discusses the history of biometrics using fingerprinting in China in the 14th century. It describes the main types of biometric devices as behavioral (e.g. voice, signature) or physical (e.g. fingerprint, face) and lists their common uses including banking, attendance tracking, and data security. Finally, it compares biometric security to other methods and outlines some limitations such as noise in data and variations over time.
Graphical password authentication



Graphical password authenticationSuraj Swarnakar This document discusses graphical password authentication as an alternative to text passwords. It provides an overview of different authentication methods before focusing on the drawbacks of text passwords. Graphical passwords are introduced as a way to make passwords more secure yet easier for users. The document then surveys two categories of graphical passwords - recall-based techniques which require reproducing a password and recognition-based techniques involving identifying pre-selected images. It concludes by discussing the advantages and disadvantages of graphical passwords.
Graphical password authentication



Graphical password authenticationanilaja Password is a secret word or string of characters used to authenticate identity and access resources like accounts, emails, apps, networks, websites and databases. Common types of authentication include token-based using keys or cards, biometric using fingerprints or facial recognition, and knowledge-based using text or graphical passwords, which are the most widely used. Graphical passwords present images and require the user to select or click points in a specific order for authentication. They provide more security than text passwords but also have drawbacks like taking more time and storage and being vulnerable to shoulder surfing.
Graphical Password Authentication



Graphical Password AuthenticationShobha Rani Hi guys , here is new presentation which is related to password authentication named as Graphical Password Authentication.Here i have covered all the topics which are related to GPA .I will also provide a documentation regarding this topic if u need .So please comment below for the document and fallow @shobha rani
Graphical password



Graphical passwordsowji888 This document discusses graphical passwords as an alternative to traditional alphanumeric passwords. It begins with an introduction and definitions of passwords and graphical passwords. It then compares the advantages of graphical passwords, such as being easier for users to remember and harder for attackers to guess. The document outlines a simple graphical password scheme using image click points. It also discusses issues like the shoulder surfing problem where passwords can be observed and solutions to increase security like using triangle shapes or movable frames.
SEMINAR REPORT ON 3D PASSWORD



SEMINAR REPORT ON 3D PASSWORDKarishma Khan This document discusses 3D passwords as a new authentication technique that combines existing methods like text passwords, graphical passwords, and biometrics into a single 3D virtual environment. The user interacts with various objects in the virtual world to create their unique 3D password. When logging in, they must recreate the same sequence of interactions. This makes 3D passwords more secure by increasing the number of possible passwords and making them difficult for attackers to guess. The document outlines how a 3D password system would work, including designing the virtual environment, recording the user's interactions as their password, and guidelines for the virtual world design like real-life similarity, unique distinguishable objects, and appropriate size.
Automatic Attendance system using Facial Recognition



Automatic Attendance system using Facial RecognitionNikyaa7 It is a boimetric based App,which is gradually evolving in the universal boimetric solution with a virtually zero effort from the user end when compared with other boimetric options.
3D Password PPT



3D Password PPTSeminar Links The 3-D password is a multifactor authentication scheme that combines these various authentication schemes into a single 3-D virtual environment. The virtual environment can contain any existing authentication scheme or even any upcoming authentication schemes by adding it as a response to actions performed on an object. Therefore, the resulted password space becomes very large compared to any existing authentication schemes.
Graphical password authentication using pccp with sound signature



Graphical password authentication using pccp with sound signatureeSAT Journals Abstract
Persuasive Cued-Click Point is an advanced method of cued click point of graphical password technique which includes usability and security evaluations. It also useful for reduces hotspot problem and hence it helps the user in selecting password of higher security. This paper includes the persuasion to influence user choice in click based graphical passwords, so that users select more desultory and more difficult to guess the passwords. In this paper includes sound signature for recover the password if user forgot password or click point ,then playing the sound signature which is selected at registration time then it set new password and access the account. This paper include dead zone new concept to avoiding Shoulder surfing attack in graphical password authentication.
Keywords: Graphical Password, Authentication, Password Images, and PCCP etc…
Biometrics Based Authentication AKASH



Biometrics Based Authentication AKASHAkash Deep Maurya This document outlines a presentation on biometric authentication. It discusses authentication and its types, biometrics and why they are used, the characteristics and modes of biometric systems, different biometric techniques including fingerprint, face, iris, hand geometry and voice recognition, a comparison of techniques, applications and limitations. The working process of a biometric system including enrollment, authentication, capturing, pre-processing, feature extraction and matching is also summarized.
Deepfake detection



Deepfake detectionWeverify Deepfake detection models require clean training data to generalize well. The document discusses preprocessing training data by filtering out false detections from face extraction. This improved log loss error on evaluation datasets for models trained with the preprocessed data. However, deepfake detection remains challenging due to limited generalization, overfitting, and the broad scope of possible manipulations. The importance of preprocessing training data and methods to address challenges are discussed.
Graphical password based hybrid authentication system for smart hand held dev...



Graphical password based hybrid authentication system for smart hand held dev...Alexander Decker The document proposes a new hybrid graphical password scheme for authentication on smart handheld devices. It combines recognition and recall-based techniques. During registration, the user selects objects as a graphical password and assigns digits to each object. For authentication, the user selects the objects in order and enters the corresponding digits. The scheme aims to improve usability and security over text passwords while addressing issues like shoulder surfing that graphical passwords often face. It is designed for smart devices like phones which are more convenient than desktop computers.
Graphical Password Authentication



Graphical Password AuthenticationAbha nandan note: A slide for any presentation should not contain more than 4-5 sentences but this presentation has more than the requirement.So, i suggest you to edit as per your requirement and to make it more effective, you can add animations as well.
Face detection and recognition



Face detection and recognitionPankaj Thakur Presentation on Face detection and recognition - Credits goes to Mr Shriram, "https://www.hackster.io/sriram17ei/facial-recognition-opencv-python-9bc724"
Security in Embedded systems 



Security in Embedded systems Naveen Jakhar, I.T.S Topics covered in this presentation:
What is an Embedded system ?
What are MISRA C rules ?
MISRA C conformance and deviations
Tools for MISRA C conformance
Embedded Security Rules
3D Password Presentation



3D Password PresentationSambit Mishra Users nowadays are provided with major password stereotypes such as textual passwords, biometric scanning, tokens or cards (such as an ATM) etc. Mostly textual passwords follow an encryption algorithm as mentioned aboveBiometric scanning is your "natural" signature and Cards or Tokens prove your validity. But some people hate the fact to carry around their cards, some refuse to undergo strong IR exposure to their retinas(Biometric scanning). Mostly textual passwords, nowadays, are kept very simple say a word from the dictionary or their pet names, girlfriends etc. Years back Klein performed such tests and he could crack 10-15 passwords per day. Now with the technology change, fast processors and many tools on the Internet this has become a Child's Play.
Face recognization



Face recognizationleenak770 This document provides an overview of face recognition technology. It discusses 2D and 3D facial recognition, how the technology works by measuring facial features to create a unique face print, hardware and software requirements, advantages like identifying repeat offenders, and applications in security, multimedia, and law enforcement. The conclusion states that while progress has been made, continued work is needed to develop more accurate systems.
Face recognition attendance system



Face recognition attendance systemNaomi Kulkarni This document summarizes a face recognition attendance system project. The project uses face recognition technology to take attendance by comparing captured images to stored student records. It has a completed status. The methodology follows a waterfall model. System diagrams include context, data flow, and architecture diagrams. The database stores student data like name, roll number, attendance, and captured images. The system allows for student registration by capturing images, training the model, and recognizing faces to mark attendance. Developing this project provided experience with real-world software development processes.
Atm using fingerprint



Atm using fingerprintAnIsh Kumar The document discusses using fingerprint biometrics for authentication in ATM machines. Fingerprints provide high universality, distinctiveness, permanence and performance making them suitable for biometric authentication. The technical processes of minutiae extraction from fingerprints and the biometric system workflow are described. Applications of fingerprint ATMs include added security for banking, membership verification, and food/ticket purchases. Potential disadvantages include false acceptance and rejection rates and issues with certain users. Future areas of development include improved matching algorithms and database security to further enhance fingerprint biometrics for ATM authentication.
Graphical User Authentication



Graphical User AuthenticationSarthak Gupta Graphical passwords are an alternative authentication method that uses images instead of text. They are easier for users to remember but take longer to set up and log in. While more secure than text passwords, most schemes are vulnerable to shoulder surfing. However, techniques like movable frames could add security by countering observation. Overall, graphical passwords balance usability and security but require more development to address issues and achieve widespread adoption.
Similar to Image Based Password Authentication for Illiterate using Touch screen by Deepak Yadav (20)
Fingerprint base security system



Fingerprint base security systempraful borad This document describes a fingerprint-based security system project. The system uses a fingerprint sensor and microcontroller to scan fingerprints and compare them to registered fingerprints to grant access. It has two modes - master mode to add and delete users, and user mode to authenticate employees. If the scanned fingerprint matches a registered print, the microcontroller sends the user ID to the computer and activates devices like unlocking a door. The system aims to provide secure access control for organizations using biometric fingerprint identification.
Report (Electromagnetic Password Door Lock System)



Report (Electromagnetic Password Door Lock System)Siang Wei Lee This document describes a student's mini project to develop a microcontroller-based electronic door lock system. It includes chapters on the introduction, design and implementation, and software design. The introduction provides background on embedded systems and microcontrollers. It defines the problem of people forgetting door keys and outlines the project aims to create a cheaper digital door lock system. The design and implementation chapter describes the hardware design including schematic diagrams for the power supply, microcontroller, LCD display, buttons/buzzer/relay, and keypad units. It also includes PCB layout diagrams. The software design chapter discusses configuring the microcontroller ports and LCD, and scanning the keypad using functions to detect button presses and check the password.
Alcohol report



Alcohol reportchandan kumar This document describes a microcontroller-based automatic engine locking system for drunken drivers. The system uses an AT89S52 microcontroller and various hardware components like an alcohol detection sensor, buzzer, LCD display, motors and more. It detects alcohol levels using a sensor and locks the engine by activating a relay if alcohol is detected above the set limit, simulating the locking process. The system is programmed using Keil software and aims to prevent accidents caused by drunk driving.
Microcontroller based automatic engine locking system for drunken drivers



Microcontroller based automatic engine locking system for drunken driversVinny Chweety This document describes a mini project report on a microcontroller-based automatic engine locking system for drunken drivers. The system uses an AT89S52 microcontroller and various hardware components like an alcohol detection sensor, buzzer, LCD display, motors/engine, and other supporting circuitry. If the alcohol detection sensor detects alcohol levels above a set limit from the driver's breath, the microcontroller will lock the engine by activating a relay to prevent drunken driving and accidents. The project aims to increase road safety by preventing intoxicated individuals from operating vehicles.
embedded systems



embedded systemsShanmuga Vadivu This document describes a touch screen and Zigbee based control system for apartments using an embedded system. The system uses a microcontroller, touch screen, Zigbee modules, and other components to allow users to control home appliances in their apartment wirelessly via the touch screen or voice commands. The microcontroller interfaces with the touch screen, Zigbee modules, and other devices. It receives input from the touch screen or other inputs and sends wireless signals via Zigbee to control appliances like lights and fans. The system aims to provide a compact, user-friendly, and low-cost way to remotely control home appliances within an apartment.
Presentation on Embedded system using micro controller by PARAS JHA



Presentation on Embedded system using micro controller by PARAS JHAParas Jha in this presentation you have to seen some topics details on embedded system using pic micro controller
Report on Embedded Based Home security system



Report on Embedded Based Home security systemNIT srinagar This document describes an embedded home security system that uses various sensors and components. The system uses an AT89S52 microcontroller along with an IR sensor, LCD display, GSM module, LEDs and other components. The IR sensor detects intruders and the GSM module sends alerts. It provides automated security monitoring and user authentication to prevent break-ins. The system is designed to be effective, practical and reasonably priced for home security.
intership ppt see.pptx



intership ppt see.pptxManojG81 This document summarizes an internship project on embedded C and digital voice recorders. The project involved designing and prototyping a digital voice recorder using an ATmega32U4 microcontroller on a development board. Key aspects of the project included input conditioning using a microphone, amplification, and filtering stages to prepare the audio for recording. Output conditioning involved pulse-width modulation of the recorded audio and reconstruction filtering to produce an analog waveform for playback. Testing showed the input amplification provided a suitable volume level and the output amplification allowed for increased listening volume. The project demonstrated the application of electronic and software design concepts to create a functional digital voice recorder.
Decibel meter using IoT with notice board



Decibel meter using IoT with notice boardIRJET Journal This document describes a system to monitor sound levels using an IoT device and display the results. A sound sensor measures noise intensity and sends the data to a NodeMCU microcontroller via WiFi. The NodeMCU then uploads the real-time data to a cloud database and displays it on a local LCD screen. The system can detect low, moderate, and high noise levels and activate different colored LEDs and a buzzer accordingly. The cloud database allows monitoring sound levels remotely from any location. The system is intended to help control and monitor noise, especially in industrial areas.
Industrial monitoring and control system using android application



Industrial monitoring and control system using android applicationAvinash Vemula Automation takes the complete control of total plants few authentication and manual actions are needed from user side for completing action .Hence there is a must situation for users presence at all times in the control for taking some timely needed control actions. The proposed system provides a good solution to this problem. The whole control room environment is additionally implemented in the arm-android platform and the same is communicated to the process through Bluetooth. Now the user in control can use mobile at anytime, anywhere to monitor and control the whole plant.8051 is used here for acquiring process control parameters from the sensors like temperature, gas etc and transmitting it via a Bluetooth module to an android device. Hence the parameter values can be monitored and stored simultaneously.
ESP32 CAM Face Detection Door Lock



ESP32 CAM Face Detection Door LockIRJET Journal 1. The document describes a smart door lock system that uses facial recognition with an ESP32 CAM microcontroller to lock and unlock doors. It analyzes faces detected by the ESP32 CAM and only unlocks the door if the face matches an authorized user that was previously enrolled in the system.
2. The system is powered by batteries and works by comparing detected faces in real-time to authorized faces stored during the enrollment process. When an enrolled face is recognized, the ESP32 CAM sends a signal to a relay module that activates the solenoid lock to unlock the door.
3. The ESP32 CAM provides video streaming and face detection capabilities. The overall circuit diagram connects the ESP32 CAM to a relay module
Wireless appliances control report



Wireless appliances control reportengineerssolution This document is a report on a wireless based control project submitted for a Bachelor of Technology degree. It describes a wireless secured lock system using an AT89S52 microcontroller that allows only authorized persons to access appliances via entering a code on a keypad. The system uses RF transmission at 433MHz between a transmitter with an encoder, and a receiver with a decoder connected to the microcontroller. If the entered code matches the stored code, the microcontroller activates a relay to power the appliance. The report includes block diagrams of the system components, descriptions of the microcontroller and other ICs, the circuit diagram, and the software flowchart.
Debasish sahu embedded software engineer 2 years 



Debasish sahu embedded software engineer 2 years Debasish Sahu Around 2 years of experience as Embedded Software Engineer .Hands on Experience in C and C++.Expertise on developing the solutions using AVR Studio, KEIL compiler.Expertise on usability of Proteus 7 professional for hardware designing.Knowledge in Software development life cycle processes.Knowledge in Microcontroller Concepts Good in Analyzing & Understanding requirements.Good Interpersonal skills, commitment, result oriented, hardworking and zeal to learn new technologies.
final project report_full edit



final project report_full editSayam Roy This document is a project report on a GSM based robotic vehicle. It was submitted by 4 students - Nipun Nair, Abir Bose, Sayam Roy, and Shashi Bhushan - in partial fulfillment of their Bachelor of Engineering degree in Electrical and Electronics Engineering from St. Peter's University. The report includes an abstract, introduction to embedded systems, description of the project block diagram, list of hardware components used, schematic diagram, coding, testing procedures, results, and conclusion.
Electronic eye for security system @1000KV Technologies 9030844877



Electronic eye for security system @1000KV Technologies 90308448771000kv technologies electronics engineering live projects abstracts
electronics projects, electronics projects for engineering final year students, electronics and communication engineering projects for final year students,100kv,1000kv,1000kv technologies,1000kv projects,technologies,live projects,Hyderabad live projects,live projects in, diploma low cost projects,1000kv projects, , academic projects,btech live projects,Hyderabad,1000kilovolts,1000kilovolts technologies ,btech main projects ,
REAL TIME FACE DETECTING UNAUTHORIZED HUMAN MOVEMENT USING ESP 32 CAM MODULE



REAL TIME FACE DETECTING UNAUTHORIZED HUMAN MOVEMENT USING ESP 32 CAM MODULEIRJET Journal This document describes a real-time face detection system using an ESP 32 CAM module to detect unauthorized human movement and provide security. The system uses a PIR motion sensor to detect movement, the ESP 32 CAM module to capture images with its in-built camera, and sends the images to an Android device via a Blynk app. It also controls an electric mini lock using a relay connected to the ESP 32 CAM module. The system is programmed in Python and detects movement, captures images, sends notifications to alert the owner, and can control the lock based on commands sent through the Blynk app. The goal is to provide security and automation for homes and businesses using computer vision and IoT technologies.
Report (2)



Report (2)Shivangi Dwivedi This document provides an overview of embedded systems and interfacing with the ATmega8 microcontroller. It discusses the characteristics of embedded systems and gives examples such as appliances, medical devices, vehicles, and more. It also covers the 8051 and AVR microcontrollers, focusing on the ATmega8's architecture, programming, and interfacing with various components like LEDs, LCDs, seven segment displays, motors, and sensors. The goal is to provide knowledge about embedded systems and practical experience interfacing the ATmega8 microcontroller.
Smart home project technical paper



Smart home project technical paperAnwar Al Ahdab This document describes a smart home project that uses an embedded web server to control various smart home functions. It includes 6 chapters that cover the introduction, main block diagrams, components and cost analysis, design approach and details, schedule and tasks, and conclusion. The introduction defines what a smart home is and describes the features of the project, which aims to implement a low-cost smart home system. The main block diagrams section outlines the use of an Ethernet module, wireless connectivity using ZigBee, and a sensor network with a centralized controller. The design approach provides circuit diagrams and code for an access control system and main control interface.
Gesture control robot using accelerometer documentation



Gesture control robot using accelerometer documentationRajendra Prasad The document provides an overview of embedded systems and describes a gesture controlled robot project. It discusses the basic blocks of an embedded system including the CPU, memory, input/output devices and communication interfaces. It then describes the transmitter and receiver blocks of the gesture controlled robot. The transmitter contains an accelerometer, analog to digital converter, encoder and RF transmitter. The receiver contains a microcontroller, decoder, motor driver and RF receiver. It explains how hand gestures are sensed and transmitted wirelessly to control the robot's movement. Finally, it provides background on the 8051 microcontroller family used in the project.
Ad
Recently uploaded (20)
Drupalcamp Finland – Measuring Front-end Energy Consumption



Drupalcamp Finland – Measuring Front-end Energy ConsumptionExove How to measure web front-end energy consumption using Firefox Profiler. Presented in DrupalCamp Finland on April 25th, 2025.
Andrew Marnell: Transforming Business Strategy Through Data-Driven Insights



Andrew Marnell: Transforming Business Strategy Through Data-Driven InsightsAndrew Marnell With expertise in data architecture, performance tracking, and revenue forecasting, Andrew Marnell plays a vital role in aligning business strategies with data insights. Andrew Marnell’s ability to lead cross-functional teams ensures businesses achieve sustainable growth and operational excellence.
Semantic Cultivators : The Critical Future Role to Enable AI



Semantic Cultivators : The Critical Future Role to Enable AIartmondano By 2026, AI agents will consume 10x more enterprise data than humans, but with none of the contextual understanding that prevents catastrophic misinterpretations.
Increasing Retail Store Efficiency How can Planograms Save Time and Money.pptx



Increasing Retail Store Efficiency How can Planograms Save Time and Money.pptxAnoop Ashok In today's fast-paced retail environment, efficiency is key. Every minute counts, and every penny matters. One tool that can significantly boost your store's efficiency is a well-executed planogram. These visual merchandising blueprints not only enhance store layouts but also save time and money in the process.
Quantum Computing Quick Research Guide by Arthur Morgan



Quantum Computing Quick Research Guide by Arthur MorganArthur Morgan This is a Quick Research Guide (QRG).
QRGs include the following:
- A brief, high-level overview of the QRG topic.
- A milestone timeline for the QRG topic.
- Links to various free online resource materials to provide a deeper dive into the QRG topic.
- Conclusion and a recommendation for at least two books available in the SJPL system on the QRG topic.
QRGs planned for the series:
- Artificial Intelligence QRG
- Quantum Computing QRG
- Big Data Analytics QRG
- Spacecraft Guidance, Navigation & Control QRG (coming 2026)
- UK Home Computing & The Birth of ARM QRG (coming 2027)
Any questions or comments?
- Please contact Arthur Morgan at [email protected].
100% human made.
The Evolution of Meme Coins A New Era for Digital Currency ppt.pdf



The Evolution of Meme Coins A New Era for Digital Currency ppt.pdfAbi john Analyze the growth of meme coins from mere online jokes to potential assets in the digital economy. Explore the community, culture, and utility as they elevate themselves to a new era in cryptocurrency.
Cyber Awareness overview for 2025 month of security



Cyber Awareness overview for 2025 month of securityriccardosl1 Cyber awareness training educates employees on risk associated with internet and malicious emails
Heap, Types of Heap, Insertion and Deletion



Heap, Types of Heap, Insertion and DeletionJaydeep Kale This pdf will explain what is heap, its type, insertion and deletion in heap and Heap sort
DevOpsDays Atlanta 2025 - Building 10x Development Organizations.pptx



DevOpsDays Atlanta 2025 - Building 10x Development Organizations.pptxJustin Reock Building 10x Organizations with Modern Productivity Metrics
10x developers may be a myth, but 10x organizations are very real, as proven by the influential study performed in the 1980s, ‘The Coding War Games.’
Right now, here in early 2025, we seem to be experiencing YAPP (Yet Another Productivity Philosophy), and that philosophy is converging on developer experience. It seems that with every new method we invent for the delivery of products, whether physical or virtual, we reinvent productivity philosophies to go alongside them.
But which of these approaches actually work? DORA? SPACE? DevEx? What should we invest in and create urgency behind today, so that we don’t find ourselves having the same discussion again in a decade?
AI Changes Everything – Talk at Cardiff Metropolitan University, 29th April 2...



AI Changes Everything – Talk at Cardiff Metropolitan University, 29th April 2...Alan Dix Talk at the final event of Data Fusion Dynamics: A Collaborative UK-Saudi Initiative in Cybersecurity and Artificial Intelligence funded by the British Council UK-Saudi Challenge Fund 2024, Cardiff Metropolitan University, 29th April 2025
https://alandix.com/academic/talks/CMet2025-AI-Changes-Everything/
Is AI just another technology, or does it fundamentally change the way we live and think?
Every technology has a direct impact with micro-ethical consequences, some good, some bad. However more profound are the ways in which some technologies reshape the very fabric of society with macro-ethical impacts. The invention of the stirrup revolutionised mounted combat, but as a side effect gave rise to the feudal system, which still shapes politics today. The internal combustion engine offers personal freedom and creates pollution, but has also transformed the nature of urban planning and international trade. When we look at AI the micro-ethical issues, such as bias, are most obvious, but the macro-ethical challenges may be greater.
At a micro-ethical level AI has the potential to deepen social, ethnic and gender bias, issues I have warned about since the early 1990s! It is also being used increasingly on the battlefield. However, it also offers amazing opportunities in health and educations, as the recent Nobel prizes for the developers of AlphaFold illustrate. More radically, the need to encode ethics acts as a mirror to surface essential ethical problems and conflicts.
At the macro-ethical level, by the early 2000s digital technology had already begun to undermine sovereignty (e.g. gambling), market economics (through network effects and emergent monopolies), and the very meaning of money. Modern AI is the child of big data, big computation and ultimately big business, intensifying the inherent tendency of digital technology to concentrate power. AI is already unravelling the fundamentals of the social, political and economic world around us, but this is a world that needs radical reimagining to overcome the global environmental and human challenges that confront us. Our challenge is whether to let the threads fall as they may, or to use them to weave a better future.
#StandardsGoals for 2025: Standards & certification roundup - Tech Forum 2025



#StandardsGoals for 2025: Standards & certification roundup - Tech Forum 2025BookNet Canada Book industry standards are evolving rapidly. In the first part of this session, we’ll share an overview of key developments from 2024 and the early months of 2025. Then, BookNet’s resident standards expert, Tom Richardson, and CEO, Lauren Stewart, have a forward-looking conversation about what’s next.
Link to recording, transcript, and accompanying resource: https://bnctechforum.ca/sessions/standardsgoals-for-2025-standards-certification-roundup/
Presented by BookNet Canada on May 6, 2025 with support from the Department of Canadian Heritage.
What is Model Context Protocol(MCP) - The new technology for communication bw...



What is Model Context Protocol(MCP) - The new technology for communication bw...Vishnu Singh Chundawat The MCP (Model Context Protocol) is a framework designed to manage context and interaction within complex systems. This SlideShare presentation will provide a detailed overview of the MCP Model, its applications, and how it plays a crucial role in improving communication and decision-making in distributed systems. We will explore the key concepts behind the protocol, including the importance of context, data management, and how this model enhances system adaptability and responsiveness. Ideal for software developers, system architects, and IT professionals, this presentation will offer valuable insights into how the MCP Model can streamline workflows, improve efficiency, and create more intuitive systems for a wide range of use cases.
Technology Trends in 2025: AI and Big Data Analytics



Technology Trends in 2025: AI and Big Data AnalyticsInData Labs At InData Labs, we have been keeping an ear to the ground, looking out for AI-enabled digital transformation trends coming our way in 2025. Our report will provide a look into the technology landscape of the future, including:
-Artificial Intelligence Market Overview
-Strategies for AI Adoption in 2025
-Anticipated drivers of AI adoption and transformative technologies
-Benefits of AI and Big data for your business
-Tips on how to prepare your business for innovation
-AI and data privacy: Strategies for securing data privacy in AI models, etc.
Download your free copy nowand implement the key findings to improve your business.
Mobile App Development Company in Saudi Arabia



Mobile App Development Company in Saudi ArabiaSteve Jonas EmizenTech is a globally recognized software development company, proudly serving businesses since 2013. With over 11+ years of industry experience and a team of 200+ skilled professionals, we have successfully delivered 1200+ projects across various sectors. As a leading Mobile App Development Company In Saudi Arabia we offer end-to-end solutions for iOS, Android, and cross-platform applications. Our apps are known for their user-friendly interfaces, scalability, high performance, and strong security features. We tailor each mobile application to meet the unique needs of different industries, ensuring a seamless user experience. EmizenTech is committed to turning your vision into a powerful digital product that drives growth, innovation, and long-term success in the competitive mobile landscape of Saudi Arabia.
Procurement Insights Cost To Value Guide.pptx



Procurement Insights Cost To Value Guide.pptxJon Hansen Procurement Insights integrated Historic Procurement Industry Archives, serves as a powerful complement — not a competitor — to other procurement industry firms. It fills critical gaps in depth, agility, and contextual insight that most traditional analyst and association models overlook.
Learn more about this value- driven proprietary service offering here.
Designing Low-Latency Systems with Rust and ScyllaDB: An Architectural Deep Dive



Designing Low-Latency Systems with Rust and ScyllaDB: An Architectural Deep DiveScyllaDB Want to learn practical tips for designing systems that can scale efficiently without compromising speed?
Join us for a workshop where we’ll address these challenges head-on and explore how to architect low-latency systems using Rust. During this free interactive workshop oriented for developers, engineers, and architects, we’ll cover how Rust’s unique language features and the Tokio async runtime enable high-performance application development.
As you explore key principles of designing low-latency systems with Rust, you will learn how to:
- Create and compile a real-world app with Rust
- Connect the application to ScyllaDB (NoSQL data store)
- Negotiate tradeoffs related to data modeling and querying
- Manage and monitor the database for consistently low latencies
Into The Box Conference Keynote Day 1 (ITB2025)



Into The Box Conference Keynote Day 1 (ITB2025)Ortus Solutions, Corp This is the keynote of the Into the Box conference, highlighting the release of the BoxLang JVM language, its key enhancements, and its vision for the future.
Splunk Security Update | Public Sector Summit Germany 2025



Splunk Security Update | Public Sector Summit Germany 2025Splunk Splunk Security Update
Sprecher: Marcel Tanuatmadja
How Can I use the AI Hype in my Business Context?



How Can I use the AI Hype in my Business Context?Daniel Lehner 𝙄𝙨 𝘼𝙄 𝙟𝙪𝙨𝙩 𝙝𝙮𝙥𝙚? 𝙊𝙧 𝙞𝙨 𝙞𝙩 𝙩𝙝𝙚 𝙜𝙖𝙢𝙚 𝙘𝙝𝙖𝙣𝙜𝙚𝙧 𝙮𝙤𝙪𝙧 𝙗𝙪𝙨𝙞𝙣𝙚𝙨𝙨 𝙣𝙚𝙚𝙙𝙨?
Everyone’s talking about AI but is anyone really using it to create real value?
Most companies want to leverage AI. Few know 𝗵𝗼𝘄.
✅ What exactly should you ask to find real AI opportunities?
✅ Which AI techniques actually fit your business?
✅ Is your data even ready for AI?
If you’re not sure, you’re not alone. This is a condensed version of the slides I presented at a Linkedin webinar for Tecnovy on 28.04.2025.
What is Model Context Protocol(MCP) - The new technology for communication bw...



What is Model Context Protocol(MCP) - The new technology for communication bw...Vishnu Singh Chundawat
Ad
Image Based Password Authentication for Illiterate using Touch screen by Deepak Yadav
- 1. Project Team: Deepak Yadav (1001031031) Deepak Kumar (1001031029) Arvind Yadav (1001031022) Deepankar Ram (1001031032)
- 2. Table of Content Introduction Hardware Description Advantages and disadvantages Procedural steps for compilation, simulation and dumping Conclusion References
- 3. Introduction The main aim of this project is to provide a security system for illiterates. Since the images are more easily to recalling in comparison to string of character. The images are displayed on touch screen ,one can enter correct sequences of images get authenticated. Gives exposure about how touch screen interface in our practical life. It can be easily installed in industries ,houses ,poultry form for security .
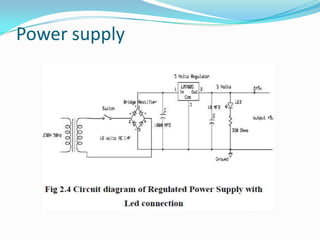
- 5. Hardware Description The major building blocks of this project are: Regulated power supply with voltage regulator Micro controller Touch screen sensor Stepper motor Buzzer
- 6. Power supply
- 7. Microcontroller (PIC16F72) 1. 2. 3. a. The microcontroller used in this project is PIC16F72. The PIC families of microcontrollers are developed by Microchip Technology Inc. PIC microcontrollers: PIC12CXXX 12/14-bit program word . b. c. d. PIC 16C5X 12-bit program word . PIC16CXXX and PIC16FXXX 14-bit program word . PIC17CXXX and PIC18CXXX 16-bit program word.
- 8. Technologies of Touch Screen There are a number of types of touch screen technology. 1. Resistive 2. Surface acoustic wave 3. Capacitive 4. Surface capacitance 5. Projected capacitance 6. Infrared 7. Strain gauge 8. Optical imaging
- 9. Working of Resistive Touch screens 1. Polyester Film 2. Upper Resistive 3. 4. 5. 6. 7. circuit Layer Conductive ITO (Transparent Metal Coating). Lower Resistive Circuit Layer Insulating Dots Glass/AcrylicSubstrat -e Touch screen
- 10. Continue…. The contact can close the switch an generated Voltages. Touch screen controller convert it into (X,Y) Co-ordinate system and hence the position of touch is sense by controller easily.
- 11. Stepper motor It is gear based motor. The stepper motor are connected with ULN2803 driver. When the correct password entered the lock attached to the motor is open.
- 12. Buzzer Basically it works as sound source based on piezoelectric diaphragm. It is consists of electrode ,when dc voltage applied across electrode produces sound. To switch on buzzer -high 1 To switch off buzzer -low 1
- 13. Advantages Easily recalling. Image based password is more secure than text based password. Less vulnerable. Easily installation method.
- 14. Disadvantages Since it is totally based on password hence shoulder surfing can reduce the security of system. Taken more prevention for touch screen safety.
- 15. Procedural steps for compilation, simulation and dumping PIC compiler is used for programming. After programming run the programs, it generated a .hex extension file. The .hex extension file are dumping into microcontroller using PIC kit programmer.
- 16. Conclusion Image password is easily remember than string of character password. Image password is more secure than text based password. Less vulnerable by attacker. Know the exposure of touch screen interface in practical life. Shoulder surfing reduce the security of system.
- 18. Thank you


