Install Windows Server 2012 Step-by-Step
84 likes28,166 views
This document provides a step-by-step guide to installing Windows Server 2012. It was written by Mehdi Poustchi Amin, a network administrator and founder of Iran's honeynet project, and presented in India in October 2013. The guide outlines the installation process and is intended to assist administrators with deploying Windows Server 2012.
1 of 23






















Ad
Recommended
Install Windows Server 2008 Step-by-Step
Install Windows Server 2008 Step-by-StepMehdi Poustchi Amin This document provides a step-by-step guide to installing Windows Server 2008. It was written by Mehdi Poustchi Amin, a network administrator and founder of Iran's honeynet project, and presents the installation process.
Install windows 8.1 Pro
Install windows 8.1 ProMehdi Poustchi Amin To install Windows 8.1 Pro, download the installation files, run the setup.exe file to begin installation, and follow the on-screen instructions to accept license terms, select a custom or upgrade installation, and enter your product key. The installation will then format your hard drive, copy files, configure settings, and install updates so you have a functional Windows 8.1 Pro system.
Install Linux CentOS 7.0
Install Linux CentOS 7.0Mehdi Poustchi Amin This document provides instructions for installing Linux CentOS 7.0 in 3 steps. It is authored by Sayyed Mehdi Poustchi Amin, a network administrator and founder of Iran's honeynet project. Amin has several IT certifications and provides his contact information.
VMware Workstation 7
VMware Workstation 7Mehdi Poustchi Amin VMware Workstation 7.1 is virtualization software that allows users to run multiple operating systems on a single computer. It has a 30-day trial version available for download from VMware.com for $189. The document was presented by Mehdi Poustchi Amin, a network administrator and founder of Iran's honeynet project who was giving a presentation on VMware Workstation virtualization.
VMware Server 2
VMware Server 2Mehdi Poustchi Amin VMware Installation & Configuration document discusses VMware Server 2 for both Windows and Linux versions. It provides information on VMware Server software and is presented by Sayyed Mehdi Poustchi Amin, a network administrator and founder of Iran's honeynet project who works at Azad University of Mashhad and SICSR.
VMware ESX 3.5
VMware ESX 3.5Mehdi Poustchi Amin This document provides information on installing and configuring VMware ESX Server 3.5 and VMware Infrastructure Client 2.5. It was presented by Sayyed Mehdi Poustchi Amin, who has several IT certifications and works as a network administrator and research assistant. The presentation covers VMware's network virtualization technology using ESX Server and how to manage the virtual infrastructure with the Infrastructure Client software.
Install Linux CentOS 6 x86_64 - minimum installation
Install Linux CentOS 6 x86_64 - minimum installationMehdi Poustchi Amin Installing Linux in 3 steps: download the CentOS 6.4 x86_64 ISO file, burn it to a CD or USB drive, then boot from the disc and select the "Minimum installation" option to quickly install the basic Linux system files and utilities.
Pascal-Armand-resume
Pascal-Armand-resumevisual_resume Pascal Armand is a system administrator with over 10 years of experience administrating Linux systems. He has worked as a Linux system administrator for intrinsec and Alter Way. Pascal has education in commerce and management from ISCG Institut supérieur commerce & gestion from 2003 to 2005. His skills include Linux, open source, Debian, MySQL, and Bash.
Honeypots in Cyberwar
Honeypots in CyberwarMehdi Poustchi Amin Honeypots and honeynets are used to study cyber attacks. A honeypot is a computer system set up to attract cyber attacks so threats can be observed and analyzed. A honeynet contains multiple honeypots and allows attacks on an entire network to be monitored. Deploying honeypots provides benefits like risk mitigation, intrusion detection, and research opportunities to study attacker techniques. However, honeypots also have downsides like limited visibility and potential additional security risks if compromised.
How to use OpenPGP for Email Encryption & Signing
How to use OpenPGP for Email Encryption & SigningMehdi Poustchi Amin OpenPGP is a standard for encrypting and digitally signing emails. It allows users to encrypt emails to ensure only the intended recipient can read the message. Digital signatures authenticate who sent the email and confirm the message contents were not altered. OpenPGP provides security and privacy for email communication.
How to create Self-Sign Certificate by using OpenSSL
How to create Self-Sign Certificate by using OpenSSLMehdi Poustchi Amin This document provides instructions for creating a self-signed certificate using OpenSSL. It outlines downloading and installing OpenSSL and Visual C++ 2008, changing environment variables, downloading an OpenSSL configuration file, making directories, creating required files, entering a password and information, generating a server certificate, and copying and installing the certificate.
Virtualization
VirtualizationMehdi Poustchi Amin VMware provides server virtualization software that allows multiple virtual machines to run on the same physical server. This increases hardware utilization and consolidation ratios. Key benefits include reduced costs from lower hardware, power, cooling, and real estate needs as well as faster provisioning times. VMware's product line includes ESX Server, VirtualCenter, VMotion, DRS, HA, and other tools for managing and optimizing virtualized environments. Customers report benefits like supporting more workloads without increasing staff and reducing provisioning time from weeks to hours.
All about Honeypots & Honeynets
All about Honeypots & HoneynetsMehdi Poustchi Amin The document discusses honeypots and honeynets. It defines a honeypot as a decoy system intended to be attacked to gather threat intelligence. Honeynets contain multiple honeypots within a controlled network for monitoring. The document outlines the benefits of deploying honeypots, such as risk mitigation and research. It also discusses techniques for installing and detecting honeypots, and the future of honeypot technologies.
Configuring RAID 1 on CentOs
Configuring RAID 1 on CentOsMehdi Poustchi Amin This document provides biographical information about Mehdi Poustchi Amin and Hedieh Amirjahanshahi, including their certifications and place of study from 2007 to 2008 at Symbiosis Institute of Computer Studies & Research.
Installing Parsix 1
Installing Parsix 1Mehdi Poustchi Amin This document provides biographical information about two IT professionals - Mehdi Poustchi Amin who holds MCSA/MCSE certifications, and Hedieh Amirjahanshahi who holds an MCP certification. Both studied at Symbiosis Institute of Computer Studies & Research from 2007 to 2008. The document also includes a link to Mehdi Poustchi Amin's blog.
Installing Debian 4
Installing Debian 4Mehdi Poustchi Amin This document provides biographical information about two IT professionals, Mehdi Poustchi Amin who holds MCSA/MCSE certifications, and Hedieh Amirjahanshahi who holds an MCP certification. It also mentions they attended Symbiosis Institute of Computer Studies & Research from 2008 to 2009. A link to Mehdi Poustchi Amin's blog is provided at the bottom.
Installing Mandriva 2008
Installing Mandriva 2008Mehdi Poustchi Amin SICSR is an institute that provides computer studies and research. It has provided education and research in these areas since 2008. The document likely contains details about the programs, faculty, or achievements of SICSR during the 2008-2009 period.
Installing Fedora 8
Installing Fedora 8Mehdi Poustchi Amin This document provides biographical information about two IT professionals, Mehdi Poustchi Amin who holds MCSA/MCSE certifications and Hedieh Amirjahanshahi who holds an MCP certification. It also lists their affiliation with the Symbiosis Institute of Computer Studies & Research from 2007 to 2008. It includes a link to Mehdi Poustchi Amin's blogspot page.
Installing Windows2008 Server
Installing Windows2008 ServerMehdi Poustchi Amin This document provides biographical information about Mehdi Poustchi, including his affiliation with Symbiosis Institute of Computer Studies & Research from 2008 to 2009. It also includes a link to his blogspot page at http://poustchi.blogspot.com which likely provides additional biographical details.
Proxy Servers & Firewalls
Proxy Servers & FirewallsMehdi Poustchi Amin Proxy servers and firewalls both act as gateways between internal networks and external networks like the internet. Proxy servers improve performance by caching frequently requested content, control bandwidth usage, and filter requests. Firewalls protect internal networks from external threats by packet filtering, analyzing packets, providing proxy services, and logging and alerting administrators of potential threats. Popular proxy software includes Squid, ISA Server, and WinRoute, while popular firewall software includes ISA Server, Cisco PIX, Norton Internet Security, and ZoneAlarm.
Installing Linux CentOs 5.0 Step-by-Step
Installing Linux CentOs 5.0 Step-by-StepMehdi Poustchi Amin This document provides biographical information about Mehdi Poustchi, including that he attended Symbiosis Institute of Computer Studies & Research from 2007 to 2008. It also includes a link to his blogspot blog.
Installing RHEL 5 Linux RedHat Enterprise Edition step-by-step
Installing RHEL 5 Linux RedHat Enterprise Edition step-by-stepMehdi Poustchi Amin This document provides information about an individual named Mehdi Poustchi Amin Hedieh Amirjahanshahi and their association with Symbiosis Institute of Computer Studies & Research (SICSR) from 2007 to 2008.
Installing Linux RedHat Enterprise Edition
Installing Linux RedHat Enterprise EditionMehdi Poustchi Amin Installing Linux RedHat Enterprise Edition Step bye Step
Installing Ubuntu7.04 Linux
Installing Ubuntu7.04 LinuxMehdi Poustchi Amin The document is a research paper written by Hedieh AmirJahanshahi, Mehdi Poustchi Amin, and others from the Symbiosis Institute of Computers Studies & Research in July 2007. It likely discusses topics related to computers and research, though no specific details about the content are provided in this brief metadata.
Installing Mandriva Linux
Installing Mandriva LinuxMehdi Poustchi Amin The document is a research paper written by Hedieh AmirJahanshahi, Mehdi Poustchi Amin, and others from Symbiosis Institute of Computers Studies & Research in June 2007. It likely discusses topics related to computers and research, though no specific details about the content are provided in this brief metadata.
Installing Windows2000 Server
Installing Windows2000 ServerMehdi Poustchi Amin This document provides step-by-step instructions for installing Windows 2000 Server. It describes downloading and running the installation files, selecting installation options such as computer name and time zone, and completing the basic configuration of a new Windows 2000 Server installation named MYSERVER in Tehran, Iran.
Installing Debian Linux
Installing Debian LinuxMehdi Poustchi Amin Installing Debian Linux is a step-by-step guide written by Mehdi Poustchi, Amin Hedieh, and AmirJahanshahi from the Symbiosis Institute of Computers Studies & Research in June 2007. The document provides instructions for installing the Debian Linux operating system.
cnc-processing-centers-centateq-p-110-en.pdf
cnc-processing-centers-centateq-p-110-en.pdfAmirStern2 מרכז עיבודים תעשייתי בעל 3/4/5 צירים, עד 22 החלפות כלים עם כל אפשרויות העיבוד הדרושות. בעל שטח עבודה גדול ומחשב נוח וקל להפעלה בשפה העברית/רוסית/אנגלית/ספרדית/ערבית ועוד..
מסוגל לבצע פעולות עיבוד שונות המתאימות לענפים שונים: קידוח אנכי, אופקי, ניסור, וכרסום אנכי.
Connecting Data and Intelligence: The Role of FME in Machine Learning
Connecting Data and Intelligence: The Role of FME in Machine LearningSafe Software In this presentation, we want to explore powerful data integration and preparation for Machine Learning. FME is known for its ability to manipulate and transform geospatial data, connecting diverse data sources into efficient and automated workflows. By integrating FME with Machine Learning techniques, it is possible to transform raw data into valuable insights faster and more accurately, enabling intelligent analysis and data-driven decision making.
More Related Content
More from Mehdi Poustchi Amin (19)
Honeypots in Cyberwar
Honeypots in CyberwarMehdi Poustchi Amin Honeypots and honeynets are used to study cyber attacks. A honeypot is a computer system set up to attract cyber attacks so threats can be observed and analyzed. A honeynet contains multiple honeypots and allows attacks on an entire network to be monitored. Deploying honeypots provides benefits like risk mitigation, intrusion detection, and research opportunities to study attacker techniques. However, honeypots also have downsides like limited visibility and potential additional security risks if compromised.
How to use OpenPGP for Email Encryption & Signing
How to use OpenPGP for Email Encryption & SigningMehdi Poustchi Amin OpenPGP is a standard for encrypting and digitally signing emails. It allows users to encrypt emails to ensure only the intended recipient can read the message. Digital signatures authenticate who sent the email and confirm the message contents were not altered. OpenPGP provides security and privacy for email communication.
How to create Self-Sign Certificate by using OpenSSL
How to create Self-Sign Certificate by using OpenSSLMehdi Poustchi Amin This document provides instructions for creating a self-signed certificate using OpenSSL. It outlines downloading and installing OpenSSL and Visual C++ 2008, changing environment variables, downloading an OpenSSL configuration file, making directories, creating required files, entering a password and information, generating a server certificate, and copying and installing the certificate.
Virtualization
VirtualizationMehdi Poustchi Amin VMware provides server virtualization software that allows multiple virtual machines to run on the same physical server. This increases hardware utilization and consolidation ratios. Key benefits include reduced costs from lower hardware, power, cooling, and real estate needs as well as faster provisioning times. VMware's product line includes ESX Server, VirtualCenter, VMotion, DRS, HA, and other tools for managing and optimizing virtualized environments. Customers report benefits like supporting more workloads without increasing staff and reducing provisioning time from weeks to hours.
All about Honeypots & Honeynets
All about Honeypots & HoneynetsMehdi Poustchi Amin The document discusses honeypots and honeynets. It defines a honeypot as a decoy system intended to be attacked to gather threat intelligence. Honeynets contain multiple honeypots within a controlled network for monitoring. The document outlines the benefits of deploying honeypots, such as risk mitigation and research. It also discusses techniques for installing and detecting honeypots, and the future of honeypot technologies.
Configuring RAID 1 on CentOs
Configuring RAID 1 on CentOsMehdi Poustchi Amin This document provides biographical information about Mehdi Poustchi Amin and Hedieh Amirjahanshahi, including their certifications and place of study from 2007 to 2008 at Symbiosis Institute of Computer Studies & Research.
Installing Parsix 1
Installing Parsix 1Mehdi Poustchi Amin This document provides biographical information about two IT professionals - Mehdi Poustchi Amin who holds MCSA/MCSE certifications, and Hedieh Amirjahanshahi who holds an MCP certification. Both studied at Symbiosis Institute of Computer Studies & Research from 2007 to 2008. The document also includes a link to Mehdi Poustchi Amin's blog.
Installing Debian 4
Installing Debian 4Mehdi Poustchi Amin This document provides biographical information about two IT professionals, Mehdi Poustchi Amin who holds MCSA/MCSE certifications, and Hedieh Amirjahanshahi who holds an MCP certification. It also mentions they attended Symbiosis Institute of Computer Studies & Research from 2008 to 2009. A link to Mehdi Poustchi Amin's blog is provided at the bottom.
Installing Mandriva 2008
Installing Mandriva 2008Mehdi Poustchi Amin SICSR is an institute that provides computer studies and research. It has provided education and research in these areas since 2008. The document likely contains details about the programs, faculty, or achievements of SICSR during the 2008-2009 period.
Installing Fedora 8
Installing Fedora 8Mehdi Poustchi Amin This document provides biographical information about two IT professionals, Mehdi Poustchi Amin who holds MCSA/MCSE certifications and Hedieh Amirjahanshahi who holds an MCP certification. It also lists their affiliation with the Symbiosis Institute of Computer Studies & Research from 2007 to 2008. It includes a link to Mehdi Poustchi Amin's blogspot page.
Installing Windows2008 Server
Installing Windows2008 ServerMehdi Poustchi Amin This document provides biographical information about Mehdi Poustchi, including his affiliation with Symbiosis Institute of Computer Studies & Research from 2008 to 2009. It also includes a link to his blogspot page at http://poustchi.blogspot.com which likely provides additional biographical details.
Proxy Servers & Firewalls
Proxy Servers & FirewallsMehdi Poustchi Amin Proxy servers and firewalls both act as gateways between internal networks and external networks like the internet. Proxy servers improve performance by caching frequently requested content, control bandwidth usage, and filter requests. Firewalls protect internal networks from external threats by packet filtering, analyzing packets, providing proxy services, and logging and alerting administrators of potential threats. Popular proxy software includes Squid, ISA Server, and WinRoute, while popular firewall software includes ISA Server, Cisco PIX, Norton Internet Security, and ZoneAlarm.
Installing Linux CentOs 5.0 Step-by-Step
Installing Linux CentOs 5.0 Step-by-StepMehdi Poustchi Amin This document provides biographical information about Mehdi Poustchi, including that he attended Symbiosis Institute of Computer Studies & Research from 2007 to 2008. It also includes a link to his blogspot blog.
Installing RHEL 5 Linux RedHat Enterprise Edition step-by-step
Installing RHEL 5 Linux RedHat Enterprise Edition step-by-stepMehdi Poustchi Amin This document provides information about an individual named Mehdi Poustchi Amin Hedieh Amirjahanshahi and their association with Symbiosis Institute of Computer Studies & Research (SICSR) from 2007 to 2008.
Installing Linux RedHat Enterprise Edition
Installing Linux RedHat Enterprise EditionMehdi Poustchi Amin Installing Linux RedHat Enterprise Edition Step bye Step
Installing Ubuntu7.04 Linux
Installing Ubuntu7.04 LinuxMehdi Poustchi Amin The document is a research paper written by Hedieh AmirJahanshahi, Mehdi Poustchi Amin, and others from the Symbiosis Institute of Computers Studies & Research in July 2007. It likely discusses topics related to computers and research, though no specific details about the content are provided in this brief metadata.
Installing Mandriva Linux
Installing Mandriva LinuxMehdi Poustchi Amin The document is a research paper written by Hedieh AmirJahanshahi, Mehdi Poustchi Amin, and others from Symbiosis Institute of Computers Studies & Research in June 2007. It likely discusses topics related to computers and research, though no specific details about the content are provided in this brief metadata.
Installing Windows2000 Server
Installing Windows2000 ServerMehdi Poustchi Amin This document provides step-by-step instructions for installing Windows 2000 Server. It describes downloading and running the installation files, selecting installation options such as computer name and time zone, and completing the basic configuration of a new Windows 2000 Server installation named MYSERVER in Tehran, Iran.
Installing Debian Linux
Installing Debian LinuxMehdi Poustchi Amin Installing Debian Linux is a step-by-step guide written by Mehdi Poustchi, Amin Hedieh, and AmirJahanshahi from the Symbiosis Institute of Computers Studies & Research in June 2007. The document provides instructions for installing the Debian Linux operating system.
Recently uploaded (20)
cnc-processing-centers-centateq-p-110-en.pdf
cnc-processing-centers-centateq-p-110-en.pdfAmirStern2 מרכז עיבודים תעשייתי בעל 3/4/5 צירים, עד 22 החלפות כלים עם כל אפשרויות העיבוד הדרושות. בעל שטח עבודה גדול ומחשב נוח וקל להפעלה בשפה העברית/רוסית/אנגלית/ספרדית/ערבית ועוד..
מסוגל לבצע פעולות עיבוד שונות המתאימות לענפים שונים: קידוח אנכי, אופקי, ניסור, וכרסום אנכי.
Connecting Data and Intelligence: The Role of FME in Machine Learning
Connecting Data and Intelligence: The Role of FME in Machine LearningSafe Software In this presentation, we want to explore powerful data integration and preparation for Machine Learning. FME is known for its ability to manipulate and transform geospatial data, connecting diverse data sources into efficient and automated workflows. By integrating FME with Machine Learning techniques, it is possible to transform raw data into valuable insights faster and more accurately, enabling intelligent analysis and data-driven decision making.
WebdriverIO & JavaScript: The Perfect Duo for Web Automation
WebdriverIO & JavaScript: The Perfect Duo for Web Automationdigitaljignect In today’s dynamic digital landscape, ensuring the quality and dependability of web applications is essential. While Selenium has been a longstanding solution for automating browser tasks, the integration of WebdriverIO (WDIO) with Selenium and JavaScript marks a significant advancement in automation testing. WDIO enhances the testing process by offering a robust interface that improves test creation, execution, and management. This amalgamation capitalizes on the strengths of both tools, leveraging Selenium’s broad browser support and WDIO’s modern, efficient approach to test automation. As automation testing becomes increasingly vital for faster development cycles and superior software releases, WDIO emerges as a versatile framework, particularly potent when paired with JavaScript, making it a preferred choice for contemporary testing teams.
Oh, the Possibilities - Balancing Innovation and Risk with Generative AI.pdf
Oh, the Possibilities - Balancing Innovation and Risk with Generative AI.pdfPriyanka Aash Oh, the Possibilities - Balancing Innovation and Risk with Generative AI
Curietech AI in action - Accelerate MuleSoft development
Curietech AI in action - Accelerate MuleSoft developmentshyamraj55 CurieTech AI in Action – Accelerate MuleSoft Development
Overview:
This presentation demonstrates how CurieTech AI’s purpose-built agents empower MuleSoft developers to create integration workflows faster, more accurately, and with less manual effort
linkedin.com
+12
curietech.ai
+12
meetups.mulesoft.com
+12
.
Key Highlights:
Dedicated AI agents for every stage: Coding, Testing (MUnit), Documentation, Code Review, and Migration
curietech.ai
+7
curietech.ai
+7
medium.com
+7
DataWeave automation: Generate mappings from tables or samples—95%+ complete within minutes
linkedin.com
+7
curietech.ai
+7
medium.com
+7
Integration flow generation: Auto-create Mule flows based on specifications—speeds up boilerplate development
curietech.ai
+1
medium.com
+1
Efficient code reviews: Gain intelligent feedback on flows, patterns, and error handling
youtube.com
+8
curietech.ai
+8
curietech.ai
+8
Test & documentation automation: Auto-generate MUnit test cases, sample data, and detailed docs from code
curietech.ai
+5
curietech.ai
+5
medium.com
+5
Why Now?
Achieve 10× productivity gains, slashing development time from hours to minutes
curietech.ai
+3
curietech.ai
+3
medium.com
+3
Maintain high accuracy with code quality matching or exceeding manual efforts
curietech.ai
+2
curietech.ai
+2
curietech.ai
+2
Ideal for developers, architects, and teams wanting to scale MuleSoft projects with AI efficiency
Conclusion:
CurieTech AI transforms MuleSoft development into an AI-accelerated workflow—letting you focus on innovation, not repetition.
AI VIDEO MAGAZINE - June 2025 - r/aivideo
AI VIDEO MAGAZINE - June 2025 - r/aivideo1pcity Studios, Inc AI VIDEO MAGAZINE - r/aivideo community newsletter – Exclusive Tutorials: How to make an AI VIDEO from scratch, PLUS: How to make AI MUSIC, Hottest ai videos of 2025, Exclusive Interviews, New Tools, Previews, and MORE - JUNE 2025 ISSUE -
Using the SQLExecutor for Data Quality Management: aka One man's love for the...
Using the SQLExecutor for Data Quality Management: aka One man's love for the...Safe Software The SQLExecutor is one of FME’s most powerful and flexible transformers. Pivvot maintains a robust internal metadata hierarchy used to support ingestion and curation of thousands of external data sources that must be managed for quality before entering our platform. By using the SQLExecutor, Pivvot can efficiently detect problems and perform analysis before data is extracted from our staging environment, removing the need for rollbacks or cycles waisted on a failed job. This presentation will walk through three distinct examples of how Pivvot uses the SQLExecutor to engage its metadata hierarchy and integrate with its Data Quality Management workflows efficiently and within the source postgres database. Spatial Validation –Validating spatial prerequisites before entering a production environment. Reference Data Validation - Dynamically validate domain-ed columns across any table and multiple columns per table. Practical De-duplication - Removing identical or near-identical well point locations from two distinct source datasets in the same table.
Cracking the Code - Unveiling Synergies Between Open Source Security and AI.pdf
Cracking the Code - Unveiling Synergies Between Open Source Security and AI.pdfPriyanka Aash Cracking the Code - Unveiling Synergies Between Open Source Security and AI
Quantum AI: Where Impossible Becomes Probable
Quantum AI: Where Impossible Becomes ProbableSaikat Basu Imagine combining the "brains" of Artificial Intelligence (AI) with the "super muscles" of Quantum Computing. That's Quantum AI!
It's a new field that uses the mind-bending rules of quantum physics to make AI even more powerful.
You are not excused! How to avoid security blind spots on the way to production
You are not excused! How to avoid security blind spots on the way to productionMichele Leroux Bustamante We live in an ever evolving landscape for cyber threats creating security risk for your production systems. Mitigating these risks requires participation throughout all stages from development through production delivery - and by every role including architects, developers QA and DevOps engineers, product owners and leadership. No one is excused! This session will cover examples of common mistakes or missed opportunities that can lead to vulnerabilities in production - and ways to do better throughout the development lifecycle.
"Scaling in space and time with Temporal", Andriy Lupa.pdf
"Scaling in space and time with Temporal", Andriy Lupa.pdfFwdays Design patterns like Event Sourcing and Event Streaming have long become standards for building real-time analytics systems. However, when the system load becomes nonlinear with fast and often unpredictable spikes, it's crucial to respond quickly in order not to lose real-time operating itself.
In this talk, I’ll share my experience implementing and using a tool like Temporal.io. We'll explore the evolution of our system for maintaining real-time report generation and discuss how we use Temporal both for short-lived pipelines and long-running background tasks.
The Future of Product Management in AI ERA.pdf
The Future of Product Management in AI ERA.pdfAlyona Owens Hi, I’m Aly Owens, I have a special pleasure to stand here as over a decade ago I graduated from CityU as an international student with an MBA program. I enjoyed the diversity of the school, ability to work and study, the network that came with being here, and of course the price tag for students here has always been more affordable than most around.
Since then I have worked for major corporations like T-Mobile and Microsoft and many more, and I have founded a startup. I've also been teaching product management to ensure my students save time and money to get to the same level as me faster avoiding popular mistakes. Today as I’ve transitioned to teaching and focusing on the startup, I hear everybody being concerned about Ai stealing their jobs… We’ll talk about it shortly.
But before that, I want to take you back to 1997. One of my favorite movies is “Fifth Element”. It wowed me with futuristic predictions when I was a kid and I’m impressed by the number of these predictions that have already come true. Self-driving cars, video calls and smart TV, personalized ads and identity scanning. Sci-fi movies and books gave us many ideas and some are being implemented as we speak. But we often get ahead of ourselves:
Flying cars,Colonized planets, Human-like AI: not yet, Time travel, Mind-machine neural interfaces for everyone: Only in experimental stages (e.g. Neuralink).
Cyberpunk dystopias: Some vibes (neon signs + inequality + surveillance), but not total dystopia (thankfully).
On the bright side, we predict that the working hours should drop as Ai becomes our helper and there shouldn’t be a need to work 8 hours/day. Nobody knows for sure but we can require that from legislation. Instead of waiting to see what the government and billionaires come up with, I say we should design our own future.
So, we as humans, when we don’t know something - fear takes over. The same thing happened during the industrial revolution. In the Industrial Era, machines didn’t steal jobs—they transformed them but people were scared about their jobs. The AI era is making similar changes except it feels like robots will take the center stage instead of a human. First off, even when it comes to the hottest space in the military - drones, Ai does a fraction of work. AI algorithms enable real-time decision-making, obstacle avoidance, and mission optimization making drones far more autonomous and capable than traditional remote-controlled aircraft. Key technologies include computer vision for object detection, GPS-enhanced navigation, and neural networks for learning and adaptation. But guess what? There are only 2 companies right now that utilize Ai in drones to make autonomous decisions - Skydio and DJI.
Coordinated Disclosure for ML - What's Different and What's the Same.pdf
Coordinated Disclosure for ML - What's Different and What's the Same.pdfPriyanka Aash Coordinated Disclosure for ML - What's Different and What's the Same
2025_06_18 - OpenMetadata Community Meeting.pdf
2025_06_18 - OpenMetadata Community Meeting.pdfOpenMetadata The community meetup was held Wednesday June 18, 2025 @ 9:00 AM PST.
Catch the next OpenMetadata Community Meetup @ https://www.meetup.com/openmetadata-meetup-group/
In this month's OpenMetadata Community Meetup, "Enforcing Quality & SLAs with OpenMetadata Data Contracts," we covered data contracts, why they matter, and how to implement them in OpenMetadata to increase the quality of your data assets!
Agenda Highlights:
👋 Introducing Data Contracts: An agreement between data producers and consumers
📝 Data Contracts key components: Understanding a contract and its purpose
🧑🎨 Writing your first contract: How to create your own contracts in OpenMetadata
🦾 An OpenMetadata MCP Server update!
➕ And More!
Securing Account Lifecycles in the Age of Deepfakes.pptx
Securing Account Lifecycles in the Age of Deepfakes.pptxFIDO Alliance Securing Account Lifecycles in the Age of Deepfakes
Enhance GitHub Copilot using MCP - Enterprise version.pdf
Enhance GitHub Copilot using MCP - Enterprise version.pdfNilesh Gule Slide deck related to the GitHub Copilot Bootcamp in Melbourne on 17 June 2025
"Database isolation: how we deal with hundreds of direct connections to the d...
"Database isolation: how we deal with hundreds of direct connections to the d...Fwdays What can go wrong if you allow each service to access the database directly? In a startup, this seems like a quick and easy solution, but as the system scales, problems appear that no one could have guessed.
In my talk, I'll share Solidgate's experience in transforming its architecture: from the chaos of direct connections to a service-based data access model. I will talk about the transition stages, bottlenecks, and how isolation affected infrastructure support. I will honestly show what worked and what didn't. In short, we will analyze the controversy of this talk.
CapCut Pro Crack For PC Latest Version {Fully Unlocked} 2025
CapCut Pro Crack For PC Latest Version {Fully Unlocked} 2025pcprocore 👉𝗡𝗼𝘁𝗲:𝗖𝗼𝗽𝘆 𝗹𝗶𝗻𝗸 & 𝗽𝗮𝘀𝘁𝗲 𝗶𝗻𝘁𝗼 𝗚𝗼𝗼𝗴𝗹𝗲 𝗻𝗲𝘄 𝘁𝗮𝗯> https://pcprocore.com/ 👈◀
CapCut Pro Crack is a powerful tool that has taken the digital world by storm, offering users a fully unlocked experience that unleashes their creativity. With its user-friendly interface and advanced features, it’s no wonder why aspiring videographers are turning to this software for their projects.
You are not excused! How to avoid security blind spots on the way to production
You are not excused! How to avoid security blind spots on the way to productionMichele Leroux Bustamante
Ad
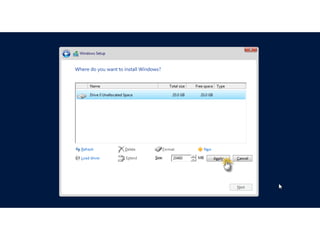
Install Windows Server 2012 Step-by-Step
- 1. Installing Windows Server 2012 step by step Sayyed Mehdi Poustchi Amin India – Oct 2013
- 2. Speaker Mehdi Poustchi Amin [email protected] CCNA,MCTS,MCITP,MCSE, MCSA,MCP Network Administrator Founder of Iran’s honeynet project www.Honeynet.ir Research Assistant
