Internet technology unit 5
- 1. COURCES WE OFFER: BSC(IT) FY,SY,TY BSC(CS) FY,SY,TY BSC(IT/CS) PROJECTS MCA (ENTRANCE) ENGG(IT/ELECTRONICS/EXTC) ADDRESS: 302 PARANJPE UDYOG BHAVAN, NEAR KHANDELWAL SWEETS, THANE STATION, THANE WEST. TEL: 8097071144/55 STAY CONNECTED FOR MORE UPDATES AND STUDY NOTES FACEBOOK : https://www.facebook.com/weittutorial EMAIL: [email protected] 1TEL:8097071144/55
- 2. Unit 5 1.Remote Login: TELNET and SSH 2.File Transfer: FTP and TFTP 3.World Wide Web and HTTP 2TEL:8097071144/55
- 4. TELNET TELNET is an abbreviation for TErminaL NETwork. It is the standard TCP/IP protocol for virtual terminal service as proposed by ISO. TELNET enables the establishment of a connection to a remote system in such a way that the local terminal appears to be a terminal at the remote system. TELNET is a general-purpose client-server application program TEL:8097071144/55 4
- 5. Concepts Time-Sharing Environment TELNET was designed at a time when most operating systems, such as UNIX, were operating in a time-sharing environment. In such an environment, a large computer supports multiple users. In a time-sharing environment, all of the processing must be done by the central computer. When a user types a character on the keyboard, the character is usually sent to the computer and echoed to the monitor. Time-sharing creates an environment in which each user has the illusion of a dedicated computer. TEL:8097071144/55 5
- 6. Login In a time-sharing environment, users are part of the system with some right to access resources. Each authorized user has an identification and probably a password. To access the system, the user logs into the system with a user id or login name. TEL:8097071144/55 6
- 7. Local Login When a user logs into a local time-sharing system, it is called local login. TEL:8097071144/55 7
- 8. Remote Login When a user wants to access an application program or utility located on a remote machine, he or she performs remote login. Here the TELNET client and server programs come into use. The user sends the keystrokes to the terminal driver where the local operating system accepts the characters but does not interpret them. The characters are sent to the TELNET client, which transforms the characters to a universal character set called Network Virtual Terminal (NVT) characters and delivers them to the local TCP/IP stack TEL:8097071144/55 8
- 10. Network Virtual Terminal (NVT) The mechanism to access a remote computer is complex. This is because every computer and its operating system accepts a special combination of characters as tokens. dealing with heterogeneous systems is a problem TELNET solves this problem by defining a universal interface called the Network Virtual Terminal (NVT) character set. Via this interface, the client TELNET translates characters (data or commands) that come from the local terminal into NVT form and delivers them to the network. The server TELNET, on the other hand, translates data and commands from NVT form into the form acceptable by the remote computer. TEL:8097071144/55 10
- 12. NVT Character Set NVT uses two sets of characters, one for data and one for control. Both are 8-bit bytes Data Characters For data, NVT normally uses what is called NVT ASCII. This is an 8-bit character set in which the seven lowest order bits are the same as US ASCII TEL:8097071144/55 12
- 14. Embedding TELNET uses only one TCP connection. The same connection is used for sending both data and control characters. TELNET accomplishes this by embedding the control characters in the data stream. to distinguish data from control characters, each sequence of control characters is preceded by a special control character called interpret as control (IAC). imagine a user wants a server to display a file (file1) on a remote server.(cat file1) and the name of the file has been mistyped (filea instead of file1). The user uses the backspace key to correct this situation.(cat filea<backspace>1) default implementation of TELNET, the user cannot edit locally; the editing is done at the remote server. The backspace character is translated into two remote characters (IAC EC), which is embedded in the data and sent to the remote server TEL:8097071144/55 14
- 15. An example of embedding TEL:8097071144/55 15
- 16. Options TELNET lets the client and server negotiate options before or during the use of the service. Options are extra features available to a user with a more sophisticated terminal. TEL:8097071144/55 16
- 17. Option Negotiation To use any of the options mentioned in the previous section first requires option negotiation between the client and the server. Four control characters are used for this purpose NVT character set for option negotiation TEL:8097071144/55 17
- 18. Enabling an Option Offer to Enable Request to Enable TEL:8097071144/55 18
- 19. Disabling an Option Offer to Disable Request to Disable TEL:8097071144/55 19
- 20. option negotiation The request consists of three characters: IAC, DO, and ECHO. The server accepts the request and enables the option. It informs the client by sending the three character approval: IAC, WILL, and ECHO. Echo option TEL:8097071144/55 20
- 21. Symmetry One interesting feature of TELNET is its symmetric option negotiation in which the client and server are given equal opportunity. A client or server can install a more sophisticated version of TELNET with more options. When it is connected to a party, it can offer or request these new options. TEL:8097071144/55 21
- 22. Suboption Negotiation Some options require additional information. For example, to define the type or speed of a terminal, the negotiation includes a string or a number to define the type or speed. NVT character set for suboption negotiation TEL:8097071144/55 22
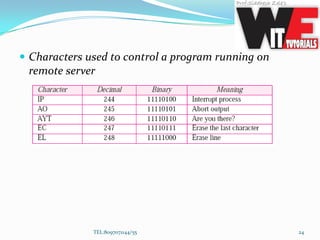
- 23. Controlling the Server When an application program is running on the local computer, special characters are used to interrupt (abort) the program (for example, Ctrl+c), or erase the last character typed (for example, delete key or backspace key), and so on. However, when a program is running on a remote computer, these control characters are sent to the remote machine. TEL:8097071144/55 23
- 24. Characters used to control a program running on remote server TEL:8097071144/55 24
- 25. Example of interrupting an application program TEL:8097071144/55 25
- 26. Out-of-Band Signaling The user wants to interrupt the application program, but the program does not read data from the buffer. The TCP at the server site has found that the buffer is full and has sent a segment specifying that the client window size should be zero. In other words, the TCP at the server site is announcing that no more regular traffic is accepted. To remedy such a situation, an urgent TCP segment should be sent from the client to the server. The urgent segment overrides the regular flow-control mechanism. Although TCP is not accepting normal segments, it must accept an urgent segment. TEL:8097071144/55 26
- 27. Escape Character user wants characters interpreted by the client instead of the server. In this case, the user can use an escape character, normally Ctrl+] (shown as ^]). TEL:8097071144/55 27
- 28. Modes of Operation TELNET implementations operate in one of three modes: 1. default mode, 2. Character mode, or 3. line mode. TEL:8097071144/55 28
- 29. default mode The default mode is used if no other modes are invoked through option negotiation. In this mode, the echoing is done by the client. The user types a character and the client echoes the character on the screen (or printer) but does not send it until a whole line is completed. After sending the whole line to the server, the client waits for the GA (go ahead) command from the server before accepting a new line from the user. The operation is half-duplex. Half-duplex operation is not efficient when the TCP connection itself is full-duplex TEL:8097071144/55 29
- 30. Character Mode In the character mode, each character typed is sent by the client to the server. The server normally echoes the character back to be displayed on the client screen. The client and the server negotiate the terminal type and terminal speed and then the server checks the login and password of the user Slow due to each character acknowledgement TEL:8097071144/55 30
- 32. Line Mode A new mode has been proposed to compensate for the deficiencies of the default mode and the character mode. In this mode, called the line mode, line editing (echoing, character erasing, line erasing, and so on) is done by the client. The client then sends line mode is full-duplex with the client sending one line after another, without the need for an intervening GA (go ahead) character from the server. TEL:8097071144/55 32
- 33. User Interface The normal user does not use TELNET commands as defined above. Usually, the operating system (UNIX, for example) defines an interface with user-friendly commands. Interface is responsible for translating the user-friendly commands to the previously defined commands in the protocol. TEL:8097071144/55 33
- 34. Security Issue TELNET suffers from security problems. Although TELNET requires a login name and password (when exchanging text), often this is not enough. A microcomputer connected to a broadcast LAN can easily eavesdrop using snooper software and capture a login name and the corresponding password (even if it is encrypted). TEL:8097071144/55 34
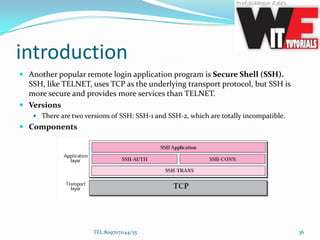
- 36. introduction Another popular remote login application program is Secure Shell (SSH). SSH, like TELNET, uses TCP as the underlying transport protocol, but SSH is more secure and provides more services than TELNET. Versions There are two versions of SSH: SSH-1 and SSH-2, which are totally incompatible. Components TEL:8097071144/55 36
- 37. SSH Transport-Layer Protocol (SSH-TRANS) Since TCP is not a secured transport layer protocol, SSH first uses a protocol that creates a secured channel on the top of TCP. This new layer is an independent protocol referred to as SSH-TRANS. Client server exchange several security parameters to establish a secure channel on the top of the TCP SSH Authentication Protocol (SSH-AUTH) After a secure channel is established between the client and the server and the server is authenticated for the client, SSH can call another software that can authenticate the client for the server. SSH Connection Protocol (SSH-CONN) One of the services provided by the SSH-CONN protocol is to do multiplexing. SSH-CONN takes the secure channel established by the two previous protocols and lets the client create multiple logical channels over it. SSH Applications SSH allows several application programs to use the connection. Each application can create a logical channel TEL:8097071144/55 37
- 38. Port Forwarding One of the interesting services provided by the SSH protocol is to provide port forwarding. We can use the secured channels available in SSH to access an application program that does not provide security services. TEL:8097071144/55 38
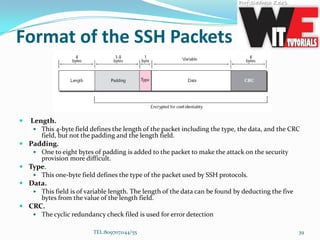
- 39. Format of the SSH Packets Length. This 4-byte field defines the length of the packet including the type, the data, and the CRC field, but not the padding and the length field. Padding. One to eight bytes of padding is added to the packet to make the attack on the security provision more difficult. Type. This one-byte field defines the type of the packet used by SSH protocols. Data. This field is of variable length. The length of the data can be found by deducting the five bytes from the value of the length field. CRC. The cyclic redundancy check filed is used for error detection TEL:8097071144/55 39
- 41. FTP File Transfer Protocol (FTP) is the standard mechanism provided by TCP/IP for copying a file from one host to another. FTP differs from other client-server applications in that it establishes two connections between the hosts. One connection is used for data transfer, the other for control information (commands and responses). Separation of commands and data transfer makes FTP more efficient. FTP uses two well-known TCP ports: Port 21 is used for the control connection, and port 20 is used for the data connection. TEL:8097071144/55 41
- 43. Control Connection 1. The server issues a passive open on the well-known port 21 and waits for a client. 2. The client uses an ephemeral port and issues an active open. TEL:8097071144/55 43
- 45. Communication The FTP client and server, which run on different computers, must communicate with each other. These two computers may use different operating systems, different character sets, different file structures, and different file formats. FTP must make this heterogeneity compatible. TEL:8097071144/55 45
- 46. Communication over Control Connection It uses the NVT ASCII character set Communication over Data Connection. We want to transfer files through the data connection. The heterogeneity problem is resolved by defining three attributes of communication: file type, data structure, and transmission mode TEL:8097071144/55 46
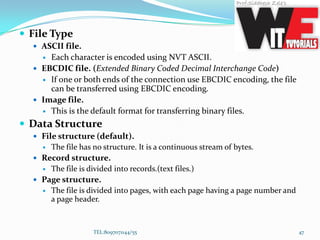
- 47. File Type ASCII file. Each character is encoded using NVT ASCII. EBCDIC file. (Extended Binary Coded Decimal Interchange Code) If one or both ends of the connection use EBCDIC encoding, the file can be transferred using EBCDIC encoding. Image file. This is the default format for transferring binary files. Data Structure File structure (default). The file has no structure. It is a continuous stream of bytes. Record structure. The file is divided into records.(text files.) Page structure. The file is divided into pages, with each page having a page number and a page header. TEL:8097071144/55 47
- 48. Transmission Mode Stream mode. This is the default mode. Data are delivered from FTP to TCP as a continuous stream of bytes. Block mode. Data can be delivered from FTP to TCP in blocks. Compressed mode. If the file is big, the data can be compressed. TEL:8097071144/55 48
- 49. Command Processing FTP uses the control connection to establish a communication between the client control process and the server control process. During this communication, the commands are sent from the client to the server and the responses are sent from the server to the client TEL:8097071144/55 49
- 50. commands Commands, which are sent from the FTP client control process, are in the form of ASCII uppercase, which may or may not be followed by an argument. We can roughly divide the commands into six groups: 1. access commands, 2. file management commands, 3. data formatting commands, 4. port defining commands, 5. file transferring commands, and 6. miscellaneous commands TEL:8097071144/55 50
- 53. Data formatting commands These commands let the user define the data structure, file type, and transmission mode. TEL:8097071144/55 53
- 54. Port defining commands These commands define the port number for the data connection on the client site. TEL:8097071144/55 54
- 56. Miscellaneous commands These commands deliver information to the FTP user at the client site. TEL:8097071144/55 56
- 57. Responses Every FTP command generates at least one response. A response has two parts: a three digit number followed by text. We represent the three digits as xyz TEL:8097071144/55 57
- 58. First Digit The first digit defines the status of the command. 1yz (positive preliminary reply). The action has started. The server will send another reply before accepting another command. 2yz (positive completion reply). The action has been completed. The server will accept another command. 3yz (positive intermediate reply). The command has been accepted, but further information is needed. 4yz (transient negative completion reply). The action did not take place, but the error is temporary. The same command can be sent later. 5yz (permanent negative completion reply). The command was not accepted and should not be retried again. TEL:8097071144/55 58
- 59. Second Digit The second digit also defines the status of the command. x0z (syntax). x1z (information). x2z (connections). x3z (authentication and accounting). x4z (unspecified). x5z (file system). TEL:8097071144/55 59
- 60. Third Digit The third digit provides additional information. TEL:8097071144/55 60
- 66. Anonymous FTP To use FTP, a user needs an account (user name) and a password on the remote server. Some sites have a set of files available for public access. To access these files, a user does not need to have an account or password. Instead, the user can use anonymous as the user name and guest as the password. TEL:8097071144/55 66
- 67. Security for FTP To be secure, one can add a Secure Socket Layer between the FTP application layer and the TCP layer. In this case FTP is called SSL-FTP Another way to transfer files using a secure channel is to use another independent protocol called sftp (secure file transfer protocol). TEL:8097071144/55 67
- 68. TFTP There are occasions when we need to simply copy a file without the need for all of the features of the FTP protocol. For example, when a diskless workstation or a router is booted, we need to download the bootstrap and configuration files. Here we do not need all of the sophistication provided in FTP. We just need a protocol that quickly copies the files. Trivial File Transfer Protocol (TFTP) is designed for these types of file transfer. It is so simple that the software package can fit into the read-only memory of a diskless workstation TFTP uses the services of UDP on the well-known port 69. TEL:8097071144/55 68
- 70. RRQ The read request (RRQ) message is used by the client to establish a connection for reading data from the server OpCode. The first field is a 2-byte operation code. The value is 1 for the RRQ message. File name. The next field is a variable-size string (encoded in ASCII) that defines the name of the file. Mode. The next field is another variable-size string defining the transfer mode. WRQ The write request (WRQ) message is used by the client to establish a connection for writing data to the server. The format is the same as RRQ except that the OpCode is 2 TEL:8097071144/55 70
- 71. DATA The data (DATA) message is used by the client or the server to send blocks of data. OpCode. The first field is a 2-byte operation code. The value is 3 for the DATA message. Block number. This is a 2-byte field containing the block number. The sender of the data (client or server) uses this field for sequencing. Data. This block must be exactly 512 bytes in all DATA messages except the last block, which must be between 0 and 511 bytes. TEL:8097071144/55 71
- 72. ACK The acknowledge (ACK) message is used by the client or server to acknowledge the receipt of a data block. ERROR The ERROR message is used by the client or the server when a connection cannot be established or when there is a problem during data transmission. TEL:8097071144/55 72
- 73. Connection Connection Establishment TFTP uses RRQ, WRQ, ACK, and ERROR messages to establish connection. There is no provision for connection establishment and termination in UDP, UDP transfers each block of data encapsulated in an independent user datagram. TEL:8097071144/55 73
- 74. Connection Termination TFTP does not have a special message for termination. Termination is accomplished by sending the last block of data, which is less than 512 bytes. TEL:8097071144/55 74
- 75. Data Transfer The data transfer phase occurs between connection establishment and termination. TFTP uses the services of UDP, which is unreliable. Flow Control flow control is achieved by numbering the data blocks and waiting for an ACK before the next data block is sent. Error Control sender and the receiver both use time-outs. The sender uses a time-out for data messages; the receiver uses a time-out for acknowledgment TEL:8097071144/55 75
- 76. Sorcerer’s Apprentice Bug Although the flow- and error-control mechanism is symmetric in TFTP, it can lead to a problem known as the sorcerer’s apprentice bug, named for the cartoon character who inadvertently conjures up a mop that continuously replicates itself. This will happen if the ACK message for a packet is not lost but delayed. In this situation, every succeeding block is sent twice and every succeeding acknowledgment is received twice. TEL:8097071144/55 76
- 78. UDP port numbers used by TFTP TEL:8097071144/55 78
- 79. Security One important point about TFTP is that there is no provision for security Applications Use of TFTP with DHCP TEL:8097071144/55 79
- 81. ARCHITECTURE The WWW today is a distributed client-server service, in which a client using a browser can access a service using a server. service provided is distributed over many locations called sites. TEL:8097071144/55 81
- 83. Hypertext and Hypermedia Hypertext means creating documents that refer to other documents. When a hypertext is viewed with a browser, the link can be clicked to retrieve the other document. Hypermedia is a term applied to document that contains links to other textual document or documents containing graphics, video, or audio. TEL:8097071144/55 83
- 84. Web Client (Browser) A variety of vendors offer commercial browsers that interpret and display a Web document, and all of them use nearly the same architecture. Each browser usually consists of three parts: 1. a controller, 2. client protocol, and 3. interpreters. TEL:8097071144/55 84
- 85. Web Server The Web page is stored at the server. Each time a client request arrives, the corresponding document is sent to the client. TEL:8097071144/55 85
- 86. Uniform Resource Locator (URL) The uniform resource locator (URL) is a standard locator for specifying any kind of information on the Internet. TEL:8097071144/55 86
- 87. Web documents Static Documents Static documents are fixed-content documents that are created and stored in a server. Dynamic Documents When a request arrives, the Web server runs an application program or a script that creates the dynamic document. Common Gateway Interface (CGI) Scripting Technologies for Dynamic Documents Hypertext Preprocessor (PHP), Java Server Pages (JSP), Active Server Pages (ASP). TEL:8097071144/55 87
- 88. Active Documents we need a program or a script to be run at the client site. These are called active documents. Java Applets JavaScript TEL:8097071144/55 88
- 90. The Hypertext Transfer Protocol (HTTP) is a protocol used mainly to access data on the World Wide Web. TEL:8097071144/55 90
- 91. HTTP Transaction HTTP itself is a stateless protocol, which means that the server does not keep information about the client. The client initializes the transaction by sending a request. The server replies by sending a response. Request Message A request message consists of a request line, a header, and sometimes a body. Request Line The first line in a request message is called a request line. TEL:8097071144/55 91
- 93. Format of the request message TEL:8097071144/55 93
- 94. Request Line fields The First field, method defines the request type The second field, URL The third field, version, gives the version of the protocol TEL:8097071144/55 94
- 95. Header Lines In Request Message Each header line has a header name, a colon, a space, and a header value. Request Header Names TEL:8097071144/55 95
- 96. Body In Request Message The body can be present in a request message. Usually, it contains the comment to be sent. TEL:8097071144/55 96
- 97. Response Message A response message consists of a status line, header lines, a blank line and sometimes a body. TEL:8097071144/55 97
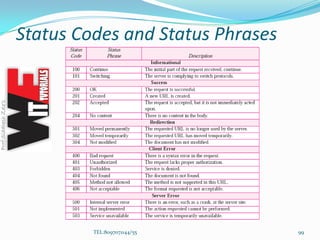
- 98. Status Line The first line in a response message is called the status line. There are three fields in this line separated by spaces and terminated by a carriage return and line feed. 1. The first field defines the version of HTTP protocol, currently 1.1. 2. The status code field defines the status of the request. It consists of three digits. Whereas the codes in the 100 range are only informational, the codes in the 200 range indicate a successful request. 3. The status phrase explains the status code in text form. The possible values for the status code and status phrase are shown in Table TEL:8097071144/55 98
- 99. Status Codes and Status Phrases TEL:8097071144/55 99
- 100. Header Lines In Response Message Each header line sends additional information from the server to the client. TEL:8097071144/55 100 Response Header Names
- 101. Body The body contains the document to be sent from the server to the client. The body is present unless the response is an error message. TEL:8097071144/55 101
- 102. The example retrieves a document Using get method for retrieving image TEL:8097071144/55 102
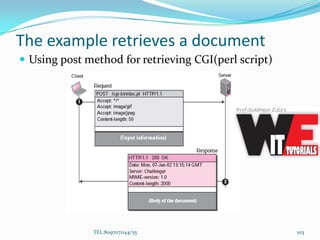
- 103. The example retrieves a document Using post method for retrieving CGI(perl script) TEL:8097071144/55 103
- 104. Persistence Nonpersistent Connection In a nonpersistent connection, one TCP connection is made for each request/response. Persistent Connection In a persistent connection, the server leaves the connection open for more requests after sending a response. TEL:8097071144/55 104
- 105. Cookies The World Wide Web was originally designed as a stateless entity. A client sends a request; a server responds. Their relationship is over. The original design of WWW, retrieving publicly available documents, exactly fits this purpose. To maintain state cookies are used. To register client to avoid renegotiation with server TEL:8097071144/55 105
- 107. Web Caching: Proxy Server HTTP supports proxy servers. A proxy server is a computer that keeps copies of responses to recent requests. The HTTP client sends a request to the proxy server. The proxy server checks its cache. If the response is not stored in the cache, the proxy server sends the request to the corresponding server. Incoming responses are sent to the proxy server and stored for future requests from other clients. TEL:8097071144/55 107
- 108. HTTP Security The HTTP per se does not provide security. HTTP can be run over the Secure Socket Layer (SSL). In this case, HTTP is referred to as HTTPS. TEL:8097071144/55 108
- 109. Refer printed notes for theory. 109TEL:8097071144/55


























![Escape Character
user wants characters interpreted by the client instead of
the server.
In this case, the user can use an escape character, normally
Ctrl+] (shown as ^]).
TEL:8097071144/55 27](https://image.slidesharecdn.com/internettechnologyunit5-180129190308/85/Internet-technology-unit-5-27-320.jpg)