Ad
Introduction to Linux OS (Part 2) - Tutorial
- 1. Introduction to Linux OS Dr. Mohamed Gamal
- 2. Information Technology Institute (ITI) Dr. Mohamed Gamal 2 Linux Users and Groups Linux/Unix operating systems have the ability to multitask in a manner similar to other operating systems. However, Linux’s major difference from other operating systems is its ability to have multiple users. Linux was designed to allow more than one user to have access to the system at the same time. In order for this multiuser design to work properly, there needs to be a method to protect users from each other. This is where permissions come into play. Linux Primary and Secondary Groups A primary group is the default group that a user account belongs to. Every user on Linux belongs to a primary group, usually stored in the `/etc/passwd` file. $ cat /etc/passwd or $ tail -n 1 /etc/passwd The /etc/passwd file in Linux and Unix-like systems stores basic information about each user or account. It is world-readable by default and can be viewed using tools like cat or a text editor. Each line in the file represents a user and contains seven fields separated by colons: » Name: The user's unique login name. » Password: Originally stored an encrypted password, now replaced by x (actual passwords are stored in /etc/shadow). » User ID (UID): A numeric identifier for the user; 0 is for root, and 100-999 are for regular users. » Group ID (GID): The user's primary group ID, usually matching the UID. » GECOS: General user information, like real name; often unused or empty. » Home Directory: The user's starting directory upon login. » Shell: The user's default shell (e.g., /bin/bash). Once a user has been created with their primary group, they can be added to other secondary groups with a maximum of 15 secondary groups, usually stored in the `/etc/group` file. $ cat /etc/group
- 3. Information Technology Institute (ITI) Dr. Mohamed Gamal 3 Add a new user Delete (or remove) a user $ sudo adduser <username> $ sudo userdel <username> $ sudo adduser Ahmed $ sudo userdel Ahmed Change a user’s password Change user details $ sudo passwd <username> $ sudo chfn <username> $ sudo chfn -f "" -o "" -p "" -h "" <username> $ sudo nano /etc/passwd $ sudo passwd Ahmed $ sudo chfn Ahmed $ sudo chfn -f "Ahmed" -o "" -p "" -h "" Ahmed Switch to another user (su: switch user) $ su <username> $ su Ahmed Create a new group Delete (or remove) a group $ sudo groupadd <group name> $ groupdel <group name> $ sudo groupadd Marketing $ groupdel Marketing Add a group to a user (a: append, G: group) Remove a user from a group $ usermod -a -G <group name> <username> $ gpasswd -d <username> <group name> $ usermod -a -G Marketing Ahmed $ gpasswd -d Ahmed Marketing View all groups a user in $ groups <username> $ groups Ahmed
- 4. Information Technology Institute (ITI) Dr. Mohamed Gamal 4 View all sudoers file and edit user permissions The sudoers file is a configuration file that defines which users or groups have permission to run commands with elevated privileges (i.e., using sudo), and under what conditions, usually located at /etc/sudoers. $ sudo visudo Ahmed All=(ALL) NOPASSWD: /usr/bin/top, /usr/bin/ls Now Ahmed is a sudoer! $ su Ahmed $ sudo ls Edit group permissions $ sudo visudo %Marketing ALL=NOPASSWD: /usr/bin/ls, /usr/bin/less, /usr/bin/apt
- 5. Information Technology Institute (ITI) Dr. Mohamed Gamal 5 Linux File Permissions A process is a task or a group of tasks running on your computer. It's different from a program or a command. One command can start multiple processes at once. Processes can work independently or be related, and a problem in one process might not always affect others. Processes use resources like memory, CPU time, and devices (like printers or hard drives). The operating system manages these resources to keep everything running smoothly. -/d rw-r--r-- 1 centos9 centos9 56 Aug 5 16:52 file.py ↓ ↓ ↓ ↓ ↓ ↓ ↓ ↓ ↓ Type (file/dir) User Group Other No. hard links Owner/User Group Size Date Time Name
- 6. Information Technology Institute (ITI) Dr. Mohamed Gamal 6 Manipulating Files Change mode of a file $ chmod [u/g/o/a] [+/-/=] [r/w/x] [filename/dirname] Type Explanation u user g group o other a all three Type Explanation + add permission - remove permission = set only this permission to u/g/i=o Use -R flag to apply the permission changes to all files and directories within a specific directory. Function Example Adding Permissions $ chmod a+w file.py $ chmod u+x file.py $ chmod -R a+w Games Removing Permissions $ chmod -R a-w Games $ chmod -R a=w Games $ chmod a=wr file.py Adding permissions to all (user, group, other users) $ chmod +x file.txt $ chmod g+w,o-rw,a+x file.txt » Use comma-separated permissions without spaces. Changing the owner of the file $ chown Options New_Owner:NEW_GROUP [filename/dirname] Examples $ chown Ahmed file.txt $ chown :developers file.txt $ chown Ahmed:developers file.txt $ chown -R Ahmed Games
- 7. Information Technology Institute (ITI) Dr. Mohamed Gamal 7 Text Editors (Nano, Vi/Vim) 1) Nano $ nano file.txt If the file exists, nano will open it, otherwise it will create a new file. Description Command Help CTRL + G Save As CTRL + O Cancel CTRL + C Exit/Close CTRL + X Highlight/Select CTRL + 6 Copy ALT + 6 Cut CTRL + K Paste CTRL + U
- 8. Information Technology Institute (ITI) Dr. Mohamed Gamal 8 2) Vi/Vim $ vi file.txt or $ vim file.txt Mode Key Description Command Mode ESC • The default mode when you start Vi/Vim. • You use this mode to execute commands for navigating, copying, deleting, and more. Insert Mode i • This is where you can type and edit text. • Press ESC to return to Command Mode. Visual Mode v • Used for highlighting/selecting text. • Press ESC to return to Command Mode.
- 9. Information Technology Institute (ITI) Dr. Mohamed Gamal 9 Function Key Mode Description Copy (Yank) y Visual/Command Copy the selected text or a specified range. Paste Text p Command Mode Paste the copied text after the cursor. Delete Text d Visual/Command Delete the selected text or a specified range. Delete Line dd or [num]dd Command Mode Delete the current line(s). Delete Word dw or d[num]w Command Mode Delete a word(s). Undo Change u Command Mode Undo the last change. Redo Change CTRL + r Command Mode Redo the change that was undone. Searching /<pattern> or ?<pattern> Command Mode Start a forward/reverse search for <pattern>. Move to Line Start 0 Command Mode Move the cursor to the beginning of the current line. Move to Line End CTRL + e Command Mode Move the cursor to the end of the current line. Save and Exit :wq or ZZ Command Mode Save changes and exit Vim. Exit Without Saving :q! Command Mode Exit Vim without saving changes. Split Window (Horizontal) :split <filename> Command Mode Open a file in a new horizontal split window. Split Window (Vertical) :vsplit <filename> Command Mode Open a file in a new vertical split window. Move Between Splits CTRL + w + arrow key or h, j, k, l Command Mode Move between split wind Graphical Editors So far we’ve learned about various command line editors. However, if you are running Linux as a desktop operating system you might be interesting in some graphical text editors and word processors. » emacs – Emacs has both graphical and command line modes. » gedit – The default text editor for the Gnome desktop environment. » gvim – The graphical version of vim. » kedit – The default text editor for the KDE (K Desktop Environment) desktop environment.
- 10. Information Technology Institute (ITI) Dr. Mohamed Gamal 10 Microsoft Word Replacement If you are looking for a Microsoft Word replacement, consider – AbiWord or – LibreOffice which is a complete office suite with a spreadsheet program, a database, and presentation software. Code/Text Editors for Linux – Visual Studio Code (VS Code) – Sublime Text – Gedit – GNOME's simple and lightweight text editor. – Kate – etc. Steps to Set Your Default Editor You can set $EDITOR in your personal initialization files to ensure your favorite editor is used, be it nano, emacs, vi, or something else. 1) Open your shell's configuration file (i.e., ~/.bashrc) $ nano ~/.bashrc 2) Set the $EDITOR variable $ export EDITOR='vim' 3) Apply the changes $ source ~/.bashrc Now, whenever you invoke a command that requires an editor (e.g., crontab -e, git commit, etc.), it will open in your preferred editor.
- 11. Information Technology Institute (ITI) Dr. Mohamed Gamal 11 Creating a Collection of Files If you want to bundle a group of files and/or directories together in an archive (not compressing), you can use the tar command which is one of the oldest and common methods for creating and working with compressed backup archives. – You may want to create a copy or backup of a group of files. – You may have several files you want to transfer at once or as a set. $ tar [-] c|x|t f <tarfile> <pattern> Note that you have the choice to precede the tar arguments with a hyphen ( - ) or omit it. For example, $ tar cf file.tar it is the same as $ tar -cf file.tar. tar option Description c Create a tar archive. x Extract files from the archive. t Display the table of contents (list). v Causes tar to be verbose. f <file> The tar archive file to perform operations against. $ cd /home/MG $ mkdir data $ touch data/file.txt data/report.doc $ tar cf archived.tar data/ $ tar tf archived.tar $ file archived.tar $ cd /tmp $ tar xf /home/MG/ archived.tar $ ls data/ $ touch secret secret.bak $ tar cvf misc.tar sec* data
- 12. Information Technology Institute (ITI) Dr. Mohamed Gamal 12 Compressing Files To Save Space Compressing files in Linux is a common way to save space on disk. Linux provides several tools and utilities to compress files and directories effectively. Command Description $ gzip <file> Compress file. The resulting compressed file is named file.gz. $ gunzip <file> Uncompress files. $ gzcat or zcat Concatenates and prints compressed files. Hint: You can use the command du to display how much space is used by the file. $ du -h archived.tar $ gzip archived.tar $ ls -lh $ du -h archived.tar.gz $ gunzip archived.tar.gz $ ls -lh Linux provides several other tools and utilities to compress files and directories effectively. Command Decompression $ bzip2 <file> $ bunzip2 $ zip <file> $ unzip $ xz <file> $ xz
- 13. Information Technology Institute (ITI) Dr. Mohamed Gamal 13 Compressing Archives using tar In modern versions of the tar command gzip , bzip2, and xz compressions are built-in. $ tar zcfv compressed_gzip.tar.gz data $ tar jcfv compressed_bzip2.tar.bz2 data $ tar Jcfv compressed_xz.tar.xz data
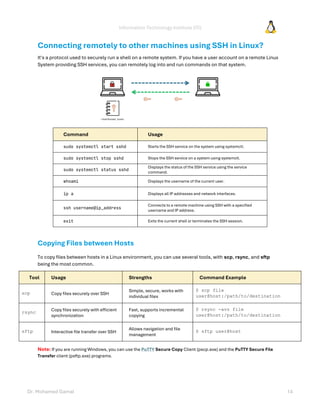
- 14. Information Technology Institute (ITI) Dr. Mohamed Gamal 14 Connecting remotely to other machines using SSH in Linux? It's a protocol used to securely run a shell on a remote system. If you have a user account on a remote Linux System providing SSH services, you can remotely log into and run commands on that system. Command Usage sudo systemctl start sshd Starts the SSH service on the system using systemctl. sudo systemctl stop sshd Stops the SSH service on a system using systemctl. sudo systemctl status sshd Displays the status of the SSH service using the service command. whoami Displays the username of the current user. ip a Displays all IP addresses and network interfaces. ssh username@ip_address Connects to a remote machine using SSH with a specified username and IP address. exit Exits the current shell or terminates the SSH session. Copying Files between Hosts To copy files between hosts in a Linux environment, you can use several tools, with scp, rsync, and sftp being the most common. Tool Usage Strengths Command Example scp Copy files securely over SSH Simple, secure, works with individual files $ scp file user@host:/path/to/destination rsync Copy files securely with efficient synchronization Fast, supports incremental copying $ rsync -avz file user@host:/path/to/destination sftp Interactive file transfer over SSH Allows navigation and file management $ sftp user@host Note: If you are running Windows, you can use the PuTTY Secure Copy Client (pscp.exe) and the PuTTY Secure File Transfer client (psftp.exe) programs.
- 15. Information Technology Institute (ITI) Dr. Mohamed Gamal 15 1. Using scp (Secure Copy) scp is a command-line tool for securely copying files between local and remote hosts over SSH. $ scp [options] source_file username@destination_host:destination_path ▪ Copying a file from local to remote: $ scp /path/to/local/file username@remote_host/ip:/path/to/remote/directory $ scp /C/Users/MG/Downloads/file.txt [email protected]:/home/MG ▪ Copying a file from remote to local: $ scp username@remote_host:/path/to/remote/file /path/to/local/directory $ scp [email protected]:/home/MG/data.csv /C/Users/MG/Downloads ▪ Copying a directory recursively ( -r flag ): $ scp -r /path/to/local/directory username@remote_host:/path/to/remote/directory $ scp -r username@remote_host:/path/to/remote/directory /path/to/local/directory $ scp -r /C/Users/MG/Downloads/Test [email protected]:/home/MG $ scp -r [email protected]:/home/MG/Pictures /C/Users/MG/Downloads ▪ Using a different SSH port (default port is 22): $ scp -P port /path/to/local/file username@remote_host:/path/to/remote/directory $ scp -P 22 [email protected]:/home/MG/data.csv /C/Users/MG/Downloads Other Similar Commands: – rsync – sftp
- 16. Information Technology Institute (ITI) Dr. Mohamed Gamal 16 Listing Processes and Displaying Information Process Types: – A process is a program which is being executed. – Any process may create a child process. – All processes are descendants of the first system process, which is system. – A process can run in the background or foreground. $ echo $$ (See the PID of your current shell process) $ exit $ echo $$ The ps (process status) command in Linux is used to list processes and display information about them. It provides various options to customize the output, depending on what information you want. The ps command uses /proc directory to gather information about running processes. When you run ps, it reads process-related files in the /proc directory to provide details. $ ls -lh /proc $ ps [options] Option Description -e Everything, all processes. -f Full format listing. -u <username> Display processes running as username. -p <PID> Display process information for PID. -l Display Parent PID ‘PPID’. aux Display a comprehensive list of all processes currently running. … …
- 17. Information Technology Institute (ITI) Dr. Mohamed Gamal 17 $ ps $ ps -ef $ ps -ef | head -n 5 $ ps -fu MG $ ps -l (display Parent PID ‘PPID’) $ ps aux | head $ ps aux | grep -i vim $ ls /proc/ $ ps aux | grep 813 (which is shown in /proc) Other similar command $ pstree Display running processes in a tree format. Command Description $ pidof <process name> $ pgrep <process name> Find the PID of a running program. $ pidof vim (find the PID of a running process named vim) $ pgrep vim (find the PID of a running process named vim) Here’re other commands that allow you to view running processes as well but for real-time monitoring. Option Description top Interactive process viewer. » Type 1 to displays all CPU cores' activity individually. » Type s to change the refresh rate (delay between updates). » Type h for help. » Type k to kill a process by entering its PID. » Type r to renice a process to change its priority (-20 to 19, where lower is higher priority). » Press q to quit. » Type z or Z to toggle color display for better readability. » Type n to change the number of processes shown. » Type O to filter processes based on their names (COMMAND=NAME). » Type Shift+P to sort by CPU usage. » Type Shift+T to sort by process time (CPU time used). » Type Shift+M to by memory usage. uptime Display for how long the system has been running.
- 18. Information Technology Institute (ITI) Dr. Mohamed Gamal 18 $ top PID The ID of the running process. USER The process owner. PR The priority of the process. NI The nice value of the process. VIRT The virtual memory size used by the process. RES The resident memory size used by the process (physical memory). SHR The amount of shared memory used by the process. S The state of the process. » R: Running. » S: Sleeping. » D: Uninterruptible sleep. » Z: Zombie. » T: Stopped or traced. » I: Idle %CPU The CPU usage percentage by the process. %MEM The memory usage percentage by the process. TIME+ The total CPU time the process has used since it started. COMMAND The name or command that started the process.
- 19. Information Technology Institute (ITI) Dr. Mohamed Gamal 19 Filtering processes by their name (e.g., firefox) by pressing ‘o’.
- 20. Information Technology Institute (ITI) Dr. Mohamed Gamal 20 Running Processes in the Foreground and Background Up until this point all the commands we have been executing have been running in the foreground. When a command, process, or program is running in the foreground the shell prompt will not be displayed until that process exits. Why run processes in the background? – For long running programs it can be convenient to send them to the background. – Processes that are backgrounded still execute and perform their task, however they do not block you from entering further commands at the shell prompt. Command Description Example $ <command> Start command in the foreground. $ ls -lh $ <command> & Start command in the background. $ sleep 1000 & CTRL + C Kill the running foreground process. - CTRL + Z Suspend the foreground process. - $ bg [%num] Background a suspended process. $ bg %1 $ fg [%num] Foreground a background process. $ fg %1 $ kill [%num] Kill a process by job number or PID. $ kill %1 $ jobs [%num] List jobs. » Plus sign (+): the current job. » Minus sign (-): the previous job. $ jobs
- 21. Information Technology Institute (ITI) Dr. Mohamed Gamal 21 Killing Processes Killing processes in Linux involves terminating processes by sending signals, typically using commands like kill, pkill, or killall. Command Description CTRL + C Kill the running foreground process. $ kill -[signal] <PID> Send a signal to a process by PID. $ kill -l Display a list of signals. $ man 7 signal Display the manual for all signals. $ pkill <process name> Send a signal to process by name. $ killall <process name> Sends a signal to all processes with a specific name. » SIGINT (2): Interrupt signal, sent when you press CTRL+C in the terminal. » SIGTERM (15): Politely asks a process to terminate gracefully, this is the default signal. » SIGKILL (9): Forces termination if a process does not respond. » SIGSTOP (19): Stops (pauses) a process. » SIGCONT (18): Resumes a stopped process. Running all the following is equivalent which is the default behavior. $ kill <PID> $ kill -15 <PID> $ kill -TERM <PID> $ kill -SIGTERM <PID>
- 22. Information Technology Institute (ITI) Dr. Mohamed Gamal 22 Priority and Nice Values in Linux (Article) Some processes may be highly CPU-intensive but not as important as others and hence can have a lower priority while others may or may not be highly CPU intensive but are very important and hence should have higher priority. – For example, if there is a process A, which detects fraud with input data and there is another process B, which makes hourly backups of some data, then the priority(A) > priority(B). – This ensures that if both A and B are running at the same time, A would be allocated more processing bandwidth. Priority Value: Determines the actual priority of a process, used by the Linux kernel for scheduling. – Range: 0–139 (real-time: 0–99, user-space: 100–139). Real-time processes in Linux are high-priority tasks that must complete within strict timing constraints, ensuring they get CPU time before other processes (e.g., embedded systems, telecommunications, …, etc.). User processes in Linux are regular tasks initiated by normal users, with lower priority than real-time processes, and their execution can be adjusted using the nice value. Nice Value: A user-controlled value to influence process priority. – Range: -20 to +19 (-20 is highest priority, 0 is default, +19 is lowest priority) Priority Value = Nice Value + 20 To see how these work together let us run a process that takes a lot of processing power continuously, we will use a shell script (infinite.sh) which uses an infinite loop in it to demonstrate how this works. $ cat > infinite.sh # take input from the terminal #!/bin/bash while true; do echo "Running..." done # Press Ctrl+D here to save and exit Run $ sh infinite.sh & to run the script in the background, use $ top then CTRL+P to see that this process (PID-3227 for example) is taking high processing power of the CPU.
- 23. Information Technology Institute (ITI) Dr. Mohamed Gamal 23 If we run two more processes of infinite.sh then all of them (e.g., PID-3227, 3328, 3295) get equal CPU as all have the same priority (e.g., %CPU = 16.9 for all the three). Now let us give these processes different nice values, there are two ways to do this: 1) Start a new process with a nice value using the $ nice command $ nice -n <nice_val> [command] $ nice -n 10 sh infinite.sh & • When we run this we get another process (PID-8509) with the priority as 30 • Priority = 20 + 10 = 30 • As it has the least priority, it gets the least amount of CPU.
- 24. Information Technology Institute (ITI) Dr. Mohamed Gamal 24 2) Change a running process nice value by its PID using $ renice command $ renice -n <nice_val> -p [PID] $ renice -n 5 -p 8585 • When we run this, the process with PID-8585 get its priority changed to 25. • Priority = 20 + 5 = 25 • The CPU is allocated accordingly as well. Note that: » Regular users can only set positive nice values (0 to 19) to lower a process's priority. » Only the root user (administrator) can set negative nice values (-20 to -1) to increase a process's priority. Summary Feature $ nice $ renice When used When starting a new process For changing running processes Root privilege Required for negative nice values Effect Sets the initial nice value Modifies an existing nice value
- 25. Information Technology Institute (ITI) Dr. Mohamed Gamal 25 Analyzing and Sorting Logs In Linux, system logs are stored in the /var/log directory, which contains log filesfor various system activities, applications, services, and security. Analyzing and sorting logs in Linux is a crucial step for troubleshooting, monitoring, and understanding the behavior of the system. Log File Purpose /var/log/messages Most syslog messages. /var/log/secure Log file for security and authentication-related messages and errors. /var/log/maillog Log file with main server-related messages. /var/log/boot.log Messages related to system start up. … … $ df -h (report file system disk space usage) $ cat /var/log/messages $ less /var/log/boot.log $ tail -f /var/log/messages $ grep "error" /var/log/messages $ sort /var/log/messages $ awk '{print $1, $2, $3}' /var/log/ messages
- 26. Information Technology Institute (ITI) Dr. Mohamed Gamal 26 Scheduling Jobs Cron is a time-based job scheduling service that automates tasks or performs routine maintenance. It checks for scheduled jobs every minute and executes them accordingly. – cron: the service responsible for running scheduled jobs, typically started when the system boots. – Crontab (Cron Table): a program used to create, read, update, and delete job schedules. The crontab file defines when and what commands to run, with five time specification fields (minutes, hour, day of the month, month, and day of the week), followed by the command to execute. Commands $ crontab -e Edit (e) the crontab file for the current user. $ crontab -l List (l) current user's crontab entries. $ crontab -r Remove (r) the current user's crontab file. Examples (Crontab Generator): 0 0 * * 3 <exec_file> (Cron job every Wednesday at midnight) * /30 * * * ls –l (Cron job every half hour) 0 0 * * 1-5 (Run on weekdays only at midnight) $ crontab -e # open crontab file * /30 * * * ls –l Once you write and save a crontab entry using $ crontab -e, the cron daemon (cron) automatically schedules the job based on the specified timing. $ sudo systemctl status crond
- 27. Information Technology Institute (ITI) Dr. Mohamed Gamal 27 Package Management on CentOS, Fedora, and RedHat-based Distributions (Installing Software) A package in Linux is a collection of files that make up an application, along with metadata such as the app's description, version, and dependencies. To install or remove packages, superuser privileges are required. A package manager is used to install, upgrade, and remove packages, while also handling dependencies and tracking installed packages and their versions. 1) Using $ yum Command The yum command is a package management tool for RPM-based distributions like CentOS, Fedora, and RedHat. Search for a package $ yum search <package name> $ yum search inkscape Install a package $ sudo yum install <package name> $ sudo yum install inkscape Remove a package $ sudo yum remove <package name> $ sudo yum remove inkscape Get information about a package $ yum info <package name> $ yum info inkscape Update a Specific Package $ sudo yum update <package name> $ sudo yum update nginx Update All System Packages $ sudo yum update $ sudo yum update 2) Using rpm Command The $rpm command can also be used to manage packages, such as listing installed packages, installing a package from a file, and listing files belonging to a package. List all installed packages $ rpm -qa $ rpm -qa | sort | head Install a package $ rpm -ivh <package-file.rpm> $ sudo rpm -ivh SpiderOak-5.0.3-1.i386.rpm List all files belonging to a package $ rpm -ql <package name> $ rpm -ql inkscape
- 28. Information Technology Institute (ITI) Dr. Mohamed Gamal 28 The dnf package manager is an improved, modern version of yum, designed to address its limitations while maintaining its core functionality. yum/dnf






![Information Technology Institute (ITI)
Dr. Mohamed Gamal 6
Manipulating Files
Change mode of a file
$ chmod [u/g/o/a] [+/-/=] [r/w/x] [filename/dirname]
Type Explanation
u user
g group
o other
a all three
Type Explanation
+ add permission
- remove permission
= set only this permission to u/g/i=o
Use -R flag to apply the permission changes to all files and directories within a specific directory.
Function Example
Adding Permissions
$ chmod a+w file.py
$ chmod u+x file.py
$ chmod -R a+w Games
Removing Permissions
$ chmod -R a-w Games
$ chmod -R a=w Games
$ chmod a=wr file.py
Adding permissions to all
(user, group, other users)
$ chmod +x file.txt
$ chmod g+w,o-rw,a+x file.txt
» Use comma-separated permissions without spaces.
Changing the owner of the file
$ chown Options New_Owner:NEW_GROUP [filename/dirname]
Examples
$ chown Ahmed file.txt
$ chown :developers file.txt
$ chown Ahmed:developers file.txt
$ chown -R Ahmed Games](https://image.slidesharecdn.com/introductiontolinuxospart2-250110205821-40c028c9/85/Introduction-to-Linux-OS-Part-2-Tutorial-6-320.jpg)


![Information Technology Institute (ITI)
Dr. Mohamed Gamal 9
Function Key Mode Description
Copy (Yank) y Visual/Command
Copy the selected text or a
specified range.
Paste Text p Command Mode
Paste the copied text after the
cursor.
Delete Text d Visual/Command
Delete the selected text or a
specified range.
Delete Line dd or [num]dd Command Mode Delete the current line(s).
Delete Word dw or d[num]w Command Mode Delete a word(s).
Undo Change u Command Mode Undo the last change.
Redo Change CTRL + r Command Mode
Redo the change that was
undone.
Searching /<pattern> or ?<pattern> Command Mode
Start a forward/reverse search for
<pattern>.
Move to Line Start 0 Command Mode
Move the cursor to the beginning
of the current line.
Move to Line End CTRL + e Command Mode
Move the cursor to the end of the
current line.
Save and Exit :wq or ZZ Command Mode Save changes and exit Vim.
Exit Without Saving :q! Command Mode Exit Vim without saving changes.
Split Window
(Horizontal)
:split <filename> Command Mode
Open a file in a new horizontal
split window.
Split Window
(Vertical)
:vsplit <filename> Command Mode
Open a file in a new vertical split
window.
Move Between Splits
CTRL + w + arrow key or
h, j, k, l
Command Mode Move between split wind
Graphical Editors
So far we’ve learned about various command line editors. However, if you are running Linux as a desktop
operating system you might be interesting in some graphical text editors and word processors.
» emacs – Emacs has both graphical and command line modes.
» gedit – The default text editor for the Gnome desktop environment.
» gvim – The graphical version of vim.
» kedit – The default text editor for the KDE (K Desktop Environment) desktop environment.](https://image.slidesharecdn.com/introductiontolinuxospart2-250110205821-40c028c9/85/Introduction-to-Linux-OS-Part-2-Tutorial-9-320.jpg)

![Information Technology Institute (ITI)
Dr. Mohamed Gamal 11
Creating a Collection of Files
If you want to bundle a group of files and/or directories together in an archive (not compressing), you can use
the tar command which is one of the oldest and common methods for creating and working with
compressed backup archives.
– You may want to create a copy or backup of a group of files.
– You may have several files you want to transfer at once or as a set.
$ tar [-] c|x|t f <tarfile> <pattern>
Note that you have the choice to precede the tar arguments with a hyphen ( - ) or omit it. For example, $ tar
cf file.tar it is the same as $ tar -cf file.tar.
tar option Description
c Create a tar archive.
x Extract files from the archive.
t Display the table of contents (list).
v Causes tar to be verbose.
f <file> The tar archive file to perform operations against.
$ cd /home/MG
$ mkdir data
$ touch data/file.txt data/report.doc
$ tar cf archived.tar data/
$ tar tf archived.tar
$ file archived.tar
$ cd /tmp
$ tar xf /home/MG/ archived.tar
$ ls data/
$ touch secret secret.bak
$ tar cvf misc.tar sec* data](https://image.slidesharecdn.com/introductiontolinuxospart2-250110205821-40c028c9/85/Introduction-to-Linux-OS-Part-2-Tutorial-11-320.jpg)


![Information Technology Institute (ITI)
Dr. Mohamed Gamal 15
1. Using scp (Secure Copy)
scp is a command-line tool for securely copying files between local and remote hosts over SSH.
$ scp [options] source_file username@destination_host:destination_path
▪ Copying a file from local to remote:
$ scp /path/to/local/file username@remote_host/ip:/path/to/remote/directory
$ scp /C/Users/MG/Downloads/file.txt MG@172.26.107.24:/home/MG
▪ Copying a file from remote to local:
$ scp username@remote_host:/path/to/remote/file /path/to/local/directory
$ scp MG@172.26.107.24:/home/MG/data.csv /C/Users/MG/Downloads
▪ Copying a directory recursively ( -r flag ):
$ scp -r /path/to/local/directory username@remote_host:/path/to/remote/directory
$ scp -r username@remote_host:/path/to/remote/directory /path/to/local/directory
$ scp -r /C/Users/MG/Downloads/Test MG@172.26.107.24:/home/MG
$ scp -r MG@172.26.107.24:/home/MG/Pictures /C/Users/MG/Downloads
▪ Using a different SSH port (default port is 22):
$ scp -P port /path/to/local/file username@remote_host:/path/to/remote/directory
$ scp -P 22 MG@172.26.107.24:/home/MG/data.csv /C/Users/MG/Downloads
Other Similar Commands:
– rsync
– sftp](https://image.slidesharecdn.com/introductiontolinuxospart2-250110205821-40c028c9/85/Introduction-to-Linux-OS-Part-2-Tutorial-15-320.jpg)
![Information Technology Institute (ITI)
Dr. Mohamed Gamal 16
Listing Processes and Displaying Information
Process Types:
– A process is a program which is being executed.
– Any process may create a child process.
– All processes are descendants of the first system process, which is system.
– A process can run in the background or foreground.
$ echo $$ (See the PID of your current shell process)
$ exit
$ echo $$
The ps (process status) command in Linux is used to list processes and display information about them. It
provides various options to customize the output, depending on what information you want.
The ps command uses /proc directory to gather information about running processes. When you run ps, it
reads process-related files in the /proc directory to provide details.
$ ls -lh /proc
$ ps [options]
Option Description
-e Everything, all processes.
-f Full format listing.
-u <username> Display processes running as username.
-p <PID> Display process information for PID.
-l Display Parent PID ‘PPID’.
aux Display a comprehensive list of all processes currently running.
… …](https://image.slidesharecdn.com/introductiontolinuxospart2-250110205821-40c028c9/85/Introduction-to-Linux-OS-Part-2-Tutorial-16-320.jpg)



![Information Technology Institute (ITI)
Dr. Mohamed Gamal 20
Running Processes in the Foreground and Background
Up until this point all the commands we have been executing have been running in the foreground. When a
command, process, or program is running in the foreground the shell prompt will not be displayed until that
process exits.
Why run processes in the background?
– For long running programs it can be convenient to send them to the background.
– Processes that are backgrounded still execute and perform their task, however they do not block you
from entering further commands at the shell prompt.
Command Description Example
$ <command> Start command in the foreground. $ ls -lh
$ <command> & Start command in the background. $ sleep 1000 &
CTRL + C Kill the running foreground process. -
CTRL + Z Suspend the foreground process. -
$ bg [%num] Background a suspended process. $ bg %1
$ fg [%num] Foreground a background process. $ fg %1
$ kill [%num] Kill a process by job number or PID. $ kill %1
$ jobs [%num]
List jobs.
» Plus sign (+): the current job.
» Minus sign (-): the previous job.
$ jobs](https://image.slidesharecdn.com/introductiontolinuxospart2-250110205821-40c028c9/85/Introduction-to-Linux-OS-Part-2-Tutorial-20-320.jpg)
![Information Technology Institute (ITI)
Dr. Mohamed Gamal 21
Killing Processes
Killing processes in Linux involves terminating processes by sending signals, typically using commands like kill, pkill,
or killall.
Command Description
CTRL + C Kill the running foreground process.
$ kill -[signal] <PID> Send a signal to a process by PID.
$ kill -l Display a list of signals.
$ man 7 signal Display the manual for all signals.
$ pkill <process name> Send a signal to process by name.
$ killall <process name> Sends a signal to all processes with a specific name.
» SIGINT (2): Interrupt signal, sent when you press CTRL+C in the terminal.
» SIGTERM (15): Politely asks a process to terminate gracefully, this is the default signal.
» SIGKILL (9): Forces termination if a process does not respond.
» SIGSTOP (19): Stops (pauses) a process.
» SIGCONT (18): Resumes a stopped process.
Running all the following is equivalent which is the default behavior.
$ kill <PID>
$ kill -15 <PID>
$ kill -TERM <PID>
$ kill -SIGTERM <PID>](https://image.slidesharecdn.com/introductiontolinuxospart2-250110205821-40c028c9/85/Introduction-to-Linux-OS-Part-2-Tutorial-21-320.jpg)

![Information Technology Institute (ITI)
Dr. Mohamed Gamal 23
If we run two more processes of infinite.sh then all of them (e.g., PID-3227, 3328, 3295) get equal CPU as all
have the same priority (e.g., %CPU = 16.9 for all the three).
Now let us give these processes different nice values, there are two ways to do this:
1) Start a new process with a nice value using the $ nice command
$ nice -n <nice_val> [command]
$ nice -n 10 sh infinite.sh &
• When we run this we get another process (PID-8509) with the priority as 30
• Priority = 20 + 10 = 30
• As it has the least priority, it gets the least amount of CPU.](https://image.slidesharecdn.com/introductiontolinuxospart2-250110205821-40c028c9/85/Introduction-to-Linux-OS-Part-2-Tutorial-23-320.jpg)
![Information Technology Institute (ITI)
Dr. Mohamed Gamal 24
2) Change a running process nice value by its PID using $ renice command
$ renice -n <nice_val> -p [PID]
$ renice -n 5 -p 8585
• When we run this, the process with PID-8585 get its priority changed to 25.
• Priority = 20 + 5 = 25
• The CPU is allocated accordingly as well.
Note that:
» Regular users can only set positive nice values (0 to 19) to lower a process's priority.
» Only the root user (administrator) can set negative nice values (-20 to -1) to increase a process's priority.
Summary
Feature $ nice $ renice
When used When starting a new process For changing running processes
Root privilege Required for negative nice values
Effect Sets the initial nice value Modifies an existing nice value](https://image.slidesharecdn.com/introductiontolinuxospart2-250110205821-40c028c9/85/Introduction-to-Linux-OS-Part-2-Tutorial-24-320.jpg)







































































