Introduction to os module 1 pdf operating system
- 1. FUNDAMENTALS OF OPERATING SYSTEMS S Savitha Assistant Professor ECE Dept
- 3. Module-1 Introduction: What operating systems do; Computer System Organization, Computer System architecture; Operating System operations; Resource Management Operating System Structures: Operating System Services, User and Operating System interface; System calls, Application Program Interface, Types of system calls;
- 4. Operating system An operating system acts as an intermediary between the user of a computer and computer hardware. The purpose of an operating system is to provide an environment in which a user can execute programs in a convenient and efficient manner The most popular operating systems are Windows, MacOS, Android and Linux.
- 6. Purpose of Operating Systems ● Interface Between Hardware and Software ● File Management ● User Interface ● Ability to Run Programs ● Manage Hardware Without an operating system, a computer would be like a collection of unconnected parts—its hardware would exist, but there would be no way to control or interact with it in a meaningful way.
- 7. Definition An operating system is a program that controls the execution of application programs and acts as an interface between the user of a computer and the computer hardware. A more common definition is that the operating system is the one program running at all times on the computer (usually called the kernel), with all else being application program
- 8. How does an OS work? ● The OS is loaded into the computer by a boot program. ● Users interact with the OS through a user interface (UI), such as a command-line interface (CLI) or a graphical user interface (GUI). ● Application programs use the OS by requesting services through an application program interface (API). ● The OS manages the computer's hardware and software resources. ● The OS schedules tasks for efficient use of the system. ● The OS keeps track of time and resources used by various tasks and users.
- 9. How does an OS work? Once installed, an operating system relies on a large library of device drivers to tailor its services to the specific hardware environment. For example, every application could make a common call to a storage device. The OS receives that call and uses the corresponding driver to translate the call into actions, or commands, needed for the underlying hardware on that specific computer
- 10. Operating system as User Interface – 1. User 2. System and application programs 3. Operating system 4. Hardware
- 11. History of OS 1956 The first Operating System was GN-NAA I/O in 1956 by Genera; Motors. GM-NAA I/O (1956) 1960s IBM developed a time sharing system TSS/360 OS/360, DOS/360 and TSS/360 1970s Unix popularized simplicity and multitasking; rise of personal computers with basic OSs. Unix (1971), CP/M (1974) 1980s GUI-based OSs gained traction; networking features became standard. Apple Macintosh (1984), Windows (1985) 1990s Open-source Linux emerged; GUIs in Windows and Mac OS improved. Linux (1991), Windows 95 (1995) 2000s-Present Mobile OSs dominated; cloud and virtualization technologies advanced computing. iOS (2007), Android (2008)
- 12. List of common Operating Systems Windows OS Developer : Microsoft Key Features : User-friendly interface, software compatibility, hardware support, Strong gaming support. Advantages : Easy to use for most users, Broad support from third-party applications , Frequent updates and support. Typical Use Cases : Personal computing, Business environment, Gaming. macOS Developer : Apple. Key Features : Sleek, intuitive user interface, Strong integration with other Apple products, Robust security features, High performance and stability. Advantages : Optimized for Apple hardware, Seamless experience across Apple ecosystem, Superior graphics and multimedia capabilities. Typical Use Cases : Creative industries (design, video editing, music production), Personal computing, Professional environments.
- 13. List of common OS Linux Developer : Community-driven (various distributions). Key Features : Open-source and highly customizable, Robust security and stability, Lightweight and can run on older hardware, Large selection of distributions (e.g., Ubuntu, Fedora, Debian). Advantages : Free to use and distribute, Strong community support, Suitable for servers and development environments. Typical Use Cases : Servers and data centers, Development and programming, Personal computing for tech enthusiasts. Unix Developer: Originally AT&T Bell Labs, various commercial and open-source versions available Key Features: Multiuser and multitasking capabilities, Strong security and stability, Powerful command-line interface, Portability across different hardware platforms Advantages: Reliable and robust performance, Suitable for high-performance computing and servers, Extensive support for networking Typical Use Cases: Servers and workstations, Development environments, Research and academic settings
- 14. What does OS do? User View:
- 15. User View ● Ease of use ● Security
- 16. What does OS do? System view: ● OS is a resource allocator ( manages all resources) ● OS is a control program (controls and executes program)
- 17. Functions of an Operating System ● Memory Management ● Processor Management ● Device Management ● File Management ● I/O Management ● Booting ● Security
- 18. Functions of an Operating System User Interface or Command Interpreter
- 19. Functions of an Operating System Performs Basic Computer Tasks The management of various peripheral devices such as the mouse, keyboard, and printer is carried out by the operating system. Today most operating systems are plug-and-play. These operating systems automatically recognize and configure the devices with no user interference.
- 20. Functions of an Operating System Network Management Network Communication: Think of them as traffic cops for your internet traffic. Operating systems help computers talk to each other and the internet. They manage how data is packaged and sent over the network, making sure it arrives safely and in the right order. Settings and Monitoring: Think of them as the settings and security guard for your internet connection. They also let you set up your network connections, like Wi-Fi or Ethernet
- 22. Computer Organisation ● Computer system ● Storage structure ● I/O structure
- 23. Interrupt timeline for a single program doing output
- 24. BOOTSTRAP ● The first program to run on computer power-on is a bootstrap program, which then loads the operating system ● Bootstrap is stored in (ROM)/ (EEPROM)
- 25. Interrupt Interrupts are the events that take place to inform the operating system to stop the current execution of the current process and handle the Interrupt Service Routine (ISR). ISR is responsible for finding out which software or hardware caused the interruption and informing the CPU about it. CPU will service the request and after the completion of the request, CPU resumes the execution of the process which CPU was previously executing. Interrupts can be caused by hardware as well as software
- 26. Interrupt request lines. nonmaskable interrupt, which is reserved for events such as unrecoverable memory errors. maskable: it can be turned off by the CPU before the execution of critical instruction sequences that must not be interrupted. The maskable interrupt is used by device controllers to request service.
- 27. The CPU hardware has a wire called the interrupt-request line that the CPU senses after executing every instruction.
- 28. ● The Von Neumann architecture, which is the foundation of most modern computers. Named after John von Neumann. ● The Von Neumann architecture popularized the stored-program concept, making computers more flexible and easier to reprogram. ● This design stores both data and instructions in the same memory, simplifying hardware design and enabling general-purpose computing. ● A single bus is used for transferring data, addresses, and control signals, which can limit performance. ● Sequential Execution: Instructions are executed one at a time in a sequential manner. Von Neumann architecture
- 29. Von Neumann architecture first fetches an instruction from memory and stores that instruction in the instruction register. The instruction is then decoded and may cause operands to be fetched from memory and stored in some internal register. After the instruction on the operands has been executed, the result may be stored back in memory. Notice that the memory unit sees only a stream of memory addresses.
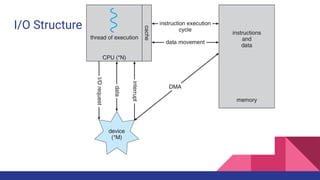
- 31. Storage Structure Main memory ( RAM ) ● Programs must be loaded into RAM to run. ● Instructions and data fetched from RAM into registers. ● RAM is volatile ● "Medium" size and speed Volatile memory faster, smaller, and more expensive per bit: ● Registers ● CPU Cache Non-volatile memory ( "permanent" storage ) is slower, larger, and less expensive per bit: Electronic disks Magnetic disks Optical disks Magnetic Tapes
- 33. 1. Registers Registers are small, high-speed memory units located in the CPU. They are used to store the most frequently used data and instructions. Registers have the fastest access time and the smallest storage capacity, typically ranging from 16 to 64 bits. 2. Cache Memory Cache memory is designed to minimize the time it takes to access data by providing the CPU with quick access to frequently used data.
- 34. 3. Main Memory Main memory, also known as RAM (Random Access Memory), is the primary memory of a computer system. It has a larger storage capacity than cache memory, but it is slower. Main memory is used to store data and instructions that are currently in use by the CPU. Types of Main Memory Static RAM: Static RAM stores the binary information in flip flops and information remains valid until power is supplied. Static RAM has a faster access time and is used in implementing cache memory. Dynamic RAM: It stores the binary information as a charge on the capacitor. It requires refreshing circuitry to maintain the charge on the capacitors after a few milliseconds. It contains more memory cells per unit area as compared to SRAM.
- 35. 4. Secondary Storage Secondary storage, such as hard disk drives (HDD) and solid-state drives (SSD) , is a non-volatile memory unit that has a larger storage capacity than main memory. It is used to store data and instructions that are not currently in use by the CPU. Secondary storage has the slowest access time and is typically the least expensive type of memory in the memory hierarchy. 5. Magnetic Disk Magnetic Disks are simply circular plates that are fabricated with either a metal or a plastic or a magnetized material. The Magnetic disks work at a high speed inside the computer and these are frequently used. 6. Magnetic Tape Magnetic Tape is simply a magnetic recording device that is covered with a plastic film. Magnetic Tape is generally used for the backup of data. In the case of a magnetic tape, the access time for a computer is a little slower and therefore, it requires some amount of time for accessing the strip.
- 36. I/O Structure
- 37. Computer-System Architecture ● Single-Processor Systems ● Multiprocessor Systems ● Clustered Systems
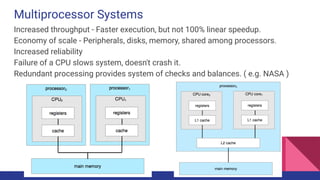
- 38. Single-Processor Systems One main CPU which manages the computer and runs user apps. Other specialized processors ( disk controllers, GPUs, etc. ) do not run user apps.
- 39. Multiprocessor Systems Increased throughput - Faster execution, but not 100% linear speedup. Economy of scale - Peripherals, disks, memory, shared among processors. Increased reliability Failure of a CPU slows system, doesn't crash it. Redundant processing provides system of checks and balances. ( e.g. NASA )
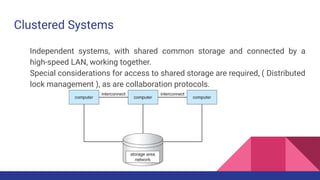
- 40. Clustered Systems Independent systems, with shared common storage and connected by a high-speed LAN, working together. Special considerations for access to shared storage are required, ( Distributed lock management ), as are collaboration protocols.
- 41. Operating-System Operations ● Multiprogramming and Multitasking ● Dual-Mode and Multimode Operation ● Timer
- 42. Types of OS ● Batch OS ● Multiprogramming OS ● Multitasking time sharing OS ● Multiprocessing OS ● Real time OS
- 43. Operating-System Structure A time-sharing ( multi-user multi-tasking ) OS requires: ● Memory management ● Process management ● Job scheduling ● Resource allocation strategies ● Swap space / virtual memory in physical memory ● Interrupt handling ● File system management ● Protection and security ● Inter-process communications
- 44. Resource Management Process Management Memory Management File-System Management Mass Storage Management
- 45. Process Management The OS has to create and delete processes, schedule processes (and threads) on CPUs, suspend and resume processes, provide mechanisms for process synchronization, and provide mechanisms for process communication.
- 46. Memory Management The OS has to keep track of which parts of memory are currently being used, and which processes are using them. Allocate and deallocate memory space as needed. Decide which processes (or parts of processes) and data to copy into or out of memory.
- 47. File-System Management The OS has to ● create and delete files ● create and delete directories (folders), ● support primitives for manipulating files and directories, ● map files onto mass storage, and back up files on stable (nonvolatile) storage media.
- 48. Mass Storage Management Regarding mass storage, the OS has to mount and unmount devices, manage free space, allocate storage, schedule disk accesses, perform partitioning, and provide protection.
- 49. Cache Management Some of the caching that goes on in computers is controlled by the operating system, and some is not.
- 50. Cache Management Migration of integer A from disk to register
- 51. Security and Protection ● Modern computing systems require security and protection. ● The system grants only an authorized process access to a resource. ● The OS must surveil the system and ensure that resources are utilized safely and correctly. ● To maintain protection and security, the operating system must manage certain kinds of data, such as user ID numbers, group ID numbers, and passwords.
- 52. Virtualization ● Virtualization is a technology that enables one computer to function simultaneously as several different computers, each with its own operating system. ● Under virtualization several guest operating systems can run 'on top of' a host operating system, and all of these systems use the computer hardware natively. ● A person might use a virtualized operating systems to run an applications that is not available on the host operating system. ● If someone develops versions of a new application to execute on several different operating systems, virtualization could allow the developer to test and debug all the version on one computer. ● There is a Linux virtual machine provided with the text.
- 53. Dual and multimode operation
- 54. Timer ● Before the kernel begins executing user code, a timer is set to generate an interrupt. ● The timer interrupt handler reverts control back to the kernel. ● This assures that no user process can take over the system. ● Timer control is a privileged instruction, ( requiring kernel mode )
- 57. ● User Interfaces - Means by which users can issue commands to the system. Depending on the system these may be a command-line interface ( e.g. sh, csh, ksh, tcsh, etc. ), a GUI interface ( e.g. Windows, X-Windows, KDE, Gnome, etc. ), or a batch command systems. The latter are generally older systems using punch cards of job-control language, JCL, but may still be used today for specialty systems designed for a single purpose. ● Program Execution - The OS must be able to load a program into RAM, run the program, and terminate the program, either normally or abnormally. ● I/O Operations - The OS is responsible for transferring data to and from I/O devices, including keyboards, terminals, printers, and storage devices. ● File-System Manipulation - In addition to raw data storage, the OS is also responsible for maintaining directory and subdirectory structures, mapping file names to specific blocks of data storage, and providing tools for navigating and utilizing the file system.
- 58. ● Communications - Inter-process communications, IPC, either between processes running on the same processor, or between processes running on separate processors or separate machines. May be implemented as either shared memory or message passing, ( or some systems may offer both. ) ● Error Detection - Both hardware and software errors must be detected and handled appropriately, with a minimum of harmful repercussions. Some systems may include complex error avoidance or recovery systems, including backups, RAID drives, and other redundant systems. Debugging and diagnostic tools aid users and administrators in tracing down the cause of problems.
- 59. ● Resource Allocation - E.g. CPU cycles, main memory, storage space, and peripheral devices. Some resources are managed with generic systems and others with very carefully designed and specially tuned systems, customized for a particular resource and operating environment. ● Accounting - Keeping track of system activity and resource usage, either for billing purposes or for statistical record keeping that can be used to optimize future performance. ● Protection and Security - Preventing harm to the system and to resources, either through wayward internal processes or malicious outsiders. Authentication, ownership, and restricted access are obvious parts of this system. Highly secure systems may log all process activity down to excruciating detail, and security regulation dictate the storage of those records on permanent non-erasable medium for extended times in secure ( off-site ) facilities.
- 62. System call ● The use of APIs instead of direct system calls provides for greater program portability between different systems. The API then makes the appropriate system calls through the system call interface, using a table lookup to access specific numbered system calls ● Parameters are generally passed to system calls via registers, or less commonly, by values pushed onto the stack. Large blocks of data are generally accessed indirectly, through a memory address passed in a register or on the stack
- 63. The handling of a user application invoking the open( ) system call
- 64. Types of system calls
- 67. Types of System Call