Introduction to the OSI 7 layer model and Data Link Layer
- 1. Introduction to OSI 7 layer model and Data Link Layer in Detail VNIT ACM Student Chapter - Mustaqim Moulavi
- 2. Introduction to Number system Binary number system
- 3. Introduction to Number system Hexadecimal number system 0000 = 0 = (0) 10 0001 = 1 = (1) 10 0010 = 2 . 1010 = A = (10) 10 . 1110 = E = (14) 10 1111 = F = (15) 10
- 4. 7 Layer OSI Model of Networking Architecture ISO/ Open System Interconnection Reference Model It divides network architecture into seven layers which, from top to bottom A layer is a collection of conceptually similar functions that provide services to the layer above it and receives service from the layer below it.
- 5. 7 Layer OSI Model of Networking Architecture Outlines WHAT needs to be done to send data from one computer to another. Each layer Provides services to the layer above it And gets services From layer below it You can see it like Each layer is customer Of the layer below it And provides services to Layer above it
- 6. 7 Layer OSI Model of Networking Architecture What each layer does?
- 7. Remembering the 7 Layers 7 - A pplication A ll 6 - P resentation P eople 5 - S ession S eem 4 - T ransport T o 3 - N etwork N eed 2 - D ata Link D ata 1 - P hysical P rocessing
- 8. Topics for today’s seminar Data Link Layer in Detail in 3 parts The Basic Design principles for Layer 2 i.e. Link Layer communication between only 2 nodes and dealing with problems Working of Real networks - Ethernet (LAN) system at the Link Layer level Wireshark Demo showing the actual live data flowing in the network in the form of packets, decoding them and understanding what all this data packets means.*
- 9. Some terminology: hosts and routers are nodes communication channels that connect adjacent nodes along communication path are links wired links wireless links LANs layer-2 packet is a frame , encapsulates datagram “ link”
- 10. What is link layer? data-link layer has responsibility of transferring datagram from one node to adjacent node over a link Deals with communication between adjacent nodes joined by a physical(LAN wire, WIFI, Bluetooth) link. “ link”
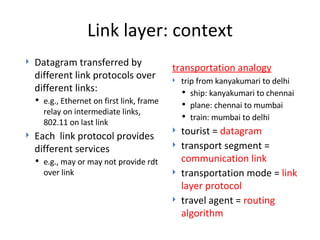
- 11. Link layer: context Datagram transferred by different link protocols over different links: e.g., Ethernet on first link, frame relay on intermediate links, 802.11 on last link Each link protocol provides different services e.g., may or may not provide rdt over link transportation analogy trip from kanyakumari to delhi ship: kanyakumari to chennai plane: chennai to mumbai train: mumbai to delhi tourist = datagram transport segment = communication link transportation mode = link layer protocol travel agent = routing algorithm
- 12. Why data link layer is required? The data sent in the physical layer is in the form of 0 and 1. physical layer doesn't understand what it means. It is like 2 blind persons communicating with only 2 words YES and NO. No one knows where a sentence starts and where it ends and what it means. Moreover Communication circuits make errors occasionally. The function of the link layer is to provide error free communication and make some meaning out of the data sent/receieved.
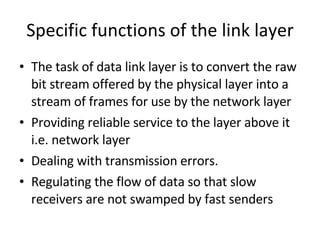
- 13. Specific functions of the link layer The task of data link layer is to convert the raw bit stream offered by the physical layer into a stream of frames for use by the network layer Providing reliable service to the layer above it i.e. network layer Dealing with transmission errors. Regulating the flow of data so that slow receivers are not swamped by fast senders
- 14. Link Layer Services Framing, link access: encapsulate datagram into frame, adding header, trailer channel access if shared medium “ MAC” addresses used in frame headers to identify source, dest different from IP address! Reliable delivery between adjacent nodes seldom used on low bit error link (fiber, some twisted pair) wireless links: high error rates Q: why both link-level and end-end reliability?
- 15. Link Layer Services (more) Flow Control: pacing between adjacent sending and receiving nodes Error Detection : errors caused by signal attenuation, noise. receiver detects presence of errors: signals sender for retransmission or drops frame (used in fiber optics and wired networks) Error Correction: receiver identifies and corrects bit error(s) without resorting to retransmission (used in wifi)
- 16. Adaptors Communicating sending side: encapsulates datagram in a frame adds error checking bits, flow control, etc. receiving side looks for errors, flow control, etc extracts datagram, passes to receiving node sending node datagram adapter adapter link layer protocol frame frame
- 17. One of the Methods of Framing Starting and ending flags with bit stuffing Each frame begins and ends with a special bit pattern (flag byte) 01111110 Whenever the senders data link layer encounters five consecutive ones in the data it automatically stuffs a zero bit into the outgoing bit stream Thus if the receiver looses track of where it is all it has to do is to scan input for flag sequences since they can only occur at frame boundaries and never within the data.
- 18. Reliable delivery The outgoing frames are numbered and the receiver sends an acknowledgement for that particular frame So the sender knows which frames the receiver has received. Sender knows which frame to send again and which shouldn’t be sent again. This ensures the reliable delivery of the data
- 19. Flow control Sender wants to send fast than the capacity of the receiver. The frames might be lost in this case Feedback based flow control Receiver sends back information to sender giving it permission to send more data For example when a connection is setup the receiver might say “you may send me n frames now but after they have been sent do not send any more until I have told you to continue”
- 20. Error Detection EDC= Error Detection and Correction bits (redundancy) D = Data protected by error checking, may include header fields Error detection not 100% reliable! protocol may miss some errors, but rarely larger EDC field yields better detection and correction
- 21. Parity Checking Single Bit Parity: Detect single bit errors Two Dimensional Bit Parity : Detect and correct single bit errors Chances are 50:50
- 22. Sender: treat segment contents as sequence of 16-bit integers checksum: addition (1’s complement sum) of segment contents sender puts checksum value into UDP checksum field Receiver: compute checksum of received segment check if computed checksum equals checksum field value: NO - error detected YES - no error detected. But maybe errors nonetheless? More later …. Goal: detect “errors” (e.g., flipped bits) in transmitted segment (note: used at transport layer only )
- 23. Checksumming: Cyclic Redundancy Check used at link layer view data bits, D , as a binary number choose r+1 bit pattern (generator function), G goal: choose r CRC bits, R , such that <D+R> exactly divisible by G (modulo 2) receiver knows G, divides <D,R> by G. If non-zero remainder: error detected! widely used in practice
- 24. CRC Example D = 101110 Add r = 000 after D (for purpose of division only) G= 1001 Remainder R = 011 Add remainder R to D D+R = 101110(011) This bitpattern is divisible by generator function and so will be error free IEEE 802 G function = 1000001001100000010001110110110111
- 25. Working of Ethernet MAC Addresses and ARP 32-bit IP address: network-layer address used to get datagram to destination IP subnet MAC (or LAN or physical or Ethernet) address: used to get datagram from one interface to another physically-connected interface (same network) 48 bit MAC address (for most LANs) burned in the adapter ROM
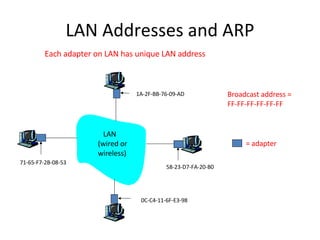
- 26. LAN Addresses and ARP Each adapter on LAN has unique LAN address Broadcast address = FF-FF-FF-FF-FF-FF = adapter 1A-2F-BB-76-09-AD 58-23-D7-FA-20-B0 0C-C4-11-6F-E3-98 71-65-F7-2B-08-53 LAN (wired or wireless)
- 27. LAN Address (more) MAC address allocation administered by IEEE manufacturer buys portion of MAC address space (to assure uniqueness) Analogy: (a) MAC address: like Social Security Number (b) IP address: like postal address MAC flat address (no hierarchy) ➜ portability can move LAN card from one LAN to another IP hierarchical address NOT portable depends on IP subnet to which node is attached
- 28. ARP: Address Resolution Protocol Each IP node (Host, Router) on LAN has ARP table ARP Table: IP/MAC address mappings for some LAN nodes < IP address; MAC address; TTL> TTL (Time To Live): time after which address mapping will be forgotten (typically 20 min) 1A-2F-BB-76-09-AD 58-23-D7-FA-20-B0 0C-C4-11-6F-E3-98 71-65-F7-2B-08-53 LAN 237.196.7.23 237.196.7.78 237.196.7.14 237.196.7.88 Question: how to determine MAC address of B knowing B’s IP address?
- 29. ARP protocol: Same LAN (network) A wants to send datagram to B, and B’s MAC address not in A’s ARP table. A broadcasts ARP query packet, containing B's IP address Dest MAC address = FF-FF-FF-FF-FF-FF all machines on LAN receive ARP query B receives ARP packet, replies to A with its (B's) MAC address frame sent to A’s MAC address (unicast) A caches (saves) IP-to-MAC address pair in its ARP table until information becomes old (times out) soft state: information that times out (goes away) unless refreshed ARP is “plug-and-play”: nodes create their ARP tables without intervention from net administrator
- 30. Routing to another LAN send datagram from A to B via R assume A know’s B IP address In routing table at source Host, find router 111.111.111.110 Two ARP tables in router R, one for each IP network (LAN) In ARP table at source, find MAC address E6-E9-00-17-BB-4B, etc A R B
- 31. A creates datagram with source A, destination B A uses ARP to get R’s MAC address for 111.111.111.110 A creates link-layer frame with R's MAC address as dest, frame contains A-to-B IP datagram A’s adapter sends frame R’s adapter receives frame R extracts IP datagram from Ethernet frame, sees its destined to B R uses ARP to get B’s MAC address R creates frame containing A-to-B IP datagram sends to B A R B
- 32. Ethernet Frame Structure Sending adapter encapsulates IP datagram (or other network layer protocol packet) in Ethernet frame Preamble: 7 bytes with pattern 10101010 followed by one byte with pattern 10101011 used to synchronize receiver, sender clock rates
- 33. Ethernet Frame Structure (more) Addresses: 6 bytes if adapter receives frame with matching destination address, or with broadcast address (eg ARP packet), it passes data in frame to net-layer protocol otherwise, adapter discards frame Type: indicates the higher layer protocol (mostly IP but others may be supported such as Novell IPX and AppleTalk) CRC: checked at receiver, if error is detected, the frame is simply dropped 5: DataLink Layer
- 34. Wireshark Demo to see Ethernet packets References : Computer Networks – Andrew S. Tanenbaum Computer Networking : A Top-Down Approach Featuring the Internet – James F. Kurose , Keith W. Ross