IoT Networking Part 2
3 likes1,322 views
The document discusses several common IoT networking protocols: - MQTT is a lightweight publish/subscribe protocol that works over TCP/IP and supports three quality of service (QoS) levels. - CoAP is designed for constrained devices and machine-to-machine communication using a RESTful request/response model over UDP. It defines four message types. - XMPP supports publish/subscribe messaging over TCP and uses XML, allowing for interoperability and extensibility. - AMQP is optimized for financial applications using a binary protocol over TCP, and guarantees message delivery through different levels like at-least-once and exactly-once.
1 of 24
Downloaded 123 times























Ad
Recommended
IoT Networking



IoT NetworkingHitesh Mohapatra This document discusses IoT networking and quality of service (QoS) for IoT networks. It begins by describing the characteristics of IoT devices such as low processing power, small size, and energy constraints. It then discusses enabling the classical Internet for IoT devices through standards developed by the IETF, including 6LoWPAN, ROLL, and CoRE. CoRE provides a framework for IoT applications and services discovery. The document concludes by examining policies for QoS in IoT networks to guarantee intended service, covering resource utilization, data timeliness, availability, and delivery.
IoT Connectivity 



IoT Connectivity Hitesh Mohapatra The document discusses several communication protocols that are important for the Internet of Things (IoT), including IEEE 802.15.4, Zigbee, 6LoWPAN, Wireless HART, Z-Wave, ISA 100, Bluetooth, NFC, and RFID. It provides details on IEEE 802.15.4, including its features, variants, and introduction to related protocols like Zigbee, 6LoWPAN, and Wireless HART.
nptel-1.pdf



nptel-1.pdfRagesh Warrier The document provides an introduction to the Internet of Things (IoT). It defines IoT as connecting devices, machines and tools to the internet using wireless technologies. Over 9 billion devices are currently connected, projected to exceed 20 billion. IoT unifies technologies like embedded systems, cloud computing, big data, machine learning and networking. The term originated from a 2005 report discussing internet-connected machines to machine connectivity networks extending to common household devices. IoT enables efficient monitoring and control of physical objects through embedded sensors and communication across networks.
IoT, M2M and IoT System Management



IoT, M2M and IoT System ManagementVikram Nandini Introduction
M2M Vs IoT
SDN & NFV
IoT System Management
SNMP
Network Operator Requirements
NETCONF
YANG
NETOPEER
IoT sensing and actuation



IoT sensing and actuationHitesh Mohapatra This document discusses sensors and actuators in Industry 4.0 and the Industrial Internet of Things. It defines sensors as devices that detect physical quantities and convert them into signals, and actuators as devices that convert energy signals into motion or force. It classifies sensors as passive or active, analog or digital, and scalar or vector. It also describes common sensor characteristics and classifications of actuators such as electric, fluid power, and manual linear and rotary actuators.
Numerical Problems on Ampitude Modulation



Numerical Problems on Ampitude ModulationRenji K This document provides information on amplitude modulation (AM) including important formulas, example problems, and their solutions. Formulas are given for modulation index, carrier power, total power, sideband frequencies and power. Example problems cover calculating modulation index, carrier power, total power, sideband frequencies and power for various modulation percentages and modulation indices. The last few examples calculate percentage power savings when suppressing a sideband and carrier.
8085 instruction set



8085 instruction setVelalar College of Engineering and Technology This document provides an overview of the instruction set of the 8085 microprocessor. It begins by defining what an instruction is and the classification of the 8085 instruction set. It then proceeds to describe various data transfer, arithmetic, logical, branching, and control instructions in detail through opcode, operands, examples, and before/after execution illustrations. The document aims to provide a comprehensive reference for the complete set of 246 instructions supported by the 8085 microprocessor.
Application Layer Protocols for the IoT



Application Layer Protocols for the IoTDamien Magoni A 5-part course on the two most popular application layer protocols for the IoT namely MQTT and CoAP.
IoT Communication Protocols



IoT Communication ProtocolsPradeep Kumar TS This slide features the list of communication protocols that are suitable for Internet of things. It features from http to CoAP
Protocols for IoT



Protocols for IoTAravindhan G K This is a technical presentation describing two protocols namely MQTT and CoAP for IoT communications. This explains the protocols in conjunction with OSI layers.
IOT - Unit 3.pptx



IOT - Unit 3.pptxPallaviPatil580306 IP is the standard network layer protocol for IoT due to its advantages like being open, ubiquitous, scalable and manageable. However, optimizations are needed for IP in IoT due to constraints of nodes and networks. 6LoWPAN defines optimizations like header compression, fragmentation and mesh addressing to use IP in low power wireless networks. Profiles like Thread and certifications like IPv6 Ready Logo help ensure interoperability.
Wifi & 802.11 Standards



Wifi & 802.11 StandardsVipul Kumar Maurya Wi-Fi uses radio waves to transmit data through the air according to the IEEE 802.11 standards. It allows computers and other devices to connect to the internet and each other wirelessly. The 802.11 standards include 802.11b, 802.11a, 802.11g, 802.11n, and 802.11ac which provide different speeds and capabilities. Wi-Fi networks use access points, wireless cards, and security protocols like WEP, WPA, and WPA2 to transmit data securely between devices over short ranges.
Internet of Things - module 1



Internet of Things - module 1Syed Mustafa The document outlines a syllabus for an Internet of Things Technology course. It includes 5 modules that will be covered over the semester. Evaluation will consist of 3 internal assessments weighted at 30%, 40%, and 30% respectively, covering different portions of the syllabus. Students must attain a minimum of 85% attendance and assignments will be due before each internal assessment. The class website and online testing platform are also indicated.
WSN IN IOT



WSN IN IOTskumartarget This document discusses wireless sensor networks and their role in the Internet of Things. It defines sensor networks and their architecture, including sensor nodes that communicate wirelessly to a base station. It outlines challenges for sensor networks like fault tolerance, scalability, and quality of service. It also describes how sensor networks can be integrated into the Internet of Things through different approaches, with the first using a single gateway and later approaches using hybrid networks and access points. Applications of sensor networks in IoT include wearable devices collecting biometric data and communicating it to servers.
Business models for business processes on IoT



Business models for business processes on IoTFabMinds The document discusses business models for business processes on the Internet of Things. It covers key topics like IoT applications, business models, value creation using IoT, and business model scenarios for IoT. Business models need innovation to adapt to new customer access and interactions enabled by technologies like cloud computing and mobile communications. Value is created on IoT through addressing emergent needs, information convergence, and recurrent revenue from networked products. Example business model scenarios for IoT leverage data from multiple sources like sensors, M2M, and open data.
netconf and yang



netconf and yangpavan penugonda This chapter discusses systems management for IoT and introduces NETCONF and YANG as solutions. It notes the need for automated configuration, monitoring, reliability and reusable configurations for IoT systems management. It describes SNMP and its limitations. NETCONF is introduced as a session-based network management protocol using XML and YANG for data modeling. YANG is used to model configuration and state data for NETCONF. The chapter provides an example YANG module and discusses using NETCONF and YANG for IoT systems management.
489594658-Unit-III-Iot architecture.pptx



489594658-Unit-III-Iot architecture.pptxMBIEDANGOMEGNIFRANKG Very good lecture note on IoT Architecture
TCP/IP Network ppt



TCP/IP Network pptextraganesh The document provides an overview of the TCP/IP model, describing each layer from application to network. The application layer allows programs access to networked services and contains high-level protocols like TCP and UDP. The transport layer handles reliable delivery via protocols like TCP and UDP. The internet layer organizes routing with the IP protocol. The network layer consists of device drivers and network interface cards that communicate with the physical transmission media.
Components of IOT Implementation



Components of IOT ImplementationAashiq Ahamed N In this we are going to see about:-
Sensors
Networks
Standards
Intelligent Analysis
Intelligent Actions
IPv4



IPv4Dhiraj Mishra - The document discusses Internet Protocol (IP) which is the principal communications protocol for relaying datagrams across network boundaries. There are two major versions - IPv4 which is the dominant protocol, and IPv6 which is its successor.
- IPv4 uses 32-bit addresses divided into five classes (A, B, C, D, E). It allows for over 4 billion addresses but deficiencies in the classful addressing system led to address depletion.
- Classless addressing was introduced to overcome depletion by granting variable length address blocks defined by an IP address and network mask. This provides a hierarchical addressing structure and greater flexibility.
Mobile computing (Wireless) Medium Access Control (MAC)



Mobile computing (Wireless) Medium Access Control (MAC)Jyothishmathi Institute of Technology and Science Karimnagar Motivation for a specialized MAC (Hidden and exposed terminals, Near and far terminals), SDMA, FDMA, TDMA, CDMA, Wireless LAN/(IEEE 802.11)
Mobile Network Layer: IP and Mobile IP Network Layers, Packet Delivery and Handover Management, Location Management, Registration, Tunneling and Encapsulation, Route Optimization, DHCP
The constrained application protocol (CoAP)



The constrained application protocol (CoAP)Hamdamboy (함담보이) The Constrained Application Protocol (CoAP) is a RESTful web transfer protocol for resource-constrained networks and nodes. CoAP uses a simple binary message format carried over UDP that supports asynchronous messaging with optional message confirmation and retransmission. CoAP supports features like GET, POST, PUT, DELETE methods, URIs, content formats and codes that are similar to HTTP but optimized for constrained nodes and networks.
5G Security Briefing



5G Security Briefing3G4G A detailed look at 5G security by experts from wenovator, Dr. Anand R. Prasad & Hans Christian Rudolph.
This webinar covers:
(1) 5G security
(2) Private networks security and
(3) Open vRAN security
To learn more about wenovator, visit their website: https://www.wenovator.com/
All our #3G4G5G slides and videos are available at:
Videos: https://www.youtube.com/3G4G5G
Slides: https://www.slideshare.net/3G4GLtd
Security Page: https://www.3g4g.co.uk/Security/
5G Page: https://www.3g4g.co.uk/5G/
Security Blog Posts: https://blog.3g4g.co.uk/search/label/Security
Free Training Videos: https://www.3g4g.co.uk/Training/
Zigbee Presentation



Zigbee PresentationMaathu Michael zigbee is a new wireless technolgy Designed for low power consumption allowing batteries to essentially last for ever....
IOT PROTOCOLS.pptx



IOT PROTOCOLS.pptxDRREC This document discusses IoT protocols for data communication and connection models. It describes the key pillars of IoT protocols as being device, connectivity, data, and analytics. It also outlines various types of IoT data protocols like AMQP, DDS, XMPP, and WebSocket that establish end-to-end communication. Additionally, it covers IoT network protocols like Bluetooth, LPWANs, ZigBee, Z-Wave and others that facilitate secured communication between IoT devices over the internet.
Mobile Ad hoc Networks



Mobile Ad hoc NetworksJagdeep Singh Mobile ad hoc networks (MANETs) are formed spontaneously by wireless devices without any preexisting infrastructure. Nodes in a MANET are free to move and dynamically change the network topology. MANETs have applications in military operations, emergency response, education, and home/office use. Key challenges include dynamic topology, limited resources, and lack of centralized management. Media access control protocols address issues like hidden and exposed terminals. Routing protocols can be proactive (table-based) or reactive (on-demand) to find routes between nodes in the changing network.
Mobile Network Layer



Mobile Network LayerRahul Hada Mobile Network Layer protocols and mechanisms allow nodes to change their point of attachment to different networks while maintaining ongoing communication. Key concepts include:
- Mobile IP adds mobility support to IP, allowing nodes to use the same IP address even when changing networks. It relies on home agents and care-of addresses.
- Registration allows mobile nodes to inform their home agent of their current location when visiting foreign networks. Tunneling and encapsulation techniques are used to forward packets to mobile nodes' current locations.
- Various routing protocols like DSDV have been developed for mobile ad hoc networks which have no fixed infrastructure and dynamic topologies.
lecture4week1iotnetworkingpart1-190114153249.pptx



lecture4week1iotnetworkingpart1-190114153249.pptxIshu Chaudhary The Internet of Things (IoT) represents a revolutionary concept in the realm of technology and connectivity. At its core, IoT refers to the network of physical devices, vehicles, home appliances, and other items embedded with sensors, software, and connectivity, enabling them to connect and exchange data over the internet.
The concept of IoT emerged from the convergence of multiple technologies, including wireless communication, micro-electromechanical systems (MEMS), and the internet itself. These advancements have allowed for the development of smart devices capable of collecting and transmitting data in real-time, creating opportunities for increased automation, efficiency, and even new business models across various sectors.
One of the defining characteristics of IoT is its ability to interconnect traditionally non-internet-enabled physical objects and allow them to communicate and interact with each other autonomously. This interconnectedness opens up vast possibilities for applications in industries such as healthcare, agriculture, transportation, manufacturing, and smart cities.
In healthcare, for example, IoT devices can monitor patients remotely, gather health data in real-time, and even enable predictive analytics to improve diagnostics and treatment outcomes. In agriculture, IoT sensors can monitor soil conditions, weather patterns, and crop health, leading to more efficient use of resources like water and fertilizers.
IoT also plays a crucial role in the development of smart homes and cities, where interconnected devices can enhance energy efficiency, automate household tasks, improve public safety through real-time monitoring, and optimize traffic flow and parking.
However, with the proliferation of IoT devices comes challenges related to security, privacy, interoperability, and data management. The sheer volume of data generated by IoT devices requires robust infrastructure and protocols to ensure secure transmission, storage, and analysis.
As IoT continues to evolve, its impact on society, businesses, and daily life is expected to grow exponentially. Innovations in artificial intelligence (AI) and machine learning (ML) are further enhancing the capabilities of IoT devices, enabling them to learn and adapt to user behaviors and preferences.
In conclusion, IoT represents a paradigm shift in how we perceive and interact with technology. By connecting the physical and digital worlds in unprecedented ways, IoT has the potential to drive significant advancements in efficiency, productivity, and quality of life across various domains, ushering in a new era of connectivity and innovation.
What's the Right Messaging Standard for the IoT?



What's the Right Messaging Standard for the IoT?Angelo Corsaro Different messaging and data sharing standards, such as AMQP, CoAP, DDS, MQTT, and REST have been proposed as candidate for addressing the data sharing challenges of the Internet of Things (IoT) and the Industrial Internet (I2).
In technical forums and social media there is no lack of passionate discussions that praise the merits of one standard over the other. Yet, to date, there are little or perhaps no analysis that look at the details of the different standards and perform an in depth, qualitative, analytic and empirical evaluation.
This presentation, will (1) introduce the key standards that are being proposed for the Internet of Things and the Industrial Internet, such as AMQP, CoAP, DDS, MQTT and REST, (2) present a qualitative comparison that highlights the different features provided by the various standards, (3) present an analytic comparison looking at the efficiency and scalability of the various protocols and (3) report the results of an empirical evaluation comparing the actual performances of the various standards.
Ad
More Related Content
What's hot (20)
IoT Communication Protocols



IoT Communication ProtocolsPradeep Kumar TS This slide features the list of communication protocols that are suitable for Internet of things. It features from http to CoAP
Protocols for IoT



Protocols for IoTAravindhan G K This is a technical presentation describing two protocols namely MQTT and CoAP for IoT communications. This explains the protocols in conjunction with OSI layers.
IOT - Unit 3.pptx



IOT - Unit 3.pptxPallaviPatil580306 IP is the standard network layer protocol for IoT due to its advantages like being open, ubiquitous, scalable and manageable. However, optimizations are needed for IP in IoT due to constraints of nodes and networks. 6LoWPAN defines optimizations like header compression, fragmentation and mesh addressing to use IP in low power wireless networks. Profiles like Thread and certifications like IPv6 Ready Logo help ensure interoperability.
Wifi & 802.11 Standards



Wifi & 802.11 StandardsVipul Kumar Maurya Wi-Fi uses radio waves to transmit data through the air according to the IEEE 802.11 standards. It allows computers and other devices to connect to the internet and each other wirelessly. The 802.11 standards include 802.11b, 802.11a, 802.11g, 802.11n, and 802.11ac which provide different speeds and capabilities. Wi-Fi networks use access points, wireless cards, and security protocols like WEP, WPA, and WPA2 to transmit data securely between devices over short ranges.
Internet of Things - module 1



Internet of Things - module 1Syed Mustafa The document outlines a syllabus for an Internet of Things Technology course. It includes 5 modules that will be covered over the semester. Evaluation will consist of 3 internal assessments weighted at 30%, 40%, and 30% respectively, covering different portions of the syllabus. Students must attain a minimum of 85% attendance and assignments will be due before each internal assessment. The class website and online testing platform are also indicated.
WSN IN IOT



WSN IN IOTskumartarget This document discusses wireless sensor networks and their role in the Internet of Things. It defines sensor networks and their architecture, including sensor nodes that communicate wirelessly to a base station. It outlines challenges for sensor networks like fault tolerance, scalability, and quality of service. It also describes how sensor networks can be integrated into the Internet of Things through different approaches, with the first using a single gateway and later approaches using hybrid networks and access points. Applications of sensor networks in IoT include wearable devices collecting biometric data and communicating it to servers.
Business models for business processes on IoT



Business models for business processes on IoTFabMinds The document discusses business models for business processes on the Internet of Things. It covers key topics like IoT applications, business models, value creation using IoT, and business model scenarios for IoT. Business models need innovation to adapt to new customer access and interactions enabled by technologies like cloud computing and mobile communications. Value is created on IoT through addressing emergent needs, information convergence, and recurrent revenue from networked products. Example business model scenarios for IoT leverage data from multiple sources like sensors, M2M, and open data.
netconf and yang



netconf and yangpavan penugonda This chapter discusses systems management for IoT and introduces NETCONF and YANG as solutions. It notes the need for automated configuration, monitoring, reliability and reusable configurations for IoT systems management. It describes SNMP and its limitations. NETCONF is introduced as a session-based network management protocol using XML and YANG for data modeling. YANG is used to model configuration and state data for NETCONF. The chapter provides an example YANG module and discusses using NETCONF and YANG for IoT systems management.
489594658-Unit-III-Iot architecture.pptx



489594658-Unit-III-Iot architecture.pptxMBIEDANGOMEGNIFRANKG Very good lecture note on IoT Architecture
TCP/IP Network ppt



TCP/IP Network pptextraganesh The document provides an overview of the TCP/IP model, describing each layer from application to network. The application layer allows programs access to networked services and contains high-level protocols like TCP and UDP. The transport layer handles reliable delivery via protocols like TCP and UDP. The internet layer organizes routing with the IP protocol. The network layer consists of device drivers and network interface cards that communicate with the physical transmission media.
Components of IOT Implementation



Components of IOT ImplementationAashiq Ahamed N In this we are going to see about:-
Sensors
Networks
Standards
Intelligent Analysis
Intelligent Actions
IPv4



IPv4Dhiraj Mishra - The document discusses Internet Protocol (IP) which is the principal communications protocol for relaying datagrams across network boundaries. There are two major versions - IPv4 which is the dominant protocol, and IPv6 which is its successor.
- IPv4 uses 32-bit addresses divided into five classes (A, B, C, D, E). It allows for over 4 billion addresses but deficiencies in the classful addressing system led to address depletion.
- Classless addressing was introduced to overcome depletion by granting variable length address blocks defined by an IP address and network mask. This provides a hierarchical addressing structure and greater flexibility.
Mobile computing (Wireless) Medium Access Control (MAC)



Mobile computing (Wireless) Medium Access Control (MAC)Jyothishmathi Institute of Technology and Science Karimnagar Motivation for a specialized MAC (Hidden and exposed terminals, Near and far terminals), SDMA, FDMA, TDMA, CDMA, Wireless LAN/(IEEE 802.11)
Mobile Network Layer: IP and Mobile IP Network Layers, Packet Delivery and Handover Management, Location Management, Registration, Tunneling and Encapsulation, Route Optimization, DHCP
The constrained application protocol (CoAP)



The constrained application protocol (CoAP)Hamdamboy (함담보이) The Constrained Application Protocol (CoAP) is a RESTful web transfer protocol for resource-constrained networks and nodes. CoAP uses a simple binary message format carried over UDP that supports asynchronous messaging with optional message confirmation and retransmission. CoAP supports features like GET, POST, PUT, DELETE methods, URIs, content formats and codes that are similar to HTTP but optimized for constrained nodes and networks.
5G Security Briefing



5G Security Briefing3G4G A detailed look at 5G security by experts from wenovator, Dr. Anand R. Prasad & Hans Christian Rudolph.
This webinar covers:
(1) 5G security
(2) Private networks security and
(3) Open vRAN security
To learn more about wenovator, visit their website: https://www.wenovator.com/
All our #3G4G5G slides and videos are available at:
Videos: https://www.youtube.com/3G4G5G
Slides: https://www.slideshare.net/3G4GLtd
Security Page: https://www.3g4g.co.uk/Security/
5G Page: https://www.3g4g.co.uk/5G/
Security Blog Posts: https://blog.3g4g.co.uk/search/label/Security
Free Training Videos: https://www.3g4g.co.uk/Training/
Zigbee Presentation



Zigbee PresentationMaathu Michael zigbee is a new wireless technolgy Designed for low power consumption allowing batteries to essentially last for ever....
IOT PROTOCOLS.pptx



IOT PROTOCOLS.pptxDRREC This document discusses IoT protocols for data communication and connection models. It describes the key pillars of IoT protocols as being device, connectivity, data, and analytics. It also outlines various types of IoT data protocols like AMQP, DDS, XMPP, and WebSocket that establish end-to-end communication. Additionally, it covers IoT network protocols like Bluetooth, LPWANs, ZigBee, Z-Wave and others that facilitate secured communication between IoT devices over the internet.
Mobile Ad hoc Networks



Mobile Ad hoc NetworksJagdeep Singh Mobile ad hoc networks (MANETs) are formed spontaneously by wireless devices without any preexisting infrastructure. Nodes in a MANET are free to move and dynamically change the network topology. MANETs have applications in military operations, emergency response, education, and home/office use. Key challenges include dynamic topology, limited resources, and lack of centralized management. Media access control protocols address issues like hidden and exposed terminals. Routing protocols can be proactive (table-based) or reactive (on-demand) to find routes between nodes in the changing network.
Mobile Network Layer



Mobile Network LayerRahul Hada Mobile Network Layer protocols and mechanisms allow nodes to change their point of attachment to different networks while maintaining ongoing communication. Key concepts include:
- Mobile IP adds mobility support to IP, allowing nodes to use the same IP address even when changing networks. It relies on home agents and care-of addresses.
- Registration allows mobile nodes to inform their home agent of their current location when visiting foreign networks. Tunneling and encapsulation techniques are used to forward packets to mobile nodes' current locations.
- Various routing protocols like DSDV have been developed for mobile ad hoc networks which have no fixed infrastructure and dynamic topologies.
Mobile computing (Wireless) Medium Access Control (MAC)



Mobile computing (Wireless) Medium Access Control (MAC)Jyothishmathi Institute of Technology and Science Karimnagar
Similar to IoT Networking Part 2 (20)
lecture4week1iotnetworkingpart1-190114153249.pptx



lecture4week1iotnetworkingpart1-190114153249.pptxIshu Chaudhary The Internet of Things (IoT) represents a revolutionary concept in the realm of technology and connectivity. At its core, IoT refers to the network of physical devices, vehicles, home appliances, and other items embedded with sensors, software, and connectivity, enabling them to connect and exchange data over the internet.
The concept of IoT emerged from the convergence of multiple technologies, including wireless communication, micro-electromechanical systems (MEMS), and the internet itself. These advancements have allowed for the development of smart devices capable of collecting and transmitting data in real-time, creating opportunities for increased automation, efficiency, and even new business models across various sectors.
One of the defining characteristics of IoT is its ability to interconnect traditionally non-internet-enabled physical objects and allow them to communicate and interact with each other autonomously. This interconnectedness opens up vast possibilities for applications in industries such as healthcare, agriculture, transportation, manufacturing, and smart cities.
In healthcare, for example, IoT devices can monitor patients remotely, gather health data in real-time, and even enable predictive analytics to improve diagnostics and treatment outcomes. In agriculture, IoT sensors can monitor soil conditions, weather patterns, and crop health, leading to more efficient use of resources like water and fertilizers.
IoT also plays a crucial role in the development of smart homes and cities, where interconnected devices can enhance energy efficiency, automate household tasks, improve public safety through real-time monitoring, and optimize traffic flow and parking.
However, with the proliferation of IoT devices comes challenges related to security, privacy, interoperability, and data management. The sheer volume of data generated by IoT devices requires robust infrastructure and protocols to ensure secure transmission, storage, and analysis.
As IoT continues to evolve, its impact on society, businesses, and daily life is expected to grow exponentially. Innovations in artificial intelligence (AI) and machine learning (ML) are further enhancing the capabilities of IoT devices, enabling them to learn and adapt to user behaviors and preferences.
In conclusion, IoT represents a paradigm shift in how we perceive and interact with technology. By connecting the physical and digital worlds in unprecedented ways, IoT has the potential to drive significant advancements in efficiency, productivity, and quality of life across various domains, ushering in a new era of connectivity and innovation.
What's the Right Messaging Standard for the IoT?



What's the Right Messaging Standard for the IoT?Angelo Corsaro Different messaging and data sharing standards, such as AMQP, CoAP, DDS, MQTT, and REST have been proposed as candidate for addressing the data sharing challenges of the Internet of Things (IoT) and the Industrial Internet (I2).
In technical forums and social media there is no lack of passionate discussions that praise the merits of one standard over the other. Yet, to date, there are little or perhaps no analysis that look at the details of the different standards and perform an in depth, qualitative, analytic and empirical evaluation.
This presentation, will (1) introduce the key standards that are being proposed for the Internet of Things and the Industrial Internet, such as AMQP, CoAP, DDS, MQTT and REST, (2) present a qualitative comparison that highlights the different features provided by the various standards, (3) present an analytic comparison looking at the efficiency and scalability of the various protocols and (3) report the results of an empirical evaluation comparing the actual performances of the various standards.
Phoenix Data Conference - Big Data Analytics for IoT 11/4/17



Phoenix Data Conference - Big Data Analytics for IoT 11/4/17Mark Goldstein “Big Data for IoT: Analytics from Descriptive to Predictive to Prescriptive” was presented to the Phoenix Data Conference on 11/4/17 at Grand Canyon University.
As the Internet of Things (IoT) floods data lakes and fills data oceans with sensor and real-world data, analytic tools and real-time responsiveness will require improved platforms and applications to deal with the data flow and move from descriptive to predictive to prescriptive analysis and outcomes.
INTERNWT OF THINGS KHiuahjqilkjhJU HAUI JHJKQB HJAGE IUH OLJQHNORJ BQJ



INTERNWT OF THINGS KHiuahjqilkjhJU HAUI JHJKQB HJAGE IUH OLJQHNORJ BQJ150ROHITCHANDRASHEKH DGKMJIPOJFSDIK
Io t standard_bis_arpanpal



Io t standard_bis_arpanpalArpan Pal The document discusses the need for standardization in the Internet-of-Things (IoT). It notes that IoT involves a highly heterogeneous set of sensors, devices, and data that needs interoperability standards. It describes some existing standards for different IoT layers including networking, data formats, protocols, and interfaces. The document advocates for both syntactic and semantic interoperability standards and outlines Tata Consultancy Services' contributions to various standards bodies.
3G Wireless Access, Abstract



3G Wireless Access, AbstractVictoria Burke This document discusses digital security and the need for security measures when connecting corporate computer networks to the internet. It notes that internet-based technologies like VPNs, powerline communications, satellite communications, and wireless networks increasingly connect networks globally. However, more malicious actors are finding ways to infiltrate systems through technology. While the internet is essential, there are cybersecurity risks to consider. Digital security aims to protect digital identities and assets by implementing tools, policies, and procedures to secure technology and data in online and mobile environments.
COMPARATIVE STUDY BETWEEN VARIOUS PROTOCOLS USED IN INTERNET OF THING



COMPARATIVE STUDY BETWEEN VARIOUS PROTOCOLS USED IN INTERNET OF THINGIJTRET-International Journal of Trendy Research in Engineering and Technology Internet Of Things(IoT) is emerging technology in future world.The term IoT comprises of Cloud computing, Data mining,
Big data analytics, hardware board. The Security and Interoperability is a main factor that influences the IoT Enegy
consumption is also main fator for IoT application designing.The various protocols such as MQTT,AMQP,XMPP are used in
IoT.This paper analysis the various protocols used in Internet of Things.
Security And Privacy Issues Of Iots



Security And Privacy Issues Of IotsSamantha Randall The transport layer is responsible for host-to-host communication and provides services like reliable data transfer, flow control, and multiplexing. Common transport layer protocols include TCP and UDP, which provide connection-oriented and connectionless services respectively, and help applications exchange data over network layers. The transport layer sits above the network layer and below the application layer in network stacks.
Data Science for IoT



Data Science for IoTOlivera Kotevska, Ph.D. This document provides an overview of using data science techniques for analyzing Internet of Things (IoT) network traffic, using a smart home network as an example. It first discusses IoT systems, including components, communication protocols, and challenges. It then discusses how machine learning approaches like pattern detection, feature selection, and classification can be used to analyze IoT network traffic and behaviors. Specifically, it presents how these techniques could be applied in R and RStudio to a practical smart home network case study to better understand device interactions and identify anomalies.
Message-Oriented Middleware for Edge Computing Applications



Message-Oriented Middleware for Edge Computing ApplicationsThomas Rausch Edge computing is an emerging paradigm which aims to leverage the ever increasing amount of computational resources at the edge of the network to satisfy the stringent quality of service (QoS) requirements of many modern Internet of Things (IoT) scenarios. This PhD thesis explores challenges and solutions of message-oriented middleware (MOM) for edge computing applications. In particular, we focus on QoS optimization and message delivery guarantees under the constraints of geographic dispersion, client mobility, dynamic resource availability, and privacy policies.
NetSim Webinar on IOT



NetSim Webinar on IOTKAVITHA IYER This document provides an overview of a webinar on using the NetSim network simulation platform to model Internet of Things (IoT) scenarios. The webinar covers why network simulation is useful, an introduction to NetSim and its capabilities, key IoT technologies like 802.15.4 and 6LoWPAN, designing an IoT scenario in NetSim, analyzing simulation metrics, editing protocol code, and research areas in IoT. It also includes information on contacting the company for technical support or commercial inquiries.
IOT-Monograph .docx



IOT-Monograph .docxparveen837153 The document discusses Internet of Things (IoT) concepts including:
1. It defines IoT and describes its key characteristics such as being dynamic, self-configuring, using interoperable communication protocols, and devices having unique identities.
2. It explains the physical and logical design of IoT including things in IoT, IoT protocols, functional blocks, and communication models and APIs.
3. It discusses enabling technologies for IoT like wireless sensor networks, cloud computing, big data analytics, embedded systems, and communication protocols.
The document provides a detailed overview of foundational aspects of IoT from definitions to enabling technologies.
SYSTEM SECURITY - Chapter 1 introduction



SYSTEM SECURITY - Chapter 1 introductionAfna Crcs This document discusses the history of technology and consumer markets from the 1980s to present day. It covers the evolution of internet access from dial-up modems to always-on broadband connections. It describes the transition to home networks connecting various devices and the development of triple play services. The document also provides examples of network infrastructure including residential gateways and broadband termination units.
F2CDM: Internet of Things for Healthcare Network Based Fog-to-Cloud and Data-...



F2CDM: Internet of Things for Healthcare Network Based Fog-to-Cloud and Data-...Istabraq M. Al-Joboury Internet of Things (IoT) evolves very rapidly over time, since everything such as sensors/actuators linked together from around the world with use of evolution of ubiquitous computing through the Internet. These devices have a unique IP address in order to communicate with each other and transmit data with features of wireless technologies. Fog computing or so called edge computing brings all Cloud features to embedded devices at edge network and adds more features to servers like pre-store data of Cloud, fast response, and generate overhasty users reporting. Fog mediates between Cloud and IoT devices and thus enables new types of computing and services. The future applications take the advantage of combing the two concepts Fog and Cloud in order to provide low delay Fog-based and high capacity of storage Cloud-based. This paper proposes an IoT architecture for healthcare network based on Fog to Cloud and Data in Motion (F2CDM). The proposed architecture is designed and implemented over three sites: Site 1 contains the embedded devices layer, Site 2 consists of the Fog network layer, while Site 3 consists of the Cloud network. The Fog layer is represented by a middleware server in Al-Nahrain University with temporary storage such that the data lives inside for 30 min. During this time, the selection of up-normality in behavior is send to the Cloud while the rest of the data is wiped out. On the other hand, the Cloud stores all the incoming data from Fog permanently. The F2CDM works using Message Queue Telemetry Transport (MQTT) for fast response. The results show that all data can be monitored from the Fog in real time while the critical data can be monitored from Cloud. In addition, the response time is evaluated using traffic generator called Tsung. It has been found that the proposed architecture reduces traffic on Cloud network and provides better data analysis.
15CS81- IoT- VTU- module 3



15CS81- IoT- VTU- module 3Syed Mustafa The document discusses optimizing IP for use in Internet of Things networks. It covers several key topics:
- The advantages of using IP, including its open standards, versatility, ubiquity, scalability, manageability, and role in enabling innovation.
- The need to optimize IP for constrained IoT nodes with limited resources, as well as challenges around unreliable connectivity, power consumption, and bandwidth constraints.
- Classifying IoT nodes based on their constraints and whether they use a full IP stack, optimized IP stack, or non-IP stack with gateways for connectivity.
- Considerations for the IP adoption model of replacing non-IP layers versus the adaptation model of implementing application gateways between IP and
Unify Internet Of Things with Clayster



Unify Internet Of Things with Claysterclaysterworld We provide platforms and frameworks for rapid development to unify Everything on the Internet for innovations to be created. Our customers has chosen our technology to be on the edge into the future of Internet. The future of Internet is not about a single technology or protocol, but to make them coexist.
Lecture 01 {Introduction}.pptx



Lecture 01 {Introduction}.pptxSurendraBasnet6 The document outlines the objectives and course outline for a class on data communication and computer networks. The general objectives are to familiarize students with conceptual aspects of data communication and computer networks. Specific objectives include understanding the OSI and TCP/IP models, the layers of the OSI model, and network management and security issues. The course outline covers topics like the application layer, transport layer, network layer, data link layer, physical layer, and network management and security over seven units.
Da3210751081



Da3210751081IJMER This document discusses the transition from IPv4 to IPv6. It provides background on why IPv6 was developed, noting that IPv4 addresses were being depleted and IPv6 expands the address space from 32 to 128 bits. It summarizes three main transition strategies: dual stack, tunneling, and translation. The document warns that tunneling IPv6 packets inside IPv4 packets could allow hidden IPv6 traffic and security issues if deep packet inspection is not used. Overall it emphasizes that a gradual transition combining techniques will be needed to migrate from the current IPv4 internet to an IPv6 internet.
October Southern CA Road Shows - Build Safe and Secure Distributed Systems



October Southern CA Road Shows - Build Safe and Secure Distributed SystemsReal-Time Innovations (RTI) This document discusses using the Data Distribution Service (DDS) and RTI Connext DDS for building scalable, distributed systems for the Industrial Internet of Things (IIoT). DDS provides data-centric publish-subscribe communication that supports real-time integration of sensors, controllers and applications. It enables seamless data sharing across networks, platforms and locations. RTI is a leading provider of DDS middleware and has experience integrating DDS into large industrial and military systems.
Catching the Internet of Things (IoT) Wave



Catching the Internet of Things (IoT) WaveChuck Petras The document discusses various topics related to Internet of Things (IoT) systems, including definitions of IoT, the types of connected devices, connectivity options, and software and hardware considerations for IoT devices. It provides examples of memory requirements and processor selections for IoT applications. Key networking technologies like TCP/IP, WiFi, Bluetooth, and different software architectures for IoT devices are also examined.
COMPARATIVE STUDY BETWEEN VARIOUS PROTOCOLS USED IN INTERNET OF THING



COMPARATIVE STUDY BETWEEN VARIOUS PROTOCOLS USED IN INTERNET OF THINGIJTRET-International Journal of Trendy Research in Engineering and Technology
F2CDM: Internet of Things for Healthcare Network Based Fog-to-Cloud and Data-...



F2CDM: Internet of Things for Healthcare Network Based Fog-to-Cloud and Data-...Istabraq M. Al-Joboury
October Southern CA Road Shows - Build Safe and Secure Distributed Systems



October Southern CA Road Shows - Build Safe and Secure Distributed SystemsReal-Time Innovations (RTI)
Ad
More from Hitesh Mohapatra (20)
Introduction to Edge and Fog Computing.pdf



Introduction to Edge and Fog Computing.pdfHitesh Mohapatra Edge computing and fog computing can both be defined as technological platforms that bring computing processes closer to where data is generated and collected from. This article explains the two concepts in detail and lists the similarities and differences between them.
Amazon Web Services (AWS) : Fundamentals



Amazon Web Services (AWS) : FundamentalsHitesh Mohapatra Amazon Web Services (AWS) is a popular cloud platform praised for its scalability, flexibility, and extensive range of services, making it a good choice for businesses of all sizes.
Resource Cluster and Multi-Device Broker.pdf



Resource Cluster and Multi-Device Broker.pdfHitesh Mohapatra In cloud computing, a "Resource Cluster" refers to a group of multiple computing resources (like servers, storage units) managed as a single entity to provide high availability and scalability, while a "Multi-Device Broker" acts as a intermediary that translates data formats and protocols to enable a cloud service to be accessed by a wide range of devices, even if they have different capabilities or communication standards; essentially acting as a compatibility layer between the cloud service and various client devices.
Failover System in Cloud Computing System



Failover System in Cloud Computing SystemHitesh Mohapatra Uses established clustering technologies for redundancy
Boosts availability and reliability of IT resources
Automatically transitions to standby instances when active resources become unavailable
Protects mission-critical software and reusable services from single points of failure
Can cover multiple geographical areas
Hosts redundant implementations of the same IT resource at each location
Relies on resource replication for monitoring defects and unavailability conditions
Resource Replication & Automated Scaling Listener



Resource Replication & Automated Scaling ListenerHitesh Mohapatra In cloud computing, "Resource Replication" refers to the process of creating multiple identical copies of a computing resource (like a server or database) to enhance availability and fault tolerance, while an "Automated Scaling Listener" is a service agent that constantly monitors workload demands and automatically triggers the creation or deletion of these replicated resources based on predefined thresholds, essentially allowing for dynamic scaling of applications to meet fluctuating traffic needs.
Storage Device & Usage Monitor in Cloud Computing.pdf



Storage Device & Usage Monitor in Cloud Computing.pdfHitesh Mohapatra A "Storage Device & Usage Monitor" in cloud computing refers to a tool or feature that tracks and analyzes the performance and usage of storage devices within a cloud infrastructure, providing insights into metrics like disk space utilization, read/write speeds, data access patterns, and potential storage bottlenecks, allowing administrators to optimize data storage and manage capacity effectively.
Networking in Cloud Computing Environment



Networking in Cloud Computing EnvironmentHitesh Mohapatra Cloud networking is the use of cloud-based services to connect an organization's resources, applications, and employees. It's a type of IT infrastructure that allows organizations to use virtual network components instead of physical hardware.
Uniform-Cost Search Algorithm in the AI Environment



Uniform-Cost Search Algorithm in the AI EnvironmentHitesh Mohapatra Uniform Cost Search (UCS) is a popular search algorithm used in artificial intelligence (AI) for finding the least cost path in a graph.
Logical Network Perimeter in Cloud Computing



Logical Network Perimeter in Cloud ComputingHitesh Mohapatra A logical network perimeter in cloud computing is a virtual boundary that separates a group of cloud-based IT resources from the rest of the network. It can be used to isolate resources from unauthorized users, control bandwidth, and more.
Software Product Quality - Part 1 Presentation



Software Product Quality - Part 1 PresentationHitesh Mohapatra Software product quality is how well a software product meets the needs of its users and developers. It's important to ensure high quality software, especially for safety-critical applications.
Multitenancy in cloud computing architecture



Multitenancy in cloud computing architectureHitesh Mohapatra Multitenancy in cloud computing is a software architecture that allows multiple customers to share a single cloud instance. In this model, each customer, or tenant, has their own secure virtual application instance, even though they share the same resources.
Server Consolidation in Cloud Computing Environment



Server Consolidation in Cloud Computing EnvironmentHitesh Mohapatra Server consolidation in cloud computing refers to the practice of reducing the number of physical servers by combining workloads onto fewer, more powerful virtual machines or cloud instances. This approach improves resource utilization, reduces operational costs, and enhances scalability while maintaining performance and reliability in cloud environments.
Web Services / Technology in Cloud Computing



Web Services / Technology in Cloud ComputingHitesh Mohapatra Web services in cloud computing are technologies that enable communication between different applications over the internet using standard protocols like HTTP, XML, or JSON. They allow systems to access and exchange data remotely, enabling seamless integration, scalability, and flexibility in cloud-based environments.
Resource replication in cloud computing.



Resource replication in cloud computing.Hitesh Mohapatra Resource replication in cloud computing is the process of making multiple copies of the same resource. It's done to improve the availability and performance of IT resources.
Software Measurement and Metrics (Quantified Attribute)



Software Measurement and Metrics (Quantified Attribute)Hitesh Mohapatra Software measurement is a titrate impute of a characteristic of a software product or the software process.
Software project management is an art and discipline of planning and supervis...



Software project management is an art and discipline of planning and supervis...Hitesh Mohapatra Software in project management is dedicated to the planning, scheduling, resource allocation, execution, tracking, and delivery of software and web projects.
Part 2
Software project management is an art and discipline of planning and supervis...



Software project management is an art and discipline of planning and supervis...Hitesh Mohapatra Software in project management is dedicated to the planning, scheduling, resource allocation, execution, tracking, and delivery of software and web projects.
Part 1
The life cycle of a virtual machine (VM) provisioning process



The life cycle of a virtual machine (VM) provisioning processHitesh Mohapatra The life cycle of a virtual machine (VM) provisioning process includes the following stages:
Creation: The VM is created
Configuration: The VM is configured in a development environment
Allocation: Virtual resources are allocated
Exploitation and monitoring: The VM is used and its status is monitored
Elimination: The VM is eliminated
BUSINESS CONSIDERATIONS FOR CLOUD COMPUTING



BUSINESS CONSIDERATIONS FOR CLOUD COMPUTINGHitesh Mohapatra BUSINESS CONSIDERATIONS FOR CLOUD COMPUTING
Traditional Data Center vs. Virtualization – Differences and Benefits



Traditional Data Center vs. Virtualization – Differences and BenefitsHitesh Mohapatra Traditional Data Center vs. Virtualization – Differences and Benefits
Ad
Recently uploaded (20)
Structural Response of Reinforced Self-Compacting Concrete Deep Beam Using Fi...



Structural Response of Reinforced Self-Compacting Concrete Deep Beam Using Fi...Journal of Soft Computing in Civil Engineering Analysis of reinforced concrete deep beam is based on simplified approximate method due to the complexity of the exact analysis. The complexity is due to a number of parameters affecting its response. To evaluate some of this parameters, finite element study of the structural behavior of the reinforced self-compacting concrete deep beam was carried out using Abaqus finite element modeling tool. The model was validated against experimental data from the literature. The parametric effects of varied concrete compressive strength, vertical web reinforcement ratio and horizontal web reinforcement ratio on the beam were tested on eight (8) different specimens under four points loads. The results of the validation work showed good agreement with the experimental studies. The parametric study revealed that the concrete compressive strength most significantly influenced the specimens’ response with the average of 41.1% and 49 % increment in the diagonal cracking and ultimate load respectively due to doubling of concrete compressive strength. Although the increase in horizontal web reinforcement ratio from 0.31 % to 0.63 % lead to average of 6.24 % increment on the diagonal cracking load, it does not influence the ultimate strength and the load-deflection response of the beams. Similar variation in vertical web reinforcement ratio leads to an average of 2.4 % and 15 % increment in cracking and ultimate load respectively with no appreciable effect on the load-deflection response.
Compiler Design Unit1 PPT Phases of Compiler.pptx



Compiler Design Unit1 PPT Phases of Compiler.pptxRushaliDeshmukh2 Compiler phases
Lexical analysis
Syntax analysis
Semantic analysis
Intermediate (machine-independent) code generation
Intermediate code optimization
Target (machine-dependent) code generation
Target code optimization
Level 1-Safety.pptx Presentation of Electrical Safety



Level 1-Safety.pptx Presentation of Electrical SafetyJoseAlbertoCariasDel Level 1-Safety.pptx Presentation of Electrical Safety
The Gaussian Process Modeling Module in UQLab



The Gaussian Process Modeling Module in UQLabJournal of Soft Computing in Civil Engineering We introduce the Gaussian process (GP) modeling module developed within the UQLab software framework. The novel design of the GP-module aims at providing seamless integration of GP modeling into any uncertainty quantification workflow, as well as a standalone surrogate modeling tool. We first briefly present the key mathematical tools on the basis of GP modeling (a.k.a. Kriging), as well as the associated theoretical and computational framework. We then provide an extensive overview of the available features of the software and demonstrate its flexibility and user-friendliness. Finally, we showcase the usage and the performance of the software on several applications borrowed from different fields of engineering. These include a basic surrogate of a well-known analytical benchmark function; a hierarchical Kriging example applied to wind turbine aero-servo-elastic simulations and a more complex geotechnical example that requires a non-stationary, user-defined correlation function. The GP-module, like the rest of the scientific code that is shipped with UQLab, is open source (BSD license).
"Boiler Feed Pump (BFP): Working, Applications, Advantages, and Limitations E...



"Boiler Feed Pump (BFP): Working, Applications, Advantages, and Limitations E...Infopitaara A Boiler Feed Pump (BFP) is a critical component in thermal power plants. It supplies high-pressure water (feedwater) to the boiler, ensuring continuous steam generation.
⚙️ How a Boiler Feed Pump Works
Water Collection:
Feedwater is collected from the deaerator or feedwater tank.
Pressurization:
The pump increases water pressure using multiple impellers/stages in centrifugal types.
Discharge to Boiler:
Pressurized water is then supplied to the boiler drum or economizer section, depending on design.
🌀 Types of Boiler Feed Pumps
Centrifugal Pumps (most common):
Multistage for higher pressure.
Used in large thermal power stations.
Positive Displacement Pumps (less common):
For smaller or specific applications.
Precise flow control but less efficient for large volumes.
🛠️ Key Operations and Controls
Recirculation Line: Protects the pump from overheating at low flow.
Throttle Valve: Regulates flow based on boiler demand.
Control System: Often automated via DCS/PLC for variable load conditions.
Sealing & Cooling Systems: Prevent leakage and maintain pump health.
⚠️ Common BFP Issues
Cavitation due to low NPSH (Net Positive Suction Head).
Seal or bearing failure.
Overheating from improper flow or recirculation.
ADVXAI IN MALWARE ANALYSIS FRAMEWORK: BALANCING EXPLAINABILITY WITH SECURITY



ADVXAI IN MALWARE ANALYSIS FRAMEWORK: BALANCING EXPLAINABILITY WITH SECURITYijscai With the increased use of Artificial Intelligence (AI) in malware analysis there is also an increased need to
understand the decisions models make when identifying malicious artifacts. Explainable AI (XAI) becomes
the answer to interpreting the decision-making process that AI malware analysis models use to determine
malicious benign samples to gain trust that in a production environment, the system is able to catch
malware. With any cyber innovation brings a new set of challenges and literature soon came out about XAI
as a new attack vector. Adversarial XAI (AdvXAI) is a relatively new concept but with AI applications in
many sectors, it is crucial to quickly respond to the attack surface that it creates. This paper seeks to
conceptualize a theoretical framework focused on addressing AdvXAI in malware analysis in an effort to
balance explainability with security. Following this framework, designing a machine with an AI malware
detection and analysis model will ensure that it can effectively analyze malware, explain how it came to its
decision, and be built securely to avoid adversarial attacks and manipulations. The framework focuses on
choosing malware datasets to train the model, choosing the AI model, choosing an XAI technique,
implementing AdvXAI defensive measures, and continually evaluating the model. This framework will
significantly contribute to automated malware detection and XAI efforts allowing for secure systems that
are resilient to adversarial attacks.
fluke dealers in bangalore..............



fluke dealers in bangalore..............Haresh Vaswani The Fluke 925 is a vane anemometer, a handheld device designed to measure wind speed, air flow (volume), and temperature. It features a separate sensor and display unit, allowing greater flexibility and ease of use in tight or hard-to-reach spaces. The Fluke 925 is particularly suitable for HVAC (heating, ventilation, and air conditioning) maintenance in both residential and commercial buildings, offering a durable and cost-effective solution for routine airflow diagnostics.
Data Structures_Linear data structures Linked Lists.pptx



Data Structures_Linear data structures Linked Lists.pptxRushaliDeshmukh2 Concept of Linear Data Structures, Array as an ADT, Merging of two arrays, Storage
Representation, Linear list – singly linked list implementation, insertion, deletion and searching operations on linear list, circularly linked lists- Operations for Circularly linked lists, doubly linked
list implementation, insertion, deletion and searching operations, applications of linked lists.
AI-assisted Software Testing (3-hours tutorial)



AI-assisted Software Testing (3-hours tutorial)Vəhid Gəruslu Invited tutorial at the Istanbul Software Testing Conference (ISTC) 2025 https://iststc.com/
How to use nRF24L01 module with Arduino



How to use nRF24L01 module with ArduinoCircuitDigest Learn how to wirelessly transmit sensor data using nRF24L01 and Arduino Uno. A simple project demonstrating real-time communication with DHT11 and OLED display.
DATA-DRIVEN SHOULDER INVERSE KINEMATICS YoungBeom Kim1 , Byung-Ha Park1 , Kwa...



DATA-DRIVEN SHOULDER INVERSE KINEMATICS YoungBeom Kim1 , Byung-Ha Park1 , Kwa...charlesdick1345 This paper proposes a shoulder inverse kinematics (IK) technique. Shoulder complex is comprised of the sternum, clavicle, ribs, scapula, humerus, and four joints.
Lidar for Autonomous Driving, LiDAR Mapping for Driverless Cars.pptx



Lidar for Autonomous Driving, LiDAR Mapping for Driverless Cars.pptxRishavKumar530754 LiDAR-Based System for Autonomous Cars
Autonomous Driving with LiDAR Tech
LiDAR Integration in Self-Driving Cars
Self-Driving Vehicles Using LiDAR
LiDAR Mapping for Driverless Cars
Compiler Design_Lexical Analysis phase.pptx



Compiler Design_Lexical Analysis phase.pptxRushaliDeshmukh2 The role of the lexical analyzer
Specification of tokens
Finite state machines
From a regular expressions to an NFA
Convert NFA to DFA
Transforming grammars and regular expressions
Transforming automata to grammars
Language for specifying lexical analyzers
Structural Response of Reinforced Self-Compacting Concrete Deep Beam Using Fi...



Structural Response of Reinforced Self-Compacting Concrete Deep Beam Using Fi...Journal of Soft Computing in Civil Engineering
IoT Networking Part 2
- 1. 1 Introduction: IoT Networking - Part 2 Dr. Sudip Misra Professor Department of Computer Science and Engineering Indian Institute of Technology Kharagpur Email: [email protected] Website: http://cse.iitkgp.ac.in/~smisra/ Research Lab: cse.iitkgp.ac.in/~smisra/swan/ Industry 4.0 and Industrial Internet of Things
- 2. Requirements of IoT Network Coverage High throughput Low latency Ultra reliability High power efficiency 2Industry 4.0 and Industrial Internet of Things
- 3. 3Industry 4.0 and Industrial Internet of Things MQTT
- 4. MQTT Message Queue Telemetry Transport Introduced by IBM and standardized by Organization for the Advancement of Structured Information Standards (OASIS) in 2013 Works on Publish/Subscribe framework on top of TCP/IP architecture Advantages Reliable, Lightweight, and cost-effective protocol 4Industry 4.0 and Industrial Internet of Things
- 5. MQTT Publish/Subscribe Framework 5Industry 4.0 and Industrial Internet of Things Source: Hanes, D, et al. (2017), "IoT Fundamentals: Networking Technologies, Protocols, and Use Cases for the Internet of Things", Cisco Press.
- 6. MQTT QoS QoS of MQTT protocol is maintained for two transactions First transaction: Publishing client MQTT Server Second transaction: MQTT Server Subscribing Client Client on each transaction sets the QoS level For the first transaction, publishing client sets the QoS level For second transaction, client subscriber sets the QoS level 6Industry 4.0 and Industrial Internet of Things Source: Hanes, D, et al. (2017), "IoT Fundamentals: Networking Technologies, Protocols, and Use Cases for the Internet of Things", Cisco Press.
- 7. MQTT QoS Levels Supports 3-level of QoS QoS 0: Also known as “at most once” delivery Best effort and unacknowledged data service Publisher transmits the message one time to server and server transmits it once to subscriber No retry is performed 7Industry 4.0 and Industrial Internet of Things Source: Hanes, D, et al. (2017), "IoT Fundamentals: Networking Technologies, Protocols, and Use Cases for the Internet of Things", Cisco Press.
- 8. MQTT QoS Levels QoS 1: Also known as “at least once” delivery Message delivery between the publisher, server and then between server and subscribers occurs at least once. Retry is performed until acknowledgement of message is recieved QoS 2: Also known as “exactly once” delivery This QoS level is used when neither packet loss or duplication of message is allowed Retry is performed until the message is delivered exactly once 8Industry 4.0 and Industrial Internet of Things
- 9. 9Industry 4.0 and Industrial Internet of Things CoAP
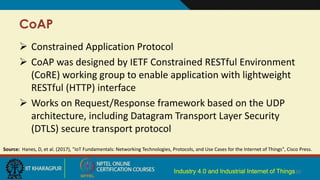
- 10. CoAP Constrained Application Protocol CoAP was designed by IETF Constrained RESTful Environment (CoRE) working group to enable application with lightweight RESTful (HTTP) interface Works on Request/Response framework based on the UDP architecture, including Datagram Transport Layer Security (DTLS) secure transport protocol 10Industry 4.0 and Industrial Internet of Things Source: Hanes, D, et al. (2017), "IoT Fundamentals: Networking Technologies, Protocols, and Use Cases for the Internet of Things", Cisco Press.
- 11. CoAP CoAP defines four types of messages CON: Conformable NON: Non-conformable RST: Reset ACK: Acknowledgement For conformable type message, the recipient must explicitly either acknowledge or reject the message. In case of non-conformable type message, the recipient sends reset message if it can’t process the message. 11Industry 4.0 and Industrial Internet of Things Source: Hanes, D, et al. (2017), "IoT Fundamentals: Networking Technologies, Protocols, and Use Cases for the Internet of Things", Cisco Press.
- 12. CoAP Utilizes GET, PUT, OBSERVE, PUSH, and DELETE messages requests to retrieve, create, initiate, update, and delete subscription respectively. Supports caching capabilities to improve the response time and reduce bandwidth consumption. Uses IP multicast to support data requests sent to a group of devices. Specialized for machine-to-machine (M2M) communication. 12Industry 4.0 and Industrial Internet of Things Source: Hanes, D, et al. (2017), "IoT Fundamentals: Networking Technologies, Protocols, and Use Cases for the Internet of Things", Cisco Press.
- 13. 13Industry 4.0 and Industrial Internet of Things XMPP
- 14. XMPP Extensible Messaging and Presence Protocol Supports Publish/Subscribe messaging framework on top of TCP protocol The communication protocol is based on Extensive Markup Language (XML). Uses Datagram Transport Layer Security (DTLS) secure transport protocol 14Industry 4.0 and Industrial Internet of Things Source: Rayes, A., & Salam, S. (2016), "Internet of Things from hype to reality: the road to digitization", Springer.
- 15. XMPP XMPP model is decentralized, no central server is required. Advantages of XMPP Interoperability: Supports interoperability between heterogeneous networks Extensibility: Supports privacy lists, multi-user chat, and publish/subscribe chat status notifications Flexibility: Supports customized markup language defined by different organizations according to their needs 15Industry 4.0 and Industrial Internet of Things Source: H. Wang et. al., "A Lightweight XMPP Publish/Subscribe Scheme for Resource-Constrained IoT Devices," IEEE Access, vol. 5, pp. 16393-16405, 2017.
- 16. 16Industry 4.0 and Industrial Internet of Things AMQP
- 17. AMQP Advance Message Queuing Protocol Optimized for financial applications Binary message-oriented protocol on top of TCP Supports Publish/Subscribe framework for both Point-to-point (P2P) Multipoint communication 17Industry 4.0 and Industrial Internet of Things Source: Rayes, A., & Salam, S. (2016), "Internet of Things from hype to reality: the road to digitization", Springer.
- 18. AMQP Uses token-based mechanism for flow control Ensures no buffer overflow at the receiving end Message delivery guarantee services: At least once: Guarantees message delivery but may do so multiple times At most once: Each message is delivered once or never Exactly once: No message drop and delivered once one 18Industry 4.0 and Industrial Internet of Things Source: Rayes, A., & Salam, S. (2016), "Internet of Things from hype to reality: the road to digitization", Springer.
- 19. 19Industry 4.0 and Industrial Internet of Things IEEE 1888
- 20. IEEE 1888 Energy-efficient network control protocol Defines a generalized data exchange protocol between network components over the IPv4/v6-based network. Universal Resource Identifiers (URIs) based data identification Applications: Environmental monitoring, energy saving, and central management systems. 20Industry 4.0 and Industrial Internet of Things Source: Rayes, A., & Salam, S. (2016), "Internet of Things from hype to reality: the road to digitization", Springer.
- 21. 21Industry 4.0 and Industrial Internet of Things DDS RTPS
- 22. DDS RTPS Distributed Data Service Real Time Publish and Subscribe Supports Publish/Subscribe framework and on top of UDP transport layer protocol. Data-centric and binary protocol Data is termed as “topics”. The users/listeners may subscribe to their particular topic of interest 22Industry 4.0 and Industrial Internet of Things Source: Rayes, A., & Salam, S. (2016), "Internet of Things from hype to reality: the road to digitization", Springer.
- 23. DDS RTPS A single topic may have multiple speakers of different priorities Supports enlisted QoS for data distribution Data persistence Delivery deadline Reliability Data freshness Applications: Military, Industrial, and healthcare monitoring 23Industry 4.0 and Industrial Internet of Things Source: Rayes, A., & Salam, S. (2016), "Internet of Things from hype to reality: the road to digitization", Springer.
- 24. 24Introduction to Internet of Things








