IT Camp 19: Top Azure security fails and how to avoid them
- 1. @ITCAMPRO #ITCAMP19Community Conference for IT Professionals Top Azure security fails and how to avoid them Karl Ots
- 2. @ITCAMPRO #ITCAMP19Community Conference for IT Professionals Many thanks to our sponsors & partners! GOLD SILVER PARTNERS PLATINUM POWERED BY
- 3. @fincooper Karl Ots Chief Consulting Officer [email protected] • Cloud & cybersecurity expert • Community leader, speaker, author & patented inventor • Working on Azure since 2011 • Helped to secure 100+ Azure applications, from startups to Fortune 500 enterprises • zure.ly/karl
- 4. @fincooper 13,7 100% 4,5 / 5 3 6. 34 / 38 experts years avg. Azure satisfaction Azure MVPs GPTW
- 5. @fincooper What to expect in this session • Azure security landscape • Top Azure security fails I have wandered upon in my adventures • Why are they bad? • How to fix them? • Resources to help you secure your Azure environment, regardless of your current status
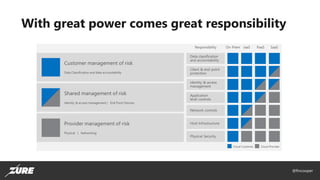
- 6. @fincooper With great power comes great responsibility
- 7. @fincooper Secure DevOps kit for Azure (AzSK) • Set of tools for assessing the security posture of your Azure environment • Main toolset includes PowerShell module to scan your Azure platform and resources against best practices from Microsoft Core Services Engineering • Easy to get started with non-intrusive platform scans, expands end-to-end tooling from developer machine to DevSecOps
- 8. @fincooper Secure DevOps kit for Azure (AzSK) Run AzSK PowerShell tool Analyze results Improve system security
- 9. @fincooper Most fails described in this session can be detected by using AzSK
- 10. @fincooper Role Based Access Control AAD Object Role Scope RBAC Assignment
- 11. @fincooper Role-Based Access Control Subscription Resource Groups Resources Owner Can perform all management operations for a resource and its child resources including access management and granting access to others. Contributor Can perform all management operations for a resource including create and delete resources. A contributor cannot grant access to other. Reader Has read-only access to a resource and its child resources. A reader cannot read secrets.
- 12. @fincooper RBAC Roles • A collection of actions • Microsoft.Compute/virtualMachines/* • Microsoft.Compute/virtualMachines/start/action • Microsoft.Network/virtualNetworks/read • +70 built-in roles for Azure RBAC • e.g. Virtual Machine Contributor, Backup Contributor, Security Reader, etc.
- 13. @fincooper Security fail #1 • Unprotected public endpoints • HTTP / RDP / SSH • Mitigation: • Every public IP is a risk and should be carefully reviewed • Use Network Security Groups to control access to / from virtual machines • Use Azure Security Center’s Just-in-time access to dynamically change NSG rules • Use Web Application Firewall to control access to public HTTP endpoints • Configure Service Endpoint Firewalls for PaaS services • AzSK Control ID: • Azure_Subscription_NetSec_Justify_PublicIPs
- 14. @fincooper
- 15. @fincooper Security fail #2 • Every user is an Owner • …In the Subscription scope • Mitigation: • Default access scope should be Resource Group, not Subscription • Default RBAC access should be Contributor, not Owner • Instead of Owner, use User Access Administrator • AzSK Control ID: • Azure_Subscription_AuthZ_Justify_Admins_Owners
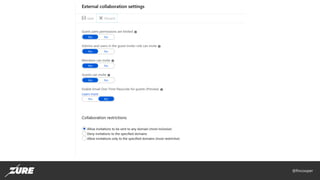
- 16. @fincooper Security fail #3 • Untrusted authentication provider being used • (Microsoft Account, Gmail, unmanaged or external Azure AD…) • Mitigation: • Always use trusted Azure AD authentication • Monitor Azure Subscription access using AAD PIM • If necessary, limit AAD Guest user inviting • AzSK control ID: • Azure_Subscription_AuthZ_Dont_Use_NonAD_Identities
- 17. @fincooper
- 18. @fincooper Security fail #4 • Storage access keys used directly • Mitigation: • Storage Access Keys should be stored in Azure Key Vault and rotated programmatically • Use data pane RBAC roles (new) • Restrict access to Microsoft.Storage/storageAccounts/listkeys/action using RBAC • AzSK control ID: • Azure_Storage_DP_Rotate_Keys
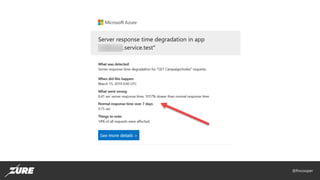
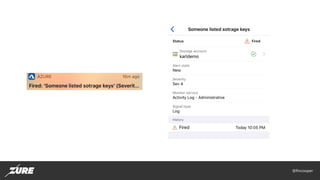
- 19. @fincooper Security fail #5 • Insufficient monitoring and alerting • Mitigation: • Configure Activity Log retention, default is only 90 days! • Enable Azure SQL Audit logging • Monitor all HTTP endpoint traffic with Application Gateway / Web Application Firewall • Enable Application Insight Smart Alerts • Enable Advanced Treat Protection for Azure SQL and Storage Accounts • Enable Service Health Alerts • Enable custom Activity Log Alerts • AzSK control ID’s • Azure_AppService_Configure_Important_Alerts • Azure_Subscription_Config_Azure_Security_Center • Azure_SQLDatabase_Audit_Enable_Threat_Detection_Server
- 20. @fincooper Storage Advanced Threat Protection Access from unusual location Application Anomaly Anonymous access Data Exfiltration Unexpected delete Upload Azure Cloud Service package Access permission change Access Inspection Data Exploration
- 21. @fincooper
- 22. @fincooper
- 23. @fincooper
- 24. @fincooper
- 25. @fincooper Security fail #6 • No network controls for PaaS storage • Mitigation: • Enable Firewall for your storage layer services • When using SAS tokens, enable IP restriction • AzSK Control ID’s: • Azure_CosmosDB_AuthZ_Enable_Firewall • Azure_SQLDatabase_AuthN_Dont_Use_SQL_AuthN • Azure_DataLakeStore_AuthZ_Enable_Firewall
- 26. @fincooper
- 27. @fincooper
- 28. @fincooper Secure DevOps kit for Azure (AzSK) • Set of tools for assessing the security posture of your Azure environment • Built by Microsoft Core Services Engineering • Used to secure 1000+ Azure subscriptions at Microsoft • Easy to get started with non-intrusive vulnerability scans, expands end-to- end tooling from developer machine to CI/CD to continuous assurance • Call to action: Use AzSK to scan your environment for security fails!
- 29. @fincooper Resources • My slides: zure.ly/karl/slides • Secure DevOps Kit for Azure: • azsk.azurewebsites.net • Microsoft Ignite 2018 session THR2104 Assess your Microsoft Azure security like a pro: • zure.ly/karl/THR2104 • Whitepaper: Develop Secure Applications on Azure: • zure.ly/karl/secureapps
- 30. @ITCAMPRO #ITCAMP19Community Conference for IT Professionals Q & A