IT103Microsoft Windows XP/OS Chap11
- 1. CONFIGURING TCP/IP ADDRESSING AND SECURITY Chapter 11
- 2. OVERVIEW Understand IP addressing Manage IP subnetting and subnet masks Understand IP security terminology Manage Internet security features of Windows XP Configure and troubleshoot Windows Firewall Chapter 11: CONFIGURING TCP/IP ADDRESSING AND SECURITY
- 3. Overview - 2 This chapter addresses advanced TCP/IP addressing and Internet security. It introduces students to classless interdomain routing (CIDR) subnetting and subnet masks, and it explores the binary nature of IP addresses and the knowledge necessary to troubleshoot addressing issues. We will also introduce Windows XP Internet security features such as Windows Firewall. Proper configuration and operation of Windows Firewall can protect systems inexpensively. Chapter 11: CONFIGURING TCP/IP ADDRESSING AND SECURITY
- 4. UNDERSTANDING BINARY NUMBERS Chapter 11: CONFIGURING TCP/IP ADDRESSING AND SECURITY
- 5. CONVERTING DECIMAL ADDRESSES TO BINARY Chapter 11: CONFIGURING TCP/IP ADDRESSING AND SECURITY
- 6. CONVERTING BINARY ADDRESSES TO DECIMAL Chapter 11: CONFIGURING TCP/IP ADDRESSING AND SECURITY
- 7. USING CALCULATOR TO CONVERT NUMBERS Chapter 11: CONFIGURING TCP/IP ADDRESSING AND SECURITY
- 8. SUBNET MASKS Chapter 11: CONFIGURING TCP/IP ADDRESSING AND SECURITY
- 9. PROBLEMS WITH CLASSFUL ADDRESSES Wasted addresses Shortage of address blocks Excessive routing table entries Netblock - a range of consecutive IP addresses Chapter 11: CONFIGURING TCP/IP ADDRESSING AND SECURITY
- 10. … More detail… Netblocks were rigid, so organizations needing a contiguous address space were assigned an address block that, in some cases, was vastly larger than they needed. One example was any organization assigned a Class A netblock. Who has 1.7 million public systems? The supply of netblocks was limited. The Class A networks were all taken, and Class B networks were getting scarce. To deal with the scarcity of Class B blocks, some organizations obtained multiple Class C blocks to support their requirements. This resulted in a proliferation of routing table entries because several entries would be required to support several Class C networks for a single organization. Chapter 11: CONFIGURING TCP/IP ADDRESSING AND SECURITY
- 11. SUBNETTING A LARGE NETWORK Chapter 11: CONFIGURING TCP/IP ADDRESSING AND SECURITY
- 12. Previous Slide… This slide shows a Class A network being subnetted first into Class B networks and then into Class C networks. This is one solution to the scarcity of Class B networks. It creates 256 Class B subnetworks for each Class A network divided in this way. Each Class B network can then be divided into 256 Class C networks. Chapter 11: CONFIGURING TCP/IP ADDRESSING AND SECURITY
- 13. CLASSLESS INTERDOMAIN ROUTING (CIDR) Chapter 11: CONFIGURING TCP/IP ADDRESSING AND SECURITY
- 14. SUPERNETS Chapter 11: CONFIGURING TCP/IP ADDRESSING AND SECURITY
- 15. SECURING IP COMMUNICATIONS Internet threats Protective technologies Configuring and managing Windows Firewall Monitoring Internet communications security Chapter 11: CONFIGURING TCP/IP ADDRESSING AND SECURITY
- 16. INTERNET THREATS Viruses (the oldest threat) Worms (the most persistent threat) Trojan horses Spyware Zombies Direct hacking Chapter 11: CONFIGURING TCP/IP ADDRESSING AND SECURITY
- 17. VIRUSES Take advantage of gullible users Infect document, graphics, and executable files Often include mass-mailing components Can carry destructive payloads Chapter 11: CONFIGURING TCP/IP ADDRESSING AND SECURITY
- 18. Viruses (continued…) Computer viruses have been around since 1975, when John Walker released a program called Pervade to distribute a game he had invented. The game replicated itself to UNIVAC systems everywhere and, according to some accounts, eventually ended up on UNIVAC system distribution tapes. Since that time, many more virulent viruses have been written, and the damage they have caused in terms of time and money has been enormous. Corporations spend billions of dollars each year to protect themselves against viruses, and billions of dollars more when their protections fail. Chapter 11: CONFIGURING TCP/IP ADDRESSING AND SECURITY
- 19. WORMS Self-replicating Network-aware Use bugs in programs or systems to spread Can carry viruses or other payloads Chapter 11: CONFIGURING TCP/IP ADDRESSING AND SECURITY
- 20. Worms (continued…) Worms scan networks looking for systems that are running operating systems or applications with certain known vulnerabilities. When they find a vulnerability, they insert themselves into the vulnerable system and begin using it to scan for more victims. If a system is infected, any unpatched system connected to the network will be infected, repeating the cycle. Discuss any recent news-making worms. Describe their attack vector and their payload. Discuss how infections from that particular worm might be prevented. Chapter 11: CONFIGURING TCP/IP ADDRESSING AND SECURITY
- 21. TROJAN HORSES Usually e-mailed or downloaded Appear to be a useful program or game Carry payload or back door application Chapter 11: CONFIGURING TCP/IP ADDRESSING AND SECURITY
- 22. Trojan Horses (continued…) Trojan horses rely on credulous victims. They appear on the Internet as useful programs or fun games. When they are executed on the victim’s system, they install a back door application to let hackers control the system or they launch a viral payload on the victim. Chapter 11: CONFIGURING TCP/IP ADDRESSING AND SECURITY
- 23. SPYWARE Has attributes of Trojan horses or worms Spies on its victim Might transmit marketing data or transmit personal data to the spyware author Chapter 11: CONFIGURING TCP/IP ADDRESSING AND SECURITY
- 24. Spyware (continued…) Some spyware is voluntarily installed by users as part of a marketing agreement. Other versions use viral or worm vectors to spread to target systems. Once installed, some versions simply collect demographic data. Others log keystrokes or redirect browsers to sites that pay a royalty to the author. Chapter 11: CONFIGURING TCP/IP ADDRESSING AND SECURITY
- 25. ZOMBIES Payload of worm or Trojan horse Remotely controlled to attack network targets Participate in large-scale assaults on public Web sites Chapter 11: CONFIGURING TCP/IP ADDRESSING AND SECURITY
- 26. Zombies (continued…) Zombies are planted and controlled by hackers to attack large sites. Fleets of zombies can be coordinated by one “zombie master” to direct large-scale attacks against targets. Chapter 11: CONFIGURING TCP/IP ADDRESSING AND SECURITY
- 27. DIRECT HACKING Relatively low incidence Hardest form of attack to defeat Although well-publicized by the movie industry, direct interactive penetration by hackers is relatively rare because it takes time, patience, and skill to locate vulnerable components on the intended victim’s system. Many hackers prefer to use mass attacks such as worms, Trojan horses, and viruses to gain access to systems. Chapter 11: CONFIGURING TCP/IP ADDRESSING AND SECURITY
- 28. PROTECTIVE TECHNOLOGIES Security Center Windows Firewall Internet Connection Sharing (ICS) Third-party utilities Chapter 11: CONFIGURING TCP/IP ADDRESSING AND SECURITY
- 29. SECURITY CENTER Chapter 11: CONFIGURING TCP/IP ADDRESSING AND SECURITY
- 30. FIREWALL TERMINOLOGY Packet filtering The process of inspecting packet headers to determine whether they are allowed to enter the network. Those that do not conform with established rules for address, port, or protocol type are dropped. Stateful packet filtering A more advanced form of packet filtering where inbound packets must be received in response to an initial communication from the system. Outbound traffic is tracked in a “state table,” and inbound packets must conform to expected reply traffic to those communications. Chapter 11: CONFIGURING TCP/IP ADDRESSING AND SECURITY
- 31. FIREWALL TERMINOLOGY Exceptions (packet filter rules) Rules that allow some inbound traffic to enter your system. For example, to allow Remote Desktop to enter your system if you want to access your system from work or school, you would enable an exception. Chapter 11: CONFIGURING TCP/IP ADDRESSING AND SECURITY
- 32. FIREWALL TERMINOLOGY Allowed traffic Packet traffic that is allowed to pass the firewall. Rejected traffic Packet traffic that has not met acceptance rules and is dropped. Logging The process by which firewalls maintain a history of acceptance and rejection events. Logging is often used to discover penetration attempts or troubleshoot connectivity issues. Chapter 11: CONFIGURING TCP/IP ADDRESSING AND SECURITY
- 33. ENABLING WINDOWS FIREWALL Chapter 11: CONFIGURING TCP/IP ADDRESSING AND SECURITY
- 34. FIREWALL EXCEPTIONS Chapter 11: CONFIGURING TCP/IP ADDRESSING AND SECURITY
- 35. ADVANCED WINDOWS FIREWALL SETTINGS Chapter 11: CONFIGURING TCP/IP ADDRESSING AND SECURITY ICMP - Internet Control Message Protocol
- 36. MONITORING INTERNET SECURITY Windows Firewall monitoring Service logs Event logs Chapter 11: CONFIGURING TCP/IP ADDRESSING AND SECURITY
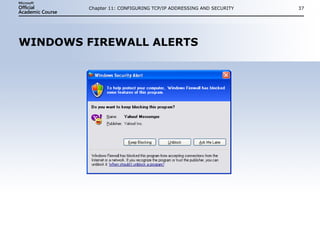
- 37. WINDOWS FIREWALL ALERTS Chapter 11: CONFIGURING TCP/IP ADDRESSING AND SECURITY
- 38. WINDOWS FIREWALL LOGS Chapter 11: CONFIGURING TCP/IP ADDRESSING AND SECURITY
- 39. SERVER LOGS Chapter 11: CONFIGURING TCP/IP ADDRESSING AND SECURITY
- 40. SUMMARY IP addresses are 32-bit binary addresses. The network portion of IP addresses determines location. CIDR allows creation of custom netblocks. CIDR permits use of variable-length subnet masks. Windows Firewall blocks unauthorized packets. Windows Firewall exceptions allow specified traffic to pass through the firewall. Alerts and logs warn of attempted attacks. Chapter 11: CONFIGURING TCP/IP ADDRESSING AND SECURITY
Editor's Notes
- #3: This chapter addresses advanced TCP/IP addressing and Internet security. It introduces students to classless interdomain routing (CIDR) subnetting and subnet masks, and it explores the binary nature of IP addresses and the knowledge necessary to troubleshoot addressing issues. We will also introduce Windows XP Internet security features such as Windows Firewall. Proper configuration and operation of Windows Firewall can protect systems inexpensively.
- #5: This slide depicts the relationship between decimal number 179 and its binary equivalent. Many students will be familiar with the principles of the binary numbering system. Make sure that the others understand this slide. Without a basic understanding of binary numbering and the base 2 number system, students will not understand the next part of this chapter.
- #6: This slide shows the conversion of a dotted decimal IP address to its binary equivalent. Make it clear that IP operates at the binary level and that the dotted decimal representations we see are only for our convenience.
- #7: This slide shows the conversion of a binary IP address to its dotted decimal equivalent. Walk through the conversion with students.
- #8: This slide depicts the use of Calculator to convert the decimal number 179 to binary and back again. Stress the importance of maintaining leading zeros when converting numbers in this way. IP addresses require complete octets to be effective.
- #9: This slide shows a decimal subnet mask and the same subnet mask in binary form. Point out how the subnet mask designates the portion of the address that belongs to the network and the portion that belongs to the host.
- #10: This slide lists three disadvantages of classful IP addressing: Netblocks were rigid, so organizations needing a contiguous address space were assigned an address block that, in some cases, was vastly larger than they needed. One example was any organization assigned a Class A netblock. Who has 1.7 million public systems? The supply of netblocks was limited. The Class A networks were all taken, and Class B networks were getting scarce. To deal with the scarcity of Class B blocks, some organizations obtained multiple Class C blocks to support their requirements. This resulted in a proliferation of routing table entries because several entries would be required to support several Class C networks for a single organization.
- #12: This slide shows a Class A network being subnetted first into Class B networks and then into Class C networks. This is one solution to the scarcity of Class B networks. It creates 256 Class B subnetworks for each Class A network divided in this way. Each Class B network can then be divided into 256 Class C networks. The remaining problem with this method is that there is no provision for organizations that need 300 addresses (a fraction of a Class B) or 6 addresses (a fraction of a Class C). The next slide shows the solution. Find out how many of your students know the answer already.
- #14: Spend some time on this slide, which presents a lot of information. We are using a CIDR subnet mask to divide a Class B netblock into eight smaller netblocks, each with 8,190 addresses. Point out how the new network address combinations added by extending the subnet mask are used to generate the new network IDs. Also explain how the new netblock ranges are calculated by beginning with the network ID and ending with the value for a host portion of all 1s. Explain how the network ID and the broadcast are reserved, yielding 2n–2 possible addresses. Finally, point out the CIDR notation that is used to define the new subnet masks. Ask students how the scenario might differ if we used the subnet mask /18 or /20 .
- #15: This slide depicts the use of CIDR to create a supernet from eight Class C netblocks. Describe this process and have students calculate the number of addresses in the new network.
- #16: This slide introduces the section of Chapter 11 dealing with IP communications security. Conduct a discussion of current threats, and then explain how Windows XP deals with those threats. End with a discussion of security monitoring.
- #17: This slide lists the major categories of Internet threats. Discuss each in turn, and have students provide examples of each. Point out the persistent nature of worms. (All it takes to keep a worm alive is a single unattended Windows XP system somewhere.)
- #18: Computer viruses have been around since 1975, when John Walker released a program called Pervade to distribute a game he had invented. The game replicated itself to UNIVAC systems everywhere and, according to some accounts, eventually ended up on UNIVAC system distribution tapes. Since that time, many more virulent viruses have been written, and the damage they have caused in terms of time and money has been enormous. Corporations spend billions of dollars each year to protect themselves against viruses, and billions of dollars more when their protections fail.
- #20: Worms scan networks looking for systems that are running operating systems or applications with certain known vulnerabilities. When they find a vulnerability, they insert themselves into the vulnerable system and begin using it to scan for more victims. If a system is infected, any unpatched system connected to the network will be infected, repeating the cycle. Discuss any recent news-making worms. Describe their attack vector and their payload. Discuss how infections from that particular worm might be prevented.
- #22: Trojan horses rely on credulous victims. They appear on the Internet as useful programs or fun games. When they are executed on the victim’s system, they install a back door application to let hackers control the system or they launch a viral payload on the victim.
- #24: Some spyware is voluntarily installed by users as part of a marketing agreement. Other versions use viral or worm vectors to spread to target systems. Once installed, some versions simply collect demographic data. Others log keystrokes or redirect browsers to sites that pay a royalty to the author.
- #26: Zombies are planted and controlled by hackers to attack large sites. Fleets of zombies can be coordinated by one “zombie master” to direct large-scale attacks against targets.
- #28: Although well-publicized by the movie industry, direct interactive penetration by hackers is relatively rare because it takes time, patience, and skill to locate vulnerable components on the intended victim’s system. Many hackers prefer to use mass attacks such as worms, Trojan horses, and viruses to gain access to systems.
- #29: The technologies you can use to protect a Windows XP system range from the built-in Windows Firewall and ICS to third-party antivirus tools that can detect and defeat almost any known malware. In this section, we concentrate on the Windows tools. We also present the Security Center, an application that allows users to monitor security configuration on their systems.
- #30: This slide depicts the Security Center console. Demonstrate this console on a classroom system and show how it monitors the status of antivirus software, firewall software, and Automatic Updates. These are widely considered to be the three most important ways to defeat malicious software. Point out the numerous links to additional information on various aspects of system security.
- #31: This slide presents some common firewall terms. Discuss each briefly to ensure that students recognize them later during discussions of firewall configuration. Packet filtering The process of inspecting packet headers to determine whether they are allowed to enter the network. Those that do not conform with established rules for address, port, or protocol type are dropped. Stateful packet filtering A more advanced form of packet filtering where inbound packets must be received in response to an initial communication from the system. Outbound traffic is tracked in a “state table,” and inbound packets must conform to expected reply traffic to those communications. Exceptions Rules that allow some inbound traffic to enter your system. For example, to allow Remote Desktop to enter your system if you want to access your system from work or school, you would enable an exception. Allowed traffic Packet traffic that is allowed to pass the firewall. Rejected traffic Packet traffic that has not met acceptance rules and is dropped. Logging The process by which firewalls maintain a history of acceptance and rejection events. Logging is often used to discover penetration attempts or troubleshoot connectivity issues.
- #32: This slide presents some common firewall terms. Discuss each briefly to ensure that students recognize them later during discussions of firewall configuration. Packet filtering The process of inspecting packet headers to determine whether they are allowed to enter the network. Those that do not conform with established rules for address, port, or protocol type are dropped. Stateful packet filtering A more advanced form of packet filtering where inbound packets must be received in response to an initial communication from the system. Outbound traffic is tracked in a “state table,” and inbound packets must conform to expected reply traffic to those communications. Exceptions Rules that allow some inbound traffic to enter your system. For example, to allow Remote Desktop to enter your system if you want to access your system from work or school, you would enable an exception. Allowed traffic Packet traffic that is allowed to pass the firewall. Rejected traffic Packet traffic that has not met acceptance rules and is dropped. Logging The process by which firewalls maintain a history of acceptance and rejection events. Logging is often used to discover penetration attempts or troubleshoot connectivity issues.
- #33: This slide presents some common firewall terms. Discuss each briefly to ensure that students recognize them later during discussions of firewall configuration. Packet filtering The process of inspecting packet headers to determine whether they are allowed to enter the network. Those that do not conform with established rules for address, port, or protocol type are dropped. Stateful packet filtering A more advanced form of packet filtering where inbound packets must be received in response to an initial communication from the system. Outbound traffic is tracked in a “state table,” and inbound packets must conform to expected reply traffic to those communications. Exceptions Rules that allow some inbound traffic to enter your system. For example, to allow Remote Desktop to enter your system if you want to access your system from work or school, you would enable an exception. Allowed traffic Packet traffic that is allowed to pass the firewall. Rejected traffic Packet traffic that has not met acceptance rules and is dropped. Logging The process by which firewalls maintain a history of acceptance and rejection events. Logging is often used to discover penetration attempts or troubleshoot connectivity issues.
- #34: This slide shows the three main tabs of the Windows Firewall dialog box. Point out the settings as you step through the frames. If possible, demonstrate some of them on a classroom system.
- #35: This slide shows the configuration of firewall exceptions. Describe when an exception might be necessary to allow a system to provide a service or communicate with other systems using a nonstandard port or protocol. Point out the Change Scope feature, which allows you to designate which interface the exceptions apply to. Discuss how this might be important for file-sharing networks that also access the Internet.
- #36: This slide depicts the dialog boxes accessible from the Advanced tab of the Windows Firewall Properties dialog box. Point out how to designate which connections are protected by Windows Firewall and the services you can enable by using the Services tab. Explain why some of these settings might be used (for example, for a system that acts as a Web server for a small office). Describe how ICMP settings can be enabled and disabled, either per connection or globally. Refer students to the textbook for descriptions of the ICMP settings.
- #37: This slide introduces the topic of Internet security monitoring. Use the analogy of the Internet as a vast hotel or apartment building. Internet users lock their own doors for safety and privacy. They unlock them for room service or the maid but do not allow potential intruders to enter. They can hear if someone tries to pick their lock, and they can take appropriate action to call in the authorities or otherwise protect themselves. On the Internet, we also need a way to alert ourselves to attempted attacks. For this purpose, Windows Firewall has alerts and logs. Alerts notify the user when an attempt is made to open a restricted port. Logs record accepted and rejected traffic for later analysis. In addition, Internet services keep their own logs to track use of the service. These can often offer a clue as to the intent of an attacker.
- #38: Windows Firewall notifies users of new applications trying to communicate with their system and lets them take action to allow or block such applications. Describe the process and effects of adding exceptions to Windows Firewall.
- #39: This slide depicts the configuration and format of Windows Firewall logs. Point out the attempted attack on the HTTP port (the three dropped packets for port 80). If possible, open a logfile in class and examine its contents. Describe the entries and their implications.
- #40: This slide shows an excerpt of a Web server log for IIS in Windows XP. Point out the 403 (authentication) and 404 (file not found) errors. Discuss the implications of seeing a large number of these in your logs (hack attempts or searches for known vulnerabilities).
- #41: This list summarizes this chapter. As you discuss the items, return to the main points of your lecture. Make sure students understand the principles of CIDR subnet masks and CIDR notation. Stress the importance of having a strong understanding of IP addressing and security topics in real-world network designs.