JavaLand 2022 - Debugging distributed systems
0 likes142 views
This document outlines a structured approach to debugging distributed systems. It begins with observing and documenting the problem. The next steps involve creating a minimal reproducer, debugging the client and server sides, and checking DNS, routing, and network connections. Additional steps include inspecting traffic, attaching remote debuggers, and conducting a post-mortem analysis. Throughout the process, various tools can help with tasks like logging, testing, and network inspection. The document concludes by emphasizing the importance of understanding failure modes through experience debugging real issues with distributed systems.
1 of 33
Download to read offline





























Ad
Recommended
Importance of taxonomy from Holy Quran



Importance of taxonomy from Holy QuranFragariavesca This document discusses plants mentioned in the Holy Quran, including their scientific names, parts used, and medicinal properties. It provides references to over 15 plant species found in the Quran, such as dates, olives, pomegranates, onions and lentils. The document aims to highlight the importance of plant taxonomy by exploring plants with religious significance as described in Islamic scripture.
Plant Defence inducing molecules against pathogens - Lessons learned and path...



Plant Defence inducing molecules against pathogens - Lessons learned and path...Ashajyothi Mushineni This document summarizes a seminar presentation on defence inducing molecules against plant pathogens. It discusses various molecules that can induce plant defenses, such as BABA, probenazole, SA analogues, jasmonic acid, chitosan, oligogalacturonides, harpin proteins, and vitamins. Case studies demonstrate the effects of these molecules in enhancing disease resistance in plants like tomato and pepper. While these defense activators provide advantages over fungicides, challenges include potential environmental and health issues. Further research is needed to develop more economical and effective defense inducing strategies.
Biological control of weeds



Biological control of weedsIIM Ahmedabad This document discusses biological control of weeds, which involves using a weed's natural enemies like insects, mites, fungi or bacteria to suppress the weed's population over time. There are three main types of biological control: classical which uses a small number of control agents that reproduce over time to suppress the weed, inundative which uses large quantities of pathogens in an artificial epidemic, and conservation which manipulates the habitat to encourage organisms that attack the weed. The process involves identifying target weeds and control agents, testing the agents, releasing and monitoring them, and allowing the agents' populations to build up and eventually reach an equilibrium that keeps the weed below a harmful threshold level. Some examples of successful biological control agents provided include various fungi
Biopesticide & Biofertilizer - useful for Biotechnology



Biopesticide & Biofertilizer - useful for BiotechnologyPrakashPatel781970 Biopesticides are derived from natural sources as alternatives to chemical pesticides. They include microbial pesticides using microbes, and plant-incorporated protectants that genetically modify plants. Microbial herbicides and insecticides control unwanted plants and insects using fungi, bacteria, viruses and entomopathogenic fungi. Biofertilizers are microorganisms that fix atmospheric nitrogen, solubilize phosphorus, or promote plant growth. They improve soil fertility and provide nutrients to plants, but require large amounts and special storage conditions.
Mk saminar



Mk saminarMukesh Kumar The document summarizes systemic acquired resistance (SAR), a type of induced resistance in plants that confers broad-spectrum protection against pathogens. SAR is activated by initial infection, which triggers salicylic acid signaling and pathogenesis-related protein expression throughout the plant. Key regulators include NPR1, which is required for SAR, and salicylic acid, which is involved in long-distance signaling. SAR provides long-lasting resistance against bacterial, fungal, and viral pathogens.
Mastering Microservices 2022 - Debugging distributed systems



Mastering Microservices 2022 - Debugging distributed systemsBert Jan Schrijver This document outlines a structured approach to debugging distributed systems. It begins by having the debugger observe and document what is known about the problem. The next steps involve creating a minimal reproducer, debugging the client and server sides, checking DNS/routing and network connectivity, and inspecting traffic and messages. Wrapping up includes documenting lessons learned. Various tools are recommended for each step, with the overall goal of methodically eliminating potential issues to identify the root cause of problems in distributed systems.
Devoxx Belgium 2022 - Debugging distributed systems



Devoxx Belgium 2022 - Debugging distributed systemsBert Jan Schrijver This document outlines a structured approach for debugging distributed systems. It begins with observing and documenting what is known about the problem. The next steps are to create a minimal reproducer, debug the client side, check DNS and routing, and inspect the connection. Further debugging involves inspecting traffic and messages, debugging the server side, and wrapping up with documentation and a post-mortem. Key tools mentioned include logging, tracing, tests, SSH, network inspection tools, and remote debugging. The document emphasizes focusing on details, eliminating single points of failure, and gaining an understanding of potential failure modes through experience debugging real issues.
Arnhem JUG March 2023 - Debugging distributed systems



Arnhem JUG March 2023 - Debugging distributed systemsBert Jan Schrijver This document outlines a structured approach for debugging distributed systems. It begins with observing and documenting what is known about the problem. The next steps are to create a minimal reproducer, debug the client side, check DNS and routing, and inspect the connection. Further debugging involves inspecting traffic and messages, debugging the server side, and wrapping up with documentation and a post-mortem. Key tools mentioned include logging, tracing, testing, and network debugging tools. The document argues that understanding failure modes is important for building reliable distributed systems.
Debugging distributed systems



Debugging distributed systemsBert Jan Schrijver This document outlines a structured approach for debugging distributed systems. It begins with observing and documenting what is known about the problem. The next steps involve creating a minimal reproducer, debugging the client and server sides, and checking DNS, routing, and network connections. Traffic and messages should be inspected, with a focus on eliminating potential issues on the client side first. The process concludes by wrapping up with documentation of findings, impacts, and lessons learned to prevent future issues. Several tools are recommended for each step to aid in debugging distributed systems effectively.
JUG CH September 2021 - Debugging distributed systems



JUG CH September 2021 - Debugging distributed systemsBert Jan Schrijver This document provides an overview of debugging distributed systems. It begins with definitions of distributed systems and why they are difficult to debug due to factors like concurrency, lack of a global clock, and independent failures. It then outlines a structured 8 step approach to debugging distributed systems: 1) observe and document issues, 2) create a minimal reproducer, 3) debug client side, 4) check DNS and routing, 5) check connections, 6) inspect traffic and messages, 7) debug server side, and 8) wrap up with a post mortem. The document concludes with examples of distributed systems war stories and questions.
Incident Response Fails



Incident Response FailsMichael Gough Incident Response Fails – What we see with our clients, and their fails. As Incident Responders, what do we see as Incident Responders that you can do to be better prepared, reduce your incident costs, get answers faster and reduce the cost of an IR Firm if needed.
HackerHurricane
Malware Archaeology
MalwareArchaeology
LOG-MD
WTF is Penetration Testing v.2



WTF is Penetration Testing v.2Scott Sutherland This presentation will provide an overview of what a penetration test is, why companies pay for them, and what role they play in most IT security programs. It will also include a brief overview of the common skill sets and tools used by today’s security professionals. Finally, it will offer some basic advice for getting started in penetration testing. This should be interesting to aspiring pentesters trying to gain a better understanding of how penetration testing fits into the larger IT security world.
Additional resources can be found in the blog below:
https://www.netspi.com/blog/entryid/140/resources-for-aspiring-penetration-testers
More security blogs by the authors can be found @
https://www.netspi.com/blog/
Pentesting Tips: Beyond Automated Testing



Pentesting Tips: Beyond Automated TestingAndrew McNicol This document provides an agenda for a presentation on going beyond automated testing for security assessments. The presentation covers testing methodologies, soft skills needed for manual testing like determination and focus, limitations of automated testing, techniques for finding unknown systems and content, exploiting vulnerabilities, reporting and automation best practices, and recommendations for useful training resources. The goal is to share experiences with external security assessments and how manual testing finds issues missed by automated tools.
Monitoring microservices



Monitoring microservicesWilliam Brander Microservices are a great way to design your system so that it can scale. But once those pieces are in production, how do you know if all the different pieces are working properly? Are some metrics more important than others, and what story can each of the metrics tell you? This talk shows you some tools and techniques to monitor distributed systems
When Security Tools Fail You



When Security Tools Fail YouMichael Gough When your security tools fail you, and what you can do about it. This discusses actual tool fail backgrounds, what failed and what you can do to detect and/or mitigate the issues(s) another way
HackerHurricane
MalwareArchaeology
Malware Archaeology
LOG-MD
Blockchain and Hook model of engagement 



Blockchain and Hook model of engagement Rajeev Soni This is a quick overview to Blockchains and the Hooked model of technology product engagement. I speak on Product Management, Digital Marketing and Technology topics.
This is a presentation I delivered at the Jamia Milia Islamia University in Delhi.
Sophisticated Attacks - Can We Really Detect Them _v1.2.pdf



Sophisticated Attacks - Can We Really Detect Them _v1.2.pdfMichael Gough Every time I read the news, a blog, or security article like “LitterDrifter's means of self-propagation are simple. So why is it spreading so widely?” or “Hackers use new Agent Raccoon malware to backdoor US targets” or “Yellow Liderc ships its scripts and delivers IMAPLoader malware” or “New 'HrServ.dll' Web Shell Detected in APT Attack Targeting Afghan Government” and many others, I say to myself.. “Self, can we detect these attacks?, if so how?”. This talk will cover the typical things in these attacks that are basic Security 101 detectable as well as data from some of our investigations that can be used to build a robust detection strategy and what you need to detect these and most other attacks. LOG-MD, Malware Archaeology
Professional Hacking in 2011



Professional Hacking in 2011securityaegis The document provides an overview of security testing and hacking. It discusses the basics of vulnerability testing, different methodologies like network testing and web application testing. It outlines three main types of security tests: audits, assessments, and penetration tests. It discusses the importance of having permission and ethics when conducting security work. The document also provides a brief history of hacking and how the techniques have evolved over time as external vulnerabilities have been addressed.
FUEL_USERS_GROUP



FUEL_USERS_GROUPWill Pearce Purple teaming involves collaborating red and blue teams to improve cybersecurity. By using red team tactics, blue teams can practice detecting and responding to active threats. This helps validate tools and processes, find gaps in detection and response, and ensures organizations are prepared to handle real-world attacks. It differs from traditional penetration testing by focusing more on detection and response rather than just finding vulnerabilities. The goal is to gain confidence in incident response plans through practical exercises.
Heartbleed



HeartbleedPunit Goswami An introduction to The Heartbleed Vulnerability. Considered to be the worst horror of the internet age, this flaw and its discovery changed the way people thought about implementing Open source standards.
Can_We_Really_Detect_These_So_Called_Sophisticated_Attacks?



Can_We_Really_Detect_These_So_Called_Sophisticated_Attacks?Michael Gough What does it take to detect all these attacks we read about? Is it possible? Where do we start? What do we do? AHHHHHHHHHHHHHHH... This talk helps to bring an approach to use these reports to improve your security program. LOG-MD, Malware Archaeology
Owning windows 8 with human interface devices



Owning windows 8 with human interface devicesNikhil Mittal This document discusses using human interface devices like the Teensy microcontroller in penetration tests against Windows 8 systems. It introduces the Kautilya toolkit for programming Teensy payloads and demonstrates attacks against Windows 8 by connecting the Teensy and executing payloads with the privileges of the logged-in user. Limitations of this technique include storage limits on Teensy and an inability to read responses or clear itself after running. Defenses include disabling removable devices or locking USB ports.
Rewriting DevOps



Rewriting DevOpsMatthew Boeckman Six years is a long time to put up with a stack, a Senator, or an Ops approach. Craftsy has been working on a full rewrite of their core systems, and is reworking DevOps along the way. DevOps sounds good, but how do you bridge the material gap in skills and experience to bring Ops to dev, and dev to Ops? With iteration, humor, tools, and an open acceptance of failure.
Matthew Boeckman, VP - Infrastructure at Craftsy
THOTCON 0x6: Going Kinetic on Electronic Crime Networks



THOTCON 0x6: Going Kinetic on Electronic Crime NetworksJohn Bambenek Defensive security is a rat race. We detect new threats, we reverse engineer them and develop defenses while the bad guys just make new threats. We often just document a new threat and stop when the blog post is published. This talk will take it a step further on how to proactively disrupt threats and threat actors, not just from your organization but completely. As a case study, Operation Tovar and whatever else I take down between now and THOTCON will be used as examples of how this can be accomplished without a large legal team and without massive collateral damage (i.e. the No-IP incident). Tools will be demonstrated that are used for near-time surveillance of criminal networks.
From SLO to GOTY



From SLO to GOTYScyllaDB Your users aren’t interested in your CPU utilization, and nobody is starting Reddit threads about how much disk space you have available. Questions like, “How long will I be in this queue?” or “How many disconnects is that today?” draw the wrong kind of attention. Instead of trying to guess which of your system metrics have the potential to cause an issue, your tools need to evolve from asking the same kinds of questions that your users are. An SLO, or Service Level Objective, lets you do this, resulting in fewer false alarms and surprises. The result? Happier users, happier teams, and a more productive organization.
Chapter 15 incident handling



Chapter 15 incident handlingnewbie2019 This document discusses incident response and handling. It outlines the key steps in the incident response process: preparation, identification, containment, eradication, recovery, and lessons learned. Preparation involves forming a response team, developing procedures, and gathering resources. Identification involves determining the scope of an incident and preserving evidence. Containment focuses on limiting the damage of an incident through actions like quarantining systems, analyzing initial data, and making backups. Eradication aims to completely remove malicious software from affected systems.
2023 NCIT: Introduction to Intrusion Detection



2023 NCIT: Introduction to Intrusion DetectionAPNIC APNIC Senior Security Specialist Adli Wahid presents an Introduction to Intrusion Detection at the 2023 NCIT, held in Suva, Fiji from 17 to 18 August 2023.
Architecting a Post Mortem - Velocity 2018 San Jose Tutorial



Architecting a Post Mortem - Velocity 2018 San Jose TutorialWill Gallego Engineers are frequently tasked with being front and center in intense, highly demanding situations that require clear lines of communication. Our systems fail not because of a lack of attention or laziness but due to cognitive dissonance between what we believe about our environments and the objective interactions both internal and external to them.
It’s time to revisit your established beliefs surrounding failure scenarios, with an emphasis not on the “who” in decision making but instead on the “why” behind those decisions. With attention to growth mindset, you can encourage your teams to reject shallow explanations of human error for said failures and focus on how to gain greater understanding of these complexities and push the boundaries on what you believe to be static, unchanging context outside your sphere of influence.
Will Gallego walks you through the structure of postmortems used at large tech companies with real-world examples of failure scenarios and debunks myths regularly attributed to failures. You’ll learn how to incorporate open dialogue within and between teams to bridge these gaps in understanding.
APNIC Update, presented at NZNOG 2025 by Terry Sweetser



APNIC Update, presented at NZNOG 2025 by Terry SweetserAPNIC Terry Sweetser, Training Delivery Manager (South Asia & Oceania) at APNIC presented an APNIC update at NZNOG 2025 held in Napier, New Zealand from 9 to 11 April 2025.
Smart Mobile App Pitch Deck丨AI Travel App Presentation Template



Smart Mobile App Pitch Deck丨AI Travel App Presentation Templateyojeari421237 🚀 Smart Mobile App Pitch Deck – "Trip-A" | AI Travel App Presentation Template
This professional, visually engaging pitch deck is designed specifically for developers, startups, and tech students looking to present a smart travel mobile app concept with impact.
Whether you're building an AI-powered travel planner or showcasing a class project, Trip-A gives you the edge to impress investors, professors, or clients. Every slide is cleanly structured, fully editable, and tailored to highlight key aspects of a mobile travel app powered by artificial intelligence and real-time data.
💼 What’s Inside:
- Cover slide with sleek app UI preview
- AI/ML module implementation breakdown
- Key travel market trends analysis
- Competitor comparison slide
- Evaluation challenges & solutions
- Real-time data training model (AI/ML)
- “Live Demo” call-to-action slide
🎨 Why You'll Love It:
- Professional, modern layout with mobile app mockups
- Ideal for pitches, hackathons, university presentations, or MVP launches
- Easily customizable in PowerPoint or Google Slides
- High-resolution visuals and smooth gradients
📦 Format:
- PPTX / Google Slides compatible
- 16:9 widescreen
- Fully editable text, charts, and visuals
Ad
More Related Content
Similar to JavaLand 2022 - Debugging distributed systems (20)
Debugging distributed systems



Debugging distributed systemsBert Jan Schrijver This document outlines a structured approach for debugging distributed systems. It begins with observing and documenting what is known about the problem. The next steps involve creating a minimal reproducer, debugging the client and server sides, and checking DNS, routing, and network connections. Traffic and messages should be inspected, with a focus on eliminating potential issues on the client side first. The process concludes by wrapping up with documentation of findings, impacts, and lessons learned to prevent future issues. Several tools are recommended for each step to aid in debugging distributed systems effectively.
JUG CH September 2021 - Debugging distributed systems



JUG CH September 2021 - Debugging distributed systemsBert Jan Schrijver This document provides an overview of debugging distributed systems. It begins with definitions of distributed systems and why they are difficult to debug due to factors like concurrency, lack of a global clock, and independent failures. It then outlines a structured 8 step approach to debugging distributed systems: 1) observe and document issues, 2) create a minimal reproducer, 3) debug client side, 4) check DNS and routing, 5) check connections, 6) inspect traffic and messages, 7) debug server side, and 8) wrap up with a post mortem. The document concludes with examples of distributed systems war stories and questions.
Incident Response Fails



Incident Response FailsMichael Gough Incident Response Fails – What we see with our clients, and their fails. As Incident Responders, what do we see as Incident Responders that you can do to be better prepared, reduce your incident costs, get answers faster and reduce the cost of an IR Firm if needed.
HackerHurricane
Malware Archaeology
MalwareArchaeology
LOG-MD
WTF is Penetration Testing v.2



WTF is Penetration Testing v.2Scott Sutherland This presentation will provide an overview of what a penetration test is, why companies pay for them, and what role they play in most IT security programs. It will also include a brief overview of the common skill sets and tools used by today’s security professionals. Finally, it will offer some basic advice for getting started in penetration testing. This should be interesting to aspiring pentesters trying to gain a better understanding of how penetration testing fits into the larger IT security world.
Additional resources can be found in the blog below:
https://www.netspi.com/blog/entryid/140/resources-for-aspiring-penetration-testers
More security blogs by the authors can be found @
https://www.netspi.com/blog/
Pentesting Tips: Beyond Automated Testing



Pentesting Tips: Beyond Automated TestingAndrew McNicol This document provides an agenda for a presentation on going beyond automated testing for security assessments. The presentation covers testing methodologies, soft skills needed for manual testing like determination and focus, limitations of automated testing, techniques for finding unknown systems and content, exploiting vulnerabilities, reporting and automation best practices, and recommendations for useful training resources. The goal is to share experiences with external security assessments and how manual testing finds issues missed by automated tools.
Monitoring microservices



Monitoring microservicesWilliam Brander Microservices are a great way to design your system so that it can scale. But once those pieces are in production, how do you know if all the different pieces are working properly? Are some metrics more important than others, and what story can each of the metrics tell you? This talk shows you some tools and techniques to monitor distributed systems
When Security Tools Fail You



When Security Tools Fail YouMichael Gough When your security tools fail you, and what you can do about it. This discusses actual tool fail backgrounds, what failed and what you can do to detect and/or mitigate the issues(s) another way
HackerHurricane
MalwareArchaeology
Malware Archaeology
LOG-MD
Blockchain and Hook model of engagement 



Blockchain and Hook model of engagement Rajeev Soni This is a quick overview to Blockchains and the Hooked model of technology product engagement. I speak on Product Management, Digital Marketing and Technology topics.
This is a presentation I delivered at the Jamia Milia Islamia University in Delhi.
Sophisticated Attacks - Can We Really Detect Them _v1.2.pdf



Sophisticated Attacks - Can We Really Detect Them _v1.2.pdfMichael Gough Every time I read the news, a blog, or security article like “LitterDrifter's means of self-propagation are simple. So why is it spreading so widely?” or “Hackers use new Agent Raccoon malware to backdoor US targets” or “Yellow Liderc ships its scripts and delivers IMAPLoader malware” or “New 'HrServ.dll' Web Shell Detected in APT Attack Targeting Afghan Government” and many others, I say to myself.. “Self, can we detect these attacks?, if so how?”. This talk will cover the typical things in these attacks that are basic Security 101 detectable as well as data from some of our investigations that can be used to build a robust detection strategy and what you need to detect these and most other attacks. LOG-MD, Malware Archaeology
Professional Hacking in 2011



Professional Hacking in 2011securityaegis The document provides an overview of security testing and hacking. It discusses the basics of vulnerability testing, different methodologies like network testing and web application testing. It outlines three main types of security tests: audits, assessments, and penetration tests. It discusses the importance of having permission and ethics when conducting security work. The document also provides a brief history of hacking and how the techniques have evolved over time as external vulnerabilities have been addressed.
FUEL_USERS_GROUP



FUEL_USERS_GROUPWill Pearce Purple teaming involves collaborating red and blue teams to improve cybersecurity. By using red team tactics, blue teams can practice detecting and responding to active threats. This helps validate tools and processes, find gaps in detection and response, and ensures organizations are prepared to handle real-world attacks. It differs from traditional penetration testing by focusing more on detection and response rather than just finding vulnerabilities. The goal is to gain confidence in incident response plans through practical exercises.
Heartbleed



HeartbleedPunit Goswami An introduction to The Heartbleed Vulnerability. Considered to be the worst horror of the internet age, this flaw and its discovery changed the way people thought about implementing Open source standards.
Can_We_Really_Detect_These_So_Called_Sophisticated_Attacks?



Can_We_Really_Detect_These_So_Called_Sophisticated_Attacks?Michael Gough What does it take to detect all these attacks we read about? Is it possible? Where do we start? What do we do? AHHHHHHHHHHHHHHH... This talk helps to bring an approach to use these reports to improve your security program. LOG-MD, Malware Archaeology
Owning windows 8 with human interface devices



Owning windows 8 with human interface devicesNikhil Mittal This document discusses using human interface devices like the Teensy microcontroller in penetration tests against Windows 8 systems. It introduces the Kautilya toolkit for programming Teensy payloads and demonstrates attacks against Windows 8 by connecting the Teensy and executing payloads with the privileges of the logged-in user. Limitations of this technique include storage limits on Teensy and an inability to read responses or clear itself after running. Defenses include disabling removable devices or locking USB ports.
Rewriting DevOps



Rewriting DevOpsMatthew Boeckman Six years is a long time to put up with a stack, a Senator, or an Ops approach. Craftsy has been working on a full rewrite of their core systems, and is reworking DevOps along the way. DevOps sounds good, but how do you bridge the material gap in skills and experience to bring Ops to dev, and dev to Ops? With iteration, humor, tools, and an open acceptance of failure.
Matthew Boeckman, VP - Infrastructure at Craftsy
THOTCON 0x6: Going Kinetic on Electronic Crime Networks



THOTCON 0x6: Going Kinetic on Electronic Crime NetworksJohn Bambenek Defensive security is a rat race. We detect new threats, we reverse engineer them and develop defenses while the bad guys just make new threats. We often just document a new threat and stop when the blog post is published. This talk will take it a step further on how to proactively disrupt threats and threat actors, not just from your organization but completely. As a case study, Operation Tovar and whatever else I take down between now and THOTCON will be used as examples of how this can be accomplished without a large legal team and without massive collateral damage (i.e. the No-IP incident). Tools will be demonstrated that are used for near-time surveillance of criminal networks.
From SLO to GOTY



From SLO to GOTYScyllaDB Your users aren’t interested in your CPU utilization, and nobody is starting Reddit threads about how much disk space you have available. Questions like, “How long will I be in this queue?” or “How many disconnects is that today?” draw the wrong kind of attention. Instead of trying to guess which of your system metrics have the potential to cause an issue, your tools need to evolve from asking the same kinds of questions that your users are. An SLO, or Service Level Objective, lets you do this, resulting in fewer false alarms and surprises. The result? Happier users, happier teams, and a more productive organization.
Chapter 15 incident handling



Chapter 15 incident handlingnewbie2019 This document discusses incident response and handling. It outlines the key steps in the incident response process: preparation, identification, containment, eradication, recovery, and lessons learned. Preparation involves forming a response team, developing procedures, and gathering resources. Identification involves determining the scope of an incident and preserving evidence. Containment focuses on limiting the damage of an incident through actions like quarantining systems, analyzing initial data, and making backups. Eradication aims to completely remove malicious software from affected systems.
2023 NCIT: Introduction to Intrusion Detection



2023 NCIT: Introduction to Intrusion DetectionAPNIC APNIC Senior Security Specialist Adli Wahid presents an Introduction to Intrusion Detection at the 2023 NCIT, held in Suva, Fiji from 17 to 18 August 2023.
Architecting a Post Mortem - Velocity 2018 San Jose Tutorial



Architecting a Post Mortem - Velocity 2018 San Jose TutorialWill Gallego Engineers are frequently tasked with being front and center in intense, highly demanding situations that require clear lines of communication. Our systems fail not because of a lack of attention or laziness but due to cognitive dissonance between what we believe about our environments and the objective interactions both internal and external to them.
It’s time to revisit your established beliefs surrounding failure scenarios, with an emphasis not on the “who” in decision making but instead on the “why” behind those decisions. With attention to growth mindset, you can encourage your teams to reject shallow explanations of human error for said failures and focus on how to gain greater understanding of these complexities and push the boundaries on what you believe to be static, unchanging context outside your sphere of influence.
Will Gallego walks you through the structure of postmortems used at large tech companies with real-world examples of failure scenarios and debunks myths regularly attributed to failures. You’ll learn how to incorporate open dialogue within and between teams to bridge these gaps in understanding.
Recently uploaded (19)
APNIC Update, presented at NZNOG 2025 by Terry Sweetser



APNIC Update, presented at NZNOG 2025 by Terry SweetserAPNIC Terry Sweetser, Training Delivery Manager (South Asia & Oceania) at APNIC presented an APNIC update at NZNOG 2025 held in Napier, New Zealand from 9 to 11 April 2025.
Smart Mobile App Pitch Deck丨AI Travel App Presentation Template



Smart Mobile App Pitch Deck丨AI Travel App Presentation Templateyojeari421237 🚀 Smart Mobile App Pitch Deck – "Trip-A" | AI Travel App Presentation Template
This professional, visually engaging pitch deck is designed specifically for developers, startups, and tech students looking to present a smart travel mobile app concept with impact.
Whether you're building an AI-powered travel planner or showcasing a class project, Trip-A gives you the edge to impress investors, professors, or clients. Every slide is cleanly structured, fully editable, and tailored to highlight key aspects of a mobile travel app powered by artificial intelligence and real-time data.
💼 What’s Inside:
- Cover slide with sleek app UI preview
- AI/ML module implementation breakdown
- Key travel market trends analysis
- Competitor comparison slide
- Evaluation challenges & solutions
- Real-time data training model (AI/ML)
- “Live Demo” call-to-action slide
🎨 Why You'll Love It:
- Professional, modern layout with mobile app mockups
- Ideal for pitches, hackathons, university presentations, or MVP launches
- Easily customizable in PowerPoint or Google Slides
- High-resolution visuals and smooth gradients
📦 Format:
- PPTX / Google Slides compatible
- 16:9 widescreen
- Fully editable text, charts, and visuals
APNIC -Policy Development Process, presented at Local APIGA Taiwan 2025



APNIC -Policy Development Process, presented at Local APIGA Taiwan 2025APNIC Joyce Chen, Senior Advisor, Strategic Engagement at APNIC, presented on 'APNIC Policy Development Process' at the Local APIGA Taiwan 2025 event held in Taipei from 19 to 20 April 2025.
IT Services Workflow From Request to Resolution



IT Services Workflow From Request to Resolutionmzmziiskd IT Services Workflow From Request to Resolution
Reliable Vancouver Web Hosting with Local Servers & 24/7 Support



Reliable Vancouver Web Hosting with Local Servers & 24/7 Supportsteve198109 Looking for powerful and affordable web hosting in Vancouver? 4GoodHosting offers premium Canadian web hosting solutions designed specifically for individuals, startups, and businesses across British Columbia. With local data centers in Vancouver and Toronto, we ensure blazing-fast website speeds, superior uptime, and enhanced data privacy—all critical for your business success in today’s competitive digital landscape.
Our Vancouver web hosting plans are packed with value—starting as low as $2.95/month—and include secure cPanel management, free domain transfer, one-click WordPress installs, and robust email support with anti-spam protection. Whether you're hosting a personal blog, business website, or eCommerce store, our scalable cloud hosting packages are built to grow with you.
Enjoy enterprise-grade features like daily backups, DDoS protection, free SSL certificates, and unlimited bandwidth on select plans. Plus, our expert Canadian support team is available 24/7 to help you every step of the way.
At 4GoodHosting, we understand the needs of local Vancouver businesses. That’s why we focus on speed, security, and service—all hosted on Canadian soil. Start your online journey today with a reliable hosting partner trusted by thousands across Canada.
Mobile database for your company telemarketing or sms marketing campaigns. Fr...



Mobile database for your company telemarketing or sms marketing campaigns. Fr...DataProvider1 Why Mobile Database Services are Important: Powering the Future of Mobile Applications
Top Vancouver Green Business Ideas for 2025 Powered by 4GoodHosting



Top Vancouver Green Business Ideas for 2025 Powered by 4GoodHostingsteve198109 Vancouver in 2025 is more than scenic views, yoga studios, and oat milk lattes—it’s a thriving hub for eco-conscious entrepreneurs looking to make a real difference. If you’ve ever dreamed of launching a purpose-driven business, now is the time. Whether it’s urban mushroom farming, upcycled furniture sales, or vegan skincare sold online, your green idea deserves a strong digital foundation.
The 2025 Canadian eCommerce landscape is being shaped by trends like sustainability, local innovation, and consumer trust. To stay ahead, eco-startups need reliable hosting that aligns with their values. That’s where 4GoodHosting.com comes in—one of the top-rated Vancouver web hosting providers of 2025. Offering secure, sustainable, and Canadian-based hosting solutions, they help green entrepreneurs build their brand with confidence and conscience.
As eCommerce in Canada embraces localism and environmental responsibility, choosing a hosting provider that shares your vision is essential. 4GoodHosting goes beyond just hosting websites—they champion Canadian businesses, sustainable practices, and meaningful growth.
So go ahead—start that eco-friendly venture. With Vancouver web hosting from 4GoodHosting, your green business and your values are in perfect sync.
Best web hosting Vancouver 2025 for you business



Best web hosting Vancouver 2025 for you businesssteve198109 Vancouver in 2025 is more than scenic views, yoga studios, and oat milk lattes—it’s a thriving hub for eco-conscious entrepreneurs looking to make a real difference. If you’ve ever dreamed of launching a purpose-driven business, now is the time. Whether it’s urban mushroom farming, upcycled furniture sales, or vegan skincare sold online, your green idea deserves a strong digital foundation.
The 2025 Canadian eCommerce landscape is being shaped by trends like sustainability, local innovation, and consumer trust. To stay ahead, eco-startups need reliable hosting that aligns with their values. That’s where 4GoodHosting.com comes in—one of the top-rated Vancouver web hosting providers of 2025. Offering secure, sustainable, and Canadian-based hosting solutions, they help green entrepreneurs build their brand with confidence and conscience.
As eCommerce in Canada embraces localism and environmental responsibility, choosing a hosting provider that shares your vision is essential. 4GoodHosting goes beyond just hosting websites—they champion Canadian businesses, sustainable practices, and meaningful growth.
So go ahead—start that eco-friendly venture. With Vancouver web hosting from 4GoodHosting, your green business and your values are in perfect sync.
Understanding the Tor Network and Exploring the Deep Web



Understanding the Tor Network and Exploring the Deep Webnabilajabin35 While the Tor network, Dark Web, and Deep Web can seem mysterious and daunting, they are simply parts of the internet that prioritize privacy and anonymity. Using tools like Ahmia and onionland search, users can explore these hidden spaces responsibly and securely. It’s essential to understand the technology behind these networks, as well as the risks involved, to navigate them safely. Visit https://torgol.com/
DNS Resolvers and Nameservers (in New Zealand)



DNS Resolvers and Nameservers (in New Zealand)APNIC Geoff Huston, Chief Scientist at APNIC, presented on 'DNS Resolvers and Nameservers in New Zealand' at NZNOG 2025 held in Napier, New Zealand from 9 to 11 April 2025.
highend-srxseries-services-gateways-customer-presentation.pptx



highend-srxseries-services-gateways-customer-presentation.pptxelhadjcheikhdiop Juniper High End Series
Perguntas dos animais - Slides ilustrados de múltipla escolha



Perguntas dos animais - Slides ilustrados de múltipla escolhasocaslev Slides ilustrados de múltipla escolha
Ad
JavaLand 2022 - Debugging distributed systems
- 1. [email protected] Debugging distributed systems Bert Jan Schrijver @bjschrijver
- 2. Debugging distributed systems: the good parts [email protected] Bert Jan Schrijver @bjschrijver Networking 101 How the internet works
- 3. Why?
- 4. Bert Jan Schrijver L e t ’ s m e e t @bjschrijver
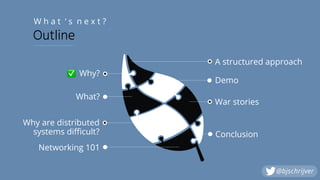
- 5. Why are distributed systems difficult? Networking 101 What? Why? ✅ Demo War stories Conclusion W h a t ‘ s n e x t ? Outline A structured approach @bjschrijver
- 6. What is a distributed system?
- 7. A distributed system is a system whose components are located on different networked computers, which communicate and coordinate their actions by passing messages to one another.
- 8. • Concurrency of components • Lack of a global clock • Independent failure of components • Distributed systems are harder to reason about Characteristics of distributed systems Source: http://www.nasa.gov/images/content/218652main_STOCC_FS_img_lg.jpg
- 9. Working with distributed systems is fundamentally different from writing software on a single computer - and the main difference is that there are lots of new and exciting ways for things to go wrong. - Martin Kleppmann “ ” Photo: Dave Lehl
- 10. What could possibly go wrong? “ ” Photo: Dave Lehl
- 11. OSI & TCP/IP Source: https://www.guru99.com/difference-tcp-ip-vs-osi-model.html
- 12. .. in your browser’s address bar and press Enter What happens when you type google.com… Source: https://github.com/alex/what-happens-when
- 13. 13
- 15. Step 1: Observe & document • What do you know about the problem? • Inspect logging, errors, metrics, tracing • Draw the path from source to target - what’s in between? Focus on details! • Document what you know • Can we reproduce in a test? • By injecting errors, for example Tools Whiteboard, documentation, logging, metrics, tracing (opentracing.io), tests, Jepsen
- 16. Step 1: Observe & document
- 17. Step 2: Create minimal reproducer • Goal: maximise the amount of debugging cycles • Focus on short development iterations / feedback loops • Get close to the action! Tools IDE, Shell scripts, SSH tunnels, Curl
- 18. Step 3: Debug client side • Focus on eliminating anything that could be wrong on the client side • Are we connecting to the right host? • Do we send the right message? • Do we receive a response? • Not much different from local debugging Tools IDE, debugger, logging
- 19. Step 4: Check DNS & routing • DNS: • Make sure you know what IP address the hostname should resolve to • Verify that this actually happens at the client • Routing: • Verify you can reach the target machine Tools host, nslookup, dig, whois, ping, traceroute, nslookup.io, dnschecker.org
- 20. Step 5: Check connection • Can we connect to the port? • If not, do we get a REJECT or a DROP? • Does the connection open and stay open? • Are we talking TLS? • What is the connection speed between us? Tools telnet, nc, curl, iperf
- 21. Step 6: Inspect traffic / messages • Do we send the right request? • Do we receive the right response? • How do we know? • How do we handle TLS? • Are there any load balancers or proxies in between? Tools curl, wireshark, tcpdump, network tab in browser, mitm/tls proxy
- 22. Step 7: Debug server side • Inspect the remote host • Can we attach a remote debugger? • See https://youtube.com/OpenValue • Profiling • Strace Tools SSH tunnels, remote debugger, profiler, strace
- 23. Step 8: Wrap up & post mortem • Document the issue: • Timeline • What did we see? • Why did it happen? • What was the impact? • How did we find out? • What did we do to mitigate and fix? • What should we do to prevent repetition? Tools Whiteboard, documentation
- 24. If you really want a reliable system, you have to understand what its failure modes are. You have to actually have witnessed it misbehaving. - Jason Cahoon “ ”
- 25. Distributed systems war stories
- 26. The time where it worked half of the time…
- 27. The one at a school…
- 29. The one with breaking news…
- 30. Summary: a structured approach to debugging distributed systems @bjschrijver Check DNS & routing Check connection Debug client side Create minimal reproducer Debug server side Observe & document Wrap up & post mortem Inspect traffic / messages
- 33. Thanks for your time. Got feedback? Tweet it! All pictures belong to their respective authors @bjschrijver







