Ad
Identity Federation on JBossAS
- 1. High Availability of Identity Federation System on JBossAS Roger Carhuatocto QA & IT Security Project Manager IN2, Ingeniería de la Información 11 October 2005
- 2. me I Worked in several Integrator Companies such as STE Consulting of the Group ALTRAN as Security and integration Consultant In Safelayer Secure Communications I was Project Manager in Horizontal Integration of PKI projects. I was responsible of Educational Services Area in esCERT-UPC (Spanish Computer Emergency Response Team of Catalonian Technical University), giving technical support to projects related to IT Security. Actually I combines my time in different initiatives related to IT Security and Open Source Projects (GOS4i, QDT-Java, INTIX-PKI and CP4DF) with leading the technical line in IN2 related to IT Security Integration for Critical Solutions.
- 3. Content The problem: Identity management User authentication, access control, privacy, anonymity, accounting, etc. Personalization, SSO, constraints on exploit identity, etc. Solutions based in standards SAML, Liberty Alliance, WS-* XML as backbone AAA: Authentication, Authorization and Attributes Solutions and products Case: IdFed System on JBossAS
- 4. Digital Identity Virtual representation of the real identity Real identity (individual identity, set of attributes): {Name=Roger, Addr=Llinars Av, DriverLic=123456, FieldEmploy=Programmer} Identifier: {Name=Roger} Authenticator (token, credential): {DriverLic=12345} Permission: {Roger can drive a Porsche} Rols that can assume: It is the vision that the rest of organizations has of the individual For electronic interactions with persons and systems The indentity never is electronic or digital, it is physic The process for establishing and validating the identity is electronic Digital identity of the individuals is distributed between a the organizations/systems whereas in each interaction with these organizations/systems a certain identity is used
- 5. Trends in Identity Mgmt Consumer Security Easy access, SSO Anonymity e-Business Consolidate relationship with customers Personalization, target ads, offers, single face to consumer Enterprise True SSO on heterogeneous environments Integration with business partners Goverment e-Goverment, constraints on how businesses exploit identity information Privacy regulations (Spain: LOPD, LSSIce)
- 6. Models of Identity Management Silo Predominant model Id-Mgmt environment is operated by a single entity for a fixed user comunity Walled garden Closed community of organizations Single Id-Mgmt System is deployed to serve the common user community of a collection of businesses. i.e B2B Federation There is no single entity that operates the Identity Mgmt System Multiple Identity Provider and partitioned store for identity information
- 7. “ A Federation is less painful than a Revolution ” Federation Two or more organizations than decide collaborate with an common objective, in this case to make business transactions or processes (trading relationships) that cross the edge of each organization (circle of trust). It is an organizational concept, nontechnician. Identity Federation Exchange information on identities between different domains and keeping full control on own identity management Allow the portability of the Digital Identity between applications and domains Liberty Alliance
- 8. Elements of an Identity Mgmt System 1/2 Basic elements: Repository (core of the system) Logical data storage facility , Identity data model (i.e. LDAP) Authentication provider / Identity provider (IdP, Asserting Party) Performing primary authentication of an individual wich will link them given identity Produce an authenticator (token) by passwd, Digital Cert (X509), smart card, etc. Policy controls (Access to and use of identity information) Authorization policies (how the information is manipulated) Privacy policies (how identity information may be disclosed) Auditing (how and by whom policy were circumvented) Management elements Provisioning / Service provider (SP, Relying Party) Manage the lifecycle of an identity: creation, linkage, setting and changing attr and privileges, decommissioning of identity Verification of data fro authority, propagate data to affiliated system Longevity (create historical record of an identity)
- 9. Elements of an Identity Mgmt System 2/2 Consumable elements: SSO Personalization Access Management Management of AAA: Authentication, Authorization and Attributes Hub of Service Hub of Identity IdP/SP IdP/SP IdP/SP IdP/SP IdP/SP Tributary agency VISA Network Healthcare public system Federation multi-provider IdP SP IdP IdP IdP IdP IdP IdP SP SP SP SP SP SP
- 10. Content The problem: Identity management User authentication, access control, privacy, anonymity, accounting, etc. Personalization, SSO, constraints on exploit identity, etc. Solutions based in standards SAML, Liberty Alliance, WS-* XML as backbone AAA: Authentication, Authorization and Attributes Solutions and products Case: IdFed System on JBossAS
- 11. Standards: SAML Service Provider ID Provider AuthN Assertion Request Credentials SAML: Security Assertion Mark-Up Language Format and protocol for asking (request) for the identity of a user who tries to enter in the system , as well as the format of the answers (response) It is a service of the applications, is transparent (hidden) to the user. The organization who emits the standard is OASIS. Based on XML, with format SOAP Transported through HTTP, HTTPs (preferred) 1 Assertion Response 2
- 12. Standards: Why SAML? May 13: Sun and Microsoft announce new identity specifications and additional measures for product interoperability: Web SSO Metadata exchange and interop profile Standards roadmap Web Federated SSO The most evolved. Hard support of the main actors of the market Confluence of Liberty 2.0 and Shibbloleth v.1.2. Last version: SAML v2.0, March 2005 Liberty ID-FF 1.1 SAML 1.0 SAML 1.1 Shibboleth 1.x Liberty ID-FF 1.2 SAML 2.0 (Mar2005) Shibboleth 2.0 (4Q2005) WS-Fed Passive interop profile SSO interop profile SSO MEX
- 13. Standards: SAML, a assertion Server which send the “assertion” Time valid of the “assertion” User being authenticated Authentication method used
- 14. Standards: SAML, functional requirements Authentication, Authorization and Attributes Necessary to develop/integrate a Gateway of IdFed for each application that we want to enable with: Web SSO Supplying and management of accounts of user federated Access control Policy for resources federated SAML does not provide: Mechanisms of login (it only transports information on login) Management of users or repositorios of credentials (ldap, etc.) Management of passwords, etc.
- 15. Solutions and products Toolkits Open Source: LASSO, SourceID, Internet2, OpenSaml Grid and SAML/ID-FF: GriShib, GridNet Comercial: Oracle (Phaos), Mycroft, Sun, PingFederate Other products SSL VPN Juniper Networks, PortWise Virtual directories Radiant Logic, OctetString, Symlabs Authorization services Bayshore Networks, Bhold, Epok, Jericho Systems XML/Web services security Actional, DataPower, Forum Systems, Layer 7, Reactivity, Sarvega, Systinet, Vordel
- 16. Content The problem: Identity management User authentication, access control, privacy, anonymity, accounting, etc. Personalization, SSO, constraints on exploit identity, etc. Solutions based in standards SAML, Liberty Alliance, WS-* XML as backbone AAA: Authentication, Authorization and Attributes Solutions and products Case: IdFed System on JBossAS
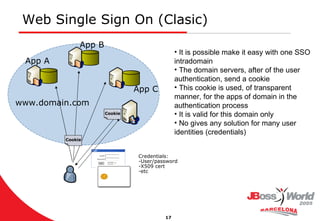
- 17. Web Single Sign On (Clasic) Credentials: User/password X509 cert etc Cookie Cookie www.domain.com App A App B App C It is possible make it easy with one SSO intradomain The domain servers, after of the user authentication, send a cookie This cookie is used, of transparent manner, for the apps of domain in the authentication process It is valid for this domain only No gives any solution for many user identities (credentials)
- 18. Cross Domain Single Sign On Credentials: User/password X509 cert etc otherdomain.com App D App E App F mydomain.com App A App B App C Plug-In Plug-In Adding a plug-in (comercial) into servers, is possible to get a interdomain SSO The servers of domain, after of user authentication, to trust its identity Is a instrisive technology, is necesary of technology agreements (generalmente bilaterales) between theys partes. Make it easy magement of many user identities (credentials) parte las múltiples identidades (credenciales) It is not scalable to multiple relationships
- 19. Identity Federation (for Web SSO) App D App E App F mydomain.com App A App B App C otherdomain.com All services enabled by adapter can: Request/Ask for identity and method of user authentication Response to others services about of identity, permissions and method of user authentication of a especific user (citizen) The servers/services denied access or not by trusting in information that the other app provide Use specifications for exchange of information of standard manner Solves multiplicity of credentials of the user by granting differents access levels to applications based in the credential security Any user can do use of credentials choosed, access into app and browsing in all applications federated Credentials: User/password X509 cert etc
- 20. Web SSO: IdFed between apps App2 App1 1 2 4 3 6 (1) User is authenticated in App1 by digital certificate (2) User logged in App1 needs to go to App2 (related to App1, but App2 uses user/password for authentication) (3) When user trying to access to App2, (4) the server request to App1 for the parameters of user identity (5) App1 sends a message with information requested, (6) App2 based in security policies gives access to the user ..vice-versa 5
- 21. Requirements for IdFed System 1. Functionality Serveral users could use it: grid infrastructure AAA, Federation policies, SSO, Nonrepudiation, Mapping and transformation of attributes, Roaming, etc. Scalability in Management of a IdFed community (many IdFed Systems), Remote configuration, etc. 2. Critical areas, potential problems Throughput, High availability, Fault tolerance/clustering, strong security, Reliable and Self Recovering, Distributed (Grid?), Several users (Grid?), etc. The standard avoid attacks such as: “replay”, “man in the middle”, etc. 3. Coexistence of protocols and evolution of standards Evolutionary NOT Revolutionary Support SAML 1.x and Liberty Alliance 2.0, Support in the future for SAML 2.0 Recently products s/WS-Federation BMC, IBM, Symlabs Microsoft AD Federation Services as part of Windows Server 2003 R2
- 22. IdFed: Common task list Normalize the repository for storing the data required for SAML Develop/Integrate a IdFed Gateway for each aplication. Define federation policies Define mechanism of sincronization between IdFed Systems SAML Gateway App1 App2 App3 SAML Gateway SAML Gateway SAML Gateway
- 23. IdFed: The gateway IDP SP SP SP Based on SAML and Opensource Use OpenSAML (generics libs in C++ and Java) Modify Lasso/SourceID (Gateway Opensource for Java y .Net) Multiprotocol?, Traductor between protocols? SAML 1.X, 2.0 Id-FF 1.X WS-FEDERATION IDP hub? SP hub? Authentication Assertion
- 24. IdFed: Federation policies Define basic policies Rols and groups Example: Users without certificate: read access to apps federated User with certificate: read-write access Best practices IdFed: Make it easy for adding new federated services to current infrastructure: Identity Providers Service Providers Attribute Providers Services of Location
- 25. JBossAS-IdFed 1. FedId Functionality AAA: JAAS/JACC Federation rules: SAML/IDFF (Liberty Alliance) Nonrepudiation, mapping of attributes and X.509 (JAAS module) IDP: JBossAS + Cluster SP: JBossAS Toolkits: Opensource or propietary 2. Critical areas Several users: grid and distributed? High availibility: Persistence with JBossMQ or grid infrastructure Autodiscovery of other FedID Gateways: multicasting Fail over: HAJNDI, Clustering, JBossMQ, Security: WS-Security, JBossSX (support non-JAAS and JAAS)
- 26. JBossAS-IdFed 3. Coexistence of protocols and evolution of standards Evolutionary NOT Revolutionary Support SAML 1.x and Liberty Alliance 2.0, Support in the future for SAML 2.0 Recently products s/WS-Federation
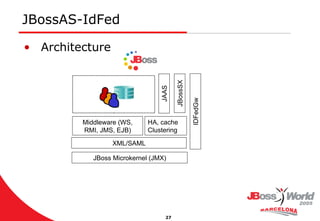
- 27. JBossAS-IdFed Architecture JAAS JBossSX IDFedGw XML/SAML Middleware (WS, RMI, JMS, EJB) JBoss Microkernel (JMX) HA, cache Clustering
- 28. High Availability of Identity Federation System on JBossAS Roger Carhuatocto QA & IT Security Project Manager IN2, Ingeniería de la Información 11 October 2005
Editor's Notes
- #2: Products JBoss AS Competitors Hibernate Competitors manual JDBC EJB 2.x (all app servers) Oracle Toplink JDO 1. 2. 3. JBossCache (JCache) Competitors OScache (OpenSymphony) Tangersol JBPM Competitors OSworkflow (OpenSympony) *WFM (http://wfmopen.sourceforge.net) Tomcat Competition JRun Weblogic Express IBM Websphere Servlet Engine *Jetty *Resin JBoss IDE Competition AppServer Specific WL Workshop WSAD (Eclipse-based) AppServer agnostic IntelliJ IDEA JBuilder *Eclipse (explain IDE-builder instead of app-builder) MyEclipse Projects Javassist Competitors ASM BCEL SERP CG-LIB (used by Spring) JBoss AOP Competitors AspectWerkz AspectJ Spring CGlib (lower level) dynaop AOPalliance JBoss Microkernel Competitors Spring Hivemind PicoContainer JBossMQ / JBossJMS Competitors IBM MQ-Series MS-MQ SonicMQ Oracle AQ *openJMS *JORAM JBoss Portal Competitors Jetspeed eXO JGroups Competitors Customers Using Ameritrade





























































































![[Webinar] Creando un "backend" con WSO2](https://cdn.slidesharecdn.com/ss_thumbnails/chakray-webinar02-creando-backend-wso2-v1-150819113016-lva1-app6892-thumbnail.jpg?width=560&fit=bounds)
![[Webinar] SOA ágil con WSO2](https://cdn.slidesharecdn.com/ss_thumbnails/chakray-webinar01-agilesoa-v1-150819112720-lva1-app6892-thumbnail.jpg?width=560&fit=bounds)
![[Webinar] Gestión Identidades y Control de Acceso en los Servicios usando WSO...](https://cdn.slidesharecdn.com/ss_thumbnails/chakray-rcarhuatocto-webinar-wso2is-1-150817121220-lva1-app6892-thumbnail.jpg?width=560&fit=bounds)
















