Know What’s in Your Containers! Manage and Secure all Open Source that Composes All Your Containers
- 1. Know What’s in Your Containers! Manage and Secure all Open Source that composes your Containers
- 2. Container Security Tool Landscape SERVER HOST OS CONTAINER ENGINE BINS / LIBS BINS / LIBS APPLICATION 1 APPLICATION 2 Static Analysis Best for Developer Custom Code Software Composition Best for Open Source Dynamic Analysis Best for Runtime DEVELOPMENT DEPLOYMENT NETWORK
- 3. We help you build secure, high-quality software faster Integrated Tools Managed Services Strategy & Planning Program Acceleration Build Security In Maturity Model (BSIMM) Static Analysis Find and fix security vulnerabilities and quality issues in your code as it’s being developed Coverity Software Composition Analysis Detect and manage open source and 3rd party component risks in development and production Black Duck Dynamic Analysis Test running applications for common security weaknesses and vulnerabilities Seeker Defensics DevSecOps Integration Architecture and Design Security Training Cloud Security Industry Solutions Maturity Action Plan (MAP)
- 4. • Full Container Scanning • Packaged Apps • Linux Distro and Other Software • Scans containers on Docker host • No need to modify containers • Deeper Identification • All Open Source in Container • Linux distribution files • Patches • Vulnerability Mapping • OSS Components and Versions Visibility and Control for Containers
- 5. State of Open Source 2018 Based on over 1,100 commercial applications analyzed by Black Duck On-Demand 17% 8% 96% 134% 54%HIGH 57%
- 6. Problem: Security Breaches 206 days Average cost of data breach: $7.35 Million Lost business: $4.03 Million Average time to identify and contain a breach: Source: 2017 Cost of Data Breach Study – Ponemon Institute
- 7. Apache Struts Strutting around? Taxes due April 30th CRA site shut down CVE-2017-5638 Reported by NVD March 10th Public Exploit March 7th Introduced v2.3.5 Fall, 2012 July 29th Equifax site shut down Reported by Nike Zheng Patch available March 6th, 2017
- 8. EnhancedVULNERABILITY DATA 10,000+SOURCES 1+ PETABYTES 80+ PROGRAMMING LANGUAGES 14 YRS OSS ACTIVITY Open Source Intelligence 60 DEDICATED KB TEAM BLACK DUCK KNOWLEDGEBASE
- 9. Black Duck Hub Architecture Hub Detect Scan Hub Web Application HTTPS On-Premise or Private Cloud Black Duck KnowledgeBase HTTPS Black Duck Datacenter
- 10. IDE SCM Build/CI QA Orchestration ProductionDeployTestBuild / CISCMCode TFS/VSTS CodeBuild CodePipeline Concourse Team City Eclipse Visual Studio GitHub Package Management Container/Binary Repositories Black Duck Integrations ECR GCR ACR Artifactory Red Hat Container Catalog Ruby Linux Package Managers XRay OpenShift1 Kubernetes1 Pivotal Cloud Foundry2 Cloud Foundry2 EC2 GCP Azure OpenShift3 Kubernetes3 1 Automatic Image scanning during orchestration 2 Automatic droplet scanning during cf push 3 Deployable on these platforms Chrome TravisGitLab
- 11. Addressing OpenShift Customer Security Needs with Automatically scan and monitor 3rd party Open Source in all container images in OpenShift Installed as an OpenShift project that is integrated into the OpenShift API. Continuously annotates and labels images and pods when vulnerabilities or policy violations occur. Operating System and application Open Source including non-curated Red Hat software. Regardless of image source or registry. Open Source software composition of the container image.
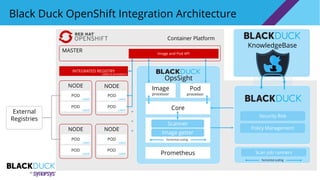
- 12. POD Container Platform Black Duck OpenShift Integration Architecture External Registries KnowledgeBase MASTER NODE NODE POD INTEGRATED REGISTRY POD POD . . . Labels Labels Labels & annotations Labels Labels NODE POD POD Labels Labels NODE POD POD Labels Labels OpsSight Image processor Pod processor Policy Management Security Risk Scan job runners horizontal scaling Core Image and Pod API Prometheus Scanner Image getter horizontal scaling
- 13. Layer Container Security For Maximum Impact üSecure Platform with Red Hat OpenShift Container Platform and RHEL Atomic Host üAdminister DISA STIG: CVE, CCE, CPE, CVSS, OVAL, and XCCDF üOVAL formatted patch definitions for Red Hat products üScan all container images in an OpenShift deployment as the are created, modified and used üProvide visibility into open source components regardless of source üAnnotate images and image streams with vulnerability information üAnnotations automatically updated as new disclosures occur – without the need for rescan
- 14. Demo!