Lcu14 306 - OP-TEE Future Enhancements
- 1. LCU14-306: OP-TEE Future Enhancements Joakim Bech, Jens Wiklander and Pascal Brand, LCU14 LCU14 BURLINGAME
- 2. Cryptographic Layer in OP-TEE ● Aim and problem ● Interaction between TA and Cryptographic Services ● Does not define how the services are implemented / data structures ● Current Status ● LibTomCrypt is the cryptographic library in OP-TEE ● End user may want to switch to ... - OpenSSL - Using ARMv8-A cryptographic extensions - Dedicated cryptographic IP ● Enhancement ● Define a low level API to easily switch from one implementation to another one.
- 3. GlobalPlatform Internal Core API 1.1 ● Current Status ● Internal API 1.0 is supported ● Enhancement ● Add support for GP Internal API 1.1 released in June 2014 ● Main updates are: - Elliptic Curve Digital Signature Algorithm (ECDSA) - Elliptic Curve Cryptography Cofactor Diffie-Hellman (ECDH) - Some errata with new error cause - Few deprecated features (object)
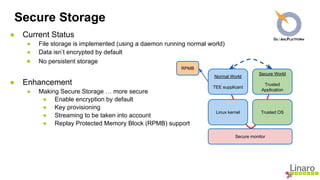
- 4. Secure Storage ● Current Status ● File storage is implemented (using a daemon running normal world) ● Data isn’t encrypted by default ● No persistent storage ● Enhancement ● Making Secure Storage … more secure ● Enable encryption by default ● Key provisioning ● Streaming to be taken into account ● Replay Protected Memory Block (RPMB) support Secure World Trusted Application Normal World TEE supplicant Linux kernel Trusted OS Secure monitor RPMB
- 5. Secure Time ● Aim and problem ● GlobalPlatform TEE Internal API defines support of the Clock ● Secure clock will be needed in DRM use cases ● Secure IP usage is specific to a given platform ● Current Status ● Only based on REE using RPC NOT Secure! ● Enhancement ● Enable clocks from both REE and Secure IP ● Create a Time API to access the Secure IP ● Fulfill TEE Internal API 1.1 requirements of maximum 15% deviation from real time
- 6. Reduce Memory Footprint ● Aim and problem ● Memory footprint of the Trusted OS part is critical ● OP-TEE enables all GlobalPlatform features by default ● Enhancement ● Make it possible to select functionality at compile time ● All cryptographic algorithms are probably not needed … ● Some functionality may not be needed (Big Number arithmetic, ...)
- 7. Multiple TA Support ● Aim ● Enable multiple TA functions to be called at the same time ● Current Status ● Threading model of the Trusted OS is ready, but not activated ● Enhancement ● Will enable multiple-TA’s running in parallel
- 8. Paging ● Aim ● Trusted OS may run on embedded memory which is small ● Enhancement ● Paging the Trusted OS would solve memory constraint ● some parts would never be paged out (mmu management,...) ● some parts could be paged in DDR (secured or encrypted)
- 9. PSCI - Power State Coordination Interface ● Aim ● Make OP-TEE aware of PSCI functions. ● Current Status ● OP-TEE aware of: CPU_ON, CPU_OFF, CPU_SUSPEND and CPU_RESUME (as stubbed functions) ● ARM-Trusted-Firmware handles ● Implemented: PSCI_VERSION, AFFINITY_INFO ● Not implemented: MIGRATE, MIGRATE_INFO_TYPE, MIGRATE_INFO_UP_CPU, SYSTEM_OFF and SYSTEM_RESET
- 10. ASLR - Address Space Layout Randomization ● Aim and problem ● Already exists in normal world (user space and kernel) ● To avoid attack like return-to-libc-attack for example ● Make it random enough! ● Enhancement ● This feature could be part of Trusted OS ● Current limitations ● We use pre-defined virtual addresses ● Trusted Applications are currently statically linked
- 11. Other Potential Enhancements ● GlobalPlatform Trusted UI 1.1 ● API to display content and capture input in a secure manner. ● User-mode TEE ● For early Trusted Applications development and debug ● Avoid the need for having a full TrustZone platform ● Support for OP-TEE in QEMU ● Virtualization team have patches enabling TrustZone functionality
- 12. More about Linaro Connect: connect.linaro.org Linaro members: www.linaro.org/members More about Linaro: www.linaro.org/about/