Lecture 06 Software Configuration Management
Download as PPTX, PDF1 like1,599 views
Lecture 06 Software Configuration Management - Course of Rekayasa Perangkat Lunak (Software Engineering) at Budi Luhur University
1 of 30
Downloaded 155 times


![The “First Law” of System Engineering
No matter where you are in the system life cycle, the
system will change, and the desire to change it will persist
throughout the life cycle. [Bersoff et al, 1980]
CS215 – Rekayasa Perangkat Lunak – Magister Ilmu Komputer Universitas Budi Luhur](https://image.slidesharecdn.com/06softwareconfigurationmanagement-151016222528-lva1-app6891/85/Lecture-06-Software-Configuration-Management-3-320.jpg)






![SCM Repository
• The SCM repository is the set of mechanisms and data structures that allow
a software team to manage change in an effective manner
• The repository performs or precipitates the following functions [For89]:
• Data integrity
• Information sharing
• Tool integration
• Data integration
• Methodology enforcement
• Document standardization
CS215 – Rekayasa Perangkat Lunak – Magister Ilmu Komputer Universitas Budi Luhur](https://image.slidesharecdn.com/06softwareconfigurationmanagement-151016222528-lva1-app6891/85/Lecture-06-Software-Configuration-Management-11-320.jpg)







![Change Control
CS215 – Rekayasa Perangkat Lunak – Magister Ilmu Komputer Universitas Budi Luhur
• Change control is vital. But the forces that make it necessary also
make it annoying. We worry about change because a tiny
perturbation in the code can create a big failure in the product.
But it can also fix a big failure or enable wonderful new
capabilities. We worry about change because a single rogue
developer could sink the project; yet brilliant ideas originate in
the minds of those rogues, and a burdensome change control
process could effectively discourage them from doing creative
work [Bac98]
• Too much change control and we create problems.Too little, and
we create other problems](https://image.slidesharecdn.com/06softwareconfigurationmanagement-151016222528-lva1-app6891/85/Lecture-06-Software-Configuration-Management-19-320.jpg)






![Content Management
CS215 – Rekayasa Perangkat Lunak – Magister Ilmu Komputer Universitas Budi Luhur
• The publishing subsystem extracts from the repository, converts it to a
form that is amenable to publication, and formats it so that it can be
transmitted to client-side browsers.The publishing subsystem accomplishes
these tasks using a series of templates.
• Each template is a function that builds a publication using one of three
different components [BOI02]:
• Static elements—text, graphics, media, and scripts that require no further processing
are transmitted directly to the client-side
• Publication services—function calls to specific retrieval and formatting services that
personalize content (using predefined rules), perform data conversion, and build
appropriate navigation links.
• External services—provide access to external corporate information infrastructure such
as enterprise data or “back-room” applications.](https://image.slidesharecdn.com/06softwareconfigurationmanagement-151016222528-lva1-app6891/85/Lecture-06-Software-Configuration-Management-26-320.jpg)




Ad
Recommended
Configuration Management



Configuration ManagementSaqib Raza A detail review of configuration and change management. This lecture provides details about how to manage different software versions of same software in a market with different customers clients and different set of functionalities.
A Brief Introduction to Software Configuration Management



A Brief Introduction to Software Configuration ManagementMd Mamunur Rashid Configuration management (CM) is the process of identifying, organizing, and controlling software changes. It aims to minimize confusion and maximize productivity by minimizing mistakes during software development. CM manages changes throughout the development process by identifying work products, establishing change control processes, and generating reports. It is important for project success and controlling quality, as uncontrolled changes can delay delivery. CM involves activities like identifying changes, controlling changes, and reporting changes. It utilizes tools like version control systems and bug trackers.
Software Configuration Management



Software Configuration ManagementArunnima B S This document discusses software configuration management (SCM). SCM is a set of activities that manage changes to software throughout its lifecycle. It involves identifying items to change, defining relationships between items, and controlling changes. The SCM process includes identifying configuration items, change control, version control, auditing, and reporting. A configuration manager plans the SCM process and oversees configuration control, auditing, and reporting. Popular SCM tools include Visual Source Safe, Concurrent Versions System, Subversion, ClearCase, and Team Foundation Server.
Software Configuration Management (SCM)



Software Configuration Management (SCM)Nishkarsh Gupta This document provides an overview of software configuration management (SCM). It defines SCM as a way to manage evolving software by controlling changes to configuration items. The key activities of SCM include identifying configuration items, establishing baselines, controlling changes through a change management process, and auditing changes. Roles in SCM include developers who implement changes and a configuration management team that manages the SCM process.
Introduction To Software Configuration Management



Introduction To Software Configuration ManagementRajesh Kumar Configuration management (CM) is a field of management that focuses on establishing and maintaining consistency of a system's or product's performance and its functional and physical attributes with its requirements, design, and operational information throughout its life.[1] For information assurance, CM can be defined as the management of security features and assurances through control of changes made to hardware, software, firmware, documentation, test, test fixtures, and test documentation throughout the life cycle of an information system.
software configuration management ppt



software configuration management pptYeshiwas Getachew This document outlines the contents of a Software Configuration Management Plan (SCMP) according to the IEEE 828 standard. It discusses that an SCMP should include sections on introduction, management, activities, schedule, resources, maintenance, and conformance to the IEEE standard. Each section is described in detail. For example, the activities section covers configuration identification, control, status accounting, audits and reviews, interface control, and subcontractor control. The document provides examples of the information that should be included in each subsection.
Configuration Management



Configuration Managementsslovepk Configuration management is used to track changes made to software systems over time. It involves planning for change management and version/release management. The objectives of configuration management are to control costs of changes and maintain evolving software products. It defines procedures for tracking changes, managing versions and releases, and building systems from components.
Software Configuration Management (SCM)



Software Configuration Management (SCM)Er. Shiva K. Shrestha SCM, is an umbrella activity that is applied throughout the software process, control of the evolution of complex systems.
Software configuration items



Software configuration itemsashok kumar This document defines software configuration items and discusses how to identify them. It states that configuration items include any hardware, software, or documents related to a software project's development, such as code files, test drivers, design documents, manuals, and system configurations. Large projects can produce thousands of potential configuration items, so an entity naming scheme should be used to uniquely identify and relate items. Common configuration items include requirements, design documents, source code, test data, and support software. Once identified, configuration items are typically organized in a tree structure.
5. scm



5. scmSagar Pednekar This document provides an overview of software configuration management (SCM). SCM is an umbrella activity that manages changes to software deliverables throughout the development process. It identifies work products that may change, establishes relationships between them, defines version control mechanisms, controls changes, and audits and reports on changes made. The key aspects of SCM covered are baselines, the SCM process, software configuration items, version control, change control, configuration auditing, and status reporting.
Software configuration management



Software configuration managementfizamustanser Software configuration management (SCM) involves managing changes to software throughout its lifecycle. SCM activities are needed because software often needs to change for reasons like new requirements, bugs, or scheduling issues. SCM defines processes and tools to make changes in a controlled manner. It involves roles like configuration managers, programmers, and users. SCM uses concepts like baselines, which are approved versions of software that further development is based on, and software configuration items (SCIs) which are components of a software system that are managed and tracked by the SCM system.
Software Configuration Management



Software Configuration ManagementChandan Chaurasia The document discusses configuration management for software engineering projects. It covers topics such as configuration management planning, change management, version and release management, and the use of CASE tools to support configuration management. Configuration management aims to manage changes to software products and control system evolution through activities like change control, version control, and configuration auditing.
Software configuration management



Software configuration managementJulia Carolina The document discusses software configuration management. It defines SCM as using configuration management tools to store versions of system components and build systems from these components while monitoring released versions. The purposes of SCM are to identify, control, and ensure proper implementation of changes as well as report changes. SCM applies to software code, data, documents, and other project materials. Factors that affect proposed changes and the concept of baselines, which serve as a basis for development, are also discussed. Finally, the typical format of a configuration management plan is outlined.
software configuratiom management role n resposnbilities



software configuratiom management role n resposnbilitiesMahesh Panchal The document discusses various roles and responsibilities in software configuration management. It describes the roles of configuration control board, configuration manager, configuration item owner, configuration librarian, configuration auditor, support manager, and person in a role. It also discusses configuration management tools, selecting configuration items, configuration audits, and the configuration librarian role.
Configuration management



Configuration managementashamarsha This document discusses software configuration management. It defines key terms like software configuration item and version. It describes the four main classes of SCIs - design documents, software code, data files, and development tools. It outlines the main tasks of SCM like control of software changes, release of versions, provision of information, and compliance verification. It also discusses topics like change control, approval of changes, release types, numeration conventions, configuration management plans, and evolution models.
Software configuration management in deep



Software configuration management in deepFáber D. Giraldo The document discusses software configuration management (SCM) and its core components of identify, control, audit, and report. It describes how SCM focuses on managing changes through identifying configuration items, controlling changes, auditing baselines, and reporting items. The key practices of SCM are then defined, including planning, version control, change control, build management, release management, problem management, and reporting.
Software Configuration Management



Software Configuration ManagementJeyanthiR The document discusses the need for software configuration management to control changes, versions, and revisions during development. It describes the basic functions of configuration management including configuration control, change management, revisions, versions, deltas, and conditional code. The roles and responsibilities of the configuration manager, module owners, and change control board in software configuration management are also outlined.
Configuration Management 



Configuration Management hdicapitalarea The document outlines plans for establishing a Configuration Management System (CMS) to manage the full lifecycle of IT and service assets. The key aspects of the CMS plan include:
1) Establishing controls over assets and configuration items (CIs) from initial planning through maintenance and problem resolution.
2) Developing processes for identifying, documenting, and maintaining CI baselines and releases.
3) Implementing status reporting, auditing, and verification to ensure the CMS accurately reflects physical environments.
4) Integrating the CMS with related service management processes like change and release management.
Software configuration management



Software configuration managementShivani Garg The document discusses software configuration management (SCM) which controls the evolution of complex software systems. SCM provides capabilities like identification, control, status tracking, auditing and reviewing of software work products. The goals of SCM include planning activities, identifying and controlling selected work products, managing changes, and informing groups of status. Objectives include remote administration, reliability, setup ease and more. The document also discusses configuration management processes, baselines, change management processes and tools, and version control.
Configuration Management



Configuration Managementelliando dias Software configuration management is important for controlling changes, monitoring versions, and maintaining traceability during software development. It involves identifying configuration items, controlling releases and changes, recording status, and auditing products. Key aspects include defining baselines, establishing a configuration control board to approve changes, using version control and change control processes, and managing baselines and workspaces. Tools and training are needed to implement configuration management practices.
SE2_Lec 22_Software Configuration Management



SE2_Lec 22_Software Configuration ManagementAmr E. Mohamed The document discusses software configuration management. It defines key terms like configuration item, version, revision, and baseline. It describes the main functions of configuration management as configuration identification, configuration control, configuration audits, and configuration status accounting. Configuration management is used to identify and track changes to software components, control access to components, and help integrate product parts.
Software Configuration Management



Software Configuration ManagementJeyanthiR This document outlines a software configuration management plan, including its objectives to define responsibilities, approaches, and methods used. It describes the contents of the plan such as baselines, identification systems, change control procedures, implementation checkpoints, and tools to support configuration management. The document also provides examples of questions to consider in requirements, design, implementation, and testing phases and discusses configuration auditing.
Software Configuration Management



Software Configuration Managementelliando dias Software Configuration Management (CM) establishes and maintains product integrity throughout development. CM involves four key functions: identification, control, status accounting, and audits of configuration items. CM planning tasks include identifying items, baselines, and roles. CM execution tasks are configuration control, status accounting, and audits. CM records like plans, schedules, change requests, audit results must be organized and maintained.
Software maintenance and configuration management, software engineering



Software maintenance and configuration management, software engineeringRupesh Vaishnav Types of Software Maintenance, Re-Engineering, Reverse Engineering, Forward Engineering, The SCM Process, Identification of Objects in the Software Configuration, Version
Control and Change Control
Software Configuration Management



Software Configuration ManagementVirendra Thakur The document discusses software configuration management (SCM), including its definition, need, elements, roles and access levels, and version numbering. SCM involves managing project items like software, code, and artifacts in a structured way, securing them for privileged users only, and controlling modifications. It establishes configuration identification, control over elements like libraries and access, and change management.
Software re engineering



Software re engineeringdeshpandeamrut Software re-engineering is a process of examining and altering a software system to restructure it and improve maintainability. It involves sub-processes like reverse engineering, redocumentation, and data re-engineering. Software re-engineering is applicable when some subsystems require frequent maintenance and can be a cost-effective way to evolve legacy software systems. The key advantages are reduced risk compared to new development and lower costs than replacing the system entirely.
Configuration Management Best Practices



Configuration Management Best PracticesTechWell Robust configuration management (CM) practices are essential for creating continuous builds to support agile’s integration and testing demands, and for rapidly packaging, releasing, and deploying applications into production. Classic CM—identifying system components, controlling change, reporting the system’s configuration, and auditing—won’t do the trick anymore. Bob Aiello presents an in-depth tour of a more robust and powerful approach to CM consisting of six key functions: source code management, build engineering, environment management, change management and control, release management, and deployment. Bob describes current and emerging CM trends—support for agile development, cloud computing, and mobile apps development—and reviews the industry standards and frameworks essential in CM today. Take back an integrated approach to establish proper IT governance and compliance using the latest CM practices while offering development teams the most effective CM practices available today.
Change And Configuration Management Market Volume Analysis, size, share and K...



Change And Configuration Management Market Volume Analysis, size, share and K...Monica Nerkar Change and configuration management is gradually gaining importance across enterprises due to its several benefits such as reduction in cost as it avoids unnecessary duplication due to knowledge of all the elements required for configuration, provides greater agility and faster problem resolution, thus giving better quality of service. In addition to this, change and configuration management have the ability to define and enforce formal policies and procedures that govern asset identification, status monitoring, and auditing and offers enhanced efficiencies, stability and control by improving visibility and tracking. Hence by configuring an efficient change and configuration management system, an enterprise can achieve greater levels of security and minimize the risk factor involved in any project.
Configuration management system comes into picture if there is any change related to the development of the product, for example if a new feature is added into the scope during the development phase of the product. Change management system is relevant when there is a change related to the timeline or the cost of the project.
software configuration management



software configuration managementFáber D. Giraldo This document discusses software configuration management (SCM). It provides definitions of SCM from sources like IEEE standards and the SWEBOK. SCM is defined as the process of managing changes to software projects through their lifecycle. Key aspects of SCM discussed include configuration items, versions and variants, baselines, change requests, SCM tools, and the unified change management process.
Software Configuration Management



Software Configuration Managementguy_davis This document discusses software configuration management principles and practices. It begins with an introduction to configuration management and its history. The main principles of SCM are then outlined, including configuration identification, change control, configuration status accounting, and configuration audits/reviews. The document also discusses SCM automation and tools, challenges in SCM, and provides a comparison of various SCM tools.
Ad
More Related Content
What's hot (20)
Software configuration items



Software configuration itemsashok kumar This document defines software configuration items and discusses how to identify them. It states that configuration items include any hardware, software, or documents related to a software project's development, such as code files, test drivers, design documents, manuals, and system configurations. Large projects can produce thousands of potential configuration items, so an entity naming scheme should be used to uniquely identify and relate items. Common configuration items include requirements, design documents, source code, test data, and support software. Once identified, configuration items are typically organized in a tree structure.
5. scm



5. scmSagar Pednekar This document provides an overview of software configuration management (SCM). SCM is an umbrella activity that manages changes to software deliverables throughout the development process. It identifies work products that may change, establishes relationships between them, defines version control mechanisms, controls changes, and audits and reports on changes made. The key aspects of SCM covered are baselines, the SCM process, software configuration items, version control, change control, configuration auditing, and status reporting.
Software configuration management



Software configuration managementfizamustanser Software configuration management (SCM) involves managing changes to software throughout its lifecycle. SCM activities are needed because software often needs to change for reasons like new requirements, bugs, or scheduling issues. SCM defines processes and tools to make changes in a controlled manner. It involves roles like configuration managers, programmers, and users. SCM uses concepts like baselines, which are approved versions of software that further development is based on, and software configuration items (SCIs) which are components of a software system that are managed and tracked by the SCM system.
Software Configuration Management



Software Configuration ManagementChandan Chaurasia The document discusses configuration management for software engineering projects. It covers topics such as configuration management planning, change management, version and release management, and the use of CASE tools to support configuration management. Configuration management aims to manage changes to software products and control system evolution through activities like change control, version control, and configuration auditing.
Software configuration management



Software configuration managementJulia Carolina The document discusses software configuration management. It defines SCM as using configuration management tools to store versions of system components and build systems from these components while monitoring released versions. The purposes of SCM are to identify, control, and ensure proper implementation of changes as well as report changes. SCM applies to software code, data, documents, and other project materials. Factors that affect proposed changes and the concept of baselines, which serve as a basis for development, are also discussed. Finally, the typical format of a configuration management plan is outlined.
software configuratiom management role n resposnbilities



software configuratiom management role n resposnbilitiesMahesh Panchal The document discusses various roles and responsibilities in software configuration management. It describes the roles of configuration control board, configuration manager, configuration item owner, configuration librarian, configuration auditor, support manager, and person in a role. It also discusses configuration management tools, selecting configuration items, configuration audits, and the configuration librarian role.
Configuration management



Configuration managementashamarsha This document discusses software configuration management. It defines key terms like software configuration item and version. It describes the four main classes of SCIs - design documents, software code, data files, and development tools. It outlines the main tasks of SCM like control of software changes, release of versions, provision of information, and compliance verification. It also discusses topics like change control, approval of changes, release types, numeration conventions, configuration management plans, and evolution models.
Software configuration management in deep



Software configuration management in deepFáber D. Giraldo The document discusses software configuration management (SCM) and its core components of identify, control, audit, and report. It describes how SCM focuses on managing changes through identifying configuration items, controlling changes, auditing baselines, and reporting items. The key practices of SCM are then defined, including planning, version control, change control, build management, release management, problem management, and reporting.
Software Configuration Management



Software Configuration ManagementJeyanthiR The document discusses the need for software configuration management to control changes, versions, and revisions during development. It describes the basic functions of configuration management including configuration control, change management, revisions, versions, deltas, and conditional code. The roles and responsibilities of the configuration manager, module owners, and change control board in software configuration management are also outlined.
Configuration Management 



Configuration Management hdicapitalarea The document outlines plans for establishing a Configuration Management System (CMS) to manage the full lifecycle of IT and service assets. The key aspects of the CMS plan include:
1) Establishing controls over assets and configuration items (CIs) from initial planning through maintenance and problem resolution.
2) Developing processes for identifying, documenting, and maintaining CI baselines and releases.
3) Implementing status reporting, auditing, and verification to ensure the CMS accurately reflects physical environments.
4) Integrating the CMS with related service management processes like change and release management.
Software configuration management



Software configuration managementShivani Garg The document discusses software configuration management (SCM) which controls the evolution of complex software systems. SCM provides capabilities like identification, control, status tracking, auditing and reviewing of software work products. The goals of SCM include planning activities, identifying and controlling selected work products, managing changes, and informing groups of status. Objectives include remote administration, reliability, setup ease and more. The document also discusses configuration management processes, baselines, change management processes and tools, and version control.
Configuration Management



Configuration Managementelliando dias Software configuration management is important for controlling changes, monitoring versions, and maintaining traceability during software development. It involves identifying configuration items, controlling releases and changes, recording status, and auditing products. Key aspects include defining baselines, establishing a configuration control board to approve changes, using version control and change control processes, and managing baselines and workspaces. Tools and training are needed to implement configuration management practices.
SE2_Lec 22_Software Configuration Management



SE2_Lec 22_Software Configuration ManagementAmr E. Mohamed The document discusses software configuration management. It defines key terms like configuration item, version, revision, and baseline. It describes the main functions of configuration management as configuration identification, configuration control, configuration audits, and configuration status accounting. Configuration management is used to identify and track changes to software components, control access to components, and help integrate product parts.
Software Configuration Management



Software Configuration ManagementJeyanthiR This document outlines a software configuration management plan, including its objectives to define responsibilities, approaches, and methods used. It describes the contents of the plan such as baselines, identification systems, change control procedures, implementation checkpoints, and tools to support configuration management. The document also provides examples of questions to consider in requirements, design, implementation, and testing phases and discusses configuration auditing.
Software Configuration Management



Software Configuration Managementelliando dias Software Configuration Management (CM) establishes and maintains product integrity throughout development. CM involves four key functions: identification, control, status accounting, and audits of configuration items. CM planning tasks include identifying items, baselines, and roles. CM execution tasks are configuration control, status accounting, and audits. CM records like plans, schedules, change requests, audit results must be organized and maintained.
Software maintenance and configuration management, software engineering



Software maintenance and configuration management, software engineeringRupesh Vaishnav Types of Software Maintenance, Re-Engineering, Reverse Engineering, Forward Engineering, The SCM Process, Identification of Objects in the Software Configuration, Version
Control and Change Control
Software Configuration Management



Software Configuration ManagementVirendra Thakur The document discusses software configuration management (SCM), including its definition, need, elements, roles and access levels, and version numbering. SCM involves managing project items like software, code, and artifacts in a structured way, securing them for privileged users only, and controlling modifications. It establishes configuration identification, control over elements like libraries and access, and change management.
Software re engineering



Software re engineeringdeshpandeamrut Software re-engineering is a process of examining and altering a software system to restructure it and improve maintainability. It involves sub-processes like reverse engineering, redocumentation, and data re-engineering. Software re-engineering is applicable when some subsystems require frequent maintenance and can be a cost-effective way to evolve legacy software systems. The key advantages are reduced risk compared to new development and lower costs than replacing the system entirely.
Configuration Management Best Practices



Configuration Management Best PracticesTechWell Robust configuration management (CM) practices are essential for creating continuous builds to support agile’s integration and testing demands, and for rapidly packaging, releasing, and deploying applications into production. Classic CM—identifying system components, controlling change, reporting the system’s configuration, and auditing—won’t do the trick anymore. Bob Aiello presents an in-depth tour of a more robust and powerful approach to CM consisting of six key functions: source code management, build engineering, environment management, change management and control, release management, and deployment. Bob describes current and emerging CM trends—support for agile development, cloud computing, and mobile apps development—and reviews the industry standards and frameworks essential in CM today. Take back an integrated approach to establish proper IT governance and compliance using the latest CM practices while offering development teams the most effective CM practices available today.
Change And Configuration Management Market Volume Analysis, size, share and K...



Change And Configuration Management Market Volume Analysis, size, share and K...Monica Nerkar Change and configuration management is gradually gaining importance across enterprises due to its several benefits such as reduction in cost as it avoids unnecessary duplication due to knowledge of all the elements required for configuration, provides greater agility and faster problem resolution, thus giving better quality of service. In addition to this, change and configuration management have the ability to define and enforce formal policies and procedures that govern asset identification, status monitoring, and auditing and offers enhanced efficiencies, stability and control by improving visibility and tracking. Hence by configuring an efficient change and configuration management system, an enterprise can achieve greater levels of security and minimize the risk factor involved in any project.
Configuration management system comes into picture if there is any change related to the development of the product, for example if a new feature is added into the scope during the development phase of the product. Change management system is relevant when there is a change related to the timeline or the cost of the project.
Viewers also liked (20)
software configuration management



software configuration managementFáber D. Giraldo This document discusses software configuration management (SCM). It provides definitions of SCM from sources like IEEE standards and the SWEBOK. SCM is defined as the process of managing changes to software projects through their lifecycle. Key aspects of SCM discussed include configuration items, versions and variants, baselines, change requests, SCM tools, and the unified change management process.
Software Configuration Management



Software Configuration Managementguy_davis This document discusses software configuration management principles and practices. It begins with an introduction to configuration management and its history. The main principles of SCM are then outlined, including configuration identification, change control, configuration status accounting, and configuration audits/reviews. The document also discusses SCM automation and tools, challenges in SCM, and provides a comparison of various SCM tools.
BW+KKS=BCO



BW+KKS=BCOWayne Acourt The document summarizes the design and construction of BW's new 1,000 sqm office space in London. Key details include:
- The design was inspired by the building's iconic Old Bailey location near St. Paul's Cathedral, seen in the angular carpet patterns and metal screens wrapping the reception area.
- The space was designed to reflect BW's values of quality, collaboration, and putting people first, with a welcoming reception, open workspaces, and meeting rooms equipped for clients and staff.
- The project was completed on time and on budget in August 2016, providing modern, sustainable workspace for BW's 130 employees while adhering to their high standards for client projects.
Data flow diagram for order system



Data flow diagram for order systemUpendra Sengar The document is a data flow diagram for an order system. It shows the flow of data between customers, the warehouse, and the order system. The order system receives new customer information and order details from customers. It then processes the orders, updating the inventory and creating picking slips for the warehouse. The warehouse packs and ships the orders, then provides shipping information back to the order system. The order system produces invoices and statements for customers.
Java fx tools



Java fx toolsTom Schindl This document discusses using JavaFX and e(fx)clipse to build code editors and IDEs. It provides an overview of JavaFX and its limitations for building tools. e(fx)clipse adds Eclipse functionality like file explorers and docking frameworks. It demonstrates building a simple editor and expanding it to an IDE. It also shows how to implement syntax highlighting using Eclipse Text and customize the appearance. Finally, it discusses integrating Xtext languages by generating IDE support that works with JavaFX without OSGi or Eclipse dependencies.
Improving Your Interview Skills for Residency 2007



Improving Your Interview Skills for Residency 2007Victor Castilla The document provides tips for improving interview skills for medical residency positions. It advises preparing by researching the hospital, program, and specialty, and developing examples from one's background to demonstrate skills. During the interview, the tips recommend presenting oneself professionally through attire, body language, and focusing answers on fit and interest in the program while staying positive. The goal is to effectively communicate one's qualifications and passion for the position.
Atomic CLI scan



Atomic CLI scanLalatendu Mohanty Introduction to OpenSCAP project and atomic CLI from Project Atomic to scan Linux containers and images for CVEs.
Networking Overview for Docker Platform



Networking Overview for Docker PlatformAditya Patawari This document provides an overview of networking in the Docker platform. It discusses the default Docker networks of none, host and bridge. It also covers user-defined networks like bridge and overlay networks. The key challenges with applications are that they are multi-tiered, dependent on other applications and third party APIs, with components residing across different containers. Docker networking aims to address these challenges.
Docker serverless v1.0



Docker serverless v1.0Thomas Chacko Serverless computing is a cloud-native paradigm where developers build and run applications without managing infrastructure. It involves short-running, stateless functions that are triggered by events. With serverless, applications automatically scale up or down based on usage, and customers only pay for the compute time used. The document discusses serverless offerings from various cloud providers, demos serverless architectures using Docker containers, and notes serverless is well-suited for event-driven workloads like mobile backends and IoT but not long-running stateful processes.
What's New in Docker 1.12?



What's New in Docker 1.12?Ajeet Singh Raina Docker Engine 1.12 can be rightly called ” A Next Generation Docker Clustering & Distributed System”. Though Docker Engine 1.12 Final Release is around corner but the recent RC3 brings lots of improvements and exciting features. One of the major highlight of this release is Docker Swarm Mode which provides powerful yet optional ability to create coordinated groups of decentralized Docker Engines. Swarm Mode combines your engine in swarms of any scale. It’s self-organizing and self-healing. It enables infrastructure-agnostic topology.The newer version democratizes orchestration with out-of-box capabilities for multi-container on multi-host app deployments.
Data Flow Diagram (DFD)



Data Flow Diagram (DFD)Anowar Hossain Data flow Diagram
In this presentation we are going to briefly
Describe what is DFD.
Why Should Use DFD ?
Components of a generic DFD.
Levels of DFD.
DFD with an example (SMS Mela).
Interview Skills



Interview SkillsUniversity of Sussex, Careers & Employability Centre This document provides an overview of interview skills and preparation. It discusses:
1. The types of interviews including face-to-face, video call, phone and Skype formats.
2. How to prepare for different types of common questions, like motivational, competency, and technical questions. The STAR model is introduced to structure answers.
3. The importance of researching the employer, practicing answers, maintaining a confident body language and tone, and asking thoughtful questions.
Proper preparation and presentation of skills and experiences are emphasized as key to performing well in interviews.
Docker Security Overview



Docker Security OverviewSreenivas Makam This document summarizes Docker security features as of release 1.12. It discusses key security modules like namespaces, cgroups, capabilities, seccomp, AppArmor/SELinux that provide access control and isolation in Docker containers. It also covers multi-tenant security, image signing, TLS for daemon access, and best practices like using official images and regular updates.
Interview Skills



Interview SkillsAnne-Mart Olsen The document provides guidance on interview skills and preparing for a job interview. It discusses the importance of first impressions and body language during an interview. Specific tips covered include dressing appropriately, maintaining good posture, making eye contact, and arriving early. The document also reviews common interview questions and advises preparing examples and stories to highlight your relevant skills and experience. Overall, it stresses the importance of researching the company beforehand, communicating enthusiasm for the role, and thanking the interviewer.
Logo design.ppt



Logo design.pptmcglp This document discusses key principles of logo design including balance, rhythm, proportion, unity, and dominance. It provides examples of logos that demonstrate each principle. Balance is shown through symmetrical logos. Rhythm is shown through regular or progressive spacing. Proportion creates depth or importance through varying element sizes. Unity connects disparate elements into a cohesive whole. Dominance guides the eye through prominent placement or sizing of key elements.
Data Flow Diagram



Data Flow DiagramPuneet Arora The document discusses data flow diagrams (DFDs) including:
- DFD symbols such as processes, data flows, data stores, and external entities
- Rules for connecting the symbols
- How to create context diagrams and level-0 DFDs to break down a system
- Strategies for developing DFDs such as top-down and bottom-up
It provides an example of drawing a context diagram and level-0 DFD for an order system.
Design concepts and principles



Design concepts and principlessaurabhshertukde The document describes key components of software design including data design, architectural design, interface design, and procedural design. It discusses the goals of the design process which are to implement requirements, create an understandable guide for code generation and testing, and address implementation from data, functional, and behavioral perspectives. The document also covers concepts like abstraction, refinement, modularity, program structure, data structures, software procedures, information hiding, and cohesion and coupling.
Dfd examples



Dfd examplesMohit The document describes data flow diagrams (DFDs), including how they differ from flowcharts by showing the flow of data rather than control flow. It then provides steps for creating DFDs using an example of a lemonade stand: 1) List activities, 2) Create a context-level DFD identifying sources and sinks, 3) Create a level 0 DFD identifying subprocesses, and 4) Create level 1 DFDs decomposing subprocesses and identifying data stores.
How to make effective presentation



How to make effective presentationSatyajeet Singh The document provides tips for designing effective PowerPoint presentations. It recommends making slides big, simple, clear, progressive and consistent. Specifically, it suggests using large font sizes, simple language and visuals, clear contrasts and focal points, focusing on key points progressively, and maintaining consistency in design elements. The document also provides tips for presenting, such as speaking loudly and making eye contact with the audience.
Ad
Similar to Lecture 06 Software Configuration Management (20)
Unit 6 Software Configuration Management



Unit 6 Software Configuration ManagementKanchanPatil34 The document discusses software configuration management (SCM), which involves identifying, controlling, and tracking changes made to software deliverables throughout development. SCM aims to maximize productivity by minimizing mistakes from changes. Key SCM activities include identifying configuration items, controlling changes through a change control board, managing different versions, and auditing configurations. The SCM process centers around an automated repository that stores configuration items and their relationships to support tasks like change management and version control.
Software configuration management, Web engineering



Software configuration management, Web engineeringdivyammo Software configuration management, Web engineering
Mod5-SCM.ppt



Mod5-SCM.pptdivyammo The document discusses software configuration management. It defines configuration management as activities that manage changes throughout the software life cycle. The key goals are to systematically control changes to the configuration and maintain integrity and traceability. Important concepts discussed include software configuration items, baselines, version control, change control processes, and content management for web applications. Secure coding practices are also summarized to develop software that is protected against security vulnerabilities.
Mod5-SCM.ppt



Mod5-SCM.pptdivyammo The document discusses software configuration management. It defines configuration management as activities that manage change throughout the software life cycle. The key goals are to systematically control changes to the configuration and maintain integrity and traceability. Important concepts discussed include software configuration items, baselines, version control, change control processes, auditing and the configuration management repository.
Fa10 mcs-005



Fa10 mcs-005Danish Nauman The document discusses software configuration management (SCM). It defines SCM as identifying, organizing, and controlling modifications to software being built by a programming team, with the goal of maximizing productivity by minimizing mistakes. SCM involves activities to identify, control, and track changes throughout the software development process. An important part of SCM is the repository, which stores software configuration items and allows developers to manage changes effectively.
lecture14.ppt



lecture14.pptubaidullah75790 This document provides an overview of software configuration management (SCM). It defines SCM as the process of managing changes to software work products throughout development. The key aspects of SCM discussed include configuration items, baselines, version control, change control, and configuration status reporting. SCM aims to identify work products that may change, define how to manage different versions, and control changes while auditing and reporting on them.
Software Configuration Management introduction



Software Configuration Management introductionMani Deepak Choudhry This document provides an overview of software configuration management (SCM). It defines SCM as the process of managing changes to software work products throughout development. The key aspects of SCM discussed include configuration items, baselines, version control, change control, and configuration status reporting. SCM aims to identify work products that may change, define how to manage different versions, and control changes to maintain software quality.
Configuration Managment Powerpoint



Configuration Managment PowerpointJeannine Jacobs, MS The document discusses software configuration management (SCM) which deals with managing changes to software, documenting changes, organizing approved software versions, and providing information about versions. It defines key SCM concepts like software configuration items (SCIs), configuration versions, and change control boards. It also discusses SCM best practices like defining control levels and responsibilities, identifying SCIs, and establishing configuration management tools and libraries. The document provides examples of SCM audits and risks of partial compliance with SCM procedures. It references additional resources on SCM tools, practices, and training.
Voyager scm



Voyager scmSivaprasanthRentala1975 SCM (Software Configuration Management) is the foundation of any software project. It provides visibility into the status of the evolving software through configuration identification, control, status accounting, and audits. This ensures everyone knows who made changes, what changes were made, when, and why. SCM addresses issues like double maintenance, simultaneous updates, and unknown versions. It benefits developers, managers, QA, and customers. SCM involves identifying configuration items, establishing baselines, document control, version control, change management, and status reporting. It helps track the current software configuration and changes made over time.
Voyager scm



Voyager scmsivaprasanth rentala SCM (Software Configuration Management) is the foundation of any software project. It provides visibility into the status of the evolving software through configuration identification, control, status accounting, and audits. This ensures everyone knows who made changes, what changes were made, when, and why. SCM addresses issues like double maintenance, simultaneous updates, and missing/unknown versions. It benefits developers, managers, QA, and customers. SCM involves identifying configuration items, establishing baselines, document control, version control, change management, and status reporting. It helps track and manage the different versions, releases, changes made to the software over time.
SE-Lecture-8.pptx



SE-Lecture-8.pptxvishal choudhary The document discusses configuration management and software configuration management (SCM) concepts. It defines key SCM terms like baseline, software configuration item, and configuration. It describes the SCM process which includes identification, version control, change control, configuration auditing, and status reporting. Challenges of SCM in component-based software development are also covered. Effective SCM is important for software projects to manage changes and maintain integrity across software versions and releases.
Software Engineering (Software Configuration Management)



Software Engineering (Software Configuration Management)ShudipPal This document provides an overview of software configuration management (SCM) concepts and definitions. It discusses SCM as the discipline for systematically controlling changes to software systems throughout the software life cycle. The key activities of SCM are identified as configuration identification, configuration change control, configuration status accounting, and configuration auditing. Baselines, configuration items, and the importance of SCM are also summarized.
chapter no 2softwareprocess-160107000546.f



chapter no 2softwareprocess-160107000546.fDuaRajpoot2 In software , you can write code to find words that begin or end with double letters from a list of words.
SE2018_Lec 21_ Software Configuration Management (SCM)



SE2018_Lec 21_ Software Configuration Management (SCM)Amr E. Mohamed Configuration management is a software engineering discipline that involves identifying and managing the configuration of software assets such as code, documents, and other project artifacts. It aims to control modifications to software and maintain integrity and traceability throughout the development and maintenance lifecycles. Key aspects of configuration management include configuration identification, change control, configuration management planning, builds, and tools.
Lecture 02 Software Process Model



Lecture 02 Software Process ModelAchmad Solichin Lecture 02 Software Process Model
Course of Rekayasa Perangkat Lunak (Software Engineering) at Budi Luhur University
Software process



Software processJennifer Polack The software process involves specification, design and implementation, validation, and evolution activities. It can be modeled using plan-driven approaches like the waterfall model or agile approaches. The waterfall model involves separate sequential phases while incremental development interleaves activities. Reuse-oriented processes focus on assembling systems from existing components. Real processes combine elements of different models. Specification defines system requirements through requirements engineering. Design translates requirements into a software structure and implementation creates an executable program. Validation verifies the system meets requirements through testing. Evolution maintains and changes the system in response to changing needs.
Course Lecture Slide about object oriented programming



Course Lecture Slide about object oriented programmingamare63 about object oriented programming course
Bse 3105 lecture 6-configuration management



Bse 3105 lecture 6-configuration managementAlonzee Tash Configuration management involves managing changes to software systems. It aims to control the costs and effort of system changes. Key CM activities include planning, change management, version management, and system building. CASE tools can support CM processes by managing configuration data, tracking changes and versions, and automating system building. Effective CM relies on document naming schemes, version identification standards, and processes for changes, releases, and daily builds.
Scm



ScmSyed Muhammad Hammad This document discusses software configuration management (SCM). It defines SCM as coordinating software development to minimize confusion from changes. The key goals of SCM are to maximize productivity by minimizing mistakes through analyzing, recording, reporting, and controlling changes. SCM provides visibility, traceability, and formal control over a software configuration and the evolution of the software. The document outlines the main functions of SCM, including identification, control, auditing, and status reporting of software configuration items and changes. It also discusses sources of change, baselines, issues to consider, and standards for SCM.
Ad
More from Achmad Solichin (20)
Kuliah Umum - Tips Publikasi Jurnal SINTA untuk Mahasiswa Galau (6 Agustus 2022)



Kuliah Umum - Tips Publikasi Jurnal SINTA untuk Mahasiswa Galau (6 Agustus 2022)Achmad Solichin Kuliah Umum - Tips Publikasi Jurnal SINTA untuk Mahasiswa Galau (6 Agustus 2022)
Diselenggarakan oleh Magister Ilmu Komputer, Universitas Budi LUhur.
Materi Webinar Web 3.0 (16 Juli 2022)



Materi Webinar Web 3.0 (16 Juli 2022)Achmad Solichin Materi Webinar "Introducting Web 3.0" yang diselenggarakan oleh BEM FTI Universitas Budi Luhur pada hari Sabtu, 16 Juli 2022.
Webinar: Kesadaran Keamanan Informasi (3 Desember 2021)



Webinar: Kesadaran Keamanan Informasi (3 Desember 2021)Achmad Solichin Berikut ringkasan dari dokumen tersebut dalam 3 kalimat:
Dokumen tersebut membahas tentang kesadaran keamanan informasi, termasuk ancaman seperti phishing, malware, kelemahan password, dan penggunaan media removable yang tidak aman. Dianjurkan untuk selalu waspada terhadap email mencurigakan, situs web tidak dikenal, serta berhati-hati dalam berbagi informasi pribadi di internet. Keamanan informasi perlu menjadi perhatian ut
Webinar PHP-ID: Mari Mengenal Logika Fuzzy (Fuzzy Logic)



Webinar PHP-ID: Mari Mengenal Logika Fuzzy (Fuzzy Logic)Achmad Solichin Derajat keanggotaan untuk banyaknya pakaian = 50 adalah:
μSEDIKIT(50) = 50-40/80-40 = 0.25
μBANYAK(50) = 50-40/80-40 = 0.25
Webinar PHP-ID: Machine Learning dengan PHP



Webinar PHP-ID: Machine Learning dengan PHPAchmad Solichin Materi webinar yang diselenggarakan oleh PHP Indonesia secara live di Facebook PHP-ID. Topik yang dibahas mengenai Machine Learning dengan PHP, baik sisi konsep maupun implementasinya.
Webinar Data Mining dengan Rapidminer | Universitas Budi Luhur



Webinar Data Mining dengan Rapidminer | Universitas Budi LuhurAchmad Solichin This document discusses data mining and the RapidMiner tool. It defines data mining as a discipline that studies methods for extracting knowledge or finding patterns from large amounts of data. It outlines the CRISP-DM process for data mining including data collection, preprocessing, modeling, evaluation, and knowledge. Common data preprocessing, modeling techniques like classification, clustering and association, and performance metrics are described. RapidMiner is presented as a popular open-source tool for visualizing the data mining process with an intuitive graphical user interface.
TREN DAN IDE RISET BIDANG DATA MINING TERBARU



TREN DAN IDE RISET BIDANG DATA MINING TERBARUAchmad Solichin Presentasi ini menyajikan Tren dan Ide Riset Bidang DATA MINING Tahun ini. Wajib disimak! Disertai juga puluhan Contoh Paper Penelitian Terkini di bidang Data Mining. Saya menjelaskan banyak ide penelitian untuk skripsi, tesis, disertasi, dll. Simak sampe akhir ya.
Metodologi Riset: Literature Review



Metodologi Riset: Literature ReviewAchmad Solichin Literature review merupakan tinjauan terhadap penelitian dan temuan terkait sebelumnya untuk mendukung penelitian yang akan dilakukan. Tahapan literature review meliputi perencanaan, pencarian literatur, evaluasi, analisis, dan penulisan ulang. Literature review bertujuan untuk menghindari penelitian yang berulang, mendapatkan dukungan teori, dan mengidentifikasi kelemahan penelitian sebelumnya.
Materi Seminar: Artificial Intelligence dengan PHP



Materi Seminar: Artificial Intelligence dengan PHPAchmad Solichin The document discusses artificial intelligence and its implementation using PHP. It begins with definitions of artificial intelligence and describes how AI works and common AI methods. It then provides examples of AI implementations in areas like fraud detection, text classification, and image processing. The document introduces PHP libraries that can be used to develop AI applications with PHP, such as PHP-ML and Rubix ML. It highlights various machine learning algorithms and features supported by these libraries and provides code demos. In the end, the document emphasizes that AI will not surpass human intelligence, which created it, and that human intelligence will also not surpass the intelligence of its creator, God.
Percobaan Perpindahan Kalor melalui Konduksi, Konveksi dan Radiasi



Percobaan Perpindahan Kalor melalui Konduksi, Konveksi dan RadiasiAchmad Solichin Percobaan ini bertujuan untuk melihat perpindahan kalor melalui konduksi, konveksi, dan radiasi. Percobaan konduksi memanaskan sendok yang dilapisi lilin sehingga lilin meleleh dari ujung ke ujung. Pada percobaan konveksi, lilin meleleh karena terkena udara panas dari api. Sedangkan pada radiasi, lilin meleleh karena panas dari api meskipun tidak menyentuhnya. Percobaan ini men
Metodologi Riset: Literature Review



Metodologi Riset: Literature ReviewAchmad Solichin Literature review merupakan tinjauan terhadap penelitian dan temuan terkait sebelumnya untuk memberikan landasan ilmiah bagi penelitian yang akan dilakukan. Tahapan literature review meliputi perencanaan, pencarian literatur, pembacaan dan pengumpulan data, analisis, penulisan draft, dan revisi untuk memperoleh gambaran menyeluruh mengenai topik penelitian.
Depth First Search (DFS) pada Graph



Depth First Search (DFS) pada GraphAchmad Solichin Slide ini menjelaskan mengenai konsep dan langkah-langkah Algoritma Depth First Search (BFS) pada Graph.
Slide disusun oleh Achmad Solichin (http://achmatim.net)
Breadth First Search (BFS) pada Graph



Breadth First Search (BFS) pada GraphAchmad Solichin Slide ini menjelaskan mengenai konsep dan langkah-langkah Algoritma Breadth First Search (BFS) pada Graph.
Slide disusun oleh Achmad Solichin | http://achmatim.net
Binary Search Tree (BST) - Algoritma dan Struktur Data



Binary Search Tree (BST) - Algoritma dan Struktur DataAchmad Solichin Paparan mengenai Binary Search Tree (BST) - Algoritma dan Struktur Data. Disusun oleh Achmad Solichin, dirangkum dari berbagai sumber.
Computer Vision di Era Industri 4.0



Computer Vision di Era Industri 4.0Achmad Solichin Materi seminar ini menjelaskan mengenai konsep dasar computer vision dan aplikasinya di era Industri 4.0. Materi seminar ini disampaikan pada acara Seminar Tahunan IT yang diselenggarakan oleh Lab ICT Universitas Budi Luhur
Seminar: Become a Reliable Web Programmer



Seminar: Become a Reliable Web ProgrammerAchmad Solichin Materi Seminar dengan tema "Become a Reliable Web Programmer" yang diselenggarakan di AMIK BSI Tangerang pada Tanggal 17-18 April 2018.
The Big 5: Future IT Trends



The Big 5: Future IT TrendsAchmad Solichin 1) The document discusses trends in information technology and how to deal with them. It identifies the top 5 IT trends as next-gen mobile devices, social media, cloud computing, the Internet of Things, and big data.
2) It also lists the 10 most popular IT professions as data scientist, entry-level engineer, UX designer, quality assurance manager, analytics manager, and others related to development, architecture, and machine learning.
3) Finally, the document provides references and contact information for Achmad Solichin, the author who works at Universitas Budi Luhur in Jakarta.
Modern PHP Developer



Modern PHP DeveloperAchmad Solichin Dokumen tersebut merangkum perjalanan Achmad Solichin sebagai PHP developer, mulai dari belajar PHP pada tahun 2000 hingga praktik terkini. Dokumen tersebut juga menjelaskan tentang sejarah dan fitur-fitur PHP serta praktik terbaik dalam pengembangan PHP modern.
Seminar: PHP Developer for Dummies



Seminar: PHP Developer for DummiesAchmad Solichin Seminar PHP dengan tema PHP From Newbie to Master, di Universitas Budi Luhur, Tanggal 4 Juni 2016.
Pertemuan 1 - Algoritma dan Struktur Data 1



Pertemuan 1 - Algoritma dan Struktur Data 1Achmad Solichin Materi Pertemuan 1 - Algoritma dan Struktur Data 1, Universitas Budi Luhur
Recently uploaded (20)
Engage Donors Through Powerful Storytelling.pdf



Engage Donors Through Powerful Storytelling.pdfTechSoup In this webinars, members learn how to craft impactful messages that connect with donors to create donor engagement.
BỘ ĐỀ TUYỂN SINH VÀO LỚP 10 TIẾNG ANH - 25 ĐỀ THI BÁM SÁT CẤU TRÚC MỚI NHẤT, ...



BỘ ĐỀ TUYỂN SINH VÀO LỚP 10 TIẾNG ANH - 25 ĐỀ THI BÁM SÁT CẤU TRÚC MỚI NHẤT, ...Nguyen Thanh Tu Collection https://app.box.com/s/n8nl163m8v9ou7xil944pod44a5wi43h
GDGLSPGCOER - Git and GitHub Workshop.pptx



GDGLSPGCOER - Git and GitHub Workshop.pptxazeenhodekar This presentation covers the fundamentals of Git and version control in a practical, beginner-friendly way. Learn key commands, the Git data model, commit workflows, and how to collaborate effectively using Git — all explained with visuals, examples, and relatable humor.
YSPH VMOC Special Report - Measles Outbreak Southwest US 5-3-2025.pptx



YSPH VMOC Special Report - Measles Outbreak Southwest US 5-3-2025.pptxYale School of Public Health - The Virtual Medical Operations Center (VMOC) A measles outbreak originating in West Texas has been linked to confirmed cases in New Mexico, with additional cases reported in Oklahoma and Kansas. The current case count is 817 from Texas, New Mexico, Oklahoma, and Kansas. 97 individuals have required hospitalization, and 3 deaths, 2 children in Texas and one adult in New Mexico. These fatalities mark the first measles-related deaths in the United States since 2015 and the first pediatric measles death since 2003.
The YSPH Virtual Medical Operations Center Briefs (VMOC) were created as a service-learning project by faculty and graduate students at the Yale School of Public Health in response to the 2010 Haiti Earthquake. Each year, the VMOC Briefs are produced by students enrolled in Environmental Health Science Course 581 - Public Health Emergencies: Disaster Planning and Response. These briefs compile diverse information sources – including status reports, maps, news articles, and web content– into a single, easily digestible document that can be widely shared and used interactively. Key features of this report include:
- Comprehensive Overview: Provides situation updates, maps, relevant news, and web resources.
- Accessibility: Designed for easy reading, wide distribution, and interactive use.
- Collaboration: The “unlocked" format enables other responders to share, copy, and adapt seamlessly. The students learn by doing, quickly discovering how and where to find critical information and presenting it in an easily understood manner.
CURRENT CASE COUNT: 817 (As of 05/3/2025)
• Texas: 688 (+20)(62% of these cases are in Gaines County).
• New Mexico: 67 (+1 )(92.4% of the cases are from Eddy County)
• Oklahoma: 16 (+1)
• Kansas: 46 (32% of the cases are from Gray County)
HOSPITALIZATIONS: 97 (+2)
• Texas: 89 (+2) - This is 13.02% of all TX cases.
• New Mexico: 7 - This is 10.6% of all NM cases.
• Kansas: 1 - This is 2.7% of all KS cases.
DEATHS: 3
• Texas: 2 – This is 0.31% of all cases
• New Mexico: 1 – This is 1.54% of all cases
US NATIONAL CASE COUNT: 967 (Confirmed and suspected):
INTERNATIONAL SPREAD (As of 4/2/2025)
• Mexico – 865 (+58)
‒Chihuahua, Mexico: 844 (+58) cases, 3 hospitalizations, 1 fatality
• Canada: 1531 (+270) (This reflects Ontario's Outbreak, which began 11/24)
‒Ontario, Canada – 1243 (+223) cases, 84 hospitalizations.
• Europe: 6,814
Grade 2 - Mathematics - Printable Worksheet



Grade 2 - Mathematics - Printable WorksheetSritoma Majumder Grade 2 - Mathematics - Printable Worksheet
Kenan Fellows Participants, Projects 2025-26 Cohort



Kenan Fellows Participants, Projects 2025-26 CohortEducationNC These are the educators participating in the Kenan Fellows Program for Teacher Leadership at NC State University.
How to Manage Purchase Alternatives in Odoo 18



How to Manage Purchase Alternatives in Odoo 18Celine George Managing purchase alternatives is crucial for ensuring a smooth and cost-effective procurement process. Odoo 18 provides robust tools to handle alternative vendors and products, enabling businesses to maintain flexibility and mitigate supply chain disruptions.
CBSE - Grade 8 - Science - Chemistry - Metals and Non Metals - Worksheet



CBSE - Grade 8 - Science - Chemistry - Metals and Non Metals - WorksheetSritoma Majumder Introduction
All the materials around us are made up of elements. These elements can be broadly divided into two major groups:
Metals
Non-Metals
Each group has its own unique physical and chemical properties. Let's understand them one by one.
Physical Properties
1. Appearance
Metals: Shiny (lustrous). Example: gold, silver, copper.
Non-metals: Dull appearance (except iodine, which is shiny).
2. Hardness
Metals: Generally hard. Example: iron.
Non-metals: Usually soft (except diamond, a form of carbon, which is very hard).
3. State
Metals: Mostly solids at room temperature (except mercury, which is a liquid).
Non-metals: Can be solids, liquids, or gases. Example: oxygen (gas), bromine (liquid), sulphur (solid).
4. Malleability
Metals: Can be hammered into thin sheets (malleable).
Non-metals: Not malleable. They break when hammered (brittle).
5. Ductility
Metals: Can be drawn into wires (ductile).
Non-metals: Not ductile.
6. Conductivity
Metals: Good conductors of heat and electricity.
Non-metals: Poor conductors (except graphite, which is a good conductor).
7. Sonorous Nature
Metals: Produce a ringing sound when struck.
Non-metals: Do not produce sound.
Chemical Properties
1. Reaction with Oxygen
Metals react with oxygen to form metal oxides.
These metal oxides are usually basic.
Non-metals react with oxygen to form non-metallic oxides.
These oxides are usually acidic.
2. Reaction with Water
Metals:
Some react vigorously (e.g., sodium).
Some react slowly (e.g., iron).
Some do not react at all (e.g., gold, silver).
Non-metals: Generally do not react with water.
3. Reaction with Acids
Metals react with acids to produce salt and hydrogen gas.
Non-metals: Do not react with acids.
4. Reaction with Bases
Some non-metals react with bases to form salts, but this is rare.
Metals generally do not react with bases directly (except amphoteric metals like aluminum and zinc).
Displacement Reaction
More reactive metals can displace less reactive metals from their salt solutions.
Uses of Metals
Iron: Making machines, tools, and buildings.
Aluminum: Used in aircraft, utensils.
Copper: Electrical wires.
Gold and Silver: Jewelry.
Zinc: Coating iron to prevent rusting (galvanization).
Uses of Non-Metals
Oxygen: Breathing.
Nitrogen: Fertilizers.
Chlorine: Water purification.
Carbon: Fuel (coal), steel-making (coke).
Iodine: Medicines.
Alloys
An alloy is a mixture of metals or a metal with a non-metal.
Alloys have improved properties like strength, resistance to rusting.
Presentation of the MIPLM subject matter expert Erdem Kaya



Presentation of the MIPLM subject matter expert Erdem KayaMIPLM Presentation of the MIPLM subject matter expert Erdem Kaya
Real GitHub Copilot Exam Dumps for Success



Real GitHub Copilot Exam Dumps for SuccessMark Soia Download updated GitHub Copilot exam dumps to boost your certification success. Get real exam questions and verified answers for guaranteed performance
How to manage Multiple Warehouses for multiple floors in odoo point of sale



How to manage Multiple Warehouses for multiple floors in odoo point of saleCeline George The need for multiple warehouses and effective inventory management is crucial for companies aiming to optimize their operations, enhance customer satisfaction, and maintain a competitive edge.
Link your Lead Opportunities into Spreadsheet using odoo CRM



Link your Lead Opportunities into Spreadsheet using odoo CRMCeline George In Odoo 17 CRM, linking leads and opportunities to a spreadsheet can be done by exporting data or using Odoo’s built-in spreadsheet integration. To export, navigate to the CRM app, filter and select the relevant records, and then export the data in formats like CSV or XLSX, which can be opened in external spreadsheet tools such as Excel or Google Sheets.
K12 Tableau Tuesday - Algebra Equity and Access in Atlanta Public Schools



K12 Tableau Tuesday - Algebra Equity and Access in Atlanta Public Schoolsdogden2 Algebra 1 is often described as a “gateway” class, a pivotal moment that can shape the rest of a student’s K–12 education. Early access is key: successfully completing Algebra 1 in middle school allows students to complete advanced math and science coursework in high school, which research shows lead to higher wages and lower rates of unemployment in adulthood.
Learn how The Atlanta Public Schools is using their data to create a more equitable enrollment in middle school Algebra classes.
World war-1(Causes & impacts at a glance) PPT by Simanchala Sarab(BABed,sem-4...



World war-1(Causes & impacts at a glance) PPT by Simanchala Sarab(BABed,sem-4...larencebapu132 This is short and accurate description of World war-1 (1914-18)
It can give you the perfect factual conceptual clarity on the great war
Regards Simanchala Sarab
Student of BABed(ITEP, Secondary stage)in History at Guru Nanak Dev University Amritsar Punjab 🙏🙏
pulse ppt.pptx Types of pulse , characteristics of pulse , Alteration of pulse



pulse ppt.pptx Types of pulse , characteristics of pulse , Alteration of pulsesushreesangita003 what is pulse ?
Purpose
physiology and Regulation of pulse
Characteristics of pulse
factors affecting pulse
Sites of pulse
Alteration of pulse
for BSC Nursing 1st semester
for Gnm Nursing 1st year
Students .
vitalsign
YSPH VMOC Special Report - Measles Outbreak Southwest US 4-30-2025.pptx



YSPH VMOC Special Report - Measles Outbreak Southwest US 4-30-2025.pptxYale School of Public Health - The Virtual Medical Operations Center (VMOC) A measles outbreak originating in West Texas has been linked to confirmed cases in New Mexico, with additional cases reported in Oklahoma and Kansas. The current case count is 795 from Texas, New Mexico, Oklahoma, and Kansas. 95 individuals have required hospitalization, and 3 deaths, 2 children in Texas and one adult in New Mexico. These fatalities mark the first measles-related deaths in the United States since 2015 and the first pediatric measles death since 2003.
The YSPH Virtual Medical Operations Center Briefs (VMOC) were created as a service-learning project by faculty and graduate students at the Yale School of Public Health in response to the 2010 Haiti Earthquake. Each year, the VMOC Briefs are produced by students enrolled in Environmental Health Science Course 581 - Public Health Emergencies: Disaster Planning and Response. These briefs compile diverse information sources – including status reports, maps, news articles, and web content– into a single, easily digestible document that can be widely shared and used interactively. Key features of this report include:
- Comprehensive Overview: Provides situation updates, maps, relevant news, and web resources.
- Accessibility: Designed for easy reading, wide distribution, and interactive use.
- Collaboration: The “unlocked" format enables other responders to share, copy, and adapt seamlessly. The students learn by doing, quickly discovering how and where to find critical information and presenting it in an easily understood manner.
Operations Management (Dr. Abdulfatah Salem).pdf



Operations Management (Dr. Abdulfatah Salem).pdfArab Academy for Science, Technology and Maritime Transport This version of the lectures is provided free of charge to graduate students studying the Operations Management course at the MBA level.
BỘ ĐỀ TUYỂN SINH VÀO LỚP 10 TIẾNG ANH - 25 ĐỀ THI BÁM SÁT CẤU TRÚC MỚI NHẤT, ...



BỘ ĐỀ TUYỂN SINH VÀO LỚP 10 TIẾNG ANH - 25 ĐỀ THI BÁM SÁT CẤU TRÚC MỚI NHẤT, ...Nguyen Thanh Tu Collection
YSPH VMOC Special Report - Measles Outbreak Southwest US 5-3-2025.pptx



YSPH VMOC Special Report - Measles Outbreak Southwest US 5-3-2025.pptxYale School of Public Health - The Virtual Medical Operations Center (VMOC)
YSPH VMOC Special Report - Measles Outbreak Southwest US 4-30-2025.pptx



YSPH VMOC Special Report - Measles Outbreak Southwest US 4-30-2025.pptxYale School of Public Health - The Virtual Medical Operations Center (VMOC)
Operations Management (Dr. Abdulfatah Salem).pdf



Operations Management (Dr. Abdulfatah Salem).pdfArab Academy for Science, Technology and Maritime Transport
Lecture 06 Software Configuration Management
- 1. Software Configuration Management Matakuliah Rekayasa Perangkat Lunak (CS215) – Gasal 2015/2016 Magister Ilmu Komputer - Universitas Budi Luhur Achmad Solichin, S.Kom, M.T.I ([email protected]) CS215 – Rekayasa Perangkat Lunak – Magister Ilmu Komputer Universitas Budi Luhur
- 2. Overview • Software Configuration Items • SCM International Standard • Software Configuration identification • Software Configuration version control • Software Configuration change control • Software Configuration auditing • Software Configuration reporting CS215 – Rekayasa Perangkat Lunak – Magister Ilmu Komputer Universitas Budi Luhur
- 3. The “First Law” of System Engineering No matter where you are in the system life cycle, the system will change, and the desire to change it will persist throughout the life cycle. [Bersoff et al, 1980] CS215 – Rekayasa Perangkat Lunak – Magister Ilmu Komputer Universitas Budi Luhur
- 4. Source of Change • New business or market conditions • New stakeholder needs demand modification • Reorganization or business growth/downsizing • Budgetary or scheduling CS215 – Rekayasa Perangkat Lunak – Magister Ilmu Komputer Universitas Budi Luhur
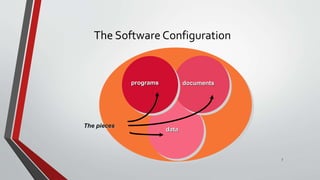
- 5. Software Change Management Software configuration management (SCM), also called change management, is a set of activities designed to manage change by identifying the work products that are likely to change, establishing relationships among them, defining mechanisms for managing different versions of these work products, controlling the changes imposed, and auditing and reporting on the changes made. CS215 – Rekayasa Perangkat Lunak – Magister Ilmu Komputer Universitas Budi Luhur
- 6. Purpose of SCM • Identify change • Control change • Ensure that change is being properly implemented • Report changes to others who may have an interest CS215 – Rekayasa Perangkat Lunak – Magister Ilmu Komputer Universitas Budi Luhur
- 7. 7 The Software Configuration programs documents data The pieces
- 8. Baseline • The IEEE (IEEE Std. No. 610.12-1990) defines a baseline as: • A specification or product that has been formally reviewed and agreed upon, that thereafter serves as the basis for further development, and that can be changed only through formal change control procedures. • a baseline is a milestone in the development of software that is marked by the delivery of one or more software configuration items and the approval of these SCIs that is obtained through a formal technical review CS215 – Rekayasa Perangkat Lunak – Magister Ilmu Komputer Universitas Budi Luhur
- 9. Baseline CS215 – Rekayasa Perangkat Lunak – Magister Ilmu Komputer Universitas Budi Luhur
- 10. Software Configuration Objects • SCIs are organized to form configuration objects that may be cataloged in the project database with a single name CS215 – Rekayasa Perangkat Lunak – Magister Ilmu Komputer Universitas Budi Luhur
- 11. SCM Repository • The SCM repository is the set of mechanisms and data structures that allow a software team to manage change in an effective manner • The repository performs or precipitates the following functions [For89]: • Data integrity • Information sharing • Tool integration • Data integration • Methodology enforcement • Document standardization CS215 – Rekayasa Perangkat Lunak – Magister Ilmu Komputer Universitas Budi Luhur
- 12. SCM Repository CS215 – Rekayasa Perangkat Lunak – Magister Ilmu Komputer Universitas Budi Luhur
- 13. Repository Features • Versioning. • saves all of these versions to enable effective management of product releases and to permit developers to go back to previous versions • Dependency tracking and change management. • The repository manages a wide variety of relationships among the data elements stored in it. • Requirements tracing. • Provides the ability to track all the design and construction components and deliverables that result from a specific requirement specification • Configuration management. • Keeps track of a series of configurations representing specific project milestones or production releases.Version management provides the needed versions, and link management keeps track of interdependencies. • Audit trails. • establishes additional information about when, why, and by whom changes are made. CS215 – Rekayasa Perangkat Lunak – Magister Ilmu Komputer Universitas Budi Luhur
- 14. SCM Elements • Component elements—a set of tools coupled within a file management system (e.g., a database) that enables access to and management of each software configuration item. • Process elements—a collection of procedures and tasks that define an effective approach to change management (and related activities) for all constituencies involved in the management, engineering and use of computer software. • Construction elements—a set of tools that automate the construction of software by ensuring that the proper set of validated components (i.e., the correct version) have been assembled. • Human elements—to implement effective SCM, the software team uses a set of tools and process features (encompassing other CM elements) CS215 – Rekayasa Perangkat Lunak – Magister Ilmu Komputer Universitas Budi Luhur
- 15. The SCM Process • How does a software team identify the discrete elements of a software configuration? • How does an organization manage the many existing versions of a program (and its documentation) in a manner that will enable change to be accommodated efficiently? • How does an organization control changes before and after software is released to a customer? • Who has responsibility for approving and ranking changes? • How can we ensure that changes have been made properly? • What mechanism is used to appraise others of changes that are made? Addresses the following questions …
- 16. SCM Process CS215 – Rekayasa Perangkat Lunak – Magister Ilmu Komputer Universitas Budi Luhur
- 17. Version Control CS215 – Rekayasa Perangkat Lunak – Magister Ilmu Komputer Universitas Budi Luhur • Version control combines procedures and tools to manage different versions of configuration objects that are created during the software process • A version control system implements or is directly integrated with four major capabilities: • a project database (repository) that stores all relevant configuration objects • a version management capability that stores all versions of a configuration object (or enables any version to be constructed using differences from past versions); • a make facility that enables the software engineer to collect all relevant configuration objects and construct a specific version of the software. • an issues tracking (also called bug tracking) capability that enables the team to record and track the status of all outstanding issues associated with each configuration object.
- 18. ConcurrentVersions System (CVS) CS215 – Rekayasa Perangkat Lunak – Magister Ilmu Komputer Universitas Budi Luhur • The CVS is a widely used tool for version control • Originally designed for source code, but useful for any text-based file, the CVS system: • establishes a simple repository, • maintains all versions of a file in a single named file by storing only the differences between progressive versions of the original file, and • protects against simultaneous changes to a file by establishing different directories for each developer, thus insulating one from another. • CVS is available at no cost forWindows, Mac OS, LINUX, and UNIX environments http://savannah.nongnu.org/projects/cvs
- 19. Change Control CS215 – Rekayasa Perangkat Lunak – Magister Ilmu Komputer Universitas Budi Luhur • Change control is vital. But the forces that make it necessary also make it annoying. We worry about change because a tiny perturbation in the code can create a big failure in the product. But it can also fix a big failure or enable wonderful new capabilities. We worry about change because a single rogue developer could sink the project; yet brilliant ideas originate in the minds of those rogues, and a burdensome change control process could effectively discourage them from doing creative work [Bac98] • Too much change control and we create problems.Too little, and we create other problems
- 21. These slides are designed to accompany Software Engineering: A Practitioner’s Approach, 7/e (McGraw-Hill 2009). Slides copyright 2009 by Roger Pressman. Auditing SCIs Change Requests SQA Plan SCM Audit
- 22. These slides are designed to accompany Software Engineering: A Practitioner’s Approach, 7/e (McGraw-Hill 2009). Slides copyright 2009 by Roger Pressman. Status Accounting SCIs Change Requests Change Reports ECOs Status Accounting Reporting
- 23. SCM forWeb Engineering CS215 – Rekayasa Perangkat Lunak – Magister Ilmu Komputer Universitas Budi Luhur • Content. • A typical WebApp contains a vast array of content—text, graphics, applets, scripts, audio/video files, forms, active page elements, tables, streaming data, and many others. • The challenge is to organize this sea of content into a rational set of configuration objects and then establish appropriate configuration control mechanisms for these objects. • People. • Because a significant percentage ofWebApp development continues to be conducted in an ad hoc manner, any person involved in the WebApp can (and often does) create content.
- 24. SCM forWeb Engineering CS215 – Rekayasa Perangkat Lunak – Magister Ilmu Komputer Universitas Budi Luhur • Scalability. • As size and complexity grow, small changes can have far-reaching and unintended affects that can be problematic.Therefore, the rigor of configuration control mechanisms should be directly proportional to application scale. • Politics. • Who ‘owns’ aWebApp? • Who assumes responsibility for the accuracy of the information on the Web site? • Who assures that quality control processes have been followed before information is published to the site? • Who is responsible for making changes? • Who assumes the cost of change?
- 25. Content Management CS215 – Rekayasa Perangkat Lunak – Magister Ilmu Komputer Universitas Budi Luhur • The collection subsystem encompasses all actions required to create and/or acquire content, and the technical functions that are necessary to • convert content into a form that can be represented by a mark-up language (e.g., HTML, XML • organize content into packets that can be displayed effectively on the client-side. • The management subsystem implements a repository that encompasses the following elements: • Content database—the information structure that has been established to store all content objects • Database capabilities—functions that enable the CMS to search for specific content objects (or categories of objects), store and retrieve objects, and manage the file structure that has been established for the content • Configuration management functions—the functional elements and associated workflow that support content object identification, version control, change management, change auditing, and reporting.
- 26. Content Management CS215 – Rekayasa Perangkat Lunak – Magister Ilmu Komputer Universitas Budi Luhur • The publishing subsystem extracts from the repository, converts it to a form that is amenable to publication, and formats it so that it can be transmitted to client-side browsers.The publishing subsystem accomplishes these tasks using a series of templates. • Each template is a function that builds a publication using one of three different components [BOI02]: • Static elements—text, graphics, media, and scripts that require no further processing are transmitted directly to the client-side • Publication services—function calls to specific retrieval and formatting services that personalize content (using predefined rules), perform data conversion, and build appropriate navigation links. • External services—provide access to external corporate information infrastructure such as enterprise data or “back-room” applications.
- 27. Content Management System CS215 – Rekayasa Perangkat Lunak – Magister Ilmu Komputer Universitas Budi Luhur
- 28. Change Management forWeb Apps CS215 – Rekayasa Perangkat Lunak – Magister Ilmu Komputer Universitas Budi Luhur
- 29. References • Roger S. Pressman, 2010, Software Engineering: A Practitioner’s Approach 7th edition, McGraw-Hill. • Ian Sommerville, 2011, Software Engineering 9th edition, Addison-Wesley. • Other references CS215 – Rekayasa Perangkat Lunak – Magister Ilmu Komputer Universitas Budi Luhur
- 30. Thanks • Achmad Solichin, S.Kom, M.T.I • [email protected] • Twitter: @achmatim • Facebook: facebook.com/achmatim • Web: http://achmatim.net CS215 – Rekayasa Perangkat Lunak – Magister Ilmu Komputer Universitas Budi Luhur





