Leveraging Software Architectures to Guide and Verify the Development of Sense/Compute/Control Applications
- 1. Leveraging Software Architecturesto Guide and Verify the Development of Sense/Compute/Control ApplicationsDamien Cassou1,2, Emilie Balland1, Charles Consel1, Julia Lawall31Phoenix, INRIA, France2Software Architecture Group, HPI, Germany3APL, DIKU, Denmark
- 2. ContributionsA design language to specify a software systemA compiler to process such specification for the verification of safety properties the guidance of the implementation the conformance2Context: Sense/Compute/Control software systems
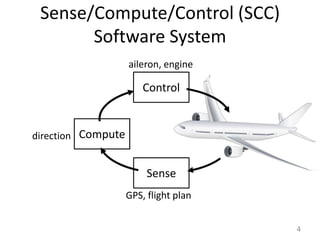
- 4. 4Sense/Compute/Control (SCC)Software Systemaileron, engineControlComputedirectionSenseGPS, flight plan
- 5. 5Sense/Compute/Control (SCC)Software Systemalarm triggeringControlEnvironmentComputeintrusion?Sensemotion detection
- 6. Found in various domainsavionics
- 9. robotics
- 10. …6Sense/Compute/Control (SCC)Software SystemsEnvironment[Taylor et al., Software Architecture: Foundations, Theory, and Practice, 2009]
- 11. The SCC Architectural StylesourcessensorsactuatorsactionsorderscontroloperatorsEnvironmentrefined informationcontextoperatorsraw data7[Chen et al., Context aggregation and dissemination in ubiquitous computing, WMCSA’02][Edwards et al., Architecture-driven self-adaptation and self-management in robotics, SEAMS’09]
- 12. The SCC Architectural Style8sourcesactuatorssensorsactionsControlorderscontroloperatorsSenseEnvironmentComputerefined informationcontextoperatorsraw data
- 14. 10The SCC Architectural StylecontroloperatorsInformation useInformation refinementcontextoperators
- 15. Going Beyond the SCC Style11 Our approacha design language
- 16. a compiler Objectivesto verify safety propertiesto guide implementationto ensure conformance
- 18. Compiling a DesignDesignLanguageabstractgeneratedDesignCompilerSoftware systemdefeats guidance and verificationconcreteDesign13
- 19. Compiling a DesignDesignLanguageabstractgeneratedDesignCompilerSoftware systemmixes design and implementationgeneratedconcreteSoftware SystemDesignCompiler14
- 20. Compiling a DesignDesignLanguageabstractgeneratedSoftware systemDesignCompilergeneratedCompilerSoftware SystemDesigngeneratedconcreteSoftware SystemDesignCompiler15
- 24. Our Approachverificationby constructionDeveloper’s codeCompilerProgrammingframeworkDesign19
- 25. 20Diving Into the Design LanguagesourcesactuatorssensorsactionsalarmtriggeringcontroloperatorsEnvironmentintrusion?contextoperatorsmotiondetection
- 28. design language dedicated to SCCactuatorscontext Intrusion as Boolean { context BuildingLocked; context Presence;}controloperators23BooleanIntrusioncontextoperatorsBooleanBooleanPresenceBuildingLockedsensors
- 30. 25keycodemotionKeypadMotionSensorAlarmactuatorsOnOffcontroloperatorsIntrusionManagercontroller IntrusionManager{ context Intrusion; action OnOff on Alarm;}IntrusionBooleanBooleanPresenceBuildingLockedBooleanIntegersensors
- 36. Interaction ContractssourceSensor3eventMain1Activation conditionevent2Data requirement1request23Emission2requestContextOperator3ContextOperator231
- 37. Interaction Contracts3Intrusion1Activation conditioncontext Intrusion asBoolean { context Presence; context BuildingLocked; interaction { whenprovided Presence get BuildingLocked maybepublish }}2Data requirement21323EmissionBuildingLockedPresence123
- 38. Compiling a Design33Developer’s codeProgrammingframeworkCompilerDesign
- 39. Programming FrameworkThe compilermapseach component description to an abstract class implementing the run-time support
- 40. each interaction contract to an abstract method constrained with type declarations34
- 41. Programming Framework35CompilerProgrammingframeworkDesignActivation conditionInteraction contract Abstract method name
- 42. parameters
- 43. return type11Data requirement2123Emission33
- 44. Code Generation36AlarmMailercontroller IntrusionManager{ context Intrusion; contextSceneImage; interaction { whenprovided Intrusion getSceneImage do OnOff on Alarm,Send on Mailer }}OnOffSendIntrusionManagerBooleanFileIntrusionSceneImageabstractclassAbstractIntrusionManager {abstract Actions onIntrusion( boolean intrusion, SceneImagesceneImage, Select select);protectedfinalclass Actions { … } protectedfinalclass Select { … } protectedfinalclassSceneImage { … } }generated framework code
- 45. Code Generation37AlarmMailercontroller IntrusionManager{ context Intrusion; contextSceneImage; interaction { whenprovided Intrusion getSceneImage do OnOff on Alarm,Send on Mailer }}OnOffSendIntrusionManagerBooleanFileIntrusionSceneImageabstractclassAbstractIntrusionManager {abstract Actions onIntrusion( boolean intrusion, SceneImagesceneImage, Select select);protectedfinalclass Actions { … } protectedfinalclass Select { … } protectedfinalclassSceneImage { … } }generated framework code
- 46. Code Generation38AlarmMailercontroller IntrusionManager{ context Intrusion; contextSceneImage; interaction { whenprovided Intrusion getSceneImage do OnOff on Alarm,Send on Mailer }}OnOffSendIntrusionManagerBooleanFileIntrusionSceneImageabstractclassAbstractIntrusionManager {abstract Actions onIntrusion( boolean intrusion, SceneImagesceneImage, Select select);protectedfinalclass Actions { … } protectedfinalclass Select { … } protectedfinalclassSceneImage { … } }generated framework code
- 47. Code Generation39AlarmMailercontroller IntrusionManager{ context Intrusion; contextSceneImage; interaction { whenprovided Intrusion getSceneImage do OnOff on Alarm,Send on Mailer }}OnOffSendIntrusionManagerBooleanFileIntrusionSceneImageabstractclassAbstractIntrusionManager {abstract Actions onIntrusion( boolean intrusion, SceneImagesceneImage, Select select);protectedfinalclass Actions { … } protectedfinalclass Select { … } protectedfinalclassSceneImage { … } }generated framework code
- 48. Code Generation40AlarmMailercontroller IntrusionManager{ context Intrusion; contextSceneImage; interaction { whenprovided Intrusion getSceneImage do OnOff on Alarm,Send on Mailer }}OnOffSendIntrusionManagerBooleanFileIntrusionSceneImageabstractclassAbstractIntrusionManager {abstract Actions onIntrusion( boolean intrusion, SceneImagesceneImage, Select select);protectedfinalclass Actions { … } protectedfinalclass Select { … } protectedfinalclassSceneImage { … } }generated framework code
- 49. Code Generation41AlarmMailercontroller IntrusionManager{ context Intrusion; contextSceneImage; interaction { whenprovided Intrusion getSceneImage do OnOff on Alarm,Send on Mailer }}OnOffSendIntrusionManagerBooleanFileIntrusionSceneImageabstractclassAbstractIntrusionManager {abstract Actions onIntrusion( boolean intrusion, SceneImagesceneImage, Select select);protectedfinalclass Actions { … } protectedfinalclass Select { … } protectedfinalclassSceneImage { … } }generated framework code
- 50. Code Generation42AlarmMailercontroller IntrusionManager{ context Intrusion; contextSceneImage; interaction { whenprovided Intrusion getSceneImage do OnOff on Alarm,Send on Mailer }}OnOffSendIntrusionManagerBooleanFileIntrusionSceneImageabstractclassAbstractIntrusionManager {abstract Actions onIntrusion( boolean intrusion, SceneImagesceneImage, Select select);protectedfinalclass Actions { … } protectedfinalclass Select { … } protectedfinalclassSceneImage { … } }generated framework code
- 51. Code Generation43AlarmMailercontroller IntrusionManager{ context Intrusion; contextSceneImage; interaction { whenprovided Intrusion getSceneImage do OnOff on Alarm,Send on Mailer }}OnOffSendIntrusionManagerBooleanFileIntrusionSceneImageabstractclassAbstractIntrusionManager {abstract Actions onIntrusion( boolean intrusion, SceneImagesceneImage, Select select);protectedfinalclass Actions { … } protectedfinalclass Select { … } protectedfinalclassSceneImage { … } }generated framework code
- 52. Code Generation44AlarmMailercontroller IntrusionManager{ context Intrusion; contextSceneImage; interaction { whenprovided Intrusion getSceneImage do OnOff on Alarm,Send on Mailer }}OnOffSendIntrusionManagerBooleanFileIntrusionSceneImageabstractclassAbstractIntrusionManager {abstract Actions onIntrusion( boolean intrusion, SceneImagesceneImage, Select select);protectedfinalclass Actions { … } protectedfinalclass Select { … } protectedfinalclassSceneImage { … } }generated framework code
- 53. Code Generation45AlarmMailercontroller IntrusionManager{ context Intrusion; contextSceneImage; interaction { whenprovided Intrusion getSceneImage do OnOff on Alarm,Send on Mailer }}OnOffSendIntrusionManagerBooleanFileIntrusionSceneImageabstractclassAbstractIntrusionManager {abstract Actions onIntrusion( boolean intrusion, SceneImagesceneImage, Select select);protectedfinalclass Actions { … } protectedfinalclass Select { … } protectedfinalclassSceneImage { … } }generated framework code
- 54. Code Generation46AlarmMailercontroller IntrusionManager{ context Intrusion; contextSceneImage; interaction { whenprovided Intrusion getSceneImage do OnOff on Alarm,Send on Mailer }}OnOffSendIntrusionManagerBooleanFileIntrusionSceneImageabstractclassAbstractIntrusionManager {abstract Actions onIntrusion( boolean intrusion, SceneImagesceneImage, Select select);protectedfinalclass Actions { … } protectedfinalclass Select { … } protectedfinalclassSceneImage { … } }generated framework code
- 55. ImplementationabstractclassAbstractIntrusionManager {abstract ActionsonIntrusion( boolean intrusion, SceneImagesceneImage, Select select);}47AlarmMailerOnOffSendIntrusionManagergenerated framework codeBooleanFileIntrusionSceneImageclassIntrusionManagerextendsAbstractIntrusionManager { ActionsonIntrusion(boolean intrusion, SceneImagesceneImage, Select select){if (intrusion) { Actions actions; actions = select.alarms().all().on(); Mailer mailer = select.mailers().anyOne(); File image = sceneImage.get();actions.add(mailer.send(“Intrusion !”, “admin”, image));return actions; }}developer code
- 56. Implementation48AlarmMailerabstractclassAbstractIntrusionManager {abstract ActionsonIntrusion( boolean intrusion, SceneImagesceneImage, Select select);}OnOffSendIntrusionManagergenerated framework codeBooleanFileIntrusionSceneImageclassIntrusionManagerextendsAbstractIntrusionManager { ActionsonIntrusion(boolean intrusion, SceneImagesceneImage, Select select){if (intrusion) { Actions actions; actions = select.alarms().all().on(); Mailer mailer = select.mailers().anyOne(); File image = sceneImage.get();actions.add(mailer.send(“Intrusion !”, “admin”, image));return actions; }}developer code
- 57. Implementation49AlarmMailerabstractclassAbstractIntrusionManager {abstract ActionsonIntrusion( boolean intrusion, SceneImagesceneImage, Select select);}OnOffSendIntrusionManagergenerated framework codeBooleanFileIntrusionSceneImageclassIntrusionManagerextendsAbstractIntrusionManager { ActionsonIntrusion(boolean intrusion, SceneImagesceneImage, Select select){if (intrusion) { Actions actions; actions = select.alarms().all().on(); Mailer mailer = select.mailers().anyOne(); File image = sceneImage.get();actions.add(mailer.send(“Intrusion !”, “admin”, image));return actions; }}developer code
- 58. Implementation50AlarmMailerabstractclassAbstractIntrusionManager {abstract ActionsonIntrusion( boolean intrusion, SceneImagesceneImage, Select select);}OnOffSendIntrusionManagergenerated framework codeBooleanFileIntrusionSceneImageclassIntrusionManagerextendsAbstractIntrusionManager { ActionsonIntrusion(boolean intrusion, SceneImagesceneImage, Select select){if (intrusion) { Actions actions; actions = select.alarms().all().on(); Mailer mailer = select.mailers().anyOne(); File image = sceneImage.get();actions.add(mailer.send(“Intrusion !”, “admin”, image));return actions; }}developer code
- 59. Implementation51AlarmMailerabstractclassAbstractIntrusionManager {abstract ActionsonIntrusion( boolean intrusion, SceneImagesceneImage, Select select);}OnOffSendIntrusionManagergenerated framework codeBooleanFileIntrusionSceneImageclassIntrusionManagerextendsAbstractIntrusionManager { ActionsonIntrusion(boolean intrusion, SceneImagesceneImage, Select select){if (intrusion) { Actions actions; actions = select.alarms().all().on(); Mailer mailer = select.mailers().anyOne(); File image = sceneImage.get();actions.add(mailer.send(“Intrusion !”, “admin”, image));return actions; }}developer code
- 60. Implementation52AlarmMailerabstractclassAbstractIntrusionManager {abstract ActionsonIntrusion( boolean intrusion, SceneImagesceneImage, Select select);}OnOffSendIntrusionManagergenerated framework codeBooleanFileIntrusionSceneImageclassIntrusionManagerextendsAbstractIntrusionManager { ActionsonIntrusion(boolean intrusion, SceneImagesceneImage, Select select){if (intrusion) { Actions actions; actions = select.alarms().all().on(); Mailer mailer = select.mailers().anyOne(); File image = sceneImage.get();actions.add(mailer.send(“Intrusion !”, “admin”, image));return actions; }}developer code
- 61. Implementation53AlarmMailerabstractclassAbstractIntrusionManager {abstract ActionsonIntrusion( boolean intrusion, SceneImagesceneImage, Select select);}OnOffSendIntrusionManagergenerated framework codeBooleanFileIntrusionSceneImageclassIntrusionManagerextendsAbstractIntrusionManager { ActionsonIntrusion(boolean intrusion, SceneImagesceneImage, Select select){if (intrusion) { Actions actions; actions = select.alarms().all().on(); Mailer mailer = select.mailers().anyOne(); File image = sceneImage.get();actions.add(mailer.send(“Intrusion !”, “admin”, image));return actions; }}developer code
- 62. Implementation54AlarmMailerabstractclassAbstractIntrusionManager {abstract ActionsonIntrusion( boolean intrusion, SceneImagesceneImage, Select select);}OnOffSendIntrusionManagergenerated framework codeBooleanFileIntrusionSceneImageclassIntrusionManagerextendsAbstractIntrusionManager { ActionsonIntrusion(boolean intrusion, SceneImagesceneImage, Select select){if (intrusion) { Actions actions; actions = select.alarms().all().on(); Mailer mailer = select.mailers().anyOne(); File image = sceneImage.get();actions.add(mailer.send(“Intrusion !”, “admin”, image));return actions; }}developer code
- 63. Implementation55AlarmMailerabstractclassAbstractIntrusionManager {abstract ActionsonIntrusion( boolean intrusion, SceneImagesceneImage, Select select);}OnOffSendIntrusionManagergenerated framework codeBooleanFileIntrusionSceneImageclassIntrusionManagerextendsAbstractIntrusionManager { ActionsonIntrusion(boolean intrusion, SceneImagesceneImage, Select select){if (intrusion) { Actions actions; actions = select.alarms().all().on(); Mailer mailer = select.mailers().anyOne(); File image = sceneImage.get();actions.add(mailer.send(“Intrusion !”, “admin”, image));return actions; }}developer code
- 64. Implementation56 do not require any documentation
- 65. leverage code completionclassIntrusionManagerextendsAbstractIntrusionManager { ActionsonIntrusion(boolean intrusion, SceneImagesceneImage, Select select){if (intrusion) { Actions actions; actions = select.alarms().all().on(); Mailer mailer = select.mailers().anyOne(); File image = sceneImage.get();actions.add(mailer.send(“Intrusion !”, “admin”, image));return actions; }}developer code
- 66. SummaryA design language dedicated to specifying SCC software systemsA compiler to process such specification for the guidance of the implementation the conformance57
- 67. Status ReportImplementation using standard language toolsJava, ANTLR, StringTemplateSafety property verificationgeneration of Promela specificationse.g., interaction invariantsSeveral application domainsavionics: simulated auto-pilot and AR dronebuilding automation: light, fire, security, newscast, etc.misc.: web-server monitoring, home messenger, etc.Ongoing empirical evaluation with both students and professional software engineershttp://diasuite.inria.frDamien Cassou, Emilie Balland, Charles Consel, Julia Lawall
- 68. 59
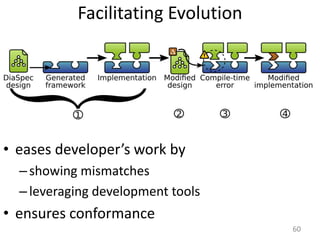
- 69. Facilitating Evolutioneases developer’s work byshowing mismatchesleveraging development toolsensures conformance60
- 70. Productivity61➡ 76% actually executed
- 71. Code Generation3booleanmotionMotionSensorPresence123<⇑MotionSensor.motion; ⇓MotionSensor.motion; ⇑ self > boolean12abstractclassAbstractPresence {abstractbooleanonMotionFromMotionSensor( boolean motion, Select select);}621231generated framework code
- 72. Implementation3booleanmotionMotionSensorPresence2boolean1abstractclassAbstractPresence {abstractbooleanonNewMotionFromMotionSensor( boolean motion, Select select);}generated framework codeclass Presence extendsAbstractPresence { booleanonMotionFromMotionSensor(boolean motion, Select select) {if (motion)return true;MotionSensors sensors = select.motionSensors().all();for (MotionSensor sensor : sensors)if (sensor.getMotion())return true;return false; }}developer code63
- 73. A Research VehicleThis work is part of a larger research project with7 PhDs leveraging the frameworksQoS (FASE’11)security (ICPS’09, DAIS’11)error-handling (OOPSLA’10)virtual testing (Mobiquitous’10 and ‘09)SIP (ICC’10, ICIN’09, IPTComm’08)end-user programming (DSLWC’09)64
- 74. LimitationsApplies only to new projectsApplies only to Sense/Compute/ControlRequires architects to learn a new languageImposes small run-time overhead65
Editor's Notes
- #2: Software architectures have long been used as a way to make software design explicit. However, these architectures are barely leveraged to guide subsequent phases of a software development cycle. In this work, we propose to leverage software architectures for the implementation and verification phases
- #4: SCC applications are applications that interact with an external environment
- #8: In this pattern, sensors…Interactions between these components are restricted.Explain that it separates the logic and the environment handling
- #9: In this style, sensors…Interactions between these components are restricted
- #10: In this style, sensors…Interactions between these components are restricted
- #11: In this style, sensors…Interactions between these components are restricted
- #12: The pattern guides the architect in describing his application. We want to go further and use this description to guide…
- #33: REQUEST + EVENT
- #64: CONFORMANCE









![…6Sense/Compute/Control (SCC)Software SystemsEnvironment[Taylor et al., Software Architecture: Foundations, Theory, and Practice, 2009]](https://image.slidesharecdn.com/icse2011-110527155008-phpapp01/85/Leveraging-Software-Architectures-to-Guide-and-Verify-the-Development-of-Sense-Compute-Control-Applications-10-320.jpg)
![The SCC Architectural StylesourcessensorsactuatorsactionsorderscontroloperatorsEnvironmentrefined informationcontextoperatorsraw data7[Chen et al., Context aggregation and dissemination in ubiquitous computing, WMCSA’02][Edwards et al., Architecture-driven self-adaptation and self-management in robotics, SEAMS’09]](https://image.slidesharecdn.com/icse2011-110527155008-phpapp01/85/Leveraging-Software-Architectures-to-Guide-and-Verify-the-Development-of-Sense-Compute-Control-Applications-11-320.jpg)