LFSMM Verifier Optimizations and 1 M Instructions
0 likes109 views
This document discusses recent optimizations to the Linux kernel's BPF verifier including rare explored state removal, read marking backpropagation pruning, and removing a large verifier lock. It analyzes profiling results showing the top functions consuming cycles in the BPF verifier. Additionally, it proposes further optimizations such as pruning point analysis and elimination, in-place branch pruning, and tail elimination. Finally, it acknowledges challenges for verifying very large 1 million instruction programs.
1 of 8
Download to read offline







Ad
Recommended
Mining the CPLEX Node Log for Faster MIP Performance



Mining the CPLEX Node Log for Faster MIP PerformanceIBM Decision Optimization First made at INFORMS in November 2013, this presentation will give you hints and tips to analyze the CPLEX log file to improve the solver's performance on your models.
M6 BLACKBELT PROJECT Rev 6.4



M6 BLACKBELT PROJECT Rev 6.4Neelesh Bhagwat This document provides details of a Six Sigma project aimed at reducing maintenance interruptions and increasing the mean time between failures (MTBF) of critical equipment at a refinery. The project focuses on pumps in critical units like crude distillation and residue manufacturing plant. The document defines the problem statement, goals, scope and assumptions. It presents analysis of failure data to identify the top 3 pumps for study based on number of repeat failures and their impact. Process flow, stakeholder mapping, communication plan and initial measurement efforts like fishbone diagrams and 5 whys are also included. The project aims to improve reliability and availability of critical pumps through root cause analysis and elimination of repeat failures.
Case Quality Management—ToyotaQuality Control Analytics at Toyo.docx



Case Quality Management—ToyotaQuality Control Analytics at Toyo.docxcowinhelen Case: Quality Management—Toyota
Quality Control Analytics at Toyota
As part of the process for improving the quality of their cars, Toyota engineers have identifi ed a potential improvement does happen to get too large, it can cause the accelerator to bind and create a potential problem for the driver. (Note: This part of the case has been fabricated for teaching purposes, and none of these data were obtained from Toyota.)
Let’s assume that, as a first step to improving the process, a sample of 40 washers coming from the machine that produces the washers was taken and the thickness measured in millimeters. The following table has the measurements from the sample:
1.9 2.0 1.9 1.8 2.2 1.7 2.0 1.9 1.7 1.8
1.8 2.2 2.1 2.2 1.9 1.8 2.1 1.6 1.8 1.6
2.1 2.4 2.2 2.1 2.1 2.0 1.8 1.7 1.9 1.9
2.1 2.0 2.4 1.7 2.2 2.0 1.6 2.0 2.1 2.2
Questions
1 If the specification is such that no washer should be greater than 2.4 millimeters, assuming that the thick-nesses are distributed normally, what fraction of the output is expected to be greater than this thickness?
The average thickness in the sample is 1.9625 and the standard deviation is .209624. The probability that the thickness is greater than 2.4 is Z = (2.4 – 1.9625)/.209624 = 2.087068 1 - NORMSDIST(2.087068) = .018441 fraction defective, so 1.8441 percent of the washers are expected to have a thickness greater than 2.4.
2 If there are an upper and lower specification, where the upper thickness limit is 2.4 and the lower thick-ness limit is 1.4, what fraction of the output is expected to be out of tolerance?
The upper limit is given in a. The lower limit is 1.4 so Z = (1.4 – 1.9625)/.209624 = -2.68337. NORMSDIST(-2.68337) = .003644 fraction defective, so .3644 percent of the washers are expected to have a thickness lower than 1.4. The total expected fraction defective would be .018441 + .003644 = .022085 or about 2.2085 percent of the washers would be expected to be out of tolerance.
3 What is the Cpk for the process?
4 What would be the Cpk for the process if it were centered between the specification limits (assume the process standard deviation is the same)?
The center of the specification limits is 1.9, which is used for X-bar in the following:
5 What percentage of output would be expected to be out of tolerance if the process were centered?
Z = (2.4 – 1.9)/.209624 = 2.385221
Fraction defective would be 2 x (1-NORMSDIST(2.385221)) = 2 x .008534 = .017069, about 1.7 percent.
6 Set up X - and range control charts for the current process. Assume the operators will take samples of 10 washers at a time.
Observation
Sample
1
2
3
4
5
6
7
8
9
10
X-bar
R
1
1.9
2
1.9
1.8
2.2
1.7
2
1.9
1.7
1.8
1.89
0.5
2
1.8
2.2
2.1
2.2
1.9
1.8
2.1
1.6
1.8
1.6
1.91
0.6
3
2.1
2.4
2.2
2.1
2.1
2
1.8
1.7
1.9
1.9
2.02
0.7
4
2.1
2
2.4
1.7
2.2
2
1.6
2
2.1
2.2
2.03
0.8
Mean:
1.9625
0.65
From Exhibit 10.13, with sample size of 10, A2 = .31, D3 = .22 and D4 = 1.78
The upper control limit for the X-bar ch.
IRJET - Steering Wheel Angle Prediction for Self-Driving Cars



IRJET - Steering Wheel Angle Prediction for Self-Driving CarsIRJET Journal This document discusses using a convolutional neural network to predict steering wheel angle for self-driving cars. The network is trained using human driving data from a simulator. The network architecture includes convolutional and fully connected layers to map input images to steering angles. The network is evaluated in the simulator and is able to drive autonomously for periods of time without human intervention, demonstrating its ability to predict steering wheel angles needed for navigation.
OSDC 2015: Georg Schönberger | Linux Performance Profiling and Monitoring



OSDC 2015: Georg Schönberger | Linux Performance Profiling and MonitoringNETWAYS Nowadays system administrators have great choices when it comes down to performance profiling and monitoring. The challenge is to pick the ppropriate tool and interpret their results correctly.
This talk is a chance to take a tour through various performance profiling and benchmarking tools, focusing on their benefit for every sysadmin. The topics will range from simple application profiling over sysstat utilities to low-level tracing methods. Besides traditional Linux methods a short glance at MySQL and Linux containers will be taken, too, as they are widely spread technologies.
At the end the goal is to gather reference points to look at, if you are faced with performance problems. Take the chance to close your knowledge gaps and learn how to get the most out of your system.
Linux Performance Profiling and Monitoring



Linux Performance Profiling and MonitoringGeorg Schönberger Presentation about Linux Performance Profiling and Monitoring, held at OSDC 2015 - a conference powered by NETWAYS.
CONDITION-BASED MAINTENANCE USING SENSOR ARRAYS AND TELEMATICS



CONDITION-BASED MAINTENANCE USING SENSOR ARRAYS AND TELEMATICSijmnct Emergence of uniquely addressable embeddable devices has raised the bar on Telematics capabilities.
Though the technology itself is not new, its application has been quite limited until now. Sensor based
telematics technologies generate volumes of data that are orders of magnitude larger than what operators
have dealt with previously. Real-time big data computation capabilities have opened the flood gates for
creating new predictive analytics capabilities into an otherwise simple data log systems, enabling real-time
control and monitoring to take preventive action in case of any anomalies. Condition-based-maintenance,
usage-based-insurance, smart metering and demand-based load generation etc. are some of the predictive analytics use cases for Telematics. This paper presents the approach of condition-based maintenance using
real-time sensor monitoring, Telematics and predictive data analytics.
Condition-based Maintenance with sensor arrays and telematics



Condition-based Maintenance with sensor arrays and telematicsGopalakrishna Palem Emergence of uniquely addressable embeddable devices has raised bar on Telematics capabilities. Sensor based Telematics technologies generate volumes of data that are orders of magnitude larger than what operators have dealt with previously. Real-time big data architectures enable real-time control and monitoring of data to detect anomalies and take preventive action. Condition-based-maintenance, usage-based-insurance, smart metering and demand-based load generation are some of the predictive analytics use cases for Telematics with real-time data streaming. This paper presents indepth analysis of condition-based maintenance using real-time sensor monitoring, Telematics and predictive data analytics.
Quality Improvement and Automation of a Flywheel Engraving Machine



Quality Improvement and Automation of a Flywheel Engraving MachineIRJET Journal This document describes a proposed quality improvement and automation project for a flywheel engraving machine. The current manufacturing process involves manual inspection of flywheel internal diameters, categorization based on diameter measurements, and manual assembly for engraving. This leads to errors. The proposed automated solution involves two main operations:
1. Sensor-based inspection of flywheel internal diameters to ensure accuracy before further processing.
2. Automation of the engraving assembly and process through a pneumatic system controlled by a microcontroller. Sensors would ensure proper flywheel positioning and engraving based on categorization.
This automated solution aims to reduce errors, improve quality and standardization, and allow easy implementation in industry for benefits like increased efficiency
IRJET- Video Based Traffic Sign Detection by Scale Based Frame Fusion Technique



IRJET- Video Based Traffic Sign Detection by Scale Based Frame Fusion TechniqueIRJET Journal This document proposes a video-based framework for detecting, tracking, and recognizing traffic signs from a camera mounted on a moving vehicle. The framework aims to improve detection accuracy by utilizing information from spatially distributed traffic signs. It uses an offline detector initially, and if that fails, employs an online detector to update the motion model. Tracking is done using a Kalman filter to predict sign locations. The detections and tracks are fused to obtain a stable classification result. The proposed approach aims to handle non-stationary environments and improve location accuracy compared to single-frame detection methods.
IRJET- FPGA Implementation of an Improved Watchdog Timer for Safety Critical ...



IRJET- FPGA Implementation of an Improved Watchdog Timer for Safety Critical ...IRJET Journal This document describes the design and implementation of an improved configurable windowed watchdog timer that can be used in safety-critical applications. The proposed watchdog timer operates independently of the processor using a dedicated clock. It uses a windowed approach with service, frame, and controller windows that can be configured via software. The design was implemented in an FPGA and its effectiveness in detecting faults was validated by injecting faults through software. It was also implemented and tested in applications like an ATM and space launch vehicle control systems.
Practical Guidelines for Solving Difficult Mixed Integer Programs



Practical Guidelines for Solving Difficult Mixed Integer ProgramsIBM Decision Optimization This Virtual User Group session, held on 2013-08-28, will give you advice and hints to analyze difficult MIP problems and improve CPLEX performance solving them.
You will find the video for this presentation by Ed Klotz on https://www.ibm.com/developerworks/community/groups/community/DecisionOptimization
IRJET- Design and Implementation of High Speed FPGA Configuration using SBI



IRJET- Design and Implementation of High Speed FPGA Configuration using SBIIRJET Journal The document discusses designing and implementing high-speed FPGA configuration using spare block interfacing (SBI). The existing system uses a single self-healing block that can be affected, interrupting scheduling. The proposed system uses SBI for more accurate, timely scheduling. Spare blocks in four directions provide scheduling help if errors occur by generating temporary storage, spare data, or delaying the clock. This improves FPGA configuration performance. The proposed system also includes a fault injection block to randomly inject faults and test the watchdog timer's ability to detect faults. Implementation of FPGA in scheduling is discussed along with results and simulations showing the proposed windowed watchdog approach checks parameters individually in each window stage.
Recent MIP Performance Improvements in IBM ILOG CPLEX Optimization Studio



Recent MIP Performance Improvements in IBM ILOG CPLEX Optimization StudioIBM Decision Optimization This Virtual User Group session, held on 2014-01-22, presents some of the techniques and algorithms used to improve the CPLEX MIP solver in versions 12.5.1 and 12.6.
IRJET- Traffic Sign and Drowsiness Detection using Open-CV



IRJET- Traffic Sign and Drowsiness Detection using Open-CVIRJET Journal This document presents a method for detecting traffic signs and driver drowsiness using OpenCV. It first preprocesses traffic sign images and extracts features using SIFT and DRLBP. Traffic sign detection is then performed using a backpropagation neural network. For drowsiness detection, the system continuously monitors the driver's eyes using a camera. It detects the open and closed state of the eyes to identify symptoms of fatigue. When the eyes are closed for too long based on a threshold, an alert is triggered to avoid accidents from drowsy driving. The proposed methods were tested on images and videos with promising results.
Mathworks CAE simulation suite – case in point from automotive and aerospace.



Mathworks CAE simulation suite – case in point from automotive and aerospace.WMG centre High Value Manufacturing Catapult This document discusses predictive maintenance and how to develop predictive maintenance algorithms using MATLAB. It defines predictive, preventative, and reactive maintenance. It then outlines the steps to develop a predictive algorithm, including acquiring sensor data, preprocessing the data, identifying condition indicators, training a model, and deploying the model. It provides examples of developing algorithms for fault classification and remaining useful life estimation using sensor data from a triplex pump.
itSMF Presentation March 2009



itSMF Presentation March 2009jdmoore The document discusses automation and its benefits. It describes how automation can reduce business costs by 41% annually by automating manual and repetitive tasks. This reduces risks and errors while improving service levels. Automating incident and change management, disaster recovery, and scaling computing resources are provided as examples. Capturing expertise in automated processes also helps address skills shortages. The document recommends automation to support several of Gershon's recommendations around managing ICT costs and skills, data centers, and sustainability.
Performance Optimization of HPC Applications: From Hardware to Source Code



Performance Optimization of HPC Applications: From Hardware to Source CodeFisnik Kraja The document summarizes optimization techniques for HPC applications from hardware selection to application code tuning. It describes analyzing application performance, choosing an appropriate system, efficiently using resources, tuning system parameters, and optimizing code. Examples are provided for AVL Fire and OpenFOAM simulations, analyzing scalability, hardware dependencies, and reducing runtime through MPI and system tuning.
IBM Streams V4.1 and Incremental Checkpointing



IBM Streams V4.1 and Incremental Checkpointinglisanl Fang Zheng is a member of the IBM Streams development team. In his presentation, Fang provides an introduction to the incremental checkpointing feature that is available in IBM Streams V4.1, including how it works and how to use it.
Meter anomaly detection



Meter anomaly detectionsabyasachi choudhury Meter Anomaly Prediction:-The Analytical Solution blends all the requisite data entities related to Interval Meter usage, voltage, meter events, read quality and other supporting data entities.
IRJET- Analysis of Micro Inversion to Improve Fault Tolerance in High Spe...



IRJET- Analysis of Micro Inversion to Improve Fault Tolerance in High Spe...IRJET Journal This document discusses techniques for improving fault tolerance in VLSI circuits through micro inversion. It begins with an introduction to increasing reliability concerns with technology scaling. It then discusses micro inversion, where operations on erroneous data are "undone" through hardware rollback of a few cycles. It describes implementing micro inversion in a register file and handling the potential domino effect in multi-module systems through common bus transactions acting as a clock. The document concludes that micro inversion combined with parallel error checking can help achieve fault tolerance in complex multi-module VLSI systems.
Qualifying a high performance memory subsysten for Functional Safety



Qualifying a high performance memory subsysten for Functional SafetyPankaj Singh Addressing the Challenges of Safety verification for LPDDR4.
✓Avoid traditional approach of starting functional safety after functional verification : Iterative and expensive development phase
1. Functional Safety Need to be Architected and not added later.
2. Safety Analysis must start prior to implementation. ‘Design for safety/verification’
3. Reuse & Synergize : Nominal and Functional Safety Verification.
✓Fault optimization with formal and other techniques is necessary to overcome challenges with scaling simulation and analysis.
✓Integrated push button fault simulation flow is need of hour and saves verification engineers time.
✓Analog defect modelling and coverage can be performed based on IEEE P2427.
markomanolis_phd_defense



markomanolis_phd_defenseGeorge Markomanolis Georgios Markomanolis presented his PhD thesis on performance evaluation and prediction of parallel applications through trace-based simulation. He developed a trace acquisition framework that decouples trace collection from the execution environment. This allows acquiring traces from large application runs in a scalable way. He also created a trace replay tool built on a fast simulation kernel that accurately replays execution traces on different system configurations. The framework was experimentally evaluated using NAS benchmarks, demonstrating scalable trace acquisition and accurate simulation results.
Distributed and Parallel Computing CheckpointingRecovery-ds14.ppt



Distributed and Parallel Computing CheckpointingRecovery-ds14.pptahmadbataineh21 Distributed and Parallel Computing
MasterClass_Quectel_LPWAN NBIOT LTE M Power



MasterClass_Quectel_LPWAN NBIOT LTE M PowerBoNg711963 The document discusses low power optimization techniques for NB-IoT and LTE-M applications. It describes the communication process and issues that can occur during cell search. It provides tips on handling attach reject errors and optimizing the application to skip inactive times. Various solutions are presented to speed up the network searching process, such as reducing the number of searched bands and locking to specific frequencies. Handling of registration exceptions and disconnects is also covered.
OSDC 2017 - Werner Fischer - Linux performance profiling and monitoring



OSDC 2017 - Werner Fischer - Linux performance profiling and monitoringNETWAYS Nowadays system administrators have great choices when it comes down to Linux performance profiling and monitoring. The challenge is to pick the appropriate tools and interpret their results correctly.
This talk is a chance to take a tour through various performance profiling and benchmarking tools, focusing on their benefit for every sysadmin.
More than 25 different tools are presented. Ranging from well known tools like strace, iostat, tcpdump or vmstat to new features like Linux tracepoints or perf_events. You will also learn which tools can be monitored by Icinga and which monitoring plugins are already available for that.
At the end the goal is to gather reference points to look at, whenever you are faced with performance problems.
Take the chance to close your knowledge gaps and learn how to get the most out of your system.
Verify High Sigma Whitepaper



Verify High Sigma WhitepaperSolido Design Automation Verify High-Sigma Design is a tool that allows designers to quickly and accurately verify high-yield circuits. It uses an importance sampling technique to estimate yield with far fewer simulations than traditional Monte Carlo methods. The tool extracts design-specific high-sigma corners from runs that can be used for rapid design iterations to improve yield. It provides yield estimation with SPICE accuracy in a fraction of the time of other methods.
EEP301: Ca06 sample



EEP301: Ca06 sampleUmang Gupta This chapter discusses measuring the time response of a plant, specifically a DC motor, to characterize its dynamic behavior. The key aspects covered are:
1. Performing a step response test by applying a step input and measuring the transient and steady-state output. This allows determining the gain and time constant.
2. The transient response is initially dominated by the plant's inertia/storage elements, while the steady-state response is determined by the input.
3. A first-order lag model is commonly used to represent dynamic behavior, with an exponential rise to a step input characterized by the time constant τ. Three methods are presented for estimating τ from step response data.
Disaggregation a Primer: Optimizing design for Edge Cloud & Bare Metal applic...



Disaggregation a Primer: Optimizing design for Edge Cloud & Bare Metal applic...Netronome From the Infra//Structure Conference May 2019 by Ron Renwick of Netronome
Disaggregation a Primer:
Optimizing design for Edge Cloud & Bare Metal applications
Hyperscalers and Edge Cloud providers have recognized economic value of disaggregated infrastructure. Netronome Agilio SmartNICs enable disaggregated architectures to perform with up to 30x lower tail latency while encrypting every session using KTLS security.
LFSMM AF XDP Queue I-DS



LFSMM AF XDP Queue I-DSNetronome Jakub Kicinski presented on problems with queue IDs when using AF_XDP. There are many different types of TX queues like per-RX queues and per-CPU queues. Currently queues are allocated on RX program attach, leading to wasted hardware resources as there is no TX vs redirect optimization. Each queue also requires separate objects for buffer counts, interrupt moderation, and other settings. The queue IDs also cause issues with the AF_XDP flow and with RSS. Overall improvements are needed to better optimize queue usage and IDs with AF_XDP.
Ad
More Related Content
Similar to LFSMM Verifier Optimizations and 1 M Instructions (20)
Quality Improvement and Automation of a Flywheel Engraving Machine



Quality Improvement and Automation of a Flywheel Engraving MachineIRJET Journal This document describes a proposed quality improvement and automation project for a flywheel engraving machine. The current manufacturing process involves manual inspection of flywheel internal diameters, categorization based on diameter measurements, and manual assembly for engraving. This leads to errors. The proposed automated solution involves two main operations:
1. Sensor-based inspection of flywheel internal diameters to ensure accuracy before further processing.
2. Automation of the engraving assembly and process through a pneumatic system controlled by a microcontroller. Sensors would ensure proper flywheel positioning and engraving based on categorization.
This automated solution aims to reduce errors, improve quality and standardization, and allow easy implementation in industry for benefits like increased efficiency
IRJET- Video Based Traffic Sign Detection by Scale Based Frame Fusion Technique



IRJET- Video Based Traffic Sign Detection by Scale Based Frame Fusion TechniqueIRJET Journal This document proposes a video-based framework for detecting, tracking, and recognizing traffic signs from a camera mounted on a moving vehicle. The framework aims to improve detection accuracy by utilizing information from spatially distributed traffic signs. It uses an offline detector initially, and if that fails, employs an online detector to update the motion model. Tracking is done using a Kalman filter to predict sign locations. The detections and tracks are fused to obtain a stable classification result. The proposed approach aims to handle non-stationary environments and improve location accuracy compared to single-frame detection methods.
IRJET- FPGA Implementation of an Improved Watchdog Timer for Safety Critical ...



IRJET- FPGA Implementation of an Improved Watchdog Timer for Safety Critical ...IRJET Journal This document describes the design and implementation of an improved configurable windowed watchdog timer that can be used in safety-critical applications. The proposed watchdog timer operates independently of the processor using a dedicated clock. It uses a windowed approach with service, frame, and controller windows that can be configured via software. The design was implemented in an FPGA and its effectiveness in detecting faults was validated by injecting faults through software. It was also implemented and tested in applications like an ATM and space launch vehicle control systems.
Practical Guidelines for Solving Difficult Mixed Integer Programs



Practical Guidelines for Solving Difficult Mixed Integer ProgramsIBM Decision Optimization This Virtual User Group session, held on 2013-08-28, will give you advice and hints to analyze difficult MIP problems and improve CPLEX performance solving them.
You will find the video for this presentation by Ed Klotz on https://www.ibm.com/developerworks/community/groups/community/DecisionOptimization
IRJET- Design and Implementation of High Speed FPGA Configuration using SBI



IRJET- Design and Implementation of High Speed FPGA Configuration using SBIIRJET Journal The document discusses designing and implementing high-speed FPGA configuration using spare block interfacing (SBI). The existing system uses a single self-healing block that can be affected, interrupting scheduling. The proposed system uses SBI for more accurate, timely scheduling. Spare blocks in four directions provide scheduling help if errors occur by generating temporary storage, spare data, or delaying the clock. This improves FPGA configuration performance. The proposed system also includes a fault injection block to randomly inject faults and test the watchdog timer's ability to detect faults. Implementation of FPGA in scheduling is discussed along with results and simulations showing the proposed windowed watchdog approach checks parameters individually in each window stage.
Recent MIP Performance Improvements in IBM ILOG CPLEX Optimization Studio



Recent MIP Performance Improvements in IBM ILOG CPLEX Optimization StudioIBM Decision Optimization This Virtual User Group session, held on 2014-01-22, presents some of the techniques and algorithms used to improve the CPLEX MIP solver in versions 12.5.1 and 12.6.
IRJET- Traffic Sign and Drowsiness Detection using Open-CV



IRJET- Traffic Sign and Drowsiness Detection using Open-CVIRJET Journal This document presents a method for detecting traffic signs and driver drowsiness using OpenCV. It first preprocesses traffic sign images and extracts features using SIFT and DRLBP. Traffic sign detection is then performed using a backpropagation neural network. For drowsiness detection, the system continuously monitors the driver's eyes using a camera. It detects the open and closed state of the eyes to identify symptoms of fatigue. When the eyes are closed for too long based on a threshold, an alert is triggered to avoid accidents from drowsy driving. The proposed methods were tested on images and videos with promising results.
Mathworks CAE simulation suite – case in point from automotive and aerospace.



Mathworks CAE simulation suite – case in point from automotive and aerospace.WMG centre High Value Manufacturing Catapult This document discusses predictive maintenance and how to develop predictive maintenance algorithms using MATLAB. It defines predictive, preventative, and reactive maintenance. It then outlines the steps to develop a predictive algorithm, including acquiring sensor data, preprocessing the data, identifying condition indicators, training a model, and deploying the model. It provides examples of developing algorithms for fault classification and remaining useful life estimation using sensor data from a triplex pump.
itSMF Presentation March 2009



itSMF Presentation March 2009jdmoore The document discusses automation and its benefits. It describes how automation can reduce business costs by 41% annually by automating manual and repetitive tasks. This reduces risks and errors while improving service levels. Automating incident and change management, disaster recovery, and scaling computing resources are provided as examples. Capturing expertise in automated processes also helps address skills shortages. The document recommends automation to support several of Gershon's recommendations around managing ICT costs and skills, data centers, and sustainability.
Performance Optimization of HPC Applications: From Hardware to Source Code



Performance Optimization of HPC Applications: From Hardware to Source CodeFisnik Kraja The document summarizes optimization techniques for HPC applications from hardware selection to application code tuning. It describes analyzing application performance, choosing an appropriate system, efficiently using resources, tuning system parameters, and optimizing code. Examples are provided for AVL Fire and OpenFOAM simulations, analyzing scalability, hardware dependencies, and reducing runtime through MPI and system tuning.
IBM Streams V4.1 and Incremental Checkpointing



IBM Streams V4.1 and Incremental Checkpointinglisanl Fang Zheng is a member of the IBM Streams development team. In his presentation, Fang provides an introduction to the incremental checkpointing feature that is available in IBM Streams V4.1, including how it works and how to use it.
Meter anomaly detection



Meter anomaly detectionsabyasachi choudhury Meter Anomaly Prediction:-The Analytical Solution blends all the requisite data entities related to Interval Meter usage, voltage, meter events, read quality and other supporting data entities.
IRJET- Analysis of Micro Inversion to Improve Fault Tolerance in High Spe...



IRJET- Analysis of Micro Inversion to Improve Fault Tolerance in High Spe...IRJET Journal This document discusses techniques for improving fault tolerance in VLSI circuits through micro inversion. It begins with an introduction to increasing reliability concerns with technology scaling. It then discusses micro inversion, where operations on erroneous data are "undone" through hardware rollback of a few cycles. It describes implementing micro inversion in a register file and handling the potential domino effect in multi-module systems through common bus transactions acting as a clock. The document concludes that micro inversion combined with parallel error checking can help achieve fault tolerance in complex multi-module VLSI systems.
Qualifying a high performance memory subsysten for Functional Safety



Qualifying a high performance memory subsysten for Functional SafetyPankaj Singh Addressing the Challenges of Safety verification for LPDDR4.
✓Avoid traditional approach of starting functional safety after functional verification : Iterative and expensive development phase
1. Functional Safety Need to be Architected and not added later.
2. Safety Analysis must start prior to implementation. ‘Design for safety/verification’
3. Reuse & Synergize : Nominal and Functional Safety Verification.
✓Fault optimization with formal and other techniques is necessary to overcome challenges with scaling simulation and analysis.
✓Integrated push button fault simulation flow is need of hour and saves verification engineers time.
✓Analog defect modelling and coverage can be performed based on IEEE P2427.
markomanolis_phd_defense



markomanolis_phd_defenseGeorge Markomanolis Georgios Markomanolis presented his PhD thesis on performance evaluation and prediction of parallel applications through trace-based simulation. He developed a trace acquisition framework that decouples trace collection from the execution environment. This allows acquiring traces from large application runs in a scalable way. He also created a trace replay tool built on a fast simulation kernel that accurately replays execution traces on different system configurations. The framework was experimentally evaluated using NAS benchmarks, demonstrating scalable trace acquisition and accurate simulation results.
Distributed and Parallel Computing CheckpointingRecovery-ds14.ppt



Distributed and Parallel Computing CheckpointingRecovery-ds14.pptahmadbataineh21 Distributed and Parallel Computing
MasterClass_Quectel_LPWAN NBIOT LTE M Power



MasterClass_Quectel_LPWAN NBIOT LTE M PowerBoNg711963 The document discusses low power optimization techniques for NB-IoT and LTE-M applications. It describes the communication process and issues that can occur during cell search. It provides tips on handling attach reject errors and optimizing the application to skip inactive times. Various solutions are presented to speed up the network searching process, such as reducing the number of searched bands and locking to specific frequencies. Handling of registration exceptions and disconnects is also covered.
OSDC 2017 - Werner Fischer - Linux performance profiling and monitoring



OSDC 2017 - Werner Fischer - Linux performance profiling and monitoringNETWAYS Nowadays system administrators have great choices when it comes down to Linux performance profiling and monitoring. The challenge is to pick the appropriate tools and interpret their results correctly.
This talk is a chance to take a tour through various performance profiling and benchmarking tools, focusing on their benefit for every sysadmin.
More than 25 different tools are presented. Ranging from well known tools like strace, iostat, tcpdump or vmstat to new features like Linux tracepoints or perf_events. You will also learn which tools can be monitored by Icinga and which monitoring plugins are already available for that.
At the end the goal is to gather reference points to look at, whenever you are faced with performance problems.
Take the chance to close your knowledge gaps and learn how to get the most out of your system.
Verify High Sigma Whitepaper



Verify High Sigma WhitepaperSolido Design Automation Verify High-Sigma Design is a tool that allows designers to quickly and accurately verify high-yield circuits. It uses an importance sampling technique to estimate yield with far fewer simulations than traditional Monte Carlo methods. The tool extracts design-specific high-sigma corners from runs that can be used for rapid design iterations to improve yield. It provides yield estimation with SPICE accuracy in a fraction of the time of other methods.
EEP301: Ca06 sample



EEP301: Ca06 sampleUmang Gupta This chapter discusses measuring the time response of a plant, specifically a DC motor, to characterize its dynamic behavior. The key aspects covered are:
1. Performing a step response test by applying a step input and measuring the transient and steady-state output. This allows determining the gain and time constant.
2. The transient response is initially dominated by the plant's inertia/storage elements, while the steady-state response is determined by the input.
3. A first-order lag model is commonly used to represent dynamic behavior, with an exponential rise to a step input characterized by the time constant τ. Three methods are presented for estimating τ from step response data.
Mathworks CAE simulation suite – case in point from automotive and aerospace.



Mathworks CAE simulation suite – case in point from automotive and aerospace.WMG centre High Value Manufacturing Catapult
More from Netronome (20)
Disaggregation a Primer: Optimizing design for Edge Cloud & Bare Metal applic...



Disaggregation a Primer: Optimizing design for Edge Cloud & Bare Metal applic...Netronome From the Infra//Structure Conference May 2019 by Ron Renwick of Netronome
Disaggregation a Primer:
Optimizing design for Edge Cloud & Bare Metal applications
Hyperscalers and Edge Cloud providers have recognized economic value of disaggregated infrastructure. Netronome Agilio SmartNICs enable disaggregated architectures to perform with up to 30x lower tail latency while encrypting every session using KTLS security.
LFSMM AF XDP Queue I-DS



LFSMM AF XDP Queue I-DSNetronome Jakub Kicinski presented on problems with queue IDs when using AF_XDP. There are many different types of TX queues like per-RX queues and per-CPU queues. Currently queues are allocated on RX program attach, leading to wasted hardware resources as there is no TX vs redirect optimization. Each queue also requires separate objects for buffer counts, interrupt moderation, and other settings. The queue IDs also cause issues with the AF_XDP flow and with RSS. Overall improvements are needed to better optimize queue usage and IDs with AF_XDP.
Using Network Acceleration for an Optimized Edge Cloud Server Architecture



Using Network Acceleration for an Optimized Edge Cloud Server ArchitectureNetronome With the rise of cloud-native principles, applications are increasingly able to take advantage of diverse, specialized and distributed infrastructure. The emergence of Edge Cloud solutions promises faster and more immersive application experiences, as well as infrastructure primitives for 5G, IoT, mobility, and more. However, this new resource comes with space and power constraints that can only be overcome by using new disaggregated architectures that leverage network acceleration and optimally sized CPUs. The session will highlight how the capabilities unleashed by hardware offload of eBPF in edge cloud microservers will enable developers to efficiently leverage the massive amounts of data on the edge and to create next-generation real-time applications.
Offloading TC Rules on OVS Internal Ports 



Offloading TC Rules on OVS Internal Ports Netronome This document discusses two approaches to allowing traffic control (TC) rules to offload rules on internal ports in Open vSwitch (OVS). The first approach is to add a TC ingress hook to OVS internal port modules so the rules can be applied. The second approach is to offload rules as egress hooks, which achieves the same outcome as ingress hooks on internal ports by generating an OVS ingress action when egressing an internal port. Currently, TC rules outputting to an internal port are not offloaded, so this bypasses the OVS kernel datapath. The proposed approaches aim to address this by allowing hardware offload of rules on internal ports.
Quality of Service Ingress Rate Limiting and OVS Hardware Offloads



Quality of Service Ingress Rate Limiting and OVS Hardware OffloadsNetronome Netronome's Pieter Jansen van Vuuren presented at Netdev 0x13 in Prague on current OVS development activities.
ODSA Sub-Project Launch



ODSA Sub-Project LaunchNetronome The charter of the ODSA (Open Domain Specification Architecture) Workgroup is to define an open specification that enables building of Domain Specific Accelerator silicon using best-of-breed components from the industry made available as chiplet dies that can be integrated together as Lego blocks on an organic substrate packaging layer. The resulting multi-chip module (MCM) silicon can be produced at significantly lower development and manufacturing costs, and will deliver much needed performance per watt and performance per dollar efficiencies in networking, security, machine learning and other applications. The ODSA Workgroup also intends to deliver implementations of the specification as board-level prototypes, RTL code and libraries.
Flexible and Scalable Domain-Specific Architectures



Flexible and Scalable Domain-Specific ArchitecturesNetronome This talk introduces the concept of a domain-specific architecture (DSA) using the Netronome Flow Processor (NFP) as an example, it will cover the motivation, design and implementation. It will explore how this architecture’s flexibility has been leveraged in the past to handle unique platforms such as the Facebook Yosemite v2 Platform. Finally approaches for designing flexible chipsets in the future will be explored, including the value of system wide computational modeling.
Unifying Network Filtering Rules for the Linux Kernel with eBPF



Unifying Network Filtering Rules for the Linux Kernel with eBPFNetronome At the core of fast network packet processing lies the ability to filter packets, or in other words, to apply a set of rules on packets, usually consisting of a pattern to match (L2 to L4 source and destination addresses and ports, protocols, etc.) and corresponding actions (redirect to a given queue, or drop the packet, etc.). Over the years, several filtering frameworks have been added to Linux. While at the lower level, ethtool can be used to configure N-tuple rules on the receive side for the hardware, the upper layers of the stack got equipped with rules for firewalling (Netfilter), traffic shaping (TC), or packet switching (Open vSwitch for example).
In this presentation, Quentin Monnet reviewed the needs for those filtering frameworks and the particularities of each one. Then focuses on the changes brought by eBPF and XDP in this landscape: as BPF programs allow for very flexible processing and can be attached very low in the stack—at the driver level, or even run on the NIC itself—they offer filtering capabilities with no precedent in terms of performance and versatility in the kernel. Lastly, the third part explores potential leads in order to create bridges between the different rule formats and to make it easier for users to build their filtering eBPF programs.
Massively Parallel RISC-V Processing with Transactional Memory



Massively Parallel RISC-V Processing with Transactional MemoryNetronome In this talk, we discuss some of the background, and describe the example of a thousand RISC-V harts performing the processing required in a SmartNIC. We show how a RISC-V solution can be tailored with a suitable choice of instruction set features, privilege modes and debug methodology.
Offloading Linux LAG Devices Via Open vSwitch and TC



Offloading Linux LAG Devices Via Open vSwitch and TCNetronome Converting Open vSwitch (OVS) kernel rules to TC Flower rules has become the standard way to offload the datapath to SmartNICs and other hardware devices. Binding such TC rules to 'offloadable' ports (such as SmartNIC representers) has been shown to enable the acceleration of packet processing while saving CPU resources on the hosting server. However, one scenario not yet well defined is the case where offloadable ports are bound to a higher level Link Aggregation (LAG) netdev, such as a Linux Bond or Team device, and where this netdev is added to an OVS bridge.
This talk describes an implementation that offloads rules that either ingress or egress to a LAG device. It highlights changes made to OVS (included in v2.9) as well as to core TC code and the driver layer in the Linux kernel. Rather than introduce new features into the kernel to handle LAG offload, the design expands upon recent, independently added kernel features including the concept of TC blocks. It is shown how, with slight modification, TC blocks can be used by OVS to represent LAG devices.
eBPF Debugging Infrastructure - Current Techniques



eBPF Debugging Infrastructure - Current TechniquesNetronome eBPF (extended Berkeley Packet Filter), in particular with its driver-level hook XDP (eXpress Data Path), has increased in importance over the past few years. As a result, the ability to rapidly debug and diagnose problems is becoming more relevant. This talk will cover common issues faced and techniques to diagnose them, including the use of bpftool for map and program introspection, the use of disassembly to inspect generated assembly code and other methods such as using debug prints and how to apply these techniques when eBPF programs are offloaded to the hardware.
The talk will also explore where the current gaps in debugging infrastructure are and suggest some of the next steps to improve this, for example, integrations with tools such as strace, valgrind or even the LLDB debugger.
Efficient JIT to 32-bit Arches



Efficient JIT to 32-bit ArchesNetronome eBPF has 64-bit general purpose registers, therefore 32-bit architectures normally need to use register pair to model them and need to generate extra instructions to manipulate the high 32-bit in the pair. Some of these overheads incurred could be eliminated if JIT compiler knows only the low 32-bit of a register is interested. This could be known through data flow (DF) analysis techniques. Either the classic iterative DF analysis or "path-sensitive" version based on verifier's code path walker.
In this talk, implementations for both versions of DF analyzer will be presented. We will see how a def-use chain based classic eBPF DF analyser looks first, and will see the possibility to integrate it with previous proposed eBPF control flow graph framework to make a stand-alone eBPF global DF analyser which could potentially serve as a library. Then, another "path-sensitive" DF analyser based on the existing verifier code path walker will be presented. We will discuss how function calls, path prune, path switch affect the implementation. Finally, we will summarize pros and cons for each, and will see how could each of them be adapted to 64-bit and 32-bit architecture back-ends.
Also, eBPF has 32-bit sub-register and ALU32 instructions associated, enable them (-mattr=+alu32) in LLVM code-gen could let the generated eBPF sequences carry more 32-bit information which could potentially easy flow analyser. This will be briefly discussed in the talk as well.
eBPF & Switch Abstractions



eBPF & Switch AbstractionsNetronome eBPF (extended Berkeley Packet Filter) has been shown to be a flexible kernel construct used for a variety of use cases, such as load balancing, intrusion detection systems (IDS), tracing and many others. One such emerging use case revolves around the proposal made by William Tu for the use of eBPF as a data path for Open vSwitch. However, there are broader switching use cases developing around the use of eBPF capable hardware. This talk is designed to explore the bottlenecks that exist in generalising the application of eBPF further to both container switching as well as physical switching.
eBPF Tooling and Debugging Infrastructure



eBPF Tooling and Debugging InfrastructureNetronome
eBPF, in particular with its driver-level hook XDP, has increased in importance over the past few years. As a result, the ability to rapidly debug and diagnose problems is becoming more relevant. This session will cover common issues faced and techniques to diagnose them, including the use of bpftool for map and program introspection, the disassembling of programs to inspect generated eBPF instructions and other methods such as using debug prints and how to apply these techniques when eBPF programs are offloaded to the hardware.
BPF Hardware Offload Deep Dive



BPF Hardware Offload Deep DiveNetronome The first version of eBPF hardware offload was merged into the Linux kernel in October 2016 and became part of Linux v4.9. For the last two years the project has been growing and evolving to integrate more closely with the core kernel infrastructure and enable more advanced use cases. This talk will explain the internals of the kernel architecture of the offload and how it allows seamless execution of unmodified eBPF datapaths in HW.
Demystify eBPF JIT Compiler



Demystify eBPF JIT CompilerNetronome This slide deck focuses on eBPF JIT compilation infrastructure and how it plays an important role in the entire eBPF life cycle inside the Linux kernel. First, it does quite a number of control flow checks to reject vulnerable programs and then JIT compiles the eBPF program to either host or offloading target instructions which boost performance. However, there is little documentation about this topic which this slide deck will dive into.
eBPF/XDP 



eBPF/XDP Netronome Netronome's half-day tutorial on host data plane acceleration at ACM SIGCOMM 2018 introduced attendees to models for host data plane acceleration and provided an in-depth understanding of SmartNIC deployment models at hyperscale cloud vendors and telecom service providers.
Presenter Bios
Jakub Kicinski is a long term Linux kernel contributor, who has been leading the kernel team at Netronome for the last two years. Jakub’s major contributions include the creation of BPF hardware offload mechanisms in the kernel and bpftool user space utility, as well as work on the Linux kernel side of OVS offload.
David Beckett is a Software Engineer at Netronome with a strong technical background of computer networks including academic research with DDoS. David has expertise in the areas of Linux architecture and computer programming. David has a Masters Degree in Electrical, Electronic Engineering at Queen’s University Belfast and continues as a PhD student studying Emerging Application Layer DDoS threats.
P4 Introduction 



P4 Introduction Netronome Netronome's half-day tutorial on host data plane acceleration at ACM SIGCOMM 2018 introduced attendees to models for host data plane acceleration and provided an in-depth understanding of SmartNIC deployment models at hyperscale cloud vendors and telecom service providers.
Presenter Bio
Jaco Joubert is a Software Engineer at Netronome focusing on P4 and its applications on the Netronome SmartNIC. He recently started investigating network acceleration for Deep Learning on distributed systems. Prior to Netronome he worked on mobile application development and was a researcher at Telkom SA focusing on the mobile core after completing his Masters Degree in Computer, Electronic Engineering in 2014.
Host Data Plane Acceleration: SmartNIC Deployment Models



Host Data Plane Acceleration: SmartNIC Deployment ModelsNetronome SIGCOMM 2018: This tutorial introduces multiple models for host data plane acceleration with SmartNICs, provides a detailed understanding of SmartNIC deployment models at hyperscale cloud vendors and telecom service providers, and introduces various open source resources available for research and product development in this space.
Presenter Bio
Simon focuses on upstream open source activities at Netronome. He is working on allowing offload of OVS offload on the Agilio platform as well as the broader question of how best to enable programming hardware offload in the Linux kernel and other upstream open source projects.
The Power of SmartNICs



The Power of SmartNICsNetronome SmartNICs are a new generation of intelligent Network Interface Cards (NICs). This intelligence allows NICs to offload virtual switching or other data plane functions in high-performance cloud data center servers.
Ad
Recently uploaded (20)
Enhancing ICU Intelligence: How Our Functional Testing Enabled a Healthcare I...



Enhancing ICU Intelligence: How Our Functional Testing Enabled a Healthcare I...Impelsys Inc. Impelsys provided a robust testing solution, leveraging a risk-based and requirement-mapped approach to validate ICU Connect and CritiXpert. A well-defined test suite was developed to assess data communication, clinical data collection, transformation, and visualization across integrated devices.
Role of Data Annotation Services in AI-Powered Manufacturing



Role of Data Annotation Services in AI-Powered ManufacturingAndrew Leo From predictive maintenance to robotic automation, AI is driving the future of manufacturing. But without high-quality annotated data, even the smartest models fall short.
Discover how data annotation services are powering accuracy, safety, and efficiency in AI-driven manufacturing systems.
Precision in data labeling = Precision on the production floor.
DevOpsDays Atlanta 2025 - Building 10x Development Organizations.pptx



DevOpsDays Atlanta 2025 - Building 10x Development Organizations.pptxJustin Reock Building 10x Organizations with Modern Productivity Metrics
10x developers may be a myth, but 10x organizations are very real, as proven by the influential study performed in the 1980s, ‘The Coding War Games.’
Right now, here in early 2025, we seem to be experiencing YAPP (Yet Another Productivity Philosophy), and that philosophy is converging on developer experience. It seems that with every new method we invent for the delivery of products, whether physical or virtual, we reinvent productivity philosophies to go alongside them.
But which of these approaches actually work? DORA? SPACE? DevEx? What should we invest in and create urgency behind today, so that we don’t find ourselves having the same discussion again in a decade?
2025-05-Q4-2024-Investor-Presentation.pptx



2025-05-Q4-2024-Investor-Presentation.pptxSamuele Fogagnolo Cloudflare Q4 Financial Results Presentation
AI and Data Privacy in 2025: Global Trends



AI and Data Privacy in 2025: Global TrendsInData Labs In this infographic, we explore how businesses can implement effective governance frameworks to address AI data privacy. Understanding it is crucial for developing effective strategies that ensure compliance, safeguard customer trust, and leverage AI responsibly. Equip yourself with insights that can drive informed decision-making and position your organization for success in the future of data privacy.
This infographic contains:
-AI and data privacy: Key findings
-Statistics on AI data privacy in the today’s world
-Tips on how to overcome data privacy challenges
-Benefits of AI data security investments.
Keep up-to-date on how AI is reshaping privacy standards and what this entails for both individuals and organizations.
Quantum Computing Quick Research Guide by Arthur Morgan



Quantum Computing Quick Research Guide by Arthur MorganArthur Morgan This is a Quick Research Guide (QRG).
QRGs include the following:
- A brief, high-level overview of the QRG topic.
- A milestone timeline for the QRG topic.
- Links to various free online resource materials to provide a deeper dive into the QRG topic.
- Conclusion and a recommendation for at least two books available in the SJPL system on the QRG topic.
QRGs planned for the series:
- Artificial Intelligence QRG
- Quantum Computing QRG
- Big Data Analytics QRG
- Spacecraft Guidance, Navigation & Control QRG (coming 2026)
- UK Home Computing & The Birth of ARM QRG (coming 2027)
Any questions or comments?
- Please contact Arthur Morgan at [email protected].
100% human made.
Cybersecurity Identity and Access Solutions using Azure AD



Cybersecurity Identity and Access Solutions using Azure ADVICTOR MAESTRE RAMIREZ Cybersecurity Identity and Access Solutions using Azure AD
Generative Artificial Intelligence (GenAI) in Business



Generative Artificial Intelligence (GenAI) in BusinessDr. Tathagat Varma My talk for the Indian School of Business (ISB) Emerging Leaders Program Cohort 9. In this talk, I discussed key issues around adoption of GenAI in business - benefits, opportunities and limitations. I also discussed how my research on Theory of Cognitive Chasms helps address some of these issues
Procurement Insights Cost To Value Guide.pptx



Procurement Insights Cost To Value Guide.pptxJon Hansen Procurement Insights integrated Historic Procurement Industry Archives, serves as a powerful complement — not a competitor — to other procurement industry firms. It fills critical gaps in depth, agility, and contextual insight that most traditional analyst and association models overlook.
Learn more about this value- driven proprietary service offering here.
Into The Box Conference Keynote Day 1 (ITB2025)



Into The Box Conference Keynote Day 1 (ITB2025)Ortus Solutions, Corp This is the keynote of the Into the Box conference, highlighting the release of the BoxLang JVM language, its key enhancements, and its vision for the future.
Linux Professional Institute LPIC-1 Exam.pdf



Linux Professional Institute LPIC-1 Exam.pdfRHCSA Guru Introduction to LPIC-1 Exam - overview, exam details, price and job opportunities
Designing Low-Latency Systems with Rust and ScyllaDB: An Architectural Deep Dive



Designing Low-Latency Systems with Rust and ScyllaDB: An Architectural Deep DiveScyllaDB Want to learn practical tips for designing systems that can scale efficiently without compromising speed?
Join us for a workshop where we’ll address these challenges head-on and explore how to architect low-latency systems using Rust. During this free interactive workshop oriented for developers, engineers, and architects, we’ll cover how Rust’s unique language features and the Tokio async runtime enable high-performance application development.
As you explore key principles of designing low-latency systems with Rust, you will learn how to:
- Create and compile a real-world app with Rust
- Connect the application to ScyllaDB (NoSQL data store)
- Negotiate tradeoffs related to data modeling and querying
- Manage and monitor the database for consistently low latencies
Rusty Waters: Elevating Lakehouses Beyond Spark



Rusty Waters: Elevating Lakehouses Beyond Sparkcarlyakerly1 Spark is a powerhouse for large datasets, but when it comes to smaller data workloads, its overhead can sometimes slow things down. What if you could achieve high performance and efficiency without the need for Spark?
At S&P Global Commodity Insights, having a complete view of global energy and commodities markets enables customers to make data-driven decisions with confidence and create long-term, sustainable value. 🌍
Explore delta-rs + CDC and how these open-source innovations power lightweight, high-performance data applications beyond Spark! 🚀
#StandardsGoals for 2025: Standards & certification roundup - Tech Forum 2025



#StandardsGoals for 2025: Standards & certification roundup - Tech Forum 2025BookNet Canada Book industry standards are evolving rapidly. In the first part of this session, we’ll share an overview of key developments from 2024 and the early months of 2025. Then, BookNet’s resident standards expert, Tom Richardson, and CEO, Lauren Stewart, have a forward-looking conversation about what’s next.
Link to recording, transcript, and accompanying resource: https://bnctechforum.ca/sessions/standardsgoals-for-2025-standards-certification-roundup/
Presented by BookNet Canada on May 6, 2025 with support from the Department of Canadian Heritage.
Cyber Awareness overview for 2025 month of security



Cyber Awareness overview for 2025 month of securityriccardosl1 Cyber awareness training educates employees on risk associated with internet and malicious emails
Manifest Pre-Seed Update | A Humanoid OEM Deeptech In France



Manifest Pre-Seed Update | A Humanoid OEM Deeptech In Francechb3 The latest updates on Manifest's pre-seed stage progress.
Heap, Types of Heap, Insertion and Deletion



Heap, Types of Heap, Insertion and DeletionJaydeep Kale This pdf will explain what is heap, its type, insertion and deletion in heap and Heap sort
IEDM 2024 Tutorial2_Advances in CMOS Technologies and Future Directions for C...



IEDM 2024 Tutorial2_Advances in CMOS Technologies and Future Directions for C...organizerofv IEDM 2024 Tutorial2
Andrew Marnell: Transforming Business Strategy Through Data-Driven Insights



Andrew Marnell: Transforming Business Strategy Through Data-Driven InsightsAndrew Marnell With expertise in data architecture, performance tracking, and revenue forecasting, Andrew Marnell plays a vital role in aligning business strategies with data insights. Andrew Marnell’s ability to lead cross-functional teams ensures businesses achieve sustainable growth and operational excellence.
Ad
LFSMM Verifier Optimizations and 1 M Instructions
- 1. © 2018 NETRONOME SYSTEMS, INC. 1 Verifier optimization work Jakub Kicinski <[email protected]> LFSMM BPF Microconference San Juan, 2 May 2019
- 2. © 2019 NETRONOME SYSTEMS, INC. 2CONFIDENTIAL Recent optimizations from Alexei ● rare explored state removal most explored states never prune any later walks - remove states after: miss_cnt > 3 + hit_cnt * 3 ● read marking backpropagation pruning read marks are propagated to source states, once state with read mark already set is reached, propagation can stop ● big verifier lock removal already covered
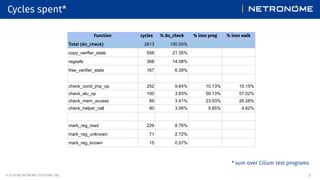
- 3. © 2019 NETRONOME SYSTEMS, INC. 3CONFIDENTIAL Cycles spent* * sum over Cilium test programs Function cycles % do_check % insn prog % insn walk Total (do_check) 2613 100.00% copy_verifier_state 558 21.35% regsafe 368 14.08% free_verifier_state 167 6.39% check_cond_jmp_op 252 9.64% 10.13% 10.15% check_alu_op 100 3.83% 59.13% 57.02% check_mem_access 89 3.41% 23.53% 26.28% check_helper_call 80 3.06% 5.65% 4.62% mark_reg_read 229 8.76% mark_reg_unknown 71 2.72% mark_reg_known 15 0.57%
- 4. © 2019 NETRONOME SYSTEMS, INC. 4CONFIDENTIAL Cycles spent* * sum over Cilium test programs Function cycles % do_check % insn prog % insn walk Total (do_check) 2613 100.00% copy_verifier_state 558 21.35% regsafe 368 14.08% free_verifier_state 167 6.39% check_cond_jmp_op 252 9.64% 10.13% 10.15% check_alu_op 100 3.83% 59.13% 57.02% check_mem_access 89 3.41% 23.53% 26.28% check_helper_call 80 3.06% 5.65% 4.62% mark_reg_read 229 8.76% mark_reg_unknown 71 2.72% mark_reg_known 15 0.57% Trivial micro optimization - avoid the use of zalloc+memcpy 19.41%
- 5. © 2019 NETRONOME SYSTEMS, INC. 5CONFIDENTIAL Pruning point analysis n prunes sum(points) 0 5137 1 615 2 242 3 167 4 51 5 39 6 45 7 19 8 24 9 17 10 11
- 6. © 2019 NETRONOME SYSTEMS, INC. 6CONFIDENTIAL Pruning point elimination ● pruning points are too dense - every 3.8 instruction in Cilium progs ● 80% of conditional branch pruning points with 0 hits ● replacing the pruning heuristic with marking every 10th instruction gives 4-20% do_check speedup for Cilium progs ● 33% more instructions walked ● no good heuristic apparent, yet ● pruning on fall through insn, rather than jmp - 4% ● in-place branch pruning Branch 9279 27.55% Shallow 4641 13.78% Pruning 24397 72.45% Total 33676
- 7. © 2019 NETRONOME SYSTEMS, INC. 7CONFIDENTIAL Other ideas ● tail elimination: r0 = const exit covered by the shallow branch optimization ● pure function detection/pruning (callsite independent) real-life benefit unclear due to small number of no-inline samples ● “fudge” builtin: var = __builtin_constant_relaxed(5, 0xff) hints the verifier should loosen the info about the constant
- 8. © 2019 NETRONOME SYSTEMS, INC. 8CONFIDENTIAL 1M instruction challenges ● jump offset (16 bit) ● instruction patching is quadratic ● pruning state grows as O(stack frames x prog len) ● execution time estimation?

