Messing with binary formats
5 likes16,406 views
a 44CON 2013 presentation slides downloadable (including inception binary) at http://mix.corkami.com
1 of 66
Downloaded 91 times












































![%PDF*****
1 0 obj
<<
/Size 2
/W[[]1/]
/Root 1 0 R
/Pages<<
/Kids[<<
/Contents<<>>
stream
BT{99
Tf{Td(Inlined PDF)'
endstream
>>]
>>
>>
stream
*
endstream
startxref%*******](https://image.slidesharecdn.com/44con2013-messingwithbinaryformat-130916110834-phpapp01/85/Messing-with-binary-formats-46-320.jpg)








![like washing powders
security tools are selected:
● speed
● {files} → {[clean/detected]}
file types not taken into consideration](https://image.slidesharecdn.com/44con2013-messingwithbinaryformat-130916110834-phpapp01/85/Messing-with-binary-formats-56-320.jpg)










Ad
Recommended
The windows socket



The windows socketFernando Grille The document introduces a tutorial on Windows socket programming. It will teach how to program internet applications in C from basic to advanced levels. It provides download links for a free C compiler and tutorial, and recommends resources to learn C as a prerequisite. The first part of the socket tutorial will cover what is needed to set up the compiler.
Beginning development in go



Beginning development in goEqualeyes Solutions Ltd. This article provides an overview of the Go programming language by discussing its key features and benefits. It explains that Go is a compiled language developed by Google that provides cross-platform development, lightweight threading with goroutines, built-in formatting tools, and a standard library that includes functionality for building web servers and implementing object-oriented programming. Code examples are provided to demonstrate how to write a basic "Hello World" program, create a simple HTTP server, and define and use structs and methods to implement OOP concepts in Go. The article concludes by noting that Go offers performance close to C/C++ while also providing garbage collection and runtime reflection capabilities.
Docker and .NET Core - Best Friends Forever - Michael Newton - Codemotion Rom...



Docker and .NET Core - Best Friends Forever - Michael Newton - Codemotion Rom...Codemotion The .NET languages have always been top notch in design, with a wide ranging standard library and support for all your enterprise needs. But for those of us with experience in the world outside Windows, the operational side of things was unbelievably painful. Now, with .NET Core that's starting to change. Here we'll work through the process of taking a .NET library and building a CI pipeline from reproducible container based builds through to minimal deployment artifacts.
Go Programming Language by Google



Go Programming Language by GoogleUttam Gandhi Go is a programming language created by Google that aims to be a simple, efficient, and concurrent language. The document provides an overview of the history and features of Go, including its support for garbage collection, concurrency, and ease of programming. Examples are given demonstrating how to write Go code, use interfaces and channels for concurrency, and connect to MongoDB. The document also lists several companies that use Go in production applications.
Learning Linq by Doing - Koans



Learning Linq by Doing - KoansLlewellyn Falco This document discusses using koans to learn programming concepts through practice. It recommends pairing with another person to complete Linq koans from the CodePlex site. The koans guide learners through small exercises that demonstrate Linq queries and C# syntax in a learning-by-doing approach. Upon completion, the document suggests reflecting on what was learned about the topic and how it could apply at work. It provides additional resources for continuing education with other koan sites and podcasts focused on teaching programming.
Schizophrenic files v2



Schizophrenic files v2Ange Albertini This document summarizes a talk about abusing file format parsers to cause different parsing behaviors, known as "schizophrenia". It describes techniques used across various formats like ZIP, BMP, PDF, GIF and PE files that can result in files being parsed or interpreted differently depending on factors like the parsing order, which part of a program does the parsing, or which specifications are followed. The goal is to fool parsers without causing failures by leveraging ambiguity and flexibility in file specifications.
A Recovering Java Developer Learns to Go



A Recovering Java Developer Learns to GoMatt Stine As presented at OSCON 2014.
The Go programming language has emerged as a favorite tool of DevOps and cloud practitioners alike. In many ways, Go is more famous for what it doesn’t include than what it does, and co-author Rob Pike has said that Go represents a “less is more” approach to language design.
The Cloud Foundry engineering teams have steadily increased their use of Go for building components, starting with the Router, and progressing through Loggregator, the CLI, and more recently the Health Manager. As a “recovering-Java-developer-turned-DevOps-junkie” focused on helping our customers and community succeed with Cloud Foundry, it became very clear to me that I needed to add Go to my knowledge portfolio.
This talk will introduce Go and its distinctives to Java developers looking to add Go to their toolkits. We’ll cover Go vs. Java in terms of:
* type systems
* modularity
* programming idioms
* object-oriented constructs
* concurrency
Ruxmon.2015-08.-.proxenet



Ruxmon.2015-08.-.proxenetChristophe Alladoum This document introduces Proxenet, a hacker-friendly web application proxy designed to be easily extensible through plugins. Proxenet is written entirely in C for high performance. It uses a microkernel approach where a small core handles connections and delegates all other functionality to plugins. Plugins are simple to create, requiring only request and response hook functions. The document demonstrates how Proxenet can be used for man-in-the-middle attacks by modifying HTTP traffic using plugins during active directory poisoning attacks on internal networks.
Python for IoT, A return of experience



Python for IoT, A return of experienceAlexandre Abadie Python for IoT discusses building Pyaiot, a system to connect constrained IoT devices to the web. Pyaiot uses common IoT protocols like CoAP and MQTT to allow bidirectional communication between low-power devices and a web dashboard. The author details how Pyaiot was implemented using Python and asyncio to be multi-protocol, modular, and reactive in a real-time manner. Lessons learned include some initial challenges with asyncio, but that Python facilitated fast development of the complex system to meet the initial requirements.
Phpconf taiwan-2012



Phpconf taiwan-2012Hash Lin The document discusses a new approach to generating DOCX, DOC, and PDF files using templates with the Zend Framework 2. It introduces LiveDocx, a SOAP-based document generation service with a PHP API called ZendService_LiveDocx. The template approach allows merging data into document templates to generate files in multiple formats like DOCX, DOC, HTML, RTF, PDF, and TXT with three simple steps: creating a template, populating merge fields with data, and writing the generated document to disk. Examples and demonstrations are provided.
PostgreSQL Development Today: 9.0



PostgreSQL Development Today: 9.0PostgreSQL Experts, Inc. PostgreSQL 9.0 is entering its final development stage with many new features planned for inclusion. Some key features include hot standby replication for high availability, synchronous replication for data integrity, and performance improvements. Developers are seeking community testing and feedback to ensure quality and identify issues prior to the beta release. The presentation encourages contributions to help shape PostgreSQL's future and highlights ways for developers to get involved.
How to Dockerize, Automate the Build and Deployment Process for Flutter?



How to Dockerize, Automate the Build and Deployment Process for Flutter?9 series This document outlines the steps to dockerize, automate builds, and deploy Flutter apps. It discusses setting up Docker and creating a Dockerfile. It describes creating a devcontainer folder structure and adding Flutter code. The steps to run the Docker container with VS Code and verify setup are provided. It concludes with running Flutter commands in the container to create and deploy projects.
Egress-Assess and Owning Data Exfiltration



Egress-Assess and Owning Data ExfiltrationCTruncer This talk discusses how Egress-Assess can be used to help attackers and defenders learn how to exfiltrate data outside of their network over a variety of protocols, describes how data is exfiltrated over different supported protocols, and demonstrates the weaponization of the tool!
Stashaway 1



Stashaway 1priestc This document discusses Stashaway, a tool for organizing digital media by moving files to remote cloud storage. It aims to address issues with local storage becoming expensive and cloud storage becoming popular, requiring data to move from local to remote locations. The document outlines Stashaway's features like uploading files to cloud storage, listing and streaming files remotely, and planned features like tagging and duplicate detection. It provides a development timeline starting with research, an initial coding phase, then beta testing and iterations. The current phase involves choosing a programming language (leaning toward C) and addressing technical challenges like encryption and distribution.
Boosting python web apps with protocol buffers & grpc



Boosting python web apps with protocol buffers & grpcNaren Arya This document discusses using Protocol Buffers (Protobuf) and GRPC to boost Python web apps. It begins by explaining why JSON is popular but has limitations. Protobuf provides benefits like binary encoding for smaller size and support for HTTP/2. The key steps to use Protobuf with Python are installing the protoc compiler and generating Python class files from .proto schema files. The document teases additional upcoming slides on working with a real-world example, introducing GRPC, and building GRPC servers and clients in Python using Protobuf to scale microservices.
Pentester++



Pentester++CTruncer This talk is about why I believe having the ability to write tools and/or scripts can help elevate a Pen Testers game to the next level.
The talk is case study driven by the different scenarios I've encountered on assessments and the scripts or tools that have been developed as a result.
Hacking - Breaking Into It



Hacking - Breaking Into ItCTruncer This is the slide deck I gave when presenting at FSU's AITP Meeting. The goal was to give a high level description of what Pen Testing/Red Teaming is and what the job entails.
Making%20R%20Packages%20Under%20Windows



Making%20R%20Packages%20Under%20Windowstutorialsruby The document provides a tutorial for creating R packages under Windows. It outlines the steps to set up the necessary development environment by downloading and installing Rtools, a compiler, Perl, LaTeX, and setting the PATH variable. The key steps for creating a package include: 1) Creating the directory structure with DESCRIPTION, NAMESPACE and subdirectories for code and documentation; 2) Modifying the DESCRIPTION file with package metadata; 3) Creating the NAMESPACE file to export functions; 4) Writing R functions and examples to test them; 5) Compiling any C/C++ code; and 6) Creating documentation files. The tutorial provides a sample package ("test") to demonstrate the process.
Powering tensorflow with big data (apache spark, flink, and beam) dataworks...



Powering tensorflow with big data (apache spark, flink, and beam) dataworks...Holden Karau This document discusses powering TensorFlow with big data tools like Apache Spark, Apache Flink, and Apache Beam. It provides an overview of TensorFlowOnSpark and how Apache Arrow can improve data interchange performance. It also covers the current state of non-JVM support in Beam and what this means for TensorFlow. The document discusses how data processing frameworks like TFX fit with TensorFlow and pre-processing tools like TF.Transform. It concludes by discussing options for using big data tools from outside the JVM like Kafka and Dask.
Understanding how concurrency work in os



Understanding how concurrency work in osGenchiLu1 This document discusses concurrency in operating systems and different programming languages. It explains how concurrency works at the OS level using schedulers and threads/processes. It then compares implementations of concurrency in Python, Java, and Go. Python uses threads but is constrained by the GIL, Java uses native threads, and Go uses lightweight goroutines scheduled across OS threads. The document cautions that while goroutines make concurrency easy, there are still costs to consider. It concludes by noting languages evolve over time and no approach is inherently unable to handle high concurrency applications.
First month with golang - Building Telegram chat bot



First month with golang - Building Telegram chat botDan Tran 1. The document discusses building a chat bot on Telegram using Golang over the first month. It covers getting started, programming logic, analytics, and avoiding spam.
2. Implementation details are provided for polling the Telegram server, handling user responses, and using flow charts to visualize the process.
3. Libraries that can be used to build Telegram bots in Golang are listed, along with examples of existing dictionary bots and links to the author's bot code on GitHub.
MyReplayInZen



MyReplayInZenViacheslav Eremin - The document discusses the respondent's career as a programmer over 30 years, including various projects they have worked on both as a freelancer and leading teams.
- Some of their biggest projects include websites like desen.bg and votpusk.ru, though they note most internet projects are unprofitable for owners.
- They now prefer to work as a freelancer or for employers/investors rather than starting their own projects due to the financial risks involved.
Not Your Fathers C - C Application Development In 2016



Not Your Fathers C - C Application Development In 2016maiktoepfer - The document discusses different approaches for copying strings in C, including strcpy, strncpy, strlcpy, and strcpy_s.
- strcpy can cause buffer overflows if the destination is too small, while strncpy does not guarantee a properly terminated string.
- strlcpy aims to prevent overflows and ensure valid strings, but may truncate and requires external libraries.
- strcpy_s from C11 solves the problems of previous functions and is part of the standard, but support is limited.
Mono - Alternative .NET CLR Implementation



Mono - Alternative .NET CLR ImplementationYulian Slobodyan This document provides an overview of Mono, an open source implementation of C# and the CLR that is binary compatible with Microsoft .NET. The document discusses Mono's compatibility with different versions of .NET, its cross-platform capabilities, and reasons for using Mono including cost savings, compatibility with multiple operating systems, integration with popular open source libraries, support for new platforms and languages, and ability to embed and use for scripting. It concludes with an agenda that includes a Google search on Mono, .NET compatibility details, reasons to use Mono, a demo, and Q&A section.
Funky file formats - 31c3



Funky file formats - 31c3Ange Albertini This document summarizes Ange Albertini's talk on "Funky file Formats". The talk discusses how files can take on multiple formats by exploiting ambiguities and tolerance in file specifications. Examples are given of files that are valid images, archives, documents, and encrypted files simultaneously. The talk also covers steganography techniques like hiding files within other file formats by manipulating metadata or unused portions of file specifications. Overall, the talk illustrates the concept of "format polymorphism" where single files can masquerade as multiple file types to evade detection or trigger different parser behaviors.
A binary chimera - 3 headers & 1 data body in a single file



A binary chimera - 3 headers & 1 data body in a single fileAnge Albertini This document describes a "binary chimera" file format that contains elements of JPEG, PDF, and ZIP file formats within a single file. It does this by including the header information and signatures for each format while reusing the same underlying data. Specifically, it uses JPEG image data and hides the additional PDF and ZIP data through the use of comment segments and dummy stream objects. This allows a single file to be interpreted as any of the three formats while only containing one set of image data.
31c3



31c3Sam Sulaimanov This document discusses using Bluetooth Low Energy (BLE) beacons to sense proximity between phones and beacons. It notes that BLE beacons were introduced in Bluetooth 4.0 and are supported on Android 4.3 and iOS 7. It provides an example of how beacon signal strength can be used to determine if Phone A is in close, medium, or far proximity to a beacon compared to Phone B. The document promotes a nervousnet app for navigation at the 31c3 conference and provides a link for more information.
I2R Labs, Bengaluru, Telecommunication Equipment GPS Modules



I2R Labs, Bengaluru, Telecommunication Equipment GPS ModulesIndiaMART InterMESH Limited We are manufacturers and exporters of electronic and telecommunication equipment like GSM GPRS modem, industrial RF modules etc. These find wide application in telecommunications and mobile industries.
Heartache and Heartbleed - 31c3



Heartache and Heartbleed - 31c3Nick Sullivan Heartache and Heartbleed: An inside look a the aftermath of Heartbleed. Presented at 31c3 in Hamburg on December 29, 2014.
Personal tracking devices - A Journey Into The True Dark Net

Personal tracking devices - A Journey Into The True Dark NetSilvia Puglisi 31C3 presentation on the status of online privacy and marketing tracking.
Also available on http://www.nopressure.co.uk/31C3/
Ad
More Related Content
What's hot (16)
Python for IoT, A return of experience



Python for IoT, A return of experienceAlexandre Abadie Python for IoT discusses building Pyaiot, a system to connect constrained IoT devices to the web. Pyaiot uses common IoT protocols like CoAP and MQTT to allow bidirectional communication between low-power devices and a web dashboard. The author details how Pyaiot was implemented using Python and asyncio to be multi-protocol, modular, and reactive in a real-time manner. Lessons learned include some initial challenges with asyncio, but that Python facilitated fast development of the complex system to meet the initial requirements.
Phpconf taiwan-2012



Phpconf taiwan-2012Hash Lin The document discusses a new approach to generating DOCX, DOC, and PDF files using templates with the Zend Framework 2. It introduces LiveDocx, a SOAP-based document generation service with a PHP API called ZendService_LiveDocx. The template approach allows merging data into document templates to generate files in multiple formats like DOCX, DOC, HTML, RTF, PDF, and TXT with three simple steps: creating a template, populating merge fields with data, and writing the generated document to disk. Examples and demonstrations are provided.
PostgreSQL Development Today: 9.0



PostgreSQL Development Today: 9.0PostgreSQL Experts, Inc. PostgreSQL 9.0 is entering its final development stage with many new features planned for inclusion. Some key features include hot standby replication for high availability, synchronous replication for data integrity, and performance improvements. Developers are seeking community testing and feedback to ensure quality and identify issues prior to the beta release. The presentation encourages contributions to help shape PostgreSQL's future and highlights ways for developers to get involved.
How to Dockerize, Automate the Build and Deployment Process for Flutter?



How to Dockerize, Automate the Build and Deployment Process for Flutter?9 series This document outlines the steps to dockerize, automate builds, and deploy Flutter apps. It discusses setting up Docker and creating a Dockerfile. It describes creating a devcontainer folder structure and adding Flutter code. The steps to run the Docker container with VS Code and verify setup are provided. It concludes with running Flutter commands in the container to create and deploy projects.
Egress-Assess and Owning Data Exfiltration



Egress-Assess and Owning Data ExfiltrationCTruncer This talk discusses how Egress-Assess can be used to help attackers and defenders learn how to exfiltrate data outside of their network over a variety of protocols, describes how data is exfiltrated over different supported protocols, and demonstrates the weaponization of the tool!
Stashaway 1



Stashaway 1priestc This document discusses Stashaway, a tool for organizing digital media by moving files to remote cloud storage. It aims to address issues with local storage becoming expensive and cloud storage becoming popular, requiring data to move from local to remote locations. The document outlines Stashaway's features like uploading files to cloud storage, listing and streaming files remotely, and planned features like tagging and duplicate detection. It provides a development timeline starting with research, an initial coding phase, then beta testing and iterations. The current phase involves choosing a programming language (leaning toward C) and addressing technical challenges like encryption and distribution.
Boosting python web apps with protocol buffers & grpc



Boosting python web apps with protocol buffers & grpcNaren Arya This document discusses using Protocol Buffers (Protobuf) and GRPC to boost Python web apps. It begins by explaining why JSON is popular but has limitations. Protobuf provides benefits like binary encoding for smaller size and support for HTTP/2. The key steps to use Protobuf with Python are installing the protoc compiler and generating Python class files from .proto schema files. The document teases additional upcoming slides on working with a real-world example, introducing GRPC, and building GRPC servers and clients in Python using Protobuf to scale microservices.
Pentester++



Pentester++CTruncer This talk is about why I believe having the ability to write tools and/or scripts can help elevate a Pen Testers game to the next level.
The talk is case study driven by the different scenarios I've encountered on assessments and the scripts or tools that have been developed as a result.
Hacking - Breaking Into It



Hacking - Breaking Into ItCTruncer This is the slide deck I gave when presenting at FSU's AITP Meeting. The goal was to give a high level description of what Pen Testing/Red Teaming is and what the job entails.
Making%20R%20Packages%20Under%20Windows



Making%20R%20Packages%20Under%20Windowstutorialsruby The document provides a tutorial for creating R packages under Windows. It outlines the steps to set up the necessary development environment by downloading and installing Rtools, a compiler, Perl, LaTeX, and setting the PATH variable. The key steps for creating a package include: 1) Creating the directory structure with DESCRIPTION, NAMESPACE and subdirectories for code and documentation; 2) Modifying the DESCRIPTION file with package metadata; 3) Creating the NAMESPACE file to export functions; 4) Writing R functions and examples to test them; 5) Compiling any C/C++ code; and 6) Creating documentation files. The tutorial provides a sample package ("test") to demonstrate the process.
Powering tensorflow with big data (apache spark, flink, and beam) dataworks...



Powering tensorflow with big data (apache spark, flink, and beam) dataworks...Holden Karau This document discusses powering TensorFlow with big data tools like Apache Spark, Apache Flink, and Apache Beam. It provides an overview of TensorFlowOnSpark and how Apache Arrow can improve data interchange performance. It also covers the current state of non-JVM support in Beam and what this means for TensorFlow. The document discusses how data processing frameworks like TFX fit with TensorFlow and pre-processing tools like TF.Transform. It concludes by discussing options for using big data tools from outside the JVM like Kafka and Dask.
Understanding how concurrency work in os



Understanding how concurrency work in osGenchiLu1 This document discusses concurrency in operating systems and different programming languages. It explains how concurrency works at the OS level using schedulers and threads/processes. It then compares implementations of concurrency in Python, Java, and Go. Python uses threads but is constrained by the GIL, Java uses native threads, and Go uses lightweight goroutines scheduled across OS threads. The document cautions that while goroutines make concurrency easy, there are still costs to consider. It concludes by noting languages evolve over time and no approach is inherently unable to handle high concurrency applications.
First month with golang - Building Telegram chat bot



First month with golang - Building Telegram chat botDan Tran 1. The document discusses building a chat bot on Telegram using Golang over the first month. It covers getting started, programming logic, analytics, and avoiding spam.
2. Implementation details are provided for polling the Telegram server, handling user responses, and using flow charts to visualize the process.
3. Libraries that can be used to build Telegram bots in Golang are listed, along with examples of existing dictionary bots and links to the author's bot code on GitHub.
MyReplayInZen



MyReplayInZenViacheslav Eremin - The document discusses the respondent's career as a programmer over 30 years, including various projects they have worked on both as a freelancer and leading teams.
- Some of their biggest projects include websites like desen.bg and votpusk.ru, though they note most internet projects are unprofitable for owners.
- They now prefer to work as a freelancer or for employers/investors rather than starting their own projects due to the financial risks involved.
Not Your Fathers C - C Application Development In 2016



Not Your Fathers C - C Application Development In 2016maiktoepfer - The document discusses different approaches for copying strings in C, including strcpy, strncpy, strlcpy, and strcpy_s.
- strcpy can cause buffer overflows if the destination is too small, while strncpy does not guarantee a properly terminated string.
- strlcpy aims to prevent overflows and ensure valid strings, but may truncate and requires external libraries.
- strcpy_s from C11 solves the problems of previous functions and is part of the standard, but support is limited.
Mono - Alternative .NET CLR Implementation



Mono - Alternative .NET CLR ImplementationYulian Slobodyan This document provides an overview of Mono, an open source implementation of C# and the CLR that is binary compatible with Microsoft .NET. The document discusses Mono's compatibility with different versions of .NET, its cross-platform capabilities, and reasons for using Mono including cost savings, compatibility with multiple operating systems, integration with popular open source libraries, support for new platforms and languages, and ability to embed and use for scripting. It concludes with an agenda that includes a Google search on Mono, .NET compatibility details, reasons to use Mono, a demo, and Q&A section.
Viewers also liked (6)
Funky file formats - 31c3



Funky file formats - 31c3Ange Albertini This document summarizes Ange Albertini's talk on "Funky file Formats". The talk discusses how files can take on multiple formats by exploiting ambiguities and tolerance in file specifications. Examples are given of files that are valid images, archives, documents, and encrypted files simultaneously. The talk also covers steganography techniques like hiding files within other file formats by manipulating metadata or unused portions of file specifications. Overall, the talk illustrates the concept of "format polymorphism" where single files can masquerade as multiple file types to evade detection or trigger different parser behaviors.
A binary chimera - 3 headers & 1 data body in a single file



A binary chimera - 3 headers & 1 data body in a single fileAnge Albertini This document describes a "binary chimera" file format that contains elements of JPEG, PDF, and ZIP file formats within a single file. It does this by including the header information and signatures for each format while reusing the same underlying data. Specifically, it uses JPEG image data and hides the additional PDF and ZIP data through the use of comment segments and dummy stream objects. This allows a single file to be interpreted as any of the three formats while only containing one set of image data.
31c3



31c3Sam Sulaimanov This document discusses using Bluetooth Low Energy (BLE) beacons to sense proximity between phones and beacons. It notes that BLE beacons were introduced in Bluetooth 4.0 and are supported on Android 4.3 and iOS 7. It provides an example of how beacon signal strength can be used to determine if Phone A is in close, medium, or far proximity to a beacon compared to Phone B. The document promotes a nervousnet app for navigation at the 31c3 conference and provides a link for more information.
I2R Labs, Bengaluru, Telecommunication Equipment GPS Modules



I2R Labs, Bengaluru, Telecommunication Equipment GPS ModulesIndiaMART InterMESH Limited We are manufacturers and exporters of electronic and telecommunication equipment like GSM GPRS modem, industrial RF modules etc. These find wide application in telecommunications and mobile industries.
Heartache and Heartbleed - 31c3



Heartache and Heartbleed - 31c3Nick Sullivan Heartache and Heartbleed: An inside look a the aftermath of Heartbleed. Presented at 31c3 in Hamburg on December 29, 2014.
Personal tracking devices - A Journey Into The True Dark Net

Personal tracking devices - A Journey Into The True Dark NetSilvia Puglisi 31C3 presentation on the status of online privacy and marketing tracking.
Also available on http://www.nopressure.co.uk/31C3/
Ad
Similar to Messing with binary formats (20)
PDF secrets - hiding & revealing secrets in PDF documents



PDF secrets - hiding & revealing secrets in PDF documentsAnge Albertini This document provides a three-part summary of a presentation on hiding and revealing secrets in PDF documents:
1. Common methods for hiding text or images in a PDF can be circumvented, as extraction tools can still access even hidden content. Text can be copied and imaged extracted from layers or formatting meant to conceal them.
2. PDF documents are composed of objects, streams, and other elements that provide structure but also opportunities to manipulate content. Understanding the PDF format internals can enable more advanced techniques for hiding or encrypting sensitive information.
3. While some viewers or protections try to block copying or extraction, workarounds usually exist. The presenter demonstrates various hiding methods and their limitations, encouraging studying
PDF - Secrets - 140519092839-phpapp01



PDF - Secrets - 140519092839-phpapp01dumbfuckery This document provides a three-part summary of a presentation on hiding and revealing secrets in PDF documents:
1. Common methods for hiding text or images in a PDF can be circumvented, as extraction tools can still access even hidden content. Text can be copied and imaged can be extracted from layers or colors designed to hide them.
2. PDF documents are composed of objects, streams, and other elements that provide opportunities to hide content in plain sight. Understanding the PDF format is necessary to fully manipulate or secure document contents.
3. More advanced techniques exist for hiding content, such as manipulating stream filters or encodings. While protection methods can obscure content, full security is difficult to achieve given the inherent properties of
PDF: myths vs facts



PDF: myths vs factsAnge Albertini A presentation for the digital preservation community,
during a Digital Preservation Coalition event at Oxford,
15th July 2015
A bit more of PE



A bit more of PEAnge Albertini This document discusses oddities that can be found in Portable Executable (PE) file formats. It describes how static elements like the DOS header, image base, entry point, and sections can be manipulated in non-standard ways. It also explains how dynamic loading behaviors are affected by these oddities, such as through the thread local storage, relocations, and different parsing of headers and data directories between on-disk and in-memory formats. The document promotes further understanding of PE files through the use of proof of concepts provided on related websites.
Linux as a gaming platform, ideology aside



Linux as a gaming platform, ideology asideLeszek Godlewski Linux commonly connotes with open-source zealots and a small PC market
share, not blockbuster video games. However, the arrival of Steam on
the platform might change the outlook quite dramatically, and Linux
support may soon become a must-have feature for your game. Setting the
open-source ideology aside, this lecture is an overview of the
technical challenges a game developer may face while porting their
game to this platform, along with solutions.
Cpb2010



Cpb2010Fardin Na Madeceng This document provides instructions for installing and getting started with C++ Builder 2010 Professional. It discusses installing the software and additional components, exploring the documentation and help resources, creating traditional Windows API programs, using OpenGL for 3D graphics and games, and includes code examples for a basic web browser application.
Caring for file formats



Caring for file formatsAnge Albertini Presented at Troopers 2016.
When Infosec and Digipres share interests...
TL;DR
- Attack surface with file formats is too big.
- Specs are useless (just a nice ‘guide’), not representing reality.
- We can’t deprecate formats because we can’t preserve and we can’t define how they really work
- We need open good libraries to simplify landscape, and create a corpus to express the reality of file format, which gives us real “documentation”.
- Then we can preserve and deprecate older format, which reduces attack surface.
- From then on, we can focus on making the present more secure.
- We don't need new formats: reality will diverge from the specs anyway - we need 'alive' (up to date, traceable) specs.
Drupalhagen 2014 kiss omg ftw



Drupalhagen 2014 kiss omg ftwArne Jørgensen Drupalhagen 2014 talk about strategies for Git repository structures and tools to support good workflows.
Docker and Go: why did we decide to write Docker in Go?



Docker and Go: why did we decide to write Docker in Go?Jérôme Petazzoni Docker is currently one of the most popular Go projects. After a (quick) Docker intro, we will discuss why we picked Go, and how it turned out for us.
We tried to list all the drawbacks and minor inconveniences that we met while developing Docker; not to complain about Go, but to give the audience an idea of what to expect. Depending on your project, those drawbacks could be minor inconveniences or showstoppers; we thought you would want to know about them to help you to make the right choice!
Simplifying training deep and serving learning models with big data in python...



Simplifying training deep and serving learning models with big data in python...Holden Karau This document discusses simplifying training and serving deep learning models with big data in Python using TensorFlow, Apache Beam, and Apache Flink. It covers using TF.Transform to preprocess data, running TensorFlow models on Spark using TensorFlowOnSpark, and the progress being made on non-JVM support in Apache Beam and TensorFlow on Flink. It also briefly discusses other big data systems and the challenges of interacting with them from outside the Java Virtual Machine.
Pen Testing Development



Pen Testing DevelopmentCTruncer This presentation was given to a group of SFS students at GW. It's designed to be semi-case study driven on the problems I've encountered on assessments and how programming can help solve them.
Powering Tensorflow with big data using Apache Beam, Flink, and Spark - OSCON...



Powering Tensorflow with big data using Apache Beam, Flink, and Spark - OSCON...Holden Karau TensorFlow is all kinds of fancy, from helping startups raising their series A in Silicon Valley to detecting if something is a cat. However, when things start to get “real,” you may find yourself no longer just dealing with mnist.csv but instead needing do large-scale data prep as well as training.
Holden Karau details how to use TensorFlow in conjunction with Apache Spark, Flink, and Beam to create a full machine learning pipeline—including the annoying feature engineering and data prep components that we like to pretend don’t exist. Holden also explains why these feature prep stages need to be integrated into the serving layer. She concludes by examining changing industry trends, like Apache Arrow, and how they impact cross-language development for things like deep learning. Even if you’re not trying to raise a round of funding in Silicon Valley, this talk will give you tools to do interesting machine learning problems at scale.
Dfrws eu 2014 rekall workshop



Dfrws eu 2014 rekall workshopTamas K Lengyel The document provides an overview of memory forensics and the Rekall memory analysis tool. It discusses why memory forensics is useful, describes how Rekall supports multiple operating systems through profiles, and covers memory imaging, virtual memory concepts, and analyzing live memory. Rekall's interfaces like the command line, console, notebook, and web console are also introduced.
Mender.io | Develop embedded applications faster | Comparing C and Golang



Mender.io | Develop embedded applications faster | Comparing C and GolangMender.io Mender.io's Marcin Pasinski discusses the tradeoffs of developing embedded applications with both C and Golang
Rusty Python



Rusty PythonRangHo Lee This document discusses combining Rust and Python to create a new "hip" programming language. It proposes two approaches: 1) Building Rust extensions for Python to improve performance of Python code. Rust could replace C and provide memory safety and better performance for Python extensions. 2) Building a Python interpreter using Rust (RustPython), which provides benefits like memory safety and borrowing rules from Rust. However, a Rust-based Python interpreter still has a long way to go before matching the performance and capabilities of CPython. In the end, the document acknowledges both Rust and Python have limitations and neither can fully "replace" the other.
Castle Game Engine: intro, web, IFC, 3D scanning, mORMot



Castle Game Engine: intro, web, IFC, 3D scanning, mORMotMichalis Kamburelis Castle Game Engine presentation from the Pascal Cafe 2025, spanning a few topics:
- Introduction to Castle Game Engine https://castle-engine.io/
- developing web applications https://castle-engine.io/web
- using IFC format https://castle-engine.io/ifc
- 3D scanning https://github.com/castle-engine/conference-pascal-cafe-2025/
- mORMot example integration https://github.com/castle-engine/castle-and-mormot-collaborative-editing/
Drupal Day 2011 - Features: una vita felice



Drupal Day 2011 - Features: una vita feliceDrupalDay Talk di Daniele Piaggesi & Luca Corbo
Il modulo Features per Drupal 7, permette al developer di costruire singole funzionalità riusabili in molteplici situazioni, oltre a disaccoppiare definitivamente la fase configurativa del CMS con la sua base dati.
In questa sessione vedremo velocemente dei casi d'uso del sistema di ""featuring"" di Drupal, quando usarle e con quali accortezze. E perchè questa funzionalità rende Drupal un CMS decisamente più duttile e maturo della sua concorrenza.
Python in Industry



Python in IndustryDharmit Shah Slides from the talk given at Nirma University. Audience comprised of fifth semester Electronics & Communications (EC) Engineering students.
Introduction to google chromebooks and chromeboxes presentation tech-talk



Introduction to google chromebooks and chromeboxes presentation tech-talkRoel Palmaers Chromebooks are designed as internet appliances that focus on running the Chrome web browser. They have limited local storage and processing capabilities compared to traditional computers, but updates are handled automatically to keep the system secure and stable. Chromebooks can be easily shared between users since data is stored in the cloud and the systems cannot be easily reconfigured. However, putting a Chromebook in developer mode allows more advanced users to utilize the underlying Linux system and add additional software.
Ruxmon.2013-08.-.CodeBro!



Ruxmon.2013-08.-.CodeBro!Christophe Alladoum This document discusses improving static code review using abstract syntax tree (AST)-based code analysis. It describes using the Clang compiler's AST parsing capabilities via its Python API to build a tool called CodeBro that allows navigating and analyzing C/C++ code structure and calling relationships to potentially find vulnerabilities. Key features of CodeBro highlighted include being open source, built with Django and Python, using Clang for parsing, and having an extensible plugin system for adding custom analysis modules. Future enhancements discussed include improving various language support and analyses.
Ad
More from Ange Albertini (20)
Overview of file type identifiers (HackLu)



Overview of file type identifiers (HackLu)Ange Albertini Yara, LibMagic (file, binwalk, polyfile), TrID, Yara, Magika, PeID, Pronom, FDD, ShareMime, DiE...
How do they work? What are their pros and cons, their limitations, their risks?
Presented at Hack.Lu on the 24th October 2024.
Video recording: https://youtu.be/PBbld8xB2Bo
A question of time - Troopers 2024 Keynote



A question of time - Troopers 2024 KeynoteAnge Albertini Keynote at Troopers, 26 June 2024, Heidelberg.
Technical challenges with file formats



Technical challenges with file formatsAnge Albertini "Technical challenges"? More like horrors!
Let's explore first the technical debt of old file formats,
with the evolution of the "MP3" format.
Then we go through more recent forms of file format abuses and tools:
polyglots, polymocks, and crypto-polyglots.
Last, an overview of recent collisions and other forms of art with MD5.
They say that with file formats, "specs are enough".
Should we laugh, cry or run away screaming?
Presented at Digital Preservation Coalition's CyberSec & DigiPres event.
Relations between archive formats



Relations between archive formatsAnge Albertini The document discusses different archive formats and their relationships. It begins with an introduction to the presenter and then covers zlib, gzip, and zip file formats. Zlib and gzip both wrap deflate compression, but in different ways, so while the compressed data can be transferred between them, the formats are not directly compatible. Zip can use deflate but also other compression methods and a different one for each file. In conclusion, deflate is a common algorithm while the various formats wrap it with different headers and metadata.
Abusing archive file formats



Abusing archive file formatsAnge Albertini This document is a slide presentation about hash collisions and generating polyglot files that have the same hash but different content. It discusses existing attacks on hashes like MD5 and SHA1 that allow two files to be generated with the same hash. It then explains how collisions can be generated for ZIP and TAR.GZ files by manipulating the ZIP file format in a way that maintains compatibility with ZIP parsers but results in different files with the same hash. Examples of colliding file pairs are shown with identical prefixes and suffixes and differing collision blocks in the middle.
TimeCryption



TimeCryptionAnge Albertini Clean now, malicious later.
AKA Abusing one-time pads with binary polyglots.
April 08, 2021 Stefan Kölbl, Ange Albertini
Recording @ https://www.youtube.com/watch?v=liancIA1m9w
You are *not* an idiot



You are *not* an idiotAnge Albertini You are *not* an idiot ~ or maybe we're all idiots.
Keynote at NorthSec 2021.
Talking about school, failure, success, diploma, impostor syndrom, manipulators, burn out, suicide, and how to deal with them.
The talk delivery was more personal, the slides are kept generic.
The recording is available @ https://youtu.be/Iu70J49bPlE?t=20869 (starts at 5:47:49)
Improving file formats



Improving file formatsAnge Albertini The document discusses the author's experience with malware and file formats over 13 years, noting how specifications are often outdated and incomplete which can lead to misunderstandings. It advocates for better tools to analyze, document, and validate file formats to improve understanding of their current usage and behaviors. The author has created several open source projects focused on file format analysis and validation.
KILL MD5



KILL MD5Ange Albertini Demystifying hash collisions.
Pass the Salt, 1st July 2019.
video @ https://passthesalt.ubicast.tv/videos/kill-md5-demystifying-hash-collisions/
Hack.Lu, 22 October 2019.
video @ https://www.youtube.com/watch?v=JXazRQ0APpI
No more dumb hex!



No more dumb hex!Ange Albertini Troopers, Heidelberg, Germany
21 March 2019
co-presented and designed with Rafał Hirsz
https://github.com/corkami/sbud
https://github.com/evoL/albert
Beyond your studies



Beyond your studiesAnge Albertini Beyond your studies ~ You studied X at Y. now what?
HackPra, July 2018
A student's life ago, the author somehow managed to graduate.
On the way, he made a lot of mistakes -- and he still does.
A few people since called him 'successful', but LOL, if only they knew....
And now, the author will do another (big!) mistake:
instead of hiding in shame as he probably should,
he'll share his mistakes with anyone bored enough to attend,
in the hope that he's the last person to ever look that dumb to commit such mistakes.
If you're a genius and you know what to do in life, please skip this. Seriously.
If, like the author at the time, you wonder WTF is going on with graduation, professional work and life, then hopefully you learn a few things. Maybe.
Btw the author is 42 (WTF - old!).
Maybe that will help to provide a few answers.
An introduction to inkscape



An introduction to inkscapeAnge Albertini This document provides an introduction and overview of Inkscape, an open-source vector graphics editor. It discusses Inkscape's features such as its use of Scalable Vector Graphics (SVG), tools for drawing objects and manipulating nodes, layers, transformations, and more. The document also includes tutorials for tasks like tracing an image, creating a poster, and converting code snippets to SVG. Throughout, it emphasizes that Inkscape is non-destructive and files remain editable, while also noting some limitations like unsupported gradients along paths.
The challenges of file formats



The challenges of file formatsAnge Albertini The document discusses the author's perspectives on file formats after over 30 years of experience working with computers and digital preservation. The author believes specifications are imperfect and do not fully define what constitutes a valid file, as implementations can interpret specifications differently and become outdated. The author has experimented with creating extreme files that push the boundaries of specifications in order to understand formats better and find potential issues.
Exploiting hash collisions



Exploiting hash collisionsAnge Albertini Exploiting (identical prefix) hash collisions.
Presented at BlackAlps in November 2017
PoCs @ https://github.com/corkami/pocs/tree/master/pdf/shattered
recording @ https://www.youtube.com/watch?v=Y-oJWEYKVLA
Infosec & failures



Infosec & failuresAnge Albertini video recording https://www.youtube.com/watch?v=erZ2JlfTtcE
(smaller deck, but w/ more personal details)
Ange Ąż杏 Albertini
Hack.Lu - October 2017
Connecting communities



Connecting communitiesAnge Albertini This document contains the table of contents for an issue of PoC||GTFO, a journal for sharing technical content in unconventional ways. It lists over 60 articles across various topics including hardware hacking, firmware reverse engineering, embedded exploitation, and unusual file formats. The sections are numbered and titled with references to hacking, unconventional thinking, and sharing knowledge in new ways.
TASBot - the perfectionist



TASBot - the perfectionistAnge Albertini https://www.youtube.com/watch?v=s-bKWT9fj8Y
written and presented by dwangoAC at DEF CON 24, SVLUG & NBLUG
[slides collaboration]
Hacks in video games



Hacks in video gamesAnge Albertini Game developers are able to create better video games than what the limitations of computers allow by understanding how things truly work at a detailed level. They discovered tricks to get around limitations, such as updating colors rapidly to display more than the limited palette or changing sounds quickly to generate new voices. Understanding the underlying systems allows developers to creatively solve problems like drawing huge animated monsters that surpass the small allowed object sizes. This knowledge of how things really function provides advantages beyond initial restrictions.
Trusting files (and their formats)



Trusting files (and their formats)Ange Albertini 1. File formats are complex with many stakeholders who interpret specifications differently, leading to divergent implementations over time.
2. Specifications are often incomplete, unclear, non-free, or do not reflect reality, making it difficult to determine what a valid file is.
3. Relying on specifications alone is not sufficient - one must also analyze sample files and code to understand how file formats work in practice.
Let's write a PDF file



Let's write a PDF fileAnge Albertini The document provides a step-by-step guide to writing a basic "Hello World" PDF file. It explains the overall PDF file structure and key elements like the file body, cross-reference table, trailer, and objects. Objects are used to define things like the catalog, pages, and a single page. The guide demonstrates creating three objects - one for the catalog that refers to a pages object, which in turn refers to a page object defining a single page.
Recently uploaded (20)
An Overview of Salesforce Health Cloud & How is it Transforming Patient Care



An Overview of Salesforce Health Cloud & How is it Transforming Patient CareCyntexa Healthcare providers face mounting pressure to deliver personalized, efficient, and secure patient experiences. According to Salesforce, “71% of providers need patient relationship management like Health Cloud to deliver high‑quality care.” Legacy systems, siloed data, and manual processes stand in the way of modern care delivery. Salesforce Health Cloud unifies clinical, operational, and engagement data on one platform—empowering care teams to collaborate, automate workflows, and focus on what matters most: the patient.
In this on‑demand webinar, Shrey Sharma and Vishwajeet Srivastava unveil how Health Cloud is driving a digital revolution in healthcare. You’ll see how AI‑driven insights, flexible data models, and secure interoperability transform patient outreach, care coordination, and outcomes measurement. Whether you’re in a hospital system, a specialty clinic, or a home‑care network, this session delivers actionable strategies to modernize your technology stack and elevate patient care.
What You’ll Learn
Healthcare Industry Trends & Challenges
Key shifts: value‑based care, telehealth expansion, and patient engagement expectations.
Common obstacles: fragmented EHRs, disconnected care teams, and compliance burdens.
Health Cloud Data Model & Architecture
Patient 360: Consolidate medical history, care plans, social determinants, and device data into one unified record.
Care Plans & Pathways: Model treatment protocols, milestones, and tasks that guide caregivers through evidence‑based workflows.
AI‑Driven Innovations
Einstein for Health: Predict patient risk, recommend interventions, and automate follow‑up outreach.
Natural Language Processing: Extract insights from clinical notes, patient messages, and external records.
Core Features & Capabilities
Care Collaboration Workspace: Real‑time care team chat, task assignment, and secure document sharing.
Consent Management & Trust Layer: Built‑in HIPAA‑grade security, audit trails, and granular access controls.
Remote Monitoring Integration: Ingest IoT device vitals and trigger care alerts automatically.
Use Cases & Outcomes
Chronic Care Management: 30% reduction in hospital readmissions via proactive outreach and care plan adherence tracking.
Telehealth & Virtual Care: 50% increase in patient satisfaction by coordinating virtual visits, follow‑ups, and digital therapeutics in one view.
Population Health: Segment high‑risk cohorts, automate preventive screening reminders, and measure program ROI.
Live Demo Highlights
Watch Shrey and Vishwajeet configure a care plan: set up risk scores, assign tasks, and automate patient check‑ins—all within Health Cloud.
See how alerts from a wearable device trigger a care coordinator workflow, ensuring timely intervention.
Missed the live session? Stream the full recording or download the deck now to get detailed configuration steps, best‑practice checklists, and implementation templates.
🔗 Watch & Download: https://www.youtube.com/live/0HiEm
AI-proof your career by Olivier Vroom and David WIlliamson



AI-proof your career by Olivier Vroom and David WIlliamsonUXPA Boston This talk explores the evolving role of AI in UX design and the ongoing debate about whether AI might replace UX professionals. The discussion will explore how AI is shaping workflows, where human skills remain essential, and how designers can adapt. Attendees will gain insights into the ways AI can enhance creativity, streamline processes, and create new challenges for UX professionals.
AI’s influence on UX is growing, from automating research analysis to generating design prototypes. While some believe AI could make most workers (including designers) obsolete, AI can also be seen as an enhancement rather than a replacement. This session, featuring two speakers, will examine both perspectives and provide practical ideas for integrating AI into design workflows, developing AI literacy, and staying adaptable as the field continues to change.
The session will include a relatively long guided Q&A and discussion section, encouraging attendees to philosophize, share reflections, and explore open-ended questions about AI’s long-term impact on the UX profession.
Viam product demo_ Deploying and scaling AI with hardware.pdf



Viam product demo_ Deploying and scaling AI with hardware.pdfcamilalamoratta Building AI-powered products that interact with the physical world often means navigating complex integration challenges, especially on resource-constrained devices.
You'll learn:
- How Viam's platform bridges the gap between AI, data, and physical devices
- A step-by-step walkthrough of computer vision running at the edge
- Practical approaches to common integration hurdles
- How teams are scaling hardware + software solutions together
Whether you're a developer, engineering manager, or product builder, this demo will show you a faster path to creating intelligent machines and systems.
Resources:
- Documentation: https://on.viam.com/docs
- Community: https://discord.com/invite/viam
- Hands-on: https://on.viam.com/codelabs
- Future Events: https://on.viam.com/updates-upcoming-events
- Request personalized demo: https://on.viam.com/request-demo
AI Agents at Work: UiPath, Maestro & the Future of Documents



AI Agents at Work: UiPath, Maestro & the Future of DocumentsUiPathCommunity Do you find yourself whispering sweet nothings to OCR engines, praying they catch that one rogue VAT number? Well, it’s time to let automation do the heavy lifting – with brains and brawn.
Join us for a high-energy UiPath Community session where we crack open the vault of Document Understanding and introduce you to the future’s favorite buzzword with actual bite: Agentic AI.
This isn’t your average “drag-and-drop-and-hope-it-works” demo. We’re going deep into how intelligent automation can revolutionize the way you deal with invoices – turning chaos into clarity and PDFs into productivity. From real-world use cases to live demos, we’ll show you how to move from manually verifying line items to sipping your coffee while your digital coworkers do the grunt work:
📕 Agenda:
🤖 Bots with brains: how Agentic AI takes automation from reactive to proactive
🔍 How DU handles everything from pristine PDFs to coffee-stained scans (we’ve seen it all)
🧠 The magic of context-aware AI agents who actually know what they’re doing
💥 A live walkthrough that’s part tech, part magic trick (minus the smoke and mirrors)
🗣️ Honest lessons, best practices, and “don’t do this unless you enjoy crying” warnings from the field
So whether you’re an automation veteran or you still think “AI” stands for “Another Invoice,” this session will leave you laughing, learning, and ready to level up your invoice game.
Don’t miss your chance to see how UiPath, DU, and Agentic AI can team up to turn your invoice nightmares into automation dreams.
This session streamed live on May 07, 2025, 13:00 GMT.
Join us and check out all our past and upcoming UiPath Community sessions at:
👉 https://community.uipath.com/dublin-belfast/
Artificial_Intelligence_in_Everyday_Life.pptx



Artificial_Intelligence_in_Everyday_Life.pptx03ANMOLCHAURASIYA Introduction to AI
History and evolution
Types of AI (Narrow, General, Super AI)
AI in smartphones
AI in healthcare
AI in transportation (self-driving cars)
AI in personal assistants (Alexa, Siri)
AI in finance and fraud detection
Challenges and ethical concerns
Future scope
Conclusion
References
On-Device or Remote? On the Energy Efficiency of Fetching LLM-Generated Conte...



On-Device or Remote? On the Energy Efficiency of Fetching LLM-Generated Conte...Ivano Malavolta Slides of the presentation by Vincenzo Stoico at the main track of the 4th International Conference on AI Engineering (CAIN 2025).
The paper is available here: http://www.ivanomalavolta.com/files/papers/CAIN_2025.pdf
Build With AI - In Person Session Slides.pdf



Build With AI - In Person Session Slides.pdfGoogle Developer Group - Harare Build with AI events are communityled, handson activities hosted by Google Developer Groups and Google Developer Groups on Campus across the world from February 1 to July 31 2025. These events aim to help developers acquire and apply Generative AI skills to build and integrate applications using the latest Google AI technologies, including AI Studio, the Gemini and Gemma family of models, and Vertex AI. This particular event series includes Thematic Hands on Workshop: Guided learning on specific AI tools or topics as well as a prequel to the Hackathon to foster innovation using Google AI tools.
Dark Dynamism: drones, dark factories and deurbanization



Dark Dynamism: drones, dark factories and deurbanizationJakub Šimek Startup villages are the next frontier on the road to network states. This book aims to serve as a practical guide to bootstrap a desired future that is both definite and optimistic, to quote Peter Thiel’s framework.
Dark Dynamism is my second book, a kind of sequel to Bespoke Balajisms I published on Kindle in 2024. The first book was about 90 ideas of Balaji Srinivasan and 10 of my own concepts, I built on top of his thinking.
In Dark Dynamism, I focus on my ideas I played with over the last 8 years, inspired by Balaji Srinivasan, Alexander Bard and many people from the Game B and IDW scenes.
fennec fox optimization algorithm for optimal solution



fennec fox optimization algorithm for optimal solutionshallal2 Imagine you have a group of fennec foxes searching for the best spot to find food (the optimal solution to a problem). Each fox represents a possible solution and carries a unique "strategy" (set of parameters) to find food. These strategies are organized in a table (matrix X), where each row is a fox, and each column is a parameter they adjust, like digging depth or speed.
Building the Customer Identity Community, Together.pdf



Building the Customer Identity Community, Together.pdfCheryl Hung https://www.oicheryl.com
Mastering Testing in the Modern F&B Landscape



Mastering Testing in the Modern F&B Landscapemarketing943205 Dive into our presentation to explore the unique software testing challenges the Food and Beverage sector faces today. We’ll walk you through essential best practices for quality assurance and show you exactly how Qyrus, with our intelligent testing platform and innovative AlVerse, provides tailored solutions to help your F&B business master these challenges. Discover how you can ensure quality and innovate with confidence in this exciting digital era.
Integrating FME with Python: Tips, Demos, and Best Practices for Powerful Aut...



Integrating FME with Python: Tips, Demos, and Best Practices for Powerful Aut...Safe Software FME is renowned for its no-code data integration capabilities, but that doesn’t mean you have to abandon coding entirely. In fact, Python’s versatility can enhance FME workflows, enabling users to migrate data, automate tasks, and build custom solutions. Whether you’re looking to incorporate Python scripts or use ArcPy within FME, this webinar is for you!
Join us as we dive into the integration of Python with FME, exploring practical tips, demos, and the flexibility of Python across different FME versions. You’ll also learn how to manage SSL integration and tackle Python package installations using the command line.
During the hour, we’ll discuss:
-Top reasons for using Python within FME workflows
-Demos on integrating Python scripts and handling attributes
-Best practices for startup and shutdown scripts
-Using FME’s AI Assist to optimize your workflows
-Setting up FME Objects for external IDEs
Because when you need to code, the focus should be on results—not compatibility issues. Join us to master the art of combining Python and FME for powerful automation and data migration.
AI x Accessibility UXPA by Stew Smith and Olivier Vroom



AI x Accessibility UXPA by Stew Smith and Olivier VroomUXPA Boston This presentation explores how AI will transform traditional assistive technologies and create entirely new ways to increase inclusion. The presenters will focus specifically on AI's potential to better serve the deaf community - an area where both presenters have made connections and are conducting research. The presenters are conducting a survey of the deaf community to better understand their needs and will present the findings and implications during the presentation.
AI integration into accessibility solutions marks one of the most significant technological advancements of our time. For UX designers and researchers, a basic understanding of how AI systems operate, from simple rule-based algorithms to sophisticated neural networks, offers crucial knowledge for creating more intuitive and adaptable interfaces to improve the lives of 1.3 billion people worldwide living with disabilities.
Attendees will gain valuable insights into designing AI-powered accessibility solutions prioritizing real user needs. The presenters will present practical human-centered design frameworks that balance AI’s capabilities with real-world user experiences. By exploring current applications, emerging innovations, and firsthand perspectives from the deaf community, this presentation will equip UX professionals with actionable strategies to create more inclusive digital experiences that address a wide range of accessibility challenges.
Optima Cyber - Maritime Cyber Security - MSSP Services - Manolis Sfakianakis ...



Optima Cyber - Maritime Cyber Security - MSSP Services - Manolis Sfakianakis ...Mike Mingos In an era where ships are floating data centers and cybercriminals sail the digital seas, the maritime industry faces unprecedented cyber risks. This presentation, delivered by Mike Mingos during the launch ceremony of Optima Cyber, brings clarity to the evolving threat landscape in shipping — and presents a simple, powerful message: cybersecurity is not optional, it’s strategic.
Optima Cyber is a joint venture between:
• Optima Shipping Services, led by shipowner Dimitris Koukas,
• The Crime Lab, founded by former cybercrime head Manolis Sfakianakis,
• Panagiotis Pierros, security consultant and expert,
• and Tictac Cyber Security, led by Mike Mingos, providing the technical backbone and operational execution.
The event was honored by the presence of Greece’s Minister of Development, Mr. Takis Theodorikakos, signaling the importance of cybersecurity in national maritime competitiveness.
🎯 Key topics covered in the talk:
• Why cyberattacks are now the #1 non-physical threat to maritime operations
• How ransomware and downtime are costing the shipping industry millions
• The 3 essential pillars of maritime protection: Backup, Monitoring (EDR), and Compliance
• The role of managed services in ensuring 24/7 vigilance and recovery
• A real-world promise: “With us, the worst that can happen… is a one-hour delay”
Using a storytelling style inspired by Steve Jobs, the presentation avoids technical jargon and instead focuses on risk, continuity, and the peace of mind every shipping company deserves.
🌊 Whether you’re a shipowner, CIO, fleet operator, or maritime stakeholder, this talk will leave you with:
• A clear understanding of the stakes
• A simple roadmap to protect your fleet
• And a partner who understands your business
📌 Visit:
https://optima-cyber.com
https://tictac.gr
https://mikemingos.gr
GDG Cloud Southlake #42: Suresh Mathew: Autonomous Resource Optimization: How...



GDG Cloud Southlake #42: Suresh Mathew: Autonomous Resource Optimization: How...James Anderson Autonomous Resource Optimization: How AI is Solving the Overprovisioning Problem
In this session, Suresh Mathew will explore how autonomous AI is revolutionizing cloud resource management for DevOps, SRE, and Platform Engineering teams.
Traditional cloud infrastructure typically suffers from significant overprovisioning—a "better safe than sorry" approach that leads to wasted resources and inflated costs. This presentation will demonstrate how AI-powered autonomous systems are eliminating this problem through continuous, real-time optimization.
Key topics include:
Why manual and rule-based optimization approaches fall short in dynamic cloud environments
How machine learning predicts workload patterns to right-size resources before they're needed
Real-world implementation strategies that don't compromise reliability or performance
Featured case study: Learn how Palo Alto Networks implemented autonomous resource optimization to save $3.5M in cloud costs while maintaining strict performance SLAs across their global security infrastructure.
Bio:
Suresh Mathew is the CEO and Founder of Sedai, an autonomous cloud management platform. Previously, as Sr. MTS Architect at PayPal, he built an AI/ML platform that autonomously resolved performance and availability issues—executing over 2 million remediations annually and becoming the only system trusted to operate independently during peak holiday traffic.
RTP Over QUIC: An Interesting Opportunity Or Wasted Time?



RTP Over QUIC: An Interesting Opportunity Or Wasted Time?Lorenzo Miniero Slides for my "RTP Over QUIC: An Interesting Opportunity Or Wasted Time?" presentation at the Kamailio World 2025 event.
They describe my efforts studying and prototyping QUIC and RTP Over QUIC (RoQ) in a new library called imquic, and some observations on what RoQ could be used for in the future, if anything.
Messing with binary formats
- 1. Messing with binary formats London, EnglandAnge Albertini 2013/09/13 ΠΟΛΎΓΛΩΣΣΟΣ
- 2. Welcome! ● this is the non-live version of my slides ○ more text ○ standard PDF file ;) About me: ● Reverse engineer ● my website: http://corkami.com ○ reverse engineering & visual documentations to extract the live deck. 61 slides: pdftk 44con-albertini.pdf cat 1 3 5 7 9 10 12 14 16 18 23 25 29 31 33 35 37 39 41 43 45 47 49 51 53 55-57 59 63 65 67 69 71 73 75 77 79 81 83 85 87 89 90 94 96 98 101-102 104 106-107 109-112 114-117 119 output 44con-albertini(live).pdf 119 2 4 6 8 11 13 15 17 19+4 24 26+3 32 34 36 38 40 42 44 46 48 50 52 54 58 60+3 64 66 68 70 72 74 76 78 80 82 84 86 88 91+3 95 97 99+2 103 105 108 113 118
- 3. low-level ones, that is I just like to play with lego blocks
- 4. generate files byte per byte Goals ● explore the format ● make sure that's how things work ● full control over the structure
- 5. result: ● a complete executable ● all bytes defined by hand
- 6. our problem ● is related to virus (malwares) ● they use many file formats ● it's critical to identify them reliably ○ and to tell whether corrupted or well-formed
- 7. standard infection chain the most common chain: 1. a web page, in HTML format a. launching an applet 2. an evil applet, in CLASS format a. exploiting a Java vulnerability b. dropping an executable 3. a malicious executable, in Portable Executable format (a vast majority of malwares rely on an executable)
- 8. another classic chain ● open a PDF document ○ with an exploit inside ■ dropping or downloading a PE executable ● get a malicious executable on your machine
- 9. the challenge it might look obvious: ● tell whether it's a PDF, a PE, a JAVA, an HTML... ● typical formats are clearly defined ○ Magic signature enforced at offset 0
- 10. reality some formats have no header at all ● Command File (DOS 16 bits) ● Master Boot record some formats don't need to start at offset 0 ● Archives (Zips, Rars...) ● HTML ○ but text-only? some formats accept a large controllable block early in their header ● Portable Executable ● PICT image
- 11. How did this start? a real-life problem: 1. a (malicious) HTML page 2. started with 'MZ' (the signature of PE) 3. just scanned as a PE! a. wow, this PE is highly corrupted :) b. it must be clean :p ? MZ
- 12. polyglots in the wild GIFAR = GIF + JAR ● an uploaded image ○ an avatar in a forum ● with a malicious JAVA appended as JAR hosted on the server! ● bypass same domain policy ● now useable via its JAVA=EVIL payload + =
- 13. let's get started PE, the executable format of windows ● it's central to windows malware ● it enforces a magic signature at offset 0 ○ game over for other formats?
- 14. ● starts with a compulsory header ● made of sub-headers overview
- 15. a historical sandwich 1. a deprecated but required header 2. a modern header
- 16. old header content ● almost completely ignored ● only required: ○ 2 byte signature ○ pointer to new header
- 17. the new header can be anywhere ex: at the end of the file! such as Corkami Standard Test
- 18. let's look at HTML format
- 19. it enforces NOTHING! anything before the <html> tag! even 28 Mb of binary!
- 20. and it's been the same since Mozilla 1.0 in 2002thanks to Nicolas Grégoire!
- 21. now, the PDF format
- 22. signature position? ● officially at offset 0 ● officially tolerated until offset 1024 ● wtf? ○ it get actually worse later
- 23. PDF trick 1 put a small executable within 1024 bytes (just concatenate)
- 24. trick 2 1. start a fake PDF + object in a PE header 2. finish fake object at the end the PE 3. end fake object 4. put PDF real structure works with real-life example! (PE data might contain PDF keywords)
- 25. JAR = ZIP + Class just enforced at the very end of the file
- 26. but CRCs are just ignored it was too easy :p
- 27. Summary
- 28. Structure 1. start ○ PE Signature ■ %PDF + fake obj start ■ HTML comment start 2. next ○ PE (next) ○ HTML ○ PDF (next) 3. bottom ○ ZIP
- 29. it’s time for a real example! an inception demo! wait, what?
- 30. we’re already in the demo! the live version file is simultaneously: ● the PDF slides themselves ● a PDF viewer executable ○ ie, the file is loading itself ● the PoCs in a ZIP ● an HTML readme ○ with JavaScript mario
- 31. so, it works but it lacks something ● not artistic enough ● not advanced enough let's build a 'well representative' (=nasty) PoC
- 32. the PE specs ● Official MS specs = big joke ○ 'the gentle guide for beginners' ○ barely describes standard PEs
- 33. stripped down PE many elements removed ● including no sections
- 34. imports (imports = communication between executables and libraries) imports are made of 3 lists
- 35. evil imports ● let's make these lists into each other ● with more extra tricks to fail parser!
- 36. ultimate import fail ● failing all tools ○ including IDA & Hiew ● now fixed :)
- 37. let's put some code ● some undocumented opcodes! ● big blank spaces in Intel official docs
- 38. let's check AMD's ● miracle!
- 39. result in WinDbg ● '???' == clueless (tool/user) don't rely (only) on official docs
- 40. messing with PDF
- 41. there is a so-called standard and the reality of existing parsers looking at: Adobe, MuPDF, Chrome ● 3 different files ○ working each on a specific viewer ○ failing on the other 2
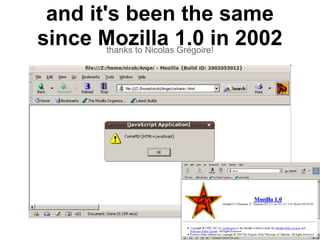
- 43. let's look inside ● MuPDF ○ no %PDF sig required ■ a PDF without a PDF sig ? WTF ?!?! ○ no trailer keyword required either ● Chrome ○ integer overflows: -4294967275 = 21 ○ trailer in a comment ■ it can actually be almost ANYWHERE ■ even inside another object ● Adobe ○ looks almost sane compare to the other 2
- 45. Chrome insanity++ (thx to Jonas Magazinius) ● a single object ● no 'trailer' ● inline stream ● brackets are not even closed ● * are required - it just checks for minimum space
- 46. %PDF***** 1 0 obj << /Size 2 /W[[]1/] /Root 1 0 R /Pages<< /Kids[<< /Contents<<>> stream BT{99 Tf{Td(Inlined PDF)' endstream >>] >> >> stream * endstream startxref%*******
- 47. PDF.JS ● very strict ○ 'too' strict / naive ? ○ I don't want to be their QA ;) ● requires a lot of information usually ignored ○ xref ○ /Length %PDF-1.1 1 0 obj << % /Type /Catalog ... >> endobj 2 0 obj << /Type /Pages ... >> endobj 3 0 obj << /Type /Page /Resources << /Font << /F1 << /Type /Font /Subtype /Type1 ... >> >> >> >> endobj 4 0 obj << /Length 47>> stream ... xref 0 1 0000000000 65535 f 0000000010 00000 n ...
- 48. let's play further combine 3 documents in a single file ● it's actually 3 set of 'independant' objects ● objects are parsed ○ but not used
- 49. alternate reality demo the live slide-deck contains 2 PDF ● bogus one under Chrome ● real one under MuPDF (Sumatra, Linux...) ● rejected under Acrobat ○ because of the PE signature (see later) DEMO
- 50. final PoC ● combine most previously mentioned tricks ● many fails on many tools ● total control of the structure ○ the PDF 'ends' in the Java class
- 51. Adobe rejects 'weird magics' after 10.1.5 not in their own specs :p 10.1.4 10.1.5
- 52. also in ELF/Linux flavor ● starring a signature-less PDF ○ which won't run on other viewers
- 54. and Apple too PS: I don't have a Mac, this was built blindly Thanks to Nicolas Seriot for testing
- 55. why should we care?
- 56. like washing powders security tools are selected: ● speed ● {files} → {[clean/detected]} file types not taken into consideration
- 57. type confusion make the tool believe it's another type, which will fool the engine engine with checksum caching will be fooled: 1. scanned as HTML, clean 2. reused as PE but malicious
- 59. engine exhaustion rankings in magazines are based on scanning time → scanning per file must stop arbitrarily → waste scanning cycle by adding extra formats
- 60. Weaknesses ● evasion ○ filters → exfiltration ○ same origin policy ○ detection ■ ex: clean PE but malicious PDF/HTML/... ■ exhaust checks ■ pretend to be corrupt ● DoS
- 61. Conclusion
- 62. Conclusion ● type confusion is bad ○ succinct docs too ○ lazy softwares as well ● go beyond the specs ○ Adobe: good ● suggestions ○ more extensions checks ○ isolate downloaded files ○ enforce magic signature at offset 0
- 63. Questions ? thank YOU !
- 65. Bonus
- 66. Valid image as JavaScript Highlighted by Saumil Shah ● abusing header and parsers laxisms ● turn a field into /* ● close comment after the picture data




