Ad
Military Edge Computing with Vault and Consul
- 1. Copyright © 2019 HashiCorp Securing The Edge: Military Computing Systems Timothy J. Olson - SE, Public Sector
- 2. Secrets Management for Tactical Systems Providing secure edge computing to warfighters Provide secrets management to tactical units for battlefield management and secure communication workflows ▪ Operable in Isolation Operational in the face of long-term losses of connectivity with infrastructure ▪ Resilient Secure against possible physical compromise ▪ Easy to Use Requires little/no development support from warfighter users
- 3. Solution: Vault + Consul Leverage Vault and Consul to provide highly available, resilient, and secure access to tactical computing systems at the edge ▪ Centrally manage and distribute K/V secrets to warfighters using Vault Agent Caching and Templating ▪ Replicate secrets and perform distributed consensus via Vault Replication ▪ Leverage Consul to perform service discovery and networking of Vault across tactical IP networks
- 4. Evolving application workload delivery Challenge How to deliver Enterprise to Edge applications securely and consistently? Solution Embracing a new operating model for dynamic cloud architectures: a cloud operating model. PHYSICAL VMs CONTAINERS SERVICES APP SERVER CLOUD NATIVE SERVERLESS EDGE DEVICES Run Development Connect Networking Secure Security Provision Operations Dedicated Infrastructure Scheduled across the fleet Host-based Static IP Service-based Dynamic IP High trust IP-based Low trust Identity-based Dedicated servers Homogeneous Capacity on-demand Heterogeneous STATIC/FIXED DYNAMIC
- 5. Evolving application workload delivery vSphere Hardware IP: Hardware vCenter vSphere Various Hardware Identity: AD/LDAP Terraform EKS / ECS Lambda CloudApp/ AppMesh Identity: AWS IAM Cloud Formation AKS / ACS Azure Functions Proprietary Identity: Azure AD Resource Manager GKE Cloud Functions Proprietary Identity: GCP IAM Cloud Dep. Manager Challenge How to deliver Enterprise to Edge applications securely and consistently? PHYSICAL VMs CONTAINERS SERVICES APP SERVER CLOUD NATIVE SERVERLESS EDGE DEVICES Solution Proprietary solutions reduce flexibility and creates complexity across vendors Run Development Connect Networking Secure Security Provision Operations DEDICATED HYBRID/MULTI CLOUD EDGEENTERPRISE
- 6. Evolving application workload delivery Networking Security Infrastructure Orchestration Challenge How to deliver Enterprise to Edge applications securely and consistently? Solution Establish central shared service platforms with a single control plane, and consistent workflows. PHYSICAL VMs CONTAINERS SERVICES APP SERVER CLOUD NATIVE SERVERLESS EDGE DEVICES EDGEENTERPRISE
- 7. A Common Operating Model with the HashiCorp Suite Provision Operations Secure Security Connect Networking Run Development Private Cloud AWS Azure GCP
- 8. Cloud Operating Model Shared Services Multi Cloud Infrastructure Automation — Infrastructure as code Compliance & management Self service infrastructure Provision / Operations Multi Cloud Security Automation — Identity-based security Secrets management Encryption as a service Advanced data protection Secure / Security Multi Cloud Networking Automation — Common service registry Service registry and discovery Network middleware automation Service mesh Connect / Networking Multi Cloud Application Automation — Workload orchestration Container orchestration Heterogeneous orchestration Run / Development
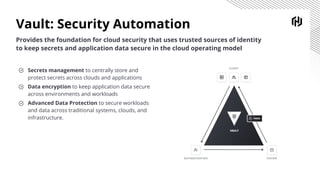
- 9. Vault: Security Automation Provides the foundation for cloud security that uses trusted sources of identity to keep secrets and application data secure in the cloud operating model Secrets management to centrally store and protect secrets across clouds and applications Data encryption to keep application data secure across environments and workloads Advanced Data Protection to secure workloads and data across traditional systems, clouds, and infrastructure.
- 10. Vault: Hybrid / Multi-Cloud Security Secure Multi Cloud Security ● Hybrid / Multi Cloud Secrets Management ○ Enables teams to securely store and tightly control access to tokens, passwords, certificates, and encryption keys for protecting machines and application ● EaaS: Encryption as a Service
- 11. Single Control Plane for cloud security ● Automate, control, and secure infrastructure and applications through one API ● Unified support across heterogeneous environments ● Integrate with providers and technologies you’re already using
- 12. © 2018 HashiCorp Vault Agent VAULT APPROACH TO DYNAMIC INFRASTRUCTURE 12 Vault Agent is a client daemon that provides the following features: ● Auto-Auth - Automatically authenticate to Vault and manage the token renewal process for locally-retrieved dynamic secrets. ● Caching - Allows client-side caching of responses containing newly created tokens and responses containing leased secrets generated off of these newly created tokens. ● Templating - Allows rendering of user supplied templates by Vault Agent, using the token generated by the Auto-Auth step.
- 13. © 2018 HashiCorp Vault Agent Caching VAULT APPROACH TO DYNAMIC INFRASTRUCTURE 13 Vault Agent Caching can cache the tokens and leased secrets proxied through the agent which includes the auto-auth token. This allows for easier access to Vault secrets for edge applications, reduces the I/O burden for basic secrets access for Vault clusters, and allows for secure local access to leased secrets for the life of a valid token
- 14. © 2018 HashiCorp Vault Agent Templates VAULT APPROACH TO DYNAMIC INFRASTRUCTURE 14 Vault Agent Templates allows Vault secrets to be rendered to files using the Consul Template markup language. This significantly simplifies the workflow when you are integrating your applications with Vault.
- 15. Consul Provides a foundation of cloud network automation using a shared registry for service based networking 50k+ Used at scale with 50k+ agents 1M+ Monthly D/Ls Service registry & health monitoring to provide a real-time directory of all services with their health status Network middleware automation with service discovery for dynamic reconfiguration as services scale up, down or move Zero trust network with service mesh to secure service-to-service traffic with identity-based security policies and encrypted traffic with Mutual-TLS
- 16. The Shift from Static to Dynamic Networking ● Modular services with dynamic IPs, running on bare metals, VMs, containers... ● 85% of volume from complex east-west traffic* ● No clear network perimeters
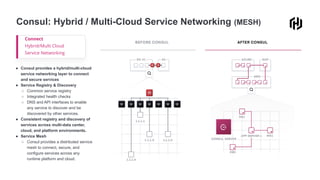
- 17. Consul: Hybrid / Multi-Cloud Service Networking (MESH) Connect Hybrid/Multi Cloud Service Networking ● Consul provides a hybrid/multi-cloud service networking layer to connect and secure services ● Service Registry & Discovery ○ Common service registry ○ Integrated health checks ○ DNS and API interfaces to enable any service to discover and be discovered by other services. ● Consistent registry and discovery of services across multi-data center, cloud, and platform environments. ● Service Mesh ○ Consul provides a distributed service mesh to connect, secure, and configure services across any runtime platform and cloud.
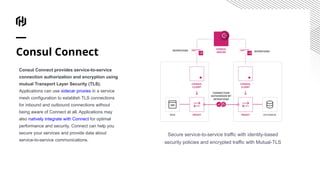
- 18. Consul Connect Consul Connect provides service-to-service connection authorization and encryption using mutual Transport Layer Security (TLS). Applications can use sidecar proxies in a service mesh configuration to establish TLS connections for inbound and outbound connections without being aware of Connect at all. Applications may also natively integrate with Connect for optimal performance and security. Connect can help you secure your services and provide data about service-to-service communications. Secure service-to-service traffic with identity-based security policies and encrypted traffic with Mutual-TLS
- 19. Single Control Plane for cloud networking ● Automate and control the data plane with central service registry ● Unified support across heterogeneous environment ● Simplified operation with single workflow
- 20. Unified Networking Solution for Hybrid/Multi-Cloud
- 21. Vault Replication for Military Systems Leverage Vault Replication to allow edge-based warfighting systems to perform secrets management with centralized Vault environments. ▪ Primary: Source of truth located in central ship or land-based command operations center. ▪ Secondaries: Located at mobile C2I centers that can connect directly to edge systems. ▪ Vault Agent: Deployed on edge warfighting systems for local secrets management operations using K/V. Primary Vault Cluster Land or naval command operations centers Vault Performance Secondary Mobile C2I such as E3 or M1113 Vault Agent Edge system that uses Vault K/V
- 22. Mesh Networking with Consul Connect Using Consul Connect will allow Vault Agents to route communications to Vault clusters via the Airborne Network ▪ Allows Vault Agent to sync ad hoc with Vault performance secondaries via TTNT, WNW to Airborne Network routers when available ▪ Minimize round trip delay and provide additional options for Vault replication reference architectures TTNT = Tactical Targeting Network Technology WNW = Wideband Network Waveform
- 23. Secrets Management in Adverse Conditions When in periods of reliable/semi-reliable connectivity, use Consul + Vault Agent Caching and Templating to reflect the active state of secrets in the primary within files local to the edge system. Vault Agent (/foo/bar, value_1) Secondary Cluster (/foo/bar, value_1) Primary Cluster (/foo/bar, value_1) Reliable/Semi-Reliable Connectivity
- 24. Secrets Management in Adverse Conditions When outside the range of connectivity, Vault Agent Caching & Templating retains the last known version of K/V in the linked file that references the secret. This ensures continued access for local applications at the edge while the secondary cluster remains disconnected in the field. Secondary Cluster (/foo/bar, value_1) Primary Cluster (/foo/bar, value_1) Reliable/Semi-Reliable Connectivity Vault Agent (/foo/bar, value_1) ?
- 25. Secrets Management in Adverse Conditions When TTL expires and/or operator thinks edge compromised, primary iterates K/V version with new value ▪ Agent is unable to retrieve an update to their K/V pair until they re-enter connectivity with a connected secondary and reauthenticate. ▪ Resilience against compromise of edge system. Compromises isolated at the edge. ▪ Ensures primary/connected secondaries can still reference previous K/V pair via previous versions. Connected Secondary V1: (/foo/bar, value_2), V0: (/foo/bar, value_1) Primary Cluster V1: (/foo/bar, value_2), V0: (/foo/bar, value_1) Reliable/Semi-Reliable Connectivity Disconnected Secondary (/foo/bar, value_1) Vault Agent (/foo/bar, value_1)
- 26. Secrets Management in Adverse Conditions When reliable/semi-reliable connectivity re-established, use Vault Agent Templating and Vault Replication to reflect the active state of secrets in the primary within files local to the edge system. Reliable/Semi-Reliable Connectivity Connected Secondary V1: (/foo/bar, value_2) V0: (/foo/bar, value_1) Primary Cluster V1: (/foo/bar, value_2) V0: (/foo/bar, value_1) Vault Agent V1: (/foo/bar, value_2) V0: (/foo/bar, value_1)
- 27. Secrets Management for Tactical Systems Vault and Consul: Providing secure edge computing to warfighters Provide secrets management to tactical units for battlefield management and secure communication workflows ▪ Operable in Isolation Operational in the face of long-term losses of connectivity with infrastructure ▪ Resilient Secure against possible physical compromise ▪ Easy to Use Requires little/no development support from warfighter users
- 28. Secrets Management for Tactical Systems Providing secure edge computing to warfighters Provide secrets management to tactical units for battlefield management and secure communication workflows Solution: Vault + Consul























































![[OpenStack Days Korea 2016] Track2 - 가상화 네트워크와 클라우드간 협업](https://cdn.slidesharecdn.com/ss_thumbnails/23vmware-160226172243-thumbnail.jpg?width=560&fit=bounds)








































![Download Wondershare Filmora Crack [2025] With Latest](https://cdn.slidesharecdn.com/ss_thumbnails/neo4j-howkgsareshapingthefutureofgenerativeaiatawssummitlondonapril2024-240426125209-2d9db05d-250419-250428115407-a04afffa-thumbnail.jpg?width=560&fit=bounds)








![Get & Download Wondershare Filmora Crack Latest [2025]](https://cdn.slidesharecdn.com/ss_thumbnails/revolutionizingresidentialwi-fi-250422112639-60fb726f-250429170801-59e1b240-thumbnail.jpg?width=560&fit=bounds)







