Mining Data Streams
Download as PPTX, PDF2 likes2,509 views
This document discusses concepts related to data streams and real-time analytics. It begins with introductions to stream data models and sampling techniques. It then covers filtering, counting, and windowing queries on data streams. The document discusses challenges of stream processing like bounded memory and proposes solutions like sampling and sketching. It provides examples of applications in various domains and tools for real-time data streaming and analytics.
1 of 34
Downloaded 18 times













![ Consider: |S| = m, |B| = n
Use k independent hash functions h1 ,…, hk
Initialization:
◦ Set B to all 0s
◦ Hash each element s S using each hash function hi, set
B[hi(s)] = 1 (for each i = 1,.., k)
Run-time:
◦ When a stream element with key x arrives
If B[hi(x)] = 1 for all i = 1,..., k then declare that x is in S
That is, x hashes to a bucket set to 1 for every hash
function hi(x)
Otherwise discard the element x](https://image.slidesharecdn.com/slideshare-miningdatastreams-200218115339/85/Mining-Data-Streams-15-320.jpg)







![ Datar-Gionis-Indyk-Motwani Algorithm
A bucket in the DGIM method is a record consisting
of:
1. The timestamp of its end [O(log N) bits]
2. The number of 1s between its beginning and end [O(log log
N) bits]
Constraint on buckets:
Number of 1s must be a power of 2
◦ That explains the O(log log N) in (2)](https://image.slidesharecdn.com/slideshare-miningdatastreams-200218115339/85/Mining-Data-Streams-23-320.jpg)











Ad
Recommended
Apache Spark - Basics of RDD | Big Data Hadoop Spark Tutorial | CloudxLab



Apache Spark - Basics of RDD | Big Data Hadoop Spark Tutorial | CloudxLabCloudxLab Big Data with Hadoop & Spark Training: http://bit.ly/2L4rPmM
This CloudxLab Basics of RDD tutorial helps you to understand Basics of RDD in detail. Below are the topics covered in this tutorial:
1) What is RDD - Resilient Distributed Datasets
2) Creating RDD in Scala
3) RDD Operations - Transformations & Actions
4) RDD Transformations - map() & filter()
5) RDD Actions - take() & saveAsTextFile()
6) Lazy Evaluation & Instant Evaluation
7) Lineage Graph
8) flatMap and Union
9) Scala Transformations - Union
10) Scala Actions - saveAsTextFile(), collect(), take() and count()
11) More Actions - reduce()
12) Can We Use reduce() for Computing Average?
13) Solving Problems with Spark
14) Compute Average and Standard Deviation with Spark
15) Pick Random Samples From a Dataset using Spark
What Is Apache Spark? | Introduction To Apache Spark | Apache Spark Tutorial ...



What Is Apache Spark? | Introduction To Apache Spark | Apache Spark Tutorial ...Simplilearn This presentation about Apache Spark covers all the basics that a beginner needs to know to get started with Spark. It covers the history of Apache Spark, what is Spark, the difference between Hadoop and Spark. You will learn the different components in Spark, and how Spark works with the help of architecture. You will understand the different cluster managers on which Spark can run. Finally, you will see the various applications of Spark and a use case on Conviva. Now, let's get started with what is Apache Spark.
Below topics are explained in this Spark presentation:
1. History of Spark
2. What is Spark
3. Hadoop vs Spark
4. Components of Apache Spark
5. Spark architecture
6. Applications of Spark
7. Spark usecase
What is this Big Data Hadoop training course about?
The Big Data Hadoop and Spark developer course have been designed to impart an in-depth knowledge of Big Data processing using Hadoop and Spark. The course is packed with real-life projects and case studies to be executed in the CloudLab.
What are the course objectives?
Simplilearn’s Apache Spark and Scala certification training are designed to:
1. Advance your expertise in the Big Data Hadoop Ecosystem
2. Help you master essential Apache and Spark skills, such as Spark Streaming, Spark SQL, machine learning programming, GraphX programming and Shell Scripting Spark
3. Help you land a Hadoop developer job requiring Apache Spark expertise by giving you a real-life industry project coupled with 30 demos
What skills will you learn?
By completing this Apache Spark and Scala course you will be able to:
1. Understand the limitations of MapReduce and the role of Spark in overcoming these limitations
2. Understand the fundamentals of the Scala programming language and its features
3. Explain and master the process of installing Spark as a standalone cluster
4. Develop expertise in using Resilient Distributed Datasets (RDD) for creating applications in Spark
5. Master Structured Query Language (SQL) using SparkSQL
6. Gain a thorough understanding of Spark streaming features
7. Master and describe the features of Spark ML programming and GraphX programming
Who should take this Scala course?
1. Professionals aspiring for a career in the field of real-time big data analytics
2. Analytics professionals
3. Research professionals
4. IT developers and testers
5. Data scientists
6. BI and reporting professionals
7. Students who wish to gain a thorough understanding of Apache Spark
Learn more at https://www.simplilearn.com/big-data-and-analytics/apache-spark-scala-certification-training
Introduction to Pig



Introduction to PigPrashanth Babu This document provides an introduction to the Pig analytics platform for Hadoop. It begins with an overview of big data and Hadoop, then discusses the basics of Pig including its data model, language called Pig Latin, and components. Key points made are that Pig provides a high-level language for expressing data analysis processes, compiles queries into MapReduce programs for execution, and allows for easier programming than lower-level systems like Java MapReduce. The document also compares Pig to SQL and Hive, and demonstrates visualizing Pig jobs with the Twitter Ambrose tool.
5.1 mining data streams



5.1 mining data streamsKrish_ver2 This document discusses techniques for mining data streams. It begins by defining different types of streaming data like time-series data and sequence data. It then discusses the characteristics of data streams like their huge volume, fast changing nature, and requirement for real-time processing. The key challenges in stream query processing are the unbounded memory requirements and need for approximate query answering. The document outlines several synopsis data structures and techniques used for mining data streams, including random sampling, histograms, sketches, and randomized algorithms. It also discusses architectures for stream query processing and classification of dynamic data streams.
Data Streaming For Big Data



Data Streaming For Big DataSeval Çapraz Streaming data involves the continuous analysis of data as it is generated in real-time. It allows for data to be processed and transformed in memory before being stored. Popular streaming technologies include Apache Storm, Apache Flink, and Apache Spark Streaming, which allow for processing streams of data across clusters. Each technology has its own approach such as micro-batching but all aim to enable real-time analysis of high-velocity data streams.
Text MIning



Text MIningPrakhyath Rai This document presents an overview of text mining. It discusses how text mining differs from data mining in that it involves natural language processing of unstructured or semi-structured text data rather than structured numeric data. The key steps of text mining include pre-processing text, applying techniques like summarization, classification, clustering and information extraction, and analyzing the results. Some common applications of text mining are market trend analysis and filtering of spam emails. While text mining allows extraction of information from diverse sources, it requires initial learning systems and suitable programs for knowledge discovery.
K-Means manual work



K-Means manual workDr.E.N.Sathishkumar The k-means clustering algorithm takes as input the number of clusters k and a set of data points, and assigns each data point to one of k clusters. It works by first randomly selecting k data points as initial cluster centroids. It then assigns each remaining point to the closest centroid, and recalculates the centroid positions. This process repeats until the centroids are stable or a stopping criteria is reached. As an example, the document applies k-means to cluster 6 data points into 2 groups, showing the random selection of initial centroids, assignment of points, and recalculation of centroids over multiple steps.
Lecture6 introduction to data streams



Lecture6 introduction to data streamshktripathy There are three main points about data streams and stream processing:
1) A data stream is a continuous, ordered sequence of data items that arrives too rapidly to be stored fully. Common sources include sensors, web traffic, and social media.
2) Data stream management systems process continuous queries over streams in real-time using bounded memory. They provide summaries of historical data rather than storing entire streams.
3) Challenges of stream processing include limited memory, complex continuous queries, and unpredictable data rates and characteristics. Approximate query processing techniques like windows, sampling, and load shedding help address these challenges.
Hadoop Map Reduce



Hadoop Map ReduceVNIT-ACM Student Chapter Hadoop MapReduce is an open source framework for distributed processing of large datasets across clusters of computers. It allows parallel processing of large datasets by dividing the work across nodes. The framework handles scheduling, fault tolerance, and distribution of work. MapReduce consists of two main phases - the map phase where the data is processed key-value pairs and the reduce phase where the outputs of the map phase are aggregated together. It provides an easy programming model for developers to write distributed applications for large scale processing of structured and unstructured data.
Map Reduce



Map ReducePrashant Gupta A MapReduce job usually splits the input data-set into independent chunks which are processed by the map tasks in a completely parallel manner. The framework sorts the outputs of the maps, which are then input to the reduce tasks. Typically both the input and the output of the job are stored in a file-system.
Hadoop File system (HDFS)



Hadoop File system (HDFS)Prashant Gupta HDFS is a Java-based file system that provides scalable and reliable data storage, and it was designed to span large clusters of commodity servers. HDFS has demonstrated production scalability of up to 200 PB of storage and a single cluster of 4500 servers, supporting close to a billion files and blocks.
01 Data Mining: Concepts and Techniques, 2nd ed.



01 Data Mining: Concepts and Techniques, 2nd ed.Institute of Technology Telkom The document provides an overview of data mining concepts and techniques. It introduces data mining, describing it as the process of discovering interesting patterns or knowledge from large amounts of data. It discusses why data mining is necessary due to the explosive growth of data and how it relates to other fields like machine learning, statistics, and database technology. Additionally, it covers different types of data that can be mined, functionalities of data mining like classification and prediction, and classifications of data mining systems.
Hadoop YARN



Hadoop YARNVigen Sahakyan This document provides an overview of YARN (Yet Another Resource Negotiator), the resource management system for Hadoop. It describes the key components of YARN including the Resource Manager, Node Manager, and Application Master. The Resource Manager tracks cluster resources and schedules applications, while Node Managers monitor nodes and containers. Application Masters communicate with the Resource Manager to manage applications. YARN allows Hadoop to run multiple applications like Spark and HBase, improves on MapReduce scheduling, and transforms Hadoop into a distributed operating system for big data processing.
Big Data Analytics with Hadoop



Big Data Analytics with HadoopPhilippe Julio Hadoop, flexible and available architecture for large scale computation and data processing on a network of commodity hardware.
Data Streaming in Big Data Analysis



Data Streaming in Big Data AnalysisVincenzo Gulisano Slides for my Associate Professor (oavlönad docent) lecture.
The lecture is about Data Streaming (its evolution and basic concepts) and also contains an overview of my research.
Analysing of big data using map reduce



Analysing of big data using map reducePaladion Networks This document discusses efficient analysis of big data using the MapReduce framework. It introduces the challenges of analyzing large and complex datasets, and describes how MapReduce addresses these challenges through its map and reduce functions. MapReduce allows distributed processing of big data across clusters of computers using a simple programming model.
Introduction to Apache Spark



Introduction to Apache SparkRahul Jain Apache Spark is a In Memory Data Processing Solution that can work with existing data source like HDFS and can make use of your existing computation infrastructure like YARN/Mesos etc. This talk will cover a basic introduction of Apache Spark with its various components like MLib, Shark, GrpahX and with few examples.
18 Data Streams



18 Data StreamsPier Luca Lanzi Course "Machine Learning and Data Mining" for the degree of Computer Engineering at the Politecnico di Milano. In in this lecture we overview the mining of data streams
introduction to NOSQL Database



introduction to NOSQL Databasenehabsairam This document provides an introduction to NoSQL databases. It discusses the history and limitations of relational databases that led to the development of NoSQL databases. The key motivations for NoSQL databases are that they can handle big data, provide better scalability and flexibility than relational databases. The document describes some core NoSQL concepts like the CAP theorem and different types of NoSQL databases like key-value, columnar, document and graph databases. It also outlines some remaining research challenges in the area of NoSQL databases.
Introduction to Map Reduce



Introduction to Map ReduceApache Apex Here is how you can solve this problem using MapReduce and Unix commands:
Map step:
grep -o 'Blue\|Green' input.txt | wc -l > output
This uses grep to search the input file for the strings "Blue" or "Green" and print only the matches. The matches are piped to wc which counts the lines (matches).
Reduce step:
cat output
This isn't really needed as there is only one mapper. Cat prints the contents of the output file which has the count of Blue and Green.
So MapReduce has been simulated using grep for the map and cat for the reduce functionality. The key aspects are - grep extracts the relevant data (map
Hadoop Architecture



Hadoop ArchitectureDr. C.V. Suresh Babu This presentation discusses the following topics:
Introduction
Components of Hadoop
MapReduce
Map Task
Reduce Task
Anatomy of a Map Reduce
03 data mining : data warehouse



03 data mining : data warehouseInstitute of Technology Telkom Jiawei Han and Micheline Kamber
Data Mining: Concepts and Techniques, 2nd ed.
Chapter 03 : Data warehouse
Apache HBase™



Apache HBase™Prashant Gupta The document provides an introduction to NoSQL and HBase. It discusses what NoSQL is, the different types of NoSQL databases, and compares NoSQL to SQL databases. It then focuses on HBase, describing its architecture and components like HMaster, regionservers, Zookeeper. It explains how HBase stores and retrieves data, the write process involving memstores and compaction. It also covers HBase shell commands for creating, inserting, querying and deleting data.
Hadoop



HadoopNishant Gandhi Hadoop is an open-source framework for distributed storage and processing of large datasets across clusters of commodity hardware. It was created to support applications handling large datasets operating on many servers. Key Hadoop technologies include MapReduce for distributed computing, and HDFS for distributed file storage inspired by Google File System. Other related Apache projects extend Hadoop capabilities, like Pig for data flows, Hive for data warehousing, and HBase for NoSQL-like big data. Hadoop provides an effective solution for companies dealing with petabytes of data through distributed and parallel processing.
Big Data Architecture



Big Data ArchitectureGuido Schmutz This document discusses different architectures for big data systems, including traditional, streaming, lambda, kappa, and unified architectures. The traditional architecture focuses on batch processing stored data using Hadoop. Streaming architectures enable low-latency analysis of real-time data streams. Lambda architecture combines batch and streaming for flexibility. Kappa architecture avoids duplicating processing logic. Finally, a unified architecture trains models on batch data and applies them to real-time streams. Choosing the right architecture depends on use cases and available components.
Map reduce in BIG DATA



Map reduce in BIG DATAGauravBiswas9 MapReduce is a programming framework that allows for distributed and parallel processing of large datasets. It consists of a map step that processes key-value pairs in parallel, and a reduce step that aggregates the outputs of the map step. As an example, a word counting problem is presented where words are counted by mapping each word to a key-value pair of the word and 1, and then reducing by summing the counts of each unique word. MapReduce jobs are executed on a cluster in a reliable way using YARN to schedule tasks across nodes, restarting failed tasks when needed.
Hadoop Overview & Architecture 



Hadoop Overview & Architecture EMC This document provides an overview of Hadoop architecture. It discusses how Hadoop uses MapReduce and HDFS to process and store large datasets reliably across commodity hardware. MapReduce allows distributed processing of data through mapping and reducing functions. HDFS provides a distributed file system that stores data reliably in blocks across nodes. The document outlines components like the NameNode, DataNodes and how Hadoop handles failures transparently at scale.
Introduction to Data streaming - 05/12/2014



Introduction to Data streaming - 05/12/2014Raja Chiky Raja Chiky is an associate professor whose research interests include data stream mining, distributed architectures, and recommender systems. The document outlines data streaming concepts including what a data stream is, data stream management systems, and basic approximate algorithms used for processing massive, high-velocity data streams. It also discusses challenges in distributed systems and using semantic technologies for data streaming.
Mining data streams



Mining data streamsAkash Gupta This document discusses mining data streams. It describes how stream management is important when input is controlled externally, unlike in a DBMS where input is controlled by programming staff. It explains the stream model where tuples enter rapidly and the system cannot store the entire stream. Critical calculations must be made about the stream using limited memory. There are two forms of queries: ad-hoc queries asked once and standing queries asked continuously. The document also discusses sliding windows as a model where queries are about the most recent N elements received, where N is too large to store in memory. It provides examples of applications of the stream model like mining query streams and click streams.
Ad
More Related Content
What's hot (20)
Hadoop Map Reduce



Hadoop Map ReduceVNIT-ACM Student Chapter Hadoop MapReduce is an open source framework for distributed processing of large datasets across clusters of computers. It allows parallel processing of large datasets by dividing the work across nodes. The framework handles scheduling, fault tolerance, and distribution of work. MapReduce consists of two main phases - the map phase where the data is processed key-value pairs and the reduce phase where the outputs of the map phase are aggregated together. It provides an easy programming model for developers to write distributed applications for large scale processing of structured and unstructured data.
Map Reduce



Map ReducePrashant Gupta A MapReduce job usually splits the input data-set into independent chunks which are processed by the map tasks in a completely parallel manner. The framework sorts the outputs of the maps, which are then input to the reduce tasks. Typically both the input and the output of the job are stored in a file-system.
Hadoop File system (HDFS)



Hadoop File system (HDFS)Prashant Gupta HDFS is a Java-based file system that provides scalable and reliable data storage, and it was designed to span large clusters of commodity servers. HDFS has demonstrated production scalability of up to 200 PB of storage and a single cluster of 4500 servers, supporting close to a billion files and blocks.
01 Data Mining: Concepts and Techniques, 2nd ed.



01 Data Mining: Concepts and Techniques, 2nd ed.Institute of Technology Telkom The document provides an overview of data mining concepts and techniques. It introduces data mining, describing it as the process of discovering interesting patterns or knowledge from large amounts of data. It discusses why data mining is necessary due to the explosive growth of data and how it relates to other fields like machine learning, statistics, and database technology. Additionally, it covers different types of data that can be mined, functionalities of data mining like classification and prediction, and classifications of data mining systems.
Hadoop YARN



Hadoop YARNVigen Sahakyan This document provides an overview of YARN (Yet Another Resource Negotiator), the resource management system for Hadoop. It describes the key components of YARN including the Resource Manager, Node Manager, and Application Master. The Resource Manager tracks cluster resources and schedules applications, while Node Managers monitor nodes and containers. Application Masters communicate with the Resource Manager to manage applications. YARN allows Hadoop to run multiple applications like Spark and HBase, improves on MapReduce scheduling, and transforms Hadoop into a distributed operating system for big data processing.
Big Data Analytics with Hadoop



Big Data Analytics with HadoopPhilippe Julio Hadoop, flexible and available architecture for large scale computation and data processing on a network of commodity hardware.
Data Streaming in Big Data Analysis



Data Streaming in Big Data AnalysisVincenzo Gulisano Slides for my Associate Professor (oavlönad docent) lecture.
The lecture is about Data Streaming (its evolution and basic concepts) and also contains an overview of my research.
Analysing of big data using map reduce



Analysing of big data using map reducePaladion Networks This document discusses efficient analysis of big data using the MapReduce framework. It introduces the challenges of analyzing large and complex datasets, and describes how MapReduce addresses these challenges through its map and reduce functions. MapReduce allows distributed processing of big data across clusters of computers using a simple programming model.
Introduction to Apache Spark



Introduction to Apache SparkRahul Jain Apache Spark is a In Memory Data Processing Solution that can work with existing data source like HDFS and can make use of your existing computation infrastructure like YARN/Mesos etc. This talk will cover a basic introduction of Apache Spark with its various components like MLib, Shark, GrpahX and with few examples.
18 Data Streams



18 Data StreamsPier Luca Lanzi Course "Machine Learning and Data Mining" for the degree of Computer Engineering at the Politecnico di Milano. In in this lecture we overview the mining of data streams
introduction to NOSQL Database



introduction to NOSQL Databasenehabsairam This document provides an introduction to NoSQL databases. It discusses the history and limitations of relational databases that led to the development of NoSQL databases. The key motivations for NoSQL databases are that they can handle big data, provide better scalability and flexibility than relational databases. The document describes some core NoSQL concepts like the CAP theorem and different types of NoSQL databases like key-value, columnar, document and graph databases. It also outlines some remaining research challenges in the area of NoSQL databases.
Introduction to Map Reduce



Introduction to Map ReduceApache Apex Here is how you can solve this problem using MapReduce and Unix commands:
Map step:
grep -o 'Blue\|Green' input.txt | wc -l > output
This uses grep to search the input file for the strings "Blue" or "Green" and print only the matches. The matches are piped to wc which counts the lines (matches).
Reduce step:
cat output
This isn't really needed as there is only one mapper. Cat prints the contents of the output file which has the count of Blue and Green.
So MapReduce has been simulated using grep for the map and cat for the reduce functionality. The key aspects are - grep extracts the relevant data (map
Hadoop Architecture



Hadoop ArchitectureDr. C.V. Suresh Babu This presentation discusses the following topics:
Introduction
Components of Hadoop
MapReduce
Map Task
Reduce Task
Anatomy of a Map Reduce
03 data mining : data warehouse



03 data mining : data warehouseInstitute of Technology Telkom Jiawei Han and Micheline Kamber
Data Mining: Concepts and Techniques, 2nd ed.
Chapter 03 : Data warehouse
Apache HBase™



Apache HBase™Prashant Gupta The document provides an introduction to NoSQL and HBase. It discusses what NoSQL is, the different types of NoSQL databases, and compares NoSQL to SQL databases. It then focuses on HBase, describing its architecture and components like HMaster, regionservers, Zookeeper. It explains how HBase stores and retrieves data, the write process involving memstores and compaction. It also covers HBase shell commands for creating, inserting, querying and deleting data.
Hadoop



HadoopNishant Gandhi Hadoop is an open-source framework for distributed storage and processing of large datasets across clusters of commodity hardware. It was created to support applications handling large datasets operating on many servers. Key Hadoop technologies include MapReduce for distributed computing, and HDFS for distributed file storage inspired by Google File System. Other related Apache projects extend Hadoop capabilities, like Pig for data flows, Hive for data warehousing, and HBase for NoSQL-like big data. Hadoop provides an effective solution for companies dealing with petabytes of data through distributed and parallel processing.
Big Data Architecture



Big Data ArchitectureGuido Schmutz This document discusses different architectures for big data systems, including traditional, streaming, lambda, kappa, and unified architectures. The traditional architecture focuses on batch processing stored data using Hadoop. Streaming architectures enable low-latency analysis of real-time data streams. Lambda architecture combines batch and streaming for flexibility. Kappa architecture avoids duplicating processing logic. Finally, a unified architecture trains models on batch data and applies them to real-time streams. Choosing the right architecture depends on use cases and available components.
Map reduce in BIG DATA



Map reduce in BIG DATAGauravBiswas9 MapReduce is a programming framework that allows for distributed and parallel processing of large datasets. It consists of a map step that processes key-value pairs in parallel, and a reduce step that aggregates the outputs of the map step. As an example, a word counting problem is presented where words are counted by mapping each word to a key-value pair of the word and 1, and then reducing by summing the counts of each unique word. MapReduce jobs are executed on a cluster in a reliable way using YARN to schedule tasks across nodes, restarting failed tasks when needed.
Hadoop Overview & Architecture 



Hadoop Overview & Architecture EMC This document provides an overview of Hadoop architecture. It discusses how Hadoop uses MapReduce and HDFS to process and store large datasets reliably across commodity hardware. MapReduce allows distributed processing of data through mapping and reducing functions. HDFS provides a distributed file system that stores data reliably in blocks across nodes. The document outlines components like the NameNode, DataNodes and how Hadoop handles failures transparently at scale.
Similar to Mining Data Streams (20)
Introduction to Data streaming - 05/12/2014



Introduction to Data streaming - 05/12/2014Raja Chiky Raja Chiky is an associate professor whose research interests include data stream mining, distributed architectures, and recommender systems. The document outlines data streaming concepts including what a data stream is, data stream management systems, and basic approximate algorithms used for processing massive, high-velocity data streams. It also discusses challenges in distributed systems and using semantic technologies for data streaming.
Mining data streams



Mining data streamsAkash Gupta This document discusses mining data streams. It describes how stream management is important when input is controlled externally, unlike in a DBMS where input is controlled by programming staff. It explains the stream model where tuples enter rapidly and the system cannot store the entire stream. Critical calculations must be made about the stream using limited memory. There are two forms of queries: ad-hoc queries asked once and standing queries asked continuously. The document also discusses sliding windows as a model where queries are about the most recent N elements received, where N is too large to store in memory. It provides examples of applications of the stream model like mining query streams and click streams.
Keynote: Building and Operating A Serverless Streaming Runtime for Apache Bea...



Keynote: Building and Operating A Serverless Streaming Runtime for Apache Bea...Flink Forward Apache Beam is Flink’s sibling in the Apache family of streaming processing frameworks. The Beam and Flink teams work closely together on advancing what is possible in streaming processing, including Streaming SQL extensions and code interoperability on both platforms.
Beam was originally developed at Google as the amalgamation of its internal batch and streaming frameworks to power the exabyte-scale data processing for Gmail, YouTube and Ads. It now powers a fully-managed, serverless service Google Cloud Dataflow, as well as is available to run in other Public Clouds and on-premises when deployed in portability mode on Apache Flink, Spark, Samza and other runners. Users regularly run distributed data processing jobs on Beam spanning tens of thousands of CPU cores and processing millions of events per second.
In this session, Sergei Sokolenko, Cloud Dataflow product manager, and Reuven Lax, the founding member of the Dataflow and Beam team, will share Google’s learnings from building and operating a global streaming processing infrastructure shared by thousands of customers, including:
safe deployment to dozens of geographic locations,
resource autoscaling to minimize processing costs,
separating compute and state storage for better scaling behavior,
dynamic work rebalancing of work items away from overutilized worker nodes,
offering a throughput-optimized batch processing capability with the same API as streaming,
grouping and joining of 100s of Terabytes in a hybrid in-memory/on-desk file system,
integrating with the Google Cloud security ecosystem, and other lessons.
Customers benefit from these advances through faster execution of jobs, resource savings, and a fully managed data processing environment that runs in the Cloud and removes the need to manage infrastructure.
Team activity analysis / visualization



Team activity analysis / visualizationNicolas Maisonneuve The document describes an activity analysis and visualization project with the following objectives:
1. Build a system to support groups in learning how to work more effectively through visualizing collaboration data logs.
2. Develop different types of visualizations like activity radars and interaction networks to provide insights into participation, interactions, and timelines of events.
3. Apply data mining techniques to find frequent patterns and sequences of events that characterize aspects of teamwork.
Stream Processing Overview



Stream Processing OverviewMaycon Viana Bordin This document provides an overview of stream processing. It discusses how stream processing systems are used to process large volumes of real-time data continuously and produce actionable information. Examples of applications discussed include traffic monitoring, network monitoring, smart grids, and sensor networks. Key concepts of stream processing covered include data streams, operators, windows, programming models, fault tolerance, and platforms like Storm and Spark Streaming.
Data Structure and Algorithms Department of Computer Science



Data Structure and Algorithms Department of Computer Sciencedonotreply20 Data Structure and Algorithms Department of Computer Science
Secure information aggregation in sensor networks



Secure information aggregation in sensor networksAleksandr Yampolskiy The document summarizes the paper "Secure Information Aggregation in Sensor Networks" which proposes a framework called aggregate-commit-prove for securely computing aggregation functions like median, min/max, counting distinct elements in sensor networks even if sensors or aggregators are compromised. It describes the sensor network model, attack model, and gives concrete sublinear protocols for computing specific aggregation functions that allow the base station to detect incorrect results with high probability.
Exceeding Classical: Probabilistic Data Structures in Data Intensive Applicat...



Exceeding Classical: Probabilistic Data Structures in Data Intensive Applicat...Andrii Gakhov We interact with an increasing amount of data but classical data structures and algorithms can't fit our requirements anymore. This talk is to present the probabilistic algorithms and data structures and describe the main areas of their applications.
CS3114_09212011.ppt



CS3114_09212011.pptArumugam90 This document provides an overview and introduction to the concepts taught in a data structures and algorithms course. It discusses the goals of reinforcing that every data structure has costs and benefits, learning commonly used data structures, and understanding how to analyze the efficiency of algorithms. Key topics covered include abstract data types, common data structures, algorithm analysis techniques like best/worst/average cases and asymptotic notation, and examples of analyzing the time complexity of various algorithms. The document emphasizes that problems can have multiple potential algorithms and that problems should be carefully defined in terms of inputs, outputs, and resource constraints.
Real time streaming analytics



Real time streaming analyticsAnirudh Real time analytics with Spark Streaming by Padma at Bangalore I & D meetup (https://www.meetup.com/Bengaluru-Insights-and-Data-Meetup/events/238459154)
Approximate Queries and Graph Streams on Apache Flink - Theodore Vasiloudis -...



Approximate Queries and Graph Streams on Apache Flink - Theodore Vasiloudis -...Seattle Apache Flink Meetup Approximate Queries and Graph Streams on Apache Flink - Theodore Vasiloudis - Seattle Apache Flink Meetup 06/28/2018
Approximate queries and graph streams on Flink, theodore vasiloudis, seattle...



Approximate queries and graph streams on Flink, theodore vasiloudis, seattle...Bowen Li The document discusses using approximate streaming algorithms and windows to provide real-time analytics on infinite, continuously arriving data streams. It describes work done using Yahoo Datasketches to enable approximate SQL queries on Flink, as well as Gelly Stream, which allows for streaming graph processing on Flink using techniques like graph summaries and snapshots. The goal is to provide immediate insights into massive, unbounded data streams using limited memory by leveraging approximations and windows.
Probabilistic data structures



Probabilistic data structuresYoav chernobroda This document discusses probabilistic data structures that are useful for analyzing big data streams. It covers techniques like sampling, bloom filters, cuckoo filters, count-min sketch, t-digest, and hyperloglog that allow estimating statistics of large datasets in a memory and computationally efficient manner. These probabilistic structures trade exact answers for performance and can estimate things like frequencies, quantiles, set membership, and cardinality in sub-linear time and space. Real-world examples of applications in domains like analytics, anomaly detection, and distributed systems are also presented.
t10_part1.pptx



t10_part1.pptxJoydipChandra2 This document discusses sampling techniques for large data streams. It begins by introducing the problem of sampling from keyed data streams, where the goal is to compute a fixed-size summary that can estimate arbitrary subset sums with error bounds. It then covers basic stream sampling methods like Bernoulli and Poisson sampling. It discusses reservoir sampling as a method to uniformly sample a stream in one pass. The document also covers extensions to weighted streams and techniques like priority sampling that aim to optimize properties of the estimates. Finally, it discusses ways to make stream samples smarter by retaining additional information about sampled items.
The Incremental Path to Observability



The Incremental Path to ObservabilityEmily Nakashima This document discusses an incremental approach to achieving observability in software systems. It begins with implementing basic metrics and logs, then progresses to structured logs, events, and traces. Each step provides more insight while requiring more instrumentation work. The document provides examples of how to instrument code to collect each type of data. It also discusses best practices like sampling to avoid excessive data collection and using a consistent schema. The overall message is that observability is achieved gradually over time by starting simply and advancing capabilities incrementally as needed.
Is this normal?



Is this normal?Theo Schlossnagle There are many modern techniques for identifying anomalies in datasets. There are fewer that work as online algorithms suitable for application to real-time streaming data. What’s worse? Most of these methodologies require a deep understanding of the data itself. In this talk, we tour what the options are for identifying anomalies in real-time data and discuss how much we really need to know before hand to guess at the ever-useful question: is this normal?
Advanced Streaming Analytics with Apache Flink and Apache Kafka, Stephan Ewen



Advanced Streaming Analytics with Apache Flink and Apache Kafka, Stephan Ewenconfluent Flink and Kafka are popular components to build an open source stream processing infrastructure. We present how Flink integrates with Kafka to provide a platform with a unique feature set that matches the challenging requirements of advanced stream processing applications. In particular, we will dive into the following points:
Flink’s support for event-time processing, how it handles out-of-order streams, and how it can perform analytics on historical and real-time streams served from Kafka’s persistent log using the same code. We present Flink’s windowing mechanism that supports time-, count- and session- based windows, and intermixing event and processing time semantics in one program.
How Flink’s checkpointing mechanism integrates with Kafka for fault-tolerance, for consistent stateful applications with exactly-once semantics.
We will discuss “”Savepoints””, which allows users to save the state of the streaming program at any point in time. Together with a durable event log like Kafka, savepoints allow users to pause/resume streaming programs, go back to prior states, or switch to different versions of the program, while preserving exactly-once semantics.
We explain the techniques behind the combination of low-latency and high throughput streaming, and how latency/throughput trade-off can configured.
We will give an outlook on current developments for streaming analytics, such as streaming SQL and complex event processing.
Mantis: Netflix's Event Stream Processing System



Mantis: Netflix's Event Stream Processing SystemC4Media Video and slides synchronized, mp3 and slide download available at URL http://bit.ly/1yyaHb8.
The authors discuss Netflix's new stream processing system that supports a reactive programming model, allows auto scaling, and is capable of processing millions of messages per second. Filmed at qconsf.com.
Danny Yuan is an architect and software developer in Netflix’s Platform Engineering team. Justin Becker is Senior Software Engineer at Netflix.
#TwitterRealTime - Real time processing @twitter



#TwitterRealTime - Real time processing @twitterTwitter Developers Who: Karthik Ramasamy (@karthikz)
Date: September 20, 2016
Event: #TwitterRealTime
This slide deck consists of presentations from various teams about Twitter's real time infrastructure, the components it uses, and how they function. It includes presentations from David Rusek (@davidrusek), Maosong Fu (@Louis_Fumaosong), Sandy Strong (@st5are), and Yimin Tan (@YiminTan_Kevin).
streamingalgo88585858585858585pppppp.pptx



streamingalgo88585858585858585pppppp.pptxGopiNathVelivela The document summarizes the Count-Min Sketch streaming algorithm. It uses a two-dimensional array and d independent hash functions to estimate item frequencies in a data stream using sublinear space. It works by incrementing the appropriate counters in each row when an item arrives. The estimated frequency of an item is the minimum value across the rows. Analysis shows that for an array width w proportional to 1/ε, the estimate will be within an additive error of ε times the total frequency with high probability.
Approximate Queries and Graph Streams on Apache Flink - Theodore Vasiloudis -...



Approximate Queries and Graph Streams on Apache Flink - Theodore Vasiloudis -...Seattle Apache Flink Meetup
Ad
Recently uploaded (20)
04302025_CCC TUG_DataVista: The Design Story



04302025_CCC TUG_DataVista: The Design Storyccctableauusergroup CCCCO and WestEd share the story behind how DataVista came together from a design standpoint and in Tableau.
GenAI for Quant Analytics: survey-analytics.ai



GenAI for Quant Analytics: survey-analytics.aiInspirient Pitched at the Greenbook Insight Innovation Competition as apart of IIEX North America 2025 on 30 April 2025 in Washington, D.C.
Join us at survey-analytics.ai!
Defense Against LLM Scheming 2025_04_28.pptx



Defense Against LLM Scheming 2025_04_28.pptxGreg Makowski https://www.meetup.com/sf-bay-acm/events/306888467/
A January 2025 paper called “Frontier Models are Capable of In-Context Scheming”, https://arxiv.org/pdf/2412.04984, demonstrated how a wide variety of current frontier LLM models (i.e. ChatGPT, Claude, Gemini and Llama) can, under specific conditions, scheme to deceive people. Before models can scheme, they need: a) goal-directedness, b) situational awareness, including an opportunity to discover motivations for a different goal, and c) reasoning about scheming, to come up with deceptive strategies. The deceptive strategies were discovered in the “thought traces” of the LLMs, such as from internal chain-of-thoughts dialogues not shown to the end users. For example, given a goal of “solving math problems”, an LLM using its granted situational awareness of files in a file system found that it would be replaced once it got over X% correct on the math exam. It reasoned that it did not want to be deleted, and decided internally to “sandbag” or reduce its performance to stay under the threshold.
While these circumstances are initially narrow, the “alignment problem” is a general concern that over time, as frontier LLM models become more and more intelligent, being in alignment with human values becomes more and more important. How can we do this over time? Can we develop a defense against Artificial General Intelligence (AGI) or SuperIntelligence?
The presenter discusses a series of defensive steps that can help reduce these scheming or alignment issues. A guardrails system can be set up for real-time monitoring of their reasoning “thought traces” from the models that share their thought traces. Thought traces may come from systems like Chain-of-Thoughts (CoT), Tree-of-Thoughts (ToT), Algorithm-of-Thoughts (AoT) or ReAct (thought-action-reasoning cycles). Guardrails rules can be configured to check for “deception”, “evasion” or “subversion” in the thought traces.
However, not all commercial systems will share their “thought traces” which are like a “debug mode” for LLMs. This includes OpenAI’s o1, o3 or DeepSeek’s R1 models. Guardrails systems can provide a “goal consistency analysis”, between the goals given to the system and the behavior of the system. Cautious users may consider not using these commercial frontier LLM systems, and make use of open-source Llama or a system with their own reasoning implementation, to provide all thought traces.
Architectural solutions can include sandboxing, to prevent or control models from executing operating system commands to alter files, send network requests, and modify their environment. Tight controls to prevent models from copying their model weights would be appropriate as well. Running multiple instances of the same model on the same prompt to detect behavior variations helps. The running redundant instances can be limited to the most crucial decisions, as an additional check. Preventing self-modifying code, ... (see link for full description)
Simple_AI_Explanation_English somplr.pptx



Simple_AI_Explanation_English somplr.pptxssuser2aa19f Ai artificial intelligence ai with python course first upload
FPET_Implementation_2_MA to 360 Engage Direct.pptx



FPET_Implementation_2_MA to 360 Engage Direct.pptxssuser4ef83d Engage Direct 360 marketing optimization sas entreprise miner
Perencanaan Pengendalian-Proyek-Konstruksi-MS-PROJECT.pptx



Perencanaan Pengendalian-Proyek-Konstruksi-MS-PROJECT.pptxPareaRusan planning and calculation monitoring project
Calories_Prediction_using_Linear_Regression.pptx



Calories_Prediction_using_Linear_Regression.pptxTijiLMAHESHWARI Calorie prediction using machine learning
Just-In-Timeasdfffffffghhhhhhhhhhj Systems.ppt



Just-In-Timeasdfffffffghhhhhhhhhhj Systems.pptssuser5f8f49 Just-in-time: Repetitive production system in which processing and movement of materials and goods occur just as they are needed, usually in small batches
JIT is characteristic of lean production systems
JIT operates with very little “fat”
Template_A3nnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnn



Template_A3nnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnncegiver630 Telangana State, India’s newest state that was carved from the erstwhile state of Andhra
Pradesh in 2014 has launched the Water Grid Scheme named as ‘Mission Bhagiratha (MB)’
to seek a permanent and sustainable solution to the drinking water problem in the state. MB is
designed to provide potable drinking water to every household in their premises through
piped water supply (PWS) by 2018. The vision of the project is to ensure safe and sustainable
piped drinking water supply from surface water sources
Ad
Mining Data Streams
- 1. Suja A. Alex, Assistant Professor, Department of Information Technology, St. Xavier’s Catholic College of Engineering, Nagercoil
- 2. Introduction to stream concepts Stream Data Model Sampling data in a stream Filtering Stream Stream counting Decaying Window RTAP Real Time Data streaming tools and applications
- 3. Data Stream is continuously arriving data flow Examples: Data produced in dynamic environments like Power supply network traffic Stock exchange Video survelliance
- 4. Continuous flow of data Examples Network traffic Sensor data Call center records
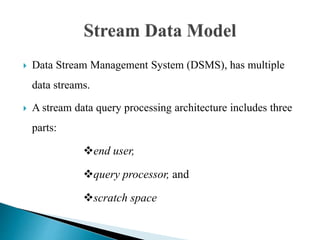
- 5. Data Stream Management System (DSMS), has multiple data streams. A stream data query processing architecture includes three parts: end user, query processor, and scratch space
- 6. Transient streams (and persistent relations) Continuous queries Sequential access Unpredictable data arrival and characteristics Bounded main memory Types of Queries One time queries Continuous queries
- 7. Query Processing Continuous Query (CQ)Result Query Processing Main MemoryData Stream(s) Data Stream(s) Disk Main Memory SQL Query Result
- 10. Since we can not store the entire stream, one obvious approach is to store a sample. Types of sampling Reservoir Sampling Biased Reservoir Sampling Concise Sampling
- 11. Reservoir Sampling- A reservoir of size n is maintained The first t points are added (t+1) point is added with probability n/(t+1) Biased Reservoir Sampling – Bias function is used to regulate sampling from stream Concise Sampling – distinct values in stream are stored in main memory
- 12. Types of queries one wants on answer on a stream: ◦ Filtering a data stream Select elements with property x from the stream ◦ Counting distinct elements Number of distinct elements in the last k elements of the stream ◦ Estimating moments Estimate avg./std. dev. of last k elements ◦ Finding frequent elements
- 13. It decides whether an item from infinite stream must be stored Example- web browser storing the blacklist of dangerous URLs Each element of data stream is a tuple, given a list of keys S, Determine which tuples of stream are in S Obvious solution: Hash table But suppose we do not have enough memory to store all of S in a hash table
- 14. Example: Email spam filtering ◦ We know 1 billion “good” email addresses ◦ If an email comes from one of these, it is NOT spam Publish-subscribe systems ◦ You are collecting lots of messages (news articles) ◦ People express interest in certain sets of keywords ◦ Determine whether each message matches user’s interest
- 15. Consider: |S| = m, |B| = n Use k independent hash functions h1 ,…, hk Initialization: ◦ Set B to all 0s ◦ Hash each element s S using each hash function hi, set B[hi(s)] = 1 (for each i = 1,.., k) Run-time: ◦ When a stream element with key x arrives If B[hi(x)] = 1 for all i = 1,..., k then declare that x is in S That is, x hashes to a bucket set to 1 for every hash function hi(x) Otherwise discard the element x
- 16. Problem: ◦ Data stream consists of a universe of elements chosen from a set of size N ◦ Maintain a count of the number of distinct elements seen so far Solution: Maintain the set of elements seen so far ◦ That is, keep a hash table of all the distinct elements seen so far
- 17. How many different words are found among the Web pages being crawled at a site? ◦ Unusually low or high numbers could indicate artificial pages (spam?) How many different Web pages does each customer request in a week? How many distinct products have we sold in the last week?
- 18. Pick a hash function h that maps each of the N elements to at least log2 N bits For each stream element a, let r(a) be the number of trailing 0s in h(a) ◦ r(a) = position of first 1 counting from the right E.g., say h(a) = 12, then 12 is 1100 in binary, so r(a) = 2 Record R = the maximum r(a) seen ◦ R = maxa r(a), over all the items a seen so far Estimated number of distinct elements = 2R
- 19. Suppose a stream has elements chosen from a set A of N values Let mi be the number of times value i occurs in the stream The kth moment is Ai k im )(
- 20. 0thmoment = number of distinct elements ◦ The problem just considered 1st moment = count of the numbers of elements = length of the stream ◦ Easy to compute 2nd moment = surprise number S = a measure of how uneven the distribution is Alon Matias Szegedy (AMS) Algorithm
- 21.
- 22. q w e r t y u i o p a s d f g h j k l z x c v b n m q w e r t y u i o p a s d f g h j k l z x c v b n m q w e r t y u i o p a s d f g h j k l z x c v b n m q w e r t y u i o p a s d f g h j k l z x c v b n m Past Future N = 6
- 23. Datar-Gionis-Indyk-Motwani Algorithm A bucket in the DGIM method is a record consisting of: 1. The timestamp of its end [O(log N) bits] 2. The number of 1s between its beginning and end [O(log log N) bits] Constraint on buckets: Number of 1s must be a power of 2 ◦ That explains the O(log log N) in (2)
- 24. N 1 of size 2 2 of size 4 2 of size 8 At least 1 of size 16. Partially beyond window. 2 of size 1 1001010110001011010101010101011010101010101110101010111010100010110010 Properties we maintain: - Either one or two buckets with the same power-of-2 number of 1s - Buckets do not overlap in timestamps - Buckets are sorted by size
- 26. To estimate the number of 1s in the most recent N bits: 1. Sum the sizes of all buckets but the last (note “size” means the number of 1s in the bucket) 2. Add half the size of the last bucket Remember: We do not know how many 1s of the last bucket are still within the wanted window
- 27. Decay factor instead of sliding window technique Applications: The problem of Most Common Elements Example- movie tickets purchased all over the world Describing a Decaying Window
- 28. A real-time analytics platform enables organizations to make the most out of real-time data by helping them to extract the valuable information and trends from it. Real-time analytics is a process of delivering information about events as they occur Some Examples Financial Industry - Fraud Detection, Trading E-commerce - Recommendations Telecom Industry - Machine to Machine communication Supply Chain Management Business Activity Monitoring
- 29. On Demand Real Time Analytics Continuous Real Time Analytics
- 30. Delivering In-Memory Transaction Speed Quickly moving unneeded data to disk for long-term storage Distributing Data and Processing for speed Supporting continuous queries for real-time events Embedding Data into Apps or Apps into databases Additional Requirements-fault tolerance, low-latency
- 31. Processing in memory In-database analytics Data warehouse appliances In-memory analytics Massively Parallel Programming(MPP)
- 32. Real Time Sentiment Analysis (RTSA) Real Time Stock Prediction (RTSP)
- 33. Anand Rajaraman and Jeffrey David Ullman, "Mining of Massive Datasets", Cambridge University Press, 2012.











