Module 3 Scanning
Download as PPT, PDF4 likes3,221 views
The document discusses scanning techniques used during penetration testing and hacking. It defines different types of scanning like port scanning, network scanning, and vulnerability scanning. It describes tools like Nmap that can be used to perform these scans and examines techniques like SYN scanning, XMAS scanning, NULL scanning, and IDLE scanning. The document also discusses using proxies and anonymizers to hide one's location while scanning and ways to document results like creating network diagrams of vulnerable systems.
1 of 55
Downloaded 293 times






















































Ad
Recommended
Ceh v5 module 03 scanning



Ceh v5 module 03 scanningVi Tính Hoàng Nam This document provides an overview of scanning techniques used in ethical hacking. It defines scanning as gathering information about IP addresses, operating systems, services, and architectures of target systems. The document outlines common scanning types like port scanning, network scanning, and vulnerability scanning. It also describes popular scanning tools like Nmap and Hping2, and scanning methods like ping sweeps, SYN stealth scans, and Xmas scans. The goal of scanning is to detect live systems, open ports, operating systems, and services to inform later stages of hacking like banner grabbing, vulnerability assessment, and network mapping.
Cross Site Scripting ( XSS)



Cross Site Scripting ( XSS)Amit Tyagi Cross Site Scripting (XSS) is a vulnerability that allows malicious users to insert client-side code into web pages that is then executed by a user's browser. This code can steal cookies, access private information, perform actions on the user's behalf, and redirect them to malicious websites. XSS works by having the server display input containing malicious JavaScript from a request. There are different types of XSS attacks, including non-persistent, persistent, and DOM-based attacks. Prevention methods include validating, sanitizing, and escaping all user input on the server-side and client-side. Web vulnerability scanners like Burp Suite can help test for XSS and other vulnerabilities.
Man in the middle attack .pptx



Man in the middle attack .pptxPradeepKumar728006 A man-in-the-middle (MitM) attack is a type of cyber attack where the attacker secretly intercepts communications between two parties who believe they are directly communicating with each other. The attacker can then steal sensitive information like user credentials by redirecting traffic to fake websites or intercepting network traffic. Common MitM attacks include DNS spoofing, HTTP spoofing, cache poisoning, and session hijacking. Organizations can help prevent these attacks by using HTTPS, avoiding public WiFi, implementing endpoint security, and warning users about phishing emails.
Vulnerabilities in modern web applications



Vulnerabilities in modern web applicationsNiyas Nazar Microsoft powerpoint presentation for BTech academic seminar.This seminar discuses about penetration testing, penetration testing tools, web application vulnerabilities, impact of vulnerabilities and security recommendations.
Packet sniffing in switched LANs



Packet sniffing in switched LANsIshraq Al Fataftah This document discusses packet sniffing and ways to detect and prevent it. Packet sniffing involves using a packet sniffer tool to analyze network traffic. While switches make sniffing more difficult than hubs by only sending packets to their intended recipients, there are still sniffing attacks possible like ARP spoofing. The document outlines techniques for sniffing detection such as ARP cache poisoning and tools like Arpwatch. It also recommends prevention methods including port security, authentication, encryption, and secure protocols.
Ceh v5 module 02 footprinting



Ceh v5 module 02 footprintingVi Tính Hoàng Nam This document provides an overview of footprinting and information gathering techniques used during the reconnaissance phase of an ethical hacking engagement. It defines footprinting as gathering a security profile of an organization through open source intelligence prior to an attack. The document outlines various methodologies for passively gathering initial information, locating networks and systems, identifying services and technologies in use, and collecting competitive intelligence. It provides examples of tools and resources that can be used to uncover personnel details, technical infrastructure information, business plans and strategies from competitors through open sources.
Network Security Presentation



Network Security PresentationAllan Pratt MBA The document provides tips for keeping a network secure, including always keeping virus software and Windows updates enabled, using firewalls, backing up data regularly, and using strong passwords. It warns about common password risks like using obvious words or writing passwords down. The document also covers securing laptops, email, wireless networks, and avoiding risks from open networks. Proper authentication, surge protection, and password protecting are emphasized as important security best practices.
Ethical Hacking Powerpoint



Ethical Hacking PowerpointRen Tuazon This powerpoint contains:
*Introduction (Hacking, hackers, Ethical Hacking, Ethical Hackers)
* Ethical Hacker Commandments
* Ethical Hacking Process
* Ethical hacking Tools
* Advantages and Disadvantages
Basics of Network Security



Basics of Network SecurityDushyant Singh This document defines network and information security and discusses various threats. It defines security as protecting systems, hardware, information and data. It outlines the principles of confidentiality, integrity and availability. It describes passive attacks like traffic analysis and active attacks like masquerading, replay and denial of service. It discusses vulnerabilities like malicious software, trap doors, logic bombs, Trojan horses, viruses and worms. It provides details on each of these threats and ways to prevent infections from malicious software.
Network scanning



Network scanningoceanofwebs A network consists of 3 parts: IP addresses, services, and ports. An IP address has a network and host address determined by the subnet mask. Services are network protocols that link server and client applications, typically running on specific ports, though any service can run on any port. Ports allow different services to be available from one location, with common services using well-known ports. Network scanning includes host scanning to locate hosts, port scanning to determine services, and vulnerability scanning to find known flaws using signature-based tools like Nmap, Nessus, GFI LANguard, and SuperScan.
Ceh v5 module 04 enumeration



Ceh v5 module 04 enumerationVi Tính Hoàng Nam This document discusses techniques for system enumeration, including establishing null sessions, enumerating user accounts, SNMP scanning, and Active Directory enumeration. It provides an overview of the system hacking cycle and covers various tools that can be used to extract information like user names, machine names, shares, and services through techniques like null sessions, SNMP probing, and using default credentials. The document also discusses countermeasures for these enumeration methods.
Packet sniffing



Packet sniffingShyama Bhuvanendran Packet sniffing involves monitoring network traffic by capturing and analyzing data packets as they flow through a network interface. It can be performed using packet sniffers, which are programs that can intercept and read all network traffic passing through a device's network interface card or wireless adapter. While packet sniffers can be used for troubleshooting network issues, they can also be used maliciously by hackers to intercept sensitive information like usernames and passwords by using techniques like ARP spoofing to fool devices into thinking the hacker's machine has the IP address of another machine on the network. Network administrators can use tools to detect the presence of packet sniffers operating in promiscuous mode and monitor ARP caches for signs of spoofing.
Introduction to foot printing



Introduction to foot printingCHETAN THAKRE This document discusses footprinting, which is the first step in hacking where a hacker gathers information about a target system. It describes footprinting as both active (direct interaction with the target) and passive (collecting publicly available information). Some methods covered include using the Wayback Machine to view past versions of websites, performing WhoIs lookups to find domain ownership data, using Nmap to discover active machines and open ports, and using social engineering to trick people into revealing confidential information. The goal of footprinting is to learn as much as possible about a target to determine suitable attacks.
Ch 5: Port Scanning



Ch 5: Port ScanningSam Bowne Slides for a college course at City College San Francisco. Based on "Hands-On Ethical Hacking and Network Defense, Third Edition" by Michael T. Simpson, Kent Backman, and James Corley -- ISBN: 9781285454610.
Instructor: Sam Bowne
Class website: https://samsclass.info/123/123_S17.shtml
Session Hijacking



Session Hijackingn|u - The Open Security Community Session hijacking involves an attacker stealing a valid user session ID to gain access to a system and retrieve data. There are several types of session hijacking such as predictable session tokens, session sniffing, and man-in-the-middle attacks. To perform session hijacking, an attacker places themselves between the victim and target server, monitors packet flows, and predicts sequence numbers to take over the user's session and inject packets to the target server. Mitigations include using HTTPS, a VPN, limiting exposure to untrusted networks, and educating employees. Tools that can be used for session hijacking include Firesheep and other programs.
Ceh v5 module 11 hacking webservers



Ceh v5 module 11 hacking webserversVi Tính Hoàng Nam This module discusses vulnerabilities in web servers like Apache and IIS. It covers how web servers work, common vulnerabilities in areas like configurations, bugs and default installations. Specific attacks covered include defacement, directory traversal using Unicode encoding, buffer overflows in ISAPI extensions and RPC DCOM. The module also discusses tools used in attacks like IISxploit and countermeasures like patch management and vulnerability scanning.
Ethical Hacking - sniffing



Ethical Hacking - sniffingBhavya Chawla Packet sniffing tools like Ethereal and Snort can be used to intercept network traffic for diagnostic or malicious purposes. Sniffing tools capture packets in either command line or GUI format and some can reassemble packets into original data like emails. Sniffing can reveal usernames, passwords, and other confidential information unless encryption is used. Common sniffing techniques include passive sniffing using hubs, active sniffing using ARP spoofing on switches, and MAC flooding to force switch traffic to a sniffer. Encryption renders captured data useless, while detection tools can find machines in promiscuous sniffing mode.
Ethical Hacking n VAPT presentation by Suvrat jain



Ethical Hacking n VAPT presentation by Suvrat jainSuvrat Jain a perfect example of your 6 weeks summer training ppt. Course-Ethical Hacking , its info and VAPT- Vulnerability Assessment n Penetration testing. about how vulnerability scanning , tools used , cracking password , etc.
Port scanning



Port scanningHemanth Pasumarthi About Port Scanning
Used Nmap and Shadow Security scanner for the best outputs.
A Detailed description on performing the port scanning mostly for the network administrators.
Why to perform? How to perform? Where to perform? these areas are taken into consideration and presented with best output results using tools "nmap scanner" and "shadow security scanner".
DDoS - Distributed Denial of Service



DDoS - Distributed Denial of ServiceEr. Shiva K. Shrestha This document discusses distributed denial of service (DDoS) attacks. It begins with an introduction that defines denial of service (DoS) attacks and how DDoS attacks differ in employing multiple compromised computers to coordinate a widespread attack. It then provides examples of targets that can be affected and overviews how DDoS attacks work by flooding the victim with traffic from many sources. The document goes on to discuss specific DDoS attack types, defenses against attacks, and how attacks are practically handled through router filtering, black hole routing, and traffic diversion techniques.
Network defenses



Network defensesG Prachi Network defenses include tools like firewalls, VPNs, and intrusion detection systems that help secure networks and protect them from cyber attacks. Firewalls act as barriers that control incoming and outgoing network traffic according to security policies. VPNs extend private networks over public networks through secure tunnels. Intrusion detection systems monitor network traffic and detect suspicious activity. Denial of service attacks aim to make network services unavailable by overwhelming them with malicious traffic. Distributed denial of service attacks use multiple compromised systems to launch large-scale attacks.
Ethical hacking ppt



Ethical hacking pptNitesh Dubey its contains all the topics which are related to the ethical hacking
its also be cover the penetration testing and describe the difference between ethical hacker and non ethical hackers
Network security



Network securitySimranpreet Singh Network security presentation that briefly covers the aspect of security in networks. The slide consists of procedural steps for network security then some of the important network security components are described. To give it a practical approach, attacks on networks are also covered.
Ethical Hacking



Ethical HackingNitheesh Adithyan This document discusses ethical hacking and penetration testing. It begins by defining ethical hacking as using the same tools and techniques as hackers, but legally in order to test an organization's security. It then covers the history of ethical hacking. The rest of the document outlines the methodology of hacking including reconnaissance, scanning, gaining access, maintaining access, and clearing tracks. It discusses the types of hackers and tools used in ethical hacking. The document concludes by discussing the advantages and disadvantages of ethical hacking.
Vulnerability and Assessment Penetration Testing



Vulnerability and Assessment Penetration TestingYvonne Marambanyika VAPT defines a wide range of security testing services to ascertain and address cyber security exposures. It includes vulnerability testing through perimeter scans for missing patches or custom exploits to bypass perimeters, as well as penetration testing by simulating real-world attacks to provide a point-in-time assessment of vulnerabilities and threats to a network infrastructure. Customers can inquire more about these security testing and analysis services by contacting the company.
Penetration Testing 



Penetration Testing RomSoft SRL Penetration testing is used to test the security of a website by simulating real attacks from outside. It identifies potential vulnerabilities to prevent harmful attacks. By understanding how attacks work, the IT team can fix issues and prevent larger attacks in the future. The presentation will demonstrate a penetration testing tool that checks the login page for security issues like authentication, redirects, and hidden code. Contact information is provided for any additional questions.
Pen Testing Explained



Pen Testing ExplainedRand W. Hirt This document provides an overview of penetration testing, including its definition, purpose, types, methodology, tools, challenges, and takeaways. Penetration testing involves modeling real-world attacks to find vulnerabilities in a system and then attempting to exploit those vulnerabilities to determine security risks. It is important for identifying flaws that need remediation and assessing an organization's security posture and risk profile. The methodology generally involves planning, reconnaissance, scanning, exploitation, and reporting phases. Challenges include performing comprehensive testing within time and budget constraints and addressing business impact.
Computer Security and Intrusion Detection(IDS/IPS)



Computer Security and Intrusion Detection(IDS/IPS)LJ PROJECTS This ppt explain you various type of possible attack, security property, Traffic Analysis, Security mechanism Intrusion detection system, vulnerability, Attack framework etc.
Access Controls Attacks



Access Controls AttacksHafiza Abas Logic bombs are malicious codes hidden in software that execute when predefined conditions are met, such as a specific date or time. They can damage systems by deleting files or entirely wiping computers. Spoofing attacks impersonate other devices or users on a network to launch attacks, steal data, or bypass access controls. Types of spoofing include IP address spoofing, ARP spoofing, DNS server spoofing, web spoofing, and email spoofing. Phishing is a form of deception designed to steal personal information like credit card numbers or passwords by tricking users into entering information on fake websites or responding to fraudulent emails.
Detection of Idle Stealth Port Scan Attack in Network Intrusion Detection Sys...



Detection of Idle Stealth Port Scan Attack in Network Intrusion Detection Sys...skpatel91 this is my thesis presentation on Detection of Idle Stealth Port Scan Attack in Network Intrusion Detection System using Snort
Ad
More Related Content
What's hot (20)
Basics of Network Security



Basics of Network SecurityDushyant Singh This document defines network and information security and discusses various threats. It defines security as protecting systems, hardware, information and data. It outlines the principles of confidentiality, integrity and availability. It describes passive attacks like traffic analysis and active attacks like masquerading, replay and denial of service. It discusses vulnerabilities like malicious software, trap doors, logic bombs, Trojan horses, viruses and worms. It provides details on each of these threats and ways to prevent infections from malicious software.
Network scanning



Network scanningoceanofwebs A network consists of 3 parts: IP addresses, services, and ports. An IP address has a network and host address determined by the subnet mask. Services are network protocols that link server and client applications, typically running on specific ports, though any service can run on any port. Ports allow different services to be available from one location, with common services using well-known ports. Network scanning includes host scanning to locate hosts, port scanning to determine services, and vulnerability scanning to find known flaws using signature-based tools like Nmap, Nessus, GFI LANguard, and SuperScan.
Ceh v5 module 04 enumeration



Ceh v5 module 04 enumerationVi Tính Hoàng Nam This document discusses techniques for system enumeration, including establishing null sessions, enumerating user accounts, SNMP scanning, and Active Directory enumeration. It provides an overview of the system hacking cycle and covers various tools that can be used to extract information like user names, machine names, shares, and services through techniques like null sessions, SNMP probing, and using default credentials. The document also discusses countermeasures for these enumeration methods.
Packet sniffing



Packet sniffingShyama Bhuvanendran Packet sniffing involves monitoring network traffic by capturing and analyzing data packets as they flow through a network interface. It can be performed using packet sniffers, which are programs that can intercept and read all network traffic passing through a device's network interface card or wireless adapter. While packet sniffers can be used for troubleshooting network issues, they can also be used maliciously by hackers to intercept sensitive information like usernames and passwords by using techniques like ARP spoofing to fool devices into thinking the hacker's machine has the IP address of another machine on the network. Network administrators can use tools to detect the presence of packet sniffers operating in promiscuous mode and monitor ARP caches for signs of spoofing.
Introduction to foot printing



Introduction to foot printingCHETAN THAKRE This document discusses footprinting, which is the first step in hacking where a hacker gathers information about a target system. It describes footprinting as both active (direct interaction with the target) and passive (collecting publicly available information). Some methods covered include using the Wayback Machine to view past versions of websites, performing WhoIs lookups to find domain ownership data, using Nmap to discover active machines and open ports, and using social engineering to trick people into revealing confidential information. The goal of footprinting is to learn as much as possible about a target to determine suitable attacks.
Ch 5: Port Scanning



Ch 5: Port ScanningSam Bowne Slides for a college course at City College San Francisco. Based on "Hands-On Ethical Hacking and Network Defense, Third Edition" by Michael T. Simpson, Kent Backman, and James Corley -- ISBN: 9781285454610.
Instructor: Sam Bowne
Class website: https://samsclass.info/123/123_S17.shtml
Session Hijacking



Session Hijackingn|u - The Open Security Community Session hijacking involves an attacker stealing a valid user session ID to gain access to a system and retrieve data. There are several types of session hijacking such as predictable session tokens, session sniffing, and man-in-the-middle attacks. To perform session hijacking, an attacker places themselves between the victim and target server, monitors packet flows, and predicts sequence numbers to take over the user's session and inject packets to the target server. Mitigations include using HTTPS, a VPN, limiting exposure to untrusted networks, and educating employees. Tools that can be used for session hijacking include Firesheep and other programs.
Ceh v5 module 11 hacking webservers



Ceh v5 module 11 hacking webserversVi Tính Hoàng Nam This module discusses vulnerabilities in web servers like Apache and IIS. It covers how web servers work, common vulnerabilities in areas like configurations, bugs and default installations. Specific attacks covered include defacement, directory traversal using Unicode encoding, buffer overflows in ISAPI extensions and RPC DCOM. The module also discusses tools used in attacks like IISxploit and countermeasures like patch management and vulnerability scanning.
Ethical Hacking - sniffing



Ethical Hacking - sniffingBhavya Chawla Packet sniffing tools like Ethereal and Snort can be used to intercept network traffic for diagnostic or malicious purposes. Sniffing tools capture packets in either command line or GUI format and some can reassemble packets into original data like emails. Sniffing can reveal usernames, passwords, and other confidential information unless encryption is used. Common sniffing techniques include passive sniffing using hubs, active sniffing using ARP spoofing on switches, and MAC flooding to force switch traffic to a sniffer. Encryption renders captured data useless, while detection tools can find machines in promiscuous sniffing mode.
Ethical Hacking n VAPT presentation by Suvrat jain



Ethical Hacking n VAPT presentation by Suvrat jainSuvrat Jain a perfect example of your 6 weeks summer training ppt. Course-Ethical Hacking , its info and VAPT- Vulnerability Assessment n Penetration testing. about how vulnerability scanning , tools used , cracking password , etc.
Port scanning



Port scanningHemanth Pasumarthi About Port Scanning
Used Nmap and Shadow Security scanner for the best outputs.
A Detailed description on performing the port scanning mostly for the network administrators.
Why to perform? How to perform? Where to perform? these areas are taken into consideration and presented with best output results using tools "nmap scanner" and "shadow security scanner".
DDoS - Distributed Denial of Service



DDoS - Distributed Denial of ServiceEr. Shiva K. Shrestha This document discusses distributed denial of service (DDoS) attacks. It begins with an introduction that defines denial of service (DoS) attacks and how DDoS attacks differ in employing multiple compromised computers to coordinate a widespread attack. It then provides examples of targets that can be affected and overviews how DDoS attacks work by flooding the victim with traffic from many sources. The document goes on to discuss specific DDoS attack types, defenses against attacks, and how attacks are practically handled through router filtering, black hole routing, and traffic diversion techniques.
Network defenses



Network defensesG Prachi Network defenses include tools like firewalls, VPNs, and intrusion detection systems that help secure networks and protect them from cyber attacks. Firewalls act as barriers that control incoming and outgoing network traffic according to security policies. VPNs extend private networks over public networks through secure tunnels. Intrusion detection systems monitor network traffic and detect suspicious activity. Denial of service attacks aim to make network services unavailable by overwhelming them with malicious traffic. Distributed denial of service attacks use multiple compromised systems to launch large-scale attacks.
Ethical hacking ppt



Ethical hacking pptNitesh Dubey its contains all the topics which are related to the ethical hacking
its also be cover the penetration testing and describe the difference between ethical hacker and non ethical hackers
Network security



Network securitySimranpreet Singh Network security presentation that briefly covers the aspect of security in networks. The slide consists of procedural steps for network security then some of the important network security components are described. To give it a practical approach, attacks on networks are also covered.
Ethical Hacking



Ethical HackingNitheesh Adithyan This document discusses ethical hacking and penetration testing. It begins by defining ethical hacking as using the same tools and techniques as hackers, but legally in order to test an organization's security. It then covers the history of ethical hacking. The rest of the document outlines the methodology of hacking including reconnaissance, scanning, gaining access, maintaining access, and clearing tracks. It discusses the types of hackers and tools used in ethical hacking. The document concludes by discussing the advantages and disadvantages of ethical hacking.
Vulnerability and Assessment Penetration Testing



Vulnerability and Assessment Penetration TestingYvonne Marambanyika VAPT defines a wide range of security testing services to ascertain and address cyber security exposures. It includes vulnerability testing through perimeter scans for missing patches or custom exploits to bypass perimeters, as well as penetration testing by simulating real-world attacks to provide a point-in-time assessment of vulnerabilities and threats to a network infrastructure. Customers can inquire more about these security testing and analysis services by contacting the company.
Penetration Testing 



Penetration Testing RomSoft SRL Penetration testing is used to test the security of a website by simulating real attacks from outside. It identifies potential vulnerabilities to prevent harmful attacks. By understanding how attacks work, the IT team can fix issues and prevent larger attacks in the future. The presentation will demonstrate a penetration testing tool that checks the login page for security issues like authentication, redirects, and hidden code. Contact information is provided for any additional questions.
Pen Testing Explained



Pen Testing ExplainedRand W. Hirt This document provides an overview of penetration testing, including its definition, purpose, types, methodology, tools, challenges, and takeaways. Penetration testing involves modeling real-world attacks to find vulnerabilities in a system and then attempting to exploit those vulnerabilities to determine security risks. It is important for identifying flaws that need remediation and assessing an organization's security posture and risk profile. The methodology generally involves planning, reconnaissance, scanning, exploitation, and reporting phases. Challenges include performing comprehensive testing within time and budget constraints and addressing business impact.
Computer Security and Intrusion Detection(IDS/IPS)



Computer Security and Intrusion Detection(IDS/IPS)LJ PROJECTS This ppt explain you various type of possible attack, security property, Traffic Analysis, Security mechanism Intrusion detection system, vulnerability, Attack framework etc.
Viewers also liked (20)
Access Controls Attacks



Access Controls AttacksHafiza Abas Logic bombs are malicious codes hidden in software that execute when predefined conditions are met, such as a specific date or time. They can damage systems by deleting files or entirely wiping computers. Spoofing attacks impersonate other devices or users on a network to launch attacks, steal data, or bypass access controls. Types of spoofing include IP address spoofing, ARP spoofing, DNS server spoofing, web spoofing, and email spoofing. Phishing is a form of deception designed to steal personal information like credit card numbers or passwords by tricking users into entering information on fake websites or responding to fraudulent emails.
Detection of Idle Stealth Port Scan Attack in Network Intrusion Detection Sys...



Detection of Idle Stealth Port Scan Attack in Network Intrusion Detection Sys...skpatel91 this is my thesis presentation on Detection of Idle Stealth Port Scan Attack in Network Intrusion Detection System using Snort
CyberLab CCEH Session - 3 Scanning Networks



CyberLab CCEH Session - 3 Scanning NetworksCyberLab This document appears to be the title slide for a presentation on scanning networks. It includes the main title "Title of the Presentation" and subtitle "SUBTITLE OF THE PRESENTATION" as well as information on the session number and topic which is scanning networks. The document also includes a website URL for an organization called CyberLabZone.
Ceh v8 labs module 03 scanning networks



Ceh v8 labs module 03 scanning networksAsep Sopyan Vulnerability scanning evaluates an organization's systems and network to identify vulnerabilities such as missing patches, unnecessary services, weak authentication, and weak encryption. The document discusses using the Advanced IP Scanner tool to perform a network scan on a target Windows Server 2008 system from a Windows 8 attacker system to check for live systems, open ports, and gather information about computers on the local network. It provides instructions on launching Advanced IP Scanner, entering an IP address range to scan, and viewing the scan results.
Chapter 3 footprinting



Chapter 3 footprintingSetia Juli Irzal Ismail This document discusses footprinting and information gathering techniques for network security. It defines footprinting as gathering information about potential target systems and networks. Both attacker and defender perspectives are considered. Basic Linux and Windows tools are covered, such as hostname, ifconfig, who, ping, traceroute, dig, nslookup, whois, arp and netstat for gathering system, network topology and user information. Packet sniffers like Wireshark are also introduced for analyzing network traffic. The document emphasizes that even basic tools can provide a lot of useful information to attackers, so defenders should aim to minimize what they reveal.
Module 2 Foot Printing



Module 2 Foot Printingleminhvuong The document provides an overview of footprinting, which is the first stage of reconnaissance during a cyber attack. It involves gathering open-source information about a target organization to understand its security profile and map its network. Some of the tools mentioned for footprinting include Whois, Nslookup, traceroute, Google Earth and various online databases to find domain information, network details, employee names and more. The goal is to learn as much as possible about the target before launching an actual attack.
Man In The Middle - Hacking Illustrated



Man In The Middle - Hacking IllustratedInfoSec Institute See how man-in-the-middle is performed. Step by step instructions and diagrams showing how this attack works
Basics of pointer, pointer expressions, pointer to pointer and pointer in fun...



Basics of pointer, pointer expressions, pointer to pointer and pointer in fun...Jayanshu Gundaniya Pointers are a data type in C that contain memory addresses as their values. They allow programs to indirectly access and manipulate the data stored at those addresses. Pointers can be used to pass arguments by reference, return values from functions, access array elements, and link data structures like linked lists. Proper initialization of pointers is important to avoid issues like accessing protected memory or going out of array bounds.
Disk scheduling



Disk schedulingAgnas Jasmine Disk scheduling algorithms are used by the operating system to efficiently service requests to read from and write to disk drives. The key components that disk scheduling aims to optimize are seek time, which is the time to move the disk head to the desired cylinder, and rotational latency, which is the additional wait for the desired sector to rotate under the head. Common disk scheduling algorithms include first-come, first-served (FCFS), shortest seek time first (SSTF), SCAN, C-SCAN, and C-LOOK, with SSTF and LOOK often being reasonable default choices.
Debs 2011 tutorial on non functional properties of event processing



Debs 2011 tutorial on non functional properties of event processingOpher Etzion The document discusses various non-functional properties of event processing systems including performance, scalability, availability, usability, and security considerations. It covers topics such as performance benchmarks and indicators, approaches to scaling systems both vertically and horizontally, high availability techniques using redundancy and duplication, usability factors like learnability and satisfaction, and validation methods for ensuring correctness.
Installing Complex Event Processing On Linux



Installing Complex Event Processing On LinuxOsama Mustafa The document is a 14 page guide for installing Oracle Complex Event Processing on Linux written by Osama Mustafa, an Oracle ACE who is a database specialist and certified ethical hacker. It provides background on the author and states that Oracle Event Processing is a solution for building applications that can filter, correlate and process events in real-time using true real-time intelligence. The document provides step-by-step instructions over 14 pages.
Reactconf 2014 - Event Stream Processing



Reactconf 2014 - Event Stream ProcessingAndy Piper Presentation from reactconf 2014 in San Francisco.
Covers Event Stream Processing, some of the theory behind it and some implementation details in the context of local and distributed. Also covers some Big Data technologies
Tutorial in DEBS 2008 - Event Processing Patterns



Tutorial in DEBS 2008 - Event Processing PatternsOpher Etzion 1. The IBM Haifa Research Lab focuses on event processing.
2. It discusses three major building blocks of event processing systems: event producers, an event processing network, and event consumers.
3. The document provides examples of using event processing to detect patterns in customer requests to identify potentially unhappy customers.
Session hijacking



Session hijackingVishal Punjabi This document discusses session hijacking, including the 3-way handshake in TCP, types of session hijacking like predictable tokens and man-in-the-middle attacks, methods for hijacking a session by sniffing packets and predicting sequence numbers, mitigations like HTTPS and VPNs, tools for hijacking sessions including Firesheep, and provides a link to download Firesheep.
Comparative Analysis of Personal Firewalls



Comparative Analysis of Personal FirewallsAndrej Šimko This thesis describes the analysis of 18 personal firewalls. It discovers the differences in their behaviour while they are under various techniques of port scanning and Denial of Service (DoS) attacks. With port scanning, the detection ability, time consumption, leaked port states and obfuscation techniques are analysed. With using different DoS attacks, performance measurements of CPU and network adapter are taken. The potential of firewall fingerprinting based on the different behaviour across multiple products is also addressed.
Access control attacks by nor liyana binti azman



Access control attacks by nor liyana binti azmanHafiza Abas This document discusses different types of access control attacks, including backdoors, spoofing attacks, man-in-the-middle attacks, replays, and TCP hijacking. Backdoors involve bypassing authentication to gain illegal access. Spoofing involves pretending to be someone else to access restricted resources. Man-in-the-middle attacks involve intercepting and relaying messages between victims to make them think they are communicating directly. Replays involve resending valid transmissions to exploit the system. TCP hijacking takes over user sessions by obtaining session IDs. Examples and video links are provided for each type of attack.
Chapter 12



Chapter 12cclay3 The document discusses network security tools in Linux including port scanners, packet sniffers, and intrusion detection systems. Port scanners like Nmap can identify services on a system by probing open ports, while packet sniffers such as Ethereal examine all network traffic. Intrusion detection software watches for intrusion attempts, with PortSentry monitoring for port scans and LIDS securing the system. System administrators can use these tools along with security audits to test vulnerabilities and improve their network security.
Complex Event Processing with Esper and WSO2 ESB



Complex Event Processing with Esper and WSO2 ESBPrabath Siriwardena The document discusses using Esper, an open source complex event processing (CEP) library, with WSO2 ESB. It provides an overview of Esper and how to configure it for use with Axiom and XML event types. The document also includes an example of using an Esper mediator to analyze ticker events and generate new events that are injected back into the ESB for further processing.
Nmap scripting engine



Nmap scripting enginen|u - The Open Security Community This document provides an overview and agenda for a training on the Nmap Scripting Engine (NSE). It begins with a 10 minute introduction to Nmap, covering what Nmap is used for and some basic scan options. Next, it spends 20 minutes reviewing the existing NSE script categories and how to use available scripts, demonstrating two sample scripts. Finally, it dedicates 20 minutes to explaining how to write your own NSE script, including the basic structure and providing an example of writing a script to find the website title.
Ad
Similar to Module 3 Scanning (20)
Scanning



ScanningAshok kumar sandhyala The document discusses various techniques for port scanning, including open scans, stealth scans, SYN scans, FIN scans, XMAS scans, and NULL scans. It describes how these scans work to determine open and closed ports on a remote system. It also introduces Nmap as a powerful port scanning tool that supports many operating systems and scan types.
Port Scanning Overview



Port Scanning OverviewPublicly traded global multi-billion services company Port scanning involves attempting to connect to ports on a target system to discover which ports are open and what services they correspond to. It is done by software that scans a range of ports, usually 0 to 65,536, and analyzes responses to determine whether ports are open, closed, or filtered. Common port scanning tools include Nmap and Netcat. While port scanning can be used maliciously for hacking, it is also used by system administrators to diagnose network issues.
Scanning and Enumeration in Cyber Security.pptx



Scanning and Enumeration in Cyber Security.pptxMahdiHasanSowrav Scanning is the first phase of active hacking used to locate target systems and networks. It involves identifying live hosts, open ports, services, and OS details through techniques like ping sweeps, port scanning, banner grabbing, and vulnerability scanning. Enumeration occurs after scanning and is used to extract additional information like usernames, shares, and services. Specific enumeration techniques discussed include SNMP enumeration, which identifies device information by querying SNMP agents, and NetBIOS enumeration, which extracts Windows account and share details. Hacking tools mentioned that assist with scanning and enumeration include Nmap, SNMPUtil, DumpSec, and Hyena.
Nmap project presentation : Unlocking Network Secrets: Mastering Port Scannin...



Nmap project presentation : Unlocking Network Secrets: Mastering Port Scannin...Boston Institute of Analytics Empower yourself to see what's lurking on your network with our Nmap project presentation! This presentation delves into the world of port scanning with Nmap, the industry-standard tool. Explore how Nmap works, uncover different scanning techniques (SYN scan, UDP scan, etc.), and learn to identify open ports, potential vulnerabilities, and running services. Whether you're a network administrator, security professional, or simply curious about your network traffic, this presentation equips you with the skills to gain valuable insights into your network health. Visit us for more nmap project presentations, https://bostoninstituteofanalytics.org/cyber-security-and-ethical-hacking/
Freeware Security Tools You Need



Freeware Security Tools You Needamiable_indian The document summarizes various free security tools that can be used to gain experience with system and network security. It describes tools for port scanning (Nessus, Saint, Nmap), firewalls (TCP Wrappers, Portsentry), intrusion detection (Snort, Logcheck), and system administration (Sudo, Lsof, Crack). The document recommends using freeware tools to familiarize yourself with security issues before evaluating commercial vendor tools.
Network Vulnerabilities And Cyber Kill Chain Essay



Network Vulnerabilities And Cyber Kill Chain EssayKaren Oliver This document discusses several networking tools, beginning with Wireshark. Wireshark is described as an open-source packet sniffer that allows users to capture and analyze network traffic passing through their computer. It started development in 1998 under the name Ethereal, and was renamed in 2006. The document then moves on to briefly describe Nmap, TCPDump, and Netcat. Nmap is a port scanning tool used for network discovery and security auditing. TCPDump is a command line packet analyzer that prints out network traffic. Netcat is a networking utility that reads and writes data across network connections using TCP or UDP.
Ethical hacking Chapter 6 - Port Scanning - Eric Vanderburg



Ethical hacking Chapter 6 - Port Scanning - Eric VanderburgEric Vanderburg This document discusses port scanning and various tools used for port scanning. It describes what port scanning is, different types of port scans like SYN and ACK scans, and popular port scanning tools like Nmap, Nessus, and Unicornscan. It also covers ping sweeps to identify active hosts and using shell scripting to automate security tasks.
Network Security Nmap N Nessus



Network Security Nmap N NessusUtkarsh Verma This document summarizes different types of network scans that can be performed using Nmap, including TCP connect scans, SYN scans, FIN scans, Xmas scans, Null scans, and least traffic scans. It also discusses why vulnerability scanning is important and compares the features of the free Nessus Home Feed versus the paid Professional Feed for vulnerability scanning. The Professional Feed provides more frequent plugin updates, policy compliance checks, unlimited PCI audits, operating system audits, and technical support compared to the free Home Feed.
01204427-scanner.ppt



01204427-scanner.pptVarunBehere1 IP network scanning involves gathering information about devices on a network such as which hosts are active and which services and ports are open. The document discusses common scanning techniques including ping sweeps to discover active hosts, port scanning to identify open ports, and methods for detecting operating systems and software versions running on remote hosts. It provides examples using the free and open-source nmap tool, which is considered the standard for port scanning and network discovery.
Port Scanning



Port Scanningamiable_indian Port scanning involves sending packets to ports on a target system to discover which ports are open and may be exploited. There are several common port scanning techniques like TCP connect scanning, SYN scanning, FIN scanning, and UDP scanning. Port scanners try to avoid detection by scanning slowly, spoofing packets, or fragmenting packets. Systems can detect port scans through signatures like many connections to different ports from the same source in a short time.
Chapter_Five[1].ppt![Chapter_Five[1].ppt](https://cdn.slidesharecdn.com/ss_thumbnails/chapterfive1-230626115846-43722011-thumbnail.jpg?width=560&fit=bounds)
![Chapter_Five[1].ppt](https://cdn.slidesharecdn.com/ss_thumbnails/chapterfive1-230626115846-43722011-thumbnail.jpg?width=560&fit=bounds)
![Chapter_Five[1].ppt](https://cdn.slidesharecdn.com/ss_thumbnails/chapterfive1-230626115846-43722011-thumbnail.jpg?width=560&fit=bounds)
![Chapter_Five[1].ppt](https://cdn.slidesharecdn.com/ss_thumbnails/chapterfive1-230626115846-43722011-thumbnail.jpg?width=560&fit=bounds)
Chapter_Five[1].pptBachaSirata The document discusses various security mechanisms and techniques including firewalls, proxy servers, and intrusion detection systems (IDS). It provides details on how firewalls, proxy servers, and IDS work to enhance network security. Firewalls can be hardware-based or software-based and inspect packets to determine if they should be allowed through or blocked. Proxy servers act as intermediaries and filter or block traffic based on rules. IDS monitors network traffic and system activities to detect intrusions and security breaches.
A Survey on different Port Scanning Methods and the Tools used to perform the...



A Survey on different Port Scanning Methods and the Tools used to perform the...Naomi Hansen This document summarizes different port scanning methods and tools used to perform them. It describes non-stealth scanning (TCP connect), inverse mapping scanning, slow scanning, SYN scanning, FIN scanning, Xmas tree scanning, null scanning, UDP scanning, and idle scanning. For each method, it provides details on how the method works, advantages/disadvantages, and example tools that can be used to implement the scanning method. The document is intended to inform readers about various port scanning techniques and their characteristics.
Week 10 - Packet Sssdssssssssniffers.ppt



Week 10 - Packet Sssdssssssssniffers.pptfzbshf qwd,poqkewvnnnnnnnnnnnjiNFIJFENNNNNNNNVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVV:OOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOEeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeefuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuusssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssss
For your final step, you will synthesize the previous steps and la



For your final step, you will synthesize the previous steps and laShainaBoling829 For your final step, you will synthesize the previous steps and labs to summarize the major findings from this project.
Specifically, you will prepare a technical report that summarizes your findings including:
1. Provide a table of common ports for protocols we studied. Discuss how security devices can be used to within a larger network to control subnets and devices within those subnets.
2. Discuss network diagnostic tools you used in this lab. Summarize their functionality and describe specifically how you used each tool. Discuss the results you used to assist in both the discovery phase and protocol analysis of the sites you analyzed. What tools impressed you the most and would be most useful for an analyst to employ in the daily activities? What other functionality do you think would be useful to cyber operations analysts?
3. Research and discuss the ethical use of these tools. For example, if you discover a serious vulnerability, what you should you do? What communications should you have with site owners prior to conducting vulnerability scans?
The report should include a title page, table of contents, list of tables and figures (as applicable), content organized into sections. Be sure to properly cite your sources throughout, and include a list of references, formatted in accordance with APA style.
Final Technical Report
31 January 2022
Llyjerylmye Amos
COP 620 Project 1 Final Technical Report
Well-known ports range from 0 to 1023, and are assigned by Internet Assigned Numbers Authority
(IANA) base on the default services that are associated with the assigned ports. Administrators may
obfuscate services that are running on well-known ports by configuring services to be utilized on unused
ephemeral ports. However, the default configuration of well-known ports allow tech savvy personnel
and software vendors to speak a common language when configuring networking devices, information
systems (IS)s and or software applications. Within this lesson, 22-SSH, 23- Telnet, 25-SMTP, 53-DNS, 80-
HTTP, 110-POP3 and 443-HTTPS were the common ports and protocols that were reviewed, table 1.
Port Protocol
22 SSH
23 Telnet
25 SMTP
53 DNS
80 HTTP
110 POP3
443 HTTPS
Table 1. Common ports studies.
Firewalls are the most common network security devices installed on information systems (IS).
According to Cisco (n.d.), “a firewall is a network security device that monitors incoming and outgoing
network traffic and decides whether to allow or block specific traffic based on a defined set of security
rules”. Security rules may be applied to specific ISs, host-based firewalls, or to the entire network,
network-based firewalls to scan emails, hard drives for malware or to allow traffic on certain sections of
the subnet. Firewalls are also categorized into specific type such as, proxy firewalls, stateful inspection
firewalls, unified threat management firewalls, next-generation firewalls (NGFW), ...
Contents namp



Contents nampshwetha mk 1. To perform active OS fingerprinting, use Nmap's "-O" flag followed by the target IP address. This sends probe packets to the target and analyzes the responses to determine the operating system.
2. For passive fingerprinting, sniff the network traffic without making contact with targets. Analyze characteristics like TCP/IP stack implementation to fingerprint operating systems.
3. Nmap is a useful tool for active fingerprinting as it has a large database of OS fingerprints. Passive fingerprinting can be done using a network sniffer without alerting targets. Both methods provide ways to remotely determine operating systems without access to
Contents namp



Contents nampshwetha mk This document is a presentation report submitted by four students at M. S. Ramaiah Institute of Technology for their 5th semester Data Communication course. It discusses the network scanning tool Nmap, describing its features for host discovery, port scanning, OS detection and more. It then provides details of performing a port scanning experiment with Nmap, explaining the different port states Nmap can detect and demonstrating TCP and UDP scan types.
Node finder presentation



Node finder presentationVarun Varshney Node Finding and Port scanning Utility for Android.
by:
Varun Varshney - 9910103491
Prabhat Goyal - 9910103582
Dept. of CSE
JIIT 128
Major Project 2013 - 2014
Nmap project presentation : Unlocking Network Secrets: Mastering Port Scannin...



Nmap project presentation : Unlocking Network Secrets: Mastering Port Scannin...Boston Institute of Analytics
Ad
More from leminhvuong (20)
Proxy



Proxyleminhvuong This document provides instructions for installing and configuring the Squid proxy server on Linux. It discusses system requirements for disk performance and memory. It also covers downloading and installing Squid, important configuration notes, starting and stopping Squid, log files, configuring cache disks and directories, access control lists, authentication, and examples of restricting web access by time and to specific websites.
Lession2 Xinetd



Lession2 Xinetdleminhvuong TCP wrappers and xinetd provide additional security layers for network services by controlling access at the application level. TCP wrappers work by checking the hosts.allow and hosts.deny files to determine if a client is allowed to connect to a wrapped service like sshd or xinetd. Xinetd is a super server that controls access and starts services like Telnet. It uses configuration files in /etc/xinetd.d to define access rules and settings for each managed service.
Iptables



Iptablesleminhvuong The document discusses Linux iptables firewall. Iptables is the default firewall package for Linux and runs inside the Linux kernel. It has three built-in tables (filter, nat, mangle) that are used to filter, alter, and inspect packets. Iptables uses built-in chains and user-defined rules to allow or deny traffic based on packet criteria like source/destination, protocol, interface etc. Common iptables commands and options are also explained.
Lession1 Linux Preview



Lession1 Linux Previewleminhvuong The document discusses Linux file systems and permissions. It describes the Virtual File System (VFS) interface and how it interacts with filesystems, inodes, and open files. It then discusses the EXT2 filesystem in more detail, describing how inodes store file metadata and how hard and soft links work. It also covers common Linux permissions and how to manage users, groups, and permissions using commands like chmod, chown, useradd, and others.
Http



Httpleminhvuong The document discusses configuration of the Apache HTTP server. It describes how to start, stop and restart the server using the /sbin/service command. It explains how to configure the server by editing the main configuration file httpd.conf located at /etc/httpd/conf/httpd.conf. The document also discusses setting the default document root directory for web pages, setting file permissions, and describes several important configuration directives that can be set in the httpd.conf file to configure the server's listening ports, directories, users and other settings.
Dns



Dnsleminhvuong The document discusses the Domain Name System (DNS) and how it works. It explains that DNS associates domain names with IP addresses, allowing hosts to connect using names instead of hard-to-remember numbers. DNS uses a hierarchical system of servers, including root servers, TLD servers, and authoritative name servers that manage domain records and refer queries to other servers as needed to resolve domain names to IP addresses.
Net Admin Intro



Net Admin Introleminhvuong This document outlines a network administration course taught by Pham Van Tinh, consisting of 30 hours of theory and 60 hours of practice. The course covers topics such as Linux, shell scripts, routing, DHCP, DNS, file transfer protocols, remote access, web servers, email, firewalls, backups and more. Students will use Red Hat Linux manuals, exam guides, and Microsoft certification guides as literature.
Lession4 Dhcp



Lession4 Dhcpleminhvuong DHCP is a protocol that automatically assigns IP addresses and other network configuration settings to clients. It allows administrators to change network settings centrally on the DHCP server rather than having to configure each client individually. The DHCP server stores lease information in /var/lib/dhcp/dhcpd.leases and is configured using /etc/dhcpd.conf which defines IP pools, default routes, DNS servers and other options. The DHCP relay agent forwards requests from clients without a local DHCP server to servers on other subnets.
Lession3 Routing



Lession3 Routingleminhvuong This document summarizes basic Linux routing concepts including enabling IP forwarding, configuring routing tables, displaying routing and ARP tables, and examples of routing rules. Key points are:
1) IP forwarding can be enabled by editing /etc/sysctl.conf or /proc/sys/net/ipv4/ip_forward.
2) The routing table contains rules with destination, interface, and optional gateway to route packets.
3) Example commands demonstrate adding routing rules for different networks through specific interfaces.
Module 1 Introduction



Module 1 Introductionleminhvuong Phase 1 involves reconnaissance where the hacker gathers information about the target without directly interacting with it. Phase 2 is scanning where the hacker scans the network to find specific information like open ports and operating systems. Phase 3 is gaining access where the hacker exploits a vulnerability to penetrate the system. Phase 4 is maintaining access where the hacker tries to retain ownership and may install backdoors. Phase 5 is covering tracks where the hacker hides evidence of the attack.
Net Security Intro



Net Security Introleminhvuong The document outlines a 15-module network security course taught by Phạm Văn Tính, PhD. The course covers ethical hacking theory over 45 hours and practice over 30 hours. Topics include footprinting, scanning, enumeration, system hacking, trojans, sniffers, denial of service attacks, social engineering, session hijacking, hacking web servers, SQL injection, wireless hacking, Linux hacking, and evading intrusion detection systems. The course material is based on CEH curriculums and references four literature sources on ethical hacking, Linux/Unix security, network security secrets and solutions, and web security.
Module 10 Physical Security



Module 10 Physical Securityleminhvuong Physical security involves preventing unauthorized access to computer systems and protecting data. It includes securing the company surroundings with fences, gates, and guards. Within premises, CCTV cameras, intruder alarms, and window/door bars provide security. Servers should be locked in enclosed rooms, and workstations in open areas need locks and CCTV monitoring. Access controls like smart cards, biometrics, and entry logs restrict access to sensitive areas. Wireless networks and other equipment also require security measures like encryption and locked storage to protect physical integrity of systems and data.
Module 9 Dos



Module 9 Dosleminhvuong The document discusses denial of service (DoS) and distributed denial of service (DDoS) attacks. It defines DoS and DDoS attacks, describes different types of DoS attacks like SYN flooding and Smurf attacks. It also explains how botnets and tools are used to launch DDoS attacks, and discusses some common DDoS countermeasures like detection, mitigation and traceback.
Module 8 System Hacking



Module 8 System Hackingleminhvuong The document discusses various techniques for hacking systems, including password cracking, privilege escalation, executing applications remotely, and using keyloggers and spyware. It provides an overview of tools that can perform functions like password cracking, sniffing network traffic, capturing credentials, escalating privileges, executing code remotely, and logging keystrokes covertly. Countermeasures to these techniques, like disabling LM hashes, changing passwords regularly, and using antivirus software, are also covered.
Module 6 Session Hijacking



Module 6 Session Hijackingleminhvuong Session hijacking involves an attacker taking over an existing TCP connection between two machines by predicting sequence numbers and spoofing IP addresses. The document discusses the difference between spoofing and hijacking, the steps an attacker takes to hijack a session including predicting sequence numbers and killing the original connection, types of session hijacking techniques, and tools that can be used for session hijacking like Juggernaut, Hunt, IP Watcher, and T-Sight. It also provides countermeasures like using encryption, secure protocols, limiting connections, and educating employees.
Module 5 Sniffers



Module 5 Sniffersleminhvuong This document provides an overview of network sniffing including definitions, vulnerable protocols, types of sniffing attacks, tools used for sniffing, and countermeasures. It discusses passive and active sniffing, ARP spoofing, MAC flooding, DNS poisoning techniques, and popular sniffing tools like Wireshark, Arpspoof, and Dsniff. It also outlines methods for detecting sniffing activity on a network such as monitoring for changed MAC addresses and unusual packets, as well as recommendations for implementing countermeasures like encryption, static ARP tables, port security, and intrusion detection systems.
Module 4 Enumeration



Module 4 Enumerationleminhvuong The document discusses techniques for enumerating information from systems during the hacking process. It describes establishing null sessions to extract user names, shares, and other details without authentication. Tools like DumpSec, Netview, Nbtstat, GetAcct, and PS Tools are also covered as ways to enumerate users, groups, shares, permissions, and more from Windows and UNIX systems. The document also provides countermeasures like restricting null sessions and the anonymous user to protect against enumeration attacks.
Call Back



Call Backleminhvuong The document discusses using remote method invocation (RMI) in Java to implement callbacks. It describes defining a listener interface that other classes can implement to be notified of events. An event source interface is defined to allow listeners to register and receive notifications. The event source is implemented as an RMI server that notifies all registered listeners when temperature changes. A client implements the listener interface and registers with the server to receive remote callbacks of temperature changes.
Recently uploaded (20)
Rusty Waters: Elevating Lakehouses Beyond Spark



Rusty Waters: Elevating Lakehouses Beyond Sparkcarlyakerly1 Spark is a powerhouse for large datasets, but when it comes to smaller data workloads, its overhead can sometimes slow things down. What if you could achieve high performance and efficiency without the need for Spark?
At S&P Global Commodity Insights, having a complete view of global energy and commodities markets enables customers to make data-driven decisions with confidence and create long-term, sustainable value. 🌍
Explore delta-rs + CDC and how these open-source innovations power lightweight, high-performance data applications beyond Spark! 🚀
Role of Data Annotation Services in AI-Powered Manufacturing



Role of Data Annotation Services in AI-Powered ManufacturingAndrew Leo From predictive maintenance to robotic automation, AI is driving the future of manufacturing. But without high-quality annotated data, even the smartest models fall short.
Discover how data annotation services are powering accuracy, safety, and efficiency in AI-driven manufacturing systems.
Precision in data labeling = Precision on the production floor.
TrustArc Webinar: Consumer Expectations vs Corporate Realities on Data Broker...



TrustArc Webinar: Consumer Expectations vs Corporate Realities on Data Broker...TrustArc Most consumers believe they’re making informed decisions about their personal data—adjusting privacy settings, blocking trackers, and opting out where they can. However, our new research reveals that while awareness is high, taking meaningful action is still lacking. On the corporate side, many organizations report strong policies for managing third-party data and consumer consent yet fall short when it comes to consistency, accountability and transparency.
This session will explore the research findings from TrustArc’s Privacy Pulse Survey, examining consumer attitudes toward personal data collection and practical suggestions for corporate practices around purchasing third-party data.
Attendees will learn:
- Consumer awareness around data brokers and what consumers are doing to limit data collection
- How businesses assess third-party vendors and their consent management operations
- Where business preparedness needs improvement
- What these trends mean for the future of privacy governance and public trust
This discussion is essential for privacy, risk, and compliance professionals who want to ground their strategies in current data and prepare for what’s next in the privacy landscape.
Network Security. Different aspects of Network Security.



Network Security. Different aspects of Network Security.gregtap1 Network Security. Different aspects of Network Security.
Buckeye Dreamin 2024: Assessing and Resolving Technical Debt



Buckeye Dreamin 2024: Assessing and Resolving Technical DebtLynda Kane Slide Deck from Buckeye Dreamin' 2024 presentation Assessing and Resolving Technical Debt. Focused on identifying technical debt in Salesforce and working towards resolving it.
"Client Partnership — the Path to Exponential Growth for Companies Sized 50-5...



"Client Partnership — the Path to Exponential Growth for Companies Sized 50-5...Fwdays Why the "more leads, more sales" approach is not a silver bullet for a company.
Common symptoms of an ineffective Client Partnership (CP).
Key reasons why CP fails.
Step-by-step roadmap for building this function (processes, roles, metrics).
Business outcomes of CP implementation based on examples of companies sized 50-500.
Procurement Insights Cost To Value Guide.pptx



Procurement Insights Cost To Value Guide.pptxJon Hansen Procurement Insights integrated Historic Procurement Industry Archives, serves as a powerful complement — not a competitor — to other procurement industry firms. It fills critical gaps in depth, agility, and contextual insight that most traditional analyst and association models overlook.
Learn more about this value- driven proprietary service offering here.
AI Changes Everything – Talk at Cardiff Metropolitan University, 29th April 2...



AI Changes Everything – Talk at Cardiff Metropolitan University, 29th April 2...Alan Dix Talk at the final event of Data Fusion Dynamics: A Collaborative UK-Saudi Initiative in Cybersecurity and Artificial Intelligence funded by the British Council UK-Saudi Challenge Fund 2024, Cardiff Metropolitan University, 29th April 2025
https://alandix.com/academic/talks/CMet2025-AI-Changes-Everything/
Is AI just another technology, or does it fundamentally change the way we live and think?
Every technology has a direct impact with micro-ethical consequences, some good, some bad. However more profound are the ways in which some technologies reshape the very fabric of society with macro-ethical impacts. The invention of the stirrup revolutionised mounted combat, but as a side effect gave rise to the feudal system, which still shapes politics today. The internal combustion engine offers personal freedom and creates pollution, but has also transformed the nature of urban planning and international trade. When we look at AI the micro-ethical issues, such as bias, are most obvious, but the macro-ethical challenges may be greater.
At a micro-ethical level AI has the potential to deepen social, ethnic and gender bias, issues I have warned about since the early 1990s! It is also being used increasingly on the battlefield. However, it also offers amazing opportunities in health and educations, as the recent Nobel prizes for the developers of AlphaFold illustrate. More radically, the need to encode ethics acts as a mirror to surface essential ethical problems and conflicts.
At the macro-ethical level, by the early 2000s digital technology had already begun to undermine sovereignty (e.g. gambling), market economics (through network effects and emergent monopolies), and the very meaning of money. Modern AI is the child of big data, big computation and ultimately big business, intensifying the inherent tendency of digital technology to concentrate power. AI is already unravelling the fundamentals of the social, political and economic world around us, but this is a world that needs radical reimagining to overcome the global environmental and human challenges that confront us. Our challenge is whether to let the threads fall as they may, or to use them to weave a better future.
Special Meetup Edition - TDX Bengaluru Meetup #52.pptx



Special Meetup Edition - TDX Bengaluru Meetup #52.pptxshyamraj55 We’re bringing the TDX energy to our community with 2 power-packed sessions:
🛠️ Workshop: MuleSoft for Agentforce
Explore the new version of our hands-on workshop featuring the latest Topic Center and API Catalog updates.
📄 Talk: Power Up Document Processing
Dive into smart automation with MuleSoft IDP, NLP, and Einstein AI for intelligent document workflows.
"Rebranding for Growth", Anna Velykoivanenko



"Rebranding for Growth", Anna VelykoivanenkoFwdays Since there is no single formula for rebranding, this presentation will explore best practices for aligning business strategy and communication to achieve business goals.
Rock, Paper, Scissors: An Apex Map Learning Journey



Rock, Paper, Scissors: An Apex Map Learning JourneyLynda Kane Slide Deck from Presentations to WITDevs (April 2021) and Cleveland Developer Group (6/28/2023) on using Rock, Paper, Scissors to learn the Map construct in Salesforce Apex development.
Automation Dreamin' 2022: Sharing Some Gratitude with Your Users



Automation Dreamin' 2022: Sharing Some Gratitude with Your UsersLynda Kane Slide Deck from Automation Dreamin'2022 presentation Sharing Some Gratitude with Your Users on creating a Flow to present a random statement of Gratitude to a User in Salesforce.
The Evolution of Meme Coins A New Era for Digital Currency ppt.pdf



The Evolution of Meme Coins A New Era for Digital Currency ppt.pdfAbi john Analyze the growth of meme coins from mere online jokes to potential assets in the digital economy. Explore the community, culture, and utility as they elevate themselves to a new era in cryptocurrency.
AI and Data Privacy in 2025: Global Trends



AI and Data Privacy in 2025: Global TrendsInData Labs In this infographic, we explore how businesses can implement effective governance frameworks to address AI data privacy. Understanding it is crucial for developing effective strategies that ensure compliance, safeguard customer trust, and leverage AI responsibly. Equip yourself with insights that can drive informed decision-making and position your organization for success in the future of data privacy.
This infographic contains:
-AI and data privacy: Key findings
-Statistics on AI data privacy in the today’s world
-Tips on how to overcome data privacy challenges
-Benefits of AI data security investments.
Keep up-to-date on how AI is reshaping privacy standards and what this entails for both individuals and organizations.
Big Data Analytics Quick Research Guide by Arthur Morgan



Big Data Analytics Quick Research Guide by Arthur MorganArthur Morgan This is a Quick Research Guide (QRG).
QRGs include the following:
- A brief, high-level overview of the QRG topic.
- A milestone timeline for the QRG topic.
- Links to various free online resource materials to provide a deeper dive into the QRG topic.
- Conclusion and a recommendation for at least two books available in the SJPL system on the QRG topic.
QRGs planned for the series:
- Artificial Intelligence QRG
- Quantum Computing QRG
- Big Data Analytics QRG
- Spacecraft Guidance, Navigation & Control QRG (coming 2026)
- UK Home Computing & The Birth of ARM QRG (coming 2027)
Any questions or comments?
- Please contact Arthur Morgan at [email protected].
100% human made.
UiPath Community Berlin: Orchestrator API, Swagger, and Test Manager API



UiPath Community Berlin: Orchestrator API, Swagger, and Test Manager APIUiPathCommunity Join this UiPath Community Berlin meetup to explore the Orchestrator API, Swagger interface, and the Test Manager API. Learn how to leverage these tools to streamline automation, enhance testing, and integrate more efficiently with UiPath. Perfect for developers, testers, and automation enthusiasts!
📕 Agenda
Welcome & Introductions
Orchestrator API Overview
Exploring the Swagger Interface
Test Manager API Highlights
Streamlining Automation & Testing with APIs (Demo)
Q&A and Open Discussion
Perfect for developers, testers, and automation enthusiasts!
👉 Join our UiPath Community Berlin chapter: https://community.uipath.com/berlin/
This session streamed live on April 29, 2025, 18:00 CET.
Check out all our upcoming UiPath Community sessions at https://community.uipath.com/events/.
AI EngineHost Review: Revolutionary USA Datacenter-Based Hosting with NVIDIA ...



AI EngineHost Review: Revolutionary USA Datacenter-Based Hosting with NVIDIA ...SOFTTECHHUB I started my online journey with several hosting services before stumbling upon Ai EngineHost. At first, the idea of paying one fee and getting lifetime access seemed too good to pass up. The platform is built on reliable US-based servers, ensuring your projects run at high speeds and remain safe. Let me take you step by step through its benefits and features as I explain why this hosting solution is a perfect fit for digital entrepreneurs.
Module 3 Scanning
- 2. Objective Definition of scanning Types and objectives of Scanning Understanding CEH Scanning methodology Checking live systems and open ports Understanding scanning techniques Different tools present to perform Scanning Understanding banner grabbing and OS fingerprinting Drawing network diagrams of vulnerable hosts Preparing proxies Understanding anonymizers Scanning countermeasures
- 3. One of the three components of intelligence gathering for an attacker The attacker finds information about the specific IP addresses Operating Systems system architecture services running on each computer The various types of scanning are as follows : Port Scanning Network Scanning Vulnerability Scanning Scanning - Definition
- 4. Types of Scanning Port Scanning A series of messages sent by someone attempting to break into a computer to learn about the computer’snetwork services Each associated with a "well-known" port number Network Scanning A procedure for identifying active hosts on a network Either for the purpose of attacking them or for network security assessment Vulnerability Scanning The automated process of proactively identifying vulnerabilities of computing systems present in a network
- 5. Objectives of Scanning To detect the live systems running on the network To discover which ports are active/running To discover the operating system running on the target system ( fingerprinting ) To discover the services running/listening on the target system To discover the IP address of the target system
- 6. Checking for Live Systems – ICMP Scanning Ping send out an ICMP Echo Request packet and awaits an ICMP Echo Reply message from an active machine. Alternatively, TCP/UDP packets are sent if incoming ICMP messages are blocked. Ping helps in assessing network traffic by time stamping each packet. Ping can also be used for resolving host names. Tools include Pinger, WS_Ping ProPack, NetScan Tools, HPing, icmpenum
- 7. Checking for open ports Port Scanning is one of the most popular reconnaissance techniques used by hackers to discover services that can be compromised. A potential target computer runs many 'services' that listen at ‘well-known’ 'ports'. By scanning which ports are available on the victim, the hacker finds potential vulnerabilities that can be exploited.
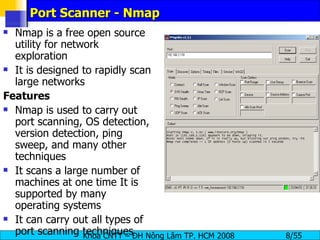
- 8. Port Scanner - Nmap Nmap is a free open source utility for network exploration It is designed to rapidly scan large networks Features Nmap is used to carry out port scanning, OS detection, version detection, ping sweep, and many other techniques It scans a large number of machines at one time It is supported by many operating systems It can carry out all types of port scanning techniques
- 10. TCP Communication Flags Standard TCP communications are controlled by flags in the TCP packet header The flags are as follows: Synchronize - also called "SYN” – Used to initiate a connection between hosts Acknowledgement - also called "ACK” – Used in establishing a connection between hosts Push - "PSH” – Instructs receiving system to send all buffered data immediately Urgent - "URG” – States that the data contained in the packet should be processed immediately Finish - also called "FIN" – Tells remote system that there will be no more transmissions Reset - also called "RST” – Also used to reset a connection
- 12. SYN Stealth / Half Open Scan It is often referred to as half open scan because it does not open a full TCP connection First a SYN packet is sent to a port of the machine, suggesting a request for connection, and the response is awaited If the port sends back a SYN/ACK packet, then it is inferred that a service at the particular port is listening. If an RST is received, then the port is not active/ listening. As soon as the SYN/ACK packet is received, an RST packet is sent, instead of an ACK, to tear down the connection The key advantage is that fewer sites log this scan
- 13. Stealth Scan Client sends a single SYN packet to the server on the appropriate port If the port is open then the server responds with a SYN/ACK packet If the server responds with an RST packet, then the remote port is in "closed” state The client sends RST packet to close the initiation before a connection can ever be established This scan also known as “half-open” scan
- 14. Xmas Scan
- 15. FIN Scan
- 16. NULL Scan
- 17. IDLE Scan
- 18. IDLE Scan: Basics Most network servers listen on TCP ports, such as web servers on port 80 and mail servers on port 25 A port is considered "open" if an application is listening on the port, otherwise it is closed One way to determine whether a port is open is to send a "SYN" (session establishment) packet to the port The target machine will send back a "SYN|ACK" (session request acknowledgment) packet if the port is open, and an "RST" (Reset) packet if the port is closed A machine which receives an unsolicited SYN|ACK packet will respond with an RST. An unsolicited RST will be ignored Every IP packet on the Internet has a "fragment identification" number Many operating systems simply increment this number for every packet they send So probing for this number can tell an attacker how many packets have been sent since the last probe
- 19. IDLE Scan: Step 1
- 20. IDLE Scan: Step 2.1 (Open Port)
- 21. IDLE Scan: Step 2.2 (Closed Port)
- 22. IDLE Scan: Step 3
- 23. ICMP Echo Scanning/List Scan ICMP echo scanning This isn't really port scanning, since ICMP doesn't have a port abstraction But it is sometimes useful to determine which hosts in a network are up by pinging them all nmap -P cert.org/24 152.148.0.0/16 List Scan This type of scan simply generates and prints a list of IPs/Names without actually pinging or port scanning them A DNS name resolution will also be carried out
- 24. TCP Connect / Full Open Scan
- 25. NMAP Scan Options Output options
- 28. IPScanner
- 29. FloppyScan
- 30. FloppyScan Steps
- 32. SAINT
- 34. Nessus Nessus is a vulnerability scanner , which looks for bugs in software An attacker can use this tool to violate the security aspects of a software product Features Plug-in-architecture NASL (Nessus Attack Scripting Language) Can test unlimited number of hosts simultaneously Smart service recognition Client-server architecture Smart plug-ins Up-to-date security vulnerability database
- 35. GFI LANGuard GFI LANGUARD analyzes the operating system and the applications running on a network and finds out the security holes present It scans the entire network, IP by IP, and provides information such as the service pack level of the machine and missing security patches, to name a few GFI LANGuard Features Fast TCP and UDP port scanning and identification Finds all the shares on the target network It alerts the pinpoint security issues Automatically detects new security holes Checks password policy Finds out all the services that are running on the target network Vulnerabilities database includes UNIX/CGI issues
- 37. Draw Network Diagrams of Vulnerable Hosts
- 38. Cheops
- 39. FriendlyPinger
- 41. Proxy Servers Proxy is a network computer that can serve as an intermediate for connection with other computers They are usually used for the following purposes: As a firewall, a proxy protects the local network from outside access As an IP addresses multiplexer, a proxy allows the connection of a number of computers to the Internet when having only one IP address Proxy servers can be used (to some extent) to anonymize web surfing Specialized proxy servers can filter out unwanted content, such as ads or 'unsuitable' material Proxy servers can afford some protection against hacking attacks
- 43. Use of Proxies for Attack
- 45. Happy Browser Tool (Proxy-based)
- 46. MultiProxy
- 47. How Does MultiProxy Work?
- 48. Anonymizers
- 50. Some anonymizer sites Many anonymizer sites create an anonymized URL by appending the name of the site the user wishes to access to their own URL, e.g.: http://anon.free.anonymizer.com/http://www.yahoo.com/ Anonymizer.com Anonymize.net @nonymouse.com Iprive.com MagusNet Public Proxy MuteMail.com PublicProxyServers.com Rewebber.de SilentSurf.com Surfola.com Ultimate-anonymity.com
- 51. Anonymizers’ limitations HTTPS. Secure protocols like "https:" cannot be properly anonymized, since the browser needs to access the site directly to properly maintain the secure encryption. Plugins. If an accessed site invokes a third-party plugin, then there is no guarantee that they will not establish independent direct connections from the user computer to a remote site. Logs. All anonymizer sites claim that they don't keep a log of requests. Some sites, such as the Anonymizer, keep a log of the addresses accessed, but don't keep a log of the connection between accessed addresses and users logged in. Java. Any Java application that is accessed through an anonymizer will not be able to bypass the Java security wall. Active X. Active-X applications have almost unlimited access to the user's computer system. JavaScript. The JavaScript scripting language is disabled with url-based anonymizers
- 53. Why Do I Need HTTP Tunneling? Let’s say your organization has blocked all the ports in your firewall and only allows port 80/443 and you want to use FTP to connect to some remote server on the Internet In this case you can send your packets via http protocol
- 54. Httptunnel for Windows httptunnel creates a bidirectional virtual data connection tunnelled in HTTP requests. The HTTP requests can be sent via an HTTP proxy if so desired This can be useful for users behind restrictive firewalls If WWW access is allowed through an HTTP proxy, it's possible to use httptunnel and, say, telnet or PPP to connect to a computer outside the firewall On the server you must run hts. If I wanted to have port 80 (http) redirect all traffic to port 23 (telnet) then it would go something like: hts -F server.test.com:23 80 On the client you would run htc. If you are going through a proxy, the -P option is needed otherwise omit it. htc -P proxy.corp.com:80 -F 23 server.test.com:80 Then telnet localhost and it will redirect the traffic out to port 80 on the proxy server and on to port 80 of the server, then to port 23.
- 55. How to Run Httptunnel?








