Ad
Network emulator
- 1. Network Emulation using tc Jeromy Fu
- 2. Agenda • Why emulation • What to be emulated • How TC works • Emulation Howto • Compared with Nistnet/WANem • Other references
- 3. Mathematic model • Mathematic model analysis can provide import insight on the behavior of a system • But, sometimes difficult because of too many factors combined
- 4. Network simulator • Network simulator is a software program that imitates the working of a computer network • fast and inexpensive • controlled and reproducible environment
- 5. Network emulator • A network emulator emulates the network which connects end-systems, not the end- systems themselves • transmit actual network traffic • Can use real code
- 6. Real world test • Impractical experiments • Planet Lab helps • not reproducible
- 7. Why emulator • Complementary More uncontrolled Trade off Risk Occurrence Likelihood of More reality Consequence of Risk Occurrence
- 8. Agenda • Why emulation • What to be emulated • How TC works • Emulation Howto • Compared with Nistnet/WANem • Other references
- 9. What to be emulated • Bandwidth. • Shaped(Policed) bandwidth more specifically. • Capacity can’t be emulated.
- 10. What to be emulated • RTT • Jitter • Queuing delay
- 11. What to be emulated • Duplicate/Disorder/Corrupt • Lossrate • Loss burstiness, a longest sequence beginning and ending with a loss, consecutive received packets is less than some value Gmin
- 12. Agenda • Why emulation • What to be emulated • How TC works • Emulation Howto • Compared with Nistnet/WANem • Other references
- 13. What is TC • TC is abbr. of Traffic Control - Rate control - Bandwidth management - Active Queue Management(AQM) - Network Emulator, pkt loss, pkt disorder, pkt duplication, pkt delay - QoS ( diffserv + rsvp ) - Many more …
- 14. How TC works
- 15. How TC works
- 16. TC basic concepts • Classification(Filter) - Used to distinguish among different classes of packets and process each class in a specific way. • Qdisc(Queue discipline) - Decide which ones to send first, which ones to delay, and which ones to drop - class/classful Qdisc: Qdisc with/without configurable internal subdivision
- 17. TC basic concepts • Class Classes either contain other Classes, or a Qdisc is attached Qdiscs and Classes are intimately tied together • Action Actions get attached to classifiers and are invoked after a successful classification. Common used actions includes instantly drop, modify or redirect packets, etc. Works on ingress only.
- 19. TC Commands • OPTIONS: options are effective for all sub commands • OBJECTS: the object of the tc command operates on • COMMAND: the sub command for each object
- 20. TC Qdisc • Operations on qdisc: add | del | replace | change | show • Handle: qdisc handle used to identify qdisc • root|ingress|parent CLASSID(handle), specify the parent node
- 21. qdisc handle • Qdisc handle is used to identify Qdisc - {none|major[:]} - none, autogen by kernel - major is 16bits HEX number(Without ‘0x’ prefix) - : is optional • Internally, qdisc_handle = major<<16
- 22. TC class • Class’s parent can be class or qdisc, classid should have the same major with parent • classid, {[major]:minor} - major/minor are both 16bits HEX numbers(Without ‘0x’ prefix), major is optional • Internally, classid = (major<<16)|minor
- 23. TC filter • Perf(prio): priority of matching. • Protocol: protocol on which the filter must operate, ip/icmp etc, see /etc/protocols. • root|classid CLASSID|handle FILTERID, specify the class or qdisc attached.
- 26. Agenda • Why emulation • What to be emulated • How TC works • Emulation Howto • Compared with Nistnet/WANem • Other references
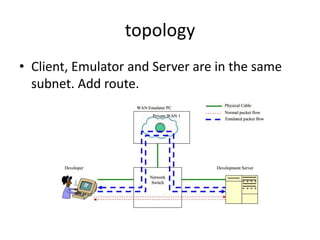
- 27. topology • Client, Emulator and Server are in the same subnet. Add route.
- 28. topology • Client, Emulator in one subnet, server in another subnet. Use NAT.
- 29. tc-tbf • Tokens are added at a fixed rate • Check if the bucket contains sufficient tokens
- 30. Bernoulli loss model • Model uncorrelated loss events, “loss probability” p. • Two state, one independent parameter.
- 31. Simple Gilbert model • A system with “consecutive loss events”, which can be characterized by a “loss probability”. (p)and a “burst duration” (1-r). • Two state, two independent parameters. • 1-r = p -> Bernoulli
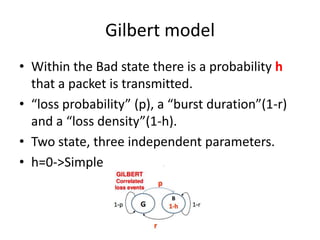
- 32. Gilbert model • Within the Bad state there is a probability h that a packet is transmitted. • “loss probability” (p), a “burst duration”(1-r) and a “loss density”(1-h). • Two state, three independent parameters. • h=0->Simple
- 33. Gilbert-Elliot model • k is the probability that the packet is transmitted while the system is in Good state. • In good state, loss events appear as “isolated” and independent with each other • Two state, four independent parameters. • k=1-> Gilbert
- 35. difference
- 36. tc-netem • Loss random(independent loss probability, correlation can be added)| Loss state | Loss gemodel | ecn
- 37. tc-netem • crand(n) = corr*crand(n-1) + (1-corr)*rand() • delay(n) = delay + distri(jitter, crand(n)) • duplicate, corrupt , loss, reorder aslo use crand. • Delay should specified if need reorder(packets should be queued first) • If gap not specified, gap = 1 will be used.
- 39. Why not loss correlation • Correlation changed the distribution
- 40. Netem example • tc qdisc add dev eth0 root netem delay 100ms 20ms 25% distribution normal • tc qdisc add dev eth0 root netem loss 0.3% 25% • tc qdisc add dev eth0 root netem duplicate 1% corrupt 0.1% • tc qdisc add dev eth0 root netem delay 10ms reorder 25% 50% gap 5
- 41. Bandwidth emulation - tbf • Tc-tbf • bfifo is the default child qdisc of tbf, • can be replace by other qdiscs such as pfifo.
- 42. Bandwidth emulation - tbf • limit - limit is the size (in bytes) of bfifo, bfifo is the queue which stores the packets. • rate - the bandwidth cap we need to enforce • burst/buffer/maxburst - this is the bucket size of the first tbf. Its value should be larger than rate/HZ to achieve the specified throughput, the larger value means more burst when traffic starts(tokens are accumulated in large bucket).
- 43. Bandwidth emulation - tbf • peakrate - if we only have one bucket, the burst rate will be larger than rate we set, so we need peakrate to limit the burst. the peakrate should be no less than rate. • mtu/minburst - most of the time, set this to MTU of the interface, larger values means larger burst.
- 44. Policing and shaping • Policer: Rate limiting without buffering, typically set at ingress, un-conformed packets are dropped directly. • Shaper: Rate limiting with buffering, typically set at exgress, and can be buffered and then if no extra buffer, then be dropped, will add extra queuing delay.
- 46. Shape emulation • No delay Bandwidth cap 1mbit/s, don't allow burst traffic, then burst = max(MTU, rate/8/HZ) = (3000,1000000/8/100) = (3000,1250) = 3000, if queuing delay 100ms, set latency 100ms or we set limit = qdelay*rate/8/1000+burst = 100*1000000/8/1000+3000 = 13750
- 47. Shape emulation • With delay attach netem to the engress first, and then add tbf to the child qdisc of netem. use limit parameter for tbf here, if using latency, tbf will not include the extra buffer needed for netem limit = tbf_burst + netem_qsize + tbf_qsize = max(rate/8/hz, MTU) + delay*rate/8000 + qdelay*rate/8000.
- 48. Police emulation • policer drops packets directly for the Non- conformant packets, and it has no buffer • tc-tbf with very small buffer. • tc-tbf use bfifo as the default child qdisc, queue length(in bytes) is set automatically by specifying 'limit' or 'latency', which ensures that the queue length is no less than token bucket depth(introduce queuing delay).
- 49. Police emulation • Workaround is replace the bfifo with pfifo • You can also use police on ingress. tc-police also use token bucket to do bandwidth cap, but it don't own queue, so there's no qdelay introduced.
- 50. Burst emulation • Most adsl will allow some burst traffic, this kind of burst is caused by the large token bucket size, which accumulates many tokens when transmission starts. • To emulate the burst, we only need to turn the 'burst' parameter.
- 51. Burst emulation • For example, we allow for 2mbit/s in the first second in the following case. 1m*t + burst = 2m*t => burst = 1m*t => burst=1m=125k
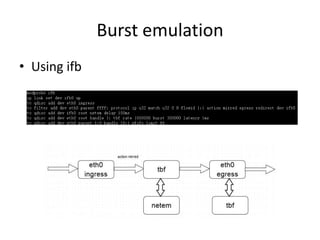
- 52. Burst emulation • What if adding delay? Any problem? • Extra burst will use the netem buffer and cause extra queuing delay. • Separate the buffer using ifb(Intermediate Functional Block device) • If traffic is redirect to ifb dev, it is returned back to the original point when dequeueing from ifb. • Can add qdisc for ifb dev
- 53. Burst emulation • Using ifb
- 54. Agenda • Why emulation • What to be emulated • How TC works • Emulation Howto • Compared with Nistnet/WANem • Other references
- 56. How Nistnet work
- 57. How Nistnet work • Bandwidth limitation is implemented as adding delay, just like a packet go through a bottleneck link. • Determine the amount of time to delay a packet. This is the maximum of two quantities: 1. Probabilistic packet delay time 2. Bandwidth-limitation delay time
- 58. How Nistnet work • probdelay = correlatedtabledist(&tableme->ltEntry.lteIDelay); if (hitme->hitreq.bandwidth) { fixed_gettimeofday(&our_time); //last queue delay bandwidthdelay = timeval_diff(&hitme->next_packet, &our_time); if (bandwidthdelay < 0) { bandwidthdelay = 0; hitme->next_packet = our_time; } //add transmission delay packettime = (long)skb->len*(MILLION/hitme->hitreq.bandwidth) + ((long)skb->len*(MILLION%hitme->hitreq.bandwidth) + hitme->hitreq.bandwidth/2)/hitme->hitreq.bandwidth; timeval_add(&hitme->next_packet, packettime); bandwidthdelay += packettime; } delay = probdelay > bandwidthdelay ? probdelay : bandwidthdelay;
- 59. Nistnet drawbacks • Bandwidth model not emulate the real one. • Queuing delay and one way delay are combined. • Buffer size can only be tune by DRD. • Only ip:port filter supported. • Not support 4 state loss burst model • Only DRD (Derivative Random Drop) AQM supported.
- 60. WANem • WANem is just a WEB UI which use tc underneath.
- 61. WANem • WEB UI, Easy to use • Add connection disconnect • Queue size need patches to work • No burst settings • No settings for GE or 4-state loss model • Queuing delay can controlled directly
- 62. Agenda • Why emulation • What to be emulated • How TC works • Emulation Howto • Compared with Nistnet/WANem • Other references
- 63. Reference • NEWT (Network Emulator for Windows Toolkit) in vs2010 • Introducing True Network Emulation in Visual Studio 2010 • Network Emulator Toolkit • dummynet • Nistnet FAQ
Editor's Notes
- #8: analysis validated by simulation, simulation validated by emulation, emulation validates by real world test.
- #30: Token bucket is used to ensure that data transmissions conform to defined limits on bandwidth and burstinessTokens are added at a fixed rateCheck if the bucket contains sufficient tokens when packets are to be sent, if so the packet will be passedOtherwise the packet will be marked or dropped.



















![qdisc handle
• Qdisc handle is used to identify Qdisc
- {none|major[:]}
- none, autogen by kernel
- major is 16bits HEX number(Without ‘0x’ prefix)
- : is optional
• Internally, qdisc_handle = major<<16](https://image.slidesharecdn.com/networkemulator-130203202445-phpapp01/85/Network-emulator-21-320.jpg)
![TC class
• Class’s parent can be class or qdisc, classid
should have the same major with parent
• classid, {[major]:minor} - major/minor are
both 16bits HEX numbers(Without ‘0x’ prefix),
major is optional
• Internally, classid = (major<<16)|minor](https://image.slidesharecdn.com/networkemulator-130203202445-phpapp01/85/Network-emulator-22-320.jpg)