Network security cryptography ppt
- 1. NETWORK SECURITY CRYPTOGRAPHY BY: R.Thushara Bharathi (CSE) S. Jahnavi (CSE)
- 2. WHAT IS NETWORK ∗ A network Is an interconnection or a media between two or more systems to share information among them. ∗ The various threats caused to network are : Remote Login Application Backdoors SMTP Session Hijackings Operating System Bugs Spams Viruses etc.
- 3. NETWORK SECURITY ∗ The security provided to the network is called network security which at present is looming on horizon as a massive problem. ∗ There are two kinds of Network Security mainly as : Transit Security : it just encrypts the packets to be transferred. Traffic Security : it acts just as a screen between hosts & remote sites.
- 4. PROBLEMS & ATTACKS ∗ There are few intertwined areas in network security as: Secrecy Authentication Non-Repudiation Integrity Control etc. ∗ The threats are classified into two categories : Passive Attacks : A passive attack is one in which the attacker eavesdrops and listens to the message but can’t modify the message. Active Attacks : An active attack is one in which the attacker modifies, deletes, replay or introduce new messages into the stream of message.
- 5. CRYPTOGRAPHY ∗ It is derived from the Greek word that meant for secret writing. ∗ Cryptography is the ability to send information between particulars in a way that it prevents others from reading the data. ∗ The data is transferred by applying two techniques by changing the plain text & Cipher texts as Encryption (P to C) & Decryption (C to P).
- 6. PRINCIPLES & SERVICES OF CRYPTOGRAPHY ∗ The two fundamental principles of cryptography are: Messages must contain some Redundancy (information not needed to understand the message). Some method is needed to foil replay attacks (validation of messages by timestamp) i.e. freshness. ∗ The services provided by the cryptography are as follows: Integrity Checking Authentication Protection to the data Confidentiality of information etc.
- 7. ENCRYPTION & DECRYPTION ∗ The way of converting the plain text to the cipher text by the means of few keys is called as “encryption”. ∗ The way of converting the cipher text to the plain text by the use of keys that are suitable to it is called as “decryption”.
- 8. SUBSTITUTION CIPHER ∗ Replacing of each letter or group of letters of plain text into cipher text by another letters is called as “substitution cipher”. ∗ The substitution may be : Monoalphabetic Substitution Digrams Trigrams
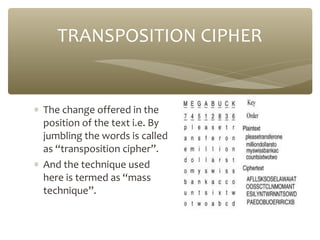
- 9. TRANSPOSITION CIPHER ∗ The change offered in the position of the text i.e. By jumbling the words is called as “transposition cipher”. ∗ And the technique used here is termed as “mass technique”.
- 10. SECRET-KEY ALGORITHMS ∗ The implementation of a simple cryptography using single key is done by the secret-key algorithms. ∗ This can be done by p-box, s-box and product cipher.
- 11. ELEMENTS OF PRODUCT CIPHERS ∗ Transpositions & substitutions can be done through p-box (a). ∗ Substitutions can be done through s-box (b). ∗ Mapping of the p-box with s-boxes form product cipher (c).
- 12. PUBLIC-KEY ALGORITHMS ∗ Public key algorithms are formed when it satisfies the following requirements: D(E(P))=P. Difficulty to deduce D from E. E cannot be broken by a chosen plain text attack.
- 13. RSA ALGORITHM ∗ RSA is derived from the names of the 3 discoverers named Rivest, Shamir, Adleman. ∗ The RSA algorithm is one of the widely used in the key algorithms. ∗ But takes much time for the large volumes of data encryption. This is done by few mathematical principles as: Choose 2 large primes. Compute n=pxq & z=(p-1)x(q-1). Find e, exd=1 mod z.
- 14. ADVANTAGES & DISADVANTAGES ∗ Advantages : Used to protect the data from the others. Used to send the data / packet in a secured way from the source to destination. Avoids in knowing the data in the way of sending. ∗ Disadvantages: Hacking is done now-a-days easily even for the data encrypted with 48 bits though the bits are extended by 52-bits.
- 15. PROPOSED CONCEPT ∗ As known the data has been easily hacked even for the 52- bit encryption too. So, the encryption bits of 52-bits should be given with the combination of both numerals and alphabets ( for example one alphabet is placed for 13-bits each). ∗ The placement of alphabet is known only to the particular sender & receiver such that it secures the data to be sent.