networking
Download as PPT, PDF8 likes12,349 views
The document discusses various topics related to computer networking including: 1. Networking involves connecting computing devices like PCs and printers to share information and resources using physical or logical connections. 2. Common network models include client-server, peer-to-peer, and domain models. 3. Network topologies describe how network elements are physically connected and include bus, star, ring, tree, mesh, and hybrid topologies.
1 of 38
Downloaded 630 times




































Ad
Recommended
Computer Networking.



Computer Networking.mvenkat2016 1) A computer network connects computers together to share resources like printers, files, and internet connections. Networks can be local-area networks within a building or wide-area networks spanning cities.
2) Common network topologies include star, bus, ring, tree and mesh. Star networks connect devices to a central hub while bus networks use a common backbone cable. Ring networks transmit messages in one direction around a closed loop.
3) Computer networks allow for resource sharing, improved communication and availability of information, though they also present security risks and require maintenance of hardware and software.
Networking ppt 



Networking ppt Shovan Mandal This document provides an overview of various computer networking concepts and components. It begins with definitions of networking basics like communications and telecommunications. It then describes the essential parts of a basic network including a message, transmitter, medium, receiver and destination. The document outlines different network topologies like bus, ring, star, star-bus and mesh. It also discusses network types like peer-to-peer and client-server networks. The document provides details on common networking media and components including coaxial cable, twisted pair cables, optical fibers, wireless transmission, hubs, gateways, routers, bridges and switches. It concludes with a brief introduction to the IEEE 802 family of standards related to local and metropolitan area networks.
Cyber security



Cyber securityHarsh verma This slide provides details about cyber security as following;
what is cyber security or computer security?
why cyber security is important?
what is cyber crime?
cyber security problems,
how to prevent from cyber crime?
global scenario of cyber crime?
organisation in world for cyber security,
top companies in cyber security,
career choice in cyber security,
scope of cyber security.
computer networks presentation



computer networks presentationKrishi Agrawal This document provides information about computer networks. It discusses that a computer network allows two or more computers to exchange information via data communication links. It then describes different types of networks like LAN, MAN, WAN based on size. It also discusses different network topologies like star, bus, ring and tree and network devices like hub, repeater, bridge, router and gateway. It finally explains common network protocols like TCP, IP, HTTP, FTP and HTTPS.
Networking presentation



Networking presentationJyoti Tewari This presentation discusses computer networks and communications. It defines a computer network as a system that connects computers and peripheral devices. Communications refers to transferring information from a sender to a receiver. Computer networks use digital signals to transmit data.
The presentation outlines three main types of computer networks: local area networks (LANs), metropolitan area networks (MANs), and wide area networks (WANs). LANs connect devices within a small physical area like a home or office, while MANs operate within a city. WANs have the largest scope and can span states, countries, or continents.
Network architectures are also introduced, including client-server models where servers provide resources and clients request them, and peer-to
Presentation on computer networking



Presentation on computer networkingJyoti Tewari This document provides an overview of computer networks, including local area networks (LANs), metropolitan area networks (MANs), and wide area networks (WANs). It discusses three main network topologies - bus, ring, and star - and compares their characteristics. The document was presented by Jyoti Tiwari for their MCA 1st semester class covering topics like the definition of computer networks, how they communicate digitally, examples of different network types classified by size and geographic reach, and distinguishing features of common network topologies.
Introduction to python for Beginners 



Introduction to python for Beginners Sujith Kumar Python is a general purpose programming language that can be used for both programming and scripting. It was created in the 1990s by Guido van Rossum who named it after the Monty Python comedy troupe. People use Python for a variety of tasks due to its readability, object-oriented capabilities, extensive libraries, and ability to integrate with other languages. To run Python code, it must first be compiled into bytecode which is then interpreted by the Python virtual machine.
Cloud computing simple ppt



Cloud computing simple pptAgarwaljay The document provides an introduction to cloud computing, defining key concepts such as cloud, cloud computing, deployment models, and service models. It explains that cloud computing allows users to access applications and store data over the internet rather than locally on a device. The main deployment models are public, private, community, and hybrid clouds, while the main service models are Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS). IaaS provides fundamental computing resources, PaaS provides development platforms, and SaaS provides software applications to users. The document discusses advantages such as lower costs and universal access, and disadvantages including internet dependence and potential security issues.
Computer network ppt communication



Computer network ppt communicationKajal Sharma This document discusses computer networks and their types. It defines a computer network as a set of interconnected computers that share resources like internet access. The document outlines different types of networks including local area networks (LANs), metropolitan area networks (MANs), wide area networks (WANs), personal area networks (PANs), client-server networks, and peer-to-peer networks. It also discusses various network topologies such as bus, star, ring, mesh and tree configurations.
Networking concepts



Networking conceptsritajindal2 The document discusses computer networks and networking concepts. It defines what a network is and explains the need for networking. It describes the components of a network including nodes, servers, network interface units. It covers the evolution of networks from ARPANET to the internet. It discusses different types of networks including LAN, MAN, WAN and their characteristics. It also covers topics like communication media, switching techniques, wireless networking and networking terms.
Basics of Networks ,Advantages and Disadvantages



Basics of Networks ,Advantages and Disadvantagessabari Giri This document discusses computer networks and networking basics. It defines what a network is as a set of devices connected by communication links. The purpose of a network is to share resources between devices. Networks must meet criteria like performance, reliability, and scalability. Different types of network connections include point-to-point and multipoint. Local area networks cover small areas like homes or offices while wide area networks connect LANs over longer distances. Key network terms are also defined such as hosts, workstations, servers, and clients.
Types of Networking Devices



Types of Networking DevicesShubham Bathe This document discusses various networking devices and wireless technologies. It describes how hubs operate at the physical layer by flooding traffic to all ports, while switches operate at the data link layer by examining packets and only sending to necessary ports. Modems convert between analog and digital signals. Bridges separate network segments, while routers connect different networks and use IP addresses. Wireless technologies discussed include Wi-Fi Direct for device-to-device connections, Wi-Fi HaLow for low power long range connections, Miracast for cable-free display sharing, ZigBee for mesh networks, and WiMax for high speed wireless broadband.
Networking devices



Networking devicesTayyab Hussain Networking devices are components that connect electronic devices and allow them to share resources over a network. Common networking devices include network interface cards, hubs, switches, bridges, routers, and modems. A switch connects network segments and can perform error checking before forwarding data packets between devices on a local area network. A router connects two or more networks and reads address information in packets to determine the best path to forward packets between networks. Routers work at the network layer and contain routing tables to define the addresses of connected networks.
Computer Networking



Computer Networkingkieshore The document discusses different types of computer networks. It describes how the Internet is a worldwide system that connects billions of devices using standard Internet protocols. An intranet also uses these protocols but is private, connecting computers within an organization. Local area networks (LANs) connect computers within a small area like a home or office, while wide area networks (WANs) connect users over broader distances using leased lines. Metropolitan area networks (MANs) connect users within a larger region like a city. The document also outlines common network topologies like ring, bus and star configurations.
Networking Fundamentals



Networking FundamentalsManjit Chavda Network Fundamentals :
1) Transmission Media
2) How Network Categorized
3) Different type of Networks
4) OSI Model of Network
5) Ethernet Cabling.
Computer network & communication answer



Computer network & communication answersmkengkilili2011 Computer networks allow interconnected computers and devices to share information and resources. They transmit digital data through physical transmission mediums like cables or wirelessly. Protocols define communication standards to minimize errors. Popular uses of networks include e-business, online education, and remote communication, which have benefited society through increased access and lower costs.
Computer network basic concepts



Computer network basic conceptsrahul kapoliya This document provides an introduction to computer networks, including their basic concepts and classifications. It defines a computer network as interconnected computers that allow sharing of resources and information. The first major network was ARPANET funded by the US Department of Defense. Networks can be classified by scale as LAN, WAN, MAN, or PAN, or by structure as client-server or peer-to-peer. Topologies include bus, star, ring, mesh and tree. Network media include twisted pair, coaxial, fiber optic and wireless. Internetworking connects distinct networks through common routing technologies like intranets, extranets and the global Internet.
An introduction to networking



An introduction to networkingJafar Nesargi This document provides an introduction to networking. It defines a network as a group of connected computers and devices that allows users to share resources. Networks enable collaboration and data sharing between multiple users. The document outlines different types of networks including local area networks (LANs), metropolitan area networks (MANs), and wide area networks (WANs). It distinguishes between peer-to-peer and client-server network models. Intranets are also discussed as private networks internal to an organization that use the same protocols as the public Internet but have restricted access.
Basics Of Networking (Overview)



Basics Of Networking (Overview)ashiesh0007 The document provides an overview of basic networking concepts including computer networks, local area networks (LANs), wide area networks (WANs), common LAN topologies, LAN transmission methods, LAN infrastructure devices, common network cabling, Ethernet, and network models like OSI and TCP/IP. It describes key aspects of each layer in the OSI model from application to network layer.
Introduction to computer network



Introduction to computer networkAshita Agrawal A computer network is defined as the interconnection of two or more computers. It is done to enable the computers to communicate and share available resources.
Components of computer network
Network benefits
Disadvantages of computer network
Classification by their geographical area
Network classification by their component role
Types of servers
Types of Computer Network



Types of Computer NetworkMohit Dasariya This presentation briefly describes the different types of computer networks along with their advantages and disadvantages and comparison between them.
NETWORK COMPONENTS



NETWORK COMPONENTSbwire sedrick Network components include nodes, links, clients, servers, and other devices that connect and allow communication between systems. Key components discussed include network interface cards, hubs, bridges, routers, switches, gateways, and wireless devices. Various media are used to physically transmit data between nodes on a network.
COMPUTER NETWORKING



COMPUTER NETWORKINGKiran Buriro This document provides an overview of computer networks. It discusses network diagrams, classifications of networks by range including LAN, WAN, PAN and MAN. Common network topologies such as bus, star, ring and mesh are described. The OSI and TCP/IP models are explained. Common network devices, switching technologies, and transmission media are defined. Signal types including analog and digital are also summarized.
Networking



NetworkingPalash Sachan To Download this PPT click on the link below:-
http://www29.zippyshare.com/v/14569917/file.html
Networking
Computer network
Types of network
Personal Area Networks (PANs)
Local Area Networks (LANs)
Metropolitan Area Networks (MANs)
Wide Area Networks (WANs)
Classification of Network Architecture
Client-server architecture
Peer-to-peer architecture
Hybrid architecture
Network topology
Bus Topology
Star Topology
Ring Topology
Mesh Topology
Tree Topology
Hybrid Topology
Types of-networks



Types of-networksStudsPlanet.com There are several types of computer networks depending on their geographical reach: local area networks (LANs) which connect devices within a building or home; metropolitan area networks (MANs) which span a city or large campus; wide area networks (WANs) which connect LANs over long distances like countries or continents; and personal area networks (PANs) which connect devices within a few meters of an individual. LANs use twisted pair cable or WiFi to link devices for resource sharing at speeds up to 10 Gbps, while MANs and WANs transmit data over phone lines or wireless links to connect larger regions. PANs allow communication between devices in close proximity, either directly or through a larger network
Introduction to Computer Networks



Introduction to Computer NetworksGhaffar Khan This document provides an overview of chapter 1 of a computer networks course. It introduces key topics that will be covered, including network hardware, network software, reference models (OSI and TCP/IP), example networks (Novell Netware, ARPANET, NSFNET, Internet), and example data communication services. It discusses concepts like layers, protocols, interfaces, services, and connection-oriented vs connectionless networks at a high level.
Computer network



Computer networkkainat fatima The document discusses different types of computer networks including LAN, WAN, and MAN. A LAN covers a small area like an office and connects computers within close proximity at speeds up to 1 Gbps. A WAN spans larger distances, connecting computers across cities and countries at slower speeds between 56 Kbps to 50 Mbps. A MAN connects LANs within a city and is larger than a LAN but smaller than a WAN. It provides higher data speeds than a WAN over its coverage area.
Networking fundamentals



Networking fundamentalsjpprakash This document provides an overview of networking fundamentals, including definitions of common network types like LANs and WANs. It describes network topologies like bus, star, and ring configurations. Communication protocols and hardware like hubs, routers, and firewalls are defined. The roles of gateways and modems in transmitting data are also summarized.
P2P Seminar



P2P SeminarCoRehab The document discusses peer-to-peer (P2P) networking. It defines P2P networking as allowing computers and software to function without special servers by directly connecting to other peers. It then discusses the history and basic concepts of P2P, including definitions, overlay networks, typical problems faced, and some popular P2P applications like file sharing using Napster, Gnutella, Kazaa, and BitTorrent. It also briefly discusses P2P for voice over IP using Skype and efforts to implement P2P on mobile devices.
Peer to-peer training



Peer to-peer trainingDavid Vershaw II, CRC This is brief guide with some tips on working with customers/clients growing through the vocational process.
Ad
More Related Content
What's hot (20)
Computer network ppt communication



Computer network ppt communicationKajal Sharma This document discusses computer networks and their types. It defines a computer network as a set of interconnected computers that share resources like internet access. The document outlines different types of networks including local area networks (LANs), metropolitan area networks (MANs), wide area networks (WANs), personal area networks (PANs), client-server networks, and peer-to-peer networks. It also discusses various network topologies such as bus, star, ring, mesh and tree configurations.
Networking concepts



Networking conceptsritajindal2 The document discusses computer networks and networking concepts. It defines what a network is and explains the need for networking. It describes the components of a network including nodes, servers, network interface units. It covers the evolution of networks from ARPANET to the internet. It discusses different types of networks including LAN, MAN, WAN and their characteristics. It also covers topics like communication media, switching techniques, wireless networking and networking terms.
Basics of Networks ,Advantages and Disadvantages



Basics of Networks ,Advantages and Disadvantagessabari Giri This document discusses computer networks and networking basics. It defines what a network is as a set of devices connected by communication links. The purpose of a network is to share resources between devices. Networks must meet criteria like performance, reliability, and scalability. Different types of network connections include point-to-point and multipoint. Local area networks cover small areas like homes or offices while wide area networks connect LANs over longer distances. Key network terms are also defined such as hosts, workstations, servers, and clients.
Types of Networking Devices



Types of Networking DevicesShubham Bathe This document discusses various networking devices and wireless technologies. It describes how hubs operate at the physical layer by flooding traffic to all ports, while switches operate at the data link layer by examining packets and only sending to necessary ports. Modems convert between analog and digital signals. Bridges separate network segments, while routers connect different networks and use IP addresses. Wireless technologies discussed include Wi-Fi Direct for device-to-device connections, Wi-Fi HaLow for low power long range connections, Miracast for cable-free display sharing, ZigBee for mesh networks, and WiMax for high speed wireless broadband.
Networking devices



Networking devicesTayyab Hussain Networking devices are components that connect electronic devices and allow them to share resources over a network. Common networking devices include network interface cards, hubs, switches, bridges, routers, and modems. A switch connects network segments and can perform error checking before forwarding data packets between devices on a local area network. A router connects two or more networks and reads address information in packets to determine the best path to forward packets between networks. Routers work at the network layer and contain routing tables to define the addresses of connected networks.
Computer Networking



Computer Networkingkieshore The document discusses different types of computer networks. It describes how the Internet is a worldwide system that connects billions of devices using standard Internet protocols. An intranet also uses these protocols but is private, connecting computers within an organization. Local area networks (LANs) connect computers within a small area like a home or office, while wide area networks (WANs) connect users over broader distances using leased lines. Metropolitan area networks (MANs) connect users within a larger region like a city. The document also outlines common network topologies like ring, bus and star configurations.
Networking Fundamentals



Networking FundamentalsManjit Chavda Network Fundamentals :
1) Transmission Media
2) How Network Categorized
3) Different type of Networks
4) OSI Model of Network
5) Ethernet Cabling.
Computer network & communication answer



Computer network & communication answersmkengkilili2011 Computer networks allow interconnected computers and devices to share information and resources. They transmit digital data through physical transmission mediums like cables or wirelessly. Protocols define communication standards to minimize errors. Popular uses of networks include e-business, online education, and remote communication, which have benefited society through increased access and lower costs.
Computer network basic concepts



Computer network basic conceptsrahul kapoliya This document provides an introduction to computer networks, including their basic concepts and classifications. It defines a computer network as interconnected computers that allow sharing of resources and information. The first major network was ARPANET funded by the US Department of Defense. Networks can be classified by scale as LAN, WAN, MAN, or PAN, or by structure as client-server or peer-to-peer. Topologies include bus, star, ring, mesh and tree. Network media include twisted pair, coaxial, fiber optic and wireless. Internetworking connects distinct networks through common routing technologies like intranets, extranets and the global Internet.
An introduction to networking



An introduction to networkingJafar Nesargi This document provides an introduction to networking. It defines a network as a group of connected computers and devices that allows users to share resources. Networks enable collaboration and data sharing between multiple users. The document outlines different types of networks including local area networks (LANs), metropolitan area networks (MANs), and wide area networks (WANs). It distinguishes between peer-to-peer and client-server network models. Intranets are also discussed as private networks internal to an organization that use the same protocols as the public Internet but have restricted access.
Basics Of Networking (Overview)



Basics Of Networking (Overview)ashiesh0007 The document provides an overview of basic networking concepts including computer networks, local area networks (LANs), wide area networks (WANs), common LAN topologies, LAN transmission methods, LAN infrastructure devices, common network cabling, Ethernet, and network models like OSI and TCP/IP. It describes key aspects of each layer in the OSI model from application to network layer.
Introduction to computer network



Introduction to computer networkAshita Agrawal A computer network is defined as the interconnection of two or more computers. It is done to enable the computers to communicate and share available resources.
Components of computer network
Network benefits
Disadvantages of computer network
Classification by their geographical area
Network classification by their component role
Types of servers
Types of Computer Network



Types of Computer NetworkMohit Dasariya This presentation briefly describes the different types of computer networks along with their advantages and disadvantages and comparison between them.
NETWORK COMPONENTS



NETWORK COMPONENTSbwire sedrick Network components include nodes, links, clients, servers, and other devices that connect and allow communication between systems. Key components discussed include network interface cards, hubs, bridges, routers, switches, gateways, and wireless devices. Various media are used to physically transmit data between nodes on a network.
COMPUTER NETWORKING



COMPUTER NETWORKINGKiran Buriro This document provides an overview of computer networks. It discusses network diagrams, classifications of networks by range including LAN, WAN, PAN and MAN. Common network topologies such as bus, star, ring and mesh are described. The OSI and TCP/IP models are explained. Common network devices, switching technologies, and transmission media are defined. Signal types including analog and digital are also summarized.
Networking



NetworkingPalash Sachan To Download this PPT click on the link below:-
http://www29.zippyshare.com/v/14569917/file.html
Networking
Computer network
Types of network
Personal Area Networks (PANs)
Local Area Networks (LANs)
Metropolitan Area Networks (MANs)
Wide Area Networks (WANs)
Classification of Network Architecture
Client-server architecture
Peer-to-peer architecture
Hybrid architecture
Network topology
Bus Topology
Star Topology
Ring Topology
Mesh Topology
Tree Topology
Hybrid Topology
Types of-networks



Types of-networksStudsPlanet.com There are several types of computer networks depending on their geographical reach: local area networks (LANs) which connect devices within a building or home; metropolitan area networks (MANs) which span a city or large campus; wide area networks (WANs) which connect LANs over long distances like countries or continents; and personal area networks (PANs) which connect devices within a few meters of an individual. LANs use twisted pair cable or WiFi to link devices for resource sharing at speeds up to 10 Gbps, while MANs and WANs transmit data over phone lines or wireless links to connect larger regions. PANs allow communication between devices in close proximity, either directly or through a larger network
Introduction to Computer Networks



Introduction to Computer NetworksGhaffar Khan This document provides an overview of chapter 1 of a computer networks course. It introduces key topics that will be covered, including network hardware, network software, reference models (OSI and TCP/IP), example networks (Novell Netware, ARPANET, NSFNET, Internet), and example data communication services. It discusses concepts like layers, protocols, interfaces, services, and connection-oriented vs connectionless networks at a high level.
Computer network



Computer networkkainat fatima The document discusses different types of computer networks including LAN, WAN, and MAN. A LAN covers a small area like an office and connects computers within close proximity at speeds up to 1 Gbps. A WAN spans larger distances, connecting computers across cities and countries at slower speeds between 56 Kbps to 50 Mbps. A MAN connects LANs within a city and is larger than a LAN but smaller than a WAN. It provides higher data speeds than a WAN over its coverage area.
Networking fundamentals



Networking fundamentalsjpprakash This document provides an overview of networking fundamentals, including definitions of common network types like LANs and WANs. It describes network topologies like bus, star, and ring configurations. Communication protocols and hardware like hubs, routers, and firewalls are defined. The roles of gateways and modems in transmitting data are also summarized.
Viewers also liked (6)
P2P Seminar



P2P SeminarCoRehab The document discusses peer-to-peer (P2P) networking. It defines P2P networking as allowing computers and software to function without special servers by directly connecting to other peers. It then discusses the history and basic concepts of P2P, including definitions, overlay networks, typical problems faced, and some popular P2P applications like file sharing using Napster, Gnutella, Kazaa, and BitTorrent. It also briefly discusses P2P for voice over IP using Skype and efforts to implement P2P on mobile devices.
Peer to-peer training



Peer to-peer trainingDavid Vershaw II, CRC This is brief guide with some tips on working with customers/clients growing through the vocational process.
Peer to Peer networks and piracy



Peer to Peer networks and piracyOffice of the Principal Accountant General (Indian Audit and Accounts Department) This document discusses peer-to-peer (P2P) networks and their relationship to piracy. It defines key terms related to P2P file sharing such as torrents, seeds, trackers, and clients. It also discusses organizations against piracy like BASCAP and popular file sharing sites like The Pirate Bay. Videos are included that demonstrate downloading content from Limewire and uTorrent as well as topics around darknet file sharing and groups that support or oppose piracy.
CCNA Router and IOS Basics



CCNA Router and IOS BasicsDsunte Wilson The document discusses the basics of Cisco routers and the Cisco IOS. It describes the router user interface, including different access methods and configuration modes. It also covers router components, passwords, and the functions of ROM, flash memory, NVRAM, RAM and interfaces.
P2 p



P2 pChester Chn This document discusses peer-to-peer (P2P) networks. It defines P2P networks as distributed networks where participants share resources like processing power, storage, or bandwidth directly without central coordination. P2P is commonly used for sharing digital content files. There are two main types of P2P network structures - structured networks which use algorithms to organize connections, and unstructured networks which connect peers arbitrarily. Bittorrent is one of the most popular P2P protocols, originally used an unstructured architecture but now some clients implement distributed hash tables for more efficient searching.
BASIC CONCEPTS OF COMPUTER NETWORKS 



BASIC CONCEPTS OF COMPUTER NETWORKS Kak Yong A computer network connects computers and devices together through communication devices and transmission media. It allows sharing of resources like printers, files, data and information. There are three main types of networks - local area networks (LANs) within a small geographical area, metropolitan area networks (MANs) within a city, and wide area networks (WANs) across large areas like countries. Network architecture refers to the overall design of a computer network and describes how it is configured and what strategies are used. The two main architectures are client/server, where a server provides services to clients, and peer-to-peer where all computers have equal capabilities without a central server.
Peer to Peer networks and piracy



Peer to Peer networks and piracyOffice of the Principal Accountant General (Indian Audit and Accounts Department)
Ad
Similar to networking (20)
Computer Networks



Computer NetworksRaj vardhan Computer networks allow devices to connect and share resources. There are several types of networks including local area networks (LANs), wide area networks (WANs), and metropolitan area networks (MANs). Networks use different topologies like bus, star, ring, mesh, and tree to connect devices. The topology impacts features like cost, ease of use, and how failure of parts affects the whole network.
NETWORKING



NETWORKINGjunaid abbasi This document provides an overview of computer networking concepts including different network topologies, types of networks, and common networking devices. It discusses peer-to-peer and client-server network models. Topologies covered include ring, bus, star, mesh, and tree. Wide area networks and local area networks are defined. Common networking devices like repeaters, bridges, routers, switches, and network interface cards are also explained.
Computer Network ssss ppt.pptx



Computer Network ssss ppt.pptxRamNivas42 This document provides an introduction to computer networks presented by Ram nivas sonkar. It begins with defining what a computer network is and discusses the key components and types of networks including LAN, MAN, WAN and PAN. It then covers topics like network topologies, wireless networks and the OSI model. Specifically, it describes common network topologies like star, bus, ring and tree and explains the layers of the OSI model from the physical layer up to the transport layer.
Types of computer networks



Types of computer networksTatheer Fatima This document summarizes different types of computer networks. It discusses local area networks (LANs) that connect devices within a small geographic area like a home or office. Metropolitan area networks (MANs) interconnect LANs within a larger region like a city. Wide area networks (WANs) connect LANs across national and international locations using technologies like fiber optics, radio waves, and satellites. The document also describes wired and wireless connection methods, client-server and peer-to-peer network functionality, common network topologies like bus, star and ring, and protocols such as TCP/IP, IPX/SPX, and AppleTalk.
COMPUTER TAPALOGY



COMPUTER TAPALOGYWASEEM ARSLAN This document provides information about a group project on computer networks. It introduces the six group members and their topics: models & topologies, methods/types, internetworking tools, OSI model, wireless networks, and communication protocols. It then provides details on each of these topics, including definitions, examples, advantages and disadvantages of different network models, topologies, types, internetworking devices, layers of the OSI model, types of wireless networks, and issues in wireless systems.
Network -Lecture Notes



Network -Lecture NotesBathshebaparimala This document defines various types of computer networks and networking concepts. It begins by defining what a computer network is. It then lists and briefly describes different types of networks including personal area networks, local area networks, wireless local area networks, campus area networks, metropolitan area networks, wide area networks, and storage area networks. It also discusses network topologies such as bus, star, ring, mesh, tree, and hybrid topologies. Finally, it provides an overview of the seven-layer OSI model.
Distributed Structure System



Distributed Structure Systemhusnaina_akhtar This document discusses different aspects of distributed systems and network topologies. It describes two types of network operating systems: peer-to-peer and client/server. It also defines different network topologies including bus, ring, star, mesh, tree, and hybrid and discusses their key features, advantages, and disadvantages. Finally, it provides a brief definition of communication protocols in distributed systems.
Presentation for slideshare



Presentation for slideshareBSITstudents This document provides an overview of computer networks and wireless networks. It discusses the different types of network topologies including bus, star, ring, tree, and mesh. It also describes different network models like PAN, LAN, MAN, and WAN according to the geographical area covered. The document introduces various internetworking tools such as bridges, routers, and gateways. It provides a brief history of the OSI model and describes the seven layers of the OSI model. Finally, it discusses wireless networks and different wireless technologies including 2G, 3G, WLAN, and WiMAX.
Computer network-and Network topology



Computer network-and Network topologyRida Shad This report discusses computer networks and network topologies. It defines a computer network and describes different types of networks based on size, including personal area networks (PANs), local area networks (LANs), metropolitan area networks (MANs), and wide area networks (WANs). The report also examines different network topologies such as bus, ring, star, mesh, tree, and hybrid topologies. For each topology, it provides details on features, advantages, and disadvantages. The conclusion emphasizes that understanding standard network topologies provides insight into important networking concepts.
Ccna(routing &and switching)



Ccna(routing &and switching)Shweta Kumari The document provides information about computer networks and routing & switching certification (CCNA). It discusses TCIL-IT, a company that provides computer networking education and training. It then covers topics such as network design, types of networks, network topologies, networking devices, cables, IP addresses, and basic router configuration commands. The document is intended to provide an overview of concepts relevant to the CCNA certification program for computer networking.
7 topology ethernet



7 topology ethernetSamit Singh The document discusses various network topologies including mesh, star, bus, ring, tree, and hybrid topologies. It provides details on how each topology connects devices, its advantages and disadvantages, and examples of applications. It also covers Ethernet, collision domains, CSMA/CD protocol, token ring networks, FDDI, and considerations for choosing a topology.
basic networking



basic networkingAnmol Bagga The document provides an overview of basic networking hardware and concepts. It defines a local area network (LAN) and discusses common LAN topologies like bus, star, and ring. It also describes common networking hardware such as hubs, switches, bridges, routers, and network interface cards. The document outlines different network media including copper, fiber optic, and wireless technologies. It provides examples of how home and business networks can be implemented using these concepts and technologies.
Arvind Singh



Arvind Singhanshul parmar The document provides an overview of basic networking hardware and concepts. It discusses common network topologies like star, bus, and ring. It also describes common networking devices like hubs, switches, bridges, routers and their functions. Finally, it covers different network media like twisted pair, coaxial cable and fiber optic cable and provides examples of local area network implementations in home and business settings.
Networking presentation



Networking presentationGajan Hai A computer network connects multiple devices together to share resources and information. There are different types of networks including LANs, WANs, MANs, PANs, and VPNs. Network topology describes how devices are physically connected, with common topologies being bus, star, ring, mesh, and tree. Key networking hardware includes network interface cards, hubs, switches, bridges, and routers. Networks are measured based on latency, data transfer rate, bandwidth, and other performance parameters. Ethernet is a common standard used to connect devices via cables or wirelessly. IP addresses identify devices on the Internet or private networks.
3.pptx



3.pptxkebeAman This document discusses different types of computer networks based on geographical coverage, architecture, and topology. It describes Local Area Networks (LANs) as covering a small area like a room or building, with high speeds up to 1000 Mbps. Metropolitan Area Networks (MANs) span a larger area like a campus or city, with lower speeds of 10-100 Mbps. Wide Area Networks (WANs) have no boundaries and can span countries, with varying speeds based on location. Common network architectures are peer-to-peer and client-server, and common topologies include bus, star, ring, mesh, and hybrid combinations. It also discusses different transmission media like twisted pair, coaxial, and optical fiber cables.
original



originalsujal Khatiwada Network topologies refer to the geometric arrangement of devices on a computer network. There are several standard network topologies including bus, star, ring, and hybrid. Each topology has advantages and disadvantages depending on factors like scalability, fault tolerance, cost, and speed. A hybrid topology combines two or more standard topologies to leverage their strengths and mitigate weaknesses.
Networking



NetworkingRajThakuri This document provides information about computer networking including definitions, components, types, and concepts. It defines a computer network as two or more connected computers that allow people to share files, printers, and other resources. There are two main types of networks based on architecture: client-server networks with a dedicated server and peer-to-peer networks without hierarchy. Other key topics covered include network topologies (bus, star, ring, etc.), transmission media (guided, unguided), protocols, and modes of communication (simplex, half-duplex, full-duplex).
Computer Networking



Computer NetworkingAlisha Jain An interconnected collection of autonomous computers is called a computer network. Networks allow computers to share resources like hardware, software, databases, and communicate with each other. The first network was ARPANET in 1969 which connected universities and defense organizations in the US. Later networks like NSFnet and the Internet improved capacity and connectivity. A network uses nodes, servers, network interface units, and types of networks can be LANs, MANs, or WANs depending on geographical reach. Networking evolved to improve sharing, reliability, and reduce costs.
Classification of Computer



Classification of ComputerAfsanaAkterRubi This document provides an overview of computer network types and topologies. It discusses the four main types of networks: local area networks (LANs), personal area networks (PANs), metropolitan area networks (MANs), and wide area networks (WANs). Each network type is defined based on its size and scope. The document also examines common network topologies like bus, star, ring, mesh, tree, and hybrid along with their advantages and disadvantages. Finally, it briefly introduces some network technologies including intranets, extranets, and the internet.
Ad
Recently uploaded (20)
How Can I use the AI Hype in my Business Context?



How Can I use the AI Hype in my Business Context?Daniel Lehner 𝙄𝙨 𝘼𝙄 𝙟𝙪𝙨𝙩 𝙝𝙮𝙥𝙚? 𝙊𝙧 𝙞𝙨 𝙞𝙩 𝙩𝙝𝙚 𝙜𝙖𝙢𝙚 𝙘𝙝𝙖𝙣𝙜𝙚𝙧 𝙮𝙤𝙪𝙧 𝙗𝙪𝙨𝙞𝙣𝙚𝙨𝙨 𝙣𝙚𝙚𝙙𝙨?
Everyone’s talking about AI but is anyone really using it to create real value?
Most companies want to leverage AI. Few know 𝗵𝗼𝘄.
✅ What exactly should you ask to find real AI opportunities?
✅ Which AI techniques actually fit your business?
✅ Is your data even ready for AI?
If you’re not sure, you’re not alone. This is a condensed version of the slides I presented at a Linkedin webinar for Tecnovy on 28.04.2025.
Splunk Security Update | Public Sector Summit Germany 2025



Splunk Security Update | Public Sector Summit Germany 2025Splunk Splunk Security Update
Sprecher: Marcel Tanuatmadja
Mobile App Development Company in Saudi Arabia



Mobile App Development Company in Saudi ArabiaSteve Jonas EmizenTech is a globally recognized software development company, proudly serving businesses since 2013. With over 11+ years of industry experience and a team of 200+ skilled professionals, we have successfully delivered 1200+ projects across various sectors. As a leading Mobile App Development Company In Saudi Arabia we offer end-to-end solutions for iOS, Android, and cross-platform applications. Our apps are known for their user-friendly interfaces, scalability, high performance, and strong security features. We tailor each mobile application to meet the unique needs of different industries, ensuring a seamless user experience. EmizenTech is committed to turning your vision into a powerful digital product that drives growth, innovation, and long-term success in the competitive mobile landscape of Saudi Arabia.
Linux Support for SMARC: How Toradex Empowers Embedded Developers



Linux Support for SMARC: How Toradex Empowers Embedded DevelopersToradex Toradex brings robust Linux support to SMARC (Smart Mobility Architecture), ensuring high performance and long-term reliability for embedded applications. Here’s how:
• Optimized Torizon OS & Yocto Support – Toradex provides Torizon OS, a Debian-based easy-to-use platform, and Yocto BSPs for customized Linux images on SMARC modules.
• Seamless Integration with i.MX 8M Plus and i.MX 95 – Toradex SMARC solutions leverage NXP’s i.MX 8 M Plus and i.MX 95 SoCs, delivering power efficiency and AI-ready performance.
• Secure and Reliable – With Secure Boot, over-the-air (OTA) updates, and LTS kernel support, Toradex ensures industrial-grade security and longevity.
• Containerized Workflows for AI & IoT – Support for Docker, ROS, and real-time Linux enables scalable AI, ML, and IoT applications.
• Strong Ecosystem & Developer Support – Toradex offers comprehensive documentation, developer tools, and dedicated support, accelerating time-to-market.
With Toradex’s Linux support for SMARC, developers get a scalable, secure, and high-performance solution for industrial, medical, and AI-driven applications.
Do you have a specific project or application in mind where you're considering SMARC? We can help with Free Compatibility Check and help you with quick time-to-market
For more information: https://www.toradex.com/computer-on-modules/smarc-arm-family
Cybersecurity Identity and Access Solutions using Azure AD



Cybersecurity Identity and Access Solutions using Azure ADVICTOR MAESTRE RAMIREZ Cybersecurity Identity and Access Solutions using Azure AD
Cyber Awareness overview for 2025 month of security



Cyber Awareness overview for 2025 month of securityriccardosl1 Cyber awareness training educates employees on risk associated with internet and malicious emails
Linux Professional Institute LPIC-1 Exam.pdf



Linux Professional Institute LPIC-1 Exam.pdfRHCSA Guru Introduction to LPIC-1 Exam - overview, exam details, price and job opportunities
Massive Power Outage Hits Spain, Portugal, and France: Causes, Impact, and On...



Massive Power Outage Hits Spain, Portugal, and France: Causes, Impact, and On...Aqusag Technologies In late April 2025, a significant portion of Europe, particularly Spain, Portugal, and parts of southern France, experienced widespread, rolling power outages that continue to affect millions of residents, businesses, and infrastructure systems.
2025-05-Q4-2024-Investor-Presentation.pptx



2025-05-Q4-2024-Investor-Presentation.pptxSamuele Fogagnolo Cloudflare Q4 Financial Results Presentation
Complete Guide to Advanced Logistics Management Software in Riyadh.pdf



Complete Guide to Advanced Logistics Management Software in Riyadh.pdfSoftware Company Explore the benefits and features of advanced logistics management software for businesses in Riyadh. This guide delves into the latest technologies, from real-time tracking and route optimization to warehouse management and inventory control, helping businesses streamline their logistics operations and reduce costs. Learn how implementing the right software solution can enhance efficiency, improve customer satisfaction, and provide a competitive edge in the growing logistics sector of Riyadh.
How analogue intelligence complements AI



How analogue intelligence complements AIPaul Rowe
Artificial Intelligence is providing benefits in many areas of work within the heritage sector, from image analysis, to ideas generation, and new research tools. However, it is more critical than ever for people, with analogue intelligence, to ensure the integrity and ethical use of AI. Including real people can improve the use of AI by identifying potential biases, cross-checking results, refining workflows, and providing contextual relevance to AI-driven results.
News about the impact of AI often paints a rosy picture. In practice, there are many potential pitfalls. This presentation discusses these issues and looks at the role of analogue intelligence and analogue interfaces in providing the best results to our audiences. How do we deal with factually incorrect results? How do we get content generated that better reflects the diversity of our communities? What roles are there for physical, in-person experiences in the digital world?
Enhancing ICU Intelligence: How Our Functional Testing Enabled a Healthcare I...



Enhancing ICU Intelligence: How Our Functional Testing Enabled a Healthcare I...Impelsys Inc. Impelsys provided a robust testing solution, leveraging a risk-based and requirement-mapped approach to validate ICU Connect and CritiXpert. A well-defined test suite was developed to assess data communication, clinical data collection, transformation, and visualization across integrated devices.
HCL Nomad Web – Best Practices and Managing Multiuser Environments



HCL Nomad Web – Best Practices and Managing Multiuser Environmentspanagenda Webinar Recording: https://www.panagenda.com/webinars/hcl-nomad-web-best-practices-and-managing-multiuser-environments/
HCL Nomad Web is heralded as the next generation of the HCL Notes client, offering numerous advantages such as eliminating the need for packaging, distribution, and installation. Nomad Web client upgrades will be installed “automatically” in the background. This significantly reduces the administrative footprint compared to traditional HCL Notes clients. However, troubleshooting issues in Nomad Web present unique challenges compared to the Notes client.
Join Christoph and Marc as they demonstrate how to simplify the troubleshooting process in HCL Nomad Web, ensuring a smoother and more efficient user experience.
In this webinar, we will explore effective strategies for diagnosing and resolving common problems in HCL Nomad Web, including
- Accessing the console
- Locating and interpreting log files
- Accessing the data folder within the browser’s cache (using OPFS)
- Understand the difference between single- and multi-user scenarios
- Utilizing Client Clocking
The Evolution of Meme Coins A New Era for Digital Currency ppt.pdf



The Evolution of Meme Coins A New Era for Digital Currency ppt.pdfAbi john Analyze the growth of meme coins from mere online jokes to potential assets in the digital economy. Explore the community, culture, and utility as they elevate themselves to a new era in cryptocurrency.
Into The Box Conference Keynote Day 1 (ITB2025)



Into The Box Conference Keynote Day 1 (ITB2025)Ortus Solutions, Corp This is the keynote of the Into the Box conference, highlighting the release of the BoxLang JVM language, its key enhancements, and its vision for the future.
What is Model Context Protocol(MCP) - The new technology for communication bw...



What is Model Context Protocol(MCP) - The new technology for communication bw...Vishnu Singh Chundawat The MCP (Model Context Protocol) is a framework designed to manage context and interaction within complex systems. This SlideShare presentation will provide a detailed overview of the MCP Model, its applications, and how it plays a crucial role in improving communication and decision-making in distributed systems. We will explore the key concepts behind the protocol, including the importance of context, data management, and how this model enhances system adaptability and responsiveness. Ideal for software developers, system architects, and IT professionals, this presentation will offer valuable insights into how the MCP Model can streamline workflows, improve efficiency, and create more intuitive systems for a wide range of use cases.
Technology Trends in 2025: AI and Big Data Analytics



Technology Trends in 2025: AI and Big Data AnalyticsInData Labs At InData Labs, we have been keeping an ear to the ground, looking out for AI-enabled digital transformation trends coming our way in 2025. Our report will provide a look into the technology landscape of the future, including:
-Artificial Intelligence Market Overview
-Strategies for AI Adoption in 2025
-Anticipated drivers of AI adoption and transformative technologies
-Benefits of AI and Big data for your business
-Tips on how to prepare your business for innovation
-AI and data privacy: Strategies for securing data privacy in AI models, etc.
Download your free copy nowand implement the key findings to improve your business.
TrustArc Webinar: Consumer Expectations vs Corporate Realities on Data Broker...



TrustArc Webinar: Consumer Expectations vs Corporate Realities on Data Broker...TrustArc Most consumers believe they’re making informed decisions about their personal data—adjusting privacy settings, blocking trackers, and opting out where they can. However, our new research reveals that while awareness is high, taking meaningful action is still lacking. On the corporate side, many organizations report strong policies for managing third-party data and consumer consent yet fall short when it comes to consistency, accountability and transparency.
This session will explore the research findings from TrustArc’s Privacy Pulse Survey, examining consumer attitudes toward personal data collection and practical suggestions for corporate practices around purchasing third-party data.
Attendees will learn:
- Consumer awareness around data brokers and what consumers are doing to limit data collection
- How businesses assess third-party vendors and their consent management operations
- Where business preparedness needs improvement
- What these trends mean for the future of privacy governance and public trust
This discussion is essential for privacy, risk, and compliance professionals who want to ground their strategies in current data and prepare for what’s next in the privacy landscape.
Rusty Waters: Elevating Lakehouses Beyond Spark



Rusty Waters: Elevating Lakehouses Beyond Sparkcarlyakerly1 Spark is a powerhouse for large datasets, but when it comes to smaller data workloads, its overhead can sometimes slow things down. What if you could achieve high performance and efficiency without the need for Spark?
At S&P Global Commodity Insights, having a complete view of global energy and commodities markets enables customers to make data-driven decisions with confidence and create long-term, sustainable value. 🌍
Explore delta-rs + CDC and how these open-source innovations power lightweight, high-performance data applications beyond Spark! 🚀
What is Model Context Protocol(MCP) - The new technology for communication bw...



What is Model Context Protocol(MCP) - The new technology for communication bw...Vishnu Singh Chundawat
networking
- 1. NETWORKING SUBMITTED BY:- POOJA DHIMAN
- 2. Networking is a practice of linking of two or more computing devices such as PCs printers etc. with each other connections between two devices is through physical media or logical media to share the information, data and resources. Network are made with hardware and software. cable / media computer networking NETWORKING
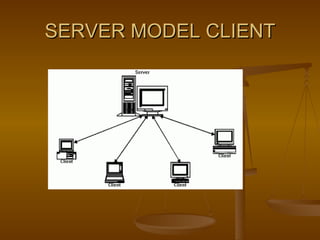
- 3. Model means connectivity of computers. Types of networking models Client – server model :- In a client server model we have one server and many clients. A client can share the resources of server, but a server cannot share the resources on client. MODELS OF NETWORKING
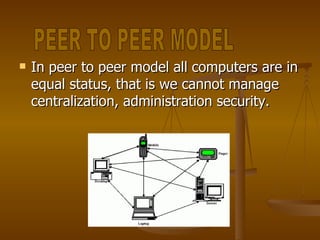
- 5. In peer to peer model all computers are in equal status, that is we cannot manage centralization, administration security. PEER TO PEER MODEL
- 6. It is a mixture of client and peer to peer model. Client can share their resources as peer to peer but with the permission of the server as in server model. It is commonly used model because in this security is more as we put restriction on both server and clients. DOMAIN MODEL
- 7. Local area network (LAN). It is restricted to a small area such as home, Offices or colleges. HUB & SWITCHE are used in LAN. CATEGORIES OF NETWORK
- 8. Campus Area Network (CAN). Made up of two or more LANs with in limited area. All the computers which are connected together have some relationship to each other e.g different buildings in a campus can be connected using different CAN. CAN
- 9. 3 . Metropolitan Area Network (MAN). MAN is the interconnection of networks in the city. It also formed by connecting remote LANs through telephone lines. MAN support data and voice transmission. e.g cable T.V network in the city. MAN
- 10. 4 . Wide Area Network (WAN). It covers a wide geographical area which includes the multiple computers or LANs. ROUTER devices is used in WAN.
- 11. Network Topology describe the way in which the elements of network are connected. They describe the physical arrangement of the network nodes. The physical topology of a network refers to the configuration of cables, computers and other peripherals etc. TOPOLOGY
- 12. Single Node Topology BUS Topology STAR Topology RING Topology TREE Topology MESH Topology HYBRID Topology KIND OF TOPOLOGY
- 13. The server and host is heaving all the information for network. Includes a single device which is connected to the server. The server is the main device used for network data storage. SINGLE NODE TOPOLOGY
- 15. Easy to install. Least expensive. Single cable is required. Only single device is connected in the entire network. Advantages Disadvantages
- 16. All the nodes on a bus topology are connected by one single cable. A bus topology consist of main run of cable with terminators at each ends. Popular on LAN’s because they are expensive and easy to install. BUS TOPOLOGY
- 17. BUS TOPOLOGY
- 18. Require less cable as compared to star topology. Less expensive than other topology. Work better for the small network. Entire network gets affected if there is a break in the main cable. Difficult to detect the faulty device. Advantages Disadvantages
- 19. Each nodes are connected to a central device called hub. Hub takes a signal that comes from any nodes & passes it along to all the other nodes in the network. Data passes through hub before reaching at its destination. Hub or switches manages n control the function of network. In it chances of failure reduce because the use of hub. STAR TOPOLOGY
- 20. STAR TOPOLOGY
- 21. Easy to install and manage. Simple in use. It is widely used. More expensive. Hub failure leads to network failure. Increased devices makes the network slow. Advantages Disadvantages
- 22. In a ring topology each devices has exactly two adjacent device for communication purpose. Message travel through ring in same direction. To implement a ring network we use TOKEN ring technology. RING TOPOLOGY
- 23. RING TOPOLOGY
- 24. Easy to manage then BUS topology. Good communications over long distance. Handle high volume of traffic. The failure of a single node of the network can cause entire network to fail. More cable of wire required. Advantages Disadvantages
- 25. In the tree topology groups of star network are connected to linear Bus backbone. This particularly helpful for colleges, universities or schools. Point to point connections are possible in the tree topology. TREE TOPOLOGY
- 26. TREE TOPOLOGY
- 27. Point to point wiring for each device. Use for the large network. More expensive than other topology. Fail in backbone affects the entire network. Advantages Disadvantage
- 28. Each node is connected to every other node in the network. Implement mesh topology expensive and difficult. While the data is traveling on the mesh network it is automatically configured to reach the destination by taking the shortest route which means the lest numbers of hobs. MESH TOPOLOGY
- 30. Entire network does not affected by one faulty device. Provide redundant paths which helps in sending data using an alternate path if a specific path fails sending the data. Very expensive. More cabling is required. Advantages Disadvantages
- 31. It is combination of different network topology. It is also known as special topology. It always accrues when two different basic network topologies are connected. Useful for corporate offices to link their LANs together while adding networks through wide area network. HYBRID TOPOLOGY
- 32. HYBRID TOPOLOGY
- 33. Easy to detect and remove faulty device. More flexible. Handle large traffic. More cabling is required. Expensive then other topologies. Asvantages Disadvantages
- 34. Set of rules. Two devices on a network to successfully communicate, the must both understood the same protocols. TCP/IP- transmission control protocol internet – it is most commonly used set of rules. Protocols
- 35. Every signals that sends & receive the data must have specific address called MAC address. MAC address is a 12 digit hexadecimal number. It can be written in any one of the formats. 00:11:11:EA:8D:F6 00-11-11-EC-8D-F6 MAC ADDRESS
- 36. 32 bit long. It contains 4 octets. Dot(.) is used to separate one octet from another. IP ADDRESS Network ID Host ID (shared by network ) (unique to every device) Ex.- 134.56.33.44 134.56.145.36 IP ADDRESS
- 37. Class A- network. host. host. host Class B- network. network. host. host Class C- network. network. network. host Class D & Class E indicate network ID. IP address exit from 0.0.0.0 to 255.255.255.255 NOTE:- IP address may vary in time for one device. The MAC address or hardware address is “branded” on the device by the manufacture. IP+MAC address together to ensure proper identification of a device. CLASSES OF IP ADDRESS
- 38. THANKYOU

