NFF-GO (YANFF) - Yet Another Network Function Framework
- 1. Intel Golang Team Gregory Shimansky
- 2. Copyright © 2017, Intel Corporation. All rights reserved. *Other names and brands may be claimed as the property of others. Legal Information Intel technologies’ features and benefits depend on system configuration and may require enabled hardware, software or service activation. Learn more at intel.com, or from the OEM or retailer. No computer system can be absolutely secure. Software and workloads used in performance tests may have been optimized for performance only on Intel microprocessors. Performance tests, such as SYSmark and MobileMark, are measured using specific computer systems, components, software, operations and functions. Any change to any of those factors may cause the results to vary. You should consult other information and performance tests to assist you in fully evaluating your contemplated purchases, including the performance of that product when combined with other products. For more complete information visit http://www.intel.com/performance. Tests document performance of components on a particular test, in specific systems. Differences in hardware, software, or configuration will affect actual performance. Consult other sources of information to evaluate performance as you consider your purchase. For more complete information about performance and benchmark results, visit http://www.intel.com/performance. Cost reduction scenarios described are intended as examples of how a given Intel- based product, in the specified circumstances and configurations, may affect future costs and provide cost savings. Circumstances will vary. Intel does not guarantee any costs or cost reduction. Results have been estimated or simulated using internal Intel analysis or architecture simulation or modeling, and provided to you for informational purposes. Any differences in your system hardware, software or configuration may affect your actual performance. Intel does not control or audit third-party benchmark data or the web sites referenced in this document. You should visit the referenced web site and confirm whether referenced data are accurate. Intel, the Intel logo and others are trademarks of Intel Corporation in the U.S. and/or other countries. *Other names and brands may be claimed as the property of others. © 2017 Intel Corporation.
- 3. Copyright © 2017, Intel Corporation. All rights reserved. *Other names and brands may be claimed as the property of others. YANFF - Yet Another Network Function Framework Framework for building performant native network functions • Open-source project • Higher level abstractions than DPDK • Go language: productivity, performance, concurrency, safety • Network functions are application programs and not virtual machines Benefits: • Easily leverage IA HW capabilities: multi-cores, AES-NI, CAT, QAT, DPDK • 10x reduction lines of code • No need to be expert network system programmer • Similar performance with C • Take advantage of cloud native deployment: continuous delivery, micro- services, containers https://github.com/intel-go/yanff 3
- 4. Copyright © 2017, Intel Corporation. All rights reserved. *Other names and brands may be claimed as the property of others. 4 Technical Motivation ▪ Developers need framework to shorten development cycle of VNFs – Currently VNFs are monolithic - “virtual appliances” instead of network functions – Significant part of VNF is about plumbing. Plumbing VNFs to CommSPs network is an art. Should be abstracted from VNFs ▪ Lack of stable and unified APIs for VNF control and data plane ▪ Challenges with access to HW Accelerators in cloud environment. ▪ Cloud-friendly APIs and designs needed. Accelerating transition to from rule-based networking to imperative networking https://github.com/intel-go/yanff
- 5. Copyright © 2017, Intel Corporation. All rights reserved. *Other names and brands may be claimed as the property of others. YANFF: Yet Another Network Function Framework • Simple but powerful abstractions: • Flow, Packet • User builds packet processing graph using “flow functions” chaining • SetReceiver -> SetHandler -> SetSender • Several predefined possibilities of adding user processing inside packet processing graph • Split, Separate, Generate, Handle • Can leverage predefined functions which parse packets, check ACL rules, etc. • Run to completion – NFs can be expressed in the flow functions and natural chaining • Auto-scaling, ease of development • Zero-copy between NFs • Flexible incoming flow handling – sources can be anything: network port, memory buffer, remote procedure call, etc. System SW Optimized SW Application IA PlatformIA Platform Optimized Platform Software Optimized Software on CPU ISA (e.g. AES, AVX) Standard NIC Accelerators (Intel® QAT) Application Smart NIC Integrated FPGA U P I YANFF 4https://github.com/intel-go/yanff
- 6. Copyright © 2017, Intel Corporation. All rights reserved. *Other names and brands may be claimed as the property of others. L3 Simple Forwarding Example var L3Rules *rules.L3Rules func main() { flow.SystemInit(16) L3Rules = rules.GetL3RulesFromORIG("Forwarding.conf") inputFlow := flow.SetReceiver(0) outputFlows := flow.SetSplitter(inputFlow, L3Splitter, uint(3)) flow.SetStopper(outputFlows[0]) for i := 1; i < 3; i++ { flow.SetSender(outputFlows[i], uint8(i-1)) } flow.SystemStart() } // User defined function for splitting packets func L3Splitter(currentPacket *packet.Packet) uint { currentPacket.ParseL4() return rules.L3_ACL_port(currentPacket, L3Rules) }
- 7. Copyright © 2017, Intel Corporation. All rights reserved. *Other names and brands may be claimed as the property of others. Configuration file for Forwarding # Source address, Destination address, L4 protocol ID, Source port, Destination port, Output port 111.2.0.0/31 ANY tcp ANY ANY 1 111.2.0.2/32 ANY tcp ANY ANY Reject ANY ANY udp 3078:3964 56:61020 2
- 8. Copyright © 2017, Intel Corporation. All rights reserved. *Other names and brands may be claimed as the property of others. Exactly The Same Example in DPDK/C … 10 more screens to get to the end… 23 SLOC in YANFF vs 2079 in DPDK/C!
- 9. Copyright © 2016, Intel Corporation. All rights reserved. *Other names and brands may be claimed as the property of others. Optimization Notice YANFF – Main Architectural Concepts Flow Abstraction without public fields, which is used for pointing connections between Flow functions. Opened by Receive / Split / Separate / Counter / Generate. Closed by Send / Merge / Stop. Packet High-level representation of network packet. Private field is *mbuf, public fields are mac / ip / data /etc: pointers to mbuf with offsets (zero copy). Is extracted before any User defined function. Can be filled after user request by Packet functions. Can be checked by Rule functions. Port Network door, used in Receive, Send. Rule Set of checking rules, used in User defined functions.
- 10. Copyright © 2016, Intel Corporation. All rights reserved. *Other names and brands may be claimed as the property of others. Optimization Notice 10 Building Processing Graph Separate(SeparateFunction) {input stay} -> Flow Flow -> SeparateFunction -> Flow Merge Flow -> Flow -> Flow Flow -> Partition (periodicity) -> Flow Flow -> calculation -> Flow Split (SplitFunction) {input closed} -> Flow Flow -> SplitFunction -> Flow -> Flow Generate (GenerateFunction) {can wait} GenerateFunction -> Flow Stop Flow -> drop Receive (Port) driver (loop) -> Flow Send (Port) Flow -> driver (loop) Read (File) PCAP file -> Flow Write (File) Flow -> PCAP file
- 11. Copyright © 2016, Intel Corporation. All rights reserved. *Other names and brands may be claimed as the property of others. Optimization Notice 11 Packet modification functions Handle (SeparateFunction) {can drop} -> Stop Flow -> SeparateFunction-> Flow Handle (HandleFunction) {can’t drop} Flow -> HandleFunction -> Flow Packet functions Parsing packet fields Parse L2 or/and L3 or/and L4 levels Checking packet fields by rule Check L2 or/and L3 or/and L4 levels Create rule Create checking rule from json / config Initializing packet fields Initialize L2 or/and L3 or/and L4 levels Rule functions Encapsulate / Decapsulate
- 12. Copyright © 2016, Intel Corporation. All rights reserved. *Other names and brands may be claimed as the property of others. Optimization Notice 12 Flow Graph Example - Forwarding 1 Receiver 2 Splitter 3 Stop 3 3 Send Send
- 13. Copyright © 2016, Intel Corporation. All rights reserved. *Other names and brands may be claimed as the property of others. Optimization Notice 13 Let’s build some functions!
- 14. Copyright © 2016, Intel Corporation. All rights reserved. *Other names and brands may be claimed as the property of others. Optimization Notice 14 Create test VMs 1.Create and provision two test VMs: $ cd $GOPATH/src/github.com/intel-go/yanff/vagrant $ vagrant up 2.Open two terminal windows 3.cd to vagrant directory below 4.run “vagrant ssh yanf-”VM_number” to connect to pktgen VM and target VM, e.g. $ vagrant ssh yanff-1 # YANFF test program host yanff-1$ bindports # if ports not bound yet $ vagrant ssh yanff-0 # pktgen host yanff-0$ bindports # if ports not bound yet
- 15. Copyright © 2017, Intel Corporation. All rights reserved. *Other names and brands may be claimed as the property of others. Let’s try (1 of 11) Flow graph: package main import "github.com/intel-go/yanff/flow" func main() { // Init YANFF system config := flow.Config{} checkFatal(flow.SystemInit(&config)) initCommonState() checkFatal(flow.SystemStart()) } 15 yanff-0$ cd $YANFF/examples/tutorial yanff-0$ ./genscripts yanff-0$ ./runpktgen.sh Pktgen:/> start 0 …… Pktgen:/> quit yanff-1$ cd $YANFF/examples/tutorial yanff-1$ sudo ./step1
- 16. Copyright © 2017, Intel Corporation. All rights reserved. *Other names and brands may be claimed as the property of others. Let’s try (2 of 11) Flow graph: Receive Send package main import "github.com/intel-go/yanff/flow" func main() { config := flow.Config{} checkFatal(flow.SystemInit(&config)) initCommonState() firstFlow, err := flow.SetReceiver(0) checkFatal(err) checkFatal(flow.SetHandler(firstFlow, modifyPacket[0], nil)) checkFatal(flow.SetSender(firstFlow, 0)) checkFatal(flow.SystemStart()) } 16 yanff-0$ ./runpktgen.sh Pktgen:/> load step2.pg Pktgen:/> start 0 … Pktgen:/> quit yanff-1$ sudo ./step2 Modify
- 17. Copyright © 2017, Intel Corporation. All rights reserved. *Other names and brands may be claimed as the property of others. Let’s try (3 of 11) Flow graph: Receive Send Partition Send package main import "github.com/intel-go/yanff/flow" func main() { config := flow.Config{} checkFatal(flow.SystemInit(&config)) initCommonState() firstFlow, err := flow.SetReceiver(0) checkFatal(err) secondFlow, err := flow.SetPartitioner(firstFlow, 300, 300) checkFatal(err) checkFatal(flow.SetHandler(firstFlow, modifyPacket[0], nil)) checkFatal(flow.SetHandler(secondFlow, modifyPacket[1], nil)) checkFatal(flow.SetSender(firstFlow, 0)) checkFatal(flow.SetSender(secondFlow, 1)) checkFatal(flow.SystemStart()) } 17 yanff-0$ ./runpktgen.sh Pktgen:/> load step3.pg Pktgen:/> start 0 … Pktgen:/> quit yanff-1$ sudo ./step3 Modify Modify
- 18. Copyright © 2017, Intel Corporation. All rights reserved. *Other names and brands may be claimed as the property of others. Let’s try (4 of 11) package main import "github.com/intel-go/yanff/flow“ import "github.com/intel-go/yanff/packet“ func main() { config := flow.Config{} checkFatal(flow.SystemInit(&config)) initCommonState() firstFlow, err := flow.SetReceiver(0) checkFatal(err) secondFlow, err := flow.SetSeparator(firstFlow, mySeparator, nil) checkFatal(err) checkFatal(flow.SetHandler(firstFlow, modifyPacket[0], nil)) checkFatal(flow.SetHandler(secondFlow, modifyPacket[1], nil)) checkFatal(flow.SetSender(firstFlow, 0)) checkFatal(flow.SetSender(secondFlow, 1)) checkFatal(flow.SystemStart()) } func mySeparator(cur *packet.Packet, ctx flow.UserContext) bool { cur.ParseL3() if cur.GetIPv4() != nil { cur.ParseL4ForIPv4() if cur.GetTCPForIPv4() != nil && packet.SwapBytesUint16(cur.GetTCPForIPv4().DstPort) == 53 { return false } } return true } Flow graph: Receive Send Separate Send 18 yanff-0$ ./runpktgen.sh Pktgen:/> load step4.pg Pktgen:/> start 0 … Pktgen:/> quit yanff-1$ sudo ./step4 Modify Modify
- 19. Copyright © 2017, Intel Corporation. All rights reserved. *Other names and brands may be claimed as the property of others. Let’s try (5 of 11) … … … import "github.com/intel-go/yanff/rules“ var L3Rules *rules.L3Rules func main() { var err error config := flow.Config{} checkFatal(flow.SystemInit(&config)) initCommonState() l3Rules, err = packet.GetL3ACLFromORIG("rules1.conf") checkFatal(err) firstFlow, err := flow.SetReceiver(0) checkFatal(err) secondFlow, err := flow.SetSeparator(firstFlow, mySeparator, nil) checkFatal(err) checkFatal(flow.SetHandler(firstFlow, modifyPacket[0], nil)) checkFatal(flow.SetHandler(secondFlow, modifyPacket[1], nil)) checkFatal(flow.SetSender(firstFlow, 0)) checkFatal(flow.SetSender(secondFlow, 1)) checkFatal(flow.SystemStart()) } func MySeparator(cur *packet.Packet, ctx flow.UserContext) bool { return cur.L3ACLPermit(l3Rules) } Flow graph: Receive Send Separate Send Rules 19 yanff-0$ ./runpktgen.sh Pktgen:/> load step5.pg Pktgen:/> start 0 … Pktgen:/> quit yanff-1$ sudo ./step5 Modify Modify
- 20. Copyright © 2017, Intel Corporation. All rights reserved. *Other names and brands may be claimed as the property of others. Let’s try (6 of 11) … … … func main() { var err error config := flow.Config{} checkFatal(flow.SystemInit(&config)) L3Rules = rules.GetL3RulesFromORIG(“rules1.conf") checkFatal(err) firstFlow, err := flow.SetReceiver(0) checkFatal(err) secondFlow, err := flow.SetSeparator(firstFlow, mySeparator, nil) checkFatal(err) checkFatal(flow.SetHandler(firstFlow, modifyPacket[0], nil)) checkFatal(flow.SetSender(firstFlow, 0)) checkFatal(flow.SetStopper(secondFlow)) checkFatal(flow.SystemStart()) } func MySeparator(cur *packet.Packet, ctx flow.UserContext) bool { return cur.L3ACLPermit(l3Rules) } Flow graph: Receive Send Separate Stop Rules 20 yanff-0$ ./runpktgen.sh Pktgen:/> load step6.pg Pktgen:/> start 0 … Pktgen:/> quit yanff-1$ sudo ./step6 Modify
- 21. Copyright © 2017, Intel Corporation. All rights reserved. *Other names and brands may be claimed as the property of others. Let’s try (7 of 11) … … … import “time” var rulesp unsafe.Pointer … … … l3Rules, err := packet.GetL3ACLFromORIG("rules1.conf") checkFatal(err) rulesp = unsafe.Pointer(&l3Rules) go updateSeparateRules() … … … func MySeparator(cur *packet.Packet, ctx flow.UserContext) bool { localL3Rules := (*packet.L3Rules)(atomic.LoadPointer(&rulesp)) return cur.L3ACLPermit(localL3Rules) } func updateSeparateRules() { for { time.Sleep(time.Second * 5) locall3Rules, err := packet.GetL3ACLFromORIG("rules1.conf") checkFatal(err) atomic.StorePointer(&rulesp, unsafe.Pointer(locall3Rules)) } } Flow graph: Receive Send Separate Stop updated Rules 21 yanff-0$ ./runpktgen.sh Pktgen:/> load step7.pg Pktgen:/> start 0 … Pktgen:/> quit yanff-1$ sudo ./step7 Modify To make changes in rules1.conf file it is necessary to connect to target VM in another window or run YANFF executable in screen terminal multiplexer.
- 22. Copyright © 2017, Intel Corporation. All rights reserved. *Other names and brands may be claimed as the property of others. Let’s try (8 of 11) … … … const flowN = 3 … … … firstFlow, err := flow.SetReceiver(0) checkFatal(err) outputFlows, err := flow.SetSplitter(firstFlow, mySplitter, flowN, nil) checkFatal(err) checkFatal(flow.SetStopper(outputFlows[0])) for i := uint8(1); i < flowN; i++ { checkFatal(flow.SetHandler(outputFlows[i], modifyPacket[i-1], nil)) checkFatal(flow.SetSender(outputFlows[i], i-1)) } … … … func mySplitter(cur *packet.Packet, ctx flow.UserContext) uint { localL3Rules := L3Rules return cur.L3ACLPort(localL3Rules) } … … … Flow graph: Receive Stop Split Send updated Rules Send 22 yanff-0$ ./runpktgen.sh Pktgen:/> load step8.pg Pktgen:/> start 0 … Pktgen:/> quit yanff-1$ sudo ./step8 Modify Modify To make changes in rules2.conf file it is necessary to connect to target VM in another window or run YANFF executable in screen terminal multiplexer.
- 23. Copyright © 2017, Intel Corporation. All rights reserved. *Other names and brands may be claimed as the property of others. Let’s try (9 of 11) … … … import "github.com/intel-go/yanff/common“ … … … firstFlow, err := flow.SetReceiver(0) checkFatal(err) outputFlows, err := flow.SetSplitter(firstFlow, mySplitter, flowN, nil) checkFatal(err) checkFatal(flow.SetStopper(outputFlows[0])) checkFatal(flow.SetHandler(outputFlows[1], myHandler, nil)) for i := uint8(1); i < flowN; i++ { checkFatal(flow.SetHandler(outputFlows[i], modifyPacket[i-1], nil)) checkFatal(flow.SetSender(outputFlows[i], i-1)) } … … … func myHandler(cur *packet.Packet, ctx flow.UserContext) { cur.EncapsulateHead(common.EtherLen, common.IPv4MinLen) cur.ParseL3() cur.GetIPv4NoCheck().SrcAddr = packet.BytesToIPv4(111, 22, 3, 0) cur.GetIPv4NoCheck().DstAddr = packet.BytesToIPv4(3, 22, 111, 0) cur.GetIPv4NoCheck().VersionIhl = 0x45 cur.GetIPv4NoCheck().NextProtoID = 0x04 } Flow graph: Receive Send Split Send updated Rules Stop Handle 23 yanff-0$ ./runpktgen.sh Pktgen:/> load step9.pg Pktgen:/> start 0 … Pktgen:/> quit yanff-1$ sudo ./step9 ModifyModify To make changes in rules2.conf file it is necessary to connect to target VM in another window or run YANFF executable in screen terminal multiplexer.
- 24. Copyright © 2017, Intel Corporation. All rights reserved. *Other names and brands may be claimed as the property of others. Let’s try (10 of 11) … … … func myHandler(curV []*packet.Packet, num uint, ctx flow.UserContext) { for i := uint(0); i < num; i++ { cur := curV[i] cur.EncapsulateHead(common.EtherLen, common.IPv4MinLen) cur.ParseL3() cur.GetIPv4NoCheck().SrcAddr = packet.BytesToIPv4(111, 22, 3, 0) cur.GetIPv4NoCheck().DstAddr = packet.BytesToIPv4(3, 22, 111, 0) cur.GetIPv4NoCheck().VersionIhl = 0x45 cur.GetIPv4NoCheck().NextProtoID = 0x04 } } Flow graph: Receive Send Split Send updated Rules Stop Handle Packet vector 24 yanff-0$ ./runpktgen.sh Pktgen:/> load step10.pg Pktgen:/> start 0 … Pktgen:/> quit yanff-1$ sudo ./step10 Modify Modify To make changes in rules2.conf file it is necessary to connect to target VM in another window or run YANFF executable in screen terminal multiplexer.
- 25. Copyright © 2017, Intel Corporation. All rights reserved. *Other names and brands may be claimed as the property of others. Let’s try (11 of 11) … … … func myHandler(curV []*packet.Packet, num uint, ctx flow.UserContext) { for i := uint(0); i < num; i++ { cur := curV[i] cur.EncapsulateHead(common.EtherLen, common.IPv4MinLen) cur.ParseL3() cur.GetIPv4NoCheck().SrcAddr = packet.BytesToIPv4(111, 22, 3, 0) cur.GetIPv4NoCheck().DstAddr = packet.BytesToIPv4(3, 22, 111, 0) cur.GetIPv4NoCheck().VersionIhl = 0x45 cur.GetIPv4NoCheck().NextProtoID = 0x04 } // Some heavy computational code heavyCode() } Flow graph: Receive Send Split Send updated Rules Stop Handle Packet vector Scaling 25 yanff-0$ ./runpktgen.sh Pktgen:/> load step11.pg Pktgen:/> start 0 … Pktgen:/> quit yanff-1$ sudo ./step11 Modify Modify To make changes in rules2.conf file it is necessary to connect to target VM in another window or run YANFF executable in screen terminal multiplexer.
- 26. Copyright © 2017, Intel Corporation. All rights reserved. *Other names and brands may be claimed as the property of others. Finally: NAT 26 yanff-0$ ./runpktgen.sh Pktgen:/> load nat.pg Pktgen:/> start 0 Pktgen:/> start 1 … Pktgen:/> quit yanff-1$ ./genscripts -pktgen direct yanff-1$ sudo ../nat/main/nat -config nat.json
- 27. Copyright © 2017, Intel Corporation. All rights reserved. *Other names and brands may be claimed as the property of others. Q & A ? 27
- 28. Copyright © 2017, Intel Corporation. All rights reserved. *Other names and brands may be claimed as the property of others. Optimization Notice 28 Optimization Notice Intel’s compilers may or may not optimize to the same degree for non-Intel microprocessors for optimizations that are not unique to Intel microprocessors. These optimizations include SSE2®, SSE3, and SSSE3 instruction sets and other optimizations. Intel does not guarantee the availability, functionality, or effectiveness of any optimization on microprocessors not manufactured by Intel. Microprocessor-dependent optimizations in this product are intended for use with Intel microprocessors. Certain optimizations not specific to Intel microarchitecture are reserved for Intel microprocessors. Please refer to the applicable product User and Reference Guides for more information regarding the specific instruction sets covered by this notice. Notice revision #20110804
- 29. Basic components • External (bytes inside network) • Flow (*mbufs inside rings) • Packets (as function arguments) Send (Port) Flow -> driver (loop) Receive (Port) driver (loop) -> Flow Stop Flow -> free Separate(SeparateFunction) {input stay} -> Flow Flow -> SeparateFunction -> Flow Merge {slow} Flow -> Flow -> Flow User defined functions Separate Function * -> Packet -> Boolean value -> Handle Function * -> Packet -> Flow functions Handle (SeparateFunction) {can drop} -> Stop Flow -> SeparateFunction-> Flow Generate (GenerateFunction) {can wait} GenerateFunction -> Flow Connections bool Packet functions Parsing packet fields Parse L2 or/and L3 or/and L4 levels Partition (periodicity) -> Flow Flow -> calculation -> Flow Instances (new types) Flow Abstraction without public fields, which is used for pointing connections between Flow functions. Opened by Receive / Split / Separate / Counter / Generate. Closed by Send / Merge / Stop. Packet High-level representation of network packet. Private field is *mbuf, public fields are mac / ip / data /etc: pointers to mbuf with offsets (zero copy). Is extracted before any User defined function. Can be filled after user request by Packet functions. Can be checked by Rule functions. Split Function -> Packet -> № of Flow -> uint Split (SplitFunction) {input closed} -> Flow Flow -> SplitFunction -> Flow -> Flow Checking packet fields by rule Check L2 or/and L3 or/and L4 levels • Flow: type “Flow” Init, Starting, Checking, Flow functions • Packet: type “Packet”, parsing / initializing packet functions • Rules: type “Rule”, parsing rules / checking Packet functions • User package: user defined functions Library External Components Create rule Create checking rule from json / config • Scheduler: Cloning of user defined flow functions • Asm: assembler functions added to GO • Common: technical functions shared by other components • Low: connections with DPDK C implementation Library Internal ComponentsHandle (HandleFunction) {can’t drop} Flow -> HandleFunction -> Flow Port Network door, used in Receive, Send. Initializing packet fields Initialize L2 or/and L3 or/and L4 levels Rule functions Rule Set of checking rules, used in User defined functions. Encapsulate / Decapsulate Generate Function * Packet -> * Can process vector of packets at one time All functions take packet and handling context All functions at separate cores and can be cloned
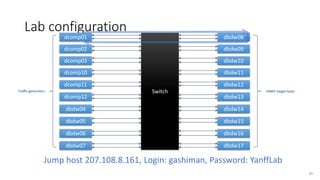
- 30. Lab configuration dcomp01 Switch dcomp02 dcomp03 dcomp10 dcomp11 dcomp12 dbdw04 dbdw05 dbdw06 dbdw07 dbdw08 dbdw09 dbdw10 dbdw11 dbdw12 dbdw13 dbdw14 dbdw15 dbdw16 dbdw17 Traffic generators 30 YANFF target hosts Jump host 207.108.8.161, Login: gashiman, Password: YanffLab
- 31. Finally (2 of 2): ipsec • Showing ipsec example 31





![Copyright © 2017, Intel Corporation. All rights reserved.
*Other names and brands may be claimed as the property of others.
L3 Simple Forwarding Example
var L3Rules *rules.L3Rules
func main() {
flow.SystemInit(16)
L3Rules = rules.GetL3RulesFromORIG("Forwarding.conf")
inputFlow := flow.SetReceiver(0)
outputFlows := flow.SetSplitter(inputFlow, L3Splitter, uint(3))
flow.SetStopper(outputFlows[0])
for i := 1; i < 3; i++ {
flow.SetSender(outputFlows[i], uint8(i-1))
}
flow.SystemStart()
}
// User defined function for splitting packets
func L3Splitter(currentPacket *packet.Packet) uint {
currentPacket.ParseL4()
return rules.L3_ACL_port(currentPacket, L3Rules)
}](https://image.slidesharecdn.com/locyanffinalpresentation-190211191004/85/NFF-GO-YANFF-Yet-Another-Network-Function-Framework-6-320.jpg)









![Copyright © 2017, Intel Corporation. All rights reserved.
*Other names and brands may be claimed as the property of others.
Let’s try (2 of 11)
Flow graph:
Receive
Send
package main
import "github.com/intel-go/yanff/flow"
func main() {
config := flow.Config{}
checkFatal(flow.SystemInit(&config))
initCommonState()
firstFlow, err := flow.SetReceiver(0)
checkFatal(err)
checkFatal(flow.SetHandler(firstFlow, modifyPacket[0], nil))
checkFatal(flow.SetSender(firstFlow, 0))
checkFatal(flow.SystemStart())
}
16
yanff-0$ ./runpktgen.sh
Pktgen:/> load step2.pg
Pktgen:/> start 0
…
Pktgen:/> quit
yanff-1$ sudo ./step2
Modify](https://image.slidesharecdn.com/locyanffinalpresentation-190211191004/85/NFF-GO-YANFF-Yet-Another-Network-Function-Framework-16-320.jpg)
![Copyright © 2017, Intel Corporation. All rights reserved.
*Other names and brands may be claimed as the property of others.
Let’s try (3 of 11)
Flow graph:
Receive
Send
Partition
Send
package main
import "github.com/intel-go/yanff/flow"
func main() {
config := flow.Config{}
checkFatal(flow.SystemInit(&config))
initCommonState()
firstFlow, err := flow.SetReceiver(0)
checkFatal(err)
secondFlow, err := flow.SetPartitioner(firstFlow, 300, 300)
checkFatal(err)
checkFatal(flow.SetHandler(firstFlow, modifyPacket[0], nil))
checkFatal(flow.SetHandler(secondFlow, modifyPacket[1], nil))
checkFatal(flow.SetSender(firstFlow, 0))
checkFatal(flow.SetSender(secondFlow, 1))
checkFatal(flow.SystemStart())
}
17
yanff-0$ ./runpktgen.sh
Pktgen:/> load step3.pg
Pktgen:/> start 0
…
Pktgen:/> quit
yanff-1$ sudo ./step3
Modify Modify](https://image.slidesharecdn.com/locyanffinalpresentation-190211191004/85/NFF-GO-YANFF-Yet-Another-Network-Function-Framework-17-320.jpg)
![Copyright © 2017, Intel Corporation. All rights reserved.
*Other names and brands may be claimed as the property of others.
Let’s try (4 of 11)
package main
import "github.com/intel-go/yanff/flow“
import "github.com/intel-go/yanff/packet“
func main() {
config := flow.Config{}
checkFatal(flow.SystemInit(&config))
initCommonState()
firstFlow, err := flow.SetReceiver(0)
checkFatal(err)
secondFlow, err := flow.SetSeparator(firstFlow, mySeparator, nil)
checkFatal(err)
checkFatal(flow.SetHandler(firstFlow, modifyPacket[0], nil))
checkFatal(flow.SetHandler(secondFlow, modifyPacket[1], nil))
checkFatal(flow.SetSender(firstFlow, 0))
checkFatal(flow.SetSender(secondFlow, 1))
checkFatal(flow.SystemStart())
}
func mySeparator(cur *packet.Packet, ctx flow.UserContext) bool {
cur.ParseL3()
if cur.GetIPv4() != nil {
cur.ParseL4ForIPv4()
if cur.GetTCPForIPv4() != nil && packet.SwapBytesUint16(cur.GetTCPForIPv4().DstPort) ==
53 {
return false
}
}
return true
}
Flow graph:
Receive
Send
Separate
Send
18
yanff-0$ ./runpktgen.sh
Pktgen:/> load step4.pg
Pktgen:/> start 0
…
Pktgen:/> quit
yanff-1$ sudo ./step4
Modify Modify](https://image.slidesharecdn.com/locyanffinalpresentation-190211191004/85/NFF-GO-YANFF-Yet-Another-Network-Function-Framework-18-320.jpg)
![Copyright © 2017, Intel Corporation. All rights reserved.
*Other names and brands may be claimed as the property of others.
Let’s try (5 of 11) … … …
import "github.com/intel-go/yanff/rules“
var L3Rules *rules.L3Rules
func main() {
var err error
config := flow.Config{}
checkFatal(flow.SystemInit(&config))
initCommonState()
l3Rules, err = packet.GetL3ACLFromORIG("rules1.conf")
checkFatal(err)
firstFlow, err := flow.SetReceiver(0)
checkFatal(err)
secondFlow, err := flow.SetSeparator(firstFlow, mySeparator, nil)
checkFatal(err)
checkFatal(flow.SetHandler(firstFlow, modifyPacket[0], nil))
checkFatal(flow.SetHandler(secondFlow, modifyPacket[1], nil))
checkFatal(flow.SetSender(firstFlow, 0))
checkFatal(flow.SetSender(secondFlow, 1))
checkFatal(flow.SystemStart())
}
func MySeparator(cur *packet.Packet, ctx flow.UserContext) bool {
return cur.L3ACLPermit(l3Rules)
}
Flow graph:
Receive
Send
Separate
Send
Rules
19
yanff-0$ ./runpktgen.sh
Pktgen:/> load step5.pg
Pktgen:/> start 0
…
Pktgen:/> quit
yanff-1$ sudo ./step5
Modify Modify](https://image.slidesharecdn.com/locyanffinalpresentation-190211191004/85/NFF-GO-YANFF-Yet-Another-Network-Function-Framework-19-320.jpg)
![Copyright © 2017, Intel Corporation. All rights reserved.
*Other names and brands may be claimed as the property of others.
Let’s try (6 of 11) … … …
func main() {
var err error
config := flow.Config{}
checkFatal(flow.SystemInit(&config))
L3Rules = rules.GetL3RulesFromORIG(“rules1.conf")
checkFatal(err)
firstFlow, err := flow.SetReceiver(0)
checkFatal(err)
secondFlow, err := flow.SetSeparator(firstFlow, mySeparator, nil)
checkFatal(err)
checkFatal(flow.SetHandler(firstFlow, modifyPacket[0], nil))
checkFatal(flow.SetSender(firstFlow, 0))
checkFatal(flow.SetStopper(secondFlow))
checkFatal(flow.SystemStart())
}
func MySeparator(cur *packet.Packet, ctx flow.UserContext) bool {
return cur.L3ACLPermit(l3Rules)
}
Flow graph:
Receive
Send
Separate
Stop
Rules
20
yanff-0$ ./runpktgen.sh
Pktgen:/> load step6.pg
Pktgen:/> start 0
…
Pktgen:/> quit
yanff-1$ sudo ./step6
Modify](https://image.slidesharecdn.com/locyanffinalpresentation-190211191004/85/NFF-GO-YANFF-Yet-Another-Network-Function-Framework-20-320.jpg)

![Copyright © 2017, Intel Corporation. All rights reserved.
*Other names and brands may be claimed as the property of others.
Let’s try (8 of 11)
… … …
const flowN = 3
… … …
firstFlow, err := flow.SetReceiver(0)
checkFatal(err)
outputFlows, err := flow.SetSplitter(firstFlow, mySplitter, flowN, nil)
checkFatal(err)
checkFatal(flow.SetStopper(outputFlows[0]))
for i := uint8(1); i < flowN; i++ {
checkFatal(flow.SetHandler(outputFlows[i], modifyPacket[i-1], nil))
checkFatal(flow.SetSender(outputFlows[i], i-1))
}
… … …
func mySplitter(cur *packet.Packet, ctx flow.UserContext) uint { localL3Rules := L3Rules
return cur.L3ACLPort(localL3Rules)
}
… … …
Flow graph:
Receive
Stop
Split
Send
updated
Rules
Send
22
yanff-0$ ./runpktgen.sh
Pktgen:/> load step8.pg
Pktgen:/> start 0
…
Pktgen:/> quit
yanff-1$ sudo ./step8
Modify
Modify
To make changes in rules2.conf file it is necessary to
connect to target VM in another window or run YANFF
executable in screen terminal multiplexer.](https://image.slidesharecdn.com/locyanffinalpresentation-190211191004/85/NFF-GO-YANFF-Yet-Another-Network-Function-Framework-22-320.jpg)
![Copyright © 2017, Intel Corporation. All rights reserved.
*Other names and brands may be claimed as the property of others.
Let’s try (9 of 11)
… … …
import "github.com/intel-go/yanff/common“
… … …
firstFlow, err := flow.SetReceiver(0)
checkFatal(err)
outputFlows, err := flow.SetSplitter(firstFlow, mySplitter, flowN, nil)
checkFatal(err)
checkFatal(flow.SetStopper(outputFlows[0]))
checkFatal(flow.SetHandler(outputFlows[1], myHandler, nil))
for i := uint8(1); i < flowN; i++ {
checkFatal(flow.SetHandler(outputFlows[i], modifyPacket[i-1], nil))
checkFatal(flow.SetSender(outputFlows[i], i-1))
}
… … …
func myHandler(cur *packet.Packet, ctx flow.UserContext) {
cur.EncapsulateHead(common.EtherLen, common.IPv4MinLen)
cur.ParseL3()
cur.GetIPv4NoCheck().SrcAddr = packet.BytesToIPv4(111, 22, 3, 0)
cur.GetIPv4NoCheck().DstAddr = packet.BytesToIPv4(3, 22, 111, 0)
cur.GetIPv4NoCheck().VersionIhl = 0x45
cur.GetIPv4NoCheck().NextProtoID = 0x04
}
Flow graph:
Receive
Send
Split
Send
updated
Rules
Stop
Handle
23
yanff-0$ ./runpktgen.sh
Pktgen:/> load step9.pg
Pktgen:/> start 0
…
Pktgen:/> quit
yanff-1$ sudo ./step9
ModifyModify
To make changes in rules2.conf file it is necessary to
connect to target VM in another window or run YANFF
executable in screen terminal multiplexer.](https://image.slidesharecdn.com/locyanffinalpresentation-190211191004/85/NFF-GO-YANFF-Yet-Another-Network-Function-Framework-23-320.jpg)
![Copyright © 2017, Intel Corporation. All rights reserved.
*Other names and brands may be claimed as the property of others.
Let’s try (10 of 11) … … …
func myHandler(curV []*packet.Packet, num uint, ctx flow.UserContext) {
for i := uint(0); i < num; i++ {
cur := curV[i]
cur.EncapsulateHead(common.EtherLen, common.IPv4MinLen)
cur.ParseL3()
cur.GetIPv4NoCheck().SrcAddr = packet.BytesToIPv4(111, 22, 3, 0)
cur.GetIPv4NoCheck().DstAddr = packet.BytesToIPv4(3, 22, 111, 0)
cur.GetIPv4NoCheck().VersionIhl = 0x45
cur.GetIPv4NoCheck().NextProtoID = 0x04
}
}
Flow graph:
Receive
Send
Split
Send
updated
Rules
Stop
Handle
Packet
vector
24
yanff-0$ ./runpktgen.sh
Pktgen:/> load step10.pg
Pktgen:/> start 0
…
Pktgen:/> quit
yanff-1$ sudo ./step10
Modify Modify
To make changes in rules2.conf file it is necessary to
connect to target VM in another window or run YANFF
executable in screen terminal multiplexer.](https://image.slidesharecdn.com/locyanffinalpresentation-190211191004/85/NFF-GO-YANFF-Yet-Another-Network-Function-Framework-24-320.jpg)
![Copyright © 2017, Intel Corporation. All rights reserved.
*Other names and brands may be claimed as the property of others.
Let’s try (11 of 11) … … …
func myHandler(curV []*packet.Packet, num uint, ctx flow.UserContext) {
for i := uint(0); i < num; i++ {
cur := curV[i]
cur.EncapsulateHead(common.EtherLen, common.IPv4MinLen)
cur.ParseL3()
cur.GetIPv4NoCheck().SrcAddr = packet.BytesToIPv4(111, 22, 3, 0)
cur.GetIPv4NoCheck().DstAddr = packet.BytesToIPv4(3, 22, 111, 0)
cur.GetIPv4NoCheck().VersionIhl = 0x45
cur.GetIPv4NoCheck().NextProtoID = 0x04
}
// Some heavy computational code
heavyCode()
}
Flow graph:
Receive
Send
Split
Send
updated
Rules
Stop
Handle
Packet
vector
Scaling
25
yanff-0$ ./runpktgen.sh
Pktgen:/> load step11.pg
Pktgen:/> start 0
…
Pktgen:/> quit
yanff-1$ sudo ./step11
Modify Modify
To make changes in rules2.conf file it is necessary to
connect to target VM in another window or run
YANFF executable in screen terminal multiplexer.](https://image.slidesharecdn.com/locyanffinalpresentation-190211191004/85/NFF-GO-YANFF-Yet-Another-Network-Function-Framework-25-320.jpg)