1 of 16
Download to read offline















Ad
Recommended
A Byte of Software Deployment



A Byte of Software DeploymentGong Haibing - What's Software Deployment
- A Minimal Python Web Application
- Trouble Shoot
- Interface between Web Server and Application
- Standardization/Automation/Monitoring/Availability
Openstack Summit Vancouver 2018 - Multicloud Networking



Openstack Summit Vancouver 2018 - Multicloud NetworkingShannon McFarland This document discusses connecting private clouds located on-premises to public clouds using multicloud networking. It begins with an overview of hybrid vs multicloud networking and reasons for using multiple cloud providers. It then covers options for extending an on-premises private cloud to a public cloud like AWS, GCP, or Azure using their native VPN services. The document discusses adding more public cloud providers and the need for automation. It introduces dynamic multipoint VPN (DMVPN) as a way to enable dynamic multicloud connectivity and extend routing protocols between sites.
ITB2019 NGINX Overview and Technical Aspects - Kevin Jones



ITB2019 NGINX Overview and Technical Aspects - Kevin JonesOrtus Solutions, Corp I will be giving a brief overview of the history of NGINX along with an overview of the features and functionality in the project as it stands today. I will give some real use case of example of how NGINX can be used to solve problems and eliminate complexity within infrastructure. I will then dive into the future of the modern web and how NGINX is monitoring and leveraging industry changes to enhance the product for individuals and companies in the industry.
DEF CON 24 - workshop - Craig Young - brainwashing embedded systems



DEF CON 24 - workshop - Craig Young - brainwashing embedded systemsFelipe Prado Firmware analysis often involves searching firmware images for known file headers and file systems like SquashFS to extract contained files. Automated binary analysis tools like binwalk can help extract files from images. HTTP interfaces are common targets for security testing since they are often exposed without authentication. Testing may uncover vulnerabilities like XSS, CSRF, SQLi or command injection. Wireless interfaces also require testing to check for issues like weak encryption or exposure of credentials in cleartext.
Fiware cloud developers week brussels



Fiware cloud developers week brusselsFernando Lopez Aguilar - The FIWARE Lab provides cloud hosting and infrastructure as a service capabilities including compute, network, storage, and PaaS functionality.
- It utilizes OpenStack for core infrastructure services including compute (Nova), networking (Neutron), storage (Cinder, Swift), and identity (Keystone).
- The PaaS Manager allows users to define templates called Blueprints to deploy multi-tier applications and software stacks across the virtual infrastructure in an automated manner.
BAUG Meetup #1 2022: Публикация ресурсов в Интернет в Microsoft Azure. Обзор ...



BAUG Meetup #1 2022: Публикация ресурсов в Интернет в Microsoft Azure. Обзор ...Dzmitry Durasau Доклад #1. Публикация ресурсов в Интернет в Microsoft Azure. Обзор технологий.
Публикуя ресурсы в Интернет, зачастую, мы сталкиваемся с проблемой выбора оптимальной технологии Azure, которая обеспечит безопасность, масштабирование и сценарии отказуостойчивости инфраструктуры. Что выбрать – Azure Traffic Manager, Azure Front Door, Azure Firewall, Azure Load Balancer, Azure Applications Gateway или просто опубликовать ресурс с динамическим или статическим IP адресом? Доклад содержит обзор вышеперечисленных технологий, а так же рекомендации по выбору подхода публикации ресурсов в Интернет.
Докладчик: Дмитрий Дурасов. MVP (Azure), MCTS, MCSA, MCP, MCT (Alumni). Cloud Solution Architect in Akveo, Minsk, Belarus
DevOPS training - Day 1/2



DevOPS training - Day 1/2Vincent Mercier Slides from training at ECV digital school - Sponsored by CALLR.com
Basics of DevOPS in one day with a workshop.
Training Webinar: Enterprise application performance with server push technol...



Training Webinar: Enterprise application performance with server push technol...OutSystems 1st Session - WebSockets, a Server Push Technology:
- Differences between Pull and Push technologies
- What are WebSockets
- A bit of History behind WebSockets
- When to use WebSockets
- How to integrate WebSockets with OutSystems
- Considerations when using WebSockets
Free Online training: https://www.outsystems.com/learn/courses/
Follow us on Twitter http://www.twitter.com/OutSystemsDev
Like us on Facebook http://www.Facebook.com/OutSystemsDev
Securing MongoDB to Serve an AWS-Based, Multi-Tenant, Security-Fanatic SaaS A...



Securing MongoDB to Serve an AWS-Based, Multi-Tenant, Security-Fanatic SaaS A...MongoDB MongoDB introduces new capabilities that change the way micro-services interact with the database, capabilities that are either absent or exist only partially in high-end commercial databases such as Oracle. In this session I will share from my experiences building a cloud-based, multi-tenant SaaS application with extreme security requirements. We will cover topics including considerations for storing multi-tenant data in the database, best practices for authentication and authorization, and performance considerations specific to security in MongoDB.
Building Secure Architectures on AWS



Building Secure Architectures on AWSManojAccTest This document provides an overview of how to build secure architectures on AWS. It discusses modeling an on-premises network architecture in AWS, securing the cloud network using security groups and IAM roles, migrating to a serverless architecture with API Gateway and Lambda, securing the serverless components with encryption and authentication, and connecting to the on-premises network using VPN or Direct Connect. It also reviews the cloud architecture against the Cloud Adoption Framework and discusses next steps to learn more about the AWS Well-Architected Framework.
Week 4 lecture material cc (1)



Week 4 lecture material cc (1)Ankit Gupta The document discusses Google Cloud Platform (GCP), which provides a set of cloud computing services including computing, storage, databases, networking, big data, machine learning, and IoT. Some key benefits of GCP include running applications on Google's global infrastructure, focusing on product development rather than system administration, mixing and matching different cloud services, and scaling applications easily to handle millions of users in a cost-effective way. GCP offers both fully managed platform services and flexible virtual machines. It also provides storage, database, and networking services to store and access data.
Learn to Add an SSL Certificate Boost Your Site's Security.pdf



Learn to Add an SSL Certificate Boost Your Site's Security.pdfReliqusConsulting
Enhance your website's security with Reliqus Consulting's simple guide on how to install an SSL certificate. Our step-by-step instructions make it easy for anyone to boost their site's protection. Learn the importance of SSL certificates and follow our user-friendly process to ensure a secure connection for your visitors. Safeguard sensitive data and build trust with your audience by implementing this crucial security measure.
Add a web server



Add a web serverAgCharu A web server is a powerful system that stores, processes, and delivers web content over a network. It uses the client-server model and HTTP for communication. When a client requests a document, the web server retrieves the document from its file system and returns it to the client. The document can be a simple file or dynamically generated by a script. To set up a web server, the document describes installing IIS on Windows 7, then installing PHP and MySQL to enable dynamic content and a database. WordPress is configured and the site is hosted on the web server. The firewall is configured and SSL is added to secure the site.
2023-May.pptx



2023-May.pptxmnaeemuetcs This document summarizes an OWASP meeting that included discussion of phishing techniques. The meeting started at 7:05PM and included discussion of the Evilginx phishing framework. Evilginx is an open source man-in-the-middle attack framework that can bypass multifactor authentication by capturing session cookies. The document provided details on how Evilginx works, examples of its usage, and information on creating custom phishing templates ("phishlets") for targeting specific websites and applications.
E gov security_tut_session_4_lab



E gov security_tut_session_4_labMustafa Jarrar This document provides a tutorial on configuring a secure Apache web server. It discusses installing and configuring Apache, generating SSL certificates, enabling HTTPS, and configuring HTTP basic authentication. The tutorial is part of a Palestinian eGovernment Academy project funded by the European Commission to help build e-government capabilities. It aims to provide students with practical skills in deploying and securing systems using Apache and authentication protocols.
Nginx A High Performance Load Balancer, Web Server & Reverse Proxy



Nginx A High Performance Load Balancer, Web Server & Reverse ProxyAmit Aggarwal Nginx is a web server which can also be used as a reverse proxy, load balancer, mail proxy and HTTP cache
NGINX Installation and Tuning



NGINX Installation and TuningNGINX, Inc. You’re ready to make your applications more responsive, scalable, fast and secure. Then it’s time to get started with NGINX. In this webinar, you will learn how to install NGINX from a package or from source onto a Linux host. We’ll then look at some common operating system tunings you could make to ensure your NGINX install is ready for prime time.
View full webinar on demand at http://nginx.com/resources/webinars/installing-tuning-nginx/
Collector Web Services



Collector Web Servicespublisyst This document summarizes a presentation about Collector Web Services given by Petrus Näslund. The presentation introduced web services and discussed related technologies like SOAP, WSDL, REST, and frameworks for integrating web services. It provided an overview of the web services available in StreamServe Persuasion and how to configure and use the StreamServe Service Gateway. Code examples and monitoring tools were also mentioned. Real-life examples and a demo of a .NET project were noted as part of the presentation.
Configuring kerberos based sso in weblogic



Configuring kerberos based sso in weblogicHarihara sarma This document provides instructions for configuring single sign-on (SSO) using Kerberos in an Oracle WebLogic server environment. It describes setting up Kerberos on the KDC server (Machine A), configuring WebLogic server (Machine B) to use Kerberos, and configuring browser clients (Machine C) to support integrated Windows authentication. Key steps include generating a Kerberos keytab file, configuring the WebLogic security realm and login modules, and setting browser preferences to allow automatic login to the intranet domain.
5 things you didn't know nginx could do velocity



5 things you didn't know nginx could do velocitysarahnovotny NGINX is a well kept secret of high performance web service. Many people know NGINX as an Open Source web server that delivers static content blazingly fast. But, it has many more features to help accelerate delivery of bits to your end users even in more complicated application environments. In this talk we’ll cover several things that most developers or administrators could implement to further delight their end users.
Web-Socket



Web-SocketPankaj Kumar Sharma WebSocket is a protocol that provides full-duplex communication channels over a single TCP connection. It was standardized in 2011 and allows for real-time data exchange between a client and server. The document discusses how WebSocket works, compares it to previous techniques like polling which had limitations, and outlines how to implement WebSocket in Java using JSR 356 and in Spring using the WebSocket API and STOMP protocol.
Session: A Reference Architecture for Running Modern APIs with NGINX Unit and...



Session: A Reference Architecture for Running Modern APIs with NGINX Unit and...NGINX, Inc. Building and deploying cloud native APIs is a complex operation, and can require a multitude of components. In this workshop we focus on the fundamentals of deploying the runtime API code and publishing the API through an API gateway. To achieve this we use NGINX Unit as a polyglot application server and NGINX web server as an API gateway. With this combination we deliver a solution lightweight enough for dev and strong enough for production.
You will learn how to use NGINX Unit to run one or more apps and APIs in a variety of languages, including seamlessly deploying new versions. You will then see the best practices for how to configure NGINX to perform the common API gateway functions of request routing, rate limiting, and authentication for multiple APIs. We will also touch on advanced use cases such as HTTP method enforcement, and JSON validation.
No previous experience of NGINX or NGINX Unit is required, but a basic knowledge of HTTP and JSON/REST APIs is valuable.
18CSC311J WEB DESIGN AND DEVELOPMENT UNIT-4



18CSC311J WEB DESIGN AND DEVELOPMENT UNIT-4Sivakumar M 18CSC311J WEB DESIGN AND DEVELOPMENT,
UNIT-4,
SRM UNIVERSITY,
VI SEMESTER,
REGULATION 2018
CENTRAL MANAGEMENT OF NETWORK AND CALL SERVICES



CENTRAL MANAGEMENT OF NETWORK AND CALL SERVICESNazmul Hossain Rakib The objective of this project is to make servers of web service, ftp service, VoIP video call service, and manage them centrally from a host in private connection or from remote connection. We will also monitor the services, we are going to install, from this central PC. If there is a problem found like no connectivity, then the monitor agent will notify the network administrator showing the error message.
Introduction to Infrastructure as Code & Automation / Introduction to Chef



Introduction to Infrastructure as Code & Automation / Introduction to ChefNathen Harvey The document provides an introduction to infrastructure as code using Chef. It begins with an introduction by Nathen Harvey and outlines the sys admin journey from manually managing servers to using automation and policy-driven configuration management. It then discusses how infrastructure as code with Chef allows treating infrastructure like code by programmatically provisioning and configuring components. The document demonstrates configuring resources like packages, services, files and more using Chef.
WebSockets: The Current State of the Most Valuable HTML5 API for Java Developers



WebSockets: The Current State of the Most Valuable HTML5 API for Java DevelopersViktor Gamov WebSockets provide a standardized way for web browsers and servers to establish two-way communications channels over a single TCP connection. They allow for more efficient real-time messaging compared to older techniques like polling and long-polling. The WebSocket API defines client-side and server-side interfaces that allow for full-duplex communications that some popular Java application servers and web servers support natively. Common use cases that benefit from WebSockets include chat applications, online games, and real-time updating of social streams.
How to Customize Your Financial Reports & Tax Reports With Odoo 17 Accounting



How to Customize Your Financial Reports & Tax Reports With Odoo 17 AccountingCeline George The Accounting module in Odoo 17 is a complete tool designed to manage all financial aspects of a business. Odoo offers a comprehensive set of tools for generating financial and tax reports, which are crucial for managing a company's finances and ensuring compliance with tax regulations.
Ad
More Related Content
Similar to Nginx-deploy on linux server with 80 and 442 (20)
Securing MongoDB to Serve an AWS-Based, Multi-Tenant, Security-Fanatic SaaS A...



Securing MongoDB to Serve an AWS-Based, Multi-Tenant, Security-Fanatic SaaS A...MongoDB MongoDB introduces new capabilities that change the way micro-services interact with the database, capabilities that are either absent or exist only partially in high-end commercial databases such as Oracle. In this session I will share from my experiences building a cloud-based, multi-tenant SaaS application with extreme security requirements. We will cover topics including considerations for storing multi-tenant data in the database, best practices for authentication and authorization, and performance considerations specific to security in MongoDB.
Building Secure Architectures on AWS



Building Secure Architectures on AWSManojAccTest This document provides an overview of how to build secure architectures on AWS. It discusses modeling an on-premises network architecture in AWS, securing the cloud network using security groups and IAM roles, migrating to a serverless architecture with API Gateway and Lambda, securing the serverless components with encryption and authentication, and connecting to the on-premises network using VPN or Direct Connect. It also reviews the cloud architecture against the Cloud Adoption Framework and discusses next steps to learn more about the AWS Well-Architected Framework.
Week 4 lecture material cc (1)



Week 4 lecture material cc (1)Ankit Gupta The document discusses Google Cloud Platform (GCP), which provides a set of cloud computing services including computing, storage, databases, networking, big data, machine learning, and IoT. Some key benefits of GCP include running applications on Google's global infrastructure, focusing on product development rather than system administration, mixing and matching different cloud services, and scaling applications easily to handle millions of users in a cost-effective way. GCP offers both fully managed platform services and flexible virtual machines. It also provides storage, database, and networking services to store and access data.
Learn to Add an SSL Certificate Boost Your Site's Security.pdf



Learn to Add an SSL Certificate Boost Your Site's Security.pdfReliqusConsulting
Enhance your website's security with Reliqus Consulting's simple guide on how to install an SSL certificate. Our step-by-step instructions make it easy for anyone to boost their site's protection. Learn the importance of SSL certificates and follow our user-friendly process to ensure a secure connection for your visitors. Safeguard sensitive data and build trust with your audience by implementing this crucial security measure.
Add a web server



Add a web serverAgCharu A web server is a powerful system that stores, processes, and delivers web content over a network. It uses the client-server model and HTTP for communication. When a client requests a document, the web server retrieves the document from its file system and returns it to the client. The document can be a simple file or dynamically generated by a script. To set up a web server, the document describes installing IIS on Windows 7, then installing PHP and MySQL to enable dynamic content and a database. WordPress is configured and the site is hosted on the web server. The firewall is configured and SSL is added to secure the site.
2023-May.pptx



2023-May.pptxmnaeemuetcs This document summarizes an OWASP meeting that included discussion of phishing techniques. The meeting started at 7:05PM and included discussion of the Evilginx phishing framework. Evilginx is an open source man-in-the-middle attack framework that can bypass multifactor authentication by capturing session cookies. The document provided details on how Evilginx works, examples of its usage, and information on creating custom phishing templates ("phishlets") for targeting specific websites and applications.
E gov security_tut_session_4_lab



E gov security_tut_session_4_labMustafa Jarrar This document provides a tutorial on configuring a secure Apache web server. It discusses installing and configuring Apache, generating SSL certificates, enabling HTTPS, and configuring HTTP basic authentication. The tutorial is part of a Palestinian eGovernment Academy project funded by the European Commission to help build e-government capabilities. It aims to provide students with practical skills in deploying and securing systems using Apache and authentication protocols.
Nginx A High Performance Load Balancer, Web Server & Reverse Proxy



Nginx A High Performance Load Balancer, Web Server & Reverse ProxyAmit Aggarwal Nginx is a web server which can also be used as a reverse proxy, load balancer, mail proxy and HTTP cache
NGINX Installation and Tuning



NGINX Installation and TuningNGINX, Inc. You’re ready to make your applications more responsive, scalable, fast and secure. Then it’s time to get started with NGINX. In this webinar, you will learn how to install NGINX from a package or from source onto a Linux host. We’ll then look at some common operating system tunings you could make to ensure your NGINX install is ready for prime time.
View full webinar on demand at http://nginx.com/resources/webinars/installing-tuning-nginx/
Collector Web Services



Collector Web Servicespublisyst This document summarizes a presentation about Collector Web Services given by Petrus Näslund. The presentation introduced web services and discussed related technologies like SOAP, WSDL, REST, and frameworks for integrating web services. It provided an overview of the web services available in StreamServe Persuasion and how to configure and use the StreamServe Service Gateway. Code examples and monitoring tools were also mentioned. Real-life examples and a demo of a .NET project were noted as part of the presentation.
Configuring kerberos based sso in weblogic



Configuring kerberos based sso in weblogicHarihara sarma This document provides instructions for configuring single sign-on (SSO) using Kerberos in an Oracle WebLogic server environment. It describes setting up Kerberos on the KDC server (Machine A), configuring WebLogic server (Machine B) to use Kerberos, and configuring browser clients (Machine C) to support integrated Windows authentication. Key steps include generating a Kerberos keytab file, configuring the WebLogic security realm and login modules, and setting browser preferences to allow automatic login to the intranet domain.
5 things you didn't know nginx could do velocity



5 things you didn't know nginx could do velocitysarahnovotny NGINX is a well kept secret of high performance web service. Many people know NGINX as an Open Source web server that delivers static content blazingly fast. But, it has many more features to help accelerate delivery of bits to your end users even in more complicated application environments. In this talk we’ll cover several things that most developers or administrators could implement to further delight their end users.
Web-Socket



Web-SocketPankaj Kumar Sharma WebSocket is a protocol that provides full-duplex communication channels over a single TCP connection. It was standardized in 2011 and allows for real-time data exchange between a client and server. The document discusses how WebSocket works, compares it to previous techniques like polling which had limitations, and outlines how to implement WebSocket in Java using JSR 356 and in Spring using the WebSocket API and STOMP protocol.
Session: A Reference Architecture for Running Modern APIs with NGINX Unit and...



Session: A Reference Architecture for Running Modern APIs with NGINX Unit and...NGINX, Inc. Building and deploying cloud native APIs is a complex operation, and can require a multitude of components. In this workshop we focus on the fundamentals of deploying the runtime API code and publishing the API through an API gateway. To achieve this we use NGINX Unit as a polyglot application server and NGINX web server as an API gateway. With this combination we deliver a solution lightweight enough for dev and strong enough for production.
You will learn how to use NGINX Unit to run one or more apps and APIs in a variety of languages, including seamlessly deploying new versions. You will then see the best practices for how to configure NGINX to perform the common API gateway functions of request routing, rate limiting, and authentication for multiple APIs. We will also touch on advanced use cases such as HTTP method enforcement, and JSON validation.
No previous experience of NGINX or NGINX Unit is required, but a basic knowledge of HTTP and JSON/REST APIs is valuable.
18CSC311J WEB DESIGN AND DEVELOPMENT UNIT-4



18CSC311J WEB DESIGN AND DEVELOPMENT UNIT-4Sivakumar M 18CSC311J WEB DESIGN AND DEVELOPMENT,
UNIT-4,
SRM UNIVERSITY,
VI SEMESTER,
REGULATION 2018
CENTRAL MANAGEMENT OF NETWORK AND CALL SERVICES



CENTRAL MANAGEMENT OF NETWORK AND CALL SERVICESNazmul Hossain Rakib The objective of this project is to make servers of web service, ftp service, VoIP video call service, and manage them centrally from a host in private connection or from remote connection. We will also monitor the services, we are going to install, from this central PC. If there is a problem found like no connectivity, then the monitor agent will notify the network administrator showing the error message.
Introduction to Infrastructure as Code & Automation / Introduction to Chef



Introduction to Infrastructure as Code & Automation / Introduction to ChefNathen Harvey The document provides an introduction to infrastructure as code using Chef. It begins with an introduction by Nathen Harvey and outlines the sys admin journey from manually managing servers to using automation and policy-driven configuration management. It then discusses how infrastructure as code with Chef allows treating infrastructure like code by programmatically provisioning and configuring components. The document demonstrates configuring resources like packages, services, files and more using Chef.
WebSockets: The Current State of the Most Valuable HTML5 API for Java Developers



WebSockets: The Current State of the Most Valuable HTML5 API for Java DevelopersViktor Gamov WebSockets provide a standardized way for web browsers and servers to establish two-way communications channels over a single TCP connection. They allow for more efficient real-time messaging compared to older techniques like polling and long-polling. The WebSocket API defines client-side and server-side interfaces that allow for full-duplex communications that some popular Java application servers and web servers support natively. Common use cases that benefit from WebSockets include chat applications, online games, and real-time updating of social streams.
Recently uploaded (20)
How to Customize Your Financial Reports & Tax Reports With Odoo 17 Accounting



How to Customize Your Financial Reports & Tax Reports With Odoo 17 AccountingCeline George The Accounting module in Odoo 17 is a complete tool designed to manage all financial aspects of a business. Odoo offers a comprehensive set of tools for generating financial and tax reports, which are crucial for managing a company's finances and ensuring compliance with tax regulations.
Herbs Used in Cosmetic Formulations .pptx



Herbs Used in Cosmetic Formulations .pptxRAJU THENGE The content is for the educational purpose for Pharmacy and Cosmetic students.
03#UNTAGGED. Generosity in architecture.



03#UNTAGGED. Generosity in architecture.MCH What makes space feel generous, and how architecture address this generosity in terms of atmosphere, metrics, and the implications of its scale? This edition of #Untagged explores these and other questions in its presentation of the 2024 edition of the Master in Collective Housing. The Master of Architecture in Collective Housing, MCH, is a postgraduate full-time international professional program of advanced architecture design in collective housing presented by Universidad Politécnica of Madrid (UPM) and Swiss Federal Institute of Technology (ETH).
Yearbook MCH 2024. Master in Advanced Studies in Collective Housing UPM - ETH
Understanding P–N Junction Semiconductors: A Beginner’s Guide



Understanding P–N Junction Semiconductors: A Beginner’s GuideGS Virdi Dive into the fundamentals of P–N junctions, the heart of every diode and semiconductor device. In this concise presentation, Dr. G.S. Virdi (Former Chief Scientist, CSIR-CEERI Pilani) covers:
What Is a P–N Junction? Learn how P-type and N-type materials join to create a diode.
Depletion Region & Biasing: See how forward and reverse bias shape the voltage–current behavior.
V–I Characteristics: Understand the curve that defines diode operation.
Real-World Uses: Discover common applications in rectifiers, signal clipping, and more.
Ideal for electronics students, hobbyists, and engineers seeking a clear, practical introduction to P–N junction semiconductors.
Presentation of the MIPLM subject matter expert Erdem Kaya



Presentation of the MIPLM subject matter expert Erdem KayaMIPLM Presentation of the MIPLM subject matter expert Erdem Kaya
pulse ppt.pptx Types of pulse , characteristics of pulse , Alteration of pulse



pulse ppt.pptx Types of pulse , characteristics of pulse , Alteration of pulsesushreesangita003 what is pulse ?
Purpose
physiology and Regulation of pulse
Characteristics of pulse
factors affecting pulse
Sites of pulse
Alteration of pulse
for BSC Nursing 1st semester
for Gnm Nursing 1st year
Students .
vitalsign
World war-1(Causes & impacts at a glance) PPT by Simanchala Sarab(BABed,sem-4...



World war-1(Causes & impacts at a glance) PPT by Simanchala Sarab(BABed,sem-4...larencebapu132 This is short and accurate description of World war-1 (1914-18)
It can give you the perfect factual conceptual clarity on the great war
Regards Simanchala Sarab
Student of BABed(ITEP, Secondary stage)in History at Guru Nanak Dev University Amritsar Punjab 🙏🙏
Contact Lens:::: An Overview.pptx.: Optometry



Contact Lens:::: An Overview.pptx.: OptometryMushahidRaza8 A comprehensive guide for Optometry students: understanding in easy launguage of contact lens.
Don't forget to like,share and comments if you found it useful!.
Odoo Inventory Rules and Routes v17 - Odoo Slides



Odoo Inventory Rules and Routes v17 - Odoo SlidesCeline George Odoo's inventory management system is highly flexible and powerful, allowing businesses to efficiently manage their stock operations through the use of Rules and Routes.
How to Manage Purchase Alternatives in Odoo 18



How to Manage Purchase Alternatives in Odoo 18Celine George Managing purchase alternatives is crucial for ensuring a smooth and cost-effective procurement process. Odoo 18 provides robust tools to handle alternative vendors and products, enabling businesses to maintain flexibility and mitigate supply chain disruptions.
Link your Lead Opportunities into Spreadsheet using odoo CRM



Link your Lead Opportunities into Spreadsheet using odoo CRMCeline George In Odoo 17 CRM, linking leads and opportunities to a spreadsheet can be done by exporting data or using Odoo’s built-in spreadsheet integration. To export, navigate to the CRM app, filter and select the relevant records, and then export the data in formats like CSV or XLSX, which can be opened in external spreadsheet tools such as Excel or Google Sheets.
CBSE - Grade 8 - Science - Chemistry - Metals and Non Metals - Worksheet



CBSE - Grade 8 - Science - Chemistry - Metals and Non Metals - WorksheetSritoma Majumder Introduction
All the materials around us are made up of elements. These elements can be broadly divided into two major groups:
Metals
Non-Metals
Each group has its own unique physical and chemical properties. Let's understand them one by one.
Physical Properties
1. Appearance
Metals: Shiny (lustrous). Example: gold, silver, copper.
Non-metals: Dull appearance (except iodine, which is shiny).
2. Hardness
Metals: Generally hard. Example: iron.
Non-metals: Usually soft (except diamond, a form of carbon, which is very hard).
3. State
Metals: Mostly solids at room temperature (except mercury, which is a liquid).
Non-metals: Can be solids, liquids, or gases. Example: oxygen (gas), bromine (liquid), sulphur (solid).
4. Malleability
Metals: Can be hammered into thin sheets (malleable).
Non-metals: Not malleable. They break when hammered (brittle).
5. Ductility
Metals: Can be drawn into wires (ductile).
Non-metals: Not ductile.
6. Conductivity
Metals: Good conductors of heat and electricity.
Non-metals: Poor conductors (except graphite, which is a good conductor).
7. Sonorous Nature
Metals: Produce a ringing sound when struck.
Non-metals: Do not produce sound.
Chemical Properties
1. Reaction with Oxygen
Metals react with oxygen to form metal oxides.
These metal oxides are usually basic.
Non-metals react with oxygen to form non-metallic oxides.
These oxides are usually acidic.
2. Reaction with Water
Metals:
Some react vigorously (e.g., sodium).
Some react slowly (e.g., iron).
Some do not react at all (e.g., gold, silver).
Non-metals: Generally do not react with water.
3. Reaction with Acids
Metals react with acids to produce salt and hydrogen gas.
Non-metals: Do not react with acids.
4. Reaction with Bases
Some non-metals react with bases to form salts, but this is rare.
Metals generally do not react with bases directly (except amphoteric metals like aluminum and zinc).
Displacement Reaction
More reactive metals can displace less reactive metals from their salt solutions.
Uses of Metals
Iron: Making machines, tools, and buildings.
Aluminum: Used in aircraft, utensils.
Copper: Electrical wires.
Gold and Silver: Jewelry.
Zinc: Coating iron to prevent rusting (galvanization).
Uses of Non-Metals
Oxygen: Breathing.
Nitrogen: Fertilizers.
Chlorine: Water purification.
Carbon: Fuel (coal), steel-making (coke).
Iodine: Medicines.
Alloys
An alloy is a mixture of metals or a metal with a non-metal.
Alloys have improved properties like strength, resistance to rusting.
Geography Sem II Unit 1C Correlation of Geography with other school subjects



Geography Sem II Unit 1C Correlation of Geography with other school subjectsProfDrShaikhImran The correlation of school subjects refers to the interconnectedness and mutual reinforcement between different academic disciplines. This concept highlights how knowledge and skills in one subject can support, enhance, or overlap with learning in another. Recognizing these correlations helps in creating a more holistic and meaningful educational experience.
One Hot encoding a revolution in Machine learning



One Hot encoding a revolution in Machine learningmomer9505 A brief introduction to ONE HOT encoding a way to communicate with machines
APM Midlands Region April 2025 Sacha Hind Circulated.pdf



APM Midlands Region April 2025 Sacha Hind Circulated.pdfAssociation for Project Management APM event hosted by the Midlands Network on 30 April 2025.
Speaker: Sacha Hind, Senior Programme Manager, Network Rail
With fierce competition in today’s job market, candidates need a lot more than a good CV and interview skills to stand out from the crowd.
Based on her own experience of progressing to a senior project role and leading a team of 35 project professionals, Sacha shared not just how to land that dream role, but how to be successful in it and most importantly, how to enjoy it!
Sacha included her top tips for aspiring leaders – the things you really need to know but people rarely tell you!
We also celebrated our Midlands Regional Network Awards 2025, and presenting the award for Midlands Student of the Year 2025.
This session provided the opportunity for personal reflection on areas attendees are currently focussing on in order to be successful versus what really makes a difference.
Sacha answered some common questions about what it takes to thrive at a senior level in a fast-paced project environment: Do I need a degree? How do I balance work with family and life outside of work? How do I get leadership experience before I become a line manager?
The session was full of practical takeaways and the audience also had the opportunity to get their questions answered on the evening with a live Q&A session.
Attendees hopefully came away feeling more confident, motivated and empowered to progress their careers
Biophysics Chapter 3 Methods of Studying Macromolecules.pdf



Biophysics Chapter 3 Methods of Studying Macromolecules.pdfPKLI-Institute of Nursing and Allied Health Sciences Lahore , Pakistan. This chapter provides an in-depth overview of the viscosity of macromolecules, an essential concept in biophysics and medical sciences, especially in understanding fluid behavior like blood flow in the human body.
Key concepts covered include:
✅ Definition and Types of Viscosity: Dynamic vs. Kinematic viscosity, cohesion, and adhesion.
⚙️ Methods of Measuring Viscosity:
Rotary Viscometer
Vibrational Viscometer
Falling Object Method
Capillary Viscometer
🌡️ Factors Affecting Viscosity: Temperature, composition, flow rate.
🩺 Clinical Relevance: Impact of blood viscosity in cardiovascular health.
🌊 Fluid Dynamics: Laminar vs. turbulent flow, Reynolds number.
🔬 Extension Techniques:
Chromatography (adsorption, partition, TLC, etc.)
Electrophoresis (protein/DNA separation)
Sedimentation and Centrifugation methods.
Biophysics Chapter 3 Methods of Studying Macromolecules.pdf



Biophysics Chapter 3 Methods of Studying Macromolecules.pdfPKLI-Institute of Nursing and Allied Health Sciences Lahore , Pakistan.
Ad
Nginx-deploy on linux server with 80 and 442
- 1. Gunicorn with Nginx Setup • 1. What is Gunicorn? • 2. What is Nginx? 3. Why Gunicorn and Nginx? • 4. Steps to create User and Group 5. Deploy.sh • 6. Gunicorn Setup • 7. Nginx Setup • 8. What is SSL certificate? • 9. How do SSL certificates work? • 10. Why you need an SSL certificate? • 11. Configure Certbot for SSL Certificate • 12. Benefits with Ngix and Gunicorn
- 2. What is Gunicorn? • Gunicorn implements the Web Server Gateway Interface (WSGI), which is a standard interface between web server software and web applications. • 1. Gunicorn (Green Unicorn) is a WSGI HTTP server for Python Web applications. • 2. Designed to be lightweight, simple and fast. • 3. WSGI (Web Server Gateway Interface) is a standard interface between web servers and Python web applications.
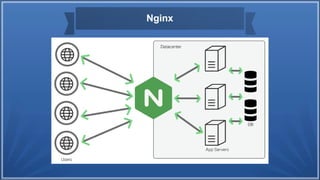
- 3. What is Nginx? • Nginx is a web server. It's the public handler, more formally called the reverse proxy, for incoming requests and scales to thousands of simultaneous connections. • 1. Nginx is a high performance, open source web server and reverse proxy server. • 2. Know for its scalability and low resources consumption. • 3. Commonly used to server static content, revers proxy and • load balancing.
- 4. Nginx
- 5. Why Gunicorn and Nginx? • 1. Gunicorn handles dynamic content and interect with the python web applications. • 2. Nginx handles static content, SSL terminations and acts as a reverse proxy. • 3. Combined, they provide a scalable and efficient web server setup.
- 6. Steps to create User and Group 1. Create a new user "“Servicename”" + create a new Group for the new user. (sudo useradd -m “Servicename 2. Add Ubuntu and www-data to “Servicename”'s new group. (sudo adduser ubuntu “Servicename”) (sudo adduser ubuntu www-data) 3. Give permission to /home/”Servicename”/ (sudo chmod -R g+w /home/”Servicename”/) 4. Configure Ngix file 5. Create a symbolic link (sudo ln -s/bin/python/usr/local/bin/python3.10) 6. Create a virtual environment (python -m venv vm) 7. Install requried packages (pip install -r requirements.txt) PostgreSQL • 1. Set a password if not configured. • 2. Create login group Roles • 3. Create a Database with owner “Servicename” rights
- 7. Deploy.sh • git push cd .. rm -f project-deploy.tar.gz rm -rf project-deploy git clone <git repository name> project-deploy --depth 1 tar --exclude-vcs -cvzf project-deploy.tar.gz project-deploy scp -C project-deploy.tar.gz [email protected]:~/ ssh [email protected] <<-SCRIPT tar -xvzf project-deploy.tar.gz rm -rf project mv project-deploy project cd project ln -s ../kyc kyc; source ../project_env/bin/activate python manage.py migrate; python manage.py collectstatic --no-input; sudo service project restart; sudo service nginx restart; SCRIPT
- 8. Gunicorn Setup • 1. Installation: pip install gunicorn • 1.1 Open your Linux terminal or shell. • 1.2 Type “ pip install gunicorn ” (without quotes), hit Enter. • 1.3 If it doesn't work, try "pip3 install gunicorn" or “ python -m pip install gunicorn “. • 1.4 Wait for the installation to terminate successfully. • 2. After installing Gunicorn you will have access to the command line script gunicorn. Running Gunicorn command: • -> gunicorn myapp:app • 3. Configuration options (workers, bind address, etc.) • 4. Example command: gunicorn -w 4 -b 0.0.0.0:8000 myapp:app
- 9. Gunicorn Setup • 1. gunicorn: This is the command to start the Gunicorn server. • 2. -w 4: This option specifies the number of worker processes Gunicorn should use. In this case, it is set to 4. Worker processes are separate instances of the application that handle incoming requests concurrently. Adjusting the number of workers can impact the server's performance. • 3. -b 0.0.0.0:8000: This option specifies the socket to bind Gunicorn to. In this case, it binds to all available network interfaces (0.0.0.0) on port 8000. This means the server will listen for incoming connections on port 8000 and be accessible from any IP address. • 4. myapp:app: This argument specifies the location of the WSGI application object. In this example, it assumes your application is in a file named myapp (without the file extension) and the WSGI application object is named app. This could vary based on the structure of your project.
- 10. Nginx Setup • 1. Installation: sudo apt-get install nginx 1.1 Installing Nginx. To install Nginx, use following command: sudo apt update sudo apt install nginx. ... • 1.2 Creating our own website. Default page is placed in /var/www/html/ location. ... • 1.3 Setting up virtual host. ... • 1.4 Activating virtual host and testing results. • 2. Basic configuration: server blocks, location blocks server { listen 80; server_name abc.com; . . . } • 3. Reverse proxy configuration for Gunicorn • 3.1 A reverse proxy is a server that sits between client devices (such as web browsers) and a backend server. • 3.2 It performs tasks on behalf of the server, acting as an intermediary between clients and the actual server hosting the application. • 3.3 Unlike a forward proxy, which handles requests from clients to the internet, a reverse proxy handles requests from clients to a server. • 4. Example Nginx configuration snippet:
- 11. What is SSL certificate • 1. An SSL certificate is a digital certificate that authenticates website’s identity and enables an encrypted connection. • 2. SSL stands for Secure Socket Layer, a security protocol that creates an encrypted link between a web server and a web browser.
- 12. How do SSL certificates work? • 1. A browser or server attempts to connect a website(i. g. Web server) secured with SSL. • 2. The browser or server requests that the web server identifies itself. • 3. The web server sends the browser or server a copy of its SSL certificate in response. • 4. The browser or server checks to see whether it trusts the SSL certificate. If it does, it signals this to the webserver. • 5. The web server then returns a digitally signed acknowledgment to start an SSL encrypted session. • 6. Encrypted data is shared between the browser or server and the webserver.
- 13. Why you need an SSL certificate • 1. Login Credentials. • 2. Credit card transactions and bank account informations. • 3. Personally identifiable information – such as full name , address, date of birth or mobile number. • 4. Legal documents and contracts. • 5. Medical records. • 6. Proprietary information.
- 14. Configure Certbot for SSL Certificate • 1. Update package Lists (sudo apt-get update) • 2. Install certbot (sudo apt-get install certbot) • 3. Install certbot nginx plugin (sudo apt-get install python3- certbot-nginx) • 4. Obtain SSL / TLS Certificates (sudo certbot)
- 15. Benefits of Gunicorn and Nginx • 1. Gunicorn provides a simple and efficient WSGI server for Python • 2. Nginx handles static files, improves security, and enhances performance • 3. Improved scalability and resource utilization





