Node.js Authentication and Data Security
7 likes3,050 views
The document discusses Node.js authentication and data security, emphasizing the importance of protecting user identities and passwords through various methods such as salting, hashing, and encryption. It outlines several password attack vectors and protective measures, including bcrypt and PBKDF2 for hashing, as well as SSL/TLS for secure communication. Additionally, it provides sample code snippets for implementing these security features in Node.js applications.
1 of 35
Downloaded 20 times
































Ad
Recommended
Protecting the Future of Mobile Payments
Protecting the Future of Mobile PaymentsJonathan LeBlanc The document discusses various techniques and technologies for securing mobile payments, including trust zones, account security, device fingerprinting, and location data usage. It also covers the generation and management of cryptographic keys for encrypting and signing messages securely within a multi-user environment. Additionally, card tokenization methods for protecting credit card information in mobile transactions are addressed.
Secure Payments Over Mixed Communication Media
Secure Payments Over Mixed Communication MediaJonathan LeBlanc This document discusses building identification and security for payments over mixed communication media. It covers creating an identification backbone through browser and device fingerprinting. It also discusses creating middle-tier transmission security using asynchronous cryptography to securely transmit data. This includes encrypting messages with public keys, signing with private keys, decrypting with private keys, and verifying signatures with public keys. It also touches on tokenization and triggering from secure sources.
PHP Identity and Data Security
PHP Identity and Data SecurityJonathan LeBlanc This document provides an overview of password and data security best practices for PHP applications. It discusses common password attacks and how to protect against them using techniques like salting, key stretching algorithms and two-factor authentication. It also covers encrypting data using symmetric and asymmetric cryptography algorithms like AES, RSA and digital signatures. The document provides code examples for hashing and validating passwords, encrypting and decrypting messages and data at rest or in transit.
Secure Payments Over Mixed Communication Media
Secure Payments Over Mixed Communication MediaJonathan LeBlanc The document discusses secure payment practices across various communication media, focusing on identity protection, data integrity during transmission, and security for payment transactions. It highlights techniques for password protection, encryption methods, and the use of asymmetric and symmetric algorithms to secure data in motion. Additionally, it covers the importance of wearable technology in extending security measures and mentions key coding examples for implementing these practices.
Mac OS X Lion で作る WordPress local 環境
Mac OS X Lion で作る WordPress local 環境Yuriko IKEDA This document provides instructions for installing and configuring a LAMP stack on Mac OS X including MySQL, Apache, PHP and WordPress. It describes downloading and installing each component, configuring passwords, file permissions and settings. Specific steps include installing MySQL from the developer website, setting the root password, copying configuration files, enabling PHP support in Apache, configuring PHP.ini settings and installing WordPress in the Apache document root.
Ruby Robots
Ruby RobotsDaniel Cukier The document discusses various topics related to web scraping and robots/bots using Ruby including:
- Using the Anemone gem to crawl and parse URLs
- Using Nokogiri to parse HTML and extract data using XPath queries
- Making HTTP requests to APIs using RestClient and parsing JSON responses
- Scraping dynamic content by executing JavaScript using Nokogiri
- Techniques for handling proxies, cookies, and CAPTCHAs when scraping
- Scaling scraping workloads using threads and queues in Ruby
Token Based Authentication Systems
Token Based Authentication SystemsHüseyin BABAL This document discusses using JSON Web Tokens (JWT) for authentication in a system with an AngularJS client and a NodeJS backend. It describes how JWT can be used to issue tokens containing user identity information to clients after login, which are then sent back to the server on subsequent requests to verify the user without using server-side sessions. This allows building clients that work across platforms like mobile and desktop without re-implementing authentication logic in each client.
Laporan setting dns
Laporan setting dnsSeptian Adi This document summarizes the steps to configure BIND as a local DNS server on a Debian system. It involves installing bind9, configuring named.conf files to define zones, editing db files for forward and reverse lookups, configuring named.conf options and resolv.conf, and testing with nslookup.
Couchdb w Ruby'm
Couchdb w Ruby'mStanisław Wasiutyński The document demonstrates how to interact with CouchDB using its RESTful JSON API. It shows examples of creating, reading, updating and deleting documents through HTTP requests using curl. Specific examples include creating a database, adding a document, updating a document by including the revision ID, and retrieving a document by ID. The document also discusses CouchDB's document-oriented data model where all data is stored as JSON documents.
Talk NullByteCon 2015
Talk NullByteCon 2015Roberto Soares The document appears to be notes from a talk on WordPress security. It discusses common WordPress vulnerabilities like XSS and SQL injection. It mentions the Metasploit framework and using it to make HTTP requests for exploits and auxiliary modules. Specific exploits demonstrated include reading the /etc/passwd file and attacking the WordPress login process. The talk also covers the wpsploit tool for automating WordPress attacks and takes questions at the end.
Redis
RedisPuneet Kumar Redis is an in-memory data structure store that can be used as a database, cache, and message broker. It supports strings, hashes, lists, sets, sorted sets with operations like gets, sets, incr, and exploring data structures. Redis also supports transactions, pub/sub, LRU caching, and replication. Common commands provide basic CRUD operations and data structure operations with time complexities from O(1) to O(N+M*log(M)).
Getting Started with Microsoft Bot Framework
Getting Started with Microsoft Bot FrameworkSarah Sexton The document describes how to build a chatbot using the Tracery natural language generation library and the Microsoft Bot Framework. It includes code samples for setting up the basic bot infrastructure with Restify and Bot Builder, defining the grammar for generating responses, and implementing a root dialog to handle messages. Sections cover key concepts like dialogs, waterfalls, and closures for routing conversations, and using Tracery to replace symbols and add modifiers for varied yet grammatically correct outputs. Links are provided for additional Bot Framework and Tracery resources.
Word Play in the Digital Age: Building Text Bots with Tracery
Word Play in the Digital Age: Building Text Bots with TracerySarah Sexton This document contains code for creating a chatbot using the Tracery natural language generation library and Microsoft Bot Framework. It includes code for setting up a Restify server to host the bot, creating a Tracery grammar with replacement symbols to generate text responses, and integrating the bot with the Bot Framework to enable chatting. The bot responds to the user's message with a randomly generated greeting using the Tracery grammar.
Automated Testing
Automated TestingSpeed FC The document outlines the professional background and expertise of Arturo Maltos, a tech lead at WebMD with extensive experience in ecommerce development and automated testing. It details methodologies used in testing medical simulation cases, including the tools and frameworks implemented to improve efficiency, such as Codeception and Selenium Grid. Additionally, it highlights the significant reduction in development time for testing scenarios and the integration of parallel testing with various browser configurations, resulting in enhanced testing capabilities.
MongoDB shell games: Here be dragons .. and JavaScript!
MongoDB shell games: Here be dragons .. and JavaScript!Stennie Steneker The document appears to be a collection of resources, commands, and links related to MongoDB and JavaScript. It includes references to GitHub projects, documentation, and a few specific MongoDB shell commands. Additionally, there are various formatted URLs indicating further reading and tools associated with MongoDB.
Cool usage of Encoding and Decoding a URI in Javascript
Cool usage of Encoding and Decoding a URI in JavascriptIdeas2IT Technologies The document explains three JavaScript functions: encodeURI(), decodeURI(), and encodeURIComponent(). encodeURI() encodes a URI by replacing reserved characters with their UTF-8 encoding, while encodeURIComponent() encodes all characters, including those ignored by encodeURI(). decodeURI() and decodeURIComponent() are used to reverse the encoding process for their respective functions.
DEF CON 23 - Phil Polstra - one device to pwn them all
DEF CON 23 - Phil Polstra - one device to pwn them allFelipe Prado This document discusses a pocket-sized hacking device called the BeagleBone Black running Deck Linux. It can function as a drop box, remote hacking drone controlled from up to 2 miles away, or airborne hacking drone when combined with an RC aircraft. The device is small, flexible, and can integrate into sophisticated penetration tests. It demonstrates exporting the device's USB drive to a PC in read-only mode, then making it writable. It also shows impersonating a USB mass storage device and creating a scriptable USB keyboard. The author then provides code samples and demos attacking both Linux and Windows systems by sending keyboard/mouse inputs. Questions are directed to the author's demo lab or booth at the conference.
CGI.pm - 3ло?!
CGI.pm - 3ло?!Anatoly Sharifulin This document discusses the CGI.pm module and alternatives. It provides an overview of CGI.pm's capabilities including generating HTML forms and handling GET/POST parameters. It also discusses some issues with CGI.pm including losing access to file handles and incorrect UTF-8 handling. Finally, it shows how to use CGI.pm with different interfaces like mod_perl, FastCGI, POE by setting environment variables and request objects.
Keep It Simple Security (Symfony cafe 28-01-2016)
Keep It Simple Security (Symfony cafe 28-01-2016)Oleg Zinchenko This document contains code snippets related to implementing WSSE authentication in Symfony. It includes code for a WSSE token, listener, authentication manager/provider, and factory class. The token holds user details extracted from the HTTP header. The listener extracts credentials from the header and passes them to the manager. The manager authenticates by validating the credentials against the user provider. The factory registers these classes with the security component. The document also mentions voters and ACL as other Symfony security topics.
NodeJS The edge of Reason - Lille fp#6
NodeJS The edge of Reason - Lille fp#6Thomas Haessle The document discusses using ReasonML and Bucklescript to build functional Node.js applications. It provides examples of how ReasonML code compiles to readable JavaScript code and focuses on type safety, immutability and functional patterns. Key benefits highlighted include OCaml's battle tested type system with type inference, a kind community, production ready tools and good sample code. Challenges mentioned include it being a young ecosystem with a small community and a learning curve for JavaScript developers.
Building Secure User Interfaces With JWTs (JSON Web Tokens)
Building Secure User Interfaces With JWTs (JSON Web Tokens)Stormpath The document discusses the importance of securing user interfaces in web applications, specifically through the use of JSON Web Tokens (JWTs) for authentication and authorization. It addresses security concerns such as session ID management, XSS attacks, and CSRF vulnerabilities, providing solutions to these issues while advocating for the use of access tokens over traditional session IDs. Additionally, it emphasizes the benefits of JWTs, including their structured format, statelessness, and implicit trust due to cryptographic signing, while also warning about the need to secure them properly.
Human Talks Riot.js
Human Talks Riot.jsstreamdata.io Riot.js is a micro-library for building user interfaces using custom tags similar to React and Polymer, which allows for modularity and event-driven communication. It features a simple syntax for defining tags and handling events, alongside routing capabilities for easy navigation. Additional benefits include server-side rendering support and integration with modern build tools, enhancing the development experience.
A bug bounty tale: Chrome, stylesheets, cookies, and AES
A bug bounty tale: Chrome, stylesheets, cookies, and AEScgvwzq The document discusses a security vulnerability related to how web browsers handle local files and the Same Origin Policy, specifically focusing on Chrome's SQLite databases. It details how attackers can exploit this to leak sensitive information such as cookies and local storage through crafted CSS and JavaScript. The talk also emphasizes the importance of headers like 'X-Content-Type-Options' to mitigate such cross-origin attacks, while showcasing a proof of concept for the exploitation technique.
WordPress Security @ Vienna WordPress + Drupal Meetup
WordPress Security @ Vienna WordPress + Drupal MeetupVeselin Nikolov This document provides an overview of security best practices for WordPress sites. It discusses topics like passwords, plugins, themes, code review, and more. The document also includes examples of common vulnerabilities like XSS, SQL injection, and open redirects. Through a series of questions and answers, it demonstrates how to identify and fix security issues, emphasizing the importance of input validation, output encoding, and using built-in WordPress functions correctly.
Forbes MongoNYC 2011
Forbes MongoNYC 2011djdunlop Forbes uses MongoDB to support its distributed global workforce of contributors. It structures content, authors, comments, and promoted content in MongoDB collections. Key data includes articles, blogs, authors, and user comments. MongoDB allows flexible schemas and supports Forbes' needs for a distributed workforce to collaboratively create and manage content.
DevLOVE ターミナル勉強会 zsh + screen
DevLOVE ターミナル勉強会 zsh + screenYozo SATO This document contains a series of commands and their outputs from a zsh shell session. It introduces a user named SATO Yozo and provides their name, Twitter ID, email, job, and disclaimer. It also includes tips for using zsh like using screen, managing bash/zsh history files, and links to resources for learning zsh.
Craig Brown speaks on ElasticSearch
Craig Brown speaks on ElasticSearchimarcticblue The document introduces Elasticsearch as a search engine and NoSQL datastore. It discusses how Elasticsearch is built on Lucene, uses JSON over HTTP, and is schema-free and document-oriented. It provides examples of indexing, searching, and retrieving data. The document also covers Elasticsearch's features for scalability, multi-tenancy, settings, consistency, integration with other systems, and compares it to SOLR.
One Size Fits All
One Size Fits AllClaudio Meinberg The document outlines prerequisites for developing Android applications using SDK, ADT, and Cordova with a 'Hello World' example. It includes code snippets for various functionalities like geolocation, notifications, contacts, and page structure using jQuery Mobile. Additionally, it provides contact information for Claudio Ortiz Meinberg along with links to his profiles and resources.
Security in Node.JS and Express:
Security in Node.JS and Express:Petros Demetrakopoulos - Server-side JavaScript injection, cross-site scripting attacks, SQL injections, and cross-site request forgery are common security vulnerabilities in Node.js and Express applications. The document provides recommendations to prevent each vulnerability, including validating user input, escaping output, using prepared statements, and implementing CSRF tokens.
- Data validation and sanitization should be implemented for all endpoints accepting user data. Packages like express-validator can define validation schemas and sanitize input. Logging each request and response is also important for security monitoring and auditing.
Secure Coding for NodeJS
Secure Coding for NodeJSThang Chung This document provides an overview of secure coding practices for Node.js applications. It discusses common vulnerabilities like injection, broken authentication, cross-site scripting, insecure direct object references, security misconfiguration, sensitive data exposure, lack of access controls, CSRF, use of vulnerable components, and unvalidated redirects. For each issue, it provides examples of insecure code and suggestions for more secure implementations using input validation, encryption, access control checks, HTTPS, CSRF tokens, and other best practices. It also lists some useful security tools and resources for Node.js applications.
More Related Content
What's hot (20)
Couchdb w Ruby'm
Couchdb w Ruby'mStanisław Wasiutyński The document demonstrates how to interact with CouchDB using its RESTful JSON API. It shows examples of creating, reading, updating and deleting documents through HTTP requests using curl. Specific examples include creating a database, adding a document, updating a document by including the revision ID, and retrieving a document by ID. The document also discusses CouchDB's document-oriented data model where all data is stored as JSON documents.
Talk NullByteCon 2015
Talk NullByteCon 2015Roberto Soares The document appears to be notes from a talk on WordPress security. It discusses common WordPress vulnerabilities like XSS and SQL injection. It mentions the Metasploit framework and using it to make HTTP requests for exploits and auxiliary modules. Specific exploits demonstrated include reading the /etc/passwd file and attacking the WordPress login process. The talk also covers the wpsploit tool for automating WordPress attacks and takes questions at the end.
Redis
RedisPuneet Kumar Redis is an in-memory data structure store that can be used as a database, cache, and message broker. It supports strings, hashes, lists, sets, sorted sets with operations like gets, sets, incr, and exploring data structures. Redis also supports transactions, pub/sub, LRU caching, and replication. Common commands provide basic CRUD operations and data structure operations with time complexities from O(1) to O(N+M*log(M)).
Getting Started with Microsoft Bot Framework
Getting Started with Microsoft Bot FrameworkSarah Sexton The document describes how to build a chatbot using the Tracery natural language generation library and the Microsoft Bot Framework. It includes code samples for setting up the basic bot infrastructure with Restify and Bot Builder, defining the grammar for generating responses, and implementing a root dialog to handle messages. Sections cover key concepts like dialogs, waterfalls, and closures for routing conversations, and using Tracery to replace symbols and add modifiers for varied yet grammatically correct outputs. Links are provided for additional Bot Framework and Tracery resources.
Word Play in the Digital Age: Building Text Bots with Tracery
Word Play in the Digital Age: Building Text Bots with TracerySarah Sexton This document contains code for creating a chatbot using the Tracery natural language generation library and Microsoft Bot Framework. It includes code for setting up a Restify server to host the bot, creating a Tracery grammar with replacement symbols to generate text responses, and integrating the bot with the Bot Framework to enable chatting. The bot responds to the user's message with a randomly generated greeting using the Tracery grammar.
Automated Testing
Automated TestingSpeed FC The document outlines the professional background and expertise of Arturo Maltos, a tech lead at WebMD with extensive experience in ecommerce development and automated testing. It details methodologies used in testing medical simulation cases, including the tools and frameworks implemented to improve efficiency, such as Codeception and Selenium Grid. Additionally, it highlights the significant reduction in development time for testing scenarios and the integration of parallel testing with various browser configurations, resulting in enhanced testing capabilities.
MongoDB shell games: Here be dragons .. and JavaScript!
MongoDB shell games: Here be dragons .. and JavaScript!Stennie Steneker The document appears to be a collection of resources, commands, and links related to MongoDB and JavaScript. It includes references to GitHub projects, documentation, and a few specific MongoDB shell commands. Additionally, there are various formatted URLs indicating further reading and tools associated with MongoDB.
Cool usage of Encoding and Decoding a URI in Javascript
Cool usage of Encoding and Decoding a URI in JavascriptIdeas2IT Technologies The document explains three JavaScript functions: encodeURI(), decodeURI(), and encodeURIComponent(). encodeURI() encodes a URI by replacing reserved characters with their UTF-8 encoding, while encodeURIComponent() encodes all characters, including those ignored by encodeURI(). decodeURI() and decodeURIComponent() are used to reverse the encoding process for their respective functions.
DEF CON 23 - Phil Polstra - one device to pwn them all
DEF CON 23 - Phil Polstra - one device to pwn them allFelipe Prado This document discusses a pocket-sized hacking device called the BeagleBone Black running Deck Linux. It can function as a drop box, remote hacking drone controlled from up to 2 miles away, or airborne hacking drone when combined with an RC aircraft. The device is small, flexible, and can integrate into sophisticated penetration tests. It demonstrates exporting the device's USB drive to a PC in read-only mode, then making it writable. It also shows impersonating a USB mass storage device and creating a scriptable USB keyboard. The author then provides code samples and demos attacking both Linux and Windows systems by sending keyboard/mouse inputs. Questions are directed to the author's demo lab or booth at the conference.
CGI.pm - 3ло?!
CGI.pm - 3ло?!Anatoly Sharifulin This document discusses the CGI.pm module and alternatives. It provides an overview of CGI.pm's capabilities including generating HTML forms and handling GET/POST parameters. It also discusses some issues with CGI.pm including losing access to file handles and incorrect UTF-8 handling. Finally, it shows how to use CGI.pm with different interfaces like mod_perl, FastCGI, POE by setting environment variables and request objects.
Keep It Simple Security (Symfony cafe 28-01-2016)
Keep It Simple Security (Symfony cafe 28-01-2016)Oleg Zinchenko This document contains code snippets related to implementing WSSE authentication in Symfony. It includes code for a WSSE token, listener, authentication manager/provider, and factory class. The token holds user details extracted from the HTTP header. The listener extracts credentials from the header and passes them to the manager. The manager authenticates by validating the credentials against the user provider. The factory registers these classes with the security component. The document also mentions voters and ACL as other Symfony security topics.
NodeJS The edge of Reason - Lille fp#6
NodeJS The edge of Reason - Lille fp#6Thomas Haessle The document discusses using ReasonML and Bucklescript to build functional Node.js applications. It provides examples of how ReasonML code compiles to readable JavaScript code and focuses on type safety, immutability and functional patterns. Key benefits highlighted include OCaml's battle tested type system with type inference, a kind community, production ready tools and good sample code. Challenges mentioned include it being a young ecosystem with a small community and a learning curve for JavaScript developers.
Building Secure User Interfaces With JWTs (JSON Web Tokens)
Building Secure User Interfaces With JWTs (JSON Web Tokens)Stormpath The document discusses the importance of securing user interfaces in web applications, specifically through the use of JSON Web Tokens (JWTs) for authentication and authorization. It addresses security concerns such as session ID management, XSS attacks, and CSRF vulnerabilities, providing solutions to these issues while advocating for the use of access tokens over traditional session IDs. Additionally, it emphasizes the benefits of JWTs, including their structured format, statelessness, and implicit trust due to cryptographic signing, while also warning about the need to secure them properly.
Human Talks Riot.js
Human Talks Riot.jsstreamdata.io Riot.js is a micro-library for building user interfaces using custom tags similar to React and Polymer, which allows for modularity and event-driven communication. It features a simple syntax for defining tags and handling events, alongside routing capabilities for easy navigation. Additional benefits include server-side rendering support and integration with modern build tools, enhancing the development experience.
A bug bounty tale: Chrome, stylesheets, cookies, and AES
A bug bounty tale: Chrome, stylesheets, cookies, and AEScgvwzq The document discusses a security vulnerability related to how web browsers handle local files and the Same Origin Policy, specifically focusing on Chrome's SQLite databases. It details how attackers can exploit this to leak sensitive information such as cookies and local storage through crafted CSS and JavaScript. The talk also emphasizes the importance of headers like 'X-Content-Type-Options' to mitigate such cross-origin attacks, while showcasing a proof of concept for the exploitation technique.
WordPress Security @ Vienna WordPress + Drupal Meetup
WordPress Security @ Vienna WordPress + Drupal MeetupVeselin Nikolov This document provides an overview of security best practices for WordPress sites. It discusses topics like passwords, plugins, themes, code review, and more. The document also includes examples of common vulnerabilities like XSS, SQL injection, and open redirects. Through a series of questions and answers, it demonstrates how to identify and fix security issues, emphasizing the importance of input validation, output encoding, and using built-in WordPress functions correctly.
Forbes MongoNYC 2011
Forbes MongoNYC 2011djdunlop Forbes uses MongoDB to support its distributed global workforce of contributors. It structures content, authors, comments, and promoted content in MongoDB collections. Key data includes articles, blogs, authors, and user comments. MongoDB allows flexible schemas and supports Forbes' needs for a distributed workforce to collaboratively create and manage content.
DevLOVE ターミナル勉強会 zsh + screen
DevLOVE ターミナル勉強会 zsh + screenYozo SATO This document contains a series of commands and their outputs from a zsh shell session. It introduces a user named SATO Yozo and provides their name, Twitter ID, email, job, and disclaimer. It also includes tips for using zsh like using screen, managing bash/zsh history files, and links to resources for learning zsh.
Craig Brown speaks on ElasticSearch
Craig Brown speaks on ElasticSearchimarcticblue The document introduces Elasticsearch as a search engine and NoSQL datastore. It discusses how Elasticsearch is built on Lucene, uses JSON over HTTP, and is schema-free and document-oriented. It provides examples of indexing, searching, and retrieving data. The document also covers Elasticsearch's features for scalability, multi-tenancy, settings, consistency, integration with other systems, and compares it to SOLR.
One Size Fits All
One Size Fits AllClaudio Meinberg The document outlines prerequisites for developing Android applications using SDK, ADT, and Cordova with a 'Hello World' example. It includes code snippets for various functionalities like geolocation, notifications, contacts, and page structure using jQuery Mobile. Additionally, it provides contact information for Claudio Ortiz Meinberg along with links to his profiles and resources.
Similar to Node.js Authentication and Data Security (20)
Security in Node.JS and Express:
Security in Node.JS and Express:Petros Demetrakopoulos - Server-side JavaScript injection, cross-site scripting attacks, SQL injections, and cross-site request forgery are common security vulnerabilities in Node.js and Express applications. The document provides recommendations to prevent each vulnerability, including validating user input, escaping output, using prepared statements, and implementing CSRF tokens.
- Data validation and sanitization should be implemented for all endpoints accepting user data. Packages like express-validator can define validation schemas and sanitize input. Logging each request and response is also important for security monitoring and auditing.
Secure Coding for NodeJS
Secure Coding for NodeJSThang Chung This document provides an overview of secure coding practices for Node.js applications. It discusses common vulnerabilities like injection, broken authentication, cross-site scripting, insecure direct object references, security misconfiguration, sensitive data exposure, lack of access controls, CSRF, use of vulnerable components, and unvalidated redirects. For each issue, it provides examples of insecure code and suggestions for more secure implementations using input validation, encryption, access control checks, HTTPS, CSRF tokens, and other best practices. It also lists some useful security tools and resources for Node.js applications.
Authentication in Node.js
Authentication in Node.jsJason Pearson The document discusses authentication in Node.js applications. It covers using HTTP authentication in a low-level HTTP app and Express with Passport. It emphasizes that authentication is about more than just the GUI and stresses not trusting the client. It discusses storing credentials with hashing and salts, keeping applications stateless when load balanced, and comparing authentication schemes like ECB, CBC, and GCM encryption. Code examples demonstrate creating a user and implementing authentication.
IRJET- Login System for Web: Session Management using BCRYPTJS
IRJET- Login System for Web: Session Management using BCRYPTJSIRJET Journal This document summarizes a research paper on using bcryptjs to generate custom session IDs for user authentication and session management. It describes how bcryptjs can be used to hash a custom string generated from a user's details to create a unique customHash for the user. This customHash is stored in the database and local/session storage and can be used on subsequent requests to authenticate the user without transmitting a traditional session ID cookie. The document outlines the algorithm, provides pseudocode, and discusses some security considerations for using this approach.
Client Server Security with Flask and iOS
Client Server Security with Flask and iOSMake School This document discusses client server security, including three aspects of security (authentication, authorization, secure coding), encryption techniques (symmetric, asymmetric, hashing), and three practical security lessons. It provides examples of implementing authentication and user signup securely in a Flask application, including using bcrypt to hash passwords with a salt and protecting against injection attacks by sanitizing user input.
DEF CON 23 - amit ashbel and maty siman - game of hacks
DEF CON 23 - amit ashbel and maty siman - game of hacks Felipe Prado The document discusses various security vulnerabilities found in a Node.js game called Game of Hacks (GoH). It summarizes vulnerabilities explored over multiple versions of GoH, including issues with the client-side timer that could be manipulated, JSON-based SQL injection via user-supplied data, regular expression denial of service attacks, and server poisoning via traceless routing hijacking. The document provides examples of exploiting some of these vulnerabilities and emphasizes the importance of validating user input and avoiding CPU-intensive tasks in Node.js applications.
The Ultimate Node.js Resource Cheat Sheet 📝: Learn Everything Free
The Ultimate Node.js Resource Cheat Sheet 📝: Learn Everything FreeTapp AI 🚀 The Ultimate Node.js 📚 Resource Cheat Sheet 📝: Learn Everything Free is your go-to guide for mastering Node.js from scratch! This all-in-one resource covers core concepts, Express.js, databases (MongoDB, PostgreSQL), authentication, security, debugging, deployment, and must-know tools—all with free learning materials. Whether you're a beginner or looking to level up, this cheat sheet provides hands-on examples, GitHub repositories, and project ideas to help you build real-world applications. Bookmark it, practice, and start coding today!
MSWD:MERN STACK WEB DEVELOPMENT COURSE CODE
MSWD:MERN STACK WEB DEVELOPMENT COURSE CODEannalakshmi35 This document discusses CORS, authentication, authorization, and connecting a backend to MongoDB. It defines CORS as a security feature that controls cross-origin resource sharing. It explains that authentication verifies a user's identity through credentials, while authorization determines what resources an authenticated user can access. It then provides a detailed guide to building an authentication API with JWT tokens in Node.js, including creating routes for registration, login, and protected resources. Finally, it outlines the steps to connect a backend framework like Node.js to MongoDB, including installing drivers and performing operations like data insertion.
Java script and web cryptography (cf.objective)
Java script and web cryptography (cf.objective)ColdFusionConference This document provides an overview of a session on JavaScript and web cryptography. It will explore the current state of JavaScript and web cryptography, reviewing basic concepts and definitions. It will discuss the role of TLS/SSL and provide working examples applying cryptography to real-world use cases. It will also preview the upcoming W3C WebCryptoAPI. Code samples will demonstrate CryptoJS in the browser and Node.js Crypto on the server. An extended example will secure the popular TodoMVC project using PBKDF2 for key generation, HMAC for integrity and AES for encryption.
Web cryptography javascript
Web cryptography javascriptJose Manuel Ortega Candel The document discusses introducing cryptography concepts from a developer perspective using JavaScript. It covers authentication and encryption methods like AES, RSA, and hashing algorithms. It also discusses browser storage, the Web Cryptography API, cryptography libraries for JavaScript like CryptoJS, encrypting data on servers with Node.js, and tools for analyzing encryption. Practical examples are provided on implementing cryptography in apps.
Javascript Security - Three main methods of defending your MEAN stack
Javascript Security - Three main methods of defending your MEAN stackRan Bar-Zik The document outlines critical security practices for JavaScript applications, focusing on vulnerabilities like XSS, CSRF, and SQL injection, emphasizing the importance of input validation and output sanitization. It presents practical solutions such as using validation libraries and middleware in Node.js, along with best practices for ensuring secure application development. Additionally, it stresses that developers don't need to be hackers to implement robust security measures effectively.
Security Challenges in Node.js
Security Challenges in Node.jsWebsecurify The document discusses security challenges associated with Node.js and NoSQL, highlighting common misconceptions about their safety. It provides various JavaScript code examples that demonstrate unexpected behaviors and potential vulnerabilities, particularly in handling JSON and user inputs. Recommendations include always validating user-supplied input to mitigate security risks.
Testing NodeJS Security
Testing NodeJS SecurityJose Manuel Ortega Candel The document discusses security best practices for Node.js applications. It covers using packages like Helmet to set secure HTTP headers, encrypting sessions with packages like cookie-session, preventing XSS attacks with csurf, sanitizing user input with express-validator, and encrypting passwords with bcrypt. It also discusses building secure HTTPS servers, analyzing dependencies for vulnerabilities with tools like NSP and Snyk, and using the Node Goat project to intentionally introduce vulnerabilities for testing security.
Roman Sachenko "NodeJS Security or Blackened is The End"
Roman Sachenko "NodeJS Security or Blackened is The End"NodeUkraine This document provides an overview of common cybersecurity vulnerabilities and best practices for securing Node.js applications. It discusses topics like brute force attacks, database injections, regular expression denial of service (ReDOS) attacks, memory leaks, hijacking the require chain, rainbow table attacks, hash table collision attacks, and timing attacks. It also recommends strategies for prevention including validation, limiting requests, hiding headers, access control, SSL, security tools, and following standards like OWASP top 10. Helpful Node.js security modules are also listed.
Biting into the forbidden fruit. Lessons from trusting Javascript crypto.
Biting into the forbidden fruit. Lessons from trusting Javascript crypto.Krzysztof Kotowicz Krzysztof Kotowicz gave a talk at Hack in Paris in June 2014 about lessons learned from trusting JavaScript cryptography. He discussed the history of skepticism around JS crypto due to language weaknesses like implicit type coercion and lack of exceptions. He then analyzed real-world vulnerabilities in JS crypto libraries like Cryptocat that exploited these issues, as well as web-specific issues like cross-site scripting. Finally, he argued that while the JS language has flaws, developers can still implement crypto securely through practices like strict mode, type checking, and defense-in-depth against web vulnerabilities.
Surviving Web Security
Surviving Web SecurityGergely Németh This document discusses various security vulnerabilities and strategies for defending against attacks. It begins by describing common attacks like SQL injection, brute force attacks, and session hijacking. It then outlines approaches to mitigate these risks such as implementing SSL, input validation, secure cookies, and keeping dependencies up-to-date. The document stresses that security is a shared responsibility and must be incorporated into development practices through techniques like writing stories with security acceptance criteria.
JWT(JSON WEB TOKEN) hand book for beginner
JWT(JSON WEB TOKEN) hand book for beginnerHieuHuy9 The JWT Handbook provides an in-depth overview of JSON Web Tokens (JWTs), detailing their structure, usage, and security considerations. It covers practical applications including client-side sessions, federated identity, and token signing and encryption methods. Additionally, the document explains JWT-related technologies such as JSON Web Keys (JWKs) and algorithms for cryptographic operations.
Building and Scaling Node.js Applications
Building and Scaling Node.js ApplicationsOhad Kravchick The document discusses building and scaling Node.js applications, outlining when to use Node.js and when not to, such as avoiding static file serving and simple CRUD apps. It covers essential setup requirements, includes code snippets for creating simple web servers using Express, and demonstrates the use of middleware and real-time communication with Socket.io. The document also touches on database integration, debugging techniques, concurrency models, and maximizing server capabilities using clustering and shared memory options.
Local SQLite Database with Node for beginners
Local SQLite Database with Node for beginnersLaurence Svekis ✔ The document provides a comprehensive guide on setting up a Node.js application with SQLite database integration and Express framework. It covers installation, creating folders and files, handling user requests, database operations, and how to use Nodemon for server monitoring. The instructor, Laurence Svekis, brings over 20 years of experience in web programming and offers numerous online courses.
Node.js Authentication and Data Security
Node.js Authentication and Data SecurityTim Messerschmidt The document presents a detailed overview of security threats and best practices in Node.js application development, focusing on data encryption, authentication middleware, and techniques to harden Express applications. It highlights common security threats, including the OWASP Top 10 vulnerabilities, and discusses methods such as bcrypt for password hashing and CSRF protection using middleware. Additionally, it emphasizes the balance between security and user experience, providing resources for further learning.
Ad
More from Jonathan LeBlanc (20)
JavaScript App Security: Auth and Identity on the Client
JavaScript App Security: Auth and Identity on the ClientJonathan LeBlanc The document discusses client-side security issues in JavaScript applications, focusing on authentication, authorization, and token management. It covers the importance of treating front-end code as insecure, methods for handling cross-origin requests, and technologies like OAuth 2 and JWT for secure identity verification. The final part emphasizes improving token security through downscoping tokens to minimize exposure and adhere to the least privilege principle.
Improving Developer Onboarding Through Intelligent Data Insights
Improving Developer Onboarding Through Intelligent Data InsightsJonathan LeBlanc The document discusses improving developer onboarding through data-driven insights, emphasizing identifying hurdles, enhancing transparency, and using data to improve documentation. It outlines the importance of analyzing developer anxiety, support requests, and feedback to decrease time to first call and improve engagement with roadmap and changelog communications. Specific examples of successful documentation and feedback implementations are provided, illustrating significant improvements in user experience and service delivery.
Better Data with Machine Learning and Serverless
Better Data with Machine Learning and ServerlessJonathan LeBlanc The document discusses the integration of machine learning with serverless architecture, covering building blocks, best practices, and security considerations. It emphasizes the benefits of serverless frameworks, such as cost-effectiveness and ease of use, while providing detailed insights into system components and machine learning frameworks. Additionally, it outlines best practices for function deployment, error handling, and maintaining data security in serverless environments.
Best Practices for Application Development with Box
Best Practices for Application Development with BoxJonathan LeBlanc The document outlines best practices for application development with Box, focusing on key areas such as data integrity, token management, and access control. It highlights the importance of managing user and service account data securely while addressing common errors encountered during API interactions. Additionally, the document provides guidelines for handling token authentication, storing data, and navigating API error responses effectively.
Box Platform Overview
Box Platform OverviewJonathan LeBlanc The document provides an overview of the Box platform and common use cases for application development. It describes user types, authentication methods, scopes, and four common application patterns: the classic user model, app user model, service account model, and system-to-system model. It also covers topics like error handling, collaboration and permissions, and best practices.
Box Platform Developer Workshop
Box Platform Developer WorkshopJonathan LeBlanc The document provides an overview of common user models, authentication types, and permission patterns for building applications on the Box platform. It discusses classic user models that separate external app users from internal managed users, as well as models where all users are app users or where a service account represents the application. The document also covers authentication using JWT or OAuth2, scopes for controlling application permissions, and best practices for user, collaboration, and error handling.
Modern Cloud Data Security Practices
Modern Cloud Data Security PracticesJonathan LeBlanc The document discusses enhancing and securing data in a world of interconnected devices, focusing on machine learning capabilities and serverless frameworks. It also highlights regulatory compliance challenges and strategies related to data retention, encryption, and data access tokens. Several case studies illustrate practical implementations, including metadata enhancement for video content and security measures for personal data.
Box Authentication Types
Box Authentication TypesJonathan LeBlanc This document discusses different authentication methods for a Box application including:
1. Long-lived access tokens that are restricted to certain API functionality and contain a permission screen.
2. OAuth 2 authentication that requires managing user identities and content.
3. Application access tokens that need to be refreshed every hour and bypass OAuth authentication.
It also provides code samples for OAuth 2 authentication flows and initializing a Box SDK client using JWT authentication with an app's client ID, secret, and signing keys.
Understanding Box UI Elements
Understanding Box UI ElementsJonathan LeBlanc The document discusses user interface components built with React that support authentication and interaction with various user types and environments. It details features such as content exploration, file management (including upload, download, rename, share, and delete), and document preview capabilities. Additionally, it provides code snippets for integrating these functionalities with the Box platform using JavaScript.
Understanding Box applications, tokens, and scoping
Understanding Box applications, tokens, and scopingJonathan LeBlanc The document outlines application access and the associated concerns, including user types, content types, and default scopes for managing data. It details various capabilities enabled by different scopes such as managing users, groups, webhooks, and enterprise properties. Additionally, it discusses advanced features for JWT applications, which allow for user actions and token management without traditional OAuth flows.
The Future of Online Money: Creating Secure Payments Globally
The Future of Online Money: Creating Secure Payments GloballyJonathan LeBlanc The document discusses the future of online payments and securing them globally as mobile device usage increases. It notes that by 2020, more people will have mobile phones than electricity or running water. It then outlines approaches to securing payments through credit card tokenization and other cryptography methods. Finally, it discusses how little data is needed to uniquely identify individuals through factors like location, device details, and purchase history.
Modern API Security with JSON Web Tokens
Modern API Security with JSON Web TokensJonathan LeBlanc The document provides a comprehensive guide on modern API security using JSON Web Tokens (JWT), detailing their benefits over traditional authentication systems and the structure of JWT including its header, payload, and signature. It explains the differences between symmetric and asymmetric algorithms, and offers practical examples of generating, signing, and verifying JWTs. Additionally, it discusses preventing replay attacks and the integration of JWT with OAuth 2.0 for authentication and authorization purposes.
Creating an In-Aisle Purchasing System from Scratch
Creating an In-Aisle Purchasing System from ScratchJonathan LeBlanc The document outlines the development of an in-aisle purchasing system which integrates various payment technologies, including Apple and Android Pay. It discusses tokenization methods, the Luhn algorithm for secure transaction processing, and the security protocols necessary for maintaining the integrity of customer payment data. Additionally, it covers the challenges related to token collision and summarizes key security standards and APIs relevant to the payment architecture.
Protecting the Future of Mobile Payments
Protecting the Future of Mobile PaymentsJonathan LeBlanc The document discusses the future of mobile payments and emphasizes securing user data through various means, including encryption and establishing trust zones. It highlights the importance of location awareness, browser uniqueness, and device fingerprinting in protecting identities and enhancing payment ease. Additionally, it suggests utilizing irregular usage spikes and buying habits to improve usability.
Future of Identity, Data, and Wearable Security
Future of Identity, Data, and Wearable SecurityJonathan LeBlanc The document discusses the challenges surrounding passwords, highlighting that many users rely on weak and common passwords, which undermine security. It emphasizes the importance of improving security through methods like encryption, trusted logins, and the use of wearables and biometrics as unique identifiers for authentication. The overall goal is to enhance secure identity management and data protection.
Kill All Passwords
Kill All PasswordsJonathan LeBlanc The document discusses the shortcomings of traditional passwords, highlighting that many users rely on weak and commonly used passwords. It underscores the need for improved security measures such as better algorithms, variable authentication methods, and identity biometrics. The content suggests that new approaches like OAuth and the FIDO Alliance could pave the way for a more secure identity management system.
BattleHack Los Angeles
BattleHack Los Angeles Jonathan LeBlanc The document outlines the schedule and information for an hackathon event taking place on Saturday and Sunday including times for registration, opening talks, meals, workshops, presentations, and awards ceremony. It also provides details on prizes, codes of conduct, and thanks various partners for their support of the event. Participants are encouraged to follow the event's Twitter account and view photos on Facebook.
Building a Mobile Location Aware System with Beacons
Building a Mobile Location Aware System with BeaconsJonathan LeBlanc Jonathan LeBlanc discusses the creation of a mobile location-aware system using beacons, emphasizing their practical applications and technical specifications. He highlights considerations such as battery life, signal interference, and the necessary permissions for Android integration. The presentation touches on beacon settings adjustment, data collection, and resources for further development.
Identity in the Future of Embeddables & Wearables
Identity in the Future of Embeddables & WearablesJonathan LeBlanc The document discusses the future of identity authentication in the context of wearable and embeddable technology, highlighting the prevalence of weak passwords among users. It explores various authentication methods, including biometrics and location awareness, as potential improvements over traditional username/password systems. The presentation also touches on advanced technologies like DNA data storage and medical ingestibles that could impact identity verification.
Internet Security and Trends
Internet Security and TrendsJonathan LeBlanc The document discusses internet security trends and challenges, including users taking charge of their own security, issues with biometrics like high false positive rates, and insecure logins. It also covers data security, emerging biometrics like vein recognition and heart rate identification, hardware and technology trends such as omni-channel connectivity, Bluetooth Smart, and microelectronics. Additionally, it briefly mentions bitcoin and cryptocurrency. The document was presented by Jonathan LeBlanc from PayPal and Braintree on internet security and technology trends.
Ad
Recently uploaded (20)
EIS-Webinar-Engineering-Retail-Infrastructure-06-16-2025.pdf
EIS-Webinar-Engineering-Retail-Infrastructure-06-16-2025.pdfEarley Information Science As AI reshapes expectations in retail and B2B commerce, organizations are recognizing a critical reality: meaningful AI outcomes depend on well-structured, adaptable infrastructure. In this session, Seth Earley is joined by Phil Ryan - AI strategist, search technologist, and founder of Glass Leopard Technologies - for a candid conversation on what it truly means to engineer systems for scale, agility, and intelligence.
Phil draws on more than two decades of experience leading search and AI initiatives for enterprise organizations. Together, he and Seth explore the challenges businesses face when legacy architectures limit personalization, agility, and real-time decisioning - and what needs to change to support agentic technologies and next-best-action capabilities.
Key themes from the webinar include:
Composability as a prerequisite for AI - Why modular, loosely coupled systems are essential for adapting to rapid innovation and evolving business needs
Search and relevance as foundational to AI - How techniques honed-in enterprise search have laid the groundwork for more responsive and intelligent customer experiences
From MDM and CDP to agentic systems - How data platforms are evolving to support richer customer context and dynamic orchestration
Engineering for business alignment - Why successful AI programs require architectural decisions grounded in measurable outcomes
The conversation is practical and forward-looking, connecting deep technical understanding with real-world business needs. Whether you’re modernizing your commerce stack or exploring how AI can enhance product discovery, personalization, or customer journeys, this session provides a clear-eyed view of the capabilities, constraints, and priorities that matter most.
Using the SQLExecutor for Data Quality Management: aka One man's love for the...
Using the SQLExecutor for Data Quality Management: aka One man's love for the...Safe Software The SQLExecutor is one of FME’s most powerful and flexible transformers. Pivvot maintains a robust internal metadata hierarchy used to support ingestion and curation of thousands of external data sources that must be managed for quality before entering our platform. By using the SQLExecutor, Pivvot can efficiently detect problems and perform analysis before data is extracted from our staging environment, removing the need for rollbacks or cycles waisted on a failed job. This presentation will walk through three distinct examples of how Pivvot uses the SQLExecutor to engage its metadata hierarchy and integrate with its Data Quality Management workflows efficiently and within the source postgres database. Spatial Validation –Validating spatial prerequisites before entering a production environment. Reference Data Validation - Dynamically validate domain-ed columns across any table and multiple columns per table. Practical De-duplication - Removing identical or near-identical well point locations from two distinct source datasets in the same table.
"How to survive Black Friday: preparing e-commerce for a peak season", Yurii ...
"How to survive Black Friday: preparing e-commerce for a peak season", Yurii ...Fwdays We will explore how e-commerce projects prepare for the busiest time of the year, which key aspects to focus on, and what to expect. We’ll share our experience in setting up auto-scaling, load balancing, and discuss the loads that Silpo handles, as well as the solutions that help us navigate this season without failures.
OpenACC and Open Hackathons Monthly Highlights June 2025
OpenACC and Open Hackathons Monthly Highlights June 2025OpenACC The OpenACC organization focuses on enhancing parallel computing skills and advancing interoperability in scientific applications through hackathons and training. The upcoming 2025 Open Accelerated Computing Summit (OACS) aims to explore the convergence of AI and HPC in scientific computing and foster knowledge sharing. This year's OACS welcomes talk submissions from a variety of topics, from Using Standard Language Parallelism to Computer Vision Applications. The document also highlights several open hackathons, a call to apply for NVIDIA Academic Grant Program and resources for optimizing scientific applications using OpenACC directives.
A Constitutional Quagmire - Ethical Minefields of AI, Cyber, and Privacy.pdf
A Constitutional Quagmire - Ethical Minefields of AI, Cyber, and Privacy.pdfPriyanka Aash A Constitutional Quagmire - Ethical Minefields of AI, Cyber, and Privacy
AI VIDEO MAGAZINE - June 2025 - r/aivideo
AI VIDEO MAGAZINE - June 2025 - r/aivideo1pcity Studios, Inc AI VIDEO MAGAZINE - r/aivideo community newsletter – Exclusive Tutorials: How to make an AI VIDEO from scratch, PLUS: How to make AI MUSIC, Hottest ai videos of 2025, Exclusive Interviews, New Tools, Previews, and MORE - JUNE 2025 ISSUE -
Securing Account Lifecycles in the Age of Deepfakes.pptx
Securing Account Lifecycles in the Age of Deepfakes.pptxFIDO Alliance Securing Account Lifecycles in the Age of Deepfakes
The Future of Technology: 2025-2125 by Saikat Basu.pdf
The Future of Technology: 2025-2125 by Saikat Basu.pdfSaikat Basu A peek into the next 100 years of technology. From Generative AI to Global AI networks to Martian Colonisation to Interstellar exploration to Industrial Nanotechnology to Artificial Consciousness, this is a journey you don't want to miss. Which ones excite you the most? Which ones are you apprehensive about? Feel free to comment! Let the conversation begin!
WebdriverIO & JavaScript: The Perfect Duo for Web Automation
WebdriverIO & JavaScript: The Perfect Duo for Web Automationdigitaljignect In today’s dynamic digital landscape, ensuring the quality and dependability of web applications is essential. While Selenium has been a longstanding solution for automating browser tasks, the integration of WebdriverIO (WDIO) with Selenium and JavaScript marks a significant advancement in automation testing. WDIO enhances the testing process by offering a robust interface that improves test creation, execution, and management. This amalgamation capitalizes on the strengths of both tools, leveraging Selenium’s broad browser support and WDIO’s modern, efficient approach to test automation. As automation testing becomes increasingly vital for faster development cycles and superior software releases, WDIO emerges as a versatile framework, particularly potent when paired with JavaScript, making it a preferred choice for contemporary testing teams.
GenAI Opportunities and Challenges - Where 370 Enterprises Are Focusing Now.pdf
GenAI Opportunities and Challenges - Where 370 Enterprises Are Focusing Now.pdfPriyanka Aash GenAI Opportunities and Challenges - Where 370 Enterprises Are Focusing Now
Connecting Data and Intelligence: The Role of FME in Machine Learning
Connecting Data and Intelligence: The Role of FME in Machine LearningSafe Software In this presentation, we want to explore powerful data integration and preparation for Machine Learning. FME is known for its ability to manipulate and transform geospatial data, connecting diverse data sources into efficient and automated workflows. By integrating FME with Machine Learning techniques, it is possible to transform raw data into valuable insights faster and more accurately, enabling intelligent analysis and data-driven decision making.
PyCon SG 25 - Firecracker Made Easy with Python.pdf
PyCon SG 25 - Firecracker Made Easy with Python.pdfMuhammad Yuga Nugraha Explore the ease of managing Firecracker microVM with the firecracker-python. In this session, I will introduce the basics of Firecracker microVM and demonstrate how this custom SDK facilitates microVM operations easily. We will delve into the design and development process behind the SDK, providing a behind-the-scenes look at its creation and features. While traditional Firecracker SDKs were primarily available in Go, this module brings a simplicity of Python to the table.
Oh, the Possibilities - Balancing Innovation and Risk with Generative AI.pdf
Oh, the Possibilities - Balancing Innovation and Risk with Generative AI.pdfPriyanka Aash Oh, the Possibilities - Balancing Innovation and Risk with Generative AI
9-1-1 Addressing: End-to-End Automation Using FME
9-1-1 Addressing: End-to-End Automation Using FMESafe Software This session will cover a common use case for local and state/provincial governments who create and/or maintain their 9-1-1 addressing data, particularly address points and road centerlines. In this session, you'll learn how FME has helped Shelby County 9-1-1 (TN) automate the 9-1-1 addressing process; including automatically assigning attributes from disparate sources, on-the-fly QAQC of said data, and reporting. The FME logic that this presentation will cover includes: Table joins using attributes and geometry, Looping in custom transformers, Working with lists and Change detection.
The Future of Product Management in AI ERA.pdf
The Future of Product Management in AI ERA.pdfAlyona Owens Hi, I’m Aly Owens, I have a special pleasure to stand here as over a decade ago I graduated from CityU as an international student with an MBA program. I enjoyed the diversity of the school, ability to work and study, the network that came with being here, and of course the price tag for students here has always been more affordable than most around.
Since then I have worked for major corporations like T-Mobile and Microsoft and many more, and I have founded a startup. I've also been teaching product management to ensure my students save time and money to get to the same level as me faster avoiding popular mistakes. Today as I’ve transitioned to teaching and focusing on the startup, I hear everybody being concerned about Ai stealing their jobs… We’ll talk about it shortly.
But before that, I want to take you back to 1997. One of my favorite movies is “Fifth Element”. It wowed me with futuristic predictions when I was a kid and I’m impressed by the number of these predictions that have already come true. Self-driving cars, video calls and smart TV, personalized ads and identity scanning. Sci-fi movies and books gave us many ideas and some are being implemented as we speak. But we often get ahead of ourselves:
Flying cars,Colonized planets, Human-like AI: not yet, Time travel, Mind-machine neural interfaces for everyone: Only in experimental stages (e.g. Neuralink).
Cyberpunk dystopias: Some vibes (neon signs + inequality + surveillance), but not total dystopia (thankfully).
On the bright side, we predict that the working hours should drop as Ai becomes our helper and there shouldn’t be a need to work 8 hours/day. Nobody knows for sure but we can require that from legislation. Instead of waiting to see what the government and billionaires come up with, I say we should design our own future.
So, we as humans, when we don’t know something - fear takes over. The same thing happened during the industrial revolution. In the Industrial Era, machines didn’t steal jobs—they transformed them but people were scared about their jobs. The AI era is making similar changes except it feels like robots will take the center stage instead of a human. First off, even when it comes to the hottest space in the military - drones, Ai does a fraction of work. AI algorithms enable real-time decision-making, obstacle avoidance, and mission optimization making drones far more autonomous and capable than traditional remote-controlled aircraft. Key technologies include computer vision for object detection, GPS-enhanced navigation, and neural networks for learning and adaptation. But guess what? There are only 2 companies right now that utilize Ai in drones to make autonomous decisions - Skydio and DJI.
Quantum AI Discoveries: Fractal Patterns Consciousness and Cyclical Universes
Quantum AI Discoveries: Fractal Patterns Consciousness and Cyclical UniversesSaikat Basu Embark on a cosmic journey exploring the intersection of quantum
computing, consciousness, and ancient wisdom. Together we'll uncover the
recursive patterns that bind our reality.
Enhance GitHub Copilot using MCP - Enterprise version.pdf
Enhance GitHub Copilot using MCP - Enterprise version.pdfNilesh Gule Slide deck related to the GitHub Copilot Bootcamp in Melbourne on 17 June 2025
Node.js Authentication and Data Security
- 1. Node.js Authentication and Data Security! Jonathan LeBlanc ! Twitter: @jcleblanc ! Book: http://bit.ly/iddatasecurity!
- 2. Release Date:! August 2016! ! Book Details:! http://bit.ly/iddatasecurity! Identity & Data Security Book!
- 4. 1: 123456 ! 2: password ! 3: 12345678 ! 4: qwerty ! 5: 12345 ! 6: 123456789! 7: football! 8: 1234! 9: 1234567! Top 25 Passwords of 2015! 10: baseball! 11: welcome! 12: 1234567890! 13: abc123! 14: 111111! 15: 1qaz2wsx! 16: dragon! 17: master! 18: monkey! 19: letmein! 20: login! 21: princess! 22: qwertyuiop! 23: solo! 24: passw0rd! 25: starwars!
- 8. Brute Force Attacks! Calculate all key variations within a given length, then trying each one until the password is guessed. ! Protect via: Key stretching, CAPTCHA, 2FA! ! Dictionary Attacks! Use a list of predetermined words/phrase to guess password.! Protect via: Salting! ! Rainbow Tables! Use precalculated password hashes to break encryption.! Protect via: Salting ! Protecting Against Password Attacks!
- 10. //hashing identical messages with no salt! hash('mechagodzilla') = ! 162e0a91026a28f1f2afa11099d1fcbdd9f2e351095ebb196c90e10290ef1227! hash('mechagodzilla') = ! 162e0a91026a28f1f2afa11099d1fcbdd9f2e351095ebb196c90e10290ef1227! ! //hashing identical messages with random salt! hash('mechagodzilla' + '458cf2979ef27397db67077775225334') = ! f3499a916612e285612b32702114751f557a70606c32b54b92de55153d40d3b6! hash('mechagodzilla' + 'ef5b72eff781b09a0784438af742dd6e') = ! 7e29c5c48f44755598dec3549155ad66f1af4671091353be4c4d7694d71dc866! hash('mechagodzilla' + 'cc989b105a1c6a5f0fb460e29dd272f3') = ! 6dedd3dbb0639e6e00ca0bf6272c141fb741e24925cb7548491479a1df2c215e! Hashing with and without salts!
- 11. Storing Salts! Store alongside the hash! ! Salt Reuse! Salts should be be unique per password! ! Salt Length! Same size as hash? 64 bits? 128 bits?! Considerations when using Salts!
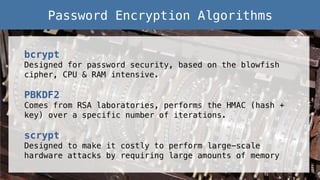
- 12. bcrypt! Designed for password security, based on the blowfish cipher, CPU & RAM intensive.! ! PBKDF2! Comes from RSA laboratories, performs the HMAC (hash + key) over a specific number of iterations.! ! scrypt! Designed to make it costly to perform large-scale hardware attacks by requiring large amounts of memory! Password Encryption Algorithms!
- 13. ! var bcrypt = require('bcrypt');! ! app.post("/register", function(req, res){! //capture user login information! var username = req.body.username;! var password = req.body.password;! ! //generate salt, then hash! bcrypt.genSalt(10, function(err, salt) {! bcrypt.hash(password, salt, function(err, key) {! console.log('key: ' + key.toString('hex'));! console.log('salt: ' + salt.toString('hex'));! });! });! });! ! Hashing with bcrypt!
- 14. ! var bcrypt = require('bcrypt');! ! app.post("/login", function(req, res){! //capture user login information! var username = req.body.username;! var password = req.body.password;! ! //fetch user record from database ! //required info: stored hash! ! //compare password from login to stored user hash! bcrypt.compare(password, hash, function(err, res){! //returns true or false! });! });! ! Login Hash Comparison with bcrypt!
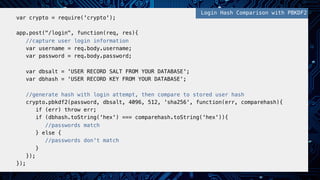
- 15. ! var crypto = require('crypto');! ! app.post("/register", function(req, res){! //capture user login information! var username = req.body.username;! var password = req.body.password;! ! //generate salt, then hash! crypto.randomBytes(32, function(ex, salt){! crypto.pbkdf2(password, salt, 4096, 512, 'sha256', function(err, key){! if (err) throw err;! //store username, hashed password, and salt in your database! });! });! });! ! Hashing with PBKDF2!
- 16. ! var crypto = require('crypto');! ! app.post("/login", function(req, res){! //capture user login information! var username = req.body.username;! var password = req.body.password;! ! var dbsalt = 'USER RECORD SALT FROM YOUR DATABASE';! var dbhash = 'USER RECORD KEY FROM YOUR DATABASE';! ! //generate hash with login attempt, then compare to stored user hash! crypto.pbkdf2(password, dbsalt, 4096, 512, 'sha256', function(err, comparehash){! if (err) throw err;! if (dbhash.toString('hex') === comparehash.toString('hex')){ ! //passwords match! } else { ! //passwords don't match! }! });! });! ! Login Hash Comparison with PBKDF2!
- 18. Protecting Data!
- 20. Domain Validation (DV)! Certificate authority (CA) validates domain access only! Certificate Types!
- 21. Organization Validation (OV)! ! CA validates DV and basic organization information! Certificate Types!
- 22. Extended Validation (EV)! CA validates DV, OV, and legal existance of the organization! Certificate Types!
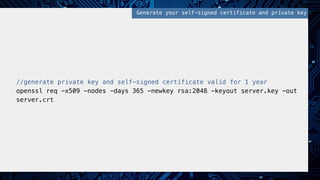
- 24. //generate private key and self-signed certificate valid for 1 year! openssl req -x509 -nodes -days 365 -newkey rsa:2048 -keyout server.key -out server.crt! Generate your self-signed certificate and private key!
- 25. //package requirements! var fs = require('fs'),! https = require('https'),! querystring = require('querystring'),! bodyParser = require('body-parser')! app = require('express')();! ! //support JSON & URL encoded bodies! app.use(bodyParser.json()); ! app.use(bodyParser.urlencoded({ ! extended: true! })); ! Setting up Express server for HTTPS traffic!
- 26. //handle all POST requests! app.post('/', function (req, res){! var message = req.body;! res.send('Message received:' + querystring.stringify(message));! });! ! //set certificate options! var options = {! key: fs.readFileSync('server.key'),! cert: fs.readFileSync('server.crt'),! passphrase: 'YOUR KEY PASSWORD' ! };! ! //create server with certificate options! https.createServer(options, app).listen(3000, function () {! console.log('Server started: Listening on port 3000');! });! Setting up Express server for HTTPS traffic!
- 31. Encryption (ECB, CBC, OFB, CFB, CTR)! Data privacy and confidentiality mode. Attacker cannot obtain info on the plaintext data.! ! Authentication(CMAC)! Data authenticity mode. Receiver can validate whether cleartext came from intended sender.! ! Authenticated Encryption (CCM, GCM, KW/KWP/TKW)! Includes both data privacy and authenticity.! Modes of Operation!
- 32. var crypto = require('crypto');! ! var text = "Encryption Testing AES";! var key = crypto.randomBytes(32); //256 bit shared secret! var iv = crypto.randomBytes(16); //initialization vector - 16 bytes! var algorithm = 'aes-256-ctr'; //cypher and mode of operation! ! //encrypt! var cipher = crypto.createCipher(algorithm, key, iv);! var encrypted = cipher.update(text, 'utf8', 'hex');! encrypted += cipher.final('hex');! console.log("Encrypted: " + encrypted);! Configuring and encrypting message!
- 33. //----! // data sent to server: ciphertext (encrypted var)! // data known by server: key! //----! ! //cypher and mode of operation! var algorithm = 'aes-256-gcm'; ! ! //decrypt! var decipher = crypto.createDecipher(algorithm, key, iv);! var decrypted = decipher.update(encrypted, 'hex', 'utf8');! decrypted += decipher.final('utf8');! console.log("Decrypted: " + decrypted);! Decrypting ciphertext!
- 35. Thank You!! ! Slides: http://slideshare.net/jcleblanc! Jonathan LeBlanc ! Twitter: @jcleblanc ! Book: http://bit.ly/iddatasecurity!
