Ad
Node.js security
- 1. Maciej Lasyk, node.js security Maciej Lasyk SEConference Kraków, 2014-05-09 node.js security
- 2. Sysadmin about node.js security? - not only sysadmin ;) - node needs thorough understanding of whole infra - 14+ years of exp software dev. / sysop - currently “noding” 4 prv & Fedora Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25Maciej Lasyk, node.js security
- 3. JS security recap – evals & co eval() like fncs takes string argument and evalute those as source code Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25Maciej Lasyk, node.js security
- 4. JS security recap – evals & co eval() like fncs takes string argument and evalute those as source code Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25 srsly – who does that? Maciej Lasyk, node.js security
- 5. JS security recap – evals & co Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25 var x = req.body.x; var y = req.body.y; var sum = eval(a + "+" + b); Maciej Lasyk, node.js security
- 6. JS security recap – evals & co Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25 var x = req.body.x; var y = req.body.y; var sum = eval(a + "+" + b); what if attacker fills 'x' with: some.super.class.wipe.the.database('now'); LOL :) Maciej Lasyk, node.js security
- 7. JS security recap – evals & co Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25 not only evals: setInterval(code,2) setTimeout(code,2) str = new Function(code) Chrome CSP denies those also :) Maciej Lasyk, node.js security
- 8. JS security recap – global namespace pollution - node.js is single threaded - all variable values are common - one could thrtically change bhv of others reqs - watch out for globals then! Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25Maciej Lasyk, node.js security
- 9. JS security recap – global namespace pollution some very awful example: Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25 var auth = false; app.get('/auth', function(req, res) { if(legit) { auth = true; res.send("success"); }); app.get('/payments-db', function(req, res) { if (auth) res.send("legit to see all payments data"); else res.send("not logged in"); }) app.listen(8080); Maciej Lasyk, node.js security
- 10. JS security recap – global namespace pollution Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25 So now imagine.. global namespace pollution + evals & co Maciej Lasyk, node.js security
- 11. JS security recap – global namespace pollution Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25 So now imagine.. global namespace pollution + evals & co Maciej Lasyk, node.js security
- 12. JS security recap – global namespace pollution Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25 So now imagine.. global namespace pollution + evals & co Watch out who you are hiring Maciej Lasyk, node.js security
- 13. JS security recap – strict mode - let's throw all errors! - declare variables! - global namespaces help Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25Maciej Lasyk, node.js security
- 14. JS security recap – strict mode Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25 "use strict"; function testFunction(){ var testvar = 4; return testvar; } // This causes a syntax error. testvar = 5; Maciej Lasyk, node.js security
- 15. JS security recap – strict mode Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25 // This causes a syntax error: "use strict"; testvar = 5; // This is ok: "use strict"; var testvar = 0; testvar = 5; Maciej Lasyk, node.js security
- 16. JS security recap – strict mode - evals & co are not that insecure now - no access to caller and args props - enable globally or for some scope - what about strict mode in 3rd party mods? Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25Maciej Lasyk, node.js security
- 17. JS security recap – strict mode Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25 "use strict"; function do_smt() { do_smt.caller; // no way :) do_smt.arguments; // no way :) } Maciej Lasyk, node.js security
- 18. JS security recap – strict mode Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25 "use strict"; eval("var smt = 123"); console.log(smt); // sorry – ReferenceError Maciej Lasyk, node.js security
- 19. JS security recap – strict mode Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25 "use strict"; eval("var smt = 123"); console.log(smt); // sorry – ReferenceError But watch out: "use strict"; var smt = 0; eval("smt = 123"); console.log(smt); // outputs “123” properly Maciej Lasyk, node.js security
- 20. JS security recap – object properties - writable: RO/RW - enumerable: no loops enumeration - configurable: deletion prohibited - all default set to True so watch out Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25Maciej Lasyk, node.js security
- 21. JS security recap – object properties var obj = {}; obj.prop = "LOL"; // OR: Object.defineProperty(obj, "prop", { writable: true, enumerable: true, configurable: true, value: "LOL" }) Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25Maciej Lasyk, node.js security
- 22. JS security recap – object properties // RO & immutable property def: var obj = {}; Object.defineProperty(obj, "prop", { value: "LOL" }); Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25Maciej Lasyk, node.js security
- 23. JS security recap – static code analysis - If not doing it already – just do - Commit hooks in (D)VCSes - JSHint / JSLint - Create policy for static code analysis - Update & check this policy regularly Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25Maciej Lasyk, node.js security
- 24. about node.js: what's up? - current stable version 0.10.28 - who is using node? https://github.com/joyent/node/wiki/Projects,-Applications,-and-Companies-Using-Node - Operating Node.js in production/Bryan Cantrill (Joyent) - Bill Scott,“Clash of the Titans: Kraken | Node.js @ paypal” Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25
- 25. about node.js: model Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25Maciej Lasyk, node.js security
- 26. about node.js: concurrency - node.js is single threaded (let's say) - multi – core? child processes (cluster.fork) - Linux containers ftw! Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25Maciej Lasyk, node.js security
- 27. about node.js: SPA Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25 (thx Sekurak.pl for this image) Maciej Lasyk, node.js security
- 28. node.js sec: exploits anyone? - http://seclists.org/bugtraq – 0 hits - http://osvdb.org – 2 hits - http://1337day.com, http://www.exploitdb.com – 1 hit - http://nodesecurity.io/advisories – 4 hits Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25Maciej Lasyk, node.js security
- 29. node.js sec: exploits anyone? - http://seclists.org/bugtraq – 0 hits - http://osvdb.org – 2 hits - http://1337day.com, http://www.exploitdb.com – 1 hit - http://nodesecurity.io/advisories – 4 hits Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25 Such security big? Maciej Lasyk, node.js security
- 30. node.js sec: exploits anyone? - http://seclists.org/bugtraq – 0 hits - http://osvdb.org – 2 hits - http://1337day.com, http://www.exploitdb.com – 1 hit - http://nodesecurity.io/advisories – 4 hits Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25 Such security big? not exactly Maciej Lasyk, node.js security
- 31. node.js sec: what's wrong? node.js security is a blank page Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25 http://www.slideshare.net/ASF-WS/asfws-2012-nodejs-security-old-vulnerabilities-in-new-dresses-par-sven-vetsch Maciej Lasyk, node.js security
- 32. node.js sec: how does sec look like? Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25Maciej Lasyk, node.js security
- 33. node.js sec: how does sec look like? Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25 Such security..Such security.. Very fortress!!1Very fortress!!1 WOW :)WOW :) Maciej Lasyk, node.js security
- 34. node.js sec: exceptions / callbacks callbacks Error object – remember to handle those Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25 var fs = require("fs"); fs.readFile("/some/file", "utf8", function (err, contents) { // err will be null if no error occured // ... otherwise there will be info about error }); forget about handling and die debugging Maciej Lasyk, node.js security
- 35. node.js sec: exceptions / eventemitter EventEmitter: emitting events 4 async actions Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25 var http = require("http"); http.get("http://nodejs.org/", function (res) { res.on("data", function (chunk) { do_something_with_chunk; }); res.on("error", function (err) { // listener handling error }); }); Attach listeners to errors events or welcome unhandled exception! Maciej Lasyk, node.js security
- 36. node.js sec: uncaught exceptions - by default node.js will print stack trace and terminate thread - EventEmitter / process / uncaughtException Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25 // it looks like this by default: process.on("uncaughtException", function (err) { console.error(err); console.trace(); process.exit(); }); Maciej Lasyk, node.js security
- 37. node.js sec: uncaught exceptions - by default node.js will print stack trace and terminate thread - EventEmitter / process / uncaughtException Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25 // it looks like this by default: process.on("uncaughtException", function (err) { console.error(err); console.trace(); process.exit(); }); So do you really want to comment out the 'process.exit()' line? Maciej Lasyk, node.js security
- 38. node.js sec: clusters scaling within multi-core envs Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25 var cluster = require('cluster'); var http = require('http'); var numCPUs = require('os').cpus().length; if (cluster.isMaster) { for (var i = 0; i < numCPUs; i++) { cluster.fork(); } cluster.on('exit', function(worker, code, signal) { console.log(worker.process.pid + ' died'); }); } else { http.createServer(function(req, res) { res.writeHead(200); res.end("hello worldn"); }).listen(8000); } Maciej Lasyk, node.js security
- 39. node.js sec: domains Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25 Handling multiple different IO operations as a single group // don't do that: var d = require('domain').create(); d.on('error', function(er) { console.log('error, but oh well', er.message); }); d.run(function() { require('http').createServer(function(req, res) { handleRequest(req, res); }).listen(PORT); }); Maciej Lasyk, node.js security
- 40. node.js sec: domains Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25 Rather use cluster & forks and exit gently..: create_cluster; fork_workers; if(worker){ var domain = require('domain'); var server = require('http').createServer(function(req, res) { var d = domain.create(); d.on('error', function(er) { console.error('error', er.stack); try { // set timeout timer // update master && print err msg // close server } catch (er2) { console.error('Error 500!', er2.stack); } } Maciej Lasyk, node.js security
- 41. node.js sec: domains Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25 Using Express take look at that: https://github.com/brianc/node-domain-middleware Assigning each Express request to a separate domain? Maciej Lasyk, node.js security
- 42. node.js sec: npm modules - npm install (-g) - who creates modules? - who verifies those? - how to update? - semantic versioning in package.json - "connect":"~1.8.7" -> 1.8.7 - 1.9 Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25Maciej Lasyk, node.js security
- 43. node.js sec: npm modules --ignore-scripts stop preinstall/prepublish scripts - mods auditing: https://nodesecurity.io/ Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25Maciej Lasyk, node.js security
- 44. node.js sec: npm modules The scale of npm modules Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25Maciej Lasyk, node.js security
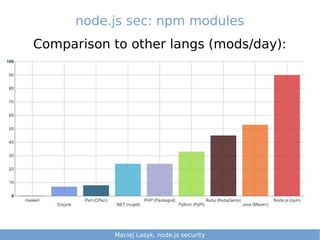
- 45. node.js sec: npm modules Comparison to other langs (mods/day): Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25Maciej Lasyk, node.js security
- 46. node.js sec: npm modules Remember: - use strict? - static analysis? - does include some test suite? - what is the dependency tree? Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25Maciej Lasyk, node.js security
- 47. node.js.express: connect / express Express – web dev framework Built on top of connect Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25Maciej Lasyk, node.js security
- 48. node.js.express: auth.basic_auth Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25 var express = require('express'), app = express(); app.use(express.basicAuth("user", "pwd")); app.get("/", function (req, res) { res.send('Hello World'); }); app.listen(8080); Plain text and simple auth issues Maciej Lasyk, node.js security
- 49. node.js.express: auth.basic_auth Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25 var users = { admin: "admin123", user: "user456" }; app.use(express.basicAuth(function (user, pass) { return users.hasOwnProperty(user) && users[user] === pass; })); Maciej Lasyk, node.js security
- 50. node.js.express: auth.SSL Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25 var express = require('express'), routes = require('./routes'), fs = require('fs') var opts = { key: fs.readFileSync('ssl/server/keys/server.key'), cert: fs.readFileSync('ssl/server/certificates/server.crt'), ca: fs.readFileSync('ssl/ca/ca.crt'), crl: fs.readFileSync('ssl/ca/ca.crl'), requestCert: true, rejectUnauthorized: true passphrase: "pwd" // <<<< really here? }; var app = module.exports = express.createServer(opts); app.configure(function(){ app.set('views', __dirname + '/views'); ... }); app.get('/', routes.index); app.listen(8443); Maciej Lasyk, node.js security
- 51. node.js.express: passport.js - provides API for authentication and authorization - authentication: - LocalStrategy - OpenIDStrategy - OAuth / FacebookStrategy Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25Maciej Lasyk, node.js security
- 52. node.js.express: authorization Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25 var users = [ { id: 1, name: "user1", role: "admin" }, { id: 2, name: "user2", role: "common" }, ]; function loadUser(req, res, next) { req.userData = users[req.params.user]; return next(); } function requireRole(role) { return function (req, res, next) { if (req.user.role === role) { return next(); } else { return next(new Error("Unauthorized")); } };} Maciej Lasyk, node.js security
- 53. node.js.express: authorization Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25 app.get("/users/:user", loadUser, function (req, res) { res.send(req.user.name); }); app.del("/users/:user", requireRole("admin"), loadUser, function (req,res) { res.send("User deleted"); }); Maciej Lasyk, node.js security
- 54. node.js.express: logging OWASP will tell you what should be logged :) https://www.owasp.org/index.php/Logging_Cheat_Sheet - authentication & authorisation - session management - errors & weirdo events - events (startups, shutdowns, slowdowns etc) - high risk functionalities (payments, privileges, admins) Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25Maciej Lasyk, node.js security
- 55. node.js.express: logging Try Winston module (Github -> flatiron/winston) Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25 - logging to console - logging to file - sending logs over HTTP - CouchDB, Redis, MongoDB, Riak etc Maciej Lasyk, node.js security
- 56. node.js.express: logging Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25 var winston = require('winston'); var logger = new (winston.Logger)({ transports: [ new (winston.transports.Console)(), new (winston.transports.File)({ filename: 'application.log' }) ] }); Maciej Lasyk, node.js security
- 57. node.js.express: sessions Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25 var express = require('express'); var app = express(); var RedisStore = require('connect-redis')(express); app.use(express.cookieParser()); app.use(express.session({ store: new RedisStore({ host: '127.0.0.2', port: 6379, db: 3, pass: 'pwd' }), secret: 'this-is-very-secret' })); app.get('/somewhere', function(req, res) { res.send('In the middle of nowhere'); }); app.listen(process.env.PORT || 8080); Maciej Lasyk, node.js security
- 58. node.js.express: sessions Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25 app.use(express.session({ secret: “very-secret”, key: “sessionId”, cookie: { httpOnly: true, secure: true } })); Maciej Lasyk, node.js security
- 59. node.js.CSI: CSRF Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25 var express = require("express"), app = express(); app.use(express.cookieParser()); app.use(express.bodyParser()); app.use(express.session({ secret: "very-secret" })); app.use(express.csrf()); Maciej Lasyk, node.js security
- 60. node.js.CSI: CSRF Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25 app.get("/valid", function (req, res) { <input type="hidden" name="_csrf" value="+req.CsrfToken()+"> res.send(output); }); app.get("/invalid", function (req, res) { no_csrf_token_field res.send(output); }); Express CSRF ignores CSRF on HTTP, GET, OPTIONS, HEAD reqs Maciej Lasyk, node.js security
- 61. node.js.CSI: input.validation Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25 var express = require("express"), app = module.exports = express(); app.use(express.bodyParser()); app.use(require("express-validator")()); app.get("/", function (req, res) { res.sendfile(__dirname + "/tpls/validate.html"); }); app.post("/", function (req, res, next) { // validation req.checkBody("name").notEmpty().is(/w+/); // filtering req.sanitize("name").trim(); ... } Maciej Lasyk, node.js security
- 62. node.js.CSI: XSS - XSS allows to access cookies, session tokens etc - or even redirect user to malicious sites - Myth: frameworks / tpls does the anti-XSS job - always encode untrusted data for correct context - OWASP ESAPI Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25Maciej Lasyk, node.js security
- 63. node.js.CSI: DoS - Error handling - Use streams / chunking - Use monitoring - Use domains / clusters - Don't be afraid of SlowLoris :) Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25Maciej Lasyk, node.js security
- 64. node.js.CSI: ReDoS - Regex could take exponential execution time - Is regex executed in the event loop thread? - Regex and user input? Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25 https://speakerdeck.com/ckarande/top-overlooked-security-threats-to-node-dot-js-web-applications Maciej Lasyk, node.js security
- 65. node.js.CSI: HPP HTTP Parameter Pollution Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25 // POST firstName=John&firstName=John req.body.color //=> [“John”, “John”] Maciej Lasyk, node.js security
- 66. node.js.CSI: HPP Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25 Modify app behavior: Maciej Lasyk, node.js security
- 67. node.js.CSI: HPP Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25 - TypeErrors, uncaught errs->DoS, - Check the expected type in the input validation - Input fuzzing / test suites - try/catch, domains, clusters Maciej Lasyk, node.js security
- 68. node.js.CSI: HTTP_headers.CSP Content Security Policy Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25 Content-Security-Policy: script-src 'self'; frame-src 'none'; object-src 'none'; report-uri /my_csp_report_parser; Maciej Lasyk, node.js security
- 69. node.js.CSI: HTTP_headers.CSP Content Security Policy Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25 Content-Security-Policy: script-src 'self'; frame-src 'none'; object-src 'none'; report-uri /my_csp_report_parser; app.use(helmet.csp.policy({ defaultPolicy: { "script-src": [ "'self'" ], "img-src": [ "'self'", "http://example.com/" ] } })); Maciej Lasyk, node.js security
- 70. node.js.CSI: HTTP_headers.HSTS HTTP Strict Transport Security Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25 app.use(helmet.hsts(X, true)); Strict-Transport-Security: max-age=X; includeSubdomains Requires HTTPS also on subdomains, respects configuration for X seconds Maciej Lasyk, node.js security
- 71. node.js.CSI: HTTP_headers.X-Frame-Options Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25 X-Frame-Options: DENY helmet.xframe('sameorigin'); helmet.xframe('allow-from', 'http://example.com'); Maciej Lasyk, node.js security
- 72. node.js.CSI: HTTP_headers.others - X-Content-Type-Options - Cache-Control - X-Powered-By Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25 X-Content-Type-Options: nosniff app.use(helmet.contentTypeOptions()); app.use(helmet.cacheControl()); app.disable(“x-powered-by”); Maciej Lasyk, node.js security
- 73. node.js.CSI: request_size Just set limits use streams instead of buffering And request size: app.use(express.limit("5mb")); Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25Maciej Lasyk, node.js security
- 74. node.js.CSI: environment.monitoring - is app functional? :) - is app overloaded? - app should provide monitoring interface - how many errors caught? - are forks alive and OK? Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25Maciej Lasyk, node.js security
- 75. node.js.CSI: environment.resources - node.js will eat ;) - use control groups || containers - monitor resources usage Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25Maciej Lasyk, node.js security
- 76. node.js.CSI: environment.sandboxing - running node.js within shared env? - selinux sandbox? - libvirt sandbox? - LXC / Docker? Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25Maciej Lasyk, node.js security
- 77. node.js.CSI: environment.ACLs Just... Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25
- 78. node.js.CSI: environment.ACLs Just... Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25 Don't run as `root`!!! Maciej Lasyk, node.js security
- 79. node.js.CSI: environment.ACLs Just... Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25 Don't run as `root`!!! And also maybe behind some LB? Maciej Lasyk, node.js security
- 80. node.js.CSI: environment.tracing_execution - SmartOS / Joyent: debugging - Bunyan / Dtrace - strace of course... Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25Maciej Lasyk, node.js security
- 81. node.js.testing: testing - maybe some interface for white-box pentests? - unit-testing 4 the sake! - OWASP Zed Attack Proxy Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25Maciej Lasyk, node.js security
- 82. So what else? sockets.io node-webkit Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25Maciej Lasyk, node.js security
- 83. node.js.learning - Node Security Book - OWASP Node Goat (top10) - nodesecurity.io (Twitter, RSS) Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25Maciej Lasyk, node.js security
- 84. node.js.hiring? - does this guy contribute? - NoSQL somehow? - not only HTTP: socket.io? - DevOps & infra? - Security? :) Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25Maciej Lasyk, node.js security
- 85. Maciej Lasyk, node.js security 1/25Maciej Lasyk, node.js security Infosec && meet.js meetups
- 86. http://maciek.lasyk.info/sysop [email protected] @docent-net node.js security Thank you :) Maciej Lasyk, node.js security 1/25 Maciej Lasyk SEConference Kraków, 2014-05-09 Maciej Lasyk, node.js security
















































![node.js.express: auth.basic_auth
Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25
var users = {
admin: "admin123",
user: "user456"
};
app.use(express.basicAuth(function (user, pass) {
return users.hasOwnProperty(user) && users[user]
=== pass;
}));
Maciej Lasyk, node.js security](https://image.slidesharecdn.com/node-140510034354-phpapp01/85/Node-js-security-49-320.jpg)


![node.js.express: authorization
Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25
var users = [
{ id: 1, name: "user1", role: "admin" },
{ id: 2, name: "user2", role: "common" },
];
function loadUser(req, res, next) {
req.userData = users[req.params.user];
return next();
}
function requireRole(role) {
return function (req, res, next) {
if (req.user.role === role) {
return next();
} else {
return next(new Error("Unauthorized"));
}
};}
Maciej Lasyk, node.js security](https://image.slidesharecdn.com/node-140510034354-phpapp01/85/Node-js-security-52-320.jpg)



![node.js.express: logging
Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25
var winston = require('winston');
var logger = new (winston.Logger)({
transports: [
new (winston.transports.Console)(),
new (winston.transports.File)({
filename: 'application.log' })
]
});
Maciej Lasyk, node.js security](https://image.slidesharecdn.com/node-140510034354-phpapp01/85/Node-js-security-56-320.jpg)








![node.js.CSI: HPP
HTTP Parameter Pollution
Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25
// POST firstName=John&firstName=John
req.body.color
//=> [“John”, “John”]
Maciej Lasyk, node.js security](https://image.slidesharecdn.com/node-140510034354-phpapp01/85/Node-js-security-65-320.jpg)



![node.js.CSI: HTTP_headers.CSP
Content Security Policy
Maciej Lasyk, Ganglia & Nagios 3/25Maciej Lasyk, node.js security 1/25
Content-Security-Policy:
script-src 'self';
frame-src 'none';
object-src 'none';
report-uri /my_csp_report_parser;
app.use(helmet.csp.policy({
defaultPolicy: {
"script-src": [ "'self'" ],
"img-src": [ "'self'", "http://example.com/" ]
}
}));
Maciej Lasyk, node.js security](https://image.slidesharecdn.com/node-140510034354-phpapp01/85/Node-js-security-69-320.jpg)





























![[Wroclaw #7] Why So Serial?](https://cdn.slidesharecdn.com/ss_thumbnails/whysoserialv1-171206133328-thumbnail.jpg?width=560&fit=bounds)














![[Wroclaw #7] Security test automation](https://cdn.slidesharecdn.com/ss_thumbnails/owaspsecuritytestautomation-171206113544-thumbnail.jpg?width=560&fit=bounds)



























































