NP - Unit 3 - Forwarding Datagram and ICMP
Download as PPTX, PDF0 likes105 views
The document discusses IP forwarding and ICMP. It describes how IP datagrams are forwarded across networks using routers and forwarding tables. ICMP allows routers to send error or control messages back to the source if a datagram experiences problems during forwarding. The key types of ICMP messages are described, such as echo request/reply for ping, destination unreachable, time exceeded, and parameter problem messages.
1 of 36
Download to read offline



































Ad
Recommended
NP - Unit 4 - Routing - RIP, OSPF and Internet Multicasting



NP - Unit 4 - Routing - RIP, OSPF and Internet Multicastinghamsa nandhini Routing protocols like RIP and OSPF automate the distribution of routing information between routers. RIP is a distance-vector protocol that uses hop counts as its metric. It faces problems like slow convergence after failures. OSPF is a link-state protocol that uses shortest path first algorithm for routing. It provides faster convergence. IP multicast uses a special address range and delivery mechanisms to efficiently deliver data from one source to multiple receivers in a group.
NP - Unit 5 - Bootstrap, Autoconfigurion and BGP



NP - Unit 5 - Bootstrap, Autoconfigurion and BGPhamsa nandhini This document discusses bootstrap and autoconfiguration protocols like DHCP and IPv6 Neighbor Discovery, as well as the inter-autonomous system routing protocol BGP. It provides details on how DHCP and NDP allow devices to automatically obtain IP addresses and configuration information. It also explains that BGP is used for routing between autonomous systems, as it propagates reachability between systems without exchanging internal metric information due to administrative boundaries. Key concepts covered include DHCP client-server interaction, NDP neighbor discovery functions, BGP message types for peer setup and route exchange, and how BGP supports routing policies between autonomous systems.
Unit 1



Unit 1hamsa nandhini This document discusses different approaches to interconnecting networks, including application-level gateways and network-level packet switching. It describes the advantages of packet switching, such as efficiency and flexibility to change technologies. The goal of internetworking is to build a unified network that supports universal communication. Routers are used to interconnect physical networks at the network layer. The user views the internet as a single virtual network, while multiple protocol layers handle lower-level functions like addressing, forwarding, reliability, and physical transmission. Layering principles include protocol independence, definition of end-to-end properties, and boundaries between layers.
98 366 mva slides lesson 5



98 366 mva slides lesson 5suddenven This document provides an overview of common TCP/IP tools including the command prompt, ipconfig, ping, and tracert. It also covers advanced TCP/IP tools such as netstat, nbtstat, pathping, nslookup, netsh, route, net, and telnet. The objectives are to understand basic and advanced TCP/IP commands and their functionality in displaying network configuration, testing connectivity, tracing network paths, and troubleshooting. Additional resources like books, courses, and exams are listed to further learning.
MVA slides lesson 5



MVA slides lesson 5Fabio Almeida- Oficina Eletrônica This document provides an overview of common TCP/IP tools including the command prompt, ipconfig, ping, and tracert for basic network testing and troubleshooting. More advanced tools covered are netstat, nbtstat, pathping, nslookup, netsh, route, net, and telnet. The objectives are to understand basic and advanced TCP/IP commands and their functionality for working with TCP/IP networks. Additional resources listed include books, instructor-led courses, and exams for further learning.
Cs553 st7 ch18-internet_protocols



Cs553 st7 ch18-internet_protocolsKathirKathiresan4 This document discusses key concepts related to internet protocols including protocol functions, encapsulation, fragmentation and reassembly, connection control, addressing, and transmission services. It provides details on how the Internet Protocol (IP) implements these functions, including IP addressing formats, the IPv4 header format, and IP services and parameters.
MVA slides lesson 7



MVA slides lesson 7Fabio Almeida- Oficina Eletrônica The document provides an overview of wide area network (WAN) technologies and routing concepts. It defines static and dynamic routing, and covers common dynamic routing protocols like RIP and OSPF. The document also describes WAN technologies such as X.25, Frame Relay, ATM, SONET/SDH, FDDI, DSL, broadband cable, and POTS/PSTN. It provides details on T-carrier systems and their international counterparts. The summary concludes with resources for additional learning on networking fundamentals and the MTA 98-366 exam.
98 366 mva slides lesson 6



98 366 mva slides lesson 6suddenven The document discusses several key networking services including DHCP, Remote Desktop Services, Routing and Remote Access Service (RRAS), IPsec, DNS, and WINS. It defines each service and explains how DHCP uses the four-step DORA process to assign IP addresses. The document also provides instructions for installing and configuring DHCP, disabling APIPA, and using Remote Desktop Connection. It describes how RRAS supports remote access VPNs and routing. IPsec encryption and authentication protocols are defined. Finally, it explains that DNS and WINS are both name resolution services, with WINS required for NetBIOS name resolution.
MVA slides lesson 4



MVA slides lesson 4Fabio Almeida- Oficina Eletrônica The document provides an overview of Internet Protocol version 4 (IPv4) and IPv6, including key concepts such as IP addresses, subnetting, network address translation (NAT), and dual IP stacks. It defines the core components and classifications of IPv4 and IPv6 addressing, and how devices configure TCP/IP settings like default gateways and DNS servers.
Network protocol



Network protocolOnline The document discusses several network protocols used at different layers of the OSI model. It introduces NetBIOS/NetBEUI which provides name registration and connection-oriented/connectionless communication over LANs. TCP/IP is described as a layered protocol suite used widely on the internet, with IP, TCP, UDP operating at the network and transport layers. ARP and RARP are discussed as protocols that resolve logical to physical addresses. ICMP and IGMP are control protocols that provide error reporting and multicast group management. IPX/SPX is presented as an alternative to TCP/IP used in Novell networks. HDLC and SDLC are synchronous data link protocols used for communication over WAN links.
TCP/IP Protocols



TCP/IP ProtocolsDanial Mirza The document provides an overview of protocol architectures and the TCP/IP protocol stack. It discusses how protocol architectures establish rules for exchanging data between systems using layered protocols. The TCP/IP model is then explained in detail through its five layers - physical, network access, internet, transport and application - and core protocols like IP, TCP and UDP. Key differences between IPv4 and IPv6 are also summarized.
98 366 mva slides lesson 7



98 366 mva slides lesson 7suddenven This document provides an overview of wide area network (WAN) technologies and routing. It defines routing as managing data flow between network segments and hosts. Routers use routing tables and IP addresses to determine the path for sending data. Dynamic routing protocols like RIP and OSPF dynamically determine routes and update them when network changes occur. Common WAN technologies discussed include Frame Relay, X.25, ATM, SONET, FDDI, and various types of DSL. The document also covers topics like interior gateway protocols, exterior gateway protocols, virtual circuits, and leased lines.
Chapter07



Chapter07Muhammad Ahad This document discusses considerations for selecting switching and routing protocols for network design. It covers switching options like transparent bridging, multilayer switching, and Spanning Tree Protocol enhancements. For routing, it examines static, dynamic, distance-vector, and link-state protocols. Selection criteria include network characteristics, scalability, and ability to adapt to changes. The document provides examples of protocols like RIP, OSPF, IS-IS, and BGP and contrasts their features and use cases.
MVA slides lesson 6



MVA slides lesson 6Fabio Almeida- Oficina Eletrônica The document discusses several key networking services including DHCP, Remote Desktop Services, Routing and Remote Access Service (RRAS), IPsec, DNS, and WINS. It defines each service and explains how DHCP uses the four-step DORA process to assign IP addresses. The document also provides instructions for installing and configuring DHCP, disabling APIPA, and using Remote Desktop Connection. It describes how RRAS supports remote access VPNs and routing. IPsec encryption protocols and when to use them are also outlined. Finally, DNS and WINS name resolution services are compared.
MVA slides lesson 1



MVA slides lesson 1Fabio Almeida- Oficina Eletrônica Networking
Fundamentals
Online Resources
• Microsoft Virtual
Academy: Networking
Fundamentals
Next Steps
• Review module content
• Complete Knowledge
Check
• Review additional
resources
Questions?
TCP/ IP 



TCP/ IP Harshit Srivastava TCP/IP is a set of communication protocols that allows devices to connect on the internet. It has two main protocols - TCP and IP. TCP ensures reliable delivery of segments through acknowledgements and retransmissions. IP handles addressing and routing of packets between networks. Common applications that use TCP/IP include HTTP, FTP, SMTP and more. It is popular due to its early development and support in operating systems like UNIX.
TCP/IP(networking)



TCP/IP(networking)welcometofacebook The document discusses TCP/IP and its transport and internet layers. It describes how TCP/IP provides reliable, connection-oriented communication using mechanisms like three-way handshakes, windowing, acknowledgments and retransmissions. It also discusses UDP, a connectionless protocol that does not provide reliability. Well-known ports allow clients to identify server applications.
02 protocols and tcp-ip



02 protocols and tcp-ipmyl_1116 The document provides an overview of protocols and the TCP/IP protocol suite. It discusses what protocols are, the need for mutually agreed upon conventions and rules for communication. It then covers protocol architecture principles like layered structures and peer-to-peer protocols. The document explains concepts like the network access layer, transport layer, application layer, and addressing requirements. It also summarizes standard protocol architectures like OSI and TCP/IP and their layered models.
presentation on TCP/IP protocols data comunications



presentation on TCP/IP protocols data comunicationsAnyapuPranav The document provides an overview of the TCP/IP protocol architecture. It discusses the five layers of TCP/IP including the physical, network access, internet, transport, and application layers. It describes the protocols used at each layer, such as IP, TCP, UDP, HTTP, and FTP. The document also discusses how data is encapsulated as it passes through each layer of the TCP/IP model and is transmitted from one host to another across networks and the internet.
Chapter05



Chapter05Muhammad Ahad This document discusses principles for designing network topologies, including:
- Using a hierarchical design with core, distribution, and access layers to reduce workload on devices and facilitate scaling. This includes Cisco's common three-layer model.
- Incorporating redundancy, modularity, and well-defined entry/exit points for protection and simplicity.
- Spanning Tree Protocol (STP) is used to prevent loops by pruning blocked ports and electing a root bridge, root ports and designated ports on switches. STP must be scaled carefully in large networks.
Firewall



FirewallMuuluu A firewall monitors and controls transmissions between an internal network and the internet. There are different types of firewalls including host-based, network-based, software-based, and hardware-based. Firewalls can also be categorized as packet filters, application-level proxies, or stateful packet filters. Stateful packet filters make access decisions based on layer 3 and 4 parameters as well as derived state information to provide high security while maintaining performance.
IP Routing



IP RoutingPeter R. Egli Overview of IP routing protocols, packet forwarding and proxy ARP.
The principle of IP routing proved to be very flexible and scalable in the growth of the Internet and TCP/IP based networks.
IP routing denotes protocols for exchanging IP address range reachability like RIP, BGP and OSPF.
In contrast to IP routing, IP packet forwarding collectively means all functions performed when an IP router receives a packet and forwards it over the output interface indicated by an IP route in the routing table.
When an IP router performs a route lookup, it calculates a route decision based on different properties like prefix (mask) length, route precedence and metrics.
Routing protocols for exchanging route information can be coarsely classified as distance vector and link state protocols. Distance vector protocols like RIP (Routing Information Protocol) exchange information about the path cost to specific targets (IP address ranges). Routers that talk distance vector protocols receive reachability information about all sub-networks indirectly from neighboring routers.
In contrast to distance vector protocols, link state protocols like OSPF disseminate information about the link state of each router link in a network to all routers in the network. Thus link state protocols tend to converge faster to topology changes since all routers have firsthand information of the topology of the network.
Proxy ARP may be a convenient solution when it comes to add additional subnets without having to add routes to routers and hosts. A proxy ARP enabled router would answer ARP requests on behalf of the targeted hosts mimicking a local network access to the requesting host.
Module 1 slides



Module 1 slidesAnaniaKapala This document provides an overview of CCNA Module 1 on internetworking. It describes the purpose of routers, switches, hubs and other network devices. It also covers networking concepts like collision domains, broadcast domains, and the operation of Ethernet networks using CSMA/CD. The document explains the OSI model layers and compares it to the TCP/IP model. It also discusses common network applications and protocols like TCP, UDP, IP, ARP and ICMP.
02 coms 525 tcpip - introduction to tcpip



02 coms 525 tcpip - introduction to tcpipPalanivel Kuppusamy The document provides information on the TCP/IP protocol suite including:
- TCP/IP has 4 layers (Application, Transport, Network, Data Link) compared to OSI's 7 layers.
- Common application layer protocols include FTP, Telnet, SMTP, HTTP.
- Transport layer protocols are TCP and UDP which provide reliable and unreliable data transmission.
- Network layer protocols like IP, ARP, and ICMP handle routing and addressing.
- Layers communicate through encapsulation where each layer adds its own header to protocol data units.
98 366 mva slides lesson 8



98 366 mva slides lesson 8suddenven The document defines key network infrastructure concepts such as the Internet, intranets, extranets, virtual private networks, and security devices. It explains that the Internet connects computer networks globally using TCP/IP, while an intranet is a private network internal to an organization. An extranet extends an intranet to external partners. Virtual private networks use encryption tunnels to provide secure connections across public networks. Various firewall types and perimeter security devices like proxies help protect networks from outside threats.
TCP/IP Basics



TCP/IP Basicssanjoysanyal TCP/IP is a set of communication protocols used to connect devices on the internet. It includes lower level protocols like IP that handle basic transport of data and higher level protocols like TCP that ensure reliable delivery of data between applications. TCP establishes connections between clients and servers that allow for reliable transmission of data streams. UDP provides a simpler transmission model without ensuring delivery but is useful for applications like broadcasting.
TCPIP



TCPIPFlavio Girella TCP/IP is a protocol suite that includes IP, TCP, and UDP. IP provides connectionless and unreliable delivery of datagrams between hosts. TCP provides reliable, connection-oriented byte stream delivery between processes using ports. UDP offers minimal datagram delivery between processes using ports in an unreliable manner. The choice between TCP and UDP depends on the application's requirements for reliability and overhead.
Tcp ip-ppt



Tcp ip-pptsuganyababu14 The document discusses the layers of the TCP/IP model:
- The application layer provides access to networked services and contains high-level protocols like SMTP, FTP, and TFTP. It is comparable to multiple OSI layers.
- The transport layer handles reliable delivery using TCP or unreliable delivery using UDP depending on application needs. It provides error detection, recovery, and flow control.
- The internet layer organizes data routing over the network using IP as well as protocols like ICMP and IGMP.
- The network interface layer consists of device drivers and network interface cards that communicate with the physical network media like cables using protocols such as ARP and PPP.
Transport Layer, Network layer.pptx



Transport Layer, Network layer.pptxMuhammadMoosaPanhwar Multiplexer takes several inputs and gives a single output, while demultiplexer takes a single input and gives several outputs. They both follow combinational logic and work on different operational principles - multiplexer is many-to-one, while demultiplexer is one-to-many. Multiplexing and demultiplexing at the transport layer allow data from multiple applications to be transmitted simultaneously over a network from source to destination, where it is directed to the appropriate application.
Internet Protocols



Internet ProtocolsRamakrishna Kongalla The document discusses Internet protocols and TCP/IP. It describes how the Internet protocols were developed in the 1970s to facilitate communication between different computer systems. The key protocols are TCP and IP. TCP provides reliable data transmission and IP provides best-effort delivery of packets across networks. The document outlines the TCP/IP protocol stack and key concepts like IP addressing, ARP, routing, ICMP, TCP connection establishment and sliding windows.
Ad
More Related Content
What's hot (20)
MVA slides lesson 4



MVA slides lesson 4Fabio Almeida- Oficina Eletrônica The document provides an overview of Internet Protocol version 4 (IPv4) and IPv6, including key concepts such as IP addresses, subnetting, network address translation (NAT), and dual IP stacks. It defines the core components and classifications of IPv4 and IPv6 addressing, and how devices configure TCP/IP settings like default gateways and DNS servers.
Network protocol



Network protocolOnline The document discusses several network protocols used at different layers of the OSI model. It introduces NetBIOS/NetBEUI which provides name registration and connection-oriented/connectionless communication over LANs. TCP/IP is described as a layered protocol suite used widely on the internet, with IP, TCP, UDP operating at the network and transport layers. ARP and RARP are discussed as protocols that resolve logical to physical addresses. ICMP and IGMP are control protocols that provide error reporting and multicast group management. IPX/SPX is presented as an alternative to TCP/IP used in Novell networks. HDLC and SDLC are synchronous data link protocols used for communication over WAN links.
TCP/IP Protocols



TCP/IP ProtocolsDanial Mirza The document provides an overview of protocol architectures and the TCP/IP protocol stack. It discusses how protocol architectures establish rules for exchanging data between systems using layered protocols. The TCP/IP model is then explained in detail through its five layers - physical, network access, internet, transport and application - and core protocols like IP, TCP and UDP. Key differences between IPv4 and IPv6 are also summarized.
98 366 mva slides lesson 7



98 366 mva slides lesson 7suddenven This document provides an overview of wide area network (WAN) technologies and routing. It defines routing as managing data flow between network segments and hosts. Routers use routing tables and IP addresses to determine the path for sending data. Dynamic routing protocols like RIP and OSPF dynamically determine routes and update them when network changes occur. Common WAN technologies discussed include Frame Relay, X.25, ATM, SONET, FDDI, and various types of DSL. The document also covers topics like interior gateway protocols, exterior gateway protocols, virtual circuits, and leased lines.
Chapter07



Chapter07Muhammad Ahad This document discusses considerations for selecting switching and routing protocols for network design. It covers switching options like transparent bridging, multilayer switching, and Spanning Tree Protocol enhancements. For routing, it examines static, dynamic, distance-vector, and link-state protocols. Selection criteria include network characteristics, scalability, and ability to adapt to changes. The document provides examples of protocols like RIP, OSPF, IS-IS, and BGP and contrasts their features and use cases.
MVA slides lesson 6



MVA slides lesson 6Fabio Almeida- Oficina Eletrônica The document discusses several key networking services including DHCP, Remote Desktop Services, Routing and Remote Access Service (RRAS), IPsec, DNS, and WINS. It defines each service and explains how DHCP uses the four-step DORA process to assign IP addresses. The document also provides instructions for installing and configuring DHCP, disabling APIPA, and using Remote Desktop Connection. It describes how RRAS supports remote access VPNs and routing. IPsec encryption protocols and when to use them are also outlined. Finally, DNS and WINS name resolution services are compared.
MVA slides lesson 1



MVA slides lesson 1Fabio Almeida- Oficina Eletrônica Networking
Fundamentals
Online Resources
• Microsoft Virtual
Academy: Networking
Fundamentals
Next Steps
• Review module content
• Complete Knowledge
Check
• Review additional
resources
Questions?
TCP/ IP 



TCP/ IP Harshit Srivastava TCP/IP is a set of communication protocols that allows devices to connect on the internet. It has two main protocols - TCP and IP. TCP ensures reliable delivery of segments through acknowledgements and retransmissions. IP handles addressing and routing of packets between networks. Common applications that use TCP/IP include HTTP, FTP, SMTP and more. It is popular due to its early development and support in operating systems like UNIX.
TCP/IP(networking)



TCP/IP(networking)welcometofacebook The document discusses TCP/IP and its transport and internet layers. It describes how TCP/IP provides reliable, connection-oriented communication using mechanisms like three-way handshakes, windowing, acknowledgments and retransmissions. It also discusses UDP, a connectionless protocol that does not provide reliability. Well-known ports allow clients to identify server applications.
02 protocols and tcp-ip



02 protocols and tcp-ipmyl_1116 The document provides an overview of protocols and the TCP/IP protocol suite. It discusses what protocols are, the need for mutually agreed upon conventions and rules for communication. It then covers protocol architecture principles like layered structures and peer-to-peer protocols. The document explains concepts like the network access layer, transport layer, application layer, and addressing requirements. It also summarizes standard protocol architectures like OSI and TCP/IP and their layered models.
presentation on TCP/IP protocols data comunications



presentation on TCP/IP protocols data comunicationsAnyapuPranav The document provides an overview of the TCP/IP protocol architecture. It discusses the five layers of TCP/IP including the physical, network access, internet, transport, and application layers. It describes the protocols used at each layer, such as IP, TCP, UDP, HTTP, and FTP. The document also discusses how data is encapsulated as it passes through each layer of the TCP/IP model and is transmitted from one host to another across networks and the internet.
Chapter05



Chapter05Muhammad Ahad This document discusses principles for designing network topologies, including:
- Using a hierarchical design with core, distribution, and access layers to reduce workload on devices and facilitate scaling. This includes Cisco's common three-layer model.
- Incorporating redundancy, modularity, and well-defined entry/exit points for protection and simplicity.
- Spanning Tree Protocol (STP) is used to prevent loops by pruning blocked ports and electing a root bridge, root ports and designated ports on switches. STP must be scaled carefully in large networks.
Firewall



FirewallMuuluu A firewall monitors and controls transmissions between an internal network and the internet. There are different types of firewalls including host-based, network-based, software-based, and hardware-based. Firewalls can also be categorized as packet filters, application-level proxies, or stateful packet filters. Stateful packet filters make access decisions based on layer 3 and 4 parameters as well as derived state information to provide high security while maintaining performance.
IP Routing



IP RoutingPeter R. Egli Overview of IP routing protocols, packet forwarding and proxy ARP.
The principle of IP routing proved to be very flexible and scalable in the growth of the Internet and TCP/IP based networks.
IP routing denotes protocols for exchanging IP address range reachability like RIP, BGP and OSPF.
In contrast to IP routing, IP packet forwarding collectively means all functions performed when an IP router receives a packet and forwards it over the output interface indicated by an IP route in the routing table.
When an IP router performs a route lookup, it calculates a route decision based on different properties like prefix (mask) length, route precedence and metrics.
Routing protocols for exchanging route information can be coarsely classified as distance vector and link state protocols. Distance vector protocols like RIP (Routing Information Protocol) exchange information about the path cost to specific targets (IP address ranges). Routers that talk distance vector protocols receive reachability information about all sub-networks indirectly from neighboring routers.
In contrast to distance vector protocols, link state protocols like OSPF disseminate information about the link state of each router link in a network to all routers in the network. Thus link state protocols tend to converge faster to topology changes since all routers have firsthand information of the topology of the network.
Proxy ARP may be a convenient solution when it comes to add additional subnets without having to add routes to routers and hosts. A proxy ARP enabled router would answer ARP requests on behalf of the targeted hosts mimicking a local network access to the requesting host.
Module 1 slides



Module 1 slidesAnaniaKapala This document provides an overview of CCNA Module 1 on internetworking. It describes the purpose of routers, switches, hubs and other network devices. It also covers networking concepts like collision domains, broadcast domains, and the operation of Ethernet networks using CSMA/CD. The document explains the OSI model layers and compares it to the TCP/IP model. It also discusses common network applications and protocols like TCP, UDP, IP, ARP and ICMP.
02 coms 525 tcpip - introduction to tcpip



02 coms 525 tcpip - introduction to tcpipPalanivel Kuppusamy The document provides information on the TCP/IP protocol suite including:
- TCP/IP has 4 layers (Application, Transport, Network, Data Link) compared to OSI's 7 layers.
- Common application layer protocols include FTP, Telnet, SMTP, HTTP.
- Transport layer protocols are TCP and UDP which provide reliable and unreliable data transmission.
- Network layer protocols like IP, ARP, and ICMP handle routing and addressing.
- Layers communicate through encapsulation where each layer adds its own header to protocol data units.
98 366 mva slides lesson 8



98 366 mva slides lesson 8suddenven The document defines key network infrastructure concepts such as the Internet, intranets, extranets, virtual private networks, and security devices. It explains that the Internet connects computer networks globally using TCP/IP, while an intranet is a private network internal to an organization. An extranet extends an intranet to external partners. Virtual private networks use encryption tunnels to provide secure connections across public networks. Various firewall types and perimeter security devices like proxies help protect networks from outside threats.
TCP/IP Basics



TCP/IP Basicssanjoysanyal TCP/IP is a set of communication protocols used to connect devices on the internet. It includes lower level protocols like IP that handle basic transport of data and higher level protocols like TCP that ensure reliable delivery of data between applications. TCP establishes connections between clients and servers that allow for reliable transmission of data streams. UDP provides a simpler transmission model without ensuring delivery but is useful for applications like broadcasting.
TCPIP



TCPIPFlavio Girella TCP/IP is a protocol suite that includes IP, TCP, and UDP. IP provides connectionless and unreliable delivery of datagrams between hosts. TCP provides reliable, connection-oriented byte stream delivery between processes using ports. UDP offers minimal datagram delivery between processes using ports in an unreliable manner. The choice between TCP and UDP depends on the application's requirements for reliability and overhead.
Tcp ip-ppt



Tcp ip-pptsuganyababu14 The document discusses the layers of the TCP/IP model:
- The application layer provides access to networked services and contains high-level protocols like SMTP, FTP, and TFTP. It is comparable to multiple OSI layers.
- The transport layer handles reliable delivery using TCP or unreliable delivery using UDP depending on application needs. It provides error detection, recovery, and flow control.
- The internet layer organizes data routing over the network using IP as well as protocols like ICMP and IGMP.
- The network interface layer consists of device drivers and network interface cards that communicate with the physical network media like cables using protocols such as ARP and PPP.
Similar to NP - Unit 3 - Forwarding Datagram and ICMP (20)
Transport Layer, Network layer.pptx



Transport Layer, Network layer.pptxMuhammadMoosaPanhwar Multiplexer takes several inputs and gives a single output, while demultiplexer takes a single input and gives several outputs. They both follow combinational logic and work on different operational principles - multiplexer is many-to-one, while demultiplexer is one-to-many. Multiplexing and demultiplexing at the transport layer allow data from multiple applications to be transmitted simultaneously over a network from source to destination, where it is directed to the appropriate application.
Internet Protocols



Internet ProtocolsRamakrishna Kongalla The document discusses Internet protocols and TCP/IP. It describes how the Internet protocols were developed in the 1970s to facilitate communication between different computer systems. The key protocols are TCP and IP. TCP provides reliable data transmission and IP provides best-effort delivery of packets across networks. The document outlines the TCP/IP protocol stack and key concepts like IP addressing, ARP, routing, ICMP, TCP connection establishment and sliding windows.
TCPIP SLIDES.ppt



TCPIP SLIDES.pptaymenshykh This document describes the TCP/IP protocol stack. It has 4 main layers: the application layer containing protocols like HTTP, FTP; the transport layer containing TCP and UDP which handle reliable/unreliable data transmission; the internet layer containing IP which routes packets between hosts, along with ARP and ICMP for address resolution and error handling; and the link layer which deals with physical network addressing and transmission. TCP/IP has fewer layers than OSI and focuses on essential functions for internetworking.
Computer network coe351- part3-final



Computer network coe351- part3-finalTaymoor Nazmy 1. A host creates a packet and places the destination address in the header.
2. The host sends the packet to the nearest router.
3. Each router uses the destination address to select the next router and forwards the packet.
4. The packet is forwarded from router to router until it reaches the destination router, which delivers it to the final destination host.
Nnnnnn



Nnnnnnnautami This document provides a summary of network protocols. It defines a network as a set of connected devices that can send and receive data. It explains that network protocols establish detailed rules for how computer systems exchange information. The document then overview Reverse Address Resolution Protocol (RARP) and several other key network protocols, including Internet Protocol (IP), Address Resolution Protocol (ARP), Internet Group Message Protocol (IGMP), and Internet Control Message Protocol (ICMP). For each protocol, it provides high-level descriptions of their functions and operations in 2 sentences or less.
Final Presentation on the Network layer



Final Presentation on the Network layerZee Haak This document provides an overview of the network layer and some of its key protocols. It begins with an introduction to the network layer and its main responsibilities, including routing packets between subnets that may have different addressing schemes or protocols. It then discusses some of the network layer's main functionalities and features. The remainder of the document defines and describes several important network layer protocols, including EIGRP, ICMP, IGMP, IPv4, and others. It provides high-level explanations of how these protocols function and their roles within the network layer.
TCP/IP and UDP protocols



TCP/IP and UDP protocolsDawood Faheem Abbasi This document discusses the TCP/IP and UDP protocols. It begins with an introduction comparing the TCP/IP model to the OSI model. The TCP/IP model has four layers compared to seven in the OSI model. It then describes the two main host-to-host layer protocols in TCP/IP - TCP and UDP. TCP is connection-oriented and provides reliable, ordered delivery. It uses segments with a header containing fields like sequence numbers. UDP is connectionless and provides fast but unreliable delivery. It uses simpler segments with fewer header fields. The document concludes by explaining the end-to-end delivery process for packets using these protocols as they are transmitted between hosts via routers.
ICMP.ppt



ICMP.pptAnilKumarD22 ICMP provides error and control messages at the Internet layer. It is used to send error messages indicating problems with datagram transmission, such as when a datagram's time to live expires or its destination is unreachable, and control messages for router discovery, timestamp requests, and redirecting traffic to better routes. Without ICMP, connectivity and routing issues would be more difficult to troubleshoot and detect.
data communication protocol



data communication protocolRamla Sheikh The document discusses Internet Control Message Protocol (ICMP) and its role in supporting the Internet Protocol (IP). ICMP provides error reporting and simple query functions. It encapsulates messages as IP datagrams. ICMP messages have a header with fields for type, code, and checksum. The checksum covers the entire ICMP message. [/SUMMARY]
474-22-DatagramForwarding.pptx



474-22-DatagramForwarding.pptxThangamaniR3 IP datagrams are forwarded across the internet through a process of encapsulation and forwarding. Routers along the path encapsulate each IP datagram within a link layer frame and forward it based on the destination address. If a datagram is larger than the maximum transmission unit of the outgoing link, routers fragment it into smaller pieces that are reassembled by the destination host. Forwarding tables allow routers to determine the next hop for each datagram using longest prefix matching.
Transport layer protocol



Transport layer protocolN.Jagadish Kumar The document discusses the differences between packets and frames, and provides details on the transport layer. It explains that the transport layer is responsible for process-to-process delivery and uses port numbers for addressing. Connection-oriented protocols like TCP use three-way handshaking for connection establishment and termination, and implement flow and error control using mechanisms like sliding windows. Connectionless protocols like UDP are simpler but unreliable, treating each packet independently.
Internet Protocol.pdf



Internet Protocol.pdfBIT DURG The document discusses Internet Protocol (IP) and its role in networking. It covers the following key points:
- IP is the primary network communication protocol and relays packets called datagrams. It provides identification of computer hosts and location services.
- IP version 4 (IPv4) uses a 32-bit address scheme to uniquely identify hosts. It provides best effort delivery of packets from source to destination.
- Other related protocols discussed include ARP, RARP, ICMP, IGMP, routing protocols, and the differences between static, dynamic and default routing. Distance vector and link state routing algorithms are also covered.
Chapter 4 internetworking [compatibility mode]![Chapter 4 internetworking [compatibility mode]](https://cdn.slidesharecdn.com/ss_thumbnails/chapter4-internetworkingcompatibilitymode-150427213051-conversion-gate02-thumbnail.jpg?width=560&fit=bounds)
![Chapter 4 internetworking [compatibility mode]](https://cdn.slidesharecdn.com/ss_thumbnails/chapter4-internetworkingcompatibilitymode-150427213051-conversion-gate02-thumbnail.jpg?width=560&fit=bounds)
![Chapter 4 internetworking [compatibility mode]](https://cdn.slidesharecdn.com/ss_thumbnails/chapter4-internetworkingcompatibilitymode-150427213051-conversion-gate02-thumbnail.jpg?width=560&fit=bounds)
![Chapter 4 internetworking [compatibility mode]](https://cdn.slidesharecdn.com/ss_thumbnails/chapter4-internetworkingcompatibilitymode-150427213051-conversion-gate02-thumbnail.jpg?width=560&fit=bounds)
Chapter 4 internetworking [compatibility mode]Sĩ Anh Nguyễn The document provides an overview of network layer concepts including internetworking, IP addressing, routing protocols, and routing algorithms. Some key points include:
- Internetworking allows different networks to connect through protocols like virtual circuits and tunneling.
- IP addresses identify systems on a network and consist of a network portion and host portion. Private IP addresses are used internally.
- Routing protocols like RIP, OSPF, and BGP allow routers to share route information and determine the best path between networks.
- Subnetting divides network classes into smaller subnets to better manage IP addresses and network design.
Tcp ip



Tcp ipDhani Ahmad TCP/IP is an internet protocol suite developed by DARPA that defines the rules and standards for communication between electronic devices connected to the internet. It operates on four layers - application, transport, internet, and network interface. Key protocols include TCP and IP which work together to break data into packets and route them to the correct destination. ARP and RARP protocols map IP addresses to MAC addresses to enable communication between devices on a local network.
IT307 Exploring the Networks.pptx



IT307 Exploring the Networks.pptxShubhamTripathi290909 This document discusses the Internet Control Message Protocol (ICMP). It defines ICMP as a protocol used to send control messages between network devices and hosts to report errors and request information. The document outlines several ICMP message types, including error reporting messages like destination unreachable, source quench, time exceeded, and parameter problem. It also discusses query messages like echo request/reply and timestamp request/reply that are used for network diagnostics. In summary, ICMP allows network devices to communicate error messages and request information to diagnose network issues.
Presentation on network_protocols



Presentation on network_protocolsIUBAT The document discusses various protocols at the network layer of the TCP/IP model, including ICMP, IGMP, ARP, and RARP.
ICMP is a control protocol used for network administration and management. It carries network status information such as issues, congestion, and host accessibility. IGMP is used to manage Internet Protocol multicast group memberships. ARP resolves IPv4 addresses to MAC addresses to allow communication between network applications and the datalink layer. RARP is a reverse address resolution protocol that allows a client to request its IPv4 address from the network when it only knows its MAC address.
ip nnnnnnnnnnnnnnnnnnbbbbbbblecture06.ppt



ip nnnnnnnnnnnnnnnnnnbbbbbbblecture06.pptVINAYTANWAR18 The Internet Protocol (IP) provides an unreliable, best-effort, connectionless packet delivery service. It defines the basic unit of data transfer called a datagram and performs routing functions according to rules for unreliable packet delivery. IP datagrams can be fragmented into smaller pieces to fit into frames when the datagram is larger than the maximum transmission unit of a network. Routers replicate some IP options in all fragments while others are replicated in a single fragment only.
Ad
More from hamsa nandhini (16)
SOA - Unit 5 - SOA and Business Process Management



SOA - Unit 5 - SOA and Business Process Managementhamsa nandhini Business process management (BPM) addresses how organizations can identify, model, develop, deploy and manage business processes involving IT systems and human interaction, with goals of reducing mismatch, increasing productivity and flexibility while reducing costs. Basic components of a business process management system (BPMS) include data, service, and process modeling as well as composite web services composed of atomic web services to implement business processes available to internal and external users. Two languages, BPEL for orchestration and CDL for choreography, specify the composition of atomic and composite services.
SOA - Unit 4 - SOA & Web Services for integration and Multi-Channel access



SOA - Unit 4 - SOA & Web Services for integration and Multi-Channel accesshamsa nandhini This document discusses service-oriented architecture (SOA) and web services for integration and multi-channel access. It covers common business drivers for integration like mergers and acquisitions. It also discusses the differences between web service integration (WSI) which is opportunistic and tactical, and service-oriented integration (SOI) which is systematic. SOI involves refining data models, defining formal service contracts, and configuring legacy systems. The document also discusses how SOA allows for multi-channel access through a layered architecture with tiers for clients, channel access, communication infrastructure, and business services. This provides benefits like reducing costs and improving efficiency.
SOA - Unit 3 - SOA and Web Services



SOA - Unit 3 - SOA and Web Serviceshamsa nandhini This document discusses key elements of a web services platform, including service contracts, service registration and lookup, security, data management, communication protocols, and quality of service. It describes the principles of service contracts, such as separating interface from implementation, and defines elements of service contracts like operation names and data profiles. It also covers technologies that support the platform, such as WSDL for contracts, UDDI for discovery, WS-Security for security, and XML for data handling. Finally, it discusses common service interaction patterns like request/response, publish/subscribe, and asynchronous messaging.
SOA - Unit 2 - Service Oriented Architecture



SOA - Unit 2 - Service Oriented Architecturehamsa nandhini This document discusses key concepts of service-oriented architecture (SOA), including common service delivery approaches, SOA concepts, and key SOA elements. It also covers SOA processes, principles, services, service contracts, and the technical and business benefits of implementing an SOA.
SOA - Unit 1 - Introduction to SOA with Web Services



SOA - Unit 1 - Introduction to SOA with Web Serviceshamsa nandhini SOA allows for loosely coupled services to perform tasks independently. Key technologies include XML, web services, and SOA. A service exposes its functionality through a standardized interface and consumes other services. SOA benefits include reuse, efficiency, and loose technology coupling. Web service specifications cover standardization, metadata management, security, reliability, transactions, and orchestration of composite services. BPM uses services to model and automate business processes to increase productivity and reduce costs.
NP - Unit 2 - Internet Addressing, ARP and RARP 



NP - Unit 2 - Internet Addressing, ARP and RARP hamsa nandhini This document discusses Internet addressing, ARP, and RARP. It begins by defining IP addresses and how they identify both the network and specific host. It then covers IPv4 addressing schemes including classful addressing using classes A-D, classless addressing using CIDR, and subnetting. The document also discusses address resolution using ARP for dynamic binding between IP and MAC addresses when they differ in size. IPv6 improvements such as larger addresses and direct mapping of IP to MAC are briefly mentioned.
Web application, cookies and sessions



Web application, cookies and sessionshamsa nandhini This document discusses various web application development topics including sending emails with PHP, handling file uploads, using JavaScript with HTML, understanding HTTP headers, using date and time functions, making a login page, using cookies and sessions to store data on the server-side and client-side. It provides code examples for tasks like setting and accessing cookies and sessions, uploading files, and sending emails. It also compares key differences between JavaScript and PHP.
PHP with MySQL



PHP with MySQLhamsa nandhini This document discusses connecting to a MySQL database from PHP, executing queries, retrieving and working with query results, ensuring secure SQL, counting returned records, updating records, sending values between scripts, and paginating query results. It provides the syntax for connecting to MySQL, executing simple queries, retrieving results using mysqli_fetch_array(), ensuring data security with mysqli_real_escape_string(), counting rows with mysqli_num_rows(), updating records using mysqli_affected_rows(), and paginating results using LIMIT.
Database design and error handling



Database design and error handlinghamsa nandhini Database design principles like normalization and different normal forms are discussed to reduce redundancy and achieve full functional dependency. Indexes are explained as ways to optimize queries using columns in WHERE, ORDER BY, and JOIN clauses. Different table types like MyISAM and InnoDB are compared in terms of features. Character sets, collations, and timezones are covered in relation to MySQL. Foreign key constraints and actions for deleting or updating are defined. Common errors in PHP and SQL are outlined along with debugging techniques like displaying errors, comments, and print/echo statements.
Introduction to MySQL in PHP



Introduction to MySQL in PHPhamsa nandhini How to create datatype for columns in tables and key constraints. To learn about creating table, insert, select, update and deleting records in table
Basics of PHP



Basics of PHPhamsa nandhini introductions about PHP, syntax, variables and comments in PHP, Data types, Branching statement, looping statement and function in PHP
XML Security



XML Securityhamsa nandhini XML security involves three basic requirements: confidentiality, authentication, and data integrity. Digital signatures authenticate the identity of the sender by having the sender encrypt a hash of the message and their private key. Canonicalization generates a standard form of an XML document before encryption. XML encryption involves selecting the XML to encrypt, converting it to canonical form, and encrypting it before sending. Digital signature elements include SignedInfo, CanonicalizationMethod, SignatureMethod, Reference, KeyInfo, Transforms, and DigestMethods.
SOAP and Web services



SOAP and Web serviceshamsa nandhini SOAP is a protocol for exchanging XML-based messages over computer networks, normally using HTTP/HTTPS. It includes procedures for encoding calls and responses, as well as rules for message exchange. A SOAP message contains an envelope, header, and body. SOAP can be used for one-way data transmission between servers, intermediaries like proxies and gateways, and across firewalls using port 80. Related web services technologies include UDDI for discovery of services and WSDL for describing how to connect to services.
XML Technologies



XML Technologieshamsa nandhini XPath is a language for finding information in an XML document, using path expressions to navigate elements and attributes. It supports operators, functions and axes to locate nodes and return node sets, booleans, strings, numbers or other values. XSLT uses XPath to select nodes for transformation and XSL-FO uses the document structure defined by XSLT for formatting and layout.
XML DTD and Schema



XML DTD and Schemahamsa nandhini This document provides an overview of XML DTD and Schema. It defines key terms like well-formed, valid, DTD and describes how a DTD is used to define element types and attributes. It also explains different DTD rules like EMPTY, ANY, #PCDATA. The document then covers XML Schema elements, data types, and how to declare elements, attributes and complex/simple types in a schema.
fundamentals of XML



fundamentals of XMLhamsa nandhini The document discusses the fundamentals of XML including XML document structure, elements, attributes, character data, the XML declaration, document type declaration, and XML content model. It also covers XML rules for structure, namespaces, and the differences between well-formed and valid XML documents.
Ad
Recently uploaded (20)
Structural Response of Reinforced Self-Compacting Concrete Deep Beam Using Fi...



Structural Response of Reinforced Self-Compacting Concrete Deep Beam Using Fi...Journal of Soft Computing in Civil Engineering Analysis of reinforced concrete deep beam is based on simplified approximate method due to the complexity of the exact analysis. The complexity is due to a number of parameters affecting its response. To evaluate some of this parameters, finite element study of the structural behavior of the reinforced self-compacting concrete deep beam was carried out using Abaqus finite element modeling tool. The model was validated against experimental data from the literature. The parametric effects of varied concrete compressive strength, vertical web reinforcement ratio and horizontal web reinforcement ratio on the beam were tested on eight (8) different specimens under four points loads. The results of the validation work showed good agreement with the experimental studies. The parametric study revealed that the concrete compressive strength most significantly influenced the specimens’ response with the average of 41.1% and 49 % increment in the diagonal cracking and ultimate load respectively due to doubling of concrete compressive strength. Although the increase in horizontal web reinforcement ratio from 0.31 % to 0.63 % lead to average of 6.24 % increment on the diagonal cracking load, it does not influence the ultimate strength and the load-deflection response of the beams. Similar variation in vertical web reinforcement ratio leads to an average of 2.4 % and 15 % increment in cracking and ultimate load respectively with no appreciable effect on the load-deflection response.
Process Parameter Optimization for Minimizing Springback in Cold Drawing Proc...



Process Parameter Optimization for Minimizing Springback in Cold Drawing Proc...Journal of Soft Computing in Civil Engineering In tube drawing process, a tube is pulled out through a die and a plug to reduce its diameter and thickness as per the requirement. Dimensional accuracy of cold drawn tubes plays a vital role in the further quality of end products and controlling rejection in manufacturing processes of these end products. Springback phenomenon is the elastic strain recovery after removal of forming loads, causes geometrical inaccuracies in drawn tubes. Further, this leads to difficulty in achieving close dimensional tolerances. In the present work springback of EN 8 D tube material is studied for various cold drawing parameters. The process parameters in this work include die semi-angle, land width and drawing speed. The experimentation is done using Taguchi’s L36 orthogonal array, and then optimization is done in data analysis software Minitab 17. The results of ANOVA shows that 15 degrees die semi-angle,5 mm land width and 6 m/min drawing speed yields least springback. Furthermore, optimization algorithms named Particle Swarm Optimization (PSO), Simulated Annealing (SA) and Genetic Algorithm (GA) are applied which shows that 15 degrees die semi-angle, 10 mm land width and 8 m/min drawing speed results in minimal springback with almost 10.5 % improvement. Finally, the results of experimentation are validated with Finite Element Analysis technique using ANSYS.
DATA-DRIVEN SHOULDER INVERSE KINEMATICS YoungBeom Kim1 , Byung-Ha Park1 , Kwa...



DATA-DRIVEN SHOULDER INVERSE KINEMATICS YoungBeom Kim1 , Byung-Ha Park1 , Kwa...charlesdick1345 This paper proposes a shoulder inverse kinematics (IK) technique. Shoulder complex is comprised of the sternum, clavicle, ribs, scapula, humerus, and four joints.
IntroSlides-April-BuildWithAI-VertexAI.pdf



IntroSlides-April-BuildWithAI-VertexAI.pdfLuiz Carneiro ☁️ GDG Cloud Munich: Build With AI Workshop - Introduction to Vertex AI! ☁️
Join us for an exciting #BuildWithAi workshop on the 28th of April, 2025 at the Google Office in Munich!
Dive into the world of AI with our "Introduction to Vertex AI" session, presented by Google Cloud expert Randy Gupta.
Fort night presentation new0903 pdf.pdf.



Fort night presentation new0903 pdf.pdf.anuragmk56 This is the document of fortnight review progress meeting
ADVXAI IN MALWARE ANALYSIS FRAMEWORK: BALANCING EXPLAINABILITY WITH SECURITY



ADVXAI IN MALWARE ANALYSIS FRAMEWORK: BALANCING EXPLAINABILITY WITH SECURITYijscai With the increased use of Artificial Intelligence (AI) in malware analysis there is also an increased need to
understand the decisions models make when identifying malicious artifacts. Explainable AI (XAI) becomes
the answer to interpreting the decision-making process that AI malware analysis models use to determine
malicious benign samples to gain trust that in a production environment, the system is able to catch
malware. With any cyber innovation brings a new set of challenges and literature soon came out about XAI
as a new attack vector. Adversarial XAI (AdvXAI) is a relatively new concept but with AI applications in
many sectors, it is crucial to quickly respond to the attack surface that it creates. This paper seeks to
conceptualize a theoretical framework focused on addressing AdvXAI in malware analysis in an effort to
balance explainability with security. Following this framework, designing a machine with an AI malware
detection and analysis model will ensure that it can effectively analyze malware, explain how it came to its
decision, and be built securely to avoid adversarial attacks and manipulations. The framework focuses on
choosing malware datasets to train the model, choosing the AI model, choosing an XAI technique,
implementing AdvXAI defensive measures, and continually evaluating the model. This framework will
significantly contribute to automated malware detection and XAI efforts allowing for secure systems that
are resilient to adversarial attacks.
International Journal of Distributed and Parallel systems (IJDPS)



International Journal of Distributed and Parallel systems (IJDPS)samueljackson3773 The growth of Internet and other web technologies requires the development of new
algorithms and architectures for parallel and distributed computing. International journal of
Distributed and parallel systems is a bimonthly open access peer-reviewed journal aims to
publish high quality scientific papers arising from original research and development from
the international community in the areas of parallel and distributed systems. IJDPS serves
as a platform for engineers and researchers to present new ideas and system technology,
with an interactive and friendly, but strongly professional atmosphere.
Degree_of_Automation.pdf for Instrumentation and industrial specialist



Degree_of_Automation.pdf for Instrumentation and industrial specialistshreyabhosale19 degree of Automation for industrial and Instrumentation learners.
Introduction to FLUID MECHANICS & KINEMATICS



Introduction to FLUID MECHANICS & KINEMATICSnarayanaswamygdas Fluid mechanics is the branch of physics concerned with the mechanics of fluids (liquids, gases, and plasmas) and the forces on them. Originally applied to water (hydromechanics), it found applications in a wide range of disciplines, including mechanical, aerospace, civil, chemical, and biomedical engineering, as well as geophysics, oceanography, meteorology, astrophysics, and biology.
It can be divided into fluid statics, the study of various fluids at rest, and fluid dynamics.
Fluid statics, also known as hydrostatics, is the study of fluids at rest, specifically when there's no relative motion between fluid particles. It focuses on the conditions under which fluids are in stable equilibrium and doesn't involve fluid motion.
Fluid kinematics is the branch of fluid mechanics that focuses on describing and analyzing the motion of fluids, such as liquids and gases, without considering the forces that cause the motion. It deals with the geometrical and temporal aspects of fluid flow, including velocity and acceleration. Fluid dynamics, on the other hand, considers the forces acting on the fluid.
Fluid dynamics is the study of the effect of forces on fluid motion. It is a branch of continuum mechanics, a subject which models matter without using the information that it is made out of atoms; that is, it models matter from a macroscopic viewpoint rather than from microscopic.
Fluid mechanics, especially fluid dynamics, is an active field of research, typically mathematically complex. Many problems are partly or wholly unsolved and are best addressed by numerical methods, typically using computers. A modern discipline, called computational fluid dynamics (CFD), is devoted to this approach. Particle image velocimetry, an experimental method for visualizing and analyzing fluid flow, also takes advantage of the highly visual nature of fluid flow.
Fundamentally, every fluid mechanical system is assumed to obey the basic laws :
Conservation of mass
Conservation of energy
Conservation of momentum
The continuum assumption
For example, the assumption that mass is conserved means that for any fixed control volume (for example, a spherical volume)—enclosed by a control surface—the rate of change of the mass contained in that volume is equal to the rate at which mass is passing through the surface from outside to inside, minus the rate at which mass is passing from inside to outside. This can be expressed as an equation in integral form over the control volume.
The continuum assumption is an idealization of continuum mechanics under which fluids can be treated as continuous, even though, on a microscopic scale, they are composed of molecules. Under the continuum assumption, macroscopic (observed/measurable) properties such as density, pressure, temperature, and bulk velocity are taken to be well-defined at "infinitesimal" volume elements—small in comparison to the characteristic length scale of the system, but large in comparison to molecular length scale
"Feed Water Heaters in Thermal Power Plants: Types, Working, and Efficiency G...



"Feed Water Heaters in Thermal Power Plants: Types, Working, and Efficiency G...Infopitaara A feed water heater is a device used in power plants to preheat water before it enters the boiler. It plays a critical role in improving the overall efficiency of the power generation process, especially in thermal power plants.
🔧 Function of a Feed Water Heater:
It uses steam extracted from the turbine to preheat the feed water.
This reduces the fuel required to convert water into steam in the boiler.
It supports Regenerative Rankine Cycle, increasing plant efficiency.
🔍 Types of Feed Water Heaters:
Open Feed Water Heater (Direct Contact)
Steam and water come into direct contact.
Mixing occurs, and heat is transferred directly.
Common in low-pressure stages.
Closed Feed Water Heater (Surface Type)
Steam and water are separated by tubes.
Heat is transferred through tube walls.
Common in high-pressure systems.
⚙️ Advantages:
Improves thermal efficiency.
Reduces fuel consumption.
Lowers thermal stress on boiler components.
Minimizes corrosion by removing dissolved gases.
DT REPORT by Tech titan GROUP to introduce the subject design Thinking



DT REPORT by Tech titan GROUP to introduce the subject design ThinkingDhruvChotaliya2 This a Report of a Design Thinking
Lidar for Autonomous Driving, LiDAR Mapping for Driverless Cars.pptx



Lidar for Autonomous Driving, LiDAR Mapping for Driverless Cars.pptxRishavKumar530754 LiDAR-Based System for Autonomous Cars
Autonomous Driving with LiDAR Tech
LiDAR Integration in Self-Driving Cars
Self-Driving Vehicles Using LiDAR
LiDAR Mapping for Driverless Cars
RICS Membership-(The Royal Institution of Chartered Surveyors).pdf



RICS Membership-(The Royal Institution of Chartered Surveyors).pdfMohamedAbdelkader115 Glad to be one of only 14 members inside Kuwait to hold this credential.
Please check the members inside kuwait from this link:
https://www.rics.org/networking/find-a-member.html?firstname=&lastname=&town=&country=Kuwait&member_grade=(AssocRICS)&expert_witness=&accrediation=&page=1
railway wheels, descaling after reheating and before forging



railway wheels, descaling after reheating and before forgingJavad Kadkhodapour railway wheels, descaling after reheating and before forging
Structural Response of Reinforced Self-Compacting Concrete Deep Beam Using Fi...



Structural Response of Reinforced Self-Compacting Concrete Deep Beam Using Fi...Journal of Soft Computing in Civil Engineering
Process Parameter Optimization for Minimizing Springback in Cold Drawing Proc...



Process Parameter Optimization for Minimizing Springback in Cold Drawing Proc...Journal of Soft Computing in Civil Engineering
NP - Unit 3 - Forwarding Datagram and ICMP
- 1. UNIT-III FORWARDING IP DATAGRAMS AND ICMP
- 2. Internet Protocol: Forwarding IP Datagrams
- 3. Forwarding in an internet • Routing was used with packet switching systems • Forwarding refer to the process of choosing the path for a packet. • Router performs forwarding. • switched Ethernet-the switches are responsible for forwarding Ethernet frames among computers. • The major differences are that in place of frames the Internet accepts and delivers IP datagrams, and in place of Ethernet addresses, the Internet uses IP addresses. Therefore, throughout the chapter, we will restrict the discussion to IP forwarding. • The information IP software uses to make forwarding decisions is known as a Forwarding Information Base(FIB).
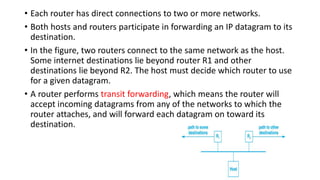
- 4. • Each router has direct connections to two or more networks. • Both hosts and routers participate in forwarding an IP datagram to its destination. • In the figure, two routers connect to the same network as the host. Some internet destinations lie beyond router R1 and other destinations lie beyond R2. The host must decide which router to use for a given datagram. • A router performs transit forwarding, which means the router will accept incoming datagrams from any of the networks to which the router attaches, and will forward each datagram on toward its destination.
- 5. Direct and Indirect delivery • forwarding into two forms: • direct delivery • indirect delivery. • Direct delivery-the transmission of a datagram from one machine across a single physical network directly to another(both connected directly). • Indirect delivery occurs when the destination of a datagram is not on a directly attached network.
- 6. Transmission across a single network • Transmission of an IP datagram between two machines on a single physical network does not involve routers. • The sender encapsulates the datagram in a physical frame, binds the next-hop address to a physical hardware address, and sends the resulting frame directly to the destination. • To determine if a destination lies on one of the directly connected networks, IP software extracts the network portion of the destination IP address and compares the network ID to the network ID of its own IP address(es).
- 7. Indirect delivery • Indirect delivery is more difficult than direct delivery because the sending machine must identify an initial router to handle the datagram. • The router must then forward the datagram on toward the destination network. • Routers in a TCP/IP internet form a cooperative, interconnected structure. Datagrams pass from router to router until they reach a router that can deliver the datagram directly. • Finally, • A host only knows about directly-connected networks; a host relies on routers to transfer datagrams to remote destinations. • Each router knows how to reach all possible destinations in the internet; given a datagram, a router can forward it correctly.
- 8. Table driven IP forwarding • IP performs datagram forwarding. The IP forwarding algorithm employs a data structure that stores information about possible destinations and how to reach them. • The data structure is known formally as an Internet Protocol forwarding table or IP forwarding table, and informally as simply a forwarding table. • Both hosts and routers have a forwarding table. • If every forwarding table contained information about every possible destination in an internet, it would be impossible to keep the tables current. • Because it allows forwarding to be based on network prefixes, the IP addressing scheme controls the size of forwarding tables.
- 9. Next-Hop forwarding • A forwarding table contains a set of pairs (N, R), where N is the network prefix for a network in the internet and R is the IP address of the “next” router along the path to network N. • Router R is called the next hop, and the idea of using a forwarding table to store a next hop for each destination is called next-hop forwarding. • the network portion of a destination IP address instead of the complete address keeps forwarding tables small. It helps hide information, keeping the details of specific hosts.
- 11. Default Routes And A Host Example • If no entry in the table matches the destination address, the forwarding software takes a second step of checking for a default route. • We say that the next hop specified in a default route is a default router. • A default route can be incorporated into a forwarding table. • A default route is especially useful when many destinations lie beyond a single router. • Default routing works especially well for typical host computers that obtain service from an ISP.
- 13. Host-Specific Routes • Most IP forwarding software allows a host-specific route to be specified as a special case. • Having host-specific routes gives a network administrator more control. • The ability to specify a route for individual machines turns out to have several possible uses: • Control over network use • Testing a new network. • Security
- 14. The IP Forwarding Algorithm
- 15. Longest-Prefix Match Paradigm • longest-prefix match - to describe the idea of examining the most specific routes first.
- 17. Forwarding Tables And IP Addresses • It is important to understand that except for decrementing the hop limit (TTL in IPv4) and recomputing the checksum, IP forwarding does not alter the original datagram. • In the algorithm, the IP address selected by the IP forwarding algorithm is called a next-hop address because it tells where the datagram must be sent next.
- 18. Handling Incoming Datagrams • host software • router software • four reasons why a host should refrain from performing any forwarding.
- 19. • Forwarding In The Presence Of Broadcast And Multicast • Software Routers And Sequential Lookup • Establishing Forwarding Tables
- 20. Internet Protocol: Error And Control Messages (ICMP)
- 21. Introduction • Connectionless system. • When a datagram arrives, a router forwards or delivers the datagram and then goes on to the next datagram; the router does not coordinate with the original sender of a datagram. • Failures of network and processor hardware, IP cannot deliver a datagram if the destination machine is temporarily or permanently disconnected from the network, if the hop limit expires before a datagram reaches its destination, or if an intermediate router becomes so overloaded that it must discard a datagram.
- 22. ICMP - Internet Control Message Protocol • allows routers to send error or control messages back to the source of a datagram that caused a problem. • ICMP is primarily intended to inform a source when a datagram sent by the source experiences problems. • ICMP messages are not usually delivered to applications. • ICMP messages are sent to Internet Protocol software on the source computer. That is, when an ICMP error message arrives on a computer, the ICMP software module on the computer handles the message. • The chief advantage of allowing hosts to use ICMP is that it provides a single mechanism used for all control and information messages.
- 23. Error Reporting Vs. Error Correction • ICMP is an error reporting mechanism • It provides a way for routers that encounter an error to report the error to the original source, but ICMP does not interact with the host nor does ICMP attempt to correct the error. • When a datagram causes an error, ICMP can only report the error condition back to the original source of the datagram; the source must relate the error to an individual application program or take other action to correct the problem.
- 24. ICMP Message Delivery • Because each ICMP message travels in an IP datagram, two levels of encapsulation are required. • IPv4 uses the PROTOCOL field in the datagram header as a type field. • When an ICMP message is carried in the payload area of an IPv4 datagram, the PROTOCOL field is set to 1. • IPv6 uses the NEXT HEADER field to specify the type of the item being carried. • When an ICMP message is carried in the payload area of an IPv6 datagram, the NEXT HEADER field of the header that is previous to the ICMP message contains 58.
- 25. ICMP Message Format • Conceptual Layering • TYPE • CODE • CHECKSUM
- 26. Example ICMP Message Types Used With IPv4
- 27. Example ICMPv6 message types and the meaning of each.
- 28. Testing Destination Reachability And Status (Ping) • Ping sends an ICMP Echo Request message to a remote computer. • Any computer that receives an ICMP Echo Request creates an ICMP Echo Reply and returns the reply to the original sender. Echo Request And Reply Message Format: • IPv4 : TYPE 8 – request, 0-reply • IPv6: TYPE request -128 reply-129
- 29. Checksum Computation And The IPv6 Pseudo-Header
- 30. Reports Of Unreachable Destinations • Whenever an error prevents a router from forwarding or delivering a datagram, the router sends an ICMP destination unreachable message back to the source and then drops(i.e., discards) the datagram. • Both IPv4 and IPv6 use the same format for destination unreachable messages.
- 31. The CODE values for an ICMP destination unreachable message
- 32. ICMP Error Reports Regarding Fragmentation
- 33. Route Change Requests From Routers • Routers are assumed to know correct routes; hosts begin with minimal routing information and learn new routes from routers
- 34. Detecting Circular Or Excessively Long Routes • ICMP time exceeded message
- 35. Reporting Other Problems • parameter problem message
- 36. Older ICMP Messages Used At Startup • ICMPv6 Router Discovery message








