VRF (virtual routing and forwarding)
3 likes3,939 views
VRF (Virtual Routing and Forwarding) is a technology that allows multiple instances of a routing table to co-exist within the same router at the same time. This increases functionality by allowing network paths to be segmented without using multiple devices. Because traffic is automatically segregated, VRF also increases network security and can eliminate the need for encryption and authentication. Internet service providers (ISPs) often take advantage of VRF to create separate virtual private networks (VPNs) for customers; thus the technology is also referred to as VPN routing and forwarding. Because the routing instances are independent, the same or overlapping IP addresses can be used without conflicting with each other.
1 of 10
Downloaded 122 times









Ad
Recommended
Virtual Routing and Forwarding, (VRF-lite)



Virtual Routing and Forwarding, (VRF-lite)NetProtocol Xpert VRF-Lite allows a single physical router to virtualize multiple routers by creating independent virtual routing tables (VRFs). Each VRF logically isolates the routing tables and network traffic of customers or applications. The physical router uses VLAN trunking to keep traffic from different VRFs separate when sending data to other devices. Configuring VRF-Lite involves defining VRFs, assigning interfaces to VRFs, and configuring routing protocols for each VRF.
Deploying IP/MPLS VPN - Cisco Networkers 2010



Deploying IP/MPLS VPN - Cisco Networkers 2010Febrian This document describes a presentation on designing MPLS Layer 3 VPN networks, covering MPLS VPN technology overview, configuration, services such as multihoming and hub-and-spoke, and best practices. The presentation discusses how MPLS VPNs use VRFs, MP-BGP, and label switching to provide scalable VPN services to enterprises by separating routing and forwarding tables for each customer VPN. Sample MPLS VPN configurations for PE, P, and route reflector routers are also provided.
Mpls L3_vpn



Mpls L3_vpnReza Farahani MPLS L3 VPN allows companies to offer Layer 3 VPN services with advantages like scalability, security, and support for duplicate IP addresses and different network topologies. The key components that enable this are VRF tables on PE routers that separate routing information for each customer to avoid duplicate IP issues, and MP-BGP which customizes VPN routing information using a Route Distinguisher, VPN label, and Route Target to support different VPN topologies. MPLS L3 VPN provides services like multi-homed sites for redundancy, hub-and-spoke networks, internet access with security, and extranets for inter-company communication.
Building DataCenter networks with VXLAN BGP-EVPN



Building DataCenter networks with VXLAN BGP-EVPNCisco Canada The session specifically covers the requirements and approaches for deploying the Underlay, Overlay as well as the inter-Fabric connectivity of Data Center Networks or Fabrics. Within the VXLAN BGP-EVPN based Overlay, we focus on the insights like forwarding and control plane functions which are critical to the simplicity operation of the architecture in achieving scale, small failure domains and consistent configuration. To complete the overlay view on VXLAN BGP-EVPN, we are going to the insides of BGP and its EVPN address-familiy and extend to about how multiple DC Fabric can be interconnected within, either as stretched Fabrics or with true DCI. The session concludes with a brief overview of manageability functions, network orchestration capabilities and multi-tenancy details. This Advanced session is intended for network, design and operation engineers from Enterprises to Service Providers.
Mpls Services



Mpls ServicesKristof De Brouwer The document provides an overview of MPLS (Multi-Protocol Label Switching) concepts and components. It discusses how MPLS separates routing from forwarding by using labels to forward packets based on the label rather than the IP address. It describes MPLS components like edge label switching routers (ELSR or PE), label switching routers (LSR or P), and the label distribution protocol (LDP). It also provides examples of MPLS forwarding and MPLS VPN operation.
Implementing cisco mpls



Implementing cisco mplsMatiullah Jamil This document provides an overview and student guide for the "Implementing Cisco MPLS (MPLS) Version 2.2" course. It introduces basic MPLS concepts including the MPLS architecture, labels, label stacks, and applications such as MPLS VPNs and traffic engineering. It also covers frame-mode MPLS implementation on Cisco IOS platforms, including configuration, monitoring, and troubleshooting tasks. Finally, it discusses MPLS VPN technology in depth, including the MPLS VPN architecture, routing model, and packet forwarding mechanisms.
Vxlan deep dive session rev0.5 final



Vxlan deep dive session rev0.5 finalKwonSun Bae VXLAN is a protocol that allows large numbers of virtual LANs to be overlaid on a physical network by encapsulating Ethernet frames within UDP packets and transporting them over an IP network. It addresses the scalability limitations of VLANs in large multi-tenant cloud environments by using a 24-bit segment ID rather than a 12-bit VLAN ID. The document provides an overview of VXLAN, why it is used, key concepts like VTEPs and VNIs, and demonstrations of VXLAN configuration on Cisco and Arista switches.
Intrdouction to VRF Implementation.pdf



Intrdouction to VRF Implementation.pdfNesibusami Virtual routing and forwarding (VRF) allows a single router to maintain multiple independent routing tables. It creates virtual routers within a physical router by isolating interfaces, routing tables, and forwarding tables for each VRF. This allows for overlapping IP addresses between VRFs. Configuring VRFs increases network security and segmentation without requiring encryption between instances.
Bgp



BgpFebrian The document provides an overview of the Border Gateway Protocol (BGP). It discusses BGP concepts such as autonomous systems, path attributes, and the BGP protocol operation. Key points include that BGP establishes peering sessions to exchange routing information, uses route attributes like AS path, next hop, and communities to determine the best path, and supports techniques like route reflection and confederation to improve scalability in large networks.
VTP



VTPHaidar-Mohammed The document discusses Virtual Trunking Protocol (VTP). It describes VTP as a Cisco proprietary protocol that exchanges VLAN information across trunk links, allowing network managers to distribute VLAN configurations to all switches in the same domain. The document outlines the key components of VTP, including domains, advertisements, and pruning. It also details the different VTP modes of server, client, and transparent and how they operate. The benefits of using VTP for VLAN management are presented, along with some common VTP configuration issues.
Bgp tutorial for ISP



Bgp tutorial for ISPWahyu Nasution This document provides an overview of BGP (Border Gateway Protocol) basics and configuration for internet service providers. It discusses BGP attributes, path selection, and applying routing policies. The key points covered include the purpose of BGP in exchanging routing information between autonomous systems, BGP neighbor configuration for internal and external peers, and using attributes like AS path, local preference, communities to influence best path selection.
MPLS L3 VPN Tutorial, by Nurul Islam Roman [APNIC 38]![MPLS L3 VPN Tutorial, by Nurul Islam Roman [APNIC 38]](https://cdn.slidesharecdn.com/ss_thumbnails/mplsl3vpnapnic381410820509-140915192004-phpapp02-thumbnail.jpg?width=560&fit=bounds)
![MPLS L3 VPN Tutorial, by Nurul Islam Roman [APNIC 38]](https://cdn.slidesharecdn.com/ss_thumbnails/mplsl3vpnapnic381410820509-140915192004-phpapp02-thumbnail.jpg?width=560&fit=bounds)
![MPLS L3 VPN Tutorial, by Nurul Islam Roman [APNIC 38]](https://cdn.slidesharecdn.com/ss_thumbnails/mplsl3vpnapnic381410820509-140915192004-phpapp02-thumbnail.jpg?width=560&fit=bounds)
![MPLS L3 VPN Tutorial, by Nurul Islam Roman [APNIC 38]](https://cdn.slidesharecdn.com/ss_thumbnails/mplsl3vpnapnic381410820509-140915192004-phpapp02-thumbnail.jpg?width=560&fit=bounds)
MPLS L3 VPN Tutorial, by Nurul Islam Roman [APNIC 38]APNIC This document discusses deploying MPLS L3VPN. It begins with an overview of MPLS and VPN terminology. It then covers the MPLS reference architecture and different node types. It describes how IP/VPN technologies use separate routing tables at provider edge (PE) routers to provide independent virtual routing and forwarding (VRF) instances for each VPN customer. The control plane uses multiprotocol BGP (MP-BGP) to distribute VPN routes between PE routers using route distinguisher (RD), route target (RT), and labels. The forwarding plane uses these labels to encapsulate and transport customer IP packets across the MPLS core. The document then discusses various IP/VPN services including load sharing, hub-and-spoke
Cisco Live! :: Carrier Ethernet 2.0 :: BRKSPG-2720 | Las Vegas July/2016



Cisco Live! :: Carrier Ethernet 2.0 :: BRKSPG-2720 | Las Vegas July/2016Bruno Teixeira The document discusses Carrier Ethernet 2.0 and next generation Carrier Ethernet architectures. It provides an agenda for topics including Carrier Ethernet fundamentals, new CE 2.0 services like E-Tree and E-Access, and service enhancements. The focus is on how CE 2.0 helps service providers expand services, simplify operations, and extend service reach through standardized MEF specifications.
OSPF Basics



OSPF BasicsMartin Bratina Open Shortest Path First (OSPF) is an interior gateway protocol that uses link state routing and the Dijkstra algorithm to calculate the shortest path to destinations within an autonomous system. It elects a Designated Router to generate network link advertisements and assist in database synchronization between routers. Routers run the Shortest Path First algorithm on their link state databases to determine the best routes and populate their routing tables.
EVPN-Presentation.pptx



EVPN-Presentation.pptxVimalMallick The document discusses Ethernet VPN (EVPN) functionality on Juniper Networks devices. It provides an overview of EVPN concepts including single-homed and multi-homed EVPN configurations, the differences between EVPN and VPLS, Junos support for EVPN, EVPN terminology, types of BGP routes used in EVPN, MAC learning processes, and trace log examples.
MPLS L3 VPN Deployment



MPLS L3 VPN DeploymentAPNIC The document provides information about an upcoming training course on deploying MPLS L3 VPNs. It includes details about the trainers, Nurul Islam Roman and Jessica Wei, their backgrounds and areas of expertise. It also outlines the course agenda which will cover topics such as MPLS VPN models, terminology, operation, configuration examples and service deployment scenarios.
Introduction to Segment Routing



Introduction to Segment RoutingMyNOG This document discusses segment routing and its benefits for incremental deployment in networks. It describes how segment routing uses MPLS or IPv6 routing headers to encode paths as ordered lists of segments. Segment routing allows more control over traffic paths compared to traditional IGP routing. It can enable traffic engineering and service chaining while maintaining network and control plane simplicity. The document argues segment routing is useful for scaling datacenters and simplifying peering relationships.
IOS Cisco - Cheat sheets



IOS Cisco - Cheat sheetsAlejandro Marin Cheats sheet for Cisco with all IPSec, IP v4, Ip v6, PPP, RIP, VLAN, VOIP, NAT, Terminations, Commands
MPLS - Multiprotocol Label Switching



MPLS - Multiprotocol Label SwitchingPeter R. Egli Overview of the MPLS backbone transmission technology.
MPLS (MultiProtocol Layer Switching) is a layer 2.5 technology that combines the virtues of IP routing and fast layer 2 packet switching.
IP packet forwarding is not suited for high-speed forwarding due to the need to evaluate multiple routes for each IP packet in order to find the optimal route, i.e. the route with the longest prefix match.
However, Internet Protocol routing provides global reachability through the IP address and through IP routing protocols like BGP or OSPF.
Layer 2 packet switching has complementary characteristics in that it does not provide global reachability through globally unique addresses but allows fast packet forwarding in hardware through the use of small and direct layer 2 lookup addresses.
MPLS combines IP routing and layer 2 switching by establishing layer 2 forwarding paths based on routes received through IP routing protocols like BGP or OSPF.
Thus the control plane of an MPLS capable device establishes layer 2 forwarding paths while the data plane then performs packet forwarding, often in hardware.
MPLS is not a layer 2 technology itself, i.e. it does not define a layer 2 protocol but rather makes use of existing layer 2 technologies like Ethernet, ATM or Frame Relay.
MPLS Layer 3 VPN 



MPLS Layer 3 VPN NetProtocol Xpert This document explains MPLS Layer 3 VPNs. It discusses how Layer 3 VPNs allow routing information to be shared between customer sites using protocols like OSPF and BGP across the service provider's MPLS network. It describes how Virtual Routing and Forwarding instances (VRFs), MP-BGP, Route Distinguishers (RDs), and Route Targets (RTs) work together to separate routing information for different customers and establish VPN connectivity between their sites while avoiding overlapping address spaces.
How BGP Works



How BGP WorksThousandEyes In this webinar, we cover how Border Gateway Protocol works. Starting from key concepts, you'll learn about Autonomous Systems, the BGP protocol, AS Path, learning and advertising routes, RIBs and route selection. See the webinar recording at https://www.thousandeyes.com/webinars/how-bgp-works
MPLS + BGP Presentation



MPLS + BGP PresentationGino McCarty This document provides an overview of Multiprotocol Label Switching (MPLS), including its history, key concepts, applications, and use by service providers. MPLS was developed in the late 1990s to meet the needs of scalable routing and quality of service on the growing internet. It works by assigning fixed length labels to data packets, allowing routers to forward based on these labels rather than long network addresses. Major applications of MPLS include traffic engineering, virtual private networks, and bandwidth management. The document discusses how service providers like MegaPath use MPLS in their backbones to provide integrated data and voice services, and nationwide networking solutions for corporate customers.
MPLS Concepts and Fundamentals



MPLS Concepts and FundamentalsShawn Zandi Early 2000s, Basic MPLS Fundamentals and Concepts by Shawn Zandi, Training Material for Networkers to learn MPLS and Label Switching
Eigrp.ppt



Eigrp.pptEdgardo Scrimaglia This document provides an overview of the Enhanced Interior Gateway Routing Protocol (EIGRP). It describes the history and development of EIGRP, its basic operation and components, including reliable transport protocol, packet types, neighbor discovery via hello packets, and route updates using the diffusing update algorithm. It also covers basic EIGRP configuration such as enabling it with the router eigrp command, advertising networks, and verifying neighbor relationships.
VLAN Trunking Protocol



VLAN Trunking ProtocolNetwax Lab VLAN Trunking Protocol (VTP) is a Cisco proprietary protocol that propagates the definition of Virtual
Local Area Networks (VLAN) on the whole local area network.[1] To do this, VTP carries VLAN
information to all the switches in a VTP domain. VTP advertisements can be sent over ISL, 802.1Q, IEEE
802.10 and LANE trunks. VTP is available on most of the Cisco Catalyst Family products.
MPLS VPN



MPLS VPNShahzaib Mahesar This document discusses MPLS VPN and its three main types: point-to-point VPNs using pseudowires to encapsulate traffic between two sites; layer 2 VPNs called VPLS that provide switched VLAN services across sites; and layer 3 VPNs known as VPRN that utilize VRF tables to segment routing for each customer using BGP. It describes how MPLS VPN works using CE, PE, and P routers to forward labeled packets through the provider network and pop the label at the destination PE to deliver the packet. Finally, it provides additional resources for learning more about MPLS VPN technologies.
CCCNP ROUTE v6_ch06



CCCNP ROUTE v6_ch06Licenciatura en Redes y Sistemas Operativos This chapter discusses implementing Border Gateway Protocol (BGP) solutions for Internet Service Provider (ISP) connectivity. It begins with an overview of BGP terminology such as autonomous systems (AS), AS numbers, and BGP peers. The chapter then covers basic BGP configuration and operation, including the exchange of routing information between BGP peers in different ASes. It also discusses considerations for connecting an enterprise network to an ISP, such as addressing, link types, redundancy, and routing protocols.
Is is



Is isIrham Nurhalim The document discusses the IS-IS routing protocol. It provides an overview of IS-IS, including that it is an interior gateway protocol used within an autonomous system. It also describes IS-IS levels, areas, and backbone routers. Finally, it discusses CLNS addressing, IS-IS PDUs like Hello packets, and other IS-IS concepts.
ODA000017 MPLS VPN(L3).ppt



ODA000017 MPLS VPN(L3).pptmarwan76 1) The document defines several types of VPNs including IP-VPN, network-based IP-VPN, VLL, VPDN, VPLS, and VPRN. 2) MPLS VPN uses MPLS to create private networks over a public IP network. It establishes VPNs by using tunneling protocols and assigning unique routing identifiers to each VPN. 3) MPLS VPN provides isolation and security for each VPN by maintaining separate forwarding tables and using route distinguishers, route targets, and MPLS labels to direct traffic to the correct VPNs.
Mpls vpn.rip



Mpls vpn.ripfarhanica This document provides a configuration example for setting up an MPLS VPN with RIP routing on the customer side. Key aspects of the configuration include:
- Creating a VRF for each VPN and configuring route targets and import/export rules for BGP extended communities to associate routes with the correct VPN
- Configuring PE interfaces with the correct VRF forwarding and IP addresses
- Redistributing routes between routing protocols (RIP, OSPF, BGP) on the PE routers to exchange routes between the CE and P routers
- Configuring IBGP between PE routers to exchange VPNv4 routes using MPLS labels and BGP extended communities
Ad
More Related Content
What's hot (20)
Bgp



BgpFebrian The document provides an overview of the Border Gateway Protocol (BGP). It discusses BGP concepts such as autonomous systems, path attributes, and the BGP protocol operation. Key points include that BGP establishes peering sessions to exchange routing information, uses route attributes like AS path, next hop, and communities to determine the best path, and supports techniques like route reflection and confederation to improve scalability in large networks.
VTP



VTPHaidar-Mohammed The document discusses Virtual Trunking Protocol (VTP). It describes VTP as a Cisco proprietary protocol that exchanges VLAN information across trunk links, allowing network managers to distribute VLAN configurations to all switches in the same domain. The document outlines the key components of VTP, including domains, advertisements, and pruning. It also details the different VTP modes of server, client, and transparent and how they operate. The benefits of using VTP for VLAN management are presented, along with some common VTP configuration issues.
Bgp tutorial for ISP



Bgp tutorial for ISPWahyu Nasution This document provides an overview of BGP (Border Gateway Protocol) basics and configuration for internet service providers. It discusses BGP attributes, path selection, and applying routing policies. The key points covered include the purpose of BGP in exchanging routing information between autonomous systems, BGP neighbor configuration for internal and external peers, and using attributes like AS path, local preference, communities to influence best path selection.
MPLS L3 VPN Tutorial, by Nurul Islam Roman [APNIC 38]![MPLS L3 VPN Tutorial, by Nurul Islam Roman [APNIC 38]](https://cdn.slidesharecdn.com/ss_thumbnails/mplsl3vpnapnic381410820509-140915192004-phpapp02-thumbnail.jpg?width=560&fit=bounds)
![MPLS L3 VPN Tutorial, by Nurul Islam Roman [APNIC 38]](https://cdn.slidesharecdn.com/ss_thumbnails/mplsl3vpnapnic381410820509-140915192004-phpapp02-thumbnail.jpg?width=560&fit=bounds)
![MPLS L3 VPN Tutorial, by Nurul Islam Roman [APNIC 38]](https://cdn.slidesharecdn.com/ss_thumbnails/mplsl3vpnapnic381410820509-140915192004-phpapp02-thumbnail.jpg?width=560&fit=bounds)
![MPLS L3 VPN Tutorial, by Nurul Islam Roman [APNIC 38]](https://cdn.slidesharecdn.com/ss_thumbnails/mplsl3vpnapnic381410820509-140915192004-phpapp02-thumbnail.jpg?width=560&fit=bounds)
MPLS L3 VPN Tutorial, by Nurul Islam Roman [APNIC 38]APNIC This document discusses deploying MPLS L3VPN. It begins with an overview of MPLS and VPN terminology. It then covers the MPLS reference architecture and different node types. It describes how IP/VPN technologies use separate routing tables at provider edge (PE) routers to provide independent virtual routing and forwarding (VRF) instances for each VPN customer. The control plane uses multiprotocol BGP (MP-BGP) to distribute VPN routes between PE routers using route distinguisher (RD), route target (RT), and labels. The forwarding plane uses these labels to encapsulate and transport customer IP packets across the MPLS core. The document then discusses various IP/VPN services including load sharing, hub-and-spoke
Cisco Live! :: Carrier Ethernet 2.0 :: BRKSPG-2720 | Las Vegas July/2016



Cisco Live! :: Carrier Ethernet 2.0 :: BRKSPG-2720 | Las Vegas July/2016Bruno Teixeira The document discusses Carrier Ethernet 2.0 and next generation Carrier Ethernet architectures. It provides an agenda for topics including Carrier Ethernet fundamentals, new CE 2.0 services like E-Tree and E-Access, and service enhancements. The focus is on how CE 2.0 helps service providers expand services, simplify operations, and extend service reach through standardized MEF specifications.
OSPF Basics



OSPF BasicsMartin Bratina Open Shortest Path First (OSPF) is an interior gateway protocol that uses link state routing and the Dijkstra algorithm to calculate the shortest path to destinations within an autonomous system. It elects a Designated Router to generate network link advertisements and assist in database synchronization between routers. Routers run the Shortest Path First algorithm on their link state databases to determine the best routes and populate their routing tables.
EVPN-Presentation.pptx



EVPN-Presentation.pptxVimalMallick The document discusses Ethernet VPN (EVPN) functionality on Juniper Networks devices. It provides an overview of EVPN concepts including single-homed and multi-homed EVPN configurations, the differences between EVPN and VPLS, Junos support for EVPN, EVPN terminology, types of BGP routes used in EVPN, MAC learning processes, and trace log examples.
MPLS L3 VPN Deployment



MPLS L3 VPN DeploymentAPNIC The document provides information about an upcoming training course on deploying MPLS L3 VPNs. It includes details about the trainers, Nurul Islam Roman and Jessica Wei, their backgrounds and areas of expertise. It also outlines the course agenda which will cover topics such as MPLS VPN models, terminology, operation, configuration examples and service deployment scenarios.
Introduction to Segment Routing



Introduction to Segment RoutingMyNOG This document discusses segment routing and its benefits for incremental deployment in networks. It describes how segment routing uses MPLS or IPv6 routing headers to encode paths as ordered lists of segments. Segment routing allows more control over traffic paths compared to traditional IGP routing. It can enable traffic engineering and service chaining while maintaining network and control plane simplicity. The document argues segment routing is useful for scaling datacenters and simplifying peering relationships.
IOS Cisco - Cheat sheets



IOS Cisco - Cheat sheetsAlejandro Marin Cheats sheet for Cisco with all IPSec, IP v4, Ip v6, PPP, RIP, VLAN, VOIP, NAT, Terminations, Commands
MPLS - Multiprotocol Label Switching



MPLS - Multiprotocol Label SwitchingPeter R. Egli Overview of the MPLS backbone transmission technology.
MPLS (MultiProtocol Layer Switching) is a layer 2.5 technology that combines the virtues of IP routing and fast layer 2 packet switching.
IP packet forwarding is not suited for high-speed forwarding due to the need to evaluate multiple routes for each IP packet in order to find the optimal route, i.e. the route with the longest prefix match.
However, Internet Protocol routing provides global reachability through the IP address and through IP routing protocols like BGP or OSPF.
Layer 2 packet switching has complementary characteristics in that it does not provide global reachability through globally unique addresses but allows fast packet forwarding in hardware through the use of small and direct layer 2 lookup addresses.
MPLS combines IP routing and layer 2 switching by establishing layer 2 forwarding paths based on routes received through IP routing protocols like BGP or OSPF.
Thus the control plane of an MPLS capable device establishes layer 2 forwarding paths while the data plane then performs packet forwarding, often in hardware.
MPLS is not a layer 2 technology itself, i.e. it does not define a layer 2 protocol but rather makes use of existing layer 2 technologies like Ethernet, ATM or Frame Relay.
MPLS Layer 3 VPN 



MPLS Layer 3 VPN NetProtocol Xpert This document explains MPLS Layer 3 VPNs. It discusses how Layer 3 VPNs allow routing information to be shared between customer sites using protocols like OSPF and BGP across the service provider's MPLS network. It describes how Virtual Routing and Forwarding instances (VRFs), MP-BGP, Route Distinguishers (RDs), and Route Targets (RTs) work together to separate routing information for different customers and establish VPN connectivity between their sites while avoiding overlapping address spaces.
How BGP Works



How BGP WorksThousandEyes In this webinar, we cover how Border Gateway Protocol works. Starting from key concepts, you'll learn about Autonomous Systems, the BGP protocol, AS Path, learning and advertising routes, RIBs and route selection. See the webinar recording at https://www.thousandeyes.com/webinars/how-bgp-works
MPLS + BGP Presentation



MPLS + BGP PresentationGino McCarty This document provides an overview of Multiprotocol Label Switching (MPLS), including its history, key concepts, applications, and use by service providers. MPLS was developed in the late 1990s to meet the needs of scalable routing and quality of service on the growing internet. It works by assigning fixed length labels to data packets, allowing routers to forward based on these labels rather than long network addresses. Major applications of MPLS include traffic engineering, virtual private networks, and bandwidth management. The document discusses how service providers like MegaPath use MPLS in their backbones to provide integrated data and voice services, and nationwide networking solutions for corporate customers.
MPLS Concepts and Fundamentals



MPLS Concepts and FundamentalsShawn Zandi Early 2000s, Basic MPLS Fundamentals and Concepts by Shawn Zandi, Training Material for Networkers to learn MPLS and Label Switching
Eigrp.ppt



Eigrp.pptEdgardo Scrimaglia This document provides an overview of the Enhanced Interior Gateway Routing Protocol (EIGRP). It describes the history and development of EIGRP, its basic operation and components, including reliable transport protocol, packet types, neighbor discovery via hello packets, and route updates using the diffusing update algorithm. It also covers basic EIGRP configuration such as enabling it with the router eigrp command, advertising networks, and verifying neighbor relationships.
VLAN Trunking Protocol



VLAN Trunking ProtocolNetwax Lab VLAN Trunking Protocol (VTP) is a Cisco proprietary protocol that propagates the definition of Virtual
Local Area Networks (VLAN) on the whole local area network.[1] To do this, VTP carries VLAN
information to all the switches in a VTP domain. VTP advertisements can be sent over ISL, 802.1Q, IEEE
802.10 and LANE trunks. VTP is available on most of the Cisco Catalyst Family products.
MPLS VPN



MPLS VPNShahzaib Mahesar This document discusses MPLS VPN and its three main types: point-to-point VPNs using pseudowires to encapsulate traffic between two sites; layer 2 VPNs called VPLS that provide switched VLAN services across sites; and layer 3 VPNs known as VPRN that utilize VRF tables to segment routing for each customer using BGP. It describes how MPLS VPN works using CE, PE, and P routers to forward labeled packets through the provider network and pop the label at the destination PE to deliver the packet. Finally, it provides additional resources for learning more about MPLS VPN technologies.
CCCNP ROUTE v6_ch06



CCCNP ROUTE v6_ch06Licenciatura en Redes y Sistemas Operativos This chapter discusses implementing Border Gateway Protocol (BGP) solutions for Internet Service Provider (ISP) connectivity. It begins with an overview of BGP terminology such as autonomous systems (AS), AS numbers, and BGP peers. The chapter then covers basic BGP configuration and operation, including the exchange of routing information between BGP peers in different ASes. It also discusses considerations for connecting an enterprise network to an ISP, such as addressing, link types, redundancy, and routing protocols.
Is is



Is isIrham Nurhalim The document discusses the IS-IS routing protocol. It provides an overview of IS-IS, including that it is an interior gateway protocol used within an autonomous system. It also describes IS-IS levels, areas, and backbone routers. Finally, it discusses CLNS addressing, IS-IS PDUs like Hello packets, and other IS-IS concepts.
Similar to VRF (virtual routing and forwarding) (20)
ODA000017 MPLS VPN(L3).ppt



ODA000017 MPLS VPN(L3).pptmarwan76 1) The document defines several types of VPNs including IP-VPN, network-based IP-VPN, VLL, VPDN, VPLS, and VPRN. 2) MPLS VPN uses MPLS to create private networks over a public IP network. It establishes VPNs by using tunneling protocols and assigning unique routing identifiers to each VPN. 3) MPLS VPN provides isolation and security for each VPN by maintaining separate forwarding tables and using route distinguishers, route targets, and MPLS labels to direct traffic to the correct VPNs.
Mpls vpn.rip



Mpls vpn.ripfarhanica This document provides a configuration example for setting up an MPLS VPN with RIP routing on the customer side. Key aspects of the configuration include:
- Creating a VRF for each VPN and configuring route targets and import/export rules for BGP extended communities to associate routes with the correct VPN
- Configuring PE interfaces with the correct VRF forwarding and IP addresses
- Redistributing routes between routing protocols (RIP, OSPF, BGP) on the PE routers to exchange routes between the CE and P routers
- Configuring IBGP between PE routers to exchange VPNv4 routes using MPLS labels and BGP extended communities
International Journal of Engineering Research and Development (IJERD)



International Journal of Engineering Research and Development (IJERD)IJERD Editor call for paper 2012, hard copy of journal, research paper publishing, where to publish research paper,
journal publishing, how to publish research paper, Call For research paper, international journal, publishing a paper, IJERD, journal of science and technology, how to get a research paper published, publishing a paper, publishing of journal, publishing of research paper, reserach and review articles, IJERD Journal, How to publish your research paper, publish research paper, open access engineering journal, Engineering journal, Mathemetics journal, Physics journal, Chemistry journal, Computer Engineering, Computer Science journal, how to submit your paper, peer reviw journal, indexed journal, reserach and review articles, engineering journal, www.ijerd.com, research journals,
yahoo journals, bing journals, International Journal of Engineering Research and Development, google journals, hard copy of journal
V R F Checking



V R F Checkinginnyspencer This document discusses security concerns regarding MPLS VPN configurations and proposes methods to check MPLS VPN configurations for errors and compliance. Key points that should be checked include VPN access points, VRF configurations, route distinguishers (RD), route targets (RT), routes, and administrative/service VPN configurations. A tool is proposed to collect configuration data from provider edge (PE) routers periodically and check for obvious errors, inconsistencies, and non-compliance between actual and allocated configurations across all VPNs in the network. Results would be provided to both network operators and VPN owners.
Cube2012 high capacity service provider design using gpmls for ip next genera...



Cube2012 high capacity service provider design using gpmls for ip next genera...Ashish Tanwer The document discusses the design of a high capacity service provider network using Generalized Multiprotocol Label Switching (GMPLS) for next generation IP networks. It outlines the internal architecture of the service provider including the use of BGP confederations, virtual routing and forwarding instances (VRFs), route targets, and route distinguishers to optimize routing. It also describes different GMPLS topology models and considers hardware designs from Cisco, Juniper, and Ciena to support latest protocols, security, and scalability.
Mpls



MplsFasih Rehman The document discusses MPLS VPN configurations. It covers VPN concepts like overlay and peer models, benefits of MPLS VPNs, and how routing information is propagated between provider edge (PE) routers using MP-BGP. Key aspects include using virtual routing and forwarding (VRF) instances to isolate customer routes, extending prefixes with route distinguishers (RDs) to handle overlapping addresses, and exchanging VPN routes between PE routers in the provider network.
MPLS-based Layer 3 VPNs.pdf



MPLS-based Layer 3 VPNs.pdfHuynh MVT This lesson describes the concept of VPN and introduces some VPN terminology.
Importance
This lesson is the foundation lesson for the MPLS VPN Curriculum.
Objectives
Upon completion of this lesson, the learner will be able to perform the following
tasks:
■ Describe the concept of VPN
■ Explain VPN terminology as defined by MPLS VPN architecture
G010314853



G010314853IOSR Journals This document discusses implementing a virtual private network (VPN) over multi-protocol label switching (MPLS). It begins with an introduction to MPLS and how it works using label switching to route packets. It then discusses VPNs and how MPLS VPNs use separate routing tables called virtual routing and forwarding tables to isolate customer networks. The document demonstrates configuring an MPLS VPN using the GNS3 network simulator with two customer edge routers connecting two customer sites over an MPLS provider network. MPLS, VPNs, and the specific configuration steps are described. In the results section, the routing tables of the customer edge routers are shown to have routes from both customer sites, demonstrating that the MPLS VPN was successfully implemented to connect
CisCon 2018 - Overlay Management Protocol e IPsec



CisCon 2018 - Overlay Management Protocol e IPsecAreaNetworking.it Relatore: Alessandro Legnani, Cisco CCIE e IP Network Architect di IT Global Consulting Srl
Sintesi e sinergia perfetta di un nuovo protocollo di routing (e non solo) con il caro vecchio e robusto IPsec (senza le problematiche ike). Perché inventarsi l’ennesima forma di tunnelig per il data plane?
Quanto sopra è la chiave del successo della soluzione sdwan Cisco/Viptela che la rende enormemente scalabile e unica sul mercato.
Wp ip-mpls-based-vpns



Wp ip-mpls-based-vpnssubha_87 This document discusses and compares layer-3 and layer-2 approaches to implementing IP/MPLS-based VPNs. MPLS layer-3 VPNs use a routed approach defined in RFC 2547, where customer routes are exchanged between provider edge (PE) routers using BGP. MPLS layer-2 VPNs can provide point-to-point or multi-point connectivity using virtual circuits or virtual private LAN service. The document evaluates aspects of each approach like supported traffic, scalability, and complexity to help service providers determine the best fit for their network.
Ospf



OspfJoshua Fonseca This document discusses configuring and troubleshooting single-area OSPF routing. It covers topics like:
- Configuring static and dynamic routing on distribution and core routers
- Configuring and verifying single-area OSPF
- Designated router election process for multiaccess networks
- Propagating default static routes in OSPF
- Securing OSPF with message digest 5 authentication
- Components of troubleshooting single-area OSPF like forming adjacencies and transitioning states
ISP core routing project



ISP core routing projectvishal sharma This document describes an ISP core routing topology project that was implemented to demonstrate how a company accesses its servers through the internet. The key features of the project include MPLS Layer 3 VPN, an IPv6 network with an IPv6 DNS server, various redundancy protocols like HSRP, VRRP and GLBP, dynamic routing protocols such as BGP, EIGRP and OSPF, and a Linux server providing services like DNS, Apache, FTP and SSH. MPLS is used to eliminate delays and provide a VPN connecting different company branches. The topology also features an IPv6 tunnel over an IPv4 network and dual stacking for IPv6/IPv4 communication.
Day one-poster-vpns



Day one-poster-vpnsDervainJocelyn This document provides information about various VPN protocols and technologies, including their layer of operation, security implementation, control and transport protocols, and key advantages and limitations. It compares protocols like SSL, VXLAN, VPLS, EVPN, MPLS IP VPN, GRE, and IPsec. For example, it notes that VXLAN operates at layer 2, uses UDP for transport, can extend VLAN scaling, and has limited hashing entropy. MPLS IP VPN operates at layer 3, uses BGP for signaling, and depends on service provider infrastructure but offers flexibility, scalability, and interoperability.
Spirent TestCenter EVPN Emulation



Spirent TestCenter EVPN EmulationMalathi Malla Spirent's EVPN emulation package allows testing of complex EVPN topologies by emulating vast numbers of virtual network devices. It provides wizards to easily configure topologies and validate performance and scalability under scenarios like unicast, multicast, and multi-homing. The package comprehensively supports EVPN protocols, encapsulations like MPLS, VXLAN, and traffic types on Ethernet interfaces from 1G to 100G.
Ospf



Ospfgopi1985 The document provides an overview of the Open Shortest Path First (OSPF) routing protocol. It describes key OSPF concepts like link-state routing, shortest path first algorithm, areas, border routers, link-state advertisements, authentication, and route redistribution. It also covers OSPF configuration and design considerations for building large networks.
Distance Vector Multicast Routing Protocol : Notes



Distance Vector Multicast Routing Protocol : NotesSubhajit Sahu Highlighted notes while studying Advanced Computer Networks:
Distance Vector Multicast Routing Protocol
Source: Wikipedia
The Distance Vector Multicast Routing Protocol (DVMRP), defined in RFC 1075, is a routing protocol used to share information between routers to facilitate the transportation of IP multicast packets among networks. It formed the basis of the Internet's historic multicast backbone, Mbone.
Wikipedia is a free online encyclopedia, created and edited by volunteers around the world and hosted by the Wikimedia Foundation.
Juniper L2 MPLS VPN



Juniper L2 MPLS VPNmehrdad1981 1. The document discusses provider-provisioned layer 2 MPLS VPNs, which allow customers to construct private networks over a shared infrastructure while maintaining independent addressing and routing.
2. Key components include customer edge routers, provider edge routers, and provider routers. The provider edge routers exchange VPN routing information and use MPLS to forward traffic across the shared core network.
3. Provisioning involves configuring customer edge devices and VPN forwarding tables at provider edges to map customer sites to MPLS labels for transport across the core.
Group 1



Group 1lifetobeart The document discusses distance vector routing protocols and their characteristics. It explains that distance vector protocols advertise routes as vectors containing the distance and direction to a destination. Periodic full table updates are sent to neighbors on a regular basis. Common distance vector protocols include RIP, IGRP and EIGRP. EIGRP differs in that it sends partial updates only when there are topological changes rather than full periodic updates.
MPLS Presentation



MPLS PresentationUnni Kannan VijayaKumar The document provides an introduction to MPLS (Multi-Protocol Label Switching) technology. It discusses the goals of MPLS including understanding the business drivers, market segments, problems addressed, benefits, and major components. The key components of MPLS technology are explained, including MPLS forwarding and signaling, label distribution protocols, MPLS network services like VPNs, QoS, and traffic engineering. An overview of typical MPLS applications is also provided.
Ad
More from Netwax Lab (20)
Eincop Netwax Lab: Lab 1 static route



Eincop Netwax Lab: Lab 1 static routeNetwax Lab The document describes setting up static routes on 7 routers (R1-R7) to allow connectivity between all routers and PCs in a network topology. It involves configuring IP addresses and static routes on each router's interfaces according to the topology diagram, so that each router has a route to every other subnet and can ping all other routers and PCs.
Eincop Netwax Lab: HSRP (Hot Standby Router Protocol)



Eincop Netwax Lab: HSRP (Hot Standby Router Protocol)Netwax Lab This document outlines the steps to configure HSRP (Hot Standby Router Protocol) on two multi-layer switches (MLS1 and MLS2) including: configuring IP addresses, EIGRP routing, web server and NTP server, setting MLS1 as the active router, tracking the state of interfaces, using HSRP for load balancing between the routers, and enabling NAT on the border router for internal traffic.
Eincop Netwax Lab: Redistribution



Eincop Netwax Lab: RedistributionNetwax Lab The document provides instructions for a lab on route redistribution between OSPF, EIGRP and RIP routing protocols. It involves configuring the routing protocols on various routers as specified in the topology, including redistributing routes between protocols. It also requires summarizing loopback routes between areas and protocols.
Eincop Netwax Lab: Route Redistribution



Eincop Netwax Lab: Route RedistributionNetwax Lab Route redistribution involves sharing routes between different routing protocols. Challenges include incompatible metrics between protocols and routing loops or suboptimal paths that can occur from redistributing routes back into their origin domain. Route maps, distribution lists, and adjusting administrative distances can control redistribution and prevent issues like feedback of routes into their source protocol.
Nxll12 zone based firewall



Nxll12 zone based firewallNetwax Lab The document describes tasks for configuring a zone-based firewall on Router 1:
1. Create an inside and outside zone on Router 1's interfaces; apply an inspect policy between the zones to allow necessary traffic.
2. Configure R2 to ping R3 by name by adding DNS and host entries.
3. Configure R2 to copy a file from R4's HTTP server using the file path and name.
4. Configure R2 as the NTP server and have the other routers synchronize to it after applying necessary firewall policies.
Nxll11 bgp



Nxll11 bgpNetwax Lab The document provides the configuration steps for a lab exercise on BGP. The steps include:
1. Configuring IBGP and EBGP neighborships between routers as shown in the topology diagram using loopback addresses.
2. Advertising loopback networks in BGP to ensure all routers have the routing information.
3. Configuring route reflectors to reduce the number of neighbor relationships needed.
4. Setting preferences for best paths between routers for certain networks.
Nxll09 access list



Nxll09 access listNetwax Lab This document provides instructions for completing 12 tasks to configure access control lists on routers. The tasks include configuring IP addresses, inter-VLAN routing, EIGRP routing, DNS, Telnet/SSH access, and ACLs to restrict traffic between VLANs and access to websites based on the VLAN. Detailed configuration steps are provided for each router to implement the access controls and routing as outlined in the tasks.
Nxll21 ospf filtering & summarization



Nxll21 ospf filtering & summarizationNetwax Lab 1. The document provides instructions for configuring OSPF routing, filtering LSAs, and summarizing routes between OSPF areas on a network with multiple routers.
2. Tasks include configuring OSPF on each router, filtering routes between areas, redistributing EIGRP routes into OSPF, and using prefix lists and route summarization.
3. The solution shows the OSPF and redistribution configurations needed on each router to implement the requested tasks and filters.
Nxll10 v lan and trunking



Nxll10 v lan and trunkingNetwax Lab The document describes the tasks and solution for a lab on VLANs and trunking. The tasks are to: 1) Configure IP addresses as shown in the topology, 2) Create DHCP servers for VLANs 10 and 20, 3) Configure SW1 as the VTP server and the others as clients with the domain "netwaxlab.com", 4) Ensure PCs get IP addresses via DHCP, and 5) Allow communication between PCs 9 and 10 which have different IPs on the same VLAN. The solution describes the configurations needed on the switches to accomplish these tasks.
Nxll16 basic asa v8.2



Nxll16 basic asa v8.2Netwax Lab The document provides instructions for configuring an ASA firewall to:
1. Configure security levels and interfaces for DMZ and DMZ1 subnets.
2. Enable ping access between the DMZ and DMZ1 interfaces.
3. Restrict telnet access to the ASA to only the R2 host.
4. Enable SSH access to the ASA from the ISP subnet only.
5. Apply PAT for the Inside, DMZ and DMZ1 interfaces.
6. Allow the ISP to telnet to the R2 host using port 2487.
Nxll20 na ting 



Nxll20 na ting Netwax Lab The document describes tasks to configure NAT on routers R1 and R2. This includes dynamically NATing internal networks and loopbacks to external IP ranges, PAT for some internal networks, and static NAT for R7's loopbacks. EIGRP is configured internally with redistribution. Access-lists are used to define the NAT source addresses and pools are used to map them to external IP ranges. Connectivity to external sites is tested with ping.
Nxll14 cut through-proxy on asa



Nxll14 cut through-proxy on asaNetwax Lab This document provides instructions for configuring cut-through proxy on an ASA firewall. It includes steps to configure interfaces, ACLs, AAA authentication with an ISE server, a virtual Telnet IP, and verification tests. The goal is to allow a client to Telnet to a virtual IP on the ASA that will authenticate with ISE and cut through to permit access to a real host IP if authentication succeeds.
Nxll17 dynamic routing with asa



Nxll17 dynamic routing with asaNetwax Lab The document describes the steps to configure dynamic routing, site-to-site VPN, and network access between devices in a lab topology. The tasks include: 1) Configuring IP addresses and dynamic routing protocols on routers and firewalls, 2) Establishing connectivity between all devices, 3) Implementing NAT and VPN services on the firewalls to allow communication between specified subnets, and 4) Opening a non-standard port for remote access between two routers via one of the firewalls.
Nxll18 vpn (s2 s gre & dmvpn)



Nxll18 vpn (s2 s gre & dmvpn)Netwax Lab 1. The document describes configuring IP addresses, DNS, a site-to-site GRE VPN between routers R5 and R6, and a DMVPN network between routers R1, R2, and R3.
2. For the GRE VPN, ISAKMP and IPsec are configured on R5 and R6 using a preshared key of "netwaxlab" to secure the GRE tunnel.
3. For the DMVPN, R1 is configured as a hub router and R2 and R3 as spoke routers. ISAKMP and IPsec are configured using a preshared key of "netwaxlab" to secure the GRE tunnels between the routers.
Nxll19 vrrp (virtual router redundancy protocol)



Nxll19 vrrp (virtual router redundancy protocol)Netwax Lab The document describes configuring VRRP (Virtual Router Redundancy Protocol) on routers R1 and R2. It involves:
1. Configuring R1 as the master for VRRP group 1 using virtual IP 10.0.0.254 and authentication.
2. Configuring R2 as the master for load-balanced VRRP group 2 using virtual IP 10.0.0.193 and a different authentication string.
3. Enabling tracking on both routers so that the priority of the backup router decreases if the route to the opposite network fails, allowing it to take over as master.
Nxll22 role based cli



Nxll22 role based cliNetwax Lab 1. The document describes tasks for configuring a role-based CLI, including configuring IP addresses, routing protocols, VPN tunnels, and access privileges for different devices.
2. It provides configuration steps for R2 and R3 to enable PAT for inside networks and configure a site-to-site VPN between them with IPsec.
3. PC5 is given full access to R13 but can only use show commands on R14, while PC4 is limited to the show history command on R11.
Nxll25 hsrp with failover



Nxll25 hsrp with failoverNetwax Lab 1. The document describes configuring high availability routing between two firewalls (ASA1 and ASA2) using failover, and between two routers (MLS3 and R2) using HSRP.
2. It provides configuration examples for failover on the ASAs, HSRP on MLS3 and R2, PAT on the ASA and R2, and EIGRP routing between the ASA and MLS3.
3. It also specifies default gateways for different PCs to reach R1 via the active HSRP router.
Nxll26 bgp ii



Nxll26 bgp iiNetwax Lab 1. The document describes the configuration steps for a lab exercise involving BGP routing. It includes tasks to configure IP addresses, IBGP, HSRP, servers, and BGP routing on multiple routers as shown in the given topology diagram.
2. Key steps are to configure IBGP between routers R1-R4, HSRP between R5-R6, servers on R6, and BGP routing between all routers as specified in the tasks and topology, including IBGP, EBGP, route reflectors, and BGP confederations.
3. The goal is to verify connectivity between loopbacks and servers across the different BGP and IBGP domains as configured.
Nxll28 ospf iii



Nxll28 ospf iiiNetwax Lab 1. The document describes tasks for configuring OSPF routing on a network topology.
2. Key configurations include enabling OSPF on each router, configuring authentication for Area 1, summarizing loopback routes on R4, and preventing Area 3 routers from receiving routes from other areas.
3. PAT is configured on routers R1 and R11 to allow traffic from multiple private networks to use a single public IP address.
Nxll23 i pv6



Nxll23 i pv6Netwax Lab The document provides instructions for configuring IPv6 on a network topology. It includes tasks to configure IPv6 addresses on routers, configure Frame-Relay over IPv6, assign IPv6 addresses to routers through autoconfiguration, and configure OSPF routing between the routers.
Ad
Recently uploaded (20)
Increasing Retail Store Efficiency How can Planograms Save Time and Money.pptx



Increasing Retail Store Efficiency How can Planograms Save Time and Money.pptxAnoop Ashok In today's fast-paced retail environment, efficiency is key. Every minute counts, and every penny matters. One tool that can significantly boost your store's efficiency is a well-executed planogram. These visual merchandising blueprints not only enhance store layouts but also save time and money in the process.
Cybersecurity Identity and Access Solutions using Azure AD



Cybersecurity Identity and Access Solutions using Azure ADVICTOR MAESTRE RAMIREZ Cybersecurity Identity and Access Solutions using Azure AD
Transcript: #StandardsGoals for 2025: Standards & certification roundup - Tec...



Transcript: #StandardsGoals for 2025: Standards & certification roundup - Tec...BookNet Canada Book industry standards are evolving rapidly. In the first part of this session, we’ll share an overview of key developments from 2024 and the early months of 2025. Then, BookNet’s resident standards expert, Tom Richardson, and CEO, Lauren Stewart, have a forward-looking conversation about what’s next.
Link to recording, presentation slides, and accompanying resource: https://bnctechforum.ca/sessions/standardsgoals-for-2025-standards-certification-roundup/
Presented by BookNet Canada on May 6, 2025 with support from the Department of Canadian Heritage.
Technology Trends in 2025: AI and Big Data Analytics



Technology Trends in 2025: AI and Big Data AnalyticsInData Labs At InData Labs, we have been keeping an ear to the ground, looking out for AI-enabled digital transformation trends coming our way in 2025. Our report will provide a look into the technology landscape of the future, including:
-Artificial Intelligence Market Overview
-Strategies for AI Adoption in 2025
-Anticipated drivers of AI adoption and transformative technologies
-Benefits of AI and Big data for your business
-Tips on how to prepare your business for innovation
-AI and data privacy: Strategies for securing data privacy in AI models, etc.
Download your free copy nowand implement the key findings to improve your business.
The Evolution of Meme Coins A New Era for Digital Currency ppt.pdf



The Evolution of Meme Coins A New Era for Digital Currency ppt.pdfAbi john Analyze the growth of meme coins from mere online jokes to potential assets in the digital economy. Explore the community, culture, and utility as they elevate themselves to a new era in cryptocurrency.
IEDM 2024 Tutorial2_Advances in CMOS Technologies and Future Directions for C...



IEDM 2024 Tutorial2_Advances in CMOS Technologies and Future Directions for C...organizerofv IEDM 2024 Tutorial2
HCL Nomad Web – Best Practices and Managing Multiuser Environments



HCL Nomad Web – Best Practices and Managing Multiuser Environmentspanagenda Webinar Recording: https://www.panagenda.com/webinars/hcl-nomad-web-best-practices-and-managing-multiuser-environments/
HCL Nomad Web is heralded as the next generation of the HCL Notes client, offering numerous advantages such as eliminating the need for packaging, distribution, and installation. Nomad Web client upgrades will be installed “automatically” in the background. This significantly reduces the administrative footprint compared to traditional HCL Notes clients. However, troubleshooting issues in Nomad Web present unique challenges compared to the Notes client.
Join Christoph and Marc as they demonstrate how to simplify the troubleshooting process in HCL Nomad Web, ensuring a smoother and more efficient user experience.
In this webinar, we will explore effective strategies for diagnosing and resolving common problems in HCL Nomad Web, including
- Accessing the console
- Locating and interpreting log files
- Accessing the data folder within the browser’s cache (using OPFS)
- Understand the difference between single- and multi-user scenarios
- Utilizing Client Clocking
Mobile App Development Company in Saudi Arabia



Mobile App Development Company in Saudi ArabiaSteve Jonas EmizenTech is a globally recognized software development company, proudly serving businesses since 2013. With over 11+ years of industry experience and a team of 200+ skilled professionals, we have successfully delivered 1200+ projects across various sectors. As a leading Mobile App Development Company In Saudi Arabia we offer end-to-end solutions for iOS, Android, and cross-platform applications. Our apps are known for their user-friendly interfaces, scalability, high performance, and strong security features. We tailor each mobile application to meet the unique needs of different industries, ensuring a seamless user experience. EmizenTech is committed to turning your vision into a powerful digital product that drives growth, innovation, and long-term success in the competitive mobile landscape of Saudi Arabia.
Role of Data Annotation Services in AI-Powered Manufacturing



Role of Data Annotation Services in AI-Powered ManufacturingAndrew Leo From predictive maintenance to robotic automation, AI is driving the future of manufacturing. But without high-quality annotated data, even the smartest models fall short.
Discover how data annotation services are powering accuracy, safety, and efficiency in AI-driven manufacturing systems.
Precision in data labeling = Precision on the production floor.
DevOpsDays Atlanta 2025 - Building 10x Development Organizations.pptx



DevOpsDays Atlanta 2025 - Building 10x Development Organizations.pptxJustin Reock Building 10x Organizations with Modern Productivity Metrics
10x developers may be a myth, but 10x organizations are very real, as proven by the influential study performed in the 1980s, ‘The Coding War Games.’
Right now, here in early 2025, we seem to be experiencing YAPP (Yet Another Productivity Philosophy), and that philosophy is converging on developer experience. It seems that with every new method we invent for the delivery of products, whether physical or virtual, we reinvent productivity philosophies to go alongside them.
But which of these approaches actually work? DORA? SPACE? DevEx? What should we invest in and create urgency behind today, so that we don’t find ourselves having the same discussion again in a decade?
Manifest Pre-Seed Update | A Humanoid OEM Deeptech In France



Manifest Pre-Seed Update | A Humanoid OEM Deeptech In Francechb3 The latest updates on Manifest's pre-seed stage progress.
Noah Loul Shares 5 Steps to Implement AI Agents for Maximum Business Efficien...



Noah Loul Shares 5 Steps to Implement AI Agents for Maximum Business Efficien...Noah Loul Artificial intelligence is changing how businesses operate. Companies are using AI agents to automate tasks, reduce time spent on repetitive work, and focus more on high-value activities. Noah Loul, an AI strategist and entrepreneur, has helped dozens of companies streamline their operations using smart automation. He believes AI agents aren't just tools—they're workers that take on repeatable tasks so your human team can focus on what matters. If you want to reduce time waste and increase output, AI agents are the next move.
Semantic Cultivators : The Critical Future Role to Enable AI



Semantic Cultivators : The Critical Future Role to Enable AIartmondano By 2026, AI agents will consume 10x more enterprise data than humans, but with none of the contextual understanding that prevents catastrophic misinterpretations.
Generative Artificial Intelligence (GenAI) in Business



Generative Artificial Intelligence (GenAI) in BusinessDr. Tathagat Varma My talk for the Indian School of Business (ISB) Emerging Leaders Program Cohort 9. In this talk, I discussed key issues around adoption of GenAI in business - benefits, opportunities and limitations. I also discussed how my research on Theory of Cognitive Chasms helps address some of these issues
Into The Box Conference Keynote Day 1 (ITB2025)



Into The Box Conference Keynote Day 1 (ITB2025)Ortus Solutions, Corp This is the keynote of the Into the Box conference, highlighting the release of the BoxLang JVM language, its key enhancements, and its vision for the future.
Designing Low-Latency Systems with Rust and ScyllaDB: An Architectural Deep Dive



Designing Low-Latency Systems with Rust and ScyllaDB: An Architectural Deep DiveScyllaDB Want to learn practical tips for designing systems that can scale efficiently without compromising speed?
Join us for a workshop where we’ll address these challenges head-on and explore how to architect low-latency systems using Rust. During this free interactive workshop oriented for developers, engineers, and architects, we’ll cover how Rust’s unique language features and the Tokio async runtime enable high-performance application development.
As you explore key principles of designing low-latency systems with Rust, you will learn how to:
- Create and compile a real-world app with Rust
- Connect the application to ScyllaDB (NoSQL data store)
- Negotiate tradeoffs related to data modeling and querying
- Manage and monitor the database for consistently low latencies
Big Data Analytics Quick Research Guide by Arthur Morgan



Big Data Analytics Quick Research Guide by Arthur MorganArthur Morgan This is a Quick Research Guide (QRG).
QRGs include the following:
- A brief, high-level overview of the QRG topic.
- A milestone timeline for the QRG topic.
- Links to various free online resource materials to provide a deeper dive into the QRG topic.
- Conclusion and a recommendation for at least two books available in the SJPL system on the QRG topic.
QRGs planned for the series:
- Artificial Intelligence QRG
- Quantum Computing QRG
- Big Data Analytics QRG
- Spacecraft Guidance, Navigation & Control QRG (coming 2026)
- UK Home Computing & The Birth of ARM QRG (coming 2027)
Any questions or comments?
- Please contact Arthur Morgan at [email protected].
100% human made.
Dev Dives: Automate and orchestrate your processes with UiPath Maestro



Dev Dives: Automate and orchestrate your processes with UiPath MaestroUiPathCommunity This session is designed to equip developers with the skills needed to build mission-critical, end-to-end processes that seamlessly orchestrate agents, people, and robots.
📕 Here's what you can expect:
- Modeling: Build end-to-end processes using BPMN.
- Implementing: Integrate agentic tasks, RPA, APIs, and advanced decisioning into processes.
- Operating: Control process instances with rewind, replay, pause, and stop functions.
- Monitoring: Use dashboards and embedded analytics for real-time insights into process instances.
This webinar is a must-attend for developers looking to enhance their agentic automation skills and orchestrate robust, mission-critical processes.
👨🏫 Speaker:
Andrei Vintila, Principal Product Manager @UiPath
This session streamed live on April 29, 2025, 16:00 CET.
Check out all our upcoming Dev Dives sessions at https://community.uipath.com/dev-dives-automation-developer-2025/.
#StandardsGoals for 2025: Standards & certification roundup - Tech Forum 2025



#StandardsGoals for 2025: Standards & certification roundup - Tech Forum 2025BookNet Canada Book industry standards are evolving rapidly. In the first part of this session, we’ll share an overview of key developments from 2024 and the early months of 2025. Then, BookNet’s resident standards expert, Tom Richardson, and CEO, Lauren Stewart, have a forward-looking conversation about what’s next.
Link to recording, transcript, and accompanying resource: https://bnctechforum.ca/sessions/standardsgoals-for-2025-standards-certification-roundup/
Presented by BookNet Canada on May 6, 2025 with support from the Department of Canadian Heritage.
VRF (virtual routing and forwarding)
- 1. VRF (Virtual Routing and Forwarding) VRF (Virtual Routing and Forwarding) is a technology that allows multiple instances of a routing table to co-exist within the same router at the same time. This increases functionality by allowing network paths to be segmented without using multiple devices. Because traffic is automatically segregated, VRF also increases network security and can eliminate the need for encryption and authentication. Internet service providers (ISPs) often take advantage of VRF to create separate virtual private networks (VPNs) for customers; thus the technology is also referred to as VPN routing and forwarding. Because the routing instances are independent, the same or overlapping IP addresses can be used without conflicting with each other. VRF acts like a logical router, but while a logical router may include many routing tables, a VRF instance uses only a single routing table. In addition, VRF requires a forwarding table that designates the next hop for each data packet, a list of devices that may be called upon to forward the packet, and a set of rules and routing protocols that govern how the packet is forwarded. These tables prevent traffic from being forwarded outside a specific VRF path and also keep out traffic that should remain outside the VRF path. When we hear about VRF, its almost synonymous to MPLS VPN. Virtual Routing and Forwarding is commonly used by Service Providers to provide services within an MPLS cloud with multiple customers. The most interesting feature of this is that, VRF allows creation of multiple routing tables within a single router. This means that overlapping use of IP addresses from different customers is possible. Some enterprises use VRF to seggrate their services like VOIP, wireless, geographical location and other varieties. Just as with a VLAN based network using 802.1q trunks to extend the VLAN between switches, a VRF based design uses 802.1q trunks, GRE tunnels, or MPLS tags to extend and tie the VRFs together. Figure 1
- 2. VRF (Virtual Routing and Forwarding) VRF-Lite (Multi-VRF) VRF-lite is a feature that enables a service provider to support two or more VPNs, where IP addresses can be overlapped among the VPNs. VRF-lite uses input interfaces to distinguish routes for different VPNs and forms virtual packet-forwarding tables by associating one or more Layer 3 interfaces with each VRF. Interfaces in a VRF can be either physical, such as Ethernet ports, or logical, such as VLAN SVIs, but a Layer 3 interface cannot belong to more than one VRF at any time. It supports multiple, overlapping, independent routing and forwarding tables per customer. Any routing protocol supported by normal VRF can be used in a VRF-Lite CE implementation. The CE supports traffic separation between customer networks. As there is no MPLS functionality on the CE, no label exchange happens between the CE and PE. VRF-lite includes these devices: Customer edge (CE) devices provide customer access to the service provider network over a data link to one or more provider edge routers. The CE device advertises the site's local routes to the provider edge router and learns the remote VPN routes from it. A Catalyst 4500 series switch can be a CE. Provider edge (PE) routers exchange routing information with CE devices by using static routing or a routing protocol such as BGP, RIPv1, or RIPv2. The PE is only required to maintain VPN routes for those VPNs to which it is directly attached, eliminating the need for the PE to maintain all of the service provider VPN routes. Each PE router maintains a VRF for each of its directly connected sites. Multiple interfaces on a PE router can be associated with a single VRF if all of these sites participate in the same VPN. Each VPN is mapped to a specified VRF. After learning local VPN routes from CEs, a PE router exchanges VPN routing information with other PE routers by using internal BGP (iBPG). Provider routers (or core routers) are any routers in the service provider network that do not attach to CE devices. With VRF-lite, multiple customers can share one CE, and only one physical link is used between the CE and the PE. The shared CE maintains separate VRF tables for each customer and switches or routes packets for each customer based on its own routing table. VRF-lite extends limited PE functionality to a CE device, giving it the ability to maintain separate VRF tables to extend the privacy and security of a VPN to the branch office. Packet-Forwarding Process in a VRF-lite CE-enabled network: When the CE receives a packet from a VPN, it looks up the routing table based on the input interface. When a route is found, the CE forwards the packet to the PE.
- 3. VRF (Virtual Routing and Forwarding) When the ingress PE receives a packet from the CE, it performs a VRF lookup. When a route is found, the router adds a corresponding MPLS label to the packet and sends it to the MPLS network. When an egress PE receives a packet from the network, it strips the label and uses the label to identify the correct VPN routing table. The egress PE then performs the normal route lookup. When a route is found, it forwards the packet to the correct adjacency. When a CE receives a packet from an egress PE, it uses the input interface to look up the correct VPN routing table. If a route is found, the CE forwards the packet within the VPN. The VRF-lite network has three major components: VPN route target communities— Lists all other members of a VPN community. You need to configure VPN route targets for each VPN community member. Multiprotocol BGP peering of VPN community PE routers— Propagates VRF reachability information to all members of a VPN community. You need to configure BGP peering in all PE routers within a VPN community. VPN forwarding— Transports all traffic between all VPN community members across a VPN service-provider network. Application Shared Datacenters- The datacenter provider can use VRFs to reduce the number of device involved. Eg. If the datacenter is hosting three different customers (that use similar IP subnets) then there might be a need to three different routers. Figure 2
- 4. VRF (Virtual Routing and Forwarding) But if VRF is used, then only one router can be used. ISP- ISPs provide links between sites of multiple customers. By the use of VRF it is possible to use the same infrastructure for multiple customers. Without VRF Figure 3 Figure 4
- 5. VRF (Virtual Routing and Forwarding) With VRF A tag is added to each route. This tag is called a Route Distinguisher. Figure 5
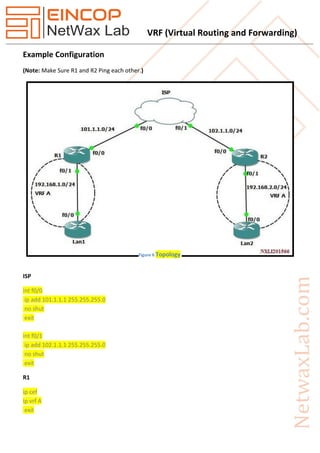
- 6. VRF (Virtual Routing and Forwarding) Example Configuration (Note: Make Sure R1 and R2 Ping each other.) ISP int f0/0 ip add 101.1.1.1 255.255.255.0 no shut exit int f0/1 ip add 102.1.1.1 255.255.255.0 no shut exit R1 ip cef ip vrf A exit Figure 6 Topology
- 7. VRF (Virtual Routing and Forwarding) int f0/0 ip add 101.1.1.100 255.255.255.0 no shut exit int f0/1 ip vrf forwarding A ip add 192.168.1.1 255.255.255.0 no shut exit ip route 0.0.0.0 0.0.0.0 101.1.1.1 crypto isakmp policy 10 encr 3des authentication pre-share group 2 lifetime 1800 exit crypto keyring KEY pre-shared-key address 102.1.1.100 key cisco exit crypto isakmp profile ISA vrf A keyring KEY match identity address 102.1.1.100 255.255.255.255 exit crypto ipsec transform-set tset esp-3des esp-sha-hmac exit ip access-list extended VPN permit ip host 192.168.1.100 host 192.168.2.100 exit crypto map CMAP 10 ipsec-isakmp set peer 102.1.1.100 set transform-set tset
- 8. VRF (Virtual Routing and Forwarding) set isakmp-profile ISA match address VPN reverse-route static exit int f0/0 crypto map CMAP exit R2 ip cef ip vrf A exit int f0/0 ip add 102.1.1.100 255.255.255.0 no shut exit int f0/1 ip vrf forwarding A ip add 192.168.2.1 255.255.255.0 no shut exit ip route 0.0.0.0 0.0.0.0 102.1.1.1 ip route vrf A 192.168.1.100 255.255.255.255 101.1.1.100 global (or you can use reverse-route static on Crypto map CMAP 10 ipsec-isakmp) crypto isakmp policy 10 encr 3des authentication pre-share group 2 lifetime 1800 exit crypto keyring KEY pre-shared-key address 101.1.1.100 key cisco exit
- 9. VRF (Virtual Routing and Forwarding) crypto isakmp profile ISA vrf A keyring KEY match identity address 101.1.1.100 255.255.255.255 exit crypto ipsec transform-set tset esp-3des esp-sha-hmac exit ip access-list extended VPN permit ip host 192.168.2.100 host 192.168.1.100 exit crypto map CMAP 10 ipsec-isakmp set peer 101.1.1.100 set transform-set tset set isakmp-profile ISA match address VPN exit int f0/0 crypto map CMAP exit Lan1 ip cef ip vrf A exit int f0/0 ip vrf forwarding A ip add 192.168.1.100 255.255.255.0 no shut exit ip route vrf A 0.0.0.0 0.0.0.0 192.168.1.1
- 10. VRF (Virtual Routing and Forwarding) Lan2 ip cef ip vrf A exit int f0/0 ip vrf forwarding A ip add 192.168.2.100 255.255.255.0 no shut exit ip route vrf A 0.0.0.0 0.0.0.0 192.168.2.1


