Oracle 11g security - 2014
1 like50 views
The document discusses Oracle's database security solutions. It notes that data security is a top priority for enterprises and that more data and breaches are occurring than ever before. It then summarizes Oracle's solutions like Database Firewall, Configuration Management, Total Recall, Audit Vault, Database Vault, and Data Masking which provide capabilities like monitoring, access control, auditing, encryption, and identity management to help secure database environments with a defense-in-depth approach.
1 of 19


















Ad
Recommended
Oracle Database 11g Security and Compliance Solutions - By Tom Kyte



Oracle Database 11g Security and Compliance Solutions - By Tom KyteEdgar Alejandro Villegas Oracle Database 11g Security and Compliance Solutions -
Presentation Slides
Oracle Webcast - Feb 2012 - http://goo.gl/T1SBIf
Tom Kyte, Sr. Technical Architect, Oracle
Troy Kitch, Sr. Manager, Database Security Product Marketing, Oracle
Security Inside Out: Latest Innovations in Oracle Database 12c



Security Inside Out: Latest Innovations in Oracle Database 12cTroy Kitch Oracle Database 12c includes more new security capabilities than any other release in Oracle history! In this presentation you will learn about these capabilities, as well as innovative new solutions to protect Oracle Database instances and non-Oracle databases. Hear how Oracle is responding to customer requirements to stay ahead of the evolving threat and regulatory landscape with new preventive controls that include data redaction and a new unified platform that provides database traffic monitoring and enterprise wide auditing.
Oracle Database Security



Oracle Database SecurityTroy Kitch The document discusses security issues with databases and Oracle's database security solutions. It notes that 97% of breaches were avoidable with basic controls, 98% of records were stolen from databases, and 84% of records were breached using stolen credentials. Oracle provides database security solutions like encryption, activity monitoring, auditing, and privileged user controls to help prevent breaches through a defense-in-depth approach.
Oracle database 12c 2 day + security guide



Oracle database 12c 2 day + security guidebupbechanhgmail This document provides a summary of the Oracle Database 2 Day + Security Guide, which introduces common day-to-day security tasks in Oracle Database. The guide is intended for database administrators who want to learn database security skills or who have some security knowledge but are new to Oracle Database. It covers topics such as securing the database installation, managing user privileges, encrypting data, controlling access with Oracle Database Vault, restricting access with Oracle Virtual Private Database, limiting access to sensitive data using Oracle Data Redaction, enforcing row-level security with Oracle Label Security, and auditing database activity. The guide includes tutorials for each of these security features to help the reader learn how to implement them. It also references related Oracle security documentation for more
Oracle database 12c security and compliance



Oracle database 12c security and complianceFITSFSd This document discusses Oracle Database 12c security features. It describes how Oracle Database 12c prevents database bypass, protects against operating system-level data access through transparent data encryption, and manages encryption keys with Oracle Key Vault. The document also covers reducing sensitive data exposure in applications, limiting exposure when sharing data, preventing application bypass, and protecting against privileged user bypass.
Auditing security of Oracle DB (Karel Miko)



Auditing security of Oracle DB (Karel Miko)DCIT, a.s. The document discusses auditing security of Oracle databases. It divides the audit into four technical phases:
1) Auditing the operating system level, including checking permissions on the Oracle home directory and verifying the OS account used for Oracle has appropriate privileges.
2) Auditing the Oracle RDBMS level, including validating the Oracle version and installed patches.
3) Auditing Oracle database instances, including verifying database options and privileges granted to users and roles.
4) Auditing related processes, such as the Oracle listener and associated configuration files.
Introducing Oracle Audit Vault and Database Firewall



Introducing Oracle Audit Vault and Database FirewallTroy Kitch Join us to hear about a new Oracle product that monitors Oracle and non-Oracle database traffic, detects unauthorized activity including SQL injection attacks, and blocks internal and external threats from reaching the database. In addition this new product collects and consolidates audit data from databases, operating systems, directories, and any custom template-defined source into a centralized, secure warehouse. This new enterprise security monitoring and auditing platform allows organizations to quickly detect and respond to threats with powerful real-time policy analysis, alerting and reporting capabilities. Based on proven SQL grammar analysis that ensures accuracy, performance, and scalability, organizations can deploy with confidence in any mode. You will also hear how organizations such as TransUnion Interactive and SquareTwo Financial rely on Oracle today to monitor and secure their Oracle and non-Oracle database environments.
AV/DF Advanced Security Option



AV/DF Advanced Security OptionDLT Solutions This document discusses database security solutions from Oracle, including Oracle Audit Vault and Database Firewall. It provides an overview of the Oracle Database Security solutions for activity monitoring, database firewalling, auditing and reporting, and encryption. It then focuses on describing the features and benefits of Oracle Audit Vault and Database Firewall, including how they provide database activity auditing and monitoring, extensive reporting, powerful alerting, and strengthened data security.
Ppt dbsec-oow2013-avdf



Ppt dbsec-oow2013-avdfMelody Liu Oracle Audit Vault and Database Firewall provide first line of defense for data security. Audit Vault collects audit data from multiple sources and stores it in a central repository, while Database Firewall monitors database activity in real-time and protects against SQL injections using positive and negative policy models. Both products support extensive reporting, alerting, and flexible deployment across the enterprise.
Best Practices in Implementing Oracle Database Security Products



Best Practices in Implementing Oracle Database Security ProductsEstuate, Inc. Information is the world’s new currency. Databases are the digital banks that store and retrieve valuable information. The growing number of high-profile incidents in which customer records, confidential information and intellectual property are leaked, lost or stolen has created an explosive demand for solutions that protect against the deliberate or inadvertent release of sensitive information.Oracle is the global leader in relational database technology, and has built a rich set of database security products and database features within its product portfolio.
Wp security-data-safe



Wp security-data-safeALI ANWAR, OCP® The objective of this workshop is to show existing Oracle Database (Enterprise
Edition, Exadata, Autonomous Database, EXACS, DBCS) customers how to
attach your Database to Data safe and gain valuable understanding of
potential risks. Using user Assessment, understand rights and entitlement of
users and review activity auditing which provides powerful insight to database
interaction. The workshop will finish with a full sensitive data discovery and
then how to anonymize date with sensitive data masking.
The workshop is delivered in an interactive way with Presentations and Hands on
Labs to ensure complete understanding.
Oracle Sparc Cloud



Oracle Sparc CloudErnest Jones Oracle's SPARC M7 processor is designed with unique security capabilities for cloud computing through Software in Silicon technology. It provides unprecedented levels of security, efficiency, and performance with features like silicon secured memory, hardware enabled secure live migration, and activity based user access control. Oracle's software in silicon technology integrates application acceleration and security at the processor level to enable the highest levels of security and application performance.
2015 AUG 24-Oracle EBS



2015 AUG 24-Oracle EBSHarriet Schneider The document discusses the need for masking sensitive data in non-production environments like test and development databases to comply with privacy regulations and prevent data breaches. It notes that the complexity of Oracle E-Business Suite applications makes custom data masking difficult without breaking the application. MENTIS provides an integrated static and dynamic data masking solution tailored for Oracle E-Business Suite that leverages pre-built intelligence to rapidly mask sensitive data locations while maintaining usability of applications across versions and environments.
Application Data Security | Seclore



Application Data Security | SecloreSeclore Today’s applications are often available over various networks and connected to the cloud, increasing vulnerabilities to security threats and breaches. Data extracted from these applications, either as documents or reports, lose the security once downloaded from the application, nor can the document be tracked. Hence it becomes vital to have strong application data security.
Bloombase store safe mf solution brief 2018 r0.91



Bloombase store safe mf solution brief 2018 r0.91Bloombase The document discusses the challenges of securing enterprise data across legacy systems and the need for comprehensive encryption and centralized key management. It introduces Bloombase StoreSafe and Micro Focus ESKM as a solution. StoreSafe provides transparent encryption across storage environments while ESKM delivers centralized, industry-validated key management for StoreSafe and other applications. Together they provide secure encryption and key management to protect sensitive data across heterogeneous systems.
Presentation1



Presentation1Kollipara Kiranmai This document outlines the table of contents for a project on securing cloud data. It discusses the existing problems of data security in cloud computing and the limitations of current encryption methods. It then proposes using decoy information technology called "fog computing" to launch disinformation attacks against malicious insiders and prevent them from distinguishing real data from fake data. The document also reviews security issues for different cloud service models like PaaS and IaaS and lists the software and hardware requirements for the project.
IRDAI Compliance & Data-Centric Security | Seclore



IRDAI Compliance & Data-Centric Security | SecloreSeclore IRDAI has prescribed an additional framework for the protection of policyholder information and data, which is required to be followed in addition to the general framework under the IT Act. Seclore’s Data-Centric security enables insurance organizations to be compliant with IRDAI’s Cyber Security Guidelines. Seclore provides persistent, granular usage controls to sensitive data stored on systems and network locations.
Oracle-Security_Executive-Presentation



Oracle-Security_Executive-Presentationstefanjung This document discusses Oracle security solutions. It begins with an overview of recent security breaches and their causes and consequences. It then discusses Oracle's defense-in-depth approach to security across infrastructure, database, middleware, applications, and interactions. The document outlines Oracle's security portfolio and components across these areas. It notes benefits to customers such as cost savings, compliance support, and integration capabilities. It concludes with recommendations based on lessons from client engagements and references Oracle security resources.
Cloud Data Security 



Cloud Data Security Seclore Today, 50% of all corporate data is stored in the cloud, and most of the data that is protected in the cloud is protected by encryption. Encryption is not enough to protect sensitive or regulatory data when shared outside the cloud. Seclore adds granular, persistent usage controls to sensitive data accessed, downloaded, or emailed from the cloud. Seclore can also protect data that is uploaded to cloud repositories such as SharePoint and OneDrive.
Securing Remote Workforce | Seclore



Securing Remote Workforce | SecloreSeclore As corporate perimeter expands to include remote employees, regulatory and sensitive data can travel across unmanaged networks or reside on unprotected personal devices. Seclore Rights Management protects data-in-transit, in-use, and at-rest by automatically applying persistent, granular usage controls to emails and documents.
GDPR Compliance & Data-Centric Security | Seclore



GDPR Compliance & Data-Centric Security | SecloreSeclore Today GDPR requires companies to take a more data-centric approach to security. Instead of focusing simply on protecting data at different layers of the technology, enterprises need to pay attention to securing data through its entire lifecycle.
Compliance regulations with Data Centric Security | Seclore



Compliance regulations with Data Centric Security | SecloreSeclore Most Compliance today has a gaping hole: there is little or no auditing of data sent outside your network to third parties or accessed on mobile devices. Seclore’s data-centric governance empowers you to control, track, and audit your data usage wherever it goes, greatly improving your ability to comply with GDPR, PCI, Export Administration, and other regional data privacy legislation.
Protecting the Healthcare Database



Protecting the Healthcare DatabaseSteve Dunn The healthcare database contains sensitive patient information and is vulnerable to attacks from both external and internal threats. While many people and systems require access to the database, this wide access increases security risks like insider breaches. To prevent unauthorized access and data breaches, organizations must implement comprehensive security strategies including professional-grade encryption of data at rest. Hardware-based encryption appliances provide superior performance and security compared to software solutions by offloading encryption processes and securely managing keys separate from encrypted data.
Azure Information Protection



Azure Information ProtectionRobert Crane Detect, classify, and protect sensitive information across cloud services and on-premises environments. Microsoft's solutions can scan for sensitive data, classify it based on sensitivity levels, and apply protections like encryption, access restrictions, and policies. Administrators can monitor protection events, access, and sharing for control and to tune policies.
Insider Threat Protection | Seclore



Insider Threat Protection | SecloreSeclore Seclore helps prevent insider risks by automatically attaching persistent, granular access and usage controls to emails and documents regardless of the device, network, or application. Seclore can also track activities on a protected document in real-time and revoke access at any time to ensure your data is safe
Inbound Data Protection



Inbound Data ProtectionSeclore The protection of personal data or intellectual property that customers, partners, and vendors share with organizations is often overlooked. Not only is sensitive data exposed to being stolen from internal and external threats, but organizations today could be held accountable to stricter compliance regulations such as GDPR and CCPA for improper handling of data.
The Seclore Data Protection Portal helps organizations safeguard sensitive data before it reaches employees and protects and tracks the data when shared within the organization.
[de Jager] Classify, Label and Protect your data with Azure Information Prote...![[de Jager] Classify, Label and Protect your data with Azure Information Prote...](https://cdn.slidesharecdn.com/ss_thumbnails/w6mg6986tiix1oas9zmi-signature-d4523b3bf020616e67040d2a940ba8bf9aeab187b20da49956548f98de22ea12-poli-180606121948-thumbnail.jpg?width=560&fit=bounds)
![[de Jager] Classify, Label and Protect your data with Azure Information Prote...](https://cdn.slidesharecdn.com/ss_thumbnails/w6mg6986tiix1oas9zmi-signature-d4523b3bf020616e67040d2a940ba8bf9aeab187b20da49956548f98de22ea12-poli-180606121948-thumbnail.jpg?width=560&fit=bounds)
![[de Jager] Classify, Label and Protect your data with Azure Information Prote...](https://cdn.slidesharecdn.com/ss_thumbnails/w6mg6986tiix1oas9zmi-signature-d4523b3bf020616e67040d2a940ba8bf9aeab187b20da49956548f98de22ea12-poli-180606121948-thumbnail.jpg?width=560&fit=bounds)
![[de Jager] Classify, Label and Protect your data with Azure Information Prote...](https://cdn.slidesharecdn.com/ss_thumbnails/w6mg6986tiix1oas9zmi-signature-d4523b3bf020616e67040d2a940ba8bf9aeab187b20da49956548f98de22ea12-poli-180606121948-thumbnail.jpg?width=560&fit=bounds)
[de Jager] Classify, Label and Protect your data with Azure Information Prote...European Collaboration Summit The document discusses security issues organizations face with data leaks and breaches. It notes a rise in intellectual property theft and data breaches often due to lack of internal controls and use of non-approved apps. New challenges in protecting data include managing hybrid data environments where data moves between on-premises and cloud locations. The document then introduces Azure Information Protection as a solution for classifying and labeling documents to set policies and control access.
Securing application data | Seclore



Securing application data | SecloreSeclore Seclore Email Encryption Plus persistent, granular usage controls are automatically applied on sensitive documents as soon as they are downloaded from or uploaded to the application. That allows employees and partners to use these applications and collaborate, with minimal impact on their productivity.
Best Practices for implementing Database Security Comprehensive Database Secu...



Best Practices for implementing Database Security Comprehensive Database Secu...Kal BO Best Practices for implementing Database Security
Comprehensive Database Security
Saikat Saha
Product Director
Database Security, Oracle
October 02, 2017
Innovations dbsec-12c-pub



Innovations dbsec-12c-pubOracleIDM The document outlines innovations in database security by Oracle. It discusses the changing security landscape, Oracle's database governance model, and its strategy for securing databases. The agenda indicates it will cover these topics and new security features in Oracle Database 12c, such as database vault, data masking, and encryption.
More Related Content
What's hot (20)
Ppt dbsec-oow2013-avdf



Ppt dbsec-oow2013-avdfMelody Liu Oracle Audit Vault and Database Firewall provide first line of defense for data security. Audit Vault collects audit data from multiple sources and stores it in a central repository, while Database Firewall monitors database activity in real-time and protects against SQL injections using positive and negative policy models. Both products support extensive reporting, alerting, and flexible deployment across the enterprise.
Best Practices in Implementing Oracle Database Security Products



Best Practices in Implementing Oracle Database Security ProductsEstuate, Inc. Information is the world’s new currency. Databases are the digital banks that store and retrieve valuable information. The growing number of high-profile incidents in which customer records, confidential information and intellectual property are leaked, lost or stolen has created an explosive demand for solutions that protect against the deliberate or inadvertent release of sensitive information.Oracle is the global leader in relational database technology, and has built a rich set of database security products and database features within its product portfolio.
Wp security-data-safe



Wp security-data-safeALI ANWAR, OCP® The objective of this workshop is to show existing Oracle Database (Enterprise
Edition, Exadata, Autonomous Database, EXACS, DBCS) customers how to
attach your Database to Data safe and gain valuable understanding of
potential risks. Using user Assessment, understand rights and entitlement of
users and review activity auditing which provides powerful insight to database
interaction. The workshop will finish with a full sensitive data discovery and
then how to anonymize date with sensitive data masking.
The workshop is delivered in an interactive way with Presentations and Hands on
Labs to ensure complete understanding.
Oracle Sparc Cloud



Oracle Sparc CloudErnest Jones Oracle's SPARC M7 processor is designed with unique security capabilities for cloud computing through Software in Silicon technology. It provides unprecedented levels of security, efficiency, and performance with features like silicon secured memory, hardware enabled secure live migration, and activity based user access control. Oracle's software in silicon technology integrates application acceleration and security at the processor level to enable the highest levels of security and application performance.
2015 AUG 24-Oracle EBS



2015 AUG 24-Oracle EBSHarriet Schneider The document discusses the need for masking sensitive data in non-production environments like test and development databases to comply with privacy regulations and prevent data breaches. It notes that the complexity of Oracle E-Business Suite applications makes custom data masking difficult without breaking the application. MENTIS provides an integrated static and dynamic data masking solution tailored for Oracle E-Business Suite that leverages pre-built intelligence to rapidly mask sensitive data locations while maintaining usability of applications across versions and environments.
Application Data Security | Seclore



Application Data Security | SecloreSeclore Today’s applications are often available over various networks and connected to the cloud, increasing vulnerabilities to security threats and breaches. Data extracted from these applications, either as documents or reports, lose the security once downloaded from the application, nor can the document be tracked. Hence it becomes vital to have strong application data security.
Bloombase store safe mf solution brief 2018 r0.91



Bloombase store safe mf solution brief 2018 r0.91Bloombase The document discusses the challenges of securing enterprise data across legacy systems and the need for comprehensive encryption and centralized key management. It introduces Bloombase StoreSafe and Micro Focus ESKM as a solution. StoreSafe provides transparent encryption across storage environments while ESKM delivers centralized, industry-validated key management for StoreSafe and other applications. Together they provide secure encryption and key management to protect sensitive data across heterogeneous systems.
Presentation1



Presentation1Kollipara Kiranmai This document outlines the table of contents for a project on securing cloud data. It discusses the existing problems of data security in cloud computing and the limitations of current encryption methods. It then proposes using decoy information technology called "fog computing" to launch disinformation attacks against malicious insiders and prevent them from distinguishing real data from fake data. The document also reviews security issues for different cloud service models like PaaS and IaaS and lists the software and hardware requirements for the project.
IRDAI Compliance & Data-Centric Security | Seclore



IRDAI Compliance & Data-Centric Security | SecloreSeclore IRDAI has prescribed an additional framework for the protection of policyholder information and data, which is required to be followed in addition to the general framework under the IT Act. Seclore’s Data-Centric security enables insurance organizations to be compliant with IRDAI’s Cyber Security Guidelines. Seclore provides persistent, granular usage controls to sensitive data stored on systems and network locations.
Oracle-Security_Executive-Presentation



Oracle-Security_Executive-Presentationstefanjung This document discusses Oracle security solutions. It begins with an overview of recent security breaches and their causes and consequences. It then discusses Oracle's defense-in-depth approach to security across infrastructure, database, middleware, applications, and interactions. The document outlines Oracle's security portfolio and components across these areas. It notes benefits to customers such as cost savings, compliance support, and integration capabilities. It concludes with recommendations based on lessons from client engagements and references Oracle security resources.
Cloud Data Security 



Cloud Data Security Seclore Today, 50% of all corporate data is stored in the cloud, and most of the data that is protected in the cloud is protected by encryption. Encryption is not enough to protect sensitive or regulatory data when shared outside the cloud. Seclore adds granular, persistent usage controls to sensitive data accessed, downloaded, or emailed from the cloud. Seclore can also protect data that is uploaded to cloud repositories such as SharePoint and OneDrive.
Securing Remote Workforce | Seclore



Securing Remote Workforce | SecloreSeclore As corporate perimeter expands to include remote employees, regulatory and sensitive data can travel across unmanaged networks or reside on unprotected personal devices. Seclore Rights Management protects data-in-transit, in-use, and at-rest by automatically applying persistent, granular usage controls to emails and documents.
GDPR Compliance & Data-Centric Security | Seclore



GDPR Compliance & Data-Centric Security | SecloreSeclore Today GDPR requires companies to take a more data-centric approach to security. Instead of focusing simply on protecting data at different layers of the technology, enterprises need to pay attention to securing data through its entire lifecycle.
Compliance regulations with Data Centric Security | Seclore



Compliance regulations with Data Centric Security | SecloreSeclore Most Compliance today has a gaping hole: there is little or no auditing of data sent outside your network to third parties or accessed on mobile devices. Seclore’s data-centric governance empowers you to control, track, and audit your data usage wherever it goes, greatly improving your ability to comply with GDPR, PCI, Export Administration, and other regional data privacy legislation.
Protecting the Healthcare Database



Protecting the Healthcare DatabaseSteve Dunn The healthcare database contains sensitive patient information and is vulnerable to attacks from both external and internal threats. While many people and systems require access to the database, this wide access increases security risks like insider breaches. To prevent unauthorized access and data breaches, organizations must implement comprehensive security strategies including professional-grade encryption of data at rest. Hardware-based encryption appliances provide superior performance and security compared to software solutions by offloading encryption processes and securely managing keys separate from encrypted data.
Azure Information Protection



Azure Information ProtectionRobert Crane Detect, classify, and protect sensitive information across cloud services and on-premises environments. Microsoft's solutions can scan for sensitive data, classify it based on sensitivity levels, and apply protections like encryption, access restrictions, and policies. Administrators can monitor protection events, access, and sharing for control and to tune policies.
Insider Threat Protection | Seclore



Insider Threat Protection | SecloreSeclore Seclore helps prevent insider risks by automatically attaching persistent, granular access and usage controls to emails and documents regardless of the device, network, or application. Seclore can also track activities on a protected document in real-time and revoke access at any time to ensure your data is safe
Inbound Data Protection



Inbound Data ProtectionSeclore The protection of personal data or intellectual property that customers, partners, and vendors share with organizations is often overlooked. Not only is sensitive data exposed to being stolen from internal and external threats, but organizations today could be held accountable to stricter compliance regulations such as GDPR and CCPA for improper handling of data.
The Seclore Data Protection Portal helps organizations safeguard sensitive data before it reaches employees and protects and tracks the data when shared within the organization.
[de Jager] Classify, Label and Protect your data with Azure Information Prote...![[de Jager] Classify, Label and Protect your data with Azure Information Prote...](https://cdn.slidesharecdn.com/ss_thumbnails/w6mg6986tiix1oas9zmi-signature-d4523b3bf020616e67040d2a940ba8bf9aeab187b20da49956548f98de22ea12-poli-180606121948-thumbnail.jpg?width=560&fit=bounds)
![[de Jager] Classify, Label and Protect your data with Azure Information Prote...](https://cdn.slidesharecdn.com/ss_thumbnails/w6mg6986tiix1oas9zmi-signature-d4523b3bf020616e67040d2a940ba8bf9aeab187b20da49956548f98de22ea12-poli-180606121948-thumbnail.jpg?width=560&fit=bounds)
![[de Jager] Classify, Label and Protect your data with Azure Information Prote...](https://cdn.slidesharecdn.com/ss_thumbnails/w6mg6986tiix1oas9zmi-signature-d4523b3bf020616e67040d2a940ba8bf9aeab187b20da49956548f98de22ea12-poli-180606121948-thumbnail.jpg?width=560&fit=bounds)
![[de Jager] Classify, Label and Protect your data with Azure Information Prote...](https://cdn.slidesharecdn.com/ss_thumbnails/w6mg6986tiix1oas9zmi-signature-d4523b3bf020616e67040d2a940ba8bf9aeab187b20da49956548f98de22ea12-poli-180606121948-thumbnail.jpg?width=560&fit=bounds)
[de Jager] Classify, Label and Protect your data with Azure Information Prote...European Collaboration Summit The document discusses security issues organizations face with data leaks and breaches. It notes a rise in intellectual property theft and data breaches often due to lack of internal controls and use of non-approved apps. New challenges in protecting data include managing hybrid data environments where data moves between on-premises and cloud locations. The document then introduces Azure Information Protection as a solution for classifying and labeling documents to set policies and control access.
Securing application data | Seclore



Securing application data | SecloreSeclore Seclore Email Encryption Plus persistent, granular usage controls are automatically applied on sensitive documents as soon as they are downloaded from or uploaded to the application. That allows employees and partners to use these applications and collaborate, with minimal impact on their productivity.
[de Jager] Classify, Label and Protect your data with Azure Information Prote...![[de Jager] Classify, Label and Protect your data with Azure Information Prote...](https://cdn.slidesharecdn.com/ss_thumbnails/w6mg6986tiix1oas9zmi-signature-d4523b3bf020616e67040d2a940ba8bf9aeab187b20da49956548f98de22ea12-poli-180606121948-thumbnail.jpg?width=560&fit=bounds)
![[de Jager] Classify, Label and Protect your data with Azure Information Prote...](https://cdn.slidesharecdn.com/ss_thumbnails/w6mg6986tiix1oas9zmi-signature-d4523b3bf020616e67040d2a940ba8bf9aeab187b20da49956548f98de22ea12-poli-180606121948-thumbnail.jpg?width=560&fit=bounds)
![[de Jager] Classify, Label and Protect your data with Azure Information Prote...](https://cdn.slidesharecdn.com/ss_thumbnails/w6mg6986tiix1oas9zmi-signature-d4523b3bf020616e67040d2a940ba8bf9aeab187b20da49956548f98de22ea12-poli-180606121948-thumbnail.jpg?width=560&fit=bounds)
![[de Jager] Classify, Label and Protect your data with Azure Information Prote...](https://cdn.slidesharecdn.com/ss_thumbnails/w6mg6986tiix1oas9zmi-signature-d4523b3bf020616e67040d2a940ba8bf9aeab187b20da49956548f98de22ea12-poli-180606121948-thumbnail.jpg?width=560&fit=bounds)
[de Jager] Classify, Label and Protect your data with Azure Information Prote...European Collaboration Summit
Similar to Oracle 11g security - 2014 (20)
Best Practices for implementing Database Security Comprehensive Database Secu...



Best Practices for implementing Database Security Comprehensive Database Secu...Kal BO Best Practices for implementing Database Security
Comprehensive Database Security
Saikat Saha
Product Director
Database Security, Oracle
October 02, 2017
Innovations dbsec-12c-pub



Innovations dbsec-12c-pubOracleIDM The document outlines innovations in database security by Oracle. It discusses the changing security landscape, Oracle's database governance model, and its strategy for securing databases. The agenda indicates it will cover these topics and new security features in Oracle Database 12c, such as database vault, data masking, and encryption.
Presentation database security audit vault & database firewall



Presentation database security audit vault & database firewallxKinAnx Download & Share Technology
Presentations http://ouo.io/XKLUj
Student Guide & Best http://ouo.io/8u1RP
Securing data in Oracle Database 12c - 2015



Securing data in Oracle Database 12c - 2015Connor McDonald The document discusses security features in Oracle Database 12c including Transparent Data Encryption (TDE), Privilege Analysis, Database Vault, Database Firewall, Data Redaction, Data Masking, and Audit Vault. It provides an overview of each technology and how they can be used to secure data at rest and in motion, monitor and control privileged access, and audit database activity. The document also outlines an agenda to cover these security controls in more depth.
5. 2010 11-03 bucharest oracle-tech_day_security



5. 2010 11-03 bucharest oracle-tech_day_securityDoina Draganescu This document outlines Oracle's product direction for data security at the source in public and private sectors. It discusses business drivers for security such as governance, risk management and compliance needs as well as security threats. It then describes Oracle's database security solutions like Transparent Data Encryption, Database Vault, and Audit Vault that secure data at rest, in motion and for testing. Case studies show how customers in various industries like banking, telecom, and public sectors have implemented Oracle's database security to protect sensitive data and comply with regulations. The document concludes that Oracle's database security solutions provide a preventive and detective approach to protect data at the source.
Database security best_practices



Database security best_practicesTarik Essawi This presentation provided techniques for securing an Oracle database, including: securing Oracle binaries and dump files; restricting and monitoring the listener; limiting privileges and authentication; implementing comprehensive auditing; and protecting data outside of production. The key areas discussed were securing the database binaries and directories, protecting the listener as a single point of failure, following the principle of least privilege, auditing for privilege escalation and changes to the audit trail, and securing backups and development data. The overall message was that firewalls alone are not enough and a layered security approach is needed to properly secure an Oracle database.
Database Private Security Jurisprudence: A Case Study using Oracle



Database Private Security Jurisprudence: A Case Study using OracleIJDMS Oracle is one of the largest vendors and the best DBMS solution of Object Relational DBMS in the IT world. Oracle Database is one of the three market-leading database technologies, along with Microsoft SQL Server's Database and IBM's DB2. Hence in this paper, we have tried to answer the million-dollar question “What is user’s responsibility to harden the oracle database for its security?” This paper gives practical guidelines for hardening the oracle database, so that attacker will be prevented to get access into the database. The practical lookout for protecting TNS, Accessing Remote Server and Prevention, Accessing Files on Remote Server, Fetching Environment Variables, Privileges and Authorizations, Access Control, writing security policy, Database Encryption, Oracle Data Mask, Standard built in Auditing and Fine Grained Auditing (FGA) is illustrated with SQL syntax and executed with suitable real life examples and its output is tested and verified. This structured method acts as Data Invictus wall for the attacker and protect user’s database.
DATABASE PRIVATE SECURITY JURISPRUDENCE: A CASE STUDY USING ORACLE



DATABASE PRIVATE SECURITY JURISPRUDENCE: A CASE STUDY USING ORACLEIJDMS Oracle is one of the largest vendors and the best DBMS solution of Object Relational DBMS in the IT world. Oracle Database is one of the three market-leading database technologies, along with Microsoft SQL Server's Database and IBM's DB2. Hence in this paper, we have tried to answer the million-dollar question “What is user’s responsibility to harden the oracle database for its security?” This paper gives practical guidelines for hardening the oracle database, so that attacker will be prevented to get access into the database. The practical lookout for protecting TNS, Accessing Remote Server and Prevention, Accessing Files on Remote Server, Fetching Environment Variables, Privileges and Authorizations, Access Control, writing security policy, Database Encryption, Oracle Data Mask, Standard built in Auditing and Fine Grained Auditing (FGA) is illustrated with SQL syntax and executed with suitable real life examples and its output is tested and verified. This structured method acts as Data Invictus wall for the attacker and protect user’s database.
Security in oracle



Security in oraclessuser40bb47 The document discusses security in Oracle databases. It covers several topics: Oracle Label Security which allows row-level access control based on user privileges; data masking and subsetting tools for replacing sensitive data; and auditing of database activities for accountability, investigation, and problem detection. Oracle provides various security components like encryption, redaction, key vaults, and firewalls to control access and monitor use of sensitive information in the database.
security in oracle database



security in oracle databasessuser40bb47 The document discusses security in Oracle databases. It covers several topics: Oracle Label Security which allows row-level access control based on user privileges; data masking and subsetting tools for replacing sensitive data; auditing of database activities for accountability, investigation, and problem detection; and encryption technologies like Transparent Data Encryption and Key Vault for securing data. Presenters Zahra Taghipoor kolaei and Seyyedeh Fatemeh Mousazadeh Mousavi led the discussion under Professor Dr. Sadegh Dorri Nogoorani during a winter 2022 class.
DOAG Oracle Database Vault



DOAG Oracle Database VaultStefan Oehrli Oracle Database Vault has been on the market for a few years now. The product has been constantly improved over the years. But where is it worthwhile to use it? Which security measures can be implemented with it? And from whom does DB Vault protect me at all? In this presentation, the technical possibilities of Database Vault 19c / 21c will be explained in addition to the experiences from two customer projects. We will try to show where the use of Database Vault is worthwhile under certain circumstances and under which conditions it is not. This also includes whether protection against snakes and thieves is ensured. PS: I asked my children what kind of presentation I should submit.The answers were snakes, thieves and cheetahs…
Database Options



Database OptionsConnor McDonald The document discusses various database options and packs available for the Oracle database. It summarizes:
- Real Application Clusters which allows databases to run on a shared platform for high availability and scalability.
- Advanced Compression which can compress tables by up to 4x to improve performance and reduce storage costs.
- Various security, management, and diagnostic packs that provide capabilities like encryption, auditing, performance monitoring and issue diagnosis, and automatic tuning.
Database Security – Issues and Best PracticesOutline



Database Security – Issues and Best PracticesOutlineOllieShoresna Database Security – Issues and Best Practices
Outline
• Intro to Database Security
•Need for Database Security
•Database Security Fundamentals
•Database Security Issues
• OWASP Top 10 – A1:2017– Injection
• OWASP Top 10 – A3:2017– Sensitive Data Exposure
•Attacks against Database Security Mechanisms
•Database Security Best Practices
2
Intro to Database Security
3
Intro to Database Security
• How does a web application work?
4
Client
Server
Involves
databases
Intro to Database Security (contd.)
•Database
• A database is “an organized collection of structured information, or
data, typically stored electronically in a computer system”
• It includes: the data, the DBMS, & applications that use them
•Database Management Systems (DBMS):
• DBMS serve “as an interface between the database and its end
users or programs, allowing users to retrieve, update, and manage
how the information is organized and optimized”
5
Source: What is a Database – Oracle –
https://www.oracle.com/database/what-is-database.html
https://www.oracle.com/database/what-is-database.html
Intro to Database Security (contd.)
•Database Management Systems (DBMS) (continued):
• DBMS also facilitate “oversight and control of databases, enabling a
variety of administrative operations such as performance
monitoring, tuning, and backup and recovery”
• Types:
• Relational, Object-Oriented, Distributed, Data Warehouses, Open Source,
Cloud, Autonomous, etc.
• Examples:
• Oracle, SQL Server, MySQL, Microsoft Access, MariaDB, PostgreSQL, etc.
6
Source: What is a Database – Oracle –
https://www.oracle.com/database/what-is-database.html
https://www.youtube.com/watch?v=_p00AzHE5U4
https://www.oracle.com/database/what-is-database.html
Intro to Database Security (contd.)
•Database Tutorial for Beginners – Lucidchart
7
Source: Lucidchart – Database Tutorial for Beginners –
https://www.youtube.com/watch?v=wR0jg0eQsZA
https://www.youtube.com/watch?v=wR0jg0eQsZA
Intro to Database Security (contd.)
•Database security refers to “the range of tools, controls, and
measures designed to establish and preserve database
confidentiality, integrity, and availability” (IBM, 2019)
•Database security involves protection of
• The data in the database
• The database management system (DBMS) itself
• Any associated applications (including web applications)
• The physical and/or virtual database server farms and their
underlying hardware
• The computing and/or network infrastructure used to access
the database (IBM, 2019)
8
https://www.ibm.com/cloud/learn/database-security
https://www.ibm.com/cloud/learn/database-security
Intro to Database Security (contd.)
•Database security involves securing data
• At rest
• Using techniques such as encryption
• Example: Amazon RDS uses 256-bit Advanced Encryption Standard (AES) for
securing database instances, automated backups, and snapshots at rest
• In flight
• Using protocols such as Transport Layer ...
Autonomous Database Security Features



Autonomous Database Security FeaturesSinanPetrusToma This document discusses security features of Oracle Autonomous Database including:
- Encryption of data at rest and in backups using transparent data encryption
- Network access control using access control lists and private endpoints
- System and data protection with features like Database Vault and command restrictions
- Discovery and masking of sensitive data using tools like Data Redaction and Data Safe
- Auditing of database activity, APIs, and network traffic for monitoring and compliance
Oracle Key Vault Data Subsetting and Masking



Oracle Key Vault Data Subsetting and MaskingDLT Solutions The document provides an overview of Oracle Key Vault and Data Subsetting and Masking Pack. It discusses how Oracle Key Vault can be used to centrally manage encryption keys and securely share them across databases, middleware, and systems. It also summarizes the key capabilities of Oracle Data Subsetting and Masking Pack, which can be used to discover, mask, and subset sensitive data to limit its proliferation while sharing non-sensitive data with others. The document highlights use cases, challenges, methodology, transformation types, and deployment options for data masking and subsetting.
Security In Oracle Database V19c



Security In Oracle Database V19calixa13 This document discusses security capabilities in Oracle databases. It covers topics like Advanced Security, KeyVault, Database Auditing, AuditVault and Database Firewall, DatabaseVault, Label Security, Real Application Security, Data Masking and Subsetting Pack, and Authentication and Authorization. The document provides details on Transparent Data Encryption, Data Redaction, key management services, unified auditing, monitoring threats, restricting privileged access, row-level security, and authentication methods in Oracle databases.
ppt-security-dbsat-222-overview-nodemo.pdf



ppt-security-dbsat-222-overview-nodemo.pdfcamyla81 DBSAT is a security assessment tool from Oracle that allows users to assess the security of their Oracle databases. It provides three main functions: it collects metadata on users, roles, privileges and security configuration; it generates a summary report of findings and recommendations; and it discovers sensitive data in the database. The tool aims to help users understand their database security posture, privileged users and roles, and sensitive data stored in the database.
MySQL Security



MySQL SecurityMario Beck MySQL offers several new functionality to enhance security and make MySQL suitable for critical environments. Several add-ons help achieving regulatory compliance like PCI-DSS. Here is an overview of these features.
Percona Live Europe 2018: What's New in MySQL 8.0 Security



Percona Live Europe 2018: What's New in MySQL 8.0 SecurityGeorgi Kodinov In this session get an overview of all the new security features in MySQL 8.0 and how they fit together to answer the modern security challenges. MySQL 8 takes a new step in tightening the security of MySQL installations and provides new and flexible tools including a brand new default authentication method, SQL roles, enhancements in transparent disk encryption, and modern password controls on password reuse, complexity, and brute force password guessing.
Oracle database threats - LAOUC Webinar



Oracle database threats - LAOUC WebinarOsama Mustafa This document discusses database security and how databases can be hacked. It begins by introducing the presenter and their qualifications. It then discusses why database security is important for protecting financial, customer and organizational data. Common ways databases are hacked include gathering information through search engines or social media, scanning for vulnerabilities, gaining unauthorized access, and maintaining that access. Specific attacks on Oracle databases and the most common database security threats are outlined, such as weak authentication, denial of service attacks, and SQL injection. The document provides examples of how to test for and exploit SQL injection vulnerabilities. It emphasizes the importance of securing databases to prevent data theft and protect sensitive information.
Ad
More from Connor McDonald (20)
Flashback ITOUG



Flashback ITOUGConnor McDonald Slides from the ITOUG events in Rome and Milan 2020.
Most people think of the Flashback features in Oracle as the "In Case of Emergency" switch, to only be used when some catastrophe has occurred on your database. And while it is true that Flashback will definitely help you 3 seconds after you press the Commit button and you realise that you probably needed to have a WHERE clause on that "delete all rows from the SALES table" SQL statement. Or for when you run "drop table" on the Production database, when you were just so sure that you were logged onto the Test system. But Flashback is not only for those "Oh No!" moments. It enables benefits for developers ranging from data consistency to continuous integration and data auditing. Tucked away in Enterprise Edition are six independent and powerful technologies that might just save your career—they will also open up a myriad of other benefits of well.
Sangam 19 - PLSQL still the coolest



Sangam 19 - PLSQL still the coolestConnor McDonald Another year goes by, and most likely, another data access framework has been invented. It will claim to be the fastest, smartest way to talk to the database, and just like all those that came before it, it will not be. Because the best database access tool has been there for more than 30 years now, and that is PL/SQL. Although we all sometimes fall prey to the mindset of “Oh look, a shiny new tool, we should start using it," the performance and simplicity of PL/SQL remain unmatched. This session looks at the failings of other data access languages, why even a cursory knowledge of PL/SQL will make you a better developer, and how to get the most out of PL/SQL when it comes to database performance.
Sangam 19 - Analytic SQL



Sangam 19 - Analytic SQLConnor McDonald Analytic SQL functions, or "window functions have been there since 8.1.6, but they are still dramatically underused by application developers. This session looks at the syntax and usage of analytic functions, and how they can supercharge your SQL skillset.
Covers analytics from their inception in 8.1.6 all the through to enhancements in 18 and 19
UKOUG - 25 years of hints and tips



UKOUG - 25 years of hints and tipsConnor McDonald A plethora of tips and techniques to boost your productivity as a DBA or Developer with the Oracle Database
Sangam 19 - Successful Applications on Autonomous



Sangam 19 - Successful Applications on AutonomousConnor McDonald The autonomous database offers insane levels of performance, but you won't be able to attain that if you are not constructing your SQL statements in a way that is scalable...and more importantly, secure from hacking
Sangam 2019 - The Latest Features



Sangam 2019 - The Latest FeaturesConnor McDonald The document discusses various ways to concatenate or aggregate column values in Oracle databases. Older methods like XMLAGG, CONNECT BY, and custom aggregate functions are compared to the simpler LISTAGG function available in Oracle 11g and higher. Upgrading to newer database versions brings improved developer productivity through easier string aggregation queries.
UKOUG 2019 - SQL features



UKOUG 2019 - SQL featuresConnor McDonald By expanding our knowledge of SQL facilities, we can let all the boring work be handled via SQL rather than a lot of middle-tier code, and we can get performance benefits as an added bonus. Here are some SQL techniques to solve problems that would otherwise require a lot of complex coding, freeing up your time to focus on the delivery of great applications.
APEX tour 2019 - successful development with autonomous



APEX tour 2019 - successful development with autonomousConnor McDonald The autonomous database offers insane levels of performance, but you won't be able to attain that if you are not constructing your SQL statements in a way that is scalable...and more importantly, secure from hacking
Apologies for most pics missing and awful layout...you can thank slideshare for that :-(
APAC Groundbreakers 2019 - Perth/Melbourne 



APAC Groundbreakers 2019 - Perth/Melbourne Connor McDonald Slides from the APAC Groundbreakers Tour from Perth and Melbourne legs. This session covered the features in 18c, 19c and 20c, along with the new free database offerings from Oracle from OpenWorld 2019
OOW19 - Flashback, not just for DBAs



OOW19 - Flashback, not just for DBAsConnor McDonald Slides from OpenWorld. Flashback has been around for long time yet people assume it should entirely within the realm of the DBA. But with modern development techniques such as continuous integration/continuous deployment, flashback actually is a perfect for *developers*
OOW19 - Read consistency



OOW19 - Read consistencyConnor McDonald Slides from the OpenWorld talk on read consistency. It is the feature that makes Oracle such a great database for performance and concurrency. But if misunderstood, it can lead to confusion for developers
OOW19 - Slower and less secure applications



OOW19 - Slower and less secure applicationsConnor McDonald Slides from OpenWorld 2019. Want to make sure your applications are slow, burn lots of CPU, and are easily broken into by hackers? Well...in reality, if you know how to do this, then you'll know how to avoid it.
OOW19 - Killing database sessions



OOW19 - Killing database sessionsConnor McDonald Slides from Openworl 2019. A look at how to safely (and unsafely) kill sessions in the Oracle database, and how to perhaps avoid killing them altogether.
OOW19 - Ten Amazing SQL features



OOW19 - Ten Amazing SQL featuresConnor McDonald Slides from Openworl 2019. 40 years old SQL continues to shine as the predominant data access language.
Latin America Tour 2019 - 18c and 19c featues



Latin America Tour 2019 - 18c and 19c featuesConnor McDonald Slides from new features session in Mexico. We look at the killer features that will make 18c and 19c great productivity upgrades for DBAs
Latin America tour 2019 - Flashback



Latin America tour 2019 - FlashbackConnor McDonald Flashback is not only for those "Oh No!" moments when we make a mistake. It enables benefits for developers ranging from data consistency to continuous integration and data auditing. Tucked away in Enterprise Edition are six independent and powerful technologies that might just save your career—they will also open up a myriad of other benefits of well.
Latin America Tour 2019 - 10 great sql features



Latin America Tour 2019 - 10 great sql featuresConnor McDonald By expanding our knowledge of SQL facilities, we can let all the boring work be handled via SQL rather than a lot of middle-tier code, and we can get performance benefits as an added bonus. Here are some SQL techniques to solve problems that would otherwise require a lot of complex coding, freeing up your time to focus on the delivery of great applications.
Latin America Tour 2019 - pattern matching



Latin America Tour 2019 - pattern matchingConnor McDonald The document discusses pattern matching and summarizing employee data by department. It provides examples of using SQL to concatenate employee names grouped by department, including older techniques using MODEL clause, CONNECT BY, and XMLTRANSFORM, as well as newer techniques using LISTAGG. It also discusses challenges in summarizing data and provides an example of analyzing customer transaction data to identify customers meeting growth criteria over single and multiple days.
Latin America Tour 2019 - slow data and sql processing



Latin America Tour 2019 - slow data and sql processingConnor McDonald The document discusses techniques for improving SQL performance by reducing parsing overhead. It describes how the library cache can store the results of previous SQL parses to avoid reparsing identical or similar statements. Binding SQL statements with placeholders avoids unnecessary reparsing when statements differ only by literal values. The document emphasizes that binding user input values is critical for security to prevent SQL injection attacks.
ANSI vs Oracle language



ANSI vs Oracle languageConnor McDonald This document discusses various SQL join queries using the EMP and DEPT tables in the Oracle database. It provides examples of inner joins, outer joins, natural joins, cross joins, and lateral joins. It explores different join types and syntax as well as filtering criteria and partitioning.
Ad
Recently uploaded (20)
Artificial Intelligence in the Nonprofit Boardroom.pdf



Artificial Intelligence in the Nonprofit Boardroom.pdfOnBoard OnBoard recently partnered with Microsoft Tech for Social Impact on the AI in the Nonprofit Boardroom Survey, an initiative designed to uncover the current and future role of artificial intelligence in nonprofit governance.
Oracle Cloud Infrastructure AI Foundations



Oracle Cloud Infrastructure AI FoundationsVICTOR MAESTRE RAMIREZ Oracle Cloud Infrastructure AI Foundations
“State-space Models vs. Transformers for Ultra-low-power Edge AI,” a Presenta...



“State-space Models vs. Transformers for Ultra-low-power Edge AI,” a Presenta...Edge AI and Vision Alliance For the full video of this presentation, please visit: https://www.edge-ai-vision.com/2025/06/state-space-models-vs-transformers-for-ultra-low-power-edge-ai-a-presentation-from-brainchip/
Tony Lewis, Chief Technology Officer at BrainChip, presents the “State-space Models vs. Transformers for Ultra-low-power Edge AI” tutorial at the May 2025 Embedded Vision Summit.
At the embedded edge, choices of language model architectures have profound implications on the ability to meet demanding performance, latency and energy efficiency requirements. In this presentation, Lewis contrasts state-space models (SSMs) with transformers for use in this constrained regime. While transformers rely on a read-write key-value cache, SSMs can be constructed as read-only architectures, enabling the use of novel memory types and reducing power consumption. Furthermore, SSMs require significantly fewer multiply-accumulate units—drastically reducing compute energy and chip area.
New techniques enable distillation-based migration from transformer models such as Llama to SSMs without major performance loss. In latency-sensitive applications, techniques such as precomputing input sequences allow SSMs to achieve sub-100 ms time-to-first-token, enabling real-time interactivity. Lewis presents a detailed side-by-side comparison of these architectures, outlining their trade-offs and opportunities at the extreme edge.
Domino IQ – Was Sie erwartet, erste Schritte und Anwendungsfälle



Domino IQ – Was Sie erwartet, erste Schritte und Anwendungsfällepanagenda Webinar Recording: https://www.panagenda.com/webinars/domino-iq-was-sie-erwartet-erste-schritte-und-anwendungsfalle/
HCL Domino iQ Server – Vom Ideenportal zur implementierten Funktion. Entdecken Sie, was es ist, was es nicht ist, und erkunden Sie die Chancen und Herausforderungen, die es bietet.
Wichtige Erkenntnisse
- Was sind Large Language Models (LLMs) und wie stehen sie im Zusammenhang mit Domino iQ
- Wesentliche Voraussetzungen für die Bereitstellung des Domino iQ Servers
- Schritt-für-Schritt-Anleitung zur Einrichtung Ihres Domino iQ Servers
- Teilen und diskutieren Sie Gedanken und Ideen, um das Potenzial von Domino iQ zu maximieren
National Fuels Treatments Initiative: Building a Seamless Map of Hazardous Fu...



National Fuels Treatments Initiative: Building a Seamless Map of Hazardous Fu...Safe Software The National Fuels Treatments Initiative (NFT) is transforming wildfire mitigation by creating a standardized map of nationwide fuels treatment locations across all land ownerships in the United States. While existing state and federal systems capture this data in diverse formats, NFT bridges these gaps, delivering the first truly integrated national view. This dataset will be used to measure the implementation of the National Cohesive Wildland Strategy and demonstrate the positive impact of collective investments in hazardous fuels reduction nationwide. In Phase 1, we developed an ETL pipeline template in FME Form, leveraging a schema-agnostic workflow with dynamic feature handling intended for fast roll-out and light maintenance. This was key as the initiative scaled from a few to over fifty contributors nationwide. By directly pulling from agency data stores, oftentimes ArcGIS Feature Services, NFT preserves existing structures, minimizing preparation needs. External mapping tables ensure consistent attribute and domain alignment, while robust change detection processes keep data current and actionable. Now in Phase 2, we’re migrating pipelines to FME Flow to take advantage of advanced scheduling, monitoring dashboards, and automated notifications to streamline operations. Join us to explore how this initiative exemplifies the power of technology, blending FME, ArcGIS Online, and AWS to solve a national business problem with a scalable, automated solution.
Cisco ISE Performance, Scalability and Best Practices.pdf



Cisco ISE Performance, Scalability and Best Practices.pdfsuperdpz Cisco ISE Performance, Scalability and Best Practices
Trends Artificial Intelligence - Mary Meeker



Trends Artificial Intelligence - Mary MeekerClive Dickens Mary Meeker’s 2024 AI report highlights a seismic shift in productivity, creativity, and business value driven by generative AI. She charts the rapid adoption of tools like ChatGPT and Midjourney, likening today’s moment to the dawn of the internet. The report emphasizes AI’s impact on knowledge work, software development, and personalized services—while also cautioning about data quality, ethical use, and the human-AI partnership. In short, Meeker sees AI as a transformative force accelerating innovation and redefining how we live and work.
Agentic AI: Beyond the Buzz- LangGraph Studio V2



Agentic AI: Beyond the Buzz- LangGraph Studio V2Shashikant Jagtap Presentation given at the LangChain community meetup London
https://lu.ma/9d5fntgj
Coveres
Agentic AI: Beyond the Buzz
Introduction to AI Agent and Agentic AI
Agent Use case and stats
Introduction to LangGraph
Build agent with LangGraph Studio V2
Creating an Accessible Future-How AI-powered Accessibility Testing is Shaping...



Creating an Accessible Future-How AI-powered Accessibility Testing is Shaping...Impelsys Inc. Web accessibility is a fundamental principle that strives to make the internet inclusive for all. According to the World Health Organization, over a billion people worldwide live with some form of disability. These individuals face significant challenges when navigating the digital landscape, making the quest for accessible web content more critical than ever.
Enter Artificial Intelligence (AI), a technological marvel with the potential to reshape the way we approach web accessibility. AI offers innovative solutions that can automate processes, enhance user experiences, and ultimately revolutionize web accessibility. In this blog post, we’ll explore how AI is making waves in the world of web accessibility.
Providing an OGC API Processes REST Interface for FME Flow



Providing an OGC API Processes REST Interface for FME FlowSafe Software This presentation will showcase an adapter for FME Flow that provides REST endpoints for FME Workspaces following the OGC API Processes specification. The implementation delivers robust, user-friendly API endpoints, including standardized methods for parameter provision. Additionally, it enhances security and user management by supporting OAuth2 authentication. Join us to discover how these advancements can elevate your enterprise integration workflows and ensure seamless, secure interactions with FME Flow.
Oracle Cloud and AI Specialization Program



Oracle Cloud and AI Specialization ProgramVICTOR MAESTRE RAMIREZ Oracle Cloud and AI Specialization Program
PyData - Graph Theory for Multi-Agent Integration



PyData - Graph Theory for Multi-Agent Integrationbarqawicloud Graph theory is a well-known concept for algorithms and can be used to orchestrate the building of multi-model pipelines. By translating tasks and dependencies into a Directed Acyclic Graph, we can orchestrate diverse AI models, including NLP, vision, and recommendation capabilities. This tutorial provides a step-by-step approach to designing graph-based AI model pipelines, focusing on clinical use cases from the field.
Enabling BIM / GIS integrations with Other Systems with FME



Enabling BIM / GIS integrations with Other Systems with FMESafe Software Jacobs has successfully utilized FME to tackle the complexities of integrating diverse data sources in a confidential $1 billion campus improvement project. The project aimed to create a comprehensive digital twin by merging Building Information Modeling (BIM) data, Construction Operations Building Information Exchange (COBie) data, and various other data sources into a unified Geographic Information System (GIS) platform. The challenge lay in the disparate nature of these data sources, which were siloed and incompatible with each other, hindering efficient data management and decision-making processes.
To address this, Jacobs leveraged FME to automate the extraction, transformation, and loading (ETL) of data between ArcGIS Indoors and IBM Maximo. This process ensured accurate transfer of maintainable asset and work order data, creating a comprehensive 2D and 3D representation of the campus for Facility Management. FME's server capabilities enabled real-time updates and synchronization between ArcGIS Indoors and Maximo, facilitating automatic updates of asset information and work orders. Additionally, Survey123 forms allowed field personnel to capture and submit data directly from their mobile devices, triggering FME workflows via webhooks for real-time data updates. This seamless integration has significantly enhanced data management, improved decision-making processes, and ensured data consistency across the project lifecycle.
Crypto Super 500 - 14th Report - June2025.pdf



Crypto Super 500 - 14th Report - June2025.pdfStephen Perrenod This OrionX's 14th semi-annual report on the state of the cryptocurrency mining market. The report focuses on Proof-of-Work cryptocurrencies since those use substantial supercomputer power to mint new coins and encode transactions on their blockchains. Only two make the cut this time, Bitcoin with $18 billion of annual economic value produced and Dogecoin with $1 billion. Bitcoin has now reached the Zettascale with typical hash rates of 0.9 Zettahashes per second. Bitcoin is powered by the world's largest decentralized supercomputer in a continuous winner take all lottery incentive network.
June Patch Tuesday



June Patch TuesdayIvanti Ivanti’s Patch Tuesday breakdown goes beyond patching your applications and brings you the intelligence and guidance needed to prioritize where to focus your attention first. Catch early analysis on our Ivanti blog, then join industry expert Chris Goettl for the Patch Tuesday Webinar Event. There we’ll do a deep dive into each of the bulletins and give guidance on the risks associated with the newly-identified vulnerabilities.
Your startup on AWS - How to architect and maintain a Lean and Mean account



Your startup on AWS - How to architect and maintain a Lean and Mean accountangelo60207 Prevent infrastructure costs from becoming a significant line item on your startup’s budget! Serial entrepreneur and software architect Angelo Mandato will share his experience with AWS Activate (startup credits from AWS) and knowledge on how to architect a lean and mean AWS account ideal for budget minded and bootstrapped startups. In this session you will learn how to manage a production ready AWS account capable of scaling as your startup grows for less than $100/month before credits. We will discuss AWS Budgets, Cost Explorer, architect priorities, and the importance of having flexible, optimized Infrastructure as Code. We will wrap everything up discussing opportunities where to save with AWS services such as S3, EC2, Load Balancers, Lambda Functions, RDS, and many others.
Mastering AI Workflows with FME - Peak of Data & AI 2025



Mastering AI Workflows with FME - Peak of Data & AI 2025Safe Software Harness the full potential of AI with FME: From creating high-quality training data to optimizing models and utilizing results, FME supports every step of your AI workflow. Seamlessly integrate a wide range of models, including those for data enhancement, forecasting, image and object recognition, and large language models. Customize AI models to meet your exact needs with FME’s powerful tools for training, optimization, and seamless integration
Edge-banding-machines-edgeteq-s-200-en-.pdf



Edge-banding-machines-edgeteq-s-200-en-.pdfAmirStern2 מכונת קנטים המתאימה לנגריות קטנות או גדולות (כמכונת גיבוי).
מדביקה קנטים מגליל או פסים, עד עובי קנט – 3 מ"מ ועובי חומר עד 40 מ"מ. בקר ממוחשב המתריע על תקלות, ומנועים מאסיביים תעשייתיים כמו במכונות הגדולות.
Viral>Wondershare Filmora 14.5.18.12900 Crack Free Download



Viral>Wondershare Filmora 14.5.18.12900 Crack Free DownloadPuppy jhon ➡ 🌍📱👉COPY & PASTE LINK👉👉👉 ➤ ➤➤ https://drfiles.net/
Wondershare Filmora Crack is a user-friendly video editing software designed for both beginners and experienced users.
Integration of Utility Data into 3D BIM Models Using a 3D Solids Modeling Wor...



Integration of Utility Data into 3D BIM Models Using a 3D Solids Modeling Wor...Safe Software Jacobs has developed a 3D utility solids modelling workflow to improve the integration of utility data into 3D Building Information Modeling (BIM) environments. This workflow, a collaborative effort between the New Zealand Geospatial Team and the Australian Data Capture Team, employs FME to convert 2D utility data into detailed 3D representations, supporting enhanced spatial analysis and clash detection.
To enable the automation of this process, Jacobs has also developed a survey data standard that standardizes the capture of existing utilities. This standard ensures consistency in data collection, forming the foundation for the subsequent automated validation and modelling steps. The workflow begins with the acquisition of utility survey data, including attributes such as location, depth, diameter, and material of utility assets like pipes and manholes. This data is validated through a custom-built tool that ensures completeness and logical consistency, including checks for proper connectivity between network components. Following validation, the data is processed using an automated modelling tool to generate 3D solids from 2D geometric representations. These solids are then integrated into BIM models to facilitate compatibility with 3D workflows and enable detailed spatial analyses.
The workflow contributes to improved spatial understanding by visualizing the relationships between utilities and other infrastructure elements. The automation of validation and modeling processes ensures consistent and accurate outputs, minimizing errors and increasing workflow efficiency.
This methodology highlights the application of FME in addressing challenges associated with geospatial data transformation and demonstrates its utility in enhancing data integration within BIM frameworks. By enabling accurate 3D representation of utility networks, the workflow supports improved design collaboration and decision-making in complex infrastructure projects
“State-space Models vs. Transformers for Ultra-low-power Edge AI,” a Presenta...



“State-space Models vs. Transformers for Ultra-low-power Edge AI,” a Presenta...Edge AI and Vision Alliance
Oracle 11g security - 2014
- 1. All About Oracle Database Security Thomas Kyte http://asktom.oracle.com/
- 2. 3 Copyright © 2010, Oracle. All rights reserved Data security remains the top priority for enterprise IT security shops with 89% of enterprises citing it as a critical or high priority. Enterprises are also continuing to focus on cutting costs and increasing efficiency. Top Priority for IT Security? Source: Forrester - The State Of Enterprise IT Security And Emerging Trends: 2009 To 2010
- 3. 4 Copyright © 2010, Oracle. All rights reserved More data than ever… Source: IDC, 2008 1,800 Exabytes Growth Doubles Yearly 2006 2011 Two Thirds of Sensitive and Regulated Data Resides in Databases…
- 4. 5 Copyright © 2010, Oracle. All rights reserved More breaches then ever… Once exposed, the data is out there – the bell can’t be un-rung PUBLICLY REPORTED DATA BREACHES Total Personally Identifying Information Records Exposed (Millions) Source: DataLossDB 0 100 200 300 400 500 600 2005 2006 2007 2008 2009 Remediation Cost Exceeds $300/record
- 5. 6 Copyright © 2010, Oracle. All rights reserved More threats than ever… Insider Fraud Is Involved in 60% of Data Breaches Source: Wall Street & Technology
- 6. © 2010 Oracle Corporation 7 • Database Vault • Label Security • Identity Management • Advanced Security • Secure Backup • Data Masking Database Security Defense In Depth Oracle Database Security Solutions • Audit Vault • Total Recall • Configuration Management Encryption & Masking Access Control Auditing • Database Firewall Monitoring & Blocking • Monitor and block threats before they reach databases • Track changes and audit database activity • Control access to data within the database • Prevent access by non database users • Remove sensitive data from non production environments
- 7. © 2010 Oracle Corporation 8 Oracle Database Firewall First Line of Defense PoliciesBuilt-in Reports Alerts Custom Reports Applications Block Log Allow Alert Substitute • Monitor database activity to prevent unauthorized database access, SQL injections, privilege or role escalation, illegal access to sensitive data, etc. • Highly accurate SQL grammar based analysis without costly false positives • Flexible SQL level enforcement options based on white lists and black lists • Scalable architecture provides enterprise performance in all deployment modes • Built-in and custom compliance reports for SOX, PCI, and other regulations
- 8. © 2010 Oracle Corporation 9 Oracle Configuration Management Secure Your Database Environment • Discover and classify databases into policy groups • Scan databases against 400+ best practices and industry standards, custom enterprise-specific configuration policies • Detect and event prevent unauthorized database configuration changes • Change management dashboards and compliance reports Monitor Configuration Management & Audit Vulnerability Management Fix Analysis & Analytics Prioritize Policy Management AssessClassify MonitorDiscover Asset Management
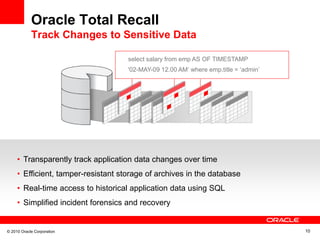
- 9. © 2010 Oracle Corporation 10 Oracle Total Recall Track Changes to Sensitive Data select salary from emp AS OF TIMESTAMP '02-MAY-09 12.00 AM‘ where emp.title = ‘admin’ • Transparently track application data changes over time • Efficient, tamper-resistant storage of archives in the database • Real-time access to historical application data using SQL • Simplified incident forensics and recovery
- 10. © 2010 Oracle Corporation 11 Oracle Audit Vault Audit Database Activity in Real-Time • Consolidate database audit trail into secure centralized repository • Detect and alert on suspicious activities, including privileged users • Out-of-the box compliance reports for SOX, PCI, and other regulations • E.g., privileged user audit, entitlements, failed logins, regulated data changes • Streamline audits with report generation, notification, attestation, archiving, etc. CRM Data ERP Data Databases HR Data Audit Data Policies Built-in Reports Alerts Custom Reports ! Auditor
- 11. © 2010 Oracle Corporation 12 Oracle Database Vault Enforce Security Policies Inside the Database • Automatic and customizable DBA separation of duties and protective realms • Enforce who, where, when, and how using rules and factors • Enforce least privilege for privileged database users • Prevent application by-pass and enforce enterprise data governance • Securely consolidate application data or enable multi-tenant data management Procurement HR Finance Application DBA select * from finance.customers DBA Security DBA Application
- 12. © 2010 Oracle Corporation 13 Disk Backups Exports Off-Site Facilities Oracle Advanced Security Protect Data from Unauthorized Users • Complete encryption for application data at rest to prevent direct access to data stored in database files, on tape, exports, etc. by IT Staff/OS users • Efficient application data encryption without application changes • Built-in two-tier key management for SoD with support for centralized key management using HSM/KMS • Strong authentication of database users for greater identity assurance Application
- 13. © 2010 Oracle Corporation 14 Oracle Data Masking Irreversibly De-Identify Data for Non-Production Use • Make application data securely available in non-production environments • Prevent application developers and testers from seeing production data • Extensible template library and policies for data masking automation • Referential integrity automatically preserved so applications continue to work • Real Application Testing friendly LAST_NAME SSN SALARY ANSKEKSL 111—23-1111 60,000 BKJHHEIEDK 222-34-1345 40,000 LAST_NAME SSN SALARY AGUILAR 203-33-3234 40,000 BENSON 323-22-2943 60,000 Production Non-Production Data never leaves Database
- 14. © 2010 Oracle Corporation 15 Oracle Database Security Solutions Defense-in-Depth for Maximum Security Activity Monitoring Database Firewall Auditing and Reporting DETECTIVE Redaction and Masking Multi-Factor Authorization Encryption PREVENTIVE ADMINISTRATIVE Data Discovery and Classification Vulnerability Scanning Database Lifecycle Management
- 15. © 2010 Oracle Corporation 16 • Database Vault • Label Security • Identity Management • Advanced Security • Secure Backup • Data Masking Oracle Database Security Solutions Complete Defense-in-Depth • Audit Vault • Total Recall • Configuration Management Encryption & Masking Access Control Auditing • Database Firewall Monitoring & Blocking • Comprehensive – single vendor addresses all your requirements • Transparent – no changes to existing applications or databases • Easy to deploy – point and click interfaces deliver value within hours • Cost Effective – integrated solutions reduce risk and lower TCO • Proven – #1 Database with over 30 years of security innovation!
- 16. © 2010 Oracle Corporation 17 Oracle Database 12c Privilege Analysis Data Redaction Auditing Encryption Advancements Code Based Access Control Invokers Rights Separation of duties
- 17. 18 Copyright © 2010, Oracle. All rights reserved For More Information oracle.com/database/security search.oracle.com or database security
- 18. 19 Copyright © 2010, Oracle. All rights reserved [email protected]
- 19. 20 Copyright © 2010, Oracle. All rights reserved
