OSV - Unit - 10 - Approaches to Virtualization
0 likes558 views
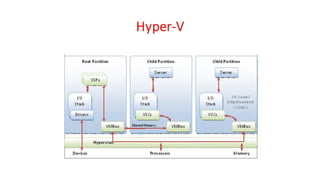
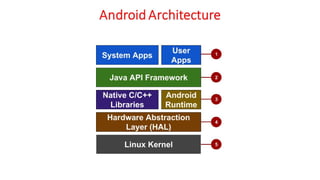
Processor Issue, Memory Management, I/O Management, VMware ESXi, Microsoft Hyper-V and Xen Variants, Java VM, Linux VServer Virtual Machine Architecture, Android Virtual Machine.
1 of 34
Downloaded 28 times
































Ad
Recommended
OSV - Unit - 5 - Deadlock



OSV - Unit - 5 - DeadlockGyanmanjari Institute Of Technology Principles of Deadlock, Starvation, Deadlock Prevention, Deadlock Avoidance, Deadlock Detection, System calls.
OSV - Unit - 6 - Memory Management



OSV - Unit - 6 - Memory ManagementGyanmanjari Institute Of Technology Memory Management requirements, Memory partitioning: Fixed and Variable Partitioning, Memory Allocation: Allocation Strategies (First Fit, Best Fit, and Worst Fit), Swapping, Paging and Fragmentation. Demand Paging, Security Issues.
Virtual Memory: Concepts, VM management, Page Replacement Policies (FIFO, LRU, Optimal, Other Strategies), Thrashing.
WD - Unit - 5 - Session and State Management using PHP



WD - Unit - 5 - Session and State Management using PHPGyanmanjari Institute Of Technology Need of session management, Various techniques for state and session management like: Hidden Fields, Query String, Cookie and Session
OSV - Unit - 9 - Virtualization Concepts



OSV - Unit - 9 - Virtualization ConceptsGyanmanjari Institute Of Technology Virtual machines; supporting multiple operating systems simultaneously on a single hardware platform; running one operating system on top of another. True or pure virtualization.
WD - Unit - 4 - PHP Basics



WD - Unit - 4 - PHP BasicsGyanmanjari Institute Of Technology Introduction to Server side programming , PHP variables, decision and looping with examples, PHP and HTML, Arrays, Functions, Browser control and detection, String, Form processing, File uploads, Dates and timezone, Working with Regular Expressions, Exception Handling, Working with JSON data, Object Oriented Programming with PHP
OSV - Unit - 2 - Process and Threads Management



OSV - Unit - 2 - Process and Threads ManagementGyanmanjari Institute Of Technology Process and Threads Management: Process Concept, Process states, Process control, Threads, Uni-processor Scheduling: Types of scheduling: Preemptive, Non preemptive, Scheduling algorithms: FCFS, SJF, RR, Priority, Thread Scheduling, Real Time Scheduling. System calls like ps, fork, join, exec family, wait.
WD - Unit - 3 - Java Script



WD - Unit - 3 - Java ScriptGyanmanjari Institute Of Technology Javascript Syntax, Types of Javascript, variables, arrays, functions, conditions, loops, Pop up boxes, Javascript objects and DOM, Javascript inbuilt functions, Javascript validations, Regular expressions, Event handling with Javascript, Callbacks in Javascript, Function as arguments in Javascript, Object concepts in Javascript
Cyber Security - Unit - 4 - Introduction to Cyber Crime and law Cyber Crimes



Cyber Security - Unit - 4 - Introduction to Cyber Crime and law Cyber CrimesGyanmanjari Institute Of Technology Introduction to Cyber Crime and law Cyber Crimes, Types of Cybercrime, Hacking, Attack vectors, Cyberspace and Criminal Behavior, Clarification of Terms, Traditional Problems Associated with Computer Crime, Introduction to Incident Response, Digital Forensics, Realms of the Cyber world, Recognizing and Defining Computer Crime, Contemporary Crimes, Contaminants and Destruction of Data, Indian IT ACT 2000.
WD - Unit - 2 - HTML & CSS



WD - Unit - 2 - HTML & CSSGyanmanjari Institute Of Technology The document discusses the benefits of exercise for both physical and mental health. It notes that regular exercise can reduce the risk of diseases like heart disease and diabetes, improve mood, and reduce feelings of stress and anxiety. The document recommends that adults get at least 150 minutes of moderate exercise per week or 75 minutes of vigorous exercise per week to experience these benefits.
Monthly Khazina-e-Ruhaniyaat June'23 (Vol.14, Issue 2)



Monthly Khazina-e-Ruhaniyaat June'23 (Vol.14, Issue 2)Darul Amal Chishtia 2nd issue of Volume 14. A magazine in urdu language mainly based on spiritual treatment and learning. Many topics on ISLAM, SUFISM, SOCIAL PROBLEMS, SELF HELP, PSYCHOLOGY, HEALTH, SPIRITUAL TREATMENT, Ruqya etc. A very useful magazine for everyone.
WD - Unit - 7 - Advanced Concepts



WD - Unit - 7 - Advanced ConceptsGyanmanjari Institute Of Technology Asynchronous Web requests using AJAX, Creating REST API using PHP
jQuery: Working with jQuery, Using plugins in jQuery and Creating Image slider, Generating charts from data using 3rd Party Libs
Modelo de trazabilidad guiado por base de datos



Modelo de trazabilidad guiado por base de datosGiovani Ramirez En los tiempos que corren, cada vez con mayor frecuencia, se hace necesario conocer la trazabilidad de los datos. Las razones que empujan a las empresas a contar con esta necesidad a la hora de planificar la gestión de datos en proyectos de Data Warehouse no son sólo de prevención o para asegurarse una fácil localización de errores que simplifique su corrección, sino que también tienen mucho que ver con las normativas legales, que empiezan a proliferar en este entorno, y que exigen controlar y conocer la trazabilidad de los datos.
Cyber Security - Unit - 1 - Systems Vulnerability Scanning Overview of Vulner...



Cyber Security - Unit - 1 - Systems Vulnerability Scanning Overview of Vulner...Gyanmanjari Institute Of Technology Systems Vulnerability Scanning Overview of vulnerability scanning, Open Port / Service Identification, Banner / Version Check, Traffic Probe, Vulnerability Probe, Vulnerability Examples, OpenVAS, Metasploit. Networks Vulnerability Scanning - Netcat, Socat, understanding Port and Services tools - Datapipe, Fpipe, WinRelay, Network Reconnaissance – Nmap, THC-Amap and System tools. Network Sniffers and Injection tools – Tcpdump and Windump, Wireshark, Ettercap, Hping Kismet.
Zagor Ludens 110 - Verakruz



Zagor Ludens 110 - VerakruzStripovizijacom The document discusses the importance of summarization for processing large amounts of text data. Automatic summarization systems aim to generate concise summaries by identifying the most important concepts and ideas within source texts. However, accurately summarizing texts remains a challenging task that current systems cannot fully achieve at a human level.
OSV - Unit - 3 - Concurrency



OSV - Unit - 3 - ConcurrencyGyanmanjari Institute Of Technology Concurrency: Principles of Concurrency, Mutual Exclusion: S/W approaches, H/W Support, Semaphores, Pipes, Message Passing, Signals, and Monitors.
DBMS Unit - 2 - Data Models



DBMS Unit - 2 - Data ModelsGyanmanjari Institute Of Technology Entity-relationship model, network model, relational and object oriented data models, integrity constraints, data manipulation operations.
Zagor vc 144 - Plamen nad Merivelom



Zagor vc 144 - Plamen nad MerivelomStripovizijacom The document discusses the benefits of exercise for mental health. It notes that regular physical activity can help reduce anxiety and depression and improve mood and cognitive function. Exercise has also been shown to enhance self-esteem and serve as a healthy means of stress management.
Python Programming ADP VTU CSE 18CS55 Module 3 Chapter 8 - A



Python Programming ADP VTU CSE 18CS55 Module 3 Chapter 8 - ADemian Antony DMello Slides contain basics of python programming: Files, Terminology, path, folders, traversal, Programming examples and Demonstrations.
Cyber Security - Unit - 3 - Web Application Tools Scanning for web vulnerabil...



Cyber Security - Unit - 3 - Web Application Tools Scanning for web vulnerabil...Gyanmanjari Institute Of Technology Web Application Tools Scanning for web vulnerabilities tools: Nikto, W3af, HTTP utilities - Curl, OpenSSL and Stunnel, Application Inspection tools – Zed Attack Proxy, Sqlmap. DVWA, Webgoat, Password Cracking and Brute-Force Tools – John the Ripper, L0htcrack, Pwdump, HTC-Hydra
WD - Unit - 1 - Introduction



WD - Unit - 1 - IntroductionGyanmanjari Institute Of Technology Basics of WWW, HTTP protocol methods and headers, HTTP Request and Response, Architecture of web browser, Web server installation and configuration, Web security, CORS, Understanding SEO
OSV - Unit - 1 - Introduction



OSV - Unit - 1 - IntroductionGyanmanjari Institute Of Technology Computer system overview, Architecture, Goals & Structures of
O.S, Basic functions, Interaction of O.S. & hardware architecture, System calls,
Batch, multiprogramming. Multitasking, time sharing, parallel, distributed & realtime
O.S.
Unit - 5 - Advance Web Designing (AJAX & jQuery)



Unit - 5 - Advance Web Designing (AJAX & jQuery)Gyanmanjari Institute Of Technology AJAX: Understanding the concept of AJAX and its importance in web development, XMLHttpRequest Object, Methods and Properties.
jQuery: Working with jQuery, using plugins in jQuery and
Creating Image slider, generating charts from data using 3rd Party
Libs.
Unit - 4 - Bootstrap (HTML, CSS, and JavaScript Framework)



Unit - 4 - Bootstrap (HTML, CSS, and JavaScript Framework)Gyanmanjari Institute Of Technology Introduction to bootstrap, download and load bootstrap,
Typography, Images, Figures, Tables, Container, Break point,
Grid System, Designing Forms, Components of Bootstrap, Helper classes in Bootstrap, Utilities in Bootstrap, Loading Icon library like font-awsome, SVG icons.
Ad
More Related Content
What's hot (20)
Cyber Security - Unit - 4 - Introduction to Cyber Crime and law Cyber Crimes



Cyber Security - Unit - 4 - Introduction to Cyber Crime and law Cyber CrimesGyanmanjari Institute Of Technology Introduction to Cyber Crime and law Cyber Crimes, Types of Cybercrime, Hacking, Attack vectors, Cyberspace and Criminal Behavior, Clarification of Terms, Traditional Problems Associated with Computer Crime, Introduction to Incident Response, Digital Forensics, Realms of the Cyber world, Recognizing and Defining Computer Crime, Contemporary Crimes, Contaminants and Destruction of Data, Indian IT ACT 2000.
WD - Unit - 2 - HTML & CSS



WD - Unit - 2 - HTML & CSSGyanmanjari Institute Of Technology The document discusses the benefits of exercise for both physical and mental health. It notes that regular exercise can reduce the risk of diseases like heart disease and diabetes, improve mood, and reduce feelings of stress and anxiety. The document recommends that adults get at least 150 minutes of moderate exercise per week or 75 minutes of vigorous exercise per week to experience these benefits.
Monthly Khazina-e-Ruhaniyaat June'23 (Vol.14, Issue 2)



Monthly Khazina-e-Ruhaniyaat June'23 (Vol.14, Issue 2)Darul Amal Chishtia 2nd issue of Volume 14. A magazine in urdu language mainly based on spiritual treatment and learning. Many topics on ISLAM, SUFISM, SOCIAL PROBLEMS, SELF HELP, PSYCHOLOGY, HEALTH, SPIRITUAL TREATMENT, Ruqya etc. A very useful magazine for everyone.
WD - Unit - 7 - Advanced Concepts



WD - Unit - 7 - Advanced ConceptsGyanmanjari Institute Of Technology Asynchronous Web requests using AJAX, Creating REST API using PHP
jQuery: Working with jQuery, Using plugins in jQuery and Creating Image slider, Generating charts from data using 3rd Party Libs
Modelo de trazabilidad guiado por base de datos



Modelo de trazabilidad guiado por base de datosGiovani Ramirez En los tiempos que corren, cada vez con mayor frecuencia, se hace necesario conocer la trazabilidad de los datos. Las razones que empujan a las empresas a contar con esta necesidad a la hora de planificar la gestión de datos en proyectos de Data Warehouse no son sólo de prevención o para asegurarse una fácil localización de errores que simplifique su corrección, sino que también tienen mucho que ver con las normativas legales, que empiezan a proliferar en este entorno, y que exigen controlar y conocer la trazabilidad de los datos.
Cyber Security - Unit - 1 - Systems Vulnerability Scanning Overview of Vulner...



Cyber Security - Unit - 1 - Systems Vulnerability Scanning Overview of Vulner...Gyanmanjari Institute Of Technology Systems Vulnerability Scanning Overview of vulnerability scanning, Open Port / Service Identification, Banner / Version Check, Traffic Probe, Vulnerability Probe, Vulnerability Examples, OpenVAS, Metasploit. Networks Vulnerability Scanning - Netcat, Socat, understanding Port and Services tools - Datapipe, Fpipe, WinRelay, Network Reconnaissance – Nmap, THC-Amap and System tools. Network Sniffers and Injection tools – Tcpdump and Windump, Wireshark, Ettercap, Hping Kismet.
Zagor Ludens 110 - Verakruz



Zagor Ludens 110 - VerakruzStripovizijacom The document discusses the importance of summarization for processing large amounts of text data. Automatic summarization systems aim to generate concise summaries by identifying the most important concepts and ideas within source texts. However, accurately summarizing texts remains a challenging task that current systems cannot fully achieve at a human level.
OSV - Unit - 3 - Concurrency



OSV - Unit - 3 - ConcurrencyGyanmanjari Institute Of Technology Concurrency: Principles of Concurrency, Mutual Exclusion: S/W approaches, H/W Support, Semaphores, Pipes, Message Passing, Signals, and Monitors.
DBMS Unit - 2 - Data Models



DBMS Unit - 2 - Data ModelsGyanmanjari Institute Of Technology Entity-relationship model, network model, relational and object oriented data models, integrity constraints, data manipulation operations.
Zagor vc 144 - Plamen nad Merivelom



Zagor vc 144 - Plamen nad MerivelomStripovizijacom The document discusses the benefits of exercise for mental health. It notes that regular physical activity can help reduce anxiety and depression and improve mood and cognitive function. Exercise has also been shown to enhance self-esteem and serve as a healthy means of stress management.
Python Programming ADP VTU CSE 18CS55 Module 3 Chapter 8 - A



Python Programming ADP VTU CSE 18CS55 Module 3 Chapter 8 - ADemian Antony DMello Slides contain basics of python programming: Files, Terminology, path, folders, traversal, Programming examples and Demonstrations.
Cyber Security - Unit - 3 - Web Application Tools Scanning for web vulnerabil...



Cyber Security - Unit - 3 - Web Application Tools Scanning for web vulnerabil...Gyanmanjari Institute Of Technology Web Application Tools Scanning for web vulnerabilities tools: Nikto, W3af, HTTP utilities - Curl, OpenSSL and Stunnel, Application Inspection tools – Zed Attack Proxy, Sqlmap. DVWA, Webgoat, Password Cracking and Brute-Force Tools – John the Ripper, L0htcrack, Pwdump, HTC-Hydra
WD - Unit - 1 - Introduction



WD - Unit - 1 - IntroductionGyanmanjari Institute Of Technology Basics of WWW, HTTP protocol methods and headers, HTTP Request and Response, Architecture of web browser, Web server installation and configuration, Web security, CORS, Understanding SEO
OSV - Unit - 1 - Introduction



OSV - Unit - 1 - IntroductionGyanmanjari Institute Of Technology Computer system overview, Architecture, Goals & Structures of
O.S, Basic functions, Interaction of O.S. & hardware architecture, System calls,
Batch, multiprogramming. Multitasking, time sharing, parallel, distributed & realtime
O.S.
Cyber Security - Unit - 4 - Introduction to Cyber Crime and law Cyber Crimes



Cyber Security - Unit - 4 - Introduction to Cyber Crime and law Cyber CrimesGyanmanjari Institute Of Technology
Cyber Security - Unit - 1 - Systems Vulnerability Scanning Overview of Vulner...



Cyber Security - Unit - 1 - Systems Vulnerability Scanning Overview of Vulner...Gyanmanjari Institute Of Technology
Cyber Security - Unit - 3 - Web Application Tools Scanning for web vulnerabil...



Cyber Security - Unit - 3 - Web Application Tools Scanning for web vulnerabil...Gyanmanjari Institute Of Technology
More from Gyanmanjari Institute Of Technology (18)
Unit - 5 - Advance Web Designing (AJAX & jQuery)



Unit - 5 - Advance Web Designing (AJAX & jQuery)Gyanmanjari Institute Of Technology AJAX: Understanding the concept of AJAX and its importance in web development, XMLHttpRequest Object, Methods and Properties.
jQuery: Working with jQuery, using plugins in jQuery and
Creating Image slider, generating charts from data using 3rd Party
Libs.
Unit - 4 - Bootstrap (HTML, CSS, and JavaScript Framework)



Unit - 4 - Bootstrap (HTML, CSS, and JavaScript Framework)Gyanmanjari Institute Of Technology Introduction to bootstrap, download and load bootstrap,
Typography, Images, Figures, Tables, Container, Break point,
Grid System, Designing Forms, Components of Bootstrap, Helper classes in Bootstrap, Utilities in Bootstrap, Loading Icon library like font-awsome, SVG icons.
Unit -3 - JavaScript (Client Side Scripting Language)



Unit -3 - JavaScript (Client Side Scripting Language)Gyanmanjari Institute Of Technology JavaScript Syntax, Types of JavaScript, variables, arrays, functions, conditions, loops, Pop up boxes, JavaScript objects and DOM, JavaScript inbuilt functions, JavaScript validations, Regular expressions, Event handling with JavaScript, Callbacks in JavaScript, Function as arguments in JavaScript.
Unit - 2 - Hypertext Markup Language & Cascading Style Sheets



Unit - 2 - Hypertext Markup Language & Cascading Style SheetsGyanmanjari Institute Of Technology HTML: HTML page structure, Basic HTML tags like heading, formatting tags paragraph, formatting text, organizing text, list, anchor, images, HTML tables, HTML forms, meta tags, multimedia tags, links, frames, HTML5 tags in relation to validations.
CSS: Introduction to CSS, Basic Syntax and structure of CSS, Need for CSS, Types of CSS, Background Properties, manipulating text and font, The Box Model, styling list, CSS Positioning, Colors and properties, borders and boxes, Margins, Padding Lists, CSS2, CSS3, Animations, Tool-Tips, Style images, Variables, Flex Box, Media Queries, Working with Gradients.
Unit - 1 - Introduction to Web Design



Unit - 1 - Introduction to Web DesignGyanmanjari Institute Of Technology Internet and Web, HTTP Protocol, Architecture of web browser, Introduction to Web Technologies, HTML, CSS, Java Script, Bootstrap, Concepts of effective web design, Web design issues, Designing effective navigation. fundamental of web
page, static and dynamic website design.
WD - Unit - 6 - Database Connectivity using PHP



WD - Unit - 6 - Database Connectivity using PHPGyanmanjari Institute Of Technology Basic commands for database connection and query execution with CURD examples, Object oriented database access using PHP
OSV - Unit - 8 - Unix/Linux Operating System



OSV - Unit - 8 - Unix/Linux Operating SystemGyanmanjari Institute Of Technology Development Of Unix/Linux, Role & Function Of Kernel, System Calls, Elementary Linux command & Shell Programming, Directory Structure, System Administration
Case study: Linux, Windows Operating System
OSV - Unit - 7 - I/O Management & Disk scheduling



OSV - Unit - 7 - I/O Management & Disk schedulingGyanmanjari Institute Of Technology I/O Devices, Organization of I/O functions, Operating System Design issues, I/O
Buffering, Disk Scheduling (FCFS, SCAN, C-SCAN, SSTF), RAID, Disk
Cache
CNS - Unit - 10 - Web Security Threats and Approaches



CNS - Unit - 10 - Web Security Threats and ApproachesGyanmanjari Institute Of Technology Web Security threats and approaches, SSL architecture and protocol, Transport layer security, HTTPS and SSH
OSV - Unit - 4 - Inter Process Communication



OSV - Unit - 4 - Inter Process CommunicationGyanmanjari Institute Of Technology Inter Process Communication:
Race Conditions, Critical Section, Mutual Exclusion, Hardware Solution, Strict Alternation, Peterson’s Solution, The Producer Consumer Problem, Semaphores, Event Counters, Monitors, Message Passing, Classical IPC Problems: Reader’s & Writer Problem, Dinning Philosopher Problem etc., Scheduling, Scheduling Algorithms.
CNS - Unit - 8 - Key Management and Distribution



CNS - Unit - 8 - Key Management and DistributionGyanmanjari Institute Of Technology Key management and distribution, symmetric key distribution using symmetric and asymmetric encryptions, distribution of public keys, X.509 certificates, Public key infrastructure
CNS - Unit - 7 - Digital Signature



CNS - Unit - 7 - Digital SignatureGyanmanjari Institute Of Technology Digital Signature, its properties, requirements and security, various digital signature schemes (Elgamal and Schnorr), NIST digital Signature algorithm
CNS - Unit - 6 - Message Authentication Code



CNS - Unit - 6 - Message Authentication CodeGyanmanjari Institute Of Technology Message Authentication Codes, its requirements and security, MACs based on Hash Functions, Macs based on Block Ciphers
CNS - Unit - 5 - Cryptographic Hash Functions



CNS - Unit - 5 - Cryptographic Hash FunctionsGyanmanjari Institute Of Technology Cryptographic Hash Functions, their applications, Simple hash functions, its requirements and security, Hash functions based on Cipher Block Chaining, Secure Hash Algorithm (SHA)
CNS - Unit - 4 - Public Key Cryptosystem 



CNS - Unit - 4 - Public Key Cryptosystem Gyanmanjari Institute Of Technology Public Key Cryptosystems with Applications, Requirements and
Cryptanalysis, RSA algorithm, its computational aspects and security, Diffie-Hillman Key Exchange algorithm, Man-in-Middle attack
CNS - Unit - 3 - Block Cipher Mode



CNS - Unit - 3 - Block Cipher ModeGyanmanjari Institute Of Technology Multiple encryption and triple DES, Electronic Code Book, Cipher Block Chaining Mode, Cipher Feedback mode, Output Feedback mode, Counter mode
CNS - Unit - 2 - Stream Ciphers and Block Ciphers



CNS - Unit - 2 - Stream Ciphers and Block CiphersGyanmanjari Institute Of Technology Stream ciphers and block ciphers, Block Cipher structure, Data Encryption standard (DES) with example, strength of DES, Design principles of block cipher, AES with structure, its transformation functions, key expansion, example and implementation
CNS - Unit - 1 - Introduction



CNS - Unit - 1 - IntroductionGyanmanjari Institute Of Technology Security services, security services, security mechanisms
Finite fields – group, ring, fields, modular arithmetic, The Euclidean algorithm.Symmetric Cipher Model, Cryptography, Cryptanalysis and Attacks; Substitution and Transposition techniques
Ad
Recently uploaded (20)
some basics electrical and electronics knowledge



some basics electrical and electronics knowledgenguyentrungdo88 This chapter discribe about common electrical divices such as passive component, the internaltional system unit and international system prefixes.
Data Structures_Searching and Sorting.pptx



Data Structures_Searching and Sorting.pptxRushaliDeshmukh2 Sorting Order and Stability in Sorting.
Concept of Internal and External Sorting.
Bubble Sort,
Insertion Sort,
Selection Sort,
Quick Sort and
Merge Sort,
Radix Sort, and
Shell Sort,
External Sorting, Time complexity analysis of Sorting Algorithms.
The Gaussian Process Modeling Module in UQLab



The Gaussian Process Modeling Module in UQLabJournal of Soft Computing in Civil Engineering We introduce the Gaussian process (GP) modeling module developed within the UQLab software framework. The novel design of the GP-module aims at providing seamless integration of GP modeling into any uncertainty quantification workflow, as well as a standalone surrogate modeling tool. We first briefly present the key mathematical tools on the basis of GP modeling (a.k.a. Kriging), as well as the associated theoretical and computational framework. We then provide an extensive overview of the available features of the software and demonstrate its flexibility and user-friendliness. Finally, we showcase the usage and the performance of the software on several applications borrowed from different fields of engineering. These include a basic surrogate of a well-known analytical benchmark function; a hierarchical Kriging example applied to wind turbine aero-servo-elastic simulations and a more complex geotechnical example that requires a non-stationary, user-defined correlation function. The GP-module, like the rest of the scientific code that is shipped with UQLab, is open source (BSD license).
Raish Khanji GTU 8th sem Internship Report.pdf



Raish Khanji GTU 8th sem Internship Report.pdfRaishKhanji This report details the practical experiences gained during an internship at Indo German Tool
Room, Ahmedabad. The internship provided hands-on training in various manufacturing technologies, encompassing both conventional and advanced techniques. Significant emphasis was placed on machining processes, including operation and fundamental
understanding of lathe and milling machines. Furthermore, the internship incorporated
modern welding technology, notably through the application of an Augmented Reality (AR)
simulator, offering a safe and effective environment for skill development. Exposure to
industrial automation was achieved through practical exercises in Programmable Logic Controllers (PLCs) using Siemens TIA software and direct operation of industrial robots
utilizing teach pendants. The principles and practical aspects of Computer Numerical Control
(CNC) technology were also explored. Complementing these manufacturing processes, the
internship included extensive application of SolidWorks software for design and modeling tasks. This comprehensive practical training has provided a foundational understanding of
key aspects of modern manufacturing and design, enhancing the technical proficiency and readiness for future engineering endeavors.
Avnet Silica's PCIM 2025 Highlights Flyer



Avnet Silica's PCIM 2025 Highlights FlyerWillDavies22 See what you can expect to find on Avnet Silica's stand at PCIM 2025.
Fort night presentation new0903 pdf.pdf.



Fort night presentation new0903 pdf.pdf.anuragmk56 This is the document of fortnight review progress meeting
AI-assisted Software Testing (3-hours tutorial)



AI-assisted Software Testing (3-hours tutorial)Vəhid Gəruslu Invited tutorial at the Istanbul Software Testing Conference (ISTC) 2025 https://iststc.com/
ELectronics Boards & Product Testing_Shiju.pdf



ELectronics Boards & Product Testing_Shiju.pdfShiju Jacob This presentation provides a high level insight about DFT analysis and test coverage calculation, finalizing test strategy, and types of tests at different levels of the product.
fluke dealers in bangalore..............



fluke dealers in bangalore..............Haresh Vaswani The Fluke 925 is a vane anemometer, a handheld device designed to measure wind speed, air flow (volume), and temperature. It features a separate sensor and display unit, allowing greater flexibility and ease of use in tight or hard-to-reach spaces. The Fluke 925 is particularly suitable for HVAC (heating, ventilation, and air conditioning) maintenance in both residential and commercial buildings, offering a durable and cost-effective solution for routine airflow diagnostics.
Artificial Intelligence (AI) basics.pptx



Artificial Intelligence (AI) basics.pptxaditichinar its all about Artificial Intelligence(Ai) and Machine Learning and not on advanced level you can study before the exam or can check for some information on Ai for project
"Boiler Feed Pump (BFP): Working, Applications, Advantages, and Limitations E...



"Boiler Feed Pump (BFP): Working, Applications, Advantages, and Limitations E...Infopitaara A Boiler Feed Pump (BFP) is a critical component in thermal power plants. It supplies high-pressure water (feedwater) to the boiler, ensuring continuous steam generation.
⚙️ How a Boiler Feed Pump Works
Water Collection:
Feedwater is collected from the deaerator or feedwater tank.
Pressurization:
The pump increases water pressure using multiple impellers/stages in centrifugal types.
Discharge to Boiler:
Pressurized water is then supplied to the boiler drum or economizer section, depending on design.
🌀 Types of Boiler Feed Pumps
Centrifugal Pumps (most common):
Multistage for higher pressure.
Used in large thermal power stations.
Positive Displacement Pumps (less common):
For smaller or specific applications.
Precise flow control but less efficient for large volumes.
🛠️ Key Operations and Controls
Recirculation Line: Protects the pump from overheating at low flow.
Throttle Valve: Regulates flow based on boiler demand.
Control System: Often automated via DCS/PLC for variable load conditions.
Sealing & Cooling Systems: Prevent leakage and maintain pump health.
⚠️ Common BFP Issues
Cavitation due to low NPSH (Net Positive Suction Head).
Seal or bearing failure.
Overheating from improper flow or recirculation.
DT REPORT by Tech titan GROUP to introduce the subject design Thinking



DT REPORT by Tech titan GROUP to introduce the subject design ThinkingDhruvChotaliya2 This a Report of a Design Thinking
Development of MLR, ANN and ANFIS Models for Estimation of PCUs at Different ...



Development of MLR, ANN and ANFIS Models for Estimation of PCUs at Different ...Journal of Soft Computing in Civil Engineering Passenger car unit (PCU) of a vehicle type depends on vehicular characteristics, stream characteristics, roadway characteristics, environmental factors, climate conditions and control conditions. Keeping in view various factors affecting PCU, a model was developed taking a volume to capacity ratio and percentage share of particular vehicle type as independent parameters. A microscopic traffic simulation model VISSIM has been used in present study for generating traffic flow data which some time very difficult to obtain from field survey. A comparison study was carried out with the purpose of verifying when the adaptive neuro-fuzzy inference system (ANFIS), artificial neural network (ANN) and multiple linear regression (MLR) models are appropriate for prediction of PCUs of different vehicle types. From the results observed that ANFIS model estimates were closer to the corresponding simulated PCU values compared to MLR and ANN models. It is concluded that the ANFIS model showed greater potential in predicting PCUs from v/c ratio and proportional share for all type of vehicles whereas MLR and ANN models did not perform well.
Development of MLR, ANN and ANFIS Models for Estimation of PCUs at Different ...



Development of MLR, ANN and ANFIS Models for Estimation of PCUs at Different ...Journal of Soft Computing in Civil Engineering
Ad














