Overview of computer
Download as PPTX, PDF2 likes736 views
types of generations, hardware and software,fundamentals of operating systems,dbms,internet applications,www,embedded software.
1 of 43
Downloaded 24 times








































Ad
Recommended
Data Modeling for NoSQL



Data Modeling for NoSQLTony Tam - Data modeling for NoSQL databases is different than relational databases and requires designing the data model around access patterns rather than object structure. Key differences include not having joins so data needs to be duplicated and modeling the data in a way that works for querying, indexing, and retrieval speed.
- The data model should focus on making the most of features like atomic updates, inner indexes, and unique identifiers. It's also important to consider how data will be added, modified, and retrieved factoring in object complexity, marshalling/unmarshalling costs, and index maintenance.
- The _id field can be tailored to the access patterns, such as using dates for time-series data to keep recent
Processing Crimes and Incident Scenes



Processing Crimes and Incident Scenesprimeteacher32 The document discusses best practices for processing crime and incident scenes involving digital evidence. It outlines general tasks investigators perform, including identifying digital artifacts as evidence, collecting and preserving evidence, analyzing and organizing it, and reproducing results reliably. It emphasizes the importance of collecting evidence systematically and in compliance with relevant rules and standards to ensure the authenticity and credibility of the evidence.
Geolocation and Mapping



Geolocation and MappingIvano Malavolta This document provides an overview of geolocation and mapping using Google Maps services. It defines geolocation as identifying the real-world location of an object like a mobile phone or computer. Mapping refers to map-making and cartography. The document reviews the navigator.geolocation API for accessing location data, the Google Maps Javascript API for embedding maps, and common overlays like markers and polylines that can be added to maps. It also summarizes services for obtaining directions and distance matrix information between locations.
Object Relational Database Management System



Object Relational Database Management SystemAmar Myana PostgreSQL is an object-relational database management system (ORDBMS) that is cross-platform and implements the majority of the SQL:2011 standard. It uses a client-server model with a postmaster daemon process that manages connections to backend server processes. PostgreSQL supports features like ACID compliance, transactions, complex queries, user-defined objects, and built-in replication. It allows custom indexing and inheritance between tables. To get started, users can create databases and tables, populate them with data, and perform queries.
Linux process management



Linux process managementRaghu nath The document discusses key concepts related to process management in Linux, including process lifecycle, states, memory segments, scheduling, and priorities. It explains that a process goes through creation, execution, termination, and removal phases repeatedly. Process states include running, stopped, interruptible, uninterruptible, and zombie. Process memory is made up of text, data, BSS, heap, and stack segments. Linux uses a O(1) CPU scheduling algorithm that scales well with process and processor counts.
Semantic Technologies for Big Data



Semantic Technologies for Big DataMarin Dimitrov This document summarizes a presentation about semantic technologies for big data. It discusses how semantic technologies can help address challenges related to the volume, velocity, and variety of big data. Specific examples are provided of large semantic datasets containing billions of triples and semantic applications that have integrated and analyzed disparate data sources. Semantic technologies are presented as a good fit for addressing big data's variety, and research is making progress in applying them to velocity and volume as well.
Class based modeling



Class based modelingMd. Shafiuzzaman Hira The document discusses class identification for a system. It identifies potential classes like homeowner, sensor, control panel, system, and sensor event by examining nouns in use cases. It then evaluates the potential classes against characteristics like retained information, needed services, and common attributes to determine which should be defined as classes in a requirements model. The security system, sensor, control panel, and sensor event classes are selected as they meet the evaluated characteristics.
Cloud Architectures - Jinesh Varia - GrepTheWeb



Cloud Architectures - Jinesh Varia - GrepTheWebjineshvaria - Cloud computing platforms like Amazon Web Services allow companies to focus on innovation rather than infrastructure maintenance by providing scalable, pay-as-you-go cloud services.
- Amazon's cloud services like EC2, S3, and SQS were used to build GrepTheWeb, a distributed text search service that can quickly search very large datasets by distributing work across elastic compute resources.
- GrepTheWeb coordinates distributed processing using SQS, stores input files in S3, runs jobs on EC2 instances, and stores results in SimpleDB to provide fast, scalable text searches without having to manage physical infrastructure.
Marco juridico de la educacion tecnica de Nicaragua.pptx



Marco juridico de la educacion tecnica de Nicaragua.pptxfrankjhellrayo1 Este documento resume el marco jurídico de la educación técnica en Nicaragua, incluyendo la Declaración Universal de los Derechos Humanos, la Constitución Política de Nicaragua, la Ley General de Educación, la Ley de Carrera Docente, y artículos relacionados con los ejes del Plan Nacional de Desarrollo Humano. También describe brevemente la nueva Ley Reguladora del Instituto Nacional Tecnológico.
Database programming



Database programmingShree M.L.Kakadiya MCA mahila college, Amreli This document discusses Python database programming. It introduces databases and how they store data in tables connected through columns. It discusses SQL for creating, accessing, and manipulating database data. It then discusses how Python supports various databases and database operations. It covers the Python DB-API for providing a standard interface for database programming. It provides examples of connecting to a database, executing queries, and retrieving and inserting data.
Operating Systems 1 (7/12) - Threads



Operating Systems 1 (7/12) - ThreadsPeter Tröger The document discusses processes and threads in operating systems. It describes how processes contain multiple threads that can run concurrently on multicore systems. Each thread has its own execution state and context stored in a thread control block. When a thread is not actively running, its context is saved so it can resume execution later. The document provides examples of how threads are implemented in Windows and Linux operating systems.
Multimedia database



Multimedia databaseRashmi Agale This document discusses multimedia databases. A multimedia database is a collection of related multimedia data managed by a multimedia database management system. It supports different data types and allows for creation, storage, access, querying and control of multimedia data. Key components include a query interface, query processing, indexing, buffer management and storage management. Challenges include large storage needs, processing time requirements, and temporal properties of some multimedia data types. Application areas mentioned are digital libraries, news on demand, video on demand, and music databases.
OPERATING SYSTEM SERVICES, OPERATING SYSTEM STRUCTURES



OPERATING SYSTEM SERVICES, OPERATING SYSTEM STRUCTURESpriyasoundar These slides will help the engineering students for understanding the functionalities of operating system and its structure. Also it will help them for their exam preparation.
CS6401 OPERATING SYSTEMS Unit 2



CS6401 OPERATING SYSTEMS Unit 2Kathirvel Ayyaswamy UNIT II PROCESS MANAGEMENT
Processes-Process Concept, Process Scheduling, Operations on Processes, Interprocess Communication; Threads- Overview, Multicore Programming, Multithreading Models; Windows 7 - Thread and SMP Management. Process Synchronization - Critical Section Problem, Mutex Locks, Semophores, Monitors; CPU Scheduling and Deadlocks.
Diagrama fisico



Diagrama fisicoCarlo Gaso El documento describe la creación de una base de datos para una inmobiliaria utilizando MySQL Workbench. Se crean tablas como Inmueble, Propietario, Cliente y otras utilizando sentencias SQL que definen los campos y claves primarias de cada tabla. Las tablas se relacionan entre sí a través de claves externas para almacenar información sobre propiedades inmobiliarias.
Computer Forensics: First Responder Training - Eric Vanderburg - JurInnov



Computer Forensics: First Responder Training - Eric Vanderburg - JurInnovEric Vanderburg This document provides an overview of a three-day computer forensics training hosted by JurInnov Ltd. It introduces the trainers and covers topics including understanding computing environments, collecting electronically stored information, forensic analysis demonstrations, and types of cases where computer forensics are useful. The document outlines concepts like what computer forensics is, sources of electronically stored information, reasons for using computer forensics, how computers operate, and methods for collecting, imaging, and analyzing various types of digital evidence from computers, networks, phones and other devices.
Multimedia db system



Multimedia db systemYojana Nanaware This document provides an overview of multimedia database management systems (MDBMS). It discusses that MDBMS can manage different types of multimedia data, including images, video, audio and more. The key tasks of a MDBMS include organizing, classifying, querying and supporting operations on multimedia data while enforcing data independence and integrity. MDBMS architectures typically feature three layers - an interface layer, an object composition layer to manage multimedia objects, and a storage layer for clustering and indexing multimedia data.
OS Unit 5 - Memory Management



OS Unit 5 - Memory ManagementGyanmanjari Institute Of Technology Basic Memory Management
Introduction
Logical and Physical address map
Memory allocation
Contiguous Memory allocation
Fixed and variable partition
Internal and External fragmentation and Compaction
Paging
Principle of operation
Page allocation
Hardware support for paging
Protection and sharing
Disadvantages of paging
Virtual Memory
Basics of Virtual Memory
Hardware and control structures
Locality of reference
Page fault
Working Set
Dirty page/Dirty bit
Demand paging
Page Replacement policies
Optimal (OPT)
First in First Out (FIFO)
Second Chance (SC)
Not recently used (NRU)
Least Recently used (LRU)
Files concepts.53



Files concepts.53myrajendra The document discusses file concepts, file management, and file attributes. It defines a file as a named collection of related information recorded on secondary storage. It describes different types of files including program files, data files, and their various structures. The document also discusses common file operations and types.
Run time storage



Run time storageRasineni Madhan Mohan Naidu The document discusses run-time environments in compiler design. It provides details about storage organization and allocation strategies at run-time. Storage is allocated either statically at compile-time, dynamically from the heap, or from the stack. The stack is used to store procedure activations by pushing activation records when procedures are called and popping them on return. Activation records contain information for each procedure call like local variables, parameters, and return values.
01-Database Administration and Management.pdf



01-Database Administration and Management.pdfTOUSEEQHAIDER14 This document provides an introduction and overview of database systems. It discusses the purpose of database systems in addressing issues with file-based data storage like data redundancy, inconsistent data, and difficulty of data access. It also describes database applications, data models, database languages like SQL, database design, database architecture, and the major components of a database system including the storage manager, query processor, and transaction manager.
Herramientas de arquitectura de informacion resumen



Herramientas de arquitectura de informacion resumenFelipe Vera (Prodigio Consultores) Este documento presenta las herramientas de arquitectura de información para el diseño de servicios de información digital. Explica que la arquitectura de información es el diseño estructural de ambientes de información compartidos para apoyar la búsqueda y uso de la información. Luego, describe la metodología de arquitectura de información, incluyendo objetivos, experiencia de usuario, contenido, estructura y diseño visual. Finalmente, presenta el modelo de Louis Rosenfeld y las herramientas de arquitectura de información agrupadas por
Computer Forensics



Computer ForensicsDaksh Verma Computer Forensics is the branch of digital forensics which deal with the evidence (data) obtained from computers to be produced in the court of law.
Black Hat: XML Out-Of-Band Data Retrieval



Black Hat: XML Out-Of-Band Data Retrievalqqlan This document summarizes XML out-of-band data retrieval attacks using XML external entities. It discusses how XML external entities can be used to retrieve files from remote servers or make requests to external resources. It also covers how entities defined in attributes can be used to bypass restrictions on external entity references. The document demonstrates these attack techniques and outlines tools that can automate XML out-of-band exploitation.
Semophores and it's types



Semophores and it's typesNishant Joshi This document discusses semaphores and their use in solving critical section problems. It defines semaphores, describes their wait and signal methods, and types including counting and binary semaphores. It then explains how semaphores can be used to solve classical synchronization problems like the bounded buffer, readers-writers, and dining philosophers problems. Examples of semaphore implementations are provided for each problem.
Web-Development-ppt.pptx



Web-Development-ppt.pptxAADITYADEVA This document provides an overview of web development. It defines web development as building, creating, and maintaining websites using tools like HTML, CSS, JavaScript, PHP, Java, Python, and Node.js. It classifies web development into frontend and backend development. The frontend is what users interact with, using tools like HTML, CSS, JavaScript, and frameworks like Bootstrap and Angular. The backend is server-side and uses tools like PHP, Java, Python, Node.js, and frameworks like Django and Rails. It describes a full-stack developer as someone proficient in both front-end and back-end development.
Ordbms



Ordbmsramandeep brar - An object-relational database (ORD) or object-relational database management system (ORDBMS) supports objects, classes, and inheritance directly in the database schema and query language, while also retaining the relational model.
- An ORDBMS supports an extended form of SQL called SQL3 for handling abstract data types. It allows storage of complex data types like images and location data.
- Key advantages of ORDBMS include reuse and sharing of code through inheritance, increased productivity for developers and users, and more powerful query capabilities. Key challenges include complexity, immaturity of the technology, and increased costs.
Computer Hardware Introduction



Computer Hardware IntroductionSeenivasan SR Computer Hardware - Generation of Computers - Motherboard Components - Printers Types - Scanners - Software
C language computer introduction to the computer hardware



C language computer introduction to the computer hardwareNIKHIL KRISHNA This document provides an overview of computer hardware, software, organization and concepts. It defines a computer as a device that performs computations and logical decisions by processing data under instruction sets. Key components include the central processing unit (CPU), memory, storage, input/output devices, and software like operating systems and applications. Fundamental concepts discussed include Moore's Law, which predicts an exponential increase in component density, Von Neumann architecture, and how memory is organized into addressable cells.
Ad
More Related Content
What's hot (20)
Marco juridico de la educacion tecnica de Nicaragua.pptx



Marco juridico de la educacion tecnica de Nicaragua.pptxfrankjhellrayo1 Este documento resume el marco jurídico de la educación técnica en Nicaragua, incluyendo la Declaración Universal de los Derechos Humanos, la Constitución Política de Nicaragua, la Ley General de Educación, la Ley de Carrera Docente, y artículos relacionados con los ejes del Plan Nacional de Desarrollo Humano. También describe brevemente la nueva Ley Reguladora del Instituto Nacional Tecnológico.
Database programming



Database programmingShree M.L.Kakadiya MCA mahila college, Amreli This document discusses Python database programming. It introduces databases and how they store data in tables connected through columns. It discusses SQL for creating, accessing, and manipulating database data. It then discusses how Python supports various databases and database operations. It covers the Python DB-API for providing a standard interface for database programming. It provides examples of connecting to a database, executing queries, and retrieving and inserting data.
Operating Systems 1 (7/12) - Threads



Operating Systems 1 (7/12) - ThreadsPeter Tröger The document discusses processes and threads in operating systems. It describes how processes contain multiple threads that can run concurrently on multicore systems. Each thread has its own execution state and context stored in a thread control block. When a thread is not actively running, its context is saved so it can resume execution later. The document provides examples of how threads are implemented in Windows and Linux operating systems.
Multimedia database



Multimedia databaseRashmi Agale This document discusses multimedia databases. A multimedia database is a collection of related multimedia data managed by a multimedia database management system. It supports different data types and allows for creation, storage, access, querying and control of multimedia data. Key components include a query interface, query processing, indexing, buffer management and storage management. Challenges include large storage needs, processing time requirements, and temporal properties of some multimedia data types. Application areas mentioned are digital libraries, news on demand, video on demand, and music databases.
OPERATING SYSTEM SERVICES, OPERATING SYSTEM STRUCTURES



OPERATING SYSTEM SERVICES, OPERATING SYSTEM STRUCTURESpriyasoundar These slides will help the engineering students for understanding the functionalities of operating system and its structure. Also it will help them for their exam preparation.
CS6401 OPERATING SYSTEMS Unit 2



CS6401 OPERATING SYSTEMS Unit 2Kathirvel Ayyaswamy UNIT II PROCESS MANAGEMENT
Processes-Process Concept, Process Scheduling, Operations on Processes, Interprocess Communication; Threads- Overview, Multicore Programming, Multithreading Models; Windows 7 - Thread and SMP Management. Process Synchronization - Critical Section Problem, Mutex Locks, Semophores, Monitors; CPU Scheduling and Deadlocks.
Diagrama fisico



Diagrama fisicoCarlo Gaso El documento describe la creación de una base de datos para una inmobiliaria utilizando MySQL Workbench. Se crean tablas como Inmueble, Propietario, Cliente y otras utilizando sentencias SQL que definen los campos y claves primarias de cada tabla. Las tablas se relacionan entre sí a través de claves externas para almacenar información sobre propiedades inmobiliarias.
Computer Forensics: First Responder Training - Eric Vanderburg - JurInnov



Computer Forensics: First Responder Training - Eric Vanderburg - JurInnovEric Vanderburg This document provides an overview of a three-day computer forensics training hosted by JurInnov Ltd. It introduces the trainers and covers topics including understanding computing environments, collecting electronically stored information, forensic analysis demonstrations, and types of cases where computer forensics are useful. The document outlines concepts like what computer forensics is, sources of electronically stored information, reasons for using computer forensics, how computers operate, and methods for collecting, imaging, and analyzing various types of digital evidence from computers, networks, phones and other devices.
Multimedia db system



Multimedia db systemYojana Nanaware This document provides an overview of multimedia database management systems (MDBMS). It discusses that MDBMS can manage different types of multimedia data, including images, video, audio and more. The key tasks of a MDBMS include organizing, classifying, querying and supporting operations on multimedia data while enforcing data independence and integrity. MDBMS architectures typically feature three layers - an interface layer, an object composition layer to manage multimedia objects, and a storage layer for clustering and indexing multimedia data.
OS Unit 5 - Memory Management



OS Unit 5 - Memory ManagementGyanmanjari Institute Of Technology Basic Memory Management
Introduction
Logical and Physical address map
Memory allocation
Contiguous Memory allocation
Fixed and variable partition
Internal and External fragmentation and Compaction
Paging
Principle of operation
Page allocation
Hardware support for paging
Protection and sharing
Disadvantages of paging
Virtual Memory
Basics of Virtual Memory
Hardware and control structures
Locality of reference
Page fault
Working Set
Dirty page/Dirty bit
Demand paging
Page Replacement policies
Optimal (OPT)
First in First Out (FIFO)
Second Chance (SC)
Not recently used (NRU)
Least Recently used (LRU)
Files concepts.53



Files concepts.53myrajendra The document discusses file concepts, file management, and file attributes. It defines a file as a named collection of related information recorded on secondary storage. It describes different types of files including program files, data files, and their various structures. The document also discusses common file operations and types.
Run time storage



Run time storageRasineni Madhan Mohan Naidu The document discusses run-time environments in compiler design. It provides details about storage organization and allocation strategies at run-time. Storage is allocated either statically at compile-time, dynamically from the heap, or from the stack. The stack is used to store procedure activations by pushing activation records when procedures are called and popping them on return. Activation records contain information for each procedure call like local variables, parameters, and return values.
01-Database Administration and Management.pdf



01-Database Administration and Management.pdfTOUSEEQHAIDER14 This document provides an introduction and overview of database systems. It discusses the purpose of database systems in addressing issues with file-based data storage like data redundancy, inconsistent data, and difficulty of data access. It also describes database applications, data models, database languages like SQL, database design, database architecture, and the major components of a database system including the storage manager, query processor, and transaction manager.
Herramientas de arquitectura de informacion resumen



Herramientas de arquitectura de informacion resumenFelipe Vera (Prodigio Consultores) Este documento presenta las herramientas de arquitectura de información para el diseño de servicios de información digital. Explica que la arquitectura de información es el diseño estructural de ambientes de información compartidos para apoyar la búsqueda y uso de la información. Luego, describe la metodología de arquitectura de información, incluyendo objetivos, experiencia de usuario, contenido, estructura y diseño visual. Finalmente, presenta el modelo de Louis Rosenfeld y las herramientas de arquitectura de información agrupadas por
Computer Forensics



Computer ForensicsDaksh Verma Computer Forensics is the branch of digital forensics which deal with the evidence (data) obtained from computers to be produced in the court of law.
Black Hat: XML Out-Of-Band Data Retrieval



Black Hat: XML Out-Of-Band Data Retrievalqqlan This document summarizes XML out-of-band data retrieval attacks using XML external entities. It discusses how XML external entities can be used to retrieve files from remote servers or make requests to external resources. It also covers how entities defined in attributes can be used to bypass restrictions on external entity references. The document demonstrates these attack techniques and outlines tools that can automate XML out-of-band exploitation.
Semophores and it's types



Semophores and it's typesNishant Joshi This document discusses semaphores and their use in solving critical section problems. It defines semaphores, describes their wait and signal methods, and types including counting and binary semaphores. It then explains how semaphores can be used to solve classical synchronization problems like the bounded buffer, readers-writers, and dining philosophers problems. Examples of semaphore implementations are provided for each problem.
Web-Development-ppt.pptx



Web-Development-ppt.pptxAADITYADEVA This document provides an overview of web development. It defines web development as building, creating, and maintaining websites using tools like HTML, CSS, JavaScript, PHP, Java, Python, and Node.js. It classifies web development into frontend and backend development. The frontend is what users interact with, using tools like HTML, CSS, JavaScript, and frameworks like Bootstrap and Angular. The backend is server-side and uses tools like PHP, Java, Python, Node.js, and frameworks like Django and Rails. It describes a full-stack developer as someone proficient in both front-end and back-end development.
Ordbms



Ordbmsramandeep brar - An object-relational database (ORD) or object-relational database management system (ORDBMS) supports objects, classes, and inheritance directly in the database schema and query language, while also retaining the relational model.
- An ORDBMS supports an extended form of SQL called SQL3 for handling abstract data types. It allows storage of complex data types like images and location data.
- Key advantages of ORDBMS include reuse and sharing of code through inheritance, increased productivity for developers and users, and more powerful query capabilities. Key challenges include complexity, immaturity of the technology, and increased costs.
Viewers also liked (20)
Computer Hardware Introduction



Computer Hardware IntroductionSeenivasan SR Computer Hardware - Generation of Computers - Motherboard Components - Printers Types - Scanners - Software
C language computer introduction to the computer hardware



C language computer introduction to the computer hardwareNIKHIL KRISHNA This document provides an overview of computer hardware, software, organization and concepts. It defines a computer as a device that performs computations and logical decisions by processing data under instruction sets. Key components include the central processing unit (CPU), memory, storage, input/output devices, and software like operating systems and applications. Fundamental concepts discussed include Moore's Law, which predicts an exponential increase in component density, Von Neumann architecture, and how memory is organized into addressable cells.
Computer Hardware



Computer HardwareDeepa Rani Computer is a device capable of performing computations and making logical decisions. It processes data under the control of computer programs. There are three main components of a computer: hardware, software, and networks. Hardware includes physical components like the central processing unit and memory. Software includes operating systems and applications. Networks allow computers to share information and resources. Moore's law predicts that the number of transistors on integrated circuits doubles approximately every two years, leading to exponential increases in computing power over time.
Computer hardware ppt1



Computer hardware ppt1Bangabandhu Sheikh Mujibur Rahman Science and Technology University The document provides an overview of basic computer hardware components. It discusses the central processing unit (CPU), memory units, input/output devices, storage devices like hard disk drives, optical drives, and peripherals. It also covers the motherboard, bus architecture, and factors that affect processing speed such as registers, RAM, the system clock, cache memory, and the bus. Printers, monitors, video cards, modems, network interface cards, air conditioners, uninterruptible power supplies, and RAID devices are also briefly described.
Introduction To Computer And Hardware



Introduction To Computer And Hardwareguest70c61b Desktop PCs are flat computers that originally designed for home use, while tower PCs are upright with components stacked inside, resembling an upright desktop PC. Monitors are specialized high-resolution screens that display images by lighting up red, green, and blue dots many times per second based on signals from the video card. Keyboards are the main input device and contain alphanumeric keys for typing as well as function keys for interacting with programs.
History of computer hardware



History of computer hardwareChristian Macatangay This document provides an overview of the history and components of computers. It discusses the evolution of computer hardware from early mechanical devices like the abacus and Babbage's Difference Engine to modern integrated circuits and microprocessors. It describes the key components of modern computer systems including the CPU, memory, storage, buses, and input/output devices. It also explains the functioning of the CPU and memory in more detail.
B) Computer Basics



B) Computer Basicsremotestaffdesignsolution A computer is an electronic device that processes data through both hardware and software. Hardware refers to physical components like the system unit, monitor, keyboard, and mouse. Software includes operating systems, applications, and utilities. Common applications include programs from Microsoft like Word, Excel, PowerPoint, Outlook, and Internet Explorer. Utilities help optimize, maintain, and secure the computer and include antivirus software, backup utilities, and file compression tools. The Internet is a global network connecting millions of computers through transmission protocols. It allows sharing of resources between servers that store information and clients that access it through browsers using URLs and HTML documents.
00 Hardware Of Personal Computer V1 1



00 Hardware Of Personal Computer V1 1Rajan Das The document summarizes the hardware components of a personal computer. It describes the central processing unit, memory (RAM and hard drives), input/output devices (keyboard, mouse, monitor, printer), and removable media (CDs, DVDs, floppy disks). It also includes diagrams of components like the CPU, memory chips, hard disk drives, and CD and DVD structures.
Presentation on introduction of computer hardware



Presentation on introduction of computer hardwareKashif Kashif This document provides an introduction to basic computer hardware components. It outlines the main internal components like the processor, RAM, motherboard, hard disk, and BIOS. It describes the processor as the brain of the computer and lists common processor types. It defines RAM and describes the two main types as static and dynamic. External peripherals are also listed, including input devices like the keyboard and mouse, as well as output devices such as the monitor, printer, and modem. The document concludes by mentioning computer case form factors.
Hardware & Input/Output (I/O) Devices



Hardware & Input/Output (I/O) DevicesMuhammad Hammad Waseem Hardware devices that are used to input and output data to a computer are called I/O devices. Input devices capture information from the external environment and convert it into a format that can be processed by the computer. Examples include keyboards, mice, scanners, microphones, and webcams. Output devices take the processed data from the computer and present it to the user. Common output devices are monitors, printers, speakers and plotters. Monitors display soft copy output while printers provide hard copy printouts.
SMPS



SMPSSudarshan Pulami The power supply unit converts alternating current (AC) voltage from the wall outlet to lower direct current (DC) voltages that components inside the computer require. It uses a switch mode power supply (SMPS) to efficiently step down the 220-240 volt AC input to stable DC outputs of +3.3V, +5V, +12V, -5V, and -12V to power the motherboard, hard drive, CD/DVD drive, and other computer components, with a maximum power output of 300 watts.
Parts of a computer



Parts of a computermycajoy The document discusses the key parts of a computer system, including both hardware and software. Software includes operating systems like Windows and application programs. Hardware includes input devices like keyboards and mice, processing devices like the central processing unit (CPU) that performs calculations, and output devices like monitors and printers that display or print information for the user. Together, hardware and software work together to power computer systems.
Hardware And Software



Hardware And Softwarezhho9 The document discusses computer hardware and components of a typical personal computer. It describes that a personal computer consists of a computer case or chassis that houses the internal components including the motherboard, central processing unit (CPU), memory, storage devices, ports, and expansion slots. The motherboard contains the CPU, RAM, firmware, buses, and connectors for other components.
3 computer hardware and fundamentals edited for 1st sem



3 computer hardware and fundamentals edited for 1st semVedpal Yadav This document provides an introduction to computer hardware components and storage devices. It discusses the basic components of a computer including the CPU, memory, and input/output devices. It describes different types of computer memory including RAM, ROM, and cache memory. It also covers various storage devices such as magnetic disks, optical disks, solid state drives, and compares their characteristics such as speed, cost, capacity, and type of access. The document provides a high-level overview of key computer hardware concepts.
CHAP 1 - INTRODUCTION TO COMPUTERS



CHAP 1 - INTRODUCTION TO COMPUTERSCikgu Johan Johari This document provides an introduction to computers by defining key computer concepts and components. It explains that a computer accepts input, processes data using a central processing unit and memory, stores data, and produces output. Computer hardware includes input, processing, output, and storage devices. Software is divided into system software, like operating systems and utilities, and application software for tasks like word processing. Popular operating systems include Windows, Mac OS, and Linux. The document outlines the basic functions of a computer system and its hardware and software components.
Hardware basics: inside the box



Hardware basics: inside the boxMiguel Rebollo 1. The document introduces the basic components and functions of a computer, including how information is received as input, processed by the CPU and memory, and produced as output.
2. It describes how information is stored and represented digitally using bits, bytes, and binary and ASCII encoding systems.
3. The core components of a computer are explained as the CPU, which executes instructions stored in memory, and memory itself, which temporarily stores data and program instructions. Other components like buses, ports and peripherals are also outlined.
Microsoft power point 2007



Microsoft power point 2007Abdul-rahaman Bin Abubakar Suleman PowerPoint is presentation software used to create slide shows. It has several views including Normal view which displays slides, outlines, and notes. The Ribbon contains tabs for commands. Animations control how objects move on slides, while transitions control movement between slides. Users can add, modify, and preview animations using the Custom Animation pane to control effects, timing, and properties.
Introduction to computer hardware



Introduction to computer hardwareMirea Mizushima A computer is an electronic device that helps people perform tasks like writing documents, creating pictures, calculations, playing games and sending email. The main parts of a computer are the system unit (central processing unit), input devices like keyboards and mice, and output devices like monitors and printers. The system unit processes data from the input devices and sends output to devices. Proper handling and care of computer parts like mice, diskettes, and keyboards is important for safety and preventing damage.
Basic Computer Operation And Troubleshooting



Basic Computer Operation And TroubleshootingPraveen Sudarsan Introduction to Computer Hardware
Case
Power switch
Reset switch
Hard drive
Floppy
CD/DVD
Zip drive
Serial ports
Parallel port
USB port
Keyboard/mouse
Network card
Modem
Sound card
Video card
RAM
Motherboard
Bus
Fan
Cables
Introduction to microsoft excel 2007



Introduction to microsoft excel 2007Abdul-rahaman Bin Abubakar Suleman This document provides an introduction and overview of Microsoft Excel 2007. It discusses the basics of Excel including rows, columns, cells, and the three types of data - labels, constants, and formulas. It describes how to launch Excel and explains the key parts of the Excel window like the ribbon, worksheet, formula bar, and status bar. It includes exercises on how to move around the worksheet, select cells, enter and edit data, and change cell entries. It also covers how to wrap text in a cell when the text is too long.
Ad
Similar to Overview of computer (20)
fdocuments.in_unit-2-foc.ppt



fdocuments.in_unit-2-foc.pptKrishanPalSingh39 This document discusses computer software and operating systems. It defines application and system software, and describes different types of operating systems like single-user/single-tasking OS, single-user/multi-tasking OS, multi-user/multi-tasking OS, time sharing OS, and real-time OS. It also covers system software components like compilers, interpreters, assemblers, and device drivers. The document outlines the system development life cycle including requirement analysis, design, coding, testing, and implementation/maintenance steps.
Introduction & Background(Operating Systems).pptx



Introduction & Background(Operating Systems).pptxssuserf7df42 This document provides an introduction and overview of operating systems. It defines an operating system as a program that manages computer resources and acts as an intermediary between hardware and software. It discusses the evolution of operating systems from early systems with manual controls to modern systems with timesharing, multiprocessing, and graphical user interfaces. It also describes different types of operating systems including single-user, distributed, network, multiprocessor, real-time, and embedded operating systems.
Introduction to Operating system CBSE 



Introduction to Operating system CBSE PrashantChahal3 computer application chapter 2 Operating system , detailed ppt
from more detail and content please give thumbss up
systems_software



systems_softwareBrian Shonhiwa Computer software refers to a set of instructions given to a computer to perform tasks and comes in two types: systems software and applications software. Systems software includes operating systems, which control computer operations and manage resources, and development programs, which help create application software. Popular operating systems include Windows, Mac OS, Linux, and UNIX.
INTRODUCTION TO COMPUTER SOFTWARE



INTRODUCTION TO COMPUTER SOFTWAREabiramiabi21 1. There are five levels of programming languages from lowest to highest: machine language, assembly language, procedural language, problem-oriented language, and natural language.
2. Machine language uses binary digits (0s and 1s) and is the only language computers can understand directly. Assembly language uses abbreviations to replace machine language instructions.
3. High-level languages like procedural and problem-oriented languages allow programmers to write code using syntax closer to human languages and are translated into machine language before execution.
OPERATING SYSTEM



OPERATING SYSTEMMadhushree Shettigar An operating system (OS) manages application programs and hardware devices. It determines which applications run and in what order, manages memory sharing between applications, and handles input/output to hardware. Popular desktop OSs include Windows, Mac OS, and Linux. Batch systems run jobs non-interactively while time-sharing systems allow interactive use by multiple users simultaneously. Distributed, network, real-time, and embedded OSs are designed for specialized environments. A library OS provides typical OS services as libraries to compose with applications.
Basic IT knowledge



Basic IT knowledgeTechsailor This document defines basic computer terminology including hardware, software, operating systems, and peripherals. It explains that a computer is a programmable machine that receives input, stores and manipulates data, and provides useful output. It also defines key hardware components like the motherboard, processor, and memory. It outlines common software types including operating systems, programming software, and applications. Finally, it describes the basic components of a website and network devices.
basicitknowledge-101119022655-phpapp02.ppt



basicitknowledge-101119022655-phpapp02.pptPawachMetharattanara This document defines basic computer terminology including hardware, software, operating systems, and peripherals. It explains that a computer is a programmable machine that receives input, stores and manipulates data, and provides useful output. It also defines internal and external hardware devices, different types of software including system software, programming software, and application software, and describes what a website is.
Internet and web by Gulshan K Maheshwari(QAU)



Internet and web by Gulshan K Maheshwari(QAU)GulshanKumar368 The document provides an overview of the history and development of the internet and world wide web. It discusses how Tim Berners-Lee first developed the idea for a hypertext-based information system in 1989 while working at CERN. It then outlines the development of key technologies and protocols that led to the creation of the internet, including ARPANET, TCP/IP, domain name addressing, HTML, and HTTP. The document also distinguishes between related terms like the internet, intranets, and the world wide web.
Unit 1 operating system



Unit 1 operating systemMeeta The document provides an introduction to operating systems, covering topics such as the need for operating systems, their evolution over different generations from batch to real-time systems, and the components of a computer system including hardware, operating system, application programs, and users. It then discusses operating system services from both the user and system point of view, and provides case studies of the Windows and Linux operating systems.
2 software



2 softwareVeeresh Khelgi This document provides an overview of software, including definitions and types of software. It discusses system software such as operating systems and their functions. It also covers application software, programming languages, and software development approaches like object-oriented programming. Specific software mentioned includes HTML, XML, Java, and UML.
Year 10 ict computing essentials



Year 10 ict computing essentialsM'Lourdes Borg The document provides an overview of operating systems and applications software. It discusses how operating systems control computer resources and enable the running of applications. Common desktop operating systems include Windows, Mac OS, Linux, and Unix. The document also summarizes different types of applications software like word processors, spreadsheets, databases, presentations, and internet browsers. It briefly outlines mobile apps, software licenses, and computer networking concepts.
Operating system concept



Operating system conceptInternational Islamic University An operating system is software that manages computer hardware resources and provides common services for computer programs. It acts as an intermediary between users and the computer hardware. The main goals of an operating system are to control allocation of system resources including memory, CPU time, and disk space, provide a platform for execution of programs, make the computer system convenient to use, and use computer hardware efficiently. An operating system separates applications from the hardware they access and manages both software and hardware resources to produce desired results. It primarily functions as a resource manager.
Operating System Unit 1



Operating System Unit 1SanthiNivas Through this PPT you may learned about Operating System, Types of OS, History of OS, Operating System Software, Gives detailed information about Device Management, Memory Management, File Management
INTERNET TECHNOLOGY



INTERNET TECHNOLOGYsubhradeep mitra The document provides an overview of the history and workings of the internet. It discusses how ARPAnet was developed in the 1960s as a military network which later became the foundation for the commercial internet. It describes important internet protocols like TCP/IP, HTTP, and DNS. It also explains client-server architecture, IP addressing, URLs, web browsers, search engines, and common uses of the internet like email, e-commerce, and social media.
Ch 2



Ch 2Sam Govea This document provides an overview of hardware and software components. It discusses:
1) The main hardware components of a computer including the CPU, memory, and secondary storage devices. The CPU contains the ALU, control unit, and registers. Memory provides temporary storage and comes in RAM and ROM types.
2) Software includes systems software like operating systems and utility programs, as well as application software. Operating systems manage hardware resources, provide user interfaces, and perform tasks like memory management. Application software interacts with the operating system to help users perform tasks.
3) Emerging trends in technology including multiprocessing, cloud computing, mobile apps, and software as a service. These trends allow for increased processing power, flexible
Chapter one_oS.ppt



Chapter one_oS.pptmiki304759 The document provides an overview of operating systems and system software. It discusses what system software is, the need for system software, types of system software including operating systems, device drivers, firmware, programming language translators, and utility software. It defines operating systems and describes their design goals. It also outlines the four main components of a computer system - hardware, operating system, application programs, and users. Finally, it discusses the key components of an operating system including process management, I/O device management, file management, memory management, and security management.
Ad
Recently uploaded (20)
Exceptional Behaviors: How Frequently Are They Tested? (AST 2025)



Exceptional Behaviors: How Frequently Are They Tested? (AST 2025)Andre Hora Exceptions allow developers to handle error cases expected to occur infrequently. Ideally, good test suites should test both normal and exceptional behaviors to catch more bugs and avoid regressions. While current research analyzes exceptions that propagate to tests, it does not explore other exceptions that do not reach the tests. In this paper, we provide an empirical study to explore how frequently exceptional behaviors are tested in real-world systems. We consider both exceptions that propagate to tests and the ones that do not reach the tests. For this purpose, we run an instrumented version of test suites, monitor their execution, and collect information about the exceptions raised at runtime. We analyze the test suites of 25 Python systems, covering 5,372 executed methods, 17.9M calls, and 1.4M raised exceptions. We find that 21.4% of the executed methods do raise exceptions at runtime. In methods that raise exceptions, on the median, 1 in 10 calls exercise exceptional behaviors. Close to 80% of the methods that raise exceptions do so infrequently, but about 20% raise exceptions more frequently. Finally, we provide implications for researchers and practitioners. We suggest developing novel tools to support exercising exceptional behaviors and refactoring expensive try/except blocks. We also call attention to the fact that exception-raising behaviors are not necessarily “abnormal” or rare.
What Do Contribution Guidelines Say About Software Testing? (MSR 2025)



What Do Contribution Guidelines Say About Software Testing? (MSR 2025)Andre Hora Software testing plays a crucial role in the contribution process of open-source projects. For example, contributions introducing new features are expected to include tests, and contributions with tests are more likely to be accepted. Although most real-world projects require contributors to write tests, the specific testing practices communicated to contributors remain unclear. In this paper, we present an empirical study to understand better how software testing is approached in contribution guidelines. We analyze the guidelines of 200 Python and JavaScript open-source software projects. We find that 78% of the projects include some form of test documentation for contributors. Test documentation is located in multiple sources, including CONTRIBUTING files (58%), external documentation (24%), and README files (8%). Furthermore, test documentation commonly explains how to run tests (83.5%), but less often provides guidance on how to write tests (37%). It frequently covers unit tests (71%), but rarely addresses integration (20.5%) and end-to-end tests (15.5%). Other key testing aspects are also less frequently discussed: test coverage (25.5%) and mocking (9.5%). We conclude by discussing implications and future research.
Designing AI-Powered APIs on Azure: Best Practices& Considerations



Designing AI-Powered APIs on Azure: Best Practices& ConsiderationsDinusha Kumarasiri AI is transforming APIs, enabling smarter automation, enhanced decision-making, and seamless integrations. This presentation explores key design principles for AI-infused APIs on Azure, covering performance optimization, security best practices, scalability strategies, and responsible AI governance. Learn how to leverage Azure API Management, machine learning models, and cloud-native architectures to build robust, efficient, and intelligent API solutions
Adobe Marketo Engage Champion Deep Dive - SFDC CRM Synch V2 & Usage Dashboards



Adobe Marketo Engage Champion Deep Dive - SFDC CRM Synch V2 & Usage DashboardsBradBedford3 Join Ajay Sarpal and Miray Vu to learn about key Marketo Engage enhancements. Discover improved in-app Salesforce CRM connector statistics for easy monitoring of sync health and throughput. Explore new Salesforce CRM Synch Dashboards providing up-to-date insights into weekly activity usage, thresholds, and limits with drill-down capabilities. Learn about proactive notifications for both Salesforce CRM sync and product usage overages. Get an update on improved Salesforce CRM synch scale and reliability coming in Q2 2025.
Key Takeaways:
Improved Salesforce CRM User Experience: Learn how self-service visibility enhances satisfaction.
Utilize Salesforce CRM Synch Dashboards: Explore real-time weekly activity data.
Monitor Performance Against Limits: See threshold limits for each product level.
Get Usage Over-Limit Alerts: Receive notifications for exceeding thresholds.
Learn About Improved Salesforce CRM Scale: Understand upcoming cloud-based incremental sync.
Expand your AI adoption with AgentExchange



Expand your AI adoption with AgentExchangeFexle Services Pvt. Ltd. AgentExchange is Salesforce’s latest innovation, expanding upon the foundation of AppExchange by offering a centralized marketplace for AI-powered digital labor. Designed for Agentblazers, developers, and Salesforce admins, this platform enables the rapid development and deployment of AI agents across industries.
Email: [email protected]
Phone: +1(630) 349 2411
Website: https://www.fexle.com/blogs/agentexchange-an-ultimate-guide-for-salesforce-consultants-businesses/?utm_source=slideshare&utm_medium=pptNg
Meet the Agents: How AI Is Learning to Think, Plan, and Collaborate



Meet the Agents: How AI Is Learning to Think, Plan, and CollaborateMaxim Salnikov Imagine if apps could think, plan, and team up like humans. Welcome to the world of AI agents and agentic user interfaces (UI)! In this session, we'll explore how AI agents make decisions, collaborate with each other, and create more natural and powerful experiences for users.
Avast Premium Security Crack FREE Latest Version 2025



Avast Premium Security Crack FREE Latest Version 2025mu394968 🌍📱👉COPY LINK & PASTE ON GOOGLE https://dr-kain-geera.info/👈🌍
Avast Premium Security is a paid subscription service that provides comprehensive online security and privacy protection for multiple devices. It includes features like antivirus, firewall, ransomware protection, and website scanning, all designed to safeguard against a wide range of online threats, according to Avast.
Key features of Avast Premium Security:
Antivirus: Protects against viruses, malware, and other malicious software, according to Avast.
Firewall: Controls network traffic and blocks unauthorized access to your devices, as noted by All About Cookies.
Ransomware protection: Helps prevent ransomware attacks, which can encrypt your files and hold them hostage.
Website scanning: Checks websites for malicious content before you visit them, according to Avast.
Email Guardian: Scans your emails for suspicious attachments and phishing attempts.
Multi-device protection: Covers up to 10 devices, including Windows, Mac, Android, and iOS, as stated by 2GO Software.
Privacy features: Helps protect your personal data and online privacy.
In essence, Avast Premium Security provides a robust suite of tools to keep your devices and online activity safe and secure, according to Avast.
How to Batch Export Lotus Notes NSF Emails to Outlook PST Easily?



How to Batch Export Lotus Notes NSF Emails to Outlook PST Easily?steaveroggers Migrating from Lotus Notes to Outlook can be a complex and time-consuming task, especially when dealing with large volumes of NSF emails. This presentation provides a complete guide on how to batch export Lotus Notes NSF emails to Outlook PST format quickly and securely. It highlights the challenges of manual methods, the benefits of using an automated tool, and introduces eSoftTools NSF to PST Converter Software — a reliable solution designed to handle bulk email migrations efficiently. Learn about the software’s key features, step-by-step export process, system requirements, and how it ensures 100% data accuracy and folder structure preservation during migration. Make your email transition smoother, safer, and faster with the right approach.
Read More:- https://www.esofttools.com/nsf-to-pst-converter.html
Revolutionizing Residential Wi-Fi PPT.pptx



Revolutionizing Residential Wi-Fi PPT.pptxnidhisingh691197 Discover why Wi-Fi 7 is set to transform wireless networking and how Router Architects is leading the way with next-gen router designs built for speed, reliability, and innovation.
Secure Test Infrastructure: The Backbone of Trustworthy Software Development



Secure Test Infrastructure: The Backbone of Trustworthy Software DevelopmentShubham Joshi A secure test infrastructure ensures that the testing process doesn’t become a gateway for vulnerabilities. By protecting test environments, data, and access points, organizations can confidently develop and deploy software without compromising user privacy or system integrity.
How can one start with crypto wallet development.pptx



How can one start with crypto wallet development.pptxlaravinson24 This presentation is a beginner-friendly guide to developing a crypto wallet from scratch. It covers essential concepts such as wallet types, blockchain integration, key management, and security best practices. Ideal for developers and tech enthusiasts looking to enter the world of Web3 and decentralized finance.
Interactive odoo dashboards for sales, CRM , Inventory, Invoice, Purchase, Pr...



Interactive odoo dashboards for sales, CRM , Inventory, Invoice, Purchase, Pr...AxisTechnolabs Interactive Odoo Dashboard for various business needs can provide users with dynamic, visually appealing dashboards tailored to their specific requirements. such a module that could support multiple dashboards for different aspects of a business
✅Visit And Buy Now : https://bit.ly/3VojWza
✅This Interactive Odoo dashboard module allow user to create their own odoo interactive dashboards for various purpose.
App download now :
Odoo 18 : https://bit.ly/3VojWza
Odoo 17 : https://bit.ly/4h9Z47G
Odoo 16 : https://bit.ly/3FJTEA4
Odoo 15 : https://bit.ly/3W7tsEB
Odoo 14 : https://bit.ly/3BqZDHg
Odoo 13 : https://bit.ly/3uNMF2t
Try Our website appointment booking odoo app : https://bit.ly/3SvNvgU
👉Want a Demo ?📧 [email protected]
➡️Contact us for Odoo ERP Set up : 091066 49361
👉Explore more apps: https://bit.ly/3oFIOCF
👉Want to know more : 🌐 https://www.axistechnolabs.com/
#odoo #odoo18 #odoo17 #odoo16 #odoo15 #odooapps #dashboards #dashboardsoftware #odooerp #odooimplementation #odoodashboardapp #bestodoodashboard #dashboardapp #odoodashboard #dashboardmodule #interactivedashboard #bestdashboard #dashboard #odootag #odooservices #odoonewfeatures #newappfeatures #odoodashboardapp #dynamicdashboard #odooapp #odooappstore #TopOdooApps #odooapp #odooexperience #odoodevelopment #businessdashboard #allinonedashboard #odooproducts
Solidworks Crack 2025 latest new + license code



Solidworks Crack 2025 latest new + license codeaneelaramzan63 Copy & Paste On Google >>> https://dr-up-community.info/
The two main methods for installing standalone licenses of SOLIDWORKS are clean installation and parallel installation (the process is different ...
Disable your internet connection to prevent the software from performing online checks during installation
Proactive Vulnerability Detection in Source Code Using Graph Neural Networks:...



Proactive Vulnerability Detection in Source Code Using Graph Neural Networks:...Ranjan Baisak As software complexity grows, traditional static analysis tools struggle to detect vulnerabilities with both precision and context—often triggering high false positive rates and developer fatigue. This article explores how Graph Neural Networks (GNNs), when applied to source code representations like Abstract Syntax Trees (ASTs), Control Flow Graphs (CFGs), and Data Flow Graphs (DFGs), can revolutionize vulnerability detection. We break down how GNNs model code semantics more effectively than flat token sequences, and how techniques like attention mechanisms, hybrid graph construction, and feedback loops significantly reduce false positives. With insights from real-world datasets and recent research, this guide shows how to build more reliable, proactive, and interpretable vulnerability detection systems using GNNs.
Download Wondershare Filmora Crack [2025] With Latest![Download Wondershare Filmora Crack [2025] With Latest](https://cdn.slidesharecdn.com/ss_thumbnails/neo4j-howkgsareshapingthefutureofgenerativeaiatawssummitlondonapril2024-240426125209-2d9db05d-250419-250428115407-a04afffa-thumbnail.jpg?width=560&fit=bounds)
![Download Wondershare Filmora Crack [2025] With Latest](https://cdn.slidesharecdn.com/ss_thumbnails/neo4j-howkgsareshapingthefutureofgenerativeaiatawssummitlondonapril2024-240426125209-2d9db05d-250419-250428115407-a04afffa-thumbnail.jpg?width=560&fit=bounds)
![Download Wondershare Filmora Crack [2025] With Latest](https://cdn.slidesharecdn.com/ss_thumbnails/neo4j-howkgsareshapingthefutureofgenerativeaiatawssummitlondonapril2024-240426125209-2d9db05d-250419-250428115407-a04afffa-thumbnail.jpg?width=560&fit=bounds)
![Download Wondershare Filmora Crack [2025] With Latest](https://cdn.slidesharecdn.com/ss_thumbnails/neo4j-howkgsareshapingthefutureofgenerativeaiatawssummitlondonapril2024-240426125209-2d9db05d-250419-250428115407-a04afffa-thumbnail.jpg?width=560&fit=bounds)
Download Wondershare Filmora Crack [2025] With Latesttahirabibi60507 Copy & Past Link 👉👉
http://drfiles.net/
Wondershare Filmora is a video editing software and app designed for both beginners and experienced users. It's known for its user-friendly interface, drag-and-drop functionality, and a wide range of tools and features for creating and editing videos. Filmora is available on Windows, macOS, iOS (iPhone/iPad), and Android platforms.
F-Secure Freedome VPN 2025 Crack Plus Activation New Version



F-Secure Freedome VPN 2025 Crack Plus Activation New Versionsaimabibi60507 Copy & Past Link 👉👉
https://dr-up-community.info/
F-Secure Freedome VPN is a virtual private network service developed by F-Secure, a Finnish cybersecurity company. It offers features such as Wi-Fi protection, IP address masking, browsing protection, and a kill switch to enhance online privacy and security .
Not So Common Memory Leaks in Java Webinar



Not So Common Memory Leaks in Java WebinarTier1 app This SlideShare presentation is from our May webinar, “Not So Common Memory Leaks & How to Fix Them?”, where we explored lesser-known memory leak patterns in Java applications. Unlike typical leaks, subtle issues such as thread local misuse, inner class references, uncached collections, and misbehaving frameworks often go undetected and gradually degrade performance. This deck provides in-depth insights into identifying these hidden leaks using advanced heap analysis and profiling techniques, along with real-world case studies and practical solutions. Ideal for developers and performance engineers aiming to deepen their understanding of Java memory management and improve application stability.
Requirements in Engineering AI- Enabled Systems: Open Problems and Safe AI Sy...



Requirements in Engineering AI- Enabled Systems: Open Problems and Safe AI Sy...Lionel Briand Keynote at RAISE workshop, ICSE 2025
Kubernetes_101_Zero_to_Platform_Engineer.pptx



Kubernetes_101_Zero_to_Platform_Engineer.pptxCloudScouts Presentacion de la primera sesion de Zero to Platform Engineer
Overview of computer
- 1. Overview of Computer Pavan Govada PGDM
- 2. Topics discussed • History • Hardware and Software • System and application software • Embedded software • Fundamentals of operating system • DBMS • World Wide Wed (www) • Internet application
- 3. History of computers • Abuscus • Slide rule • Charles babbage : Father of computer Leonardo da Vinci (1452-1519) made drawings of gear- driven calculating machines but apparently never built any.
- 4. • IBM : started by Hollerith, developed punch card technology(read/write). • Mark 1: Harvard & IBM=> First programmable digital computer.
- 5. First Generation computers(1939-1942): Binary (0’s &1’s), vacuum tubes. Second Generation computers(1956-1963): Transistors
- 6. Third Generation computers(1964-1970): Transistors are replaced by Integrated cicuits Fourth Generation computers: Microprocessor
- 7. Hardware • Components of computer: 1. Power supply(SMPS) 2. Motherboard 3. Ports and Interfaces 4. Expansion cards 5. Ribbon cables 6. Memory chips 7. Storage devices 8. Processors
- 8. Memory CPU Input Devices Output Devices Input devices: 1. Keyboard 2. Pointing devices 3. Speech recognition 4. Digital camera 5. Web cam 6. Scanner 7. Bar code reader 8. Memory card reader Output devices: 1. Printers 2. Monitors 3. Projectors 4. Headphone
- 10. Computer Software Relationships User Interface Basic Input and Output Services (BIOS) • needed for a computer to boot up User Interface Operating System User Interface Application Programs Computer Hardware
- 11. What is a (programming) language? • A program needs to be written in a language • There are many programming languages – Low-level, understandable by a computer – High-level, needs a translator! • C++ is a high level programming language A sequence of instructions A program (in computer language) An algorthm (in human language)
- 12. Translation System • Set of programs used to develop software • Types of translators: Compiler Linker • Examples Microsoft Visual C++, Eclipse, g++
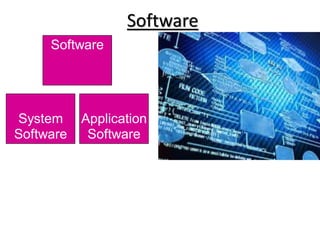
- 13. System & Application software • Application software: – Easy-to-use programs designed to perform specific tasks • System software: – Programs that support the execution and development of other programs
- 14. Application Software • Application software makes computer easy to use for completion of the task. • Common application software: Microsoft Word, WordPerfect PowerPoint Internet Explorer Photo Shop, Photo-Paint Quick Time Dreamweaver
- 15. System software • System control programs controls the execution of programs, manages the storage & processing resources of the computer and perform other management, monitoring function. • System support programs provides routine services function to the other computer programs and computer users Eg: Operating system, DOS,etc
- 17. Embedded system • An embedded system is a computer system with a dedicated function within a larger mechanical or electrical system, often with real-time computing constraints. It is embedded as part of a complete device often Including hardware and mechanical parts. • It controls the flow of the circuit according to the algorithm to achieve the desired output.
- 18. MICROPROCESSOR
- 19. MICROCONTROLLER • A microcontroller (sometimes abbreviated µC, uC or MCU) is a small computer on a single integrated circuit containing a processor core, memory, and programmable input/output peripherals.
- 20. EMBEDDED SOFTWARE • Embedded software is computer software, written to control machines or devices that are not typically thought of as computers. It is typically specialized for the particular hardware that it runs on and has time and memory constraints. • Code is typically written in C or C++ • Embedded software however is often less visible • Software that runs on anything except traditional computers
- 21. EXAMPLES • ROBOTICS SET TOP BOX REMOTES
- 22. CREATIVITY • We are the creators • We can control everything • For that we must have knowledge from Down to Bottom. • We write software at Kernel Level, Drive Level, etc. • Clear and consistent code must be written .
- 23. MICRO CONTROLLER BLOCK DIAGRAM AND INTERFACE
- 24. Fundamentals of operating system • Operating System is a software, which makes a computer to actually work. • It is the software the enables all the programs we use. • The OS organizes and controls the hardware. • OS acts as an interface between the application programs and the machine hardware. • Examples: Windows, Linux, Unix and Mac OS, etc.,
- 25. What OS does? An operating system performs basic tasks such as, • controlling and allocating memory, • prioritizing system requests, • controlling input and output devices, • facilitating networking and • managing file systems.
- 26. Types of operating systems Single user system: • Provides a platform for only one user at a time. • They are popularly associated with Desk Top operating system which run on standalone systems where no user accounts are required. • Example: DOS
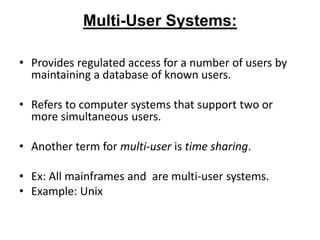
- 27. Multi-User Systems: • Provides regulated access for a number of users by maintaining a database of known users. • Refers to computer systems that support two or more simultaneous users. • Another term for multi-user is time sharing. • Ex: All mainframes and are multi-user systems. • Example: Unix
- 28. Functions of an operating system • Process management • Memory management • File management • Device management • Security management • User interface
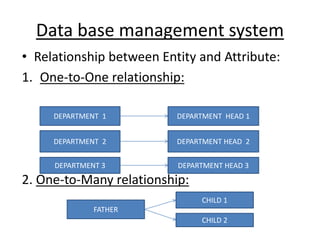
- 29. Data base management system • Relationship between Entity and Attribute: 1. One-to-One relationship: 2. One-to-Many relationship: DEPARTMENT 1 DEPARTMENT HEAD 1 DEPARTMENT 2 DEPARTMENT HEAD 2 DEPARTMENT 3 DEPARTMENT HEAD 3 FATHER CHILD 1 CHILD 2
- 30. 3. MANY-TO-MANY relationship: TELEVISION VCD PLAYER CUSTOMER 1 CUSTOMER 2 CUSTOMER 3 CUSTOMER 4
- 31. Physical data concepts • Sequential Files: Data are stored and retrieved in a logical order or sequential order. • However sequential search takes very long time. • Direct files: It facilitates accessing any record directly or randomly without having to traverse the sequence of the records. • Indexed sequential files: It is a combination of both sequential and direct files.
- 32. DATA DATA FILE FILE EMPLOYEE ALLOWANCE EMPLOYEE APPLICATION PROGRAM ALLOWANCE APPLICATION PROGRAM
- 34. Advantages of DBMS • Reduction in data redundancy. • Sharing of data. • Enforcements of standards. • Improvement in data security. • Maintenance of data integrity. • Better interaction with the user. • Efficient system.
- 36. World wide web • 1989-1990 – Tim Berners-Lee invents the World Wide Web at CERN – Means for transferring text and graphics simultaneously – Client/Server data transfer protocol • Communication via application level protocol • System ran on top of standard networking infrastructure – Text mark up language • Not invented by Bernes-Lee • Simple and easy to use • Requires a client application to render text/graphics
- 37. • Hypertext Hypertext is text which contains links to other texts. The term was invented by Ted Nelson around 1965 • Hypermedia Hypermedia is a term used for hypertext which is not constrained to be text: it can include graphics, video and sound • WEB Browser A web browser displays a web document and enables users to access web documents. Major terms
- 38. • WEB Server This is a program that waits patiently for the browser to request a web page. The servers looks for the requested information, retrieves it and send it to the browser or sends an error message if the file is not found. • Uniform Resource Locator (URL) These are the web addresses. We type URL in Address bar of the browser then hit on enter then URL request a web page to the web server.
- 39. • WEBSITE A website is a set of related WebPages(linked through hypertext links) published by an organization or an individual. • HTTP Hyper text transfer protocol is the set of rules for transferring files (text, graphic images, sound, video, and other multimedia files) on the world wide web • HTML Hyper text Markup language is a set of markup symbols or codes inserted in a file indented to display on a world wide web browser page. • XML Extensible Markup Language is a markup language that allows programmers to create customized tags.
- 40. Internet applications • E- MAIL • TELEPHONY INTERNETAND VIDEO CONFERENCING • COMMERENCE THROUGH INTERNET • NEWAGROUP • TELNET • MAILING SYSTEM • FILE TRANSFER PROTROCOL
- 41. FILE TRANSFER PROTOCOL FIRST KIND FOR EDUCATIONAL AND GOVERNMENTAL INSTITUTIONS CLIENT-SERVER PROTOCOL RELIES ON TWO COMMUNICATIONS CHANNELS BETWEEN CLIENT AND SERVER: A COMMAND CHANNEL + DATA CHANNEL A USER TYPICALLY NEEDS TO LOG ON TO THE FTP SERVER SOME SERVERS MAKE SOME OR ALL OF THEIR CONTENT AVAILABLE WITHOUT LOGIN- ANONYMOUS FTP.
- 42. COMMERCE THROUGH INTERNET • ELECTRONIC GLOBAL WORLDWIDE MARKET OPERATING 24 * 365 • EDI AND EFT • WHILE PURCHASING- SECURE FACILITIES – DIGITAL SIGNATURES AND ENCRYPTION • M-COMMERCE
- 43. THANK YOU




