Paper Study - Demand-Driven Computation of Interprocedural Data Flow
- 1. Demand-Driven Computation of Inter-procedural Data Flow Evelyn Duesterwald et al. POPL 1995 Presenter: Min-Yih Hsu
- 2. Outline • Overview • Illustrating Exhaustive Data-Flow Analysis with Copy Constant Propagation (CCP) • Demand-Driven Data-Flow Analysis • Related Works • Comments
- 3. Overview
- 5. The over-analysis problem • Users of a data-flow analysis might only need part of the results. • Generating superfluous analysis results are called over-analysis.
- 6. The over-analysis problem • Users of a data-flow analysis might only need part of the results. • Generating superfluous analysis results are called over-analysis. • Example: In constant propagation, user only asked the constant value (or non-constant) of variable x at line n.
- 7. The over-analysis problem • Users of a data-flow analysis might only need part of the results. • Generating superfluous analysis results are called over-analysis. • Example: In constant propagation, user only asked the constant value (or non-constant) of variable x at line n. • Traditional data-flow analysis will give you results of every variables in each line.
- 8. The over-analysis problem • Users of a data-flow analysis might only need part of the results. • Generating superfluous analysis results are called over-analysis. • Example: In constant propagation, user only asked the constant value (or non-constant) of variable x at line n. • Traditional data-flow analysis will give you results of every variables in each line. • A real-world application: Interactive code editor
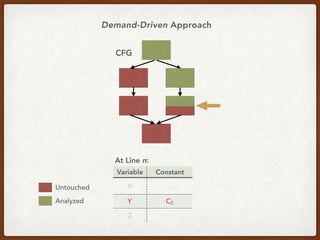
- 12. CFG Variable Constant X C1 Y C2 Z C3 At Line n: Untouched Analyzed Traditional Approach
- 13. CFG Variable Constant X C1 Y C2 Z C3 At Line n: Untouched Analyzed Traditional Approach a.k.a Exhaustive Approach
- 17. CFG Variable Constant X - Y C2 Z - At Line n: Untouched Analyzed Demand-Driven Approach
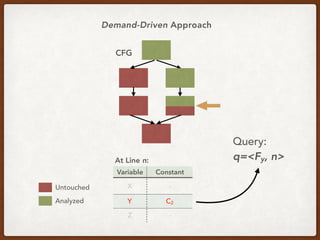
- 18. CFG Variable Constant X - Y C2 Z - At Line n: Untouched Analyzed Demand-Driven Approach Query: q=<Fy, n>
- 19. CFG Variable Constant X - Y C2 Z - At Line n: Untouched Analyzed Demand-Driven Approach Query: q=<Fy, n>
- 20. CFG Variable Constant X - Y C2 Z - At Line n: Untouched Analyzed Demand-Driven Approach Query: q=<Fy, n>
- 21. Illustrating Exhaustive Data-Flow Analysis w/ Copy Constant Propagation (CCP)
- 22. Copy Constant Propagation (CCP) A lattice L
- 23. Copy Constant Propagation (CCP) A lattice L Data flow facts at a given program point x is a k-tuple of type L. (denoted Lk) (x)v means data flow fact for variable v
- 24. Copy Constant Propagation (CCP) A lattice L Data flow facts at a given program point x is a k-tuple of type L. (denoted Lk) (x)v means data flow fact for variable v If variable v has constant c :
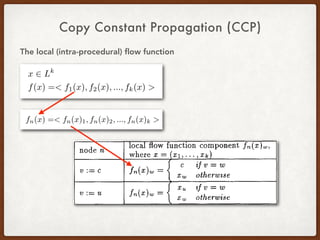
- 25. Copy Constant Propagation (CCP) The local (intra-procedural) flow function
- 26. Copy Constant Propagation (CCP) The local (intra-procedural) flow function
- 27. Copy Constant Propagation (CCP) The local (intra-procedural) flow function
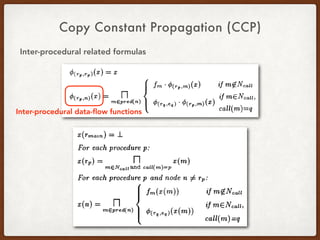
- 28. Copy Constant Propagation (CCP) Inter-procedural related formulas
- 29. Copy Constant Propagation (CCP) Inter-procedural related formulas Inter-procedural data-flow functions
- 30. Copy Constant Propagation (CCP) Inter-procedural related formulas Inter-procedural data-flow functions
- 31. Copy Constant Propagation (CCP) Inter-procedural related formulas Inter-procedural data-flow functions
- 32. Copy Constant Propagation (CCP) Inter-procedural related formulas Inter-procedural data-flow functions Inter-procedural data-flow results On program point n
- 34. CFG Variable Constant X - Y C2 Z - At Line n: Untouched Analyzed Demand-Driven Approach Query: q=<Fy, n>
- 35. CFG Variable Constant X - Y C2 Z - At Line n: Untouched Analyzed Demand-Driven Approach Query: q=<Fy, n>
- 36. Query (i.e. the “Demand”) q := <y, n>
- 37. Query (i.e. the “Demand”) q := <y, n> • y is a set of data flow facts
- 38. Query (i.e. the “Demand”) q := <y, n> • y is a set of data flow facts • n is a program point
- 39. Query (i.e. the “Demand”) q := <y, n> • y is a set of data flow facts • n is a program point • q is a boolean type result
- 40. Query (i.e. the “Demand”) q := <y, n> • y is a set of data flow facts • n is a program point • q is a boolean type result q tells if y is a safe approximation of the exhaustive data flow facts on program point n.
- 41. An Example Query in CCP* q := <[a=c], 10> “Tell me if variable a is equal to constant c at line 10”
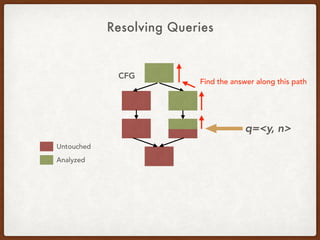
- 46. Resolving Queries CFG Untouched Analyzed q=<y, n> Find the answer along this path
- 47. Resolving Queries CFG Untouched Analyzed q=<y, n> Key Idea: Reversed Flow Function! Find the answer along this path
- 49. Reverse Flow Function If f is meet-distributive…
- 50. Reverse Flow Function If f is meet-distributive… (It’s easy to show that) fr will be join-distributive!
- 51. Reverse Flow Function If f is meet-distributive… (It’s easy to show that) fr will be join-distributive! => We can use MFP with reversed functions along the reversed path!
- 52. Reverse Flow Function What does answers?
- 53. Reverse Flow Function What does answers? Node n
- 54. Reverse Flow Function What does answers? Node n What input should I feed in…
- 55. Reverse Flow Function What does answers? Node n What input should I feed in… In order to see w=c here?
- 56. Reverse Flow Function What does answers? Node n What input should I feed in… In order to see w=c here?
- 57. Reverse Flow Function What does answers? Node n What input should I feed in… In order to see w=c here? Any Integer!
- 58. Reverse Flow Function What does answers? Node n What input should I feed in… In order to see w=c here? Impossible Any Integer!
- 59. Reverse Flow Function What does answers? Node n What input should I feed in… In order to see w=c here? Impossible Any Integer! Asking u=c instead
- 60. Inter-procedural Reverse Flow Function Additional Function Compositions Properties
- 61. Inter-procedural Reverse Flow Function Additional Function Compositions Properties +
- 62. Inter-procedural Reverse Flow Function Additional Function Compositions Properties + =
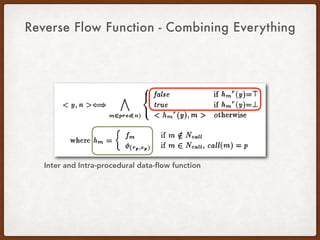
- 63. Reverse Flow Function - Combining Everything
- 64. Reverse Flow Function - Combining Everything Inter and Intra-procedural data-flow function
- 65. Reverse Flow Function - Combining Everything Inter and Intra-procedural data-flow function
- 66. Generalizing the CCP Query q := <[a=c], 10> “Tell me if variable a is equal to constant c at line 10”
- 67. Generalizing the CCP Query q := <[a=c], 10> “Tell me if variable a is equal to constant c at line 10” What c should we ask?
- 68. Generalizing the CCP Query q := <[a=c], 10> “Tell me if variable a is equal to constant c at line 10” What c should we ask? A more useful query: “Tell me the constant value (if it is) of variable a at line 10.” q’ := <[a], 10>
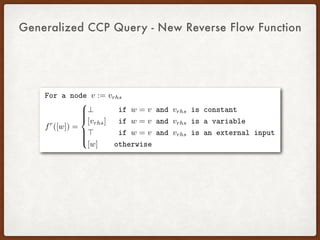
- 69. Generalized CCP Query - New Reverse Flow Function
- 70. Generalized CCP Query - New Reverse Flow Function
- 71. Generalized CCP Query - New Reverse Flow Function Also need to collect the constant value!
- 72. Generalized CCP Query - A Simple Example x = 3 y = 4 a = x r = a + 1 <[a], n>
- 73. Generalized CCP Query - A Simple Example x = 3 y = 4 a = x r = a + 1 <[a], n>
- 74. Generalized CCP Query - A Simple Example x = 3 y = 4 a = x r = a + 1 <[a], n> Final answer for this query
- 75. Generalized CCP Query - A Simple Example x = 3 y = 4 a = x r = a + 1 <[a], n> Final answer for this query
- 76. Generalized CCP Query - A Simple Example x = 3 y = 4 a = x r = a + 1 <[a], n> Final answer for this query
- 77. Takeaways
- 78. Takeaways • Reverse flow function is the core of this algorithm. • It’s join-distributive property allow us to use MFP with it.
- 79. Takeaways • Reverse flow function is the core of this algorithm. • It’s join-distributive property allow us to use MFP with it. • In the generalized query (for CCP):
- 80. Takeaways • Reverse flow function is the core of this algorithm. • It’s join-distributive property allow us to use MFP with it. • In the generalized query (for CCP): • Instead of taking its returned value from reverse functions as the query result, we used it to guide the query propagation process.
- 81. Time and Space Complexity • The same worst-case complexities as Sharir and Pnueli’s exhaustive (iterative worklist-based) data-flow analysis*. • Running Time: O(C x height(L) x |L| x |N|) • C is the maximum number of call sites, and N is the number of nodes. • Space: O(|L| x |N|) *Sharir, Micha, and Amir Pnueli. Two approaches to interprocedural data flow analysis. New York University. Courant Institute of Mathematical Sciences. ComputerScience Department, 1978.
- 82. Related Works
- 84. • Ryder, Barbara G., and Marvin C. Paull. "Incremental data-flow analysis algorithms." ACM Transactions on Programming Languages and Systems (TOPLAS) 10.1 (1988): 1-50.
- 85. • Ryder, Barbara G., and Marvin C. Paull. "Incremental data-flow analysis algorithms." ACM Transactions on Programming Languages and Systems (TOPLAS) 10.1 (1988): 1-50. • Incremental data-flow analysis need to perform full data-flow analysis on first run. Where over-analysis problem might still happen.
- 86. • Ryder, Barbara G., and Marvin C. Paull. "Incremental data-flow analysis algorithms." ACM Transactions on Programming Languages and Systems (TOPLAS) 10.1 (1988): 1-50. • Incremental data-flow analysis need to perform full data-flow analysis on first run. Where over-analysis problem might still happen. • IFDS / IDE
- 87. • Ryder, Barbara G., and Marvin C. Paull. "Incremental data-flow analysis algorithms." ACM Transactions on Programming Languages and Systems (TOPLAS) 10.1 (1988): 1-50. • Incremental data-flow analysis need to perform full data-flow analysis on first run. Where over-analysis problem might still happen. • IFDS / IDE • The authors of this paper argued that their work has “less restrictions on structure of lattice and flow functions”.
- 88. • Ryder, Barbara G., and Marvin C. Paull. "Incremental data-flow analysis algorithms." ACM Transactions on Programming Languages and Systems (TOPLAS) 10.1 (1988): 1-50. • Incremental data-flow analysis need to perform full data-flow analysis on first run. Where over-analysis problem might still happen. • IFDS / IDE • The authors of this paper argued that their work has “less restrictions on structure of lattice and flow functions”. • e.g. This work can give an approximation even with non- distributive flow function.
- 90. • (IFDS / IDE cont’d)
- 91. • (IFDS / IDE cont’d) • IFDS and IDE can not (fully) avoid over-analysis problem.
- 92. • (IFDS / IDE cont’d) • IFDS and IDE can not (fully) avoid over-analysis problem. • e.g. For CCP problem, IFDS / IDE would tell the constant value (if any) for every variables.
- 93. • (IFDS / IDE cont’d) • IFDS and IDE can not (fully) avoid over-analysis problem. • e.g. For CCP problem, IFDS / IDE would tell the constant value (if any) for every variables. • Strom, Robert E., and Daniel M. Yellin. "Extending typestate checking using conditional liveness analysis." IEEE Transactions on Software Engineering 19.5 (1993): 478-485.
- 94. • (IFDS / IDE cont’d) • IFDS and IDE can not (fully) avoid over-analysis problem. • e.g. For CCP problem, IFDS / IDE would tell the constant value (if any) for every variables. • Strom, Robert E., and Daniel M. Yellin. "Extending typestate checking using conditional liveness analysis." IEEE Transactions on Software Engineering 19.5 (1993): 478-485. • Also used the idea of backward and demand-driven program analysis.
- 95. Comments
- 96. What I Think the Paper Should Organize (Larger Box == More Important) The “Normal” Data-Flow Analysis Demand-Driven Data-Flow Analysis w/ Boolean Query Result Generalize To Non-Boolean Query Result (for CCP) Supporting Global Variables / Memory Aliasing
- 97. The Paper’s Organization (Larger Box == More Paragraphs) The “Normal” Data-Flow Analysis
- 98. The Paper’s Organization (Larger Box == More Paragraphs) The “Normal” Data-Flow Analysis Demand-Driven Data-Flow Analysis w/ Boolean Query Result
- 99. The Paper’s Organization (Larger Box == More Paragraphs) The “Normal” Data-Flow Analysis Supporting Global Variables / Memory Aliasing Demand-Driven Data-Flow Analysis w/ Boolean Query Result
- 100. The Paper’s Organization (Larger Box == More Paragraphs) The “Normal” Data-Flow Analysis Generalize To Non-Boolean Query Result (for CCP) Supporting Global Variables / Memory Aliasing Demand-Driven Data-Flow Analysis w/ Boolean Query Result
- 101. The Paper’s Organization (Larger Box == More Paragraphs) The “Normal” Data-Flow Analysis Generalize To Non-Boolean Query Result (for CCP) Supporting Global Variables / Memory Aliasing Demand-Driven Data-Flow Analysis w/ Boolean Query Result
- 102. Other Comments
- 103. Other Comments • The querying mechanism fit really well in Language Server Protocol (LSP), which is getting more attention now.
- 104. Other Comments • The querying mechanism fit really well in Language Server Protocol (LSP), which is getting more attention now. • This paper did a pretty nice survey on related works.
- 105. Other Comments • The querying mechanism fit really well in Language Server Protocol (LSP), which is getting more attention now. • This paper did a pretty nice survey on related works. • Some notations are inconsistent across paragraphs.
- 106. Other Comments • The querying mechanism fit really well in Language Server Protocol (LSP), which is getting more attention now. • This paper did a pretty nice survey on related works. • Some notations are inconsistent across paragraphs. • Amortized Time Complexity Analysis Please!!!
- 107. Summary
- 108. Summary • This work used queries to drive the data-flow analysis process to avoid generating redundant results that would never be used.
- 109. Summary • This work used queries to drive the data-flow analysis process to avoid generating redundant results that would never be used. • The algorithm performed a revered data-flow analysis from the point where users are inquiring. • The reverse data-flow function played an important role.
- 110. Summary • This work used queries to drive the data-flow analysis process to avoid generating redundant results that would never be used. • The algorithm performed a revered data-flow analysis from the point where users are inquiring. • The reverse data-flow function played an important role. • The query algorithm was augmented to support arbitrary result types. In addition to the basic boolean type.
- 111. Summary • This work used queries to drive the data-flow analysis process to avoid generating redundant results that would never be used. • The algorithm performed a revered data-flow analysis from the point where users are inquiring. • The reverse data-flow function played an important role. • The query algorithm was augmented to support arbitrary result types. In addition to the basic boolean type. • Regarding the time complexity, this algorithm is no worse than the exhaustive data-flow analysis. • Just as the incremental data-flow analysis, we hope to see the amortized time complexity.





































![An Example Query in CCP*
q := <[a=c], 10>
“Tell me if variable a is equal to constant c at line 10”](https://image.slidesharecdn.com/presentation-demand-driven-data-flow-analysis-191128041415/85/Paper-Study-Demand-Driven-Computation-of-Interprocedural-Data-Flow-41-320.jpg)






















![Generalizing the CCP Query
q := <[a=c], 10>
“Tell me if variable a is equal to constant c at line 10”](https://image.slidesharecdn.com/presentation-demand-driven-data-flow-analysis-191128041415/85/Paper-Study-Demand-Driven-Computation-of-Interprocedural-Data-Flow-66-320.jpg)
![Generalizing the CCP Query
q := <[a=c], 10>
“Tell me if variable a is equal to constant c at line 10”
What c should we ask?](https://image.slidesharecdn.com/presentation-demand-driven-data-flow-analysis-191128041415/85/Paper-Study-Demand-Driven-Computation-of-Interprocedural-Data-Flow-67-320.jpg)
![Generalizing the CCP Query
q := <[a=c], 10>
“Tell me if variable a is equal to constant c at line 10”
What c should we ask?
A more useful query:
“Tell me the constant value (if it is) of variable a at line 10.”
q’ := <[a], 10>](https://image.slidesharecdn.com/presentation-demand-driven-data-flow-analysis-191128041415/85/Paper-Study-Demand-Driven-Computation-of-Interprocedural-Data-Flow-68-320.jpg)


![Generalized CCP Query - A Simple Example
x = 3
y = 4
a = x
r = a + 1 <[a], n>](https://image.slidesharecdn.com/presentation-demand-driven-data-flow-analysis-191128041415/85/Paper-Study-Demand-Driven-Computation-of-Interprocedural-Data-Flow-72-320.jpg)
![Generalized CCP Query - A Simple Example
x = 3
y = 4
a = x
r = a + 1 <[a], n>](https://image.slidesharecdn.com/presentation-demand-driven-data-flow-analysis-191128041415/85/Paper-Study-Demand-Driven-Computation-of-Interprocedural-Data-Flow-73-320.jpg)
![Generalized CCP Query - A Simple Example
x = 3
y = 4
a = x
r = a + 1 <[a], n>
Final answer for this query](https://image.slidesharecdn.com/presentation-demand-driven-data-flow-analysis-191128041415/85/Paper-Study-Demand-Driven-Computation-of-Interprocedural-Data-Flow-74-320.jpg)
![Generalized CCP Query - A Simple Example
x = 3
y = 4
a = x
r = a + 1 <[a], n>
Final answer for this query](https://image.slidesharecdn.com/presentation-demand-driven-data-flow-analysis-191128041415/85/Paper-Study-Demand-Driven-Computation-of-Interprocedural-Data-Flow-75-320.jpg)
![Generalized CCP Query - A Simple Example
x = 3
y = 4
a = x
r = a + 1 <[a], n>
Final answer for this query](https://image.slidesharecdn.com/presentation-demand-driven-data-flow-analysis-191128041415/85/Paper-Study-Demand-Driven-Computation-of-Interprocedural-Data-Flow-76-320.jpg)



































































![[COSCUP 2021] LLVM Project: The Good, The Bad, and The Ugly](https://cdn.slidesharecdn.com/ss_thumbnails/coscup2021-llvm-210731054723-thumbnail.jpg?width=560&fit=bounds)
![[TGSA Academic Friday] How To Train Your Dragon - Intro to Modern Compiler Te...](https://cdn.slidesharecdn.com/ss_thumbnails/tgsa-academic-friday-how-to-train-your-dragon-191207230024-thumbnail.jpg?width=560&fit=bounds)



























