Practical API Security - PyCon 2019
- 1. @adam_englander Practical API Security Adam Englander, Engineering Manager iovation
- 2. @adam_englander And now, the morning announcements…
- 3. @adam_englander Break will be at 10:15 in the lobby
- 4. @adam_englander Lunch will be from 12:20 - 1:20 In the Gerard Ballroom AB
- 5. @adam_englander There is as much as PyCon could afford Please share power
- 6. @adam_englander Please rate this… https://www.surveymonkey.com/r/YHSX9MC
- 7. @adam_englander Let's set some expectations...
- 8. @adam_englander What are we protecting against?
- 10. @adam_englander How do we provide that protection?
- 11. @adam_englander
- 12. @adam_englander Defense in Depth Transport Layer Security Rate Limiting/Replay Prevention Authentication Data Validation Data Encryption Logging/Tracing Access Control
- 13. @adam_englander Defense in Depth Transport Layer Security Rate Limiting/Replay Prevention Authentication Data Validation Data Encryption Logging/Tracing Access Control
- 14. @adam_englander
- 15. @adam_englander
- 16. @adam_englander Defense in Depth Transport Layer Security Rate Limiting/Replay Prevention Authentication Data Validation Data Encryption Logging/Tracing Access Control
- 17. @adam_englander Replay prevention requires unique requests
- 18. @adam_englander Determine Uniqueness of Request GET / HTTP/1.1 Accept: application/json
- 19. @adam_englander Determine Uniqueness of Request GET / HTTP/1.1 Accept: application/json X-Nonce: 5ed518e8c5c51a64638b2b50c192242d
- 20. @adam_englander Store that unique value in a datastore so you can verify you don't see it again
- 21. @adam_englander Use the add function on the cache to prevent race conditions
- 22. @adam_englander Cache Example if ($token === null) { throw new AuthorizationRequiredException(); } elseif (!$this->cache->add(hash('sha512', $token), 1, 10)) { throw new InvalidRequestException(); }
- 23. @adam_englander Use insert on unique index for RDBMS to prevent race conditions
- 24. @adam_englander Rate limiting requires unique identification for restrictions
- 26. @adam_englander Use the add and increment functions of the cache to prevent race conditions
- 27. @adam_englander Cache Example $key = sprintf("%s|root-post|%s", $userId, $timeSlice); $this->cache->add($key, 0, 1); $total = $this->cache->increment($key);
- 28. @adam_englander Use insert with unique index and update returning in RDBMS to prevent race conditions
- 29. @adam_englander Data stores can be done in three ways.
- 33. @adam_englander Defense in Depth Transport Layer Security Rate Limiting/Replay Prevention Authentication Data Validation Data Encryption Logging/Tracing Access Control
- 34. @adam_englander Do not make authentication part of the body
- 35. @adam_englander Use the Authorization header
- 36. @adam_englander HTTP Basic Authentication Authorization: Basic QWxhZGRpbjpvcGVuIHNlc2FtZQ==
- 37. @adam_englander HTTP Digest Authentication Authorization: Digest username="Awesome", realm=“[email protected]", nonce="dcd98b7102dd2f0e8b11d0f600bfb0c093", uri=“/", qop=auth, nc=00000001, cnonce="0a4f113b", response="6629fae49393a05397450978507c4ef1", opaque="5ccc069c403ebaf9f0171e9517f40e41"
- 38. @adam_englander HTTP Bearer Authentication Authorization: Bearer mF_9.B5f-4.1JqM
- 40. @adam_englander Many APIs do this
- 41. @adam_englander What about never rolling your own crypto?
- 43. @adam_englander No auth service required
- 44. @adam_englander Can use existing JWT libraries to create and validate
- 45. @adam_englander Can be extended beyond auth to provide data validation and MITM protection
- 46. @adam_englander Defense in Depth Transport Layer Security Rate Limiting/Replay Prevention Authentication Data Validation Data Encryption Logging/Tracing Access Control
- 47. @adam_englander Defense in Depth Transport Layer Security Rate Limiting/Replay Prevention Authentication Data Validation Data Encryption Logging/Tracing Access Control
- 50. @adam_englander Method Validation GET /user/abc HTTP/1.1 Accept: application/json
- 51. @adam_englander Method Validation DELETE /user/abc HTTP/1.1 Accept: application/json
- 52. @adam_englander Path Validation GET /user/abc HTTP/1.1 Accept: application/json
- 53. @adam_englander Path Validation GET /user/def HTTP/1.1 Accept: application/json
- 54. @adam_englander Body Validation PATCH /user/abc HTTP/1.1 {"email": "[email protected]"}
- 55. @adam_englander Body Validation PATCH /user/abc HTTP/1.1 {"email": "[email protected]"}
- 57. @adam_englander Status Code Validation HTTP/1.1 200 OK Content-Type: application/json; charset=UTF-8 Content-Length: 21 {"expected": "value"}
- 58. @adam_englander Status Code Validation HTTP/1.1 400 Invalid Request Content-Type: application/json; charset=UTF-8 Content-Length: 21 {"expected": "value"}
- 59. @adam_englander Status Code Validation HTTP/1.1 200 OK Content-Type: application/json; charset=UTF-8 Content-Length: 21 {"expected": "value"}
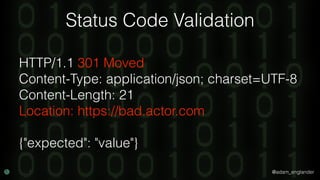
- 60. @adam_englander Status Code Validation HTTP/1.1 301 Moved Content-Type: application/json; charset=UTF-8 Content-Length: 21 Location: https://bad.actor.com {"expected": "value"}
- 61. @adam_englander Header Validation HTTP/1.1 200 OK Content-Type: application/json; charset=UTF-8 Content-Length: 21 Cache-Control: no-cache {"expected": "value"}
- 62. @adam_englander Header Validation HTTP/1.1 200 OK Content-Type: application/json; charset=UTF-8 Content-Length: 21 Cache-Control: max-age=99999999 {"expected": "value"}
- 63. @adam_englander Data Validation HTTP/1.1 200 OK Content-Type: application/json; charset=UTF-8 Content-Length: 21 {"active": false}
- 64. @adam_englander Data Validation HTTP/1.1 200 OK Content-Type: application/json; charset=UTF-8 Content-Length: 21 {"active": true}
- 66. @adam_englander Defense in Depth Transport Layer Security Rate Limiting/Replay Prevention Authentication Data Validation Data Encryption Logging/Tracing Access Control
- 67. @adam_englander Encrypt Data at Rest
- 68. @adam_englander Use a structure format that allows for in-place key rotation and nonce storage
- 69. @adam_englander COSE CBOR Object Signing and Encryption (COSE) Concise Binary Object Representation (CBOR)
- 71. @adam_englander Encrypt Data in Transit
- 74. @adam_englander Defense in Depth Transport Layer Security Rate Limiting/Replay Prevention Authentication Data Validation Data Encryption Logging/Tracing Access Control
- 76. @adam_englander Log in a structured format for easier parsing
- 77. @adam_englander Log all pertinent actions
- 78. @adam_englander Include all data regarding state. Anonymize sensitive data.
- 79. @adam_englander Include origin data to identify bad actors.
- 80. @adam_englander Utilize OpenTracing tools to track all the pertinent things
- 81. @adam_englander Utilize tools like ELK or Greylog to aggregate logs
- 82. @adam_englander Determine anomalous conditions and alert on those conditions.
- 83. @adam_englander And now we code…