Presentation On Com Dcom
- 1. DCOM Technology Katur Bharat Kumar
- 2. What is DCOM? DCOM is just COM with a longer wire DCOM extends COM to support communication among objects on different computers
- 3. Component Object Model COM is a platform-independent, distributed, object-oriented system for creating binary software components that can interact. COM objects can be created with a variety of programming languages. Object- oriented languages, such as C++, provide programming mechanisms that simplify the implementation of COM objects.
- 4. Understanding COM not an object-oriented language but a binary standard COM specifies an object model and programming requirements that enable COM objects (also called COM components) to interact with other objects
- 5. COM Design Principles Binary components Any programming language Any location(in-process, cross-process, cross-machine) Zero sacrifice in-proc performance Simplest model possible Enable extensibility and adaptability
- 6. COM Design Principles.. Encapsulation Black box - no leakage of implementation details All object manipulation through strict interfaces Polymorphism IUnknown via multiple interfaces per class IDispatch “Discoverable”: QueryInterface COM Object IRobot
- 7. Interfaces IUnknown AddRef Release QueryInterface IDispatch GetIDsOfNames GetTypeInfo GetTypeInfoCount Invoke Custom Interfaces
- 8. Notes Your application may have as much as classes as you need. It should implement at least the IUnknown interface. AddRef increments the objects usage count, and Release decrements it. Object may unload itself when the reference count reaches to zero. QueryInterface helps you to query any interface using another one. If you create and object and get the IUnknown interface you can easily access other interfaces. Applications usually query objects whether they have a certain interface. For example the COM runtime queries and object of IMarshall to decide whether custom marshalling or universal marshaller. Internet Explorer searches some certain registry keys, and loads the objects under those keys. It then queries the object of IObjectWithSite interface to decide the object will be run as a plugin. The object queries the IUnknown interface of the loader module for IWebBrowser2. When a page is loaded the plugin asks the browser the IUnknown of the document. The IHTMLDocument2 and IHTMLElement interfaces are queried using the IUnknown interface that we have. IDispatch interface has to be implemented if the object is to be used from scripting languages through automation. The script languages accessed the methods in vtable by name using the methods of IDispatch interface. COM objects also implement their custom interfaces for direct access.
- 9. COM Architecture Communication details handled by the COM run-time
- 10. Note In today's operating systems, processes are shielded from each other. A client that needs to communicate with a component in another process has to use some form of inter-process communication provided by the operating system. COM provides this communication in a completely transparent fashion: it intercepts calls from the client and forwards them to the component in another process. LPC (Local Procedure Call) is used for interprocess communcation. LPC is a system service in the Win32 subsystem. For example all the Win32 API calls are done using LPC. An application that calls the CreateWindow actually packs all of the parameters and send them to the Win32 subsystem. COM uses DCE’s (Distributed Computing Environment specified by Open Software Foundation) RPC (Remote Procedure Call) protocol. DCE was implemented for Windows platform by Digital Equipment Corporation.
- 12. Note The only difference between COM and DCOM is the connection between the client and the server.
- 13. Proxy & Stub
- 14. Notes COM uses a mechanism to pass parameters and return values accross process boundaries. The client calls the functions of the interface proxy, but the application need not worry about the details of the process. The proxy has exactly the same functions as the target interface. The proxy marshalls the data and sends to the server side. The stub gets the data sent from the client proxy and unmarshalls the data. The parameters are extracted and passed to the actual interface. The server implementation feels that the request comes from a real client. In fact the stub calls the function on the server. But the server need not have to worry about these details. The server processes the parameters and returns the parameters to the stub. The stub marshalls the return values and send to the client proxy. The proxy unmarshalls the return values and passed to the client. When an in-process object is involved, COM can simply pass the pointer directly from the object to the client, because that pointer is valid in the client's address space. Calls through that pointer end up directly in the object code, as they should, making the in- process case a fast calling model—just as fast as using raw DLLs This "marshalling" sequence creates a "proxy" object and a "stub" object that handle the cross-process communication details for that interface. COM creates the "stub" in the object's process and has the stub manage the real interface pointer. COM then creates the "proxy" in the client's process, and connects it to the stub. The proxy then supplies the interface pointer that is given to the client. Users may choose to implement their own custom marshalling by implementing the IMarshall interface. The COM runtime first queried the IMarshall interface. If it cannot find one, it uses the universal type library marshalling.
- 15. DCOM Wire Protocol Client Machine Server Machine COM Runtime COM Runtime TCP, UDP COM Client SPX,IPX Proxy Component Net BUI HTTP Other Component
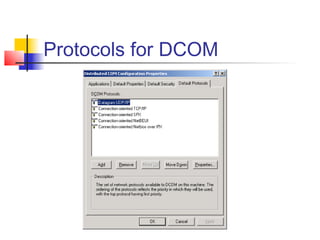
- 16. DCOM Security Secure - Security is designed and built in. Not an option. DCOM uses the extensible security framework provided by Windows NT. Security configurable DCOM stores Access Control Lists for components ACLs can be configured using the DCOM configuration tool (DCOMCNFG) or programmatically using the Windows NT registry and Win32 security functions.
- 17. COM Security Architecture Client Machine Server Machine COM Runtime COM Runtime NTLM COM Client SSL, Certs. Proxy Component NT Kerberos DCE Other Component
- 18. Components & Reuse Use existing tools and components Reduce development time and cost COM components easily configured as DCOM components COM can use many other components COM components are usable by many technologies
- 19. Notes DCOMCNFG configures remote access to COM components. COM can use Java Beans. COM components can be used by scripting languages in Web pages, XML documents, ASP pages, .NET framework, many programming languages even by COBOL.
- 20. Location Transparency COM Object locations are stored in registry Applications make calls using the globally unique CLSID. Path to COM server, or remote computer to run DCOM server is not needed by the application.
- 21. Language Neutrality Various languages can be used to create components. VB, Delphi for rapid development VC++, Java for advanced development Micro Focus COBOL Even more languages can be used to use COM components Additionally scripting languages like VB Script, JScript
- 22. Connection Management Low Bandwidth Header is 28 bytes over DCE-RPC Keep-Alive Messages bundled for all connections between Machines COM employs an efficient pinging protocol to detect if clients are active COM uses reference counting mechanism to do garbage collection
- 23. Efficient and Scalable Multiplexing - Single Port per-protocol, per server process, regardless of # of objects Scalable - Connection-Less Protocols like UDP Preferred Established Connection-Oriented (TCP) Sessions Reused by same client Client Server Client
- 24. Load Balancing DCOM does not transparently provide load balancing Makes it easy to implement load balancing Static load balancing Dynamic load balancing by means of a dedicated referral component
- 25. Platform Neutrality DCOM run-time is available for various platforms Win32 platforms, Solaris, DEC UNIX, HPUX, Linux, MVS, VMS, Mac Cross-Platform Interoperability Standard Per-Platform binary standard Unlike java, DCOM can utilize powerful platform- specific services and optimizations Less abstraction layers prevents additional overheads
- 26. Creating a simple COM server in VC++ 6.0
- 28. New ATL Object
- 30. Add New Method
- 31. Interface Definition Language ... [ object, uuid(79522A15-BA3D-46A5-92D6-DA4BE60646F4), dual, helpstring("ISimple Interface"), pointer_default(unique) ] interface ISimple : IDispatch { [id(1), helpstring("method StringLen")] HRESULT StringLen([in] BSTR str, [out,retval] long* length); }; ...
- 32. Source & Header File Source: STDMETHODIMP CSimple::StringLen(BSTR str, long* length) { *length = SysStringLen(str); return S_OK; } Header: ... public: STDMETHOD(StringLen)(/*[in]*/ BSTR str, /*[out,retval]*/ long* length); ...
- 33. Creating a Simple COM Client #include <stdio.h> #import "SimpleCom.exe" int main(int argc, char* argv[]) { SIMPLECOMLib::ISimplePtr pSimple; long len; CoInitialize(NULL); pSimple.CreateInstance(__uuidof(SIMPLECOMLib::Simple)); len = pSimple->StringLen("sample"); printf("Length = %dn", len); CoUninitialize(); return 0; }
- 34. Exception Handling try { len = pSimple->StringLen("sample"); } catch (_com_error &e) { printf(“%sn”, e.Description()); }
- 35. Registering COM Objects COM dll To register: regsvr32 mycom.dll To un-register: regsvr32 –u mycom.dll COM exe To register: mycom.exe /regserver To un-register: mycom.exe /unregserver
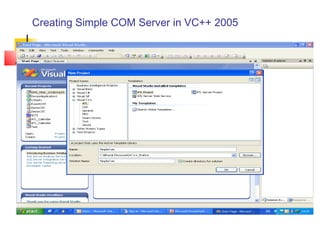
- 36. Creating Simple COM Server in VC++ 2005
- 37. ATLCOM Wizard – Step -1
- 38. ATL Com Wizard – Step -2
- 39. Inserting ATL Component Step -1
- 40. Inserting ATL Component Step - 2
- 41. ATL Object Attributes - 2005
- 42. Add Methods - 2005
- 45. Referances MSDN Library Online Professional ATL COM programming , Richard Grimes, Wrox Publishing
- 46. Useful Sites http://www.kicit.com/freebies/vcpp_source http://newdata.box.sk/bx/c/ http://programmerworld.net/books/visual_c http://msdn2.microsoft.com/en- us/visualc/aa336429.aspx
Editor's Notes
- #27: Location constraints like ODBC access, faster computers.






























![Interface Definition Language
...
[
object,
uuid(79522A15-BA3D-46A5-92D6-DA4BE60646F4),
dual,
helpstring("ISimple Interface"),
pointer_default(unique)
]
interface ISimple : IDispatch
{
[id(1), helpstring("method StringLen")] HRESULT StringLen([in]
BSTR str, [out,retval] long* length);
};
...](https://image.slidesharecdn.com/presentationoncomdcom-13455445593015-phpapp01-120821052342-phpapp01/85/Presentation-On-Com-Dcom-31-320.jpg)
![Source & Header File
Source:
STDMETHODIMP CSimple::StringLen(BSTR str, long* length)
{
*length = SysStringLen(str);
return S_OK;
}
Header:
...
public:
STDMETHOD(StringLen)(/*[in]*/ BSTR str, /*[out,retval]*/
long* length);
...](https://image.slidesharecdn.com/presentationoncomdcom-13455445593015-phpapp01-120821052342-phpapp01/85/Presentation-On-Com-Dcom-32-320.jpg)
![Creating a Simple COM Client
#include <stdio.h>
#import "SimpleCom.exe"
int main(int argc, char* argv[])
{
SIMPLECOMLib::ISimplePtr pSimple;
long len;
CoInitialize(NULL);
pSimple.CreateInstance(__uuidof(SIMPLECOMLib::Simple));
len = pSimple->StringLen("sample");
printf("Length = %dn", len);
CoUninitialize();
return 0;
}](https://image.slidesharecdn.com/presentationoncomdcom-13455445593015-phpapp01-120821052342-phpapp01/85/Presentation-On-Com-Dcom-33-320.jpg)