Program Threats
Download as PPTX, PDF7 likes15,192 views
This document discusses various types of program threats including logic bombs, viruses, worms, and trojan horses. It focuses on viruses, defining them as code fragments embedded in legitimate programs that can spread via email or macros. The document categorizes viruses and provides examples, noting that file viruses append to files, boot sector viruses infect boot sectors, macro viruses spread through documents, and polymorphic/encrypted viruses aim to avoid detection. In summary, it defines computer viruses, explains how they spread, and outlines several categories of viruses along with examples.
1 of 21
Downloaded 285 times




















Ad
Recommended
Program and System Threats



Program and System ThreatsReddhi Basu This document discusses various types of program and system threats including Trojan horses, trapdoors, buffer overflows, worms, viruses, and denial of service attacks. A Trojan horse masquerades as legitimate software to gain unauthorized access. Trapdoors are secret vulnerabilities built into programs by designers. Buffer overflows occur when more data is input than a program expects, potentially allowing code execution. Worms self-replicate to spread while viruses require host files or human action. Examples like the Morris worm and Love Bug virus are provided. Protection involves antivirus software and safe computing practices. The key differences between worms and viruses are also outlined.
Errors in measurement



Errors in measurementRavinder Jarewal The document discusses different types of errors that can occur in measurement. It describes gross errors, systematic errors like instrumental errors and environmental errors, and random errors. It also defines key terms used to analyze errors like limit of reading, greatest possible error, and discusses analyzing measurement data using statistical methods like the mean, standard deviation, variance and histograms. Measurement errors can occur due to issues like parallax, calibration, limits of the measuring device, and are analyzed statistically.
Presentation on operating system



Presentation on operating systemNitish Xavier Tirkey The document presents an overview of operating systems. It begins with an introduction that defines an operating system as software that controls computer resources and provides an interface for users. The document then discusses the structure of operating systems, including their role in managing resources and acting as an interface between hardware and users/programs. It outlines the main functions of operating systems such as process management, memory management, file management, security, and command interpretation. Finally, it briefly describes some popular operating systems like DOS, Unix, and Windows NT and concludes with the importance of operating systems for running applications and using computers.
Operating system security



Operating system securitySarmad Makhdoom This document discusses computer system security and provides information on various topics related to ensuring security. It begins with an introduction to computer security, including internet security, remote sharing, and software installation. It then covers operating system security focusing on access control, supervision, and resource allocation. Statistics on world internet usage and computer penetration rates are presented. The document goes on to discuss external interface security, internal security, surveillance, threat monitoring, access controls, cryptography, viruses, worms, trojans, spyware, specific spyware programs, internet security software options, firewalls, and phishing prevention. Recommended resources on these security topics are listed at the end.
Breast cancer diagnosis machine learning ppt



Breast cancer diagnosis machine learning pptAnkitGupta1476 This document summarizes a presentation on using machine learning to diagnose breast cancer. It introduces machine learning and explains that it uses statistical techniques to allow computer systems to learn from data without being explicitly programmed. It then provides an overview of breast cancer, risk factors, and statistics. It states that machine learning will be used to analyze breast cancer biopsy data to make diagnoses. The document outlines the steps of collecting and exploring the biopsy data, preparing training and test datasets, training a k-nearest neighbors model on the data, and calculating the model's accuracy on the test data using a confusion matrix.
Properties of logarithms



Properties of logarithmsJessica Garcia This document discusses properties of logarithms, including:
1) Logarithms with the same base "undo" each other according to the inverse function relationship between logarithms and exponents.
2) Logarithmic expressions can be expanded using properties to write them as sums or differences of individual logarithmic terms, or condensed into a single logarithm.
3) The change of base formula allows converting between logarithms with different bases, with common uses being to change to base 10 or the base of natural logarithms.
Occupational Health & Safety Presentation



Occupational Health & Safety PresentationMark Zeeman Presentation to (New & Old) employees on OH & S issues. An informed package to refresh & introduce others to issues involved within the workplace. It is focused on everyday issues occuring in work. Provides an awareness of rights & responsibilities of employees & employers. It is expected that any issues unresolved will be voiced objectively as possible. The overall intent is to provide a campaign on issues in both safety and health.
Basics of C programming



Basics of C programmingavikdhupar Introduction to C language. Compiled from different sources available online. Thanks to the original authors.
Threads (operating System)



Threads (operating System)Prakhar Maurya In this presentation, I am explaining about Threads, types of threads, its advantages and disadvantages, difference between Process and Threads, multithreading and its type.
"Like the ppt if you liked the ppt"
LinkedIn - https://in.linkedin.com/in/prakharmaurya
File Management in Operating System



File Management in Operating SystemJanki Shah Contents:
1.File Concepts
2.File Types
3.File Operations
4.Access Methods
5.Directory Structure
6.File System Structure
Os security issues



Os security issuesJOLLUSUDARSHANREDDY The document discusses several important operating system security issues. The operating system must provide protection mechanisms to prevent unauthorized access to processes and resources. It also needs flexibility to configure how resources are shared between processes and change these configurations as needed. Key security issues for an operating system include implementing protection mechanisms, controlling resource sharing, enforcing security policies, and utilizing authentication and authorization.
Process of operating system



Process of operating systemInternational Center for Chemical & Biological Sciences if you want a discription about Process in operating system and Computer Architecture then this presntation will help you.
directory structure and file system mounting



directory structure and file system mountingrajshreemuthiah This document discusses directory structures and file system mounting in operating systems. It describes several types of directory structures including single-level, two-level, hierarchical, tree, and acyclic graph structures. It notes that directories organize files in a hierarchical manner and that mounting makes storage devices available to the operating system by reading metadata about the filesystem. Mounting attaches an additional filesystem to the currently accessible filesystem, while unmounting disconnects the filesystem.
Security & protection in operating system



Security & protection in operating systemAbou Bakr Ashraf This document discusses security and protection mechanisms in operating systems. It begins by defining what security and protection mean in the context of an OS. Protection mechanisms ensure that processes only access authorized objects, while security deals with issues like authentication, threats, and policies. The document then covers topics like authentication, authorization, threats from inside and outside the system, and protection models like the monitor model and multilevel security model. It discusses techniques used by viruses, trojans, and worms to compromise systems. Finally, it defines the components of a protection system and Lampson's protection model.
2 phase locking protocol DBMS



2 phase locking protocol DBMSDhananjaysinh Jhala 1) The two-phase locking protocol requires transactions to acquire locks in two phases - the growing phase where locks can be acquired but not released, and the shrinking phase where locks can be released but not acquired.
2) The two-phase locking protocol ensures conflict serializability by ordering transactions based on their lock points.
3) However, it does not prevent deadlocks and can cause cascading rollbacks if transactions release locks before committing. Modifications like strict two-phase locking prevent this by requiring locks to be held until commit.
Dining philosopher problem operating system 



Dining philosopher problem operating system anushkashastri The document discusses the dining philosophers problem, a classic synchronization problem used to evaluate situations where multiple resources need to be allocated to multiple processes. It was originally formulated by Edsger Dijkstra in 1965 to illustrate challenges of avoiding deadlock. The problem involves 5 philosophers who share 5 chopsticks placed in the center of a table to eat. The problem is to ensure that no philosopher starves while waiting for resources. Semaphores are used as a solution where each chopstick is represented by a semaphore to ensure mutual exclusion and avoid deadlock.
Multithreading



MultithreadingDr. A. B. Shinde The document discusses multithreading and how it can be used to exploit thread-level parallelism (TLP) in processors designed for instruction-level parallelism (ILP). There are two main approaches for multithreading - fine-grained and coarse-grained. Fine-grained switches threads every instruction while coarse-grained switches on long stalls. Simultaneous multithreading (SMT) allows a processor to issue instructions from multiple threads in the same cycle by treating instructions from different threads as independent. This converts TLP into additional ILP to better utilize the resources of superscalar and multicore processors.
Memory management



Memory managementMuhammad Fayyaz This presentation slides you to the essential knowledge of memory management and an idea to create attractive slides
Virtual memory ppt



Virtual memory pptPunjab College Of Technical Education The document discusses virtual memory, including its needs, importance, advantages, and disadvantages. Virtual memory allows a computer to use more memory for programs than is physically installed by storing unused portions on disk. This allows processes to exceed physical memory limits. Page replacement algorithms like FIFO, LRU, and OPT are used to determine which pages to swap in and out between memory and disk.
Chapter 14 - Protection



Chapter 14 - ProtectionWayne Jones Jnr Goals of Protection
Principles of Protection
Domain of Protection
Access Matrix
Implementation of Access Matrix
Access Control
Revocation of Access Rights
Capability-Based Systems
Language-Based Protection
memory hierarchy



memory hierarchysreelakshmikv This document discusses the memory hierarchy in computers. It begins by explaining that computer memory is organized in a pyramid structure from fastest and smallest memory (cache) to slower and larger auxiliary memory. The main types of memory discussed are RAM, ROM, cache memory, and auxiliary storage. RAM is further divided into SRAM and DRAM. The document provides details on the characteristics of each memory type including access speed, volatility, capacity and cost. Diagrams are included to illustrate concepts like RAM, ROM, cache levels and auxiliary devices. Virtual memory is also briefly introduced at the end.
file system in operating system



file system in operating systemtittuajay The document discusses different aspects of file systems and file structures. It describes files as collections of data that have long-term existence, can be shared between processes, and organized hierarchically. File systems provide storage for files and functions to manipulate them, maintaining attributes. Common file structures include sequential, indexed sequential, and direct/hashed files. The document also outlines the components of a file system software architecture and operations performed on directories.
Using Control Flow for Generating Dynamic Content



Using Control Flow for Generating Dynamic ContentPradip Bhattarai The document discusses how program flow can be altered using keywords like if and switch conditional statements. It explains that if statements check if an expression is true and execute one of two statements depending on the result, while switch statements test a variable value and execute the statement for the matching case. The document also covers different types of ASP.NET server controls that generate markup and how controls can be dynamically generated at runtime using control flows.
Deadlock Avoidance in Operating System



Deadlock Avoidance in Operating SystemMohammad Hafiz-Al-Masud Deadlock avoidance methods analyze resource allocation to determine if granting a request would lead to an unsafe state where deadlock could occur. A deadlock happens when multiple processes are waiting indefinitely for resources held by each other in a cyclic dependency. To prevent deadlock, an operating system must have information on current resource availability and allocations, as well as future resource needs. The system only grants requests that will lead to a safe state where there are enough resources for all remaining processes and deadlock is not possible.
Memory management



Memory managementRajni Sirohi The document discusses memory management in operating systems. It covers key concepts like logical versus physical addresses, binding logical addresses to physical addresses, and different approaches to allocating memory like contiguous allocation. It also discusses dynamic storage allocation using a buddy system to merge adjacent free spaces, as well as compaction techniques to reduce external fragmentation by moving free memory blocks together. Memory management aims to efficiently share physical memory between processes using mechanisms like partitioning memory and enforcing protection boundaries.
Communication in client server system.pptx



Communication in client server system.pptxMSivani Client/server communication involves clients sending requests to a server and receiving responses. There are three main communication methods: sockets use IP addresses and port numbers to transfer unstructured data between processes; remote procedure calls allow clients to make function calls to remote servers; and pipes provide one-way or two-way interprocess communication by entering data from one endpoint and consuming it from the other.
Demand paging



Demand pagingTrinity Dwarka Virtual Memory
• Copy-on-Write
• Page Replacement
• Allocation of Frames
• Thrashing
• Operating-System Examples
Background
Page Table When Some Pages
Are Not in Main Memory
Steps in Handling a Page Fault
Virtual memory



Virtual memoryDr. Shashank Shetty Virtual memory allows processes to execute even if they are larger than physical memory by storing portions of processes on disk. When a process attempts to access memory that is not currently loaded, a page fault occurs which brings the required page into memory from disk. This is known as demand paging and allows the operating system to efficiently load only those portions of a process needed for execution, reducing memory usage and improving performance compared to loading the entire process at once.
Computer viruses



Computer virusesMDAZAD53 This document discusses computer viruses and anti-virus packages. It defines malware and viruses, explaining that viruses attach themselves to files and programs to spread. It describes different types of viruses like boot viruses, macro viruses, multipartite viruses, and file infecting viruses. Viruses can damage systems in various ways like interrupting use, modifying settings, and destroying data. The document recommends using antivirus software, firewalls, strong passwords, and updating systems to prevent virus infections.
(Training) Malware - To the Realm of Malicious Code



(Training) Malware - To the Realm of Malicious CodeSatria Ady Pradana Training on July 16, 2017.
This training is the compressed version of Malware Engineering & Crafting.
In this training, we will talk about malware as well as crafting the simple working malware. The goal of this session is to understanding malware internal so one can have tactics to combat it.
Ad
More Related Content
What's hot (20)
Threads (operating System)



Threads (operating System)Prakhar Maurya In this presentation, I am explaining about Threads, types of threads, its advantages and disadvantages, difference between Process and Threads, multithreading and its type.
"Like the ppt if you liked the ppt"
LinkedIn - https://in.linkedin.com/in/prakharmaurya
File Management in Operating System



File Management in Operating SystemJanki Shah Contents:
1.File Concepts
2.File Types
3.File Operations
4.Access Methods
5.Directory Structure
6.File System Structure
Os security issues



Os security issuesJOLLUSUDARSHANREDDY The document discusses several important operating system security issues. The operating system must provide protection mechanisms to prevent unauthorized access to processes and resources. It also needs flexibility to configure how resources are shared between processes and change these configurations as needed. Key security issues for an operating system include implementing protection mechanisms, controlling resource sharing, enforcing security policies, and utilizing authentication and authorization.
Process of operating system



Process of operating systemInternational Center for Chemical & Biological Sciences if you want a discription about Process in operating system and Computer Architecture then this presntation will help you.
directory structure and file system mounting



directory structure and file system mountingrajshreemuthiah This document discusses directory structures and file system mounting in operating systems. It describes several types of directory structures including single-level, two-level, hierarchical, tree, and acyclic graph structures. It notes that directories organize files in a hierarchical manner and that mounting makes storage devices available to the operating system by reading metadata about the filesystem. Mounting attaches an additional filesystem to the currently accessible filesystem, while unmounting disconnects the filesystem.
Security & protection in operating system



Security & protection in operating systemAbou Bakr Ashraf This document discusses security and protection mechanisms in operating systems. It begins by defining what security and protection mean in the context of an OS. Protection mechanisms ensure that processes only access authorized objects, while security deals with issues like authentication, threats, and policies. The document then covers topics like authentication, authorization, threats from inside and outside the system, and protection models like the monitor model and multilevel security model. It discusses techniques used by viruses, trojans, and worms to compromise systems. Finally, it defines the components of a protection system and Lampson's protection model.
2 phase locking protocol DBMS



2 phase locking protocol DBMSDhananjaysinh Jhala 1) The two-phase locking protocol requires transactions to acquire locks in two phases - the growing phase where locks can be acquired but not released, and the shrinking phase where locks can be released but not acquired.
2) The two-phase locking protocol ensures conflict serializability by ordering transactions based on their lock points.
3) However, it does not prevent deadlocks and can cause cascading rollbacks if transactions release locks before committing. Modifications like strict two-phase locking prevent this by requiring locks to be held until commit.
Dining philosopher problem operating system 



Dining philosopher problem operating system anushkashastri The document discusses the dining philosophers problem, a classic synchronization problem used to evaluate situations where multiple resources need to be allocated to multiple processes. It was originally formulated by Edsger Dijkstra in 1965 to illustrate challenges of avoiding deadlock. The problem involves 5 philosophers who share 5 chopsticks placed in the center of a table to eat. The problem is to ensure that no philosopher starves while waiting for resources. Semaphores are used as a solution where each chopstick is represented by a semaphore to ensure mutual exclusion and avoid deadlock.
Multithreading



MultithreadingDr. A. B. Shinde The document discusses multithreading and how it can be used to exploit thread-level parallelism (TLP) in processors designed for instruction-level parallelism (ILP). There are two main approaches for multithreading - fine-grained and coarse-grained. Fine-grained switches threads every instruction while coarse-grained switches on long stalls. Simultaneous multithreading (SMT) allows a processor to issue instructions from multiple threads in the same cycle by treating instructions from different threads as independent. This converts TLP into additional ILP to better utilize the resources of superscalar and multicore processors.
Memory management



Memory managementMuhammad Fayyaz This presentation slides you to the essential knowledge of memory management and an idea to create attractive slides
Virtual memory ppt



Virtual memory pptPunjab College Of Technical Education The document discusses virtual memory, including its needs, importance, advantages, and disadvantages. Virtual memory allows a computer to use more memory for programs than is physically installed by storing unused portions on disk. This allows processes to exceed physical memory limits. Page replacement algorithms like FIFO, LRU, and OPT are used to determine which pages to swap in and out between memory and disk.
Chapter 14 - Protection



Chapter 14 - ProtectionWayne Jones Jnr Goals of Protection
Principles of Protection
Domain of Protection
Access Matrix
Implementation of Access Matrix
Access Control
Revocation of Access Rights
Capability-Based Systems
Language-Based Protection
memory hierarchy



memory hierarchysreelakshmikv This document discusses the memory hierarchy in computers. It begins by explaining that computer memory is organized in a pyramid structure from fastest and smallest memory (cache) to slower and larger auxiliary memory. The main types of memory discussed are RAM, ROM, cache memory, and auxiliary storage. RAM is further divided into SRAM and DRAM. The document provides details on the characteristics of each memory type including access speed, volatility, capacity and cost. Diagrams are included to illustrate concepts like RAM, ROM, cache levels and auxiliary devices. Virtual memory is also briefly introduced at the end.
file system in operating system



file system in operating systemtittuajay The document discusses different aspects of file systems and file structures. It describes files as collections of data that have long-term existence, can be shared between processes, and organized hierarchically. File systems provide storage for files and functions to manipulate them, maintaining attributes. Common file structures include sequential, indexed sequential, and direct/hashed files. The document also outlines the components of a file system software architecture and operations performed on directories.
Using Control Flow for Generating Dynamic Content



Using Control Flow for Generating Dynamic ContentPradip Bhattarai The document discusses how program flow can be altered using keywords like if and switch conditional statements. It explains that if statements check if an expression is true and execute one of two statements depending on the result, while switch statements test a variable value and execute the statement for the matching case. The document also covers different types of ASP.NET server controls that generate markup and how controls can be dynamically generated at runtime using control flows.
Deadlock Avoidance in Operating System



Deadlock Avoidance in Operating SystemMohammad Hafiz-Al-Masud Deadlock avoidance methods analyze resource allocation to determine if granting a request would lead to an unsafe state where deadlock could occur. A deadlock happens when multiple processes are waiting indefinitely for resources held by each other in a cyclic dependency. To prevent deadlock, an operating system must have information on current resource availability and allocations, as well as future resource needs. The system only grants requests that will lead to a safe state where there are enough resources for all remaining processes and deadlock is not possible.
Memory management



Memory managementRajni Sirohi The document discusses memory management in operating systems. It covers key concepts like logical versus physical addresses, binding logical addresses to physical addresses, and different approaches to allocating memory like contiguous allocation. It also discusses dynamic storage allocation using a buddy system to merge adjacent free spaces, as well as compaction techniques to reduce external fragmentation by moving free memory blocks together. Memory management aims to efficiently share physical memory between processes using mechanisms like partitioning memory and enforcing protection boundaries.
Communication in client server system.pptx



Communication in client server system.pptxMSivani Client/server communication involves clients sending requests to a server and receiving responses. There are three main communication methods: sockets use IP addresses and port numbers to transfer unstructured data between processes; remote procedure calls allow clients to make function calls to remote servers; and pipes provide one-way or two-way interprocess communication by entering data from one endpoint and consuming it from the other.
Demand paging



Demand pagingTrinity Dwarka Virtual Memory
• Copy-on-Write
• Page Replacement
• Allocation of Frames
• Thrashing
• Operating-System Examples
Background
Page Table When Some Pages
Are Not in Main Memory
Steps in Handling a Page Fault
Virtual memory



Virtual memoryDr. Shashank Shetty Virtual memory allows processes to execute even if they are larger than physical memory by storing portions of processes on disk. When a process attempts to access memory that is not currently loaded, a page fault occurs which brings the required page into memory from disk. This is known as demand paging and allows the operating system to efficiently load only those portions of a process needed for execution, reducing memory usage and improving performance compared to loading the entire process at once.
Similar to Program Threats (20)
Computer viruses



Computer virusesMDAZAD53 This document discusses computer viruses and anti-virus packages. It defines malware and viruses, explaining that viruses attach themselves to files and programs to spread. It describes different types of viruses like boot viruses, macro viruses, multipartite viruses, and file infecting viruses. Viruses can damage systems in various ways like interrupting use, modifying settings, and destroying data. The document recommends using antivirus software, firewalls, strong passwords, and updating systems to prevent virus infections.
(Training) Malware - To the Realm of Malicious Code



(Training) Malware - To the Realm of Malicious CodeSatria Ady Pradana Training on July 16, 2017.
This training is the compressed version of Malware Engineering & Crafting.
In this training, we will talk about malware as well as crafting the simple working malware. The goal of this session is to understanding malware internal so one can have tactics to combat it.
Computer Viruses and Classification lecture slides ppt



Computer Viruses and Classification lecture slides pptOsama Yousaf This document discusses different types of computer viruses and malware, including macro viruses, logic bombs, boot sector viruses, multipartite viruses, polymorphic viruses, file infectors, Trojan horses, and worms. It provides examples of each type and describes how they infect systems and spread. The document also discusses famous viruses like Melissa and I Love You, as well as methods of protection like antivirus software and firewalls.
Malware: To The Realm of Malicious Code (Training)



Malware: To The Realm of Malicious Code (Training)Satria Ady Pradana Malware comes in many forms and poses increasing threats. The document discusses the basics of how malware works, including propagation techniques to spread, payloads to damage systems, and self-defense mechanisms. It also covers common malware classes like viruses, worms and Trojans. Examples are given of real malware outbreaks like WannaCry and Petya to show how quickly they can spread. Defense strategies include using antivirus software, keeping systems updated, and maintaining backups.
Viruses & Malware



Viruses & MalwareT.J. Schiel Malware is any software intended to harm a computer that is installed without consent. Common types of malware include viruses, worms, Trojans, spyware, and adware. Viruses can replicate and infect files. Worms replicate over networks without user intervention. Trojans appear useful but have hidden malicious functions. Spyware monitors user behavior and personal information. Adware displays advertisements during program use.
Software security



Software securityjes_d Software security aims to protect software from malicious attacks. Common software vulnerabilities include buffer overflows, which occur when more data is written to a buffer than it can hold, overwriting adjacent memory. Other vulnerabilities are format string exploits, SQL injection, and cross-site scripting (XSS) attacks. Malware such as viruses, worms, Trojan horses, and bots also pose security risks by accessing computers without permission and potentially damaging systems.
Virus and antivirus 



Virus and antivirus zain Ul abadin Viruses can infect computers and spread from one system to another. Antivirus software identifies and removes viruses, worms, and other malware. It also protects against future attacks. Antivirus programs scan files and compare them to virus definitions to identify infected files for removal or quarantine. They also work to prevent the spread of viruses by examining files during activities like email and removable media use. General precautions include regularly updating antivirus software and other programs, and scanning removable media for viruses before use.
Ne Course Part One



Ne Course Part Onebackdoor This document provides an overview of computer viruses and data security topics. It discusses different types of malware like viruses, worms, Trojan horses and hybrids. It also covers topics like encryption, firewalls, authentication, virtual private networks, digital certificates, digital signatures, certification authorities and online security assistants. The document aims to educate about computer viruses, data security issues and how to prevent and protect against malware.
Mitppt



MitpptAarti Prakash The document describes various computer security concepts including threats to information systems like viruses, worms, Trojans, and bots. It discusses different types of malware such as file infectors, macro viruses, encrypted viruses, and rootkits. It also outlines security defenses like using updated antivirus software, firewalls, and practicing safe email/web habits by avoiding suspicious attachments or downloads.
Types of Virus & Anti-virus



Types of Virus & Anti-virusDivyesh Rakholiya This document provides information about computer viruses, including what they are, how they spread, different types of viruses, signs that a computer may be infected, and ways to protect against viruses using anti-virus software. It defines viruses and explains that they can replicate and spread without permission. The document then describes several types of viruses like memory resident viruses, direct action viruses, overwrite viruses, and others. It also lists common signs of infection and explains how anti-virus software works to detect and remove viruses, protecting users and their devices.
virus



virusVinod siragaon Computer viruses are programs that can copy themselves and infect computers without permission. They share traits with biological viruses and pass from computer to computer. Some examples of damaging viruses include Mydoom in 2004, Melissa in 1999, and ILOVEYOU in 2000. Viruses work by attaching themselves to other programs or system areas of the disk. They have dormant, propagation, triggering, and execution phases. Anti-virus software uses techniques like pattern recognition, heuristics, integrity checking, and behavior blocking to detect viruses.
Information security



Information securityJAMEEL AHMED KHOSO WORM VIRUS ACCESS CONTROL HOW DO WORM VIRUS/COMPUTER WORMS WORK AND SPREAD HOW TO TELL IF YOU’RE COMPUTER HAS A WORM TRPOJAN TYPES OF TROJAN ACCESS CONTROL DISTRIBUTED DENIAL OF SERVICE SQL INJECTIONS & DATA ATTACK AUTHENTICATION BASIC AUTHENTICATION
Computer viruses



Computer virusesAlfred George Viruses can enter computers in several ways. There are many types of viruses including resident viruses, overwriting viruses, macro viruses, polymorphic viruses, and Trojan horses. It is important to take steps to protect computers such as installing antivirus software, using firewalls, avoiding suspicious emails and downloads, and regularly backing up files.
Computer viruses and prevention techniques



Computer viruses and prevention techniquesPrasad Athukorala Computer viruses can replicate and spread from one computer to another. There are many types of viruses like memory resident viruses, direct action viruses, overwrite viruses, boot sector viruses, macro viruses, and polymorphic viruses. Different viruses infect computers in various ways and hide in different locations. It is important to use antivirus software, firewalls, and avoid opening suspicious email attachments to prevent virus infection. Regularly updating antivirus definitions and being aware of social engineering tricks used by viruses can help keep computers secure.
W 12 computer viruses



W 12 computer virusesInstitute of Management Studies UOP The document discusses various types of computer viruses and malware, how they infect systems, and methods for protection. It describes macro viruses, boot sector viruses, polymorphic viruses, file infectors, Trojan horses, worms, and famous viruses like Melissa and ILOVEYOU. Protection methods include antivirus software that uses virus definitions and behavior analysis to detect viruses, as well as firewalls that block unauthorized network traffic.
RRB JE Stage 2 Computer and Applications Questions Part 5



RRB JE Stage 2 Computer and Applications Questions Part 5CAS Computer viruses, worms, Trojan horses, spyware, and other malware can harm computer systems in various ways. Anti-virus software, firewalls, and other security measures help protect against malware threats. Digital certificates, digital signatures, strong passwords also help secure computer systems and networks from unauthorized access.
Virus&malware



Virus&malwareRobin Garza Viruses & malware come in many forms including computer viruses, worms, Trojan horses, spyware, and adware. Computer viruses can infect systems and replicate without user knowledge. Types of viruses include resident, direct action, overwrite, boot, macro, directory, and polymorphic viruses. Worms replicate to spread to other systems without user intervention. Trojans appear benign but perform malicious actions like unauthorized access. Spyware and adware secretly monitor users or display advertisements.
Malicious software



Malicious softwaremsdeepika This document summarizes various types of malicious software including viruses, worms, trojan horses, logic bombs, and backdoors. It describes how viruses and worms operate by having dormant, propagation, and triggering phases. Viruses can attach to files or reside in memory. Worms replicate over networks to infect other systems. The document also discusses countermeasures like antivirus software, digital immune systems, and efforts to prevent, detect, and trace distributed denial of service attacks.
computervirus.ppt



computervirus.pptPritamSahoo16 This document provides an overview of computer viruses including their history, types, symptoms, and prevention methods. It discusses how the first computer virus was created in 1981 and that now there are millions of viruses. There are eight main types of viruses that can damage systems like boot sector viruses or hijack browsers. Common symptoms of a virus include slow performance, freezing, and unauthorized program activity. The best prevention methods are installing antivirus software, keeping systems updated, avoiding suspicious attachments/websites, and not using pirated software.
Ad
Recently uploaded (20)
How to Manage Opening & Closing Controls in Odoo 17 POS



How to Manage Opening & Closing Controls in Odoo 17 POSCeline George In Odoo 17 Point of Sale, the opening and closing controls are key for cash management. At the start of a shift, cashiers log in and enter the starting cash amount, marking the beginning of financial tracking. Throughout the shift, every transaction is recorded, creating an audit trail.
World war-1(Causes & impacts at a glance) PPT by Simanchala Sarab(BABed,sem-4...



World war-1(Causes & impacts at a glance) PPT by Simanchala Sarab(BABed,sem-4...larencebapu132 This is short and accurate description of World war-1 (1914-18)
It can give you the perfect factual conceptual clarity on the great war
Regards Simanchala Sarab
Student of BABed(ITEP, Secondary stage)in History at Guru Nanak Dev University Amritsar Punjab 🙏🙏
YSPH VMOC Special Report - Measles Outbreak Southwest US 4-30-2025.pptx



YSPH VMOC Special Report - Measles Outbreak Southwest US 4-30-2025.pptxYale School of Public Health - The Virtual Medical Operations Center (VMOC) A measles outbreak originating in West Texas has been linked to confirmed cases in New Mexico, with additional cases reported in Oklahoma and Kansas. The current case count is 795 from Texas, New Mexico, Oklahoma, and Kansas. 95 individuals have required hospitalization, and 3 deaths, 2 children in Texas and one adult in New Mexico. These fatalities mark the first measles-related deaths in the United States since 2015 and the first pediatric measles death since 2003.
The YSPH Virtual Medical Operations Center Briefs (VMOC) were created as a service-learning project by faculty and graduate students at the Yale School of Public Health in response to the 2010 Haiti Earthquake. Each year, the VMOC Briefs are produced by students enrolled in Environmental Health Science Course 581 - Public Health Emergencies: Disaster Planning and Response. These briefs compile diverse information sources – including status reports, maps, news articles, and web content– into a single, easily digestible document that can be widely shared and used interactively. Key features of this report include:
- Comprehensive Overview: Provides situation updates, maps, relevant news, and web resources.
- Accessibility: Designed for easy reading, wide distribution, and interactive use.
- Collaboration: The “unlocked" format enables other responders to share, copy, and adapt seamlessly. The students learn by doing, quickly discovering how and where to find critical information and presenting it in an easily understood manner.
Multi-currency in odoo accounting and Update exchange rates automatically in ...



Multi-currency in odoo accounting and Update exchange rates automatically in ...Celine George Most business transactions use the currencies of several countries for financial operations. For global transactions, multi-currency management is essential for enabling international trade.
K12 Tableau Tuesday - Algebra Equity and Access in Atlanta Public Schools



K12 Tableau Tuesday - Algebra Equity and Access in Atlanta Public Schoolsdogden2 Algebra 1 is often described as a “gateway” class, a pivotal moment that can shape the rest of a student’s K–12 education. Early access is key: successfully completing Algebra 1 in middle school allows students to complete advanced math and science coursework in high school, which research shows lead to higher wages and lower rates of unemployment in adulthood.
Learn how The Atlanta Public Schools is using their data to create a more equitable enrollment in middle school Algebra classes.
UNIT 3 NATIONAL HEALTH PROGRAMMEE. SOCIAL AND PREVENTIVE PHARMACY



UNIT 3 NATIONAL HEALTH PROGRAMMEE. SOCIAL AND PREVENTIVE PHARMACYDR.PRISCILLA MARY J NATIONAL HEALTH PROGRAMMEE
Ultimate VMware 2V0-11.25 Exam Dumps for Exam Success



Ultimate VMware 2V0-11.25 Exam Dumps for Exam SuccessMark Soia Boost your chances of passing the 2V0-11.25 exam with CertsExpert reliable exam dumps. Prepare effectively and ace the VMware certification on your first try
Quality dumps. Trusted results. — Visit CertsExpert Now: https://www.certsexpert.com/2V0-11.25-pdf-questions.html
Biophysics Chapter 3 Methods of Studying Macromolecules.pdf



Biophysics Chapter 3 Methods of Studying Macromolecules.pdfPKLI-Institute of Nursing and Allied Health Sciences Lahore , Pakistan. This chapter provides an in-depth overview of the viscosity of macromolecules, an essential concept in biophysics and medical sciences, especially in understanding fluid behavior like blood flow in the human body.
Key concepts covered include:
✅ Definition and Types of Viscosity: Dynamic vs. Kinematic viscosity, cohesion, and adhesion.
⚙️ Methods of Measuring Viscosity:
Rotary Viscometer
Vibrational Viscometer
Falling Object Method
Capillary Viscometer
🌡️ Factors Affecting Viscosity: Temperature, composition, flow rate.
🩺 Clinical Relevance: Impact of blood viscosity in cardiovascular health.
🌊 Fluid Dynamics: Laminar vs. turbulent flow, Reynolds number.
🔬 Extension Techniques:
Chromatography (adsorption, partition, TLC, etc.)
Electrophoresis (protein/DNA separation)
Sedimentation and Centrifugation methods.
Marie Boran Special Collections Librarian Hardiman Library, University of Gal...



Marie Boran Special Collections Librarian Hardiman Library, University of Gal...Library Association of Ireland Phoenix – A Collaborative Renewal of Children’s and Young People’s Services Clare Doyle - Cork City Libraries
YSPH VMOC Special Report - Measles Outbreak Southwest US 5-3-2025.pptx



YSPH VMOC Special Report - Measles Outbreak Southwest US 5-3-2025.pptxYale School of Public Health - The Virtual Medical Operations Center (VMOC) A measles outbreak originating in West Texas has been linked to confirmed cases in New Mexico, with additional cases reported in Oklahoma and Kansas. The current case count is 817 from Texas, New Mexico, Oklahoma, and Kansas. 97 individuals have required hospitalization, and 3 deaths, 2 children in Texas and one adult in New Mexico. These fatalities mark the first measles-related deaths in the United States since 2015 and the first pediatric measles death since 2003.
The YSPH Virtual Medical Operations Center Briefs (VMOC) were created as a service-learning project by faculty and graduate students at the Yale School of Public Health in response to the 2010 Haiti Earthquake. Each year, the VMOC Briefs are produced by students enrolled in Environmental Health Science Course 581 - Public Health Emergencies: Disaster Planning and Response. These briefs compile diverse information sources – including status reports, maps, news articles, and web content– into a single, easily digestible document that can be widely shared and used interactively. Key features of this report include:
- Comprehensive Overview: Provides situation updates, maps, relevant news, and web resources.
- Accessibility: Designed for easy reading, wide distribution, and interactive use.
- Collaboration: The “unlocked" format enables other responders to share, copy, and adapt seamlessly. The students learn by doing, quickly discovering how and where to find critical information and presenting it in an easily understood manner.
CURRENT CASE COUNT: 817 (As of 05/3/2025)
• Texas: 688 (+20)(62% of these cases are in Gaines County).
• New Mexico: 67 (+1 )(92.4% of the cases are from Eddy County)
• Oklahoma: 16 (+1)
• Kansas: 46 (32% of the cases are from Gray County)
HOSPITALIZATIONS: 97 (+2)
• Texas: 89 (+2) - This is 13.02% of all TX cases.
• New Mexico: 7 - This is 10.6% of all NM cases.
• Kansas: 1 - This is 2.7% of all KS cases.
DEATHS: 3
• Texas: 2 – This is 0.31% of all cases
• New Mexico: 1 – This is 1.54% of all cases
US NATIONAL CASE COUNT: 967 (Confirmed and suspected):
INTERNATIONAL SPREAD (As of 4/2/2025)
• Mexico – 865 (+58)
‒Chihuahua, Mexico: 844 (+58) cases, 3 hospitalizations, 1 fatality
• Canada: 1531 (+270) (This reflects Ontario's Outbreak, which began 11/24)
‒Ontario, Canada – 1243 (+223) cases, 84 hospitalizations.
• Europe: 6,814
One Hot encoding a revolution in Machine learning



One Hot encoding a revolution in Machine learningmomer9505 A brief introduction to ONE HOT encoding a way to communicate with machines
Understanding P–N Junction Semiconductors: A Beginner’s Guide



Understanding P–N Junction Semiconductors: A Beginner’s GuideGS Virdi Dive into the fundamentals of P–N junctions, the heart of every diode and semiconductor device. In this concise presentation, Dr. G.S. Virdi (Former Chief Scientist, CSIR-CEERI Pilani) covers:
What Is a P–N Junction? Learn how P-type and N-type materials join to create a diode.
Depletion Region & Biasing: See how forward and reverse bias shape the voltage–current behavior.
V–I Characteristics: Understand the curve that defines diode operation.
Real-World Uses: Discover common applications in rectifiers, signal clipping, and more.
Ideal for electronics students, hobbyists, and engineers seeking a clear, practical introduction to P–N junction semiconductors.
Introduction to Vibe Coding and Vibe Engineering



Introduction to Vibe Coding and Vibe EngineeringDamian T. Gordon Introduction to Vibe Coding and Vibe Engineering
pulse ppt.pptx Types of pulse , characteristics of pulse , Alteration of pulse



pulse ppt.pptx Types of pulse , characteristics of pulse , Alteration of pulsesushreesangita003 what is pulse ?
Purpose
physiology and Regulation of pulse
Characteristics of pulse
factors affecting pulse
Sites of pulse
Alteration of pulse
for BSC Nursing 1st semester
for Gnm Nursing 1st year
Students .
vitalsign
GDGLSPGCOER - Git and GitHub Workshop.pptx



GDGLSPGCOER - Git and GitHub Workshop.pptxazeenhodekar This presentation covers the fundamentals of Git and version control in a practical, beginner-friendly way. Learn key commands, the Git data model, commit workflows, and how to collaborate effectively using Git — all explained with visuals, examples, and relatable humor.
Exploring-Substances-Acidic-Basic-and-Neutral.pdf



Exploring-Substances-Acidic-Basic-and-Neutral.pdfSandeep Swamy Exploring Substances:
Acidic, Basic, and
Neutral
Welcome to the fascinating world of acids and bases! Join siblings Ashwin and
Keerthi as they explore the colorful world of substances at their school's
National Science Day fair. Their adventure begins with a mysterious white paper
that reveals hidden messages when sprayed with a special liquid.
In this presentation, we'll discover how different substances can be classified as
acidic, basic, or neutral. We'll explore natural indicators like litmus, red rose
extract, and turmeric that help us identify these substances through color
changes. We'll also learn about neutralization reactions and their applications in
our daily lives.
by sandeep swamy
The ever evoilving world of science /7th class science curiosity /samyans aca...



The ever evoilving world of science /7th class science curiosity /samyans aca...Sandeep Swamy The Ever-Evolving World of
Science
Welcome to Grade 7 Science4not just a textbook with facts, but an invitation to
question, experiment, and explore the beautiful world we live in. From tiny cells
inside a leaf to the movement of celestial bodies, from household materials to
underground water flows, this journey will challenge your thinking and expand
your knowledge.
Notice something special about this book? The page numbers follow the playful
flight of a butterfly and a soaring paper plane! Just as these objects take flight,
learning soars when curiosity leads the way. Simple observations, like paper
planes, have inspired scientific explorations throughout history.
YSPH VMOC Special Report - Measles Outbreak Southwest US 4-30-2025.pptx



YSPH VMOC Special Report - Measles Outbreak Southwest US 4-30-2025.pptxYale School of Public Health - The Virtual Medical Operations Center (VMOC)
Biophysics Chapter 3 Methods of Studying Macromolecules.pdf



Biophysics Chapter 3 Methods of Studying Macromolecules.pdfPKLI-Institute of Nursing and Allied Health Sciences Lahore , Pakistan.
Marie Boran Special Collections Librarian Hardiman Library, University of Gal...



Marie Boran Special Collections Librarian Hardiman Library, University of Gal...Library Association of Ireland
YSPH VMOC Special Report - Measles Outbreak Southwest US 5-3-2025.pptx



YSPH VMOC Special Report - Measles Outbreak Southwest US 5-3-2025.pptxYale School of Public Health - The Virtual Medical Operations Center (VMOC)
Ad
Program Threats
- 1. Program ThreatsVirus & logic bombPrepared and presented by :Medhat Dawoud5/10/20101
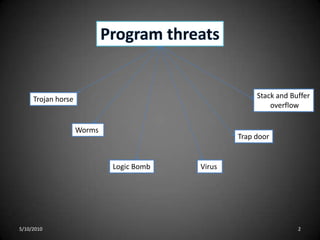
- 2. Program threatsStack and BufferoverflowTrojan horseWorms Trap doorLogic BombVirus 5/10/20102
- 3. Logic BombProgram that initiates a security incident under certain circumstances.Known by the Mentor Programmers (or any other one want to be professional in IT world).5/10/20103
- 4. VirusCode fragment embedded in legitimate program.
- 5. How do viruses work ?
- 6. Very specific to CPU architecture, operating system, applications.
- 7. Usually borne via email or as a macro.5/10/20104
- 8. Virus Con."payload" of a virus is the part of the software that actually does the damage; the rest of the virus is used to break the security.Virus dropper inserts virus onto the system.virus signature is a pattern (a series of bytes) that can be used to identify the virus .5/10/20105
- 9. Virus CategoriesMany categories of viruses, literally many thousands of viruses so that you can find a virus in two or more categories:FileBootMacroSource codePolymorphicEncryptedStealthTunnelingMultipartiteArmored5/10/20106
- 10. FileAppend itself to a file.Change the start of the program to its code.Known as parasitic viruses.usually with extensions .BIN, .COM, .EXE, .OVL, .DRV.5/10/20107
- 11. BootThe boot sector carries the Mater Boot Record (MBR) which read and load the operating system.Boot-sector viruses infect computer systems by copying code either to the boot sector on a floppy disk or the partition table on a hard disk.Executed every time the system is booting.Known as memory viruses.5/10/20108
- 12. 5/10/20109
- 13. Example for :Wreak havoc5/10/201010
- 14. MacroWritten in a high-level language.macros start automatically when a document is opened or closed (word – Excel).can be spread through e-mail attachments, discs, networks, modems, and the Internet.5/10/201011
- 15. Viruses for freeAntivirus withMillions $$5/10/201012
- 16. Source codeLooks for a source code and modifies it to include the virus and to help spread the virus.5/10/201013
- 17. 5/10/201014
- 18. PolymorphicChange virus’s signature each time.It’s designed to avoid detection by antivirus software.A polymorphic virus acts like a chameleon.5/10/201015
- 19. EncryptedEncrypted virus to avoid detection.It has a decryption code along with the encrypted virus.5/10/201016
- 20. StealthIt use some tactics to avoid detection such as altering its file size, concealing itself in memory, and Modifies parts of the system that can be used to detect it. in fact, the first computer virus, was a stealth virus5/10/201017
- 21. TunnelingInstall itself in the interrupt-handler chain or in device drivers attempting to bypass detection.Try to intercept the actions before the anti-virus software can detect the malicious code.5/10/201018
- 22. MultipartiteInfect multiple parts of the system.Including boot sector, memory, and files.So it’s difficult to be detected by the antivirus scanner.5/10/201019
- 23. ArmoredThe most dangerous type. The virus may use methods to make tracing, disassembling, and reverse engineering its code more difficult.Virus droppers and other full files which are part of a virus infestation are hidden.5/10/201020



