Protect Identities and Access to resources with Azure Active Directory
- 2. @ManageDevices #HTMDConf2021 Speaker Protect Identities and Access to Resources with Azure Active Directory Vignesh Ganesan Enterprise Cloud Architect & Technology Strategist @cloudvignesh https://www.linkedin.com/in/vignesh-ganesan-mcse-mcsa- mct-itilv3-9246384a/
- 7. @ManageDevices #HTMDConf2021 Azure AD DS B2B collaboration Azure AD B2C Azure AD offers depth and breadth Identity and access management for employees, partners, and customers Dynamic groups Self-service capabilities Azure AD Connect Conditional access Microsoft Authenticator— password-less access Azure AD Join MDM-auto enrollment/ Enterprise State Roaming Security reporting Identity protection Privileged identity management HR App integration Access reviews Connect health Remote access to on-premises apps Addition of custom cloud apps Access panel/MyApps Provisioning/ deprovisioning Group-based licensing Multi-factor authentication Office 365 App Launcher SSO to SaaS
- 9. @ManageDevices #HTMDConf2021 Secure access to resources with strong authentication
- 10. @ManageDevices #HTMDConf2021 SMS, Voice Hard Tokens OTP Windows Hello FIDO2 Security key Push notification Soft Tokens OTP Microsoft Authenticator Biometrics Azure AD Multi-Factor Authentication Verify user identities with strong authentication to establish trust We support a broad range of multi-factor authentication options Including password-less technology Multi-factor authentication prevents 99.9% of identity attacks
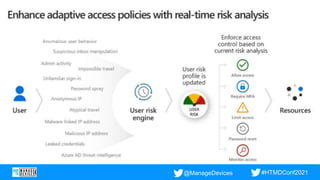
- 11. @ManageDevices #HTMDConf2021 How it works: Azure AD Multi-Factor Authentication
- 13. @ManageDevices #HTMDConf2021 Authentication method strength and security How each authentication method works Ref : https://docs.microsoft.com/en-us/azure/active-directory/authentication/concept-authentication-methods
- 14. @ManageDevices #HTMDConf2021 Enforce granular control with adaptative policies
- 17. @ManageDevices #HTMDConf2021 Azure AD Conditional Access + Microsoft Defender for Cloud Apps
- 19. @ManageDevices #HTMDConf2021 Azure AD · Conditional Access · Report- only mode Evaluate CA policies without enforcing grant or session controls, no impact on users Visualize impact of multiple CA policies using the new Conditional Access Insights workbook
- 20. @ManageDevices #HTMDConf2021 Conditional Access -Block legacy Authentication by default 68% 82%
- 21. @ManageDevices #HTMDConf2021 Block legacy authentication
- 22. @ManageDevices #HTMDConf2021 Conditional Access Insights and Troubleshooting • Details how each Conditional Access policy is evaluated at sign-in Insights and Reporting • Gaps in Conditional Access policy coverage • Impact of Conditional Access policies across the organization
- 23. @ManageDevices #HTMDConf2021 Conditional Access · User-risk policy 1. 2. 3.
- 24. @ManageDevices #HTMDConf2021 Automate risk detection and remediation
- 25. @ManageDevices #HTMDConf2021 Azure AD Identity Protection
- 27. @ManageDevices #HTMDConf2021 Azure AD Identity Protection Risk types
- 28. @ManageDevices #HTMDConf2021 Azure AD Identity protection policies Ref : https://docs.microsoft.com/en-us/azure/active-directory/identity-protection/concept-identity-protection- policies
- 29. @ManageDevices #HTMDConf2021 MFA Conditional Access Microsoft Defender for Cloud Apps Identity Protection
- 30. @ManageDevices #HTMDConf2021 References: https://docs.microsoft.com/en-IN/azure/active-directory/authentication/concept-mfa-howitworks https://docs.microsoft.com/en-in/azure/active-directory/conditional-access/overview What is Conditional Access App Control in Microsoft Cloud App Security? https://docs.microsoft.com/en-us/cloud-app-security/proxy-intro-aad https://docs.microsoft.com/en-us/cloud-app-security/proxy-deployment-aad https://techcommunity.microsoft.com/t5/itops-talk-blog/what-s-the-difference-between-azure-active- directory-identity/ba-p/1320887 It's Time to Hang Up on Phone Transports for Authentication - Microsoft Tech Community All your creds are belong to us! - Microsoft Tech Community Thank you Q&A
Editor's Notes
- #5: Talk track: We are in an era of unprecedented economic uncertainty. Many organizations face constrained resources as they navigate new business challenges. Virtually overnight, companies have seen the need to accelerate digital transformation, which ensures worker productivity and responds to rapidly shifting customer expectations. As the technology, business models, and overall landscape evolves, the way people work has changed: we no longer expect to access the myriad of corporate resources solely from the office and on company-owned devices. In many ways, every company is now a technology company, providing services for their customers and employees. And as security teams are charged with protecting an ever-growing digital footprint, they now face added pressure to cut costs. To secure their environments, organizations must develop new digital capabilities and break down data silos. Data and information are the lifeblood of the transformation, but they also increasingly attract cybercriminal activity. Traditional security approaches have failed us. A hardened perimeter (privileged corporate network) is, at best, a psychological security blanket, but it won’t hold. Siloed on-premises tools and datasets hinder visibility, correlation, and automation. Paradoxically, adding more tools typically makes you less secure due to compatibility issues and assumptions about your coverage. On top of all of this—and perhaps because of it—the cost and number of breaches increase every year. As governments try to keep up, regulatory rules are constantly changing, and the cost of compliance increases as well. Over 1,000 regulatory bodies around the world release an average of 217 updates per day.1 Keeping up isn’t easy. Since you can’t be compliant without first being secure, everything starts with security. 1 https://images.marketing.refinitiv.com/Web/ThomsonReutersFinancialRisk/%7Bf798765e-1a9b-4975-98c9-a133945d21e8%7D_Cost_of_compliance_2020_FINAL230620.pdf
- #6: Talk track: Taken together, all the trends we’ve outlined represent a shared challenge to IT security. Organizations find themselves responsible for protecting an overlapping web of technologies, many of which they may not own or manage outright. With so many devices, different user groups, and so much corporate data, traditional perimeter-based security models simply can’t keep up with the sophistication of today’s threats. Neither can the traditional models provide the visibility and controls they need to secure today’s highly distributed and hyper-mobile environment. We can no longer believe everything behind the corporate firewall will be safe. We need a security model that better adapts to the reality of the world we live in.
- #8: All this and more for less $$$ than Okta
- #11: Passwords are the weakest link in a security chain and a single point of failure without any additional verification. That’s why we believe strongly that if you only do one thing to help protect yourself, it should be to turn on multi-factor authentication (MFA) – which can prevent 99.9% of identity attacks. We support a broad range of authentication options to fit the needs for your business and your users. Passwordless methods help make MFA more convenient for users. While not all MFA is passwordless – yet – <CLICK> these forms of passwordless technology are also multi-factor authentication. Microsoft, Google, and other leaders in the industry have been developing standards to enable a simpler and stronger authentication experience across the web and mobile devices in a group called FIDO (Fast IDentity Online). The recently developed FIDO2 standard enables users to authenticate easily and securely without requiring a password to eliminate phishing. Microsoft MFA credentials that are ‘passwordless’ include: Microsoft Authenticator: For the greatest flexibility, convenience, and cost, we recommend using the Microsoft Authenticator mobile app. Microsoft Authenticator supports biometrics, push notifications, and one-time passcodes for any Azure AD-connected app and is free to download from the Apple and Android app stores. Windows Hello: For a great built-in experience on the PC, we recommend using Windows Hello. It uses your face or fingerprint to sign in automatically. FIDO2 Security keys are now available from several of our partners like Yubico, Feitian Technologies, and HID Global in a USB, NFC-enabled badge, or biometric key. We already have over 100M users of passwordless authentication and this number is about to get bigger! At Ignite we announced that in Q1 2020 we will extend passwordless authentication (in public preview) to include support for hybrid environments. If you’re hesitant to turn on MFA, there are ways to minimize disruption and make it a smooth transition for your users. With the right access policies, users are only prompted for MFA when it’s necessary. You can also use self-service portals for quick registration and password reset—saving your Help Desk thousands, or even millions, of dollars each year.
- #16: 15
- #17: Talk track: Based on Microsoft research, we’ve seen a 300-percent increase in identity attacks over the past year1, making it more critical than ever to build an identity-driven security practice based upon strong authentication and intelligent adaptive access policies. Passwords are the weakest link in a security chain. Without any additional verification, they are a single point of failure. We strongly believe that if you do just one thing to help protect yourself, you should turn on multi-factor authentication (MFA)—which can prevent 99.9 percent of identity attacks.1 To minimize user friction and ensure MFA adoption, prompt users for MFA only when necessary through adaptive access policies. We built our Microsoft Conditional Access intelligent policy engine specifically to satisfy this need. Its robust controls allow you to define specific conditions for how users authenticate and gain access to apps and data. You can customize and manage automated policies and receive reporting on the policies you apply to each sign-in. Microsoft Conditional Access enables you to enforce the core principle of Zero Trust: never trust, always verify. While Microsoft Conditional Access protects resources from suspicious requests, Azure AD Identity Protection goes further by providing ongoing risk detection and remediating suspicious user accounts. Identity Protection keeps you informed about suspicious user and sign-in behavior in your environment 24/7. Identity Protection’s automatic response proactively prevents compromised identities from being abused. We’ve honed our identity protection engine through machine learning that takes in more than 71TB of identity-related security signals.1 1Source: Microsoft Internal
- #22: Apps using their own legacy methods to authenticate with Azure AD and access company data, pose another risk for organizations. Examples of apps using legacy authentication are POP3, IMAP4, or SMTP clients. Legacy authentication apps authenticate on behalf of the user and prevent Azure AD from doing advanced security evaluations. The alternative, modern authentication, will reduce your security risk, because it supports multi-factor authentication and Conditional Access. We recommend the following three actions: Block legacy authentication if you use AD FS. Setup SharePoint Online and Exchange Online to use modern authentication. If you have Azure AD Premium, use Conditional Access policies to block legacy authentication, otherwise use Azure AD Security Defaults.
- #26: Identity Protection is a tool that allows organizations to accomplish three key tasks: Automate the detection and remediation of identity-based risks. Investigate risks using data in the portal. Export risk detection data to your SIEM.