Protecting Your Key Asset – Data Protection Best Practices V2.0 Final
- 1. Protecting your Key Asset – Data Protection Best Practices Vinod Kumar M Technology Evangelist Microsoft Corporation www.ExtremeExperts.com
- 2. Agenda “ Best Practices” is a broad area This talk focuses on operational tasks Look at various Data aspects
- 3. “ Security…But isn’t that the Admin’s Job?”
- 4. Understanding Basic Security Restricting user access Disabling services and restricting service configuration Reducing the surface area of attack for new features
- 5. Defense in Depth Always design your countermeasures to have at least two levels of defense This means that you put your defenses in serially rather than in parallel; attackers needs to overcome A and B – not A or B Use all the available countermeasures – technology, process, people Countermeasures and vulnerabilities are really two sides of the same coin
- 6. Incidents Reported Industry Wide CERT/CC incident statistics 1988 through 2006 Incident: single security issue grouping together all impacts of that that issue Issue: disruption, DOS, loss of data, misuse, damage, loss of confidentiality Source: http://www.cert.org/stats/cert_stats.html 0 20000 40000 60000 80000 100000 120000 160000 180000 '88 '90 '92 '94 '96 '98 '00 '02
- 7. Know Your Enemy Port Scanners Black Hat Community Sharing Brute Force pwd crackers Dictionary Based pwd crackers Network Sniffers De-compilers Debuggers Cracker Tools
- 8. Mobile Device – Security Aspect
- 9. Mobile – Entry Points Access to Device Access to Store-Data Access to wireless networks
- 10. Mobile – Security Practices Risk Analysis Make Security policies Password Anti-Virus Software Encryption Need-to-know Data store
- 11. Mobile – Security Practices Authentication Perimeter Security Encryption Data Encryption – Pocket PC (SQL CE – 128 bit encryption) App Encryption – .NET CF & High Encryption Pack Information Service Encryption Network Encryption Lock- Down Functionality
- 13. Where is Customer’s Data Stored? Q: Where is the biggest data exposure risk? SQL
- 14. Clients Documents Where do customers’ users keep their documents? User Profile Outlook, Sharepoint, Desktop, Temp, IE… per-machine data Search index, offline file cache, pagefile… Non-standard locations … ISV & in-house apps
- 15. What is EFS?
- 16. Encrypting File System Privacy of data that goes beyond access control Protect confidential data on laptops Configurable approach to data recovery Integrated with core operating system components Windows NT File System - NTFS Crypto API key management LSA security policy Transparent and very high performance
- 17. What EFS is not… A way to protect local user credentials A way to protect data in transit (think IPSec) A way to protect business transaction documents (think Windows Rights Management)
- 18. EFS File Encryption RNG Data decryption field generation (RSA) Data recovery field generation (RSA) DDF DRF User’s public key Recovery agent’s public key in recovery policy Randomly- generated file encryption key (FEK) File encryption (e.g. AES) A quick brown fox jumped... *#$fjda^j u539!3t t389E *&
- 19. EFS File Decryption *#$fjda^j u539!3t t389E *& DDF A quick brown fox jumped... DDF extraction (RSA) File decryption (e.g. AES) File encryption key DDF is decrypted using the user’s private key to get the file encryption key DDF contains file encryption key encrypted under user’s public key User’s private key
- 20. EFS File Recovery *#$fjda^j u539!3t t389E *& DRF A quick brown fox jumped... DRF extraction (RSA) File decryption (e.g. AES) File encryption key DRF is decrypted using the DRA ’s private key to get the file encryption key DRF contains file encryption key encrypted under DRA ’s public key DRA ’s private key
- 21. EFS best practices: recovery No local Recovery Agents Prevents data comprise in “stolen laptop” scenario Prevents out-of-process data recovery… if encrypted data needs to be recovered, it should be an audited operation Have at least 2 Recovery Agents per domain Encrypt directories, not files Ensures that temp files created in process are also encrypted Prevents data recovery from free space on the file system Encrypt CSC cache (Offline Files) Protects temporary files that maybe written during application execution
- 23. Windows Rights Management Services (RMS) Information protection technology that augments security strategies Users can easily safeguard sensitive information from unauthorized use Organizations can centrally manage internal information usage policies Uses RMS Server, RMS Client and RMS-enabled apps RMS protects information both online and offline, inside and outside of the firewall.
- 24. RMS Publishing Flow (“online”) File Recipient File Author RM Server Author creates a file and defines a set of rights and rules. Application encrypts file and sends unsigned “publishing license” to RMS; Server signs and returns publishing license. Author distributes file. Application renders file and enforces rights. Recipient clicks file to open, the application calls to RMS which validates the user and the request and issues the “use license”. Database Server File Server
- 25. If I could choose one, which one would I choose when? EFS – to encrypt all local data files automatically, under my domain account, to minimize risk of offline attack RMS – to share encrypted files easily among a group of people, or send them encrypted over the wire to any storage medium
- 27. What are Principals? Principals Permissions Securables Server Role SQL Server Login SQL Server Windows Group Domain User Account Local User Account Windows User Database Role Application Role Group Database
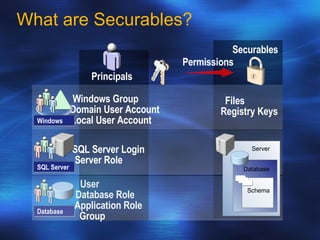
- 28. What are Securables? Principals Permissions Securables Files Registry Keys Server Schema Database Server Role SQL Server Login SQL Server Windows Group Domain User Account Local User Account Windows User Database Role Application Role Group Database
- 29. What are Permissions? Principals Permissions Securables Files Registry Keys Server Schema Database CREATE ALTER DROP CONTROL CONNECT SELECT EXECUTE UPDATE DELETE INSERT TAKE OWNERSHIP VIEW DEFINITION BACKUP GRANT/REVOKE/DENY ACL Server Role SQL Server Login SQL Server Windows Group Domain User Account Local User Account Windows User Database Role Application Role Group Database
- 30. Database Security Surface Area Reduction Authentication Mode Password Policies enforcement Administrative Privileges Catalog Security Encryption Auditing
- 31. Demo …
- 32. Summary Security is integral part of all software Maximize SQL Security to protect sensitive data Encryption is cool : Use it carefully though Understand the password policies of organization Block standard/un-used default ports Lastly, Understand all the entry points to your application
- 33. Questions ?
- 34. Resources Encrypting File System in Windows XP and Windows Server 2003 http://www.microsoft.com/technet/prodtechnol/winxppro/deploy/cryptfs.mspx Best practices for the Encrypting File System http://support.microsoft.com/default.aspx?scid=kb;en-us;223316&sd=tech What's New in Security for Windows XP Professional and Windows XP Home Edition http://www.microsoft.com/technet/prodtechnol/winxppro/evaluate/xpsec.mspx
- 35. Resources SQL Server : Security Blog http://blogs.msdn.com/lcris/ SQL Server Security and Protection http://www.microsoft.com/technet/prodtechnol/sql/2005/library/security.mspx What's New in Security for Windows XP http://www.microsoft.com/technet/prodtechnol/winxppro/evaluate/xpsec.mspx