Protocols for wireless sensor networks
Wireless Sensor Network (WSN) consists of sensor nodes which interact with each other through physical parameters like sunlight, wind, vibration, humidity etc. Routing protocols provide an optimal data transmission route from sensor nodes to sink node to save energy of nodes. From Base Station (BS) Sensor node sends and receives data to or from wireless stations. Clustering mechanism is one of the popular routing mechanisms used in WSN for optimizing the problem in sensor nodes. There are two types of clustering schemes known as homogeneous schemes and heterogeneous schemes. In Homogeneous scheme initial energy is same for each node but in heterogeneous scheme initial energy is different for each node and also used to determine the efficiency of sensor networks. Enhanced Modified LEACH (EMODLEACH) is a reactive protocol which is implemented for homogeneous network model. We have implemented the concept of Efficient Cluster head Replacement scheme and Dual transmitting power level scheme of MODLEACH along with the concept of Efficient Intra Cluster transmission Scheme of TEEN in LEACH. We analyze the PEGASIS protocol and modified the exiting protocol called improved energy balanced routing protocol (IEBRP).This IEBRP is based on cluster formation, cluster routing and other aspects of LEACH protocol.

































Recommended




























































More Related Content
What's hot (20)








































Similar to Protocols for wireless sensor networks (20)








































Recently uploaded (20)






























Protocols for wireless sensor networks
- 1. 1 Protocols for Wireless Sensor Networks By: Debabrata Singh Dept. of CSIT,ITER SOA University, Bhubaneswar Mail: [email protected]
- 2. 2 Outline Introduction Flat Routing Protocols Directed Diffusion SPIN(Sensor Protocol for Information via Negotiation. ) Hierarchical Routing Protocols LEACH(Low-energy adaptive clustering hierarchy) PEGASIS(Power Efficient Gathering in Sensor Information Systems ) TEEN(Threshold-sensitive energy efficient sensor network (TEEN)) Topic for Discussion References
- 3. 3 Introduction to WSNs A sensor network is a computer network of many, spacially distributed devices using sensors to monitor conditions at different locations. Involve three areas: sensing, communications, and computation.
- 4. 4 Introduction to WSNs Sensor nodes scattered in a sensor field Each nodes has the capabilities to collect data and route data back to the sink (Base Station). Protocols and algorithms with self-organization capabilities.
- 5. 5 Introduction - WSNs Topology Issues related to topology maintenance and change in three phases: Pre-deployment and deployment phase: Sensor nodes can be either thrown in mass or placed one by one in the sensor field. Post-deployment phase: Topology changes are due to change nodes' position, reachability, available energy, malfunctioning, and task details. Re-deployment of additional nodes phase: Additional sensor nodes can be redeployed at any time to replace malfunctioning nodes or due to changes in task dynamics.
- 6. 6 Types of Routing Protocol for WSN Single-hop Networks The network consists of n nodes, and packets are transmitted from sources to destinations directly. Multi-hop Networks The final destination of a packet might not be reached directly and the other nodes can be used to route the packet to the final destination.
- 7. 7 Flat Routing Protocols Flat Networks Every incoming packet is sent out on every outgoing line except the one it arrived on. Vast numbers of duplicate packets are generated. Routing Protocols: Directed Diffusion, SPIN.
- 8. 8 The Directed Diffusion Protocol Directed Diffusion consists of several elements: Interests Data messages Gradients Reinforcements
- 9. 9 Directed Diffusion - Interest Propagation The sink periodically broadcasts an interest message to each of its neighbors. Every node maintains an interest cache.
- 10. 10 Directed Diffusion - Gradient Establishment That every pair of neighboring nodes establishes a gradient toward each other. This technique can enable fast recovery from failed paths or reinforcement of empirically better paths.
- 11. 11 Directed Diffusion - Data Propagation A sensor node that detects a target, it computes the highest requested event rate among all its outgoing gradients. To resend a received data message, a node needs to examine the matching interest entry's gradient list.
- 12. 12 Directed Diffusion - Reinforcement The node might choose that neighbor from whom it first received the latest event matching the interest to reinforce. It is very reactive to changes in path quality.
- 13. 13 The SPIN Protocol Sensor Protocols for Information via Negotiation. Start with a source node sending its data to all of its neighbors.
- 14. 14 SPIN - Flooding deficiencies Implosion & Overlap (a) (a) (a) A B C D (a) (r, s)(q, r) A B C q s r Implosion Problem Overlap Problem
- 15. 15 SPIN-1 - three types of messages ADV When a SPIN node has data to share, it can advertise an ADV message containing meta-data. REQ A SPIN node sends an REQ message when it wishes to receive some actual data. DATA DATA messages contain actual sensor data with a meta-data header.
- 16. 16 ADVREQ The SPIN-1 Protocol Steps B A C D E F DATA ADV ADV ADV ADVREQ REQ DATA DATA
- 17. 17 The SPIN-2 Protocol When energy is plentiful, SPIN-2 nodes communicate using the same 3-stage protocol as SPIN-1 nodes. When a SPIN-2 node observes that its energy is approaching a low-energy threshold, it adapts by reducing its participation in the protocol.
- 18. 18 Hierarchical Routing Protocols Hierarchical Networks The main aim of hierarchical routing is to efficiently maintain the energy consumption of sensor nodes. Performing data aggregation and fusion in order to decrease the number of transmitted messages to the sink. Routing Protocols: LEACH, PEGASIS, TEEN.
- 19. 19 The LEACH Protocol Low-Energy Adaptive Clustering Hierarchy. Distributed cluster formation technique that enables self-organization of large numbers of nodes.
- 20. 20 LEACH - Cluster Algorithms for adapting clusters and rotating cluster head positions to evenly distribute the energy load among all the nodes. The nodes organize themselves into local clusters, with one node acting as the cluster head. The cluster head performs signal processing functions on the data, and transmits data to the remote BS.
- 21. 21 LEACH - Set-up phase Cluster Head Each cluster head node broadcasts an advertisement message (ADV) let all the other nodes that they have chosen this role for the current round. Non-Cluster Head They transmits a join-request message (Join-REQ) back to the chosen cluster head.
- 22. 22 LEACH - Set-up phase The cluster head node sets up a TDMA schedule and transmits this schedule to the nodes in the cluster. Ensures that there are no collisions among data messages. Allows the radio components to be turned off at all times except during their transmit time.
- 23. 23 LEACH - Steady-state phase Broken into frames, where nodes send their data to the cluster head at most once per frame during their allocated transmission slot. Once the cluster head receives all the data, it performs data aggregation.
- 24. 24 LEACH - Time line Time line showing LEACH operation NCH1 NCH2 … … … NCHm-1 NCHm Slot for NCH2 Frame ADV Join-REQ SCH Set-up phase
- 25. 25 The PEGASIS Protocol Power-Efficient GAthering in Sensor Information Systems. The key idea in PEGASIS is to form a chain among the sensor nodes so that each node will receive from and transmit to a close neighbor.
- 26. 26 PEGASIS - Chain The nodes will be organized to form a chain, which can either be accomplished by the sensor nodes themselves using a greedy algorithm starting from some node. When a node dies, the chain is reconstructed in the same manner to bypass the dead node.
- 27. 27 PEGASIS - Leader The main idea in PEGASIS is for each node to receive from and transmit to close neighbors and take turns being the leader for transmission to the BS. Nodes take turns transmitting to the BS, and we will use node number i mod N (N represents the number of nodes) to transmit to the BS in round i.
- 28. 28 PEGASIS - Token Token passing approach N0 N1 N2 N3 N4 BS Token Data
- 29. 29 The TEEN Protocol Threshold sensitive Energy Efficient sensor Network protocol. Proactive Protocols (LEACH) The nodes in this network periodically switch on their sensors and transmitters, sense the environment and transmit the data of interest. Reactive Protocols (TEEN) The nodes react immediately to sudden and drastic changes in the value of a sensed attribute.
- 30. 30 TEEN - Functioning At every cluster change time, the cluster-head broadcasts to its members Hard Threshold (HT) This is a threshold value for the sensed attribute. It is the absolute value of the attribute beyond which, the node sensing this value must switch on its transmitter and report to its cluster head. Soft Threshold (ST) This is a small change in the value of the sensed attribute which triggers the node to switch on its transmitter and transmit.
- 31. 31 TEEN - Hard Threshold The first time a parameter from the attribute set reaches its hard threshold value, the node switches on its transmitter and sends the sensed data. The sensed value is stored in an internal variable in the node, called the sensed value (SV).
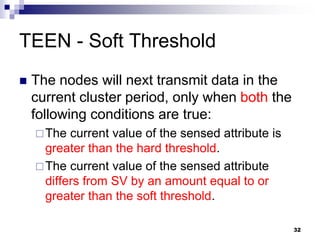
- 32. 32 TEEN - Soft Threshold The nodes will next transmit data in the current cluster period, only when both the following conditions are true: The current value of the sensed attribute is greater than the hard threshold. The current value of the sensed attribute differs from SV by an amount equal to or greater than the soft threshold.
- 33. 33 TEEN - Drawback If the thresholds are not reached, the user will not get any data from the network at all and will not come to know even if all the nodes die. This scheme practical implementation would have to ensure that there are no collisions in the cluster.
- 34. 34 References I.F. Akyildiz, W. Su*, Y. Sankarasubramaniam, and E. Cayirci, "Wireless sensor networks: a survey". K. Akkaya, M. Younis, "A Survey on Routing Protocols for Wireless Sensor Networks". J.N. Al-Karaki, A.E. Kamal, "Routing Techniques in Wireless Sensor Networks". C. Intanagonwiwat, R. Govindan, and D. Estrin, "Directed Diffusion: A Scalable and Robust Communication Paradigm for Sensor Networks". W. Heinzelman, J. Kulik, and H. Balakrishnan, "Adaptive Protocols for Information Dissemination in Wireless Sensor Networks". W. Heinzelman, A. Chandrakasan, and H. Balakrishnan, "An Application-Specific Protocol Architecture for Wireless Microsensor Networks". S. Lindsey and C. Raghavendra, "PEGASIS: Power-Efficient Gathering in Sensor Information Systems". A. Manjeshwar and D. Agrawal, "TEEN: A Routing Protocol for Enhanced Efficiency in Wireless Sensor Networks".





