QSpiders - Unix Operating Systems and Commands
Download as PPS, PDF1 like1,013 views
Operating System Resources Unix Architecture Unix File Attributes File Handling commands Basic Regular Expression Extended Regular Expression Searching for a pattern in UINIX
1 of 39
Downloaded 41 times











![To change file Permission
‘chmod’ command is used to change the permissions of
the file.
USAGE: chmod [options] mode[,mode] file1 [file2 ...]
Unix allows the user to specify modes in two ways.
1. Absolute
2. Relative
1. Absolute:
in this we use a series of 3 octal numbers to specify
the permission of a file.
Ex: chmod 501 demo.txt, chmod 777 demo.txt](https://image.slidesharecdn.com/unixnotes-part1-170214102205/85/QSpiders-Unix-Operating-Systems-and-Commands-13-320.jpg)




![ln Command
This command is used to create link for a file.
USAGE: ln [option] target link_name
ex: ln file1 file2
‘-s’ option is used to provide a soft link.
USAGE: ln –s target_file Link_name
ex: ln –s file1 file3](https://image.slidesharecdn.com/unixnotes-part1-170214102205/85/QSpiders-Unix-Operating-Systems-and-Commands-18-320.jpg)





![File Handling
commands
•
•
mkdir – is used to create directories
Usage: mkdir [OPTION]
DIRECTORY...
ex: mkdir demo
ls – is used to list all the files and
subdirectories
of the current directory.
Usage: ls [OPTION]... [FILE]...
eg. ls, ls l, ls l demo](https://image.slidesharecdn.com/unixnotes-part1-170214102205/85/QSpiders-Unix-Operating-Systems-and-Commands-24-320.jpg)
![File
Handling(contd...)
• pwd - print name of current working directory
Usage: pwd
• cd change directories
Usage: cd [DIRECTORY]
eg. cd demo
Note: the Directory can be a relative or absolute path
of Directory](https://image.slidesharecdn.com/unixnotes-part1-170214102205/85/QSpiders-Unix-Operating-Systems-and-Commands-25-320.jpg)
![cp – copy files and directories
Usage: cp [OPTION]... SOURCE DEST
Examples:
1. cp file1 file2
cp a.txt b.txt
2. cp file 1 file2…. filen directory
cp file1 file2 /home/user/demo](https://image.slidesharecdn.com/unixnotes-part1-170214102205/85/QSpiders-Unix-Operating-Systems-and-Commands-26-320.jpg)
![mv – this command is used to move a file
from one directory to another
It is also used to rename a file.
Usage: mv [OPTION]... SOURCE DEST
eg. mv source.txt target_dir
mv old.txt new.txt
rm remove files or directories
Usage: rm [OPTION]... FILE... eg. rm file1.txt , rm rf
some_dir](https://image.slidesharecdn.com/unixnotes-part1-170214102205/85/QSpiders-Unix-Operating-Systems-and-Commands-27-320.jpg)
![• find – search for files in a directory
hierarchy
Usage: find [OPTION] [path]
[action]
eg. 1. find file1.txt,
2. find name file1.txt
• history – prints recently used commands
Usage: history](https://image.slidesharecdn.com/unixnotes-part1-170214102205/85/QSpiders-Unix-Operating-Systems-and-Commands-28-320.jpg)






![Metacharacters
^ (Caret)=match expression at the start of a line, as in
^A.
$ (Dollar)=match expression at the end of a line, as in
A$.
(Back Slash)=turn off the special meaning of the next
character, as in ^.
[ ] (Brackets)=match any one of the enclosed characters,
as in [aeiou]. Use Hyphen "-" for a range, as in [0-9].
[^ ]=match any one character except those enclosed in
[ ], as in [^0-9].](https://image.slidesharecdn.com/unixnotes-part1-170214102205/85/QSpiders-Unix-Operating-Systems-and-Commands-35-320.jpg)


![Examples
grep '^From: ' demo.txt
grep '[a-zA-Z]'{any line with at least one
letter}
grep '[^a-zA-Z0-9]{anything not a letter or
number}
grep '[0-9]{3}-[0-9]{4}'{999-9999, like
phone numbers}
grep '^.$'{lines with exactly one character}](https://image.slidesharecdn.com/unixnotes-part1-170214102205/85/QSpiders-Unix-Operating-Systems-and-Commands-38-320.jpg)
![ grep '"smug"'{'smug' within double
quotes}
grep '"*smug"*'{'smug', with or without
quotes}
grep '^.'{any line that starts with a
Period "."}
grep '^.[a-z][a-z]'{line start with "." and
2 letters}](https://image.slidesharecdn.com/unixnotes-part1-170214102205/85/QSpiders-Unix-Operating-Systems-and-Commands-39-320.jpg)
Ad
Recommended
Linux basic commands



Linux basic commandsMohanKumar Palanichamy The document provides an overview of common Linux commands, including commands for executing other commands, navigating directories, listing and copying files, managing users and permissions, searching for files, processing text, managing archives, and compressing files. Examples are given for commands like ls, cd, cp, mv, rm, who, echo, alias, awk, chown, diff, grep, pushd, kill, df, cat, tar, gzip, su. Brief descriptions are provided for most commands and references are given at the end for additional Linux resources.
Linux systems - Linux Commands and Shell Scripting



Linux systems - Linux Commands and Shell ScriptingEmertxe Information Technologies Pvt Ltd Getting started with setting up embedded platform requires audience to understand some of the key aspects of Linux. This presentation deals with basics of Linux as an OS, Linux commands, vi editor, Shell features like redirection, pipes and shell scripting
Course 102: Lecture 3: Basic Concepts And Commands 



Course 102: Lecture 3: Basic Concepts And Commands Ahmed El-Arabawy This lecture covers the basic file management commands
Check the other Lectures and courses in
http://Linux4EnbeddedSystems.com
or Follow our Facebook Group at
- Facebook: @LinuxforEmbeddedSystems
Lecturer Profile:
- https://www.linkedin.com/in/ahmedelarabawy
Filepermissions in linux



Filepermissions in linuxSubashini Pandiarajan This document discusses Linux file permissions. It explains that Linux is a multi-user and multi-tasking system, so permissions can be set for files and directories using the chmod command. The chmod command allows changing permissions for the file owner, group owners, and other users using either symbolic modes like u+rwx or octal notation. It also covers the chown and chgrp commands for changing file ownership and group.
Unix/Linux Basic Commands and Shell Script



Unix/Linux Basic Commands and Shell Scriptsbmguys - Linux originated as a clone of the UNIX operating system. Key developers included Linus Torvalds and developers from the GNU project.
- Linux is open source, multi-user, and can run on a variety of hardware. It includes components like the Linux kernel, shell, terminal emulator, and desktop environments.
- The document provides information on common Linux commands, files, users/groups, permissions, and startup scripts. It describes the Linux file system and compression/archiving utilities.
Shell scripting



Shell scriptingsimha.dev.lin This document provides an overview of shell scripting in 3 paragraphs or less:
The document discusses Linux shell scripting, including that a shell is a user program that provides an environment for user interaction by reading commands from standard input and executing them. It mentions common shell types like BASH, CSH, and KSH, and that shell scripts allow storing sequences of commands in a file to execute them instead of entering each command individually. The document provides basic information on writing, executing, and using variables and input/output redirection in shell scripts.
File permission in linux



File permission in linuxPrakash Poudel This document discusses basic file permissions in Linux/Unix. It covers the different file attributes seen in the ls -l command output including permissions, owner, group, size and date. It describes the rwx permissions for owner, group and others. It also explains how to modify permissions using chmod with absolute and symbolic modes, and how to change file ownership with chown.
Quick Guide with Linux Command Line



Quick Guide with Linux Command LineAnuchit Chalothorn This document provides a quick guide to the Linux command line. It introduces Linux and the shell, and explains why the command line is useful even with graphical user interfaces. It then covers basic commands for file management, processes, archives, and input/output redirection. Finally, it briefly mentions some simple text editors and hints at using more advanced shell scripting.
Unix Linux Commands Presentation 2013



Unix Linux Commands Presentation 2013Wave Digitech Unix , Linux Commands
Unix, which is not an acronym, was developed by some of the members of the Multics team at the bell labs starting in the late 1960's by many of the same people who helped create the C programming language.
Part 02 Linux Kernel Module Programming



Part 02 Linux Kernel Module ProgrammingTushar B Kute Presentation on "Linux Kernel Module Programming".
Presented at Army Institute of Technology, Pune for FDP on "Basics of Linux Kernel Programming". by Tushar B Kute (http://tusharkute.com).
Linux presentation



Linux presentationNikhil Jain Linux is an open-source operating system based on Unix, designed for multi-user environments. The document provides an overview of basic Linux commands like ls, mkdir, cd for navigating files and directories, as well as more advanced commands for manipulating files, checking system resources, and getting system information. It also lists and describes many common Linux commands and their functions.
Unix



UnixErm78 The document provides an overview of the UNIX operating system. It discusses the history and development of UNIX from the 1960s onward. It describes the key features of UNIX including its layered architecture, kernel, shell, process management, file system, and security features. It also covers basic UNIX commands for working with files and directories, permissions, and getting help. The objective is to introduce readers to fundamental concepts of the UNIX OS.
Shell Scripting



Shell ScriptingGaurav Shinde This document provides an introduction and overview of shell scripting in Linux. It discusses what a shell script is, when they should and should not be used, examples of common shell scripts, and an introduction to programming features commonly used in shell scripts such as variables, conditionals, loops, command line arguments, and more. Key points covered include that shell scripts allow automating command execution, are useful for repetitive tasks, and come with programming features to customize behavior.
makefiles tutorial



makefiles tutorialvsubhashini This document is a tutorial on makefiles that introduces their purpose for managing complex compilations across multiple source files. It covers topics such as targets, dependencies, macros, naming conventions, phony targets, automatic variables, and default compilation rules. An example makefile is provided to demonstrate these concepts.
Basics of shell programming



Basics of shell programmingChandan Kumar Rana This document provides an overview of shell programming basics. It covers topics such as basic system commands like ls, cp, and rm; useful operations like wildcards and input/output redirection; shell variables; command substitution; decision making and loops; and other features like comments and head/tail utilities. The goal of the document is to introduce the reader to the core components of shell scripting.
Vi editor



Vi editorParikshitTaksande1 in this ppt, you find complete information of VI edited which Is text editor of UNIX operating system and all basic command like how to save files how to change how to edit how to delete
Linux - Introductions to Linux Operating System



Linux - Introductions to Linux Operating SystemVibrant Technologies & Computers This ppt gives information about:
1. Administering the server
2. Correcting installation problems
3. Setting up user accounts
4. Connecting to the network
5. Configuring utilities
Linux command ppt



Linux command pptkalyanineve Here are the key differences between relative and absolute paths in Linux:
- Relative paths specify a location relative to the current working directory, while absolute paths specify a location from the root directory.
- Relative paths start from the current directory, denoted by a period (.). Absolute paths always start from the root directory, denoted by a forward slash (/).
- Relative paths are dependent on the current working directory and may change if the working directory changes. Absolute paths will always refer to the same location regardless of current working directory.
- Examples:
- Relative: ./file.txt (current directory)
- Absolute: /home/user/file.txt (from root directory)
So in summary, relative paths
linux file sysytem& input and output



linux file sysytem& input and outputMythiliA5 The document discusses Linux file systems and input/output. It describes the basic structure of Linux file systems, including the root directory and common file system types like Ext4, XFS, and Btrfs. It also summarizes the different classes of devices in Linux - block devices, character devices, and network devices. Block devices provide access to storage and allow random access to fixed sized blocks. Character devices process data sequentially and include keyboards and printers. Network devices operate indirectly through sockets, protocols, and network drivers.
Pipes and filters



Pipes and filtersbhatvijetha Pipe allows the output of one command to be used as input for another command. The "|" symbol is used to connect commands. Common examples include using "ls | more" to view a directory listing page by page or "who > userlist.txt" to redirect the output of the who command to a file. Linux treats the keyboard, terminal screen, and error messages as standard input, output, and error. Redirectors like "<" and ">" can change where input and output are directed. Commands like sort, grep, and more are examples of filters that take input, manipulate it, and produce output.
Introduction to linux at Introductory Bioinformatics Workshop



Introduction to linux at Introductory Bioinformatics WorkshopSetor Amuzu This is a brief introduction to Linux, with emphasis on command-line interface. This presentation was made to participants of the H3ABioNet Introductory Bioinformatics workshop held in Accra, Ghana on 26 March, 2014.
Linux Basic Commands



Linux Basic CommandsHanan Nmr This document provides an overview of basic Linux commands and concepts for beginners. It covers topics such as opening the terminal, changing directories, listing and manipulating files and folders, searching for files, managing processes, installing packages, setting environment variables, and compressing files. The document is intended to help new Linux users learn the basics of how Linux is organized and how to navigate and perform tasks on the command line interface.
Implementation of FIFO in Linux



Implementation of FIFO in LinuxTushar B Kute Implementation of FIFO in Linux
Operating System Laboratory, SPPU University.
by Tushar B Kute
http://tusharkute.com
SHELL PROGRAMMING



SHELL PROGRAMMINGjinal thakrar This document provides an introduction to shell programming in Linux. It defines key terms like the kernel, processes, pipes, and filters. It explains that the kernel manages resources and I/O, while processes carry out tasks. Pipes send output between programs and filters perform operations on input. Common shells like Bash, CSH, and KSH are outlined. Shells accept commands and translate them to binary for the OS. Basic Linux commands are listed along with examples. Variables, both system and user-defined, are explained as a way to store and process data in the shell. The document provides steps for writing, naming, running and debugging shell scripts using commands like echo, cat, chmod and expressions. Local and global variables
Shell scripting



Shell scriptingManav Prasad This document provides an introduction to shell scripting using the bash shell. It covers key concepts such as shell variables, command substitution, quoting, aliases, and initializing files. The shell acts as both a command-line interface and programming language. It executes commands, supports scripting through variables and control structures, and reads initialization files on startup to customize the environment. Well-formed shell scripts allow combining and sequencing commands to perform automated tasks.
Shell programming



Shell programmingMoayad Moawiah The document provides information about shells in Linux operating systems. It defines what a kernel and shell are, explains why shells are used, describes different types of shells, and provides examples of shell scripting. The key points are:
- The kernel manages system resources and acts as an intermediary between hardware and software. A shell is a program that takes commands and runs them, providing an interface between the user and operating system.
- Shells are useful for automating tasks, combining commands to create new ones, and adding functionality to the operating system. Common shells include Bash, Bourne, C, Korn, and Tcsh.
- Shell scripts allow storing commands in files to automate tasks.
Bash Shell Scripting



Bash Shell ScriptingRaghu nath This document provides an overview of Linux Bash shell scripting. It covers topics such as writing basic scripts, variables, conditionals, loops, functions, arguments, and input/output redirection. Examples are given for many common scripting tasks like arithmetic operations, string manipulation, file operations, and comparing values. The document is intended to teach the basics of scripting in the Linux Bash shell.
Linux cheat-sheet



Linux cheat-sheetCraig Cannon This document provides a summary of common Linux commands organized by category including file permissions, networking, compression/archives, package installation, searching, login, file transfer, disk usage, directory traversal, system information, hardware information, users, file commands, and process related commands. It also includes brief descriptions and examples of commands like chmod, chown, ip, tar, rpm, grep, ssh, df, du, and kill. More detailed information on Linux commands can be found at the provided URL.
QSpiders - Automation using Selenium



QSpiders - Automation using SeleniumQspiders - Software Testing Training Institute The document discusses automation testing using Selenium. It provides an overview of Selenium, including what it is, its components like Selenium IDE, Selenium RC, Selenium Grid, and Selenium WebDriver. It explains the features and advantages of each component. Selenium is an open source tool that allows automated testing of web applications across different browsers and platforms. It supports recording and playback of tests and can help reduce testing time and costs through automation.
QSpiders - Selenium Webdriver



QSpiders - Selenium WebdriverQspiders - Software Testing Training Institute QSpiders - Selenium Webdriver Syllabus to meet growing skill demands of the current job market. Here is all new Selenium WebDriver course covering concepts from basics to advance test automation.
Ad
More Related Content
What's hot (20)
Unix Linux Commands Presentation 2013



Unix Linux Commands Presentation 2013Wave Digitech Unix , Linux Commands
Unix, which is not an acronym, was developed by some of the members of the Multics team at the bell labs starting in the late 1960's by many of the same people who helped create the C programming language.
Part 02 Linux Kernel Module Programming



Part 02 Linux Kernel Module ProgrammingTushar B Kute Presentation on "Linux Kernel Module Programming".
Presented at Army Institute of Technology, Pune for FDP on "Basics of Linux Kernel Programming". by Tushar B Kute (http://tusharkute.com).
Linux presentation



Linux presentationNikhil Jain Linux is an open-source operating system based on Unix, designed for multi-user environments. The document provides an overview of basic Linux commands like ls, mkdir, cd for navigating files and directories, as well as more advanced commands for manipulating files, checking system resources, and getting system information. It also lists and describes many common Linux commands and their functions.
Unix



UnixErm78 The document provides an overview of the UNIX operating system. It discusses the history and development of UNIX from the 1960s onward. It describes the key features of UNIX including its layered architecture, kernel, shell, process management, file system, and security features. It also covers basic UNIX commands for working with files and directories, permissions, and getting help. The objective is to introduce readers to fundamental concepts of the UNIX OS.
Shell Scripting



Shell ScriptingGaurav Shinde This document provides an introduction and overview of shell scripting in Linux. It discusses what a shell script is, when they should and should not be used, examples of common shell scripts, and an introduction to programming features commonly used in shell scripts such as variables, conditionals, loops, command line arguments, and more. Key points covered include that shell scripts allow automating command execution, are useful for repetitive tasks, and come with programming features to customize behavior.
makefiles tutorial



makefiles tutorialvsubhashini This document is a tutorial on makefiles that introduces their purpose for managing complex compilations across multiple source files. It covers topics such as targets, dependencies, macros, naming conventions, phony targets, automatic variables, and default compilation rules. An example makefile is provided to demonstrate these concepts.
Basics of shell programming



Basics of shell programmingChandan Kumar Rana This document provides an overview of shell programming basics. It covers topics such as basic system commands like ls, cp, and rm; useful operations like wildcards and input/output redirection; shell variables; command substitution; decision making and loops; and other features like comments and head/tail utilities. The goal of the document is to introduce the reader to the core components of shell scripting.
Vi editor



Vi editorParikshitTaksande1 in this ppt, you find complete information of VI edited which Is text editor of UNIX operating system and all basic command like how to save files how to change how to edit how to delete
Linux - Introductions to Linux Operating System



Linux - Introductions to Linux Operating SystemVibrant Technologies & Computers This ppt gives information about:
1. Administering the server
2. Correcting installation problems
3. Setting up user accounts
4. Connecting to the network
5. Configuring utilities
Linux command ppt



Linux command pptkalyanineve Here are the key differences between relative and absolute paths in Linux:
- Relative paths specify a location relative to the current working directory, while absolute paths specify a location from the root directory.
- Relative paths start from the current directory, denoted by a period (.). Absolute paths always start from the root directory, denoted by a forward slash (/).
- Relative paths are dependent on the current working directory and may change if the working directory changes. Absolute paths will always refer to the same location regardless of current working directory.
- Examples:
- Relative: ./file.txt (current directory)
- Absolute: /home/user/file.txt (from root directory)
So in summary, relative paths
linux file sysytem& input and output



linux file sysytem& input and outputMythiliA5 The document discusses Linux file systems and input/output. It describes the basic structure of Linux file systems, including the root directory and common file system types like Ext4, XFS, and Btrfs. It also summarizes the different classes of devices in Linux - block devices, character devices, and network devices. Block devices provide access to storage and allow random access to fixed sized blocks. Character devices process data sequentially and include keyboards and printers. Network devices operate indirectly through sockets, protocols, and network drivers.
Pipes and filters



Pipes and filtersbhatvijetha Pipe allows the output of one command to be used as input for another command. The "|" symbol is used to connect commands. Common examples include using "ls | more" to view a directory listing page by page or "who > userlist.txt" to redirect the output of the who command to a file. Linux treats the keyboard, terminal screen, and error messages as standard input, output, and error. Redirectors like "<" and ">" can change where input and output are directed. Commands like sort, grep, and more are examples of filters that take input, manipulate it, and produce output.
Introduction to linux at Introductory Bioinformatics Workshop



Introduction to linux at Introductory Bioinformatics WorkshopSetor Amuzu This is a brief introduction to Linux, with emphasis on command-line interface. This presentation was made to participants of the H3ABioNet Introductory Bioinformatics workshop held in Accra, Ghana on 26 March, 2014.
Linux Basic Commands



Linux Basic CommandsHanan Nmr This document provides an overview of basic Linux commands and concepts for beginners. It covers topics such as opening the terminal, changing directories, listing and manipulating files and folders, searching for files, managing processes, installing packages, setting environment variables, and compressing files. The document is intended to help new Linux users learn the basics of how Linux is organized and how to navigate and perform tasks on the command line interface.
Implementation of FIFO in Linux



Implementation of FIFO in LinuxTushar B Kute Implementation of FIFO in Linux
Operating System Laboratory, SPPU University.
by Tushar B Kute
http://tusharkute.com
SHELL PROGRAMMING



SHELL PROGRAMMINGjinal thakrar This document provides an introduction to shell programming in Linux. It defines key terms like the kernel, processes, pipes, and filters. It explains that the kernel manages resources and I/O, while processes carry out tasks. Pipes send output between programs and filters perform operations on input. Common shells like Bash, CSH, and KSH are outlined. Shells accept commands and translate them to binary for the OS. Basic Linux commands are listed along with examples. Variables, both system and user-defined, are explained as a way to store and process data in the shell. The document provides steps for writing, naming, running and debugging shell scripts using commands like echo, cat, chmod and expressions. Local and global variables
Shell scripting



Shell scriptingManav Prasad This document provides an introduction to shell scripting using the bash shell. It covers key concepts such as shell variables, command substitution, quoting, aliases, and initializing files. The shell acts as both a command-line interface and programming language. It executes commands, supports scripting through variables and control structures, and reads initialization files on startup to customize the environment. Well-formed shell scripts allow combining and sequencing commands to perform automated tasks.
Shell programming



Shell programmingMoayad Moawiah The document provides information about shells in Linux operating systems. It defines what a kernel and shell are, explains why shells are used, describes different types of shells, and provides examples of shell scripting. The key points are:
- The kernel manages system resources and acts as an intermediary between hardware and software. A shell is a program that takes commands and runs them, providing an interface between the user and operating system.
- Shells are useful for automating tasks, combining commands to create new ones, and adding functionality to the operating system. Common shells include Bash, Bourne, C, Korn, and Tcsh.
- Shell scripts allow storing commands in files to automate tasks.
Bash Shell Scripting



Bash Shell ScriptingRaghu nath This document provides an overview of Linux Bash shell scripting. It covers topics such as writing basic scripts, variables, conditionals, loops, functions, arguments, and input/output redirection. Examples are given for many common scripting tasks like arithmetic operations, string manipulation, file operations, and comparing values. The document is intended to teach the basics of scripting in the Linux Bash shell.
Linux cheat-sheet



Linux cheat-sheetCraig Cannon This document provides a summary of common Linux commands organized by category including file permissions, networking, compression/archives, package installation, searching, login, file transfer, disk usage, directory traversal, system information, hardware information, users, file commands, and process related commands. It also includes brief descriptions and examples of commands like chmod, chown, ip, tar, rpm, grep, ssh, df, du, and kill. More detailed information on Linux commands can be found at the provided URL.
Viewers also liked (20)
QSpiders - Automation using Selenium



QSpiders - Automation using SeleniumQspiders - Software Testing Training Institute The document discusses automation testing using Selenium. It provides an overview of Selenium, including what it is, its components like Selenium IDE, Selenium RC, Selenium Grid, and Selenium WebDriver. It explains the features and advantages of each component. Selenium is an open source tool that allows automated testing of web applications across different browsers and platforms. It supports recording and playback of tests and can help reduce testing time and costs through automation.
QSpiders - Selenium Webdriver



QSpiders - Selenium WebdriverQspiders - Software Testing Training Institute QSpiders - Selenium Webdriver Syllabus to meet growing skill demands of the current job market. Here is all new Selenium WebDriver course covering concepts from basics to advance test automation.
intro unix/linux 02



intro unix/linux 02duquoi The document provides an overview of essential Linux commands and programs for navigating the file system, examining and managing files, and accessing utilities and documentation. It discusses the development of UNIX and Linux, basic commands for executing utilities like date and hostname, passing arguments to utilities, listing processes with ps, and redirecting outputs. It also covers navigating directories, copying, moving, removing files, and deciphering error messages.
Unix(introduction)



Unix(introduction)meashi The document provides an overview of the history and development of the UNIX operating system from 1965 to 1983. It describes how UNIX originated from the Multics project at Bell Labs and MIT in 1965. It was further developed by AT&T in the 1970s and rewritten in C by Dennis Ritchie in 1973. The document also discusses the development of BSD and System V UNIX variants in the 1980s.
Unix Command Line Productivity Tips



Unix Command Line Productivity TipsKeith Bennett The document provides tips for improving productivity when using the Unix command line. It discusses advantages of the shell like flexibility and chaining commands together. It then gives examples of using shell commands in scripting languages. The majority of the document provides examples of specific Unix commands like grep, find, less and their usage for tasks like file searching, viewing files and directory listings. It concludes with tips on aliases, environment variables and symbolic links.
Unix OS & Commands



Unix OS & CommandsMohit Belwal This document provides an overview of the UNIX operating system and some basic UNIX commands. It discusses what UNIX is, its origins at Bell Laboratories in 1969, and some of its core functions like providing a filing system and loading/executing programs. It also covers the UNIX kernel and layers, file system structure, shells, logging in, and examples of common commands like ls, cat, more, pr, grep, passwd, who, and man.
UNIX and Linux - an introduction by Mathias Homann



UNIX and Linux - an introduction by Mathias HomannMathias Homann As part of my job a senior Linux systems engineer and freelance consultant, I am often asked to do staff training on various Unix and linux related topics. One such training is “UNIX and Linux – an introduction”, a 2-day intensive course which I developed.
The content is aimed individuals who are familiar with Windows back-office operations.
Read More at http://linux.eregion.de/, Copyright © Penguins and stuff
Linux intro 3 grep + Unix piping



Linux intro 3 grep + Unix pipingGiovanni Marco Dall'Olio Lecture for the "Programming for Evolutionary Biology" workshop in Leipzig 2013 (http://evop.bioinf.uni-leipzig.de/)
Unix - An Introduction



Unix - An IntroductionDeepanshu Gahlaut This document provides an introduction to the UNIX operating system. It discusses that UNIX is a multi-user, multitasking operating system developed in 1969. It describes the three categories of UNIX systems and lists some popular flavors. It also summarizes key UNIX features like portability, security, and networking. Finally, it provides overviews of the UNIX file system structure, commands, utilities and applications.
UNIX Operating System



UNIX Operating SystemUnless Yuriko This document presents information about the UNIX operating system from a group consisting of 5 members. It provides a brief history of UNIX, noting it was developed in the 1970s at Bell Labs and was intended as a programmer's workbench. The document outlines some key advantages of UNIX, including its portability, multi-tasking abilities, and security features. It also mentions some disadvantages such as its less user-friendly command line interface. In conclusion, it notes UNIX now runs on almost every type of computer.
Unix memory management



Unix memory managementTech_MX This document provides an overview of UNIX memory management. It discusses the history of UNIX and how it evolved from earlier systems like Multics. It describes swapping as an early technique for virtual memory management in UNIX and how demand paging was later introduced. Key concepts discussed include page tables, page replacement algorithms like two-handed clock, and the kernel memory allocator.
Basic Unix



Basic UnixRajesh Kumar Basic of and Unix and Command. More presentation you can find on www.scmGalaxy.com.
scmGalaxy.com is dedicated to software configuration, build and Release management. This covers CVS, VSS (Visual Source Safe),Perforce, SVN(Subversion) MKS Integrity, ClearCase,TFS,CM Synergy, Best Practices ,AnthillPro, Apache Ant, Maven, Bamboo, Cruise Control and many more tools.
Unix command-line tools



Unix command-line toolsEric Wilson The document discusses several common Unix command line utilities for text processing and file searching:
- find - Searches for files and directories based on various criteria like name, type, size, and modification time. Results can be piped to xargs to perform actions.
- grep - Searches files for text patterns. Has options for case-insensitive, recursive, and whole word searches.
- sed - Stream editor for modifying text, especially useful for find-and-replace. Can capture groups and perform transformations.
Unix Operating System



Unix Operating Systemsubhsikha The document provides an overview of the UNIX operating system. It discusses the components of a computer system including hardware, operating system, utilities, and application programs. It then defines the operating system as a program that acts as an interface between the user and computer hardware. The document outlines the goals of an operating system and provides a brief history of the development of UNIX from Multics. It also describes some key concepts of UNIX including the kernel, shell, files, directories, and multi-user capabilities.
UNIX/Linux training



UNIX/Linux trainingMichael Olafusi This document provides an overview of a 5-day UNIX/Linux training course. The training covers topics such as Linux desktops and administration, Linux command line administration, networking, servers, and programming. Each day focuses on a different aspect of UNIX/Linux including installation, desktop environments, administration tasks from the command line interface, and networking. Common Linux distributions and benefits of UNIX/Linux are also discussed.
Practical Example of grep command in unix



Practical Example of grep command in unixJavin Paul Grep command is one of most useful command in unix. having mastery in Grep and find means your productivity will be very high in unix. these grep command tutorials contains some examples of grep command in unix. It teaches how to leverage power of grep command in unix or linux. This presentation contains some of most useful example of grep command in unix.
for more tutorial see my blog
http://javarevisited.blogspot.com/2011/03/10-find-command-in-unix-examples-basic.html
http://javarevisited.blogspot.com/2011/06/10-examples-of-grep-command-in-unix-and.html
Data base



Data baseGc university faisalabad What is data and information? What is data base? What is data base management system? What are various data base models??? Components of data base function of data base. Advantages of data base. And what is system language query???
Basic Data Management Concept
Organizing Data in a Database
Database Management Systems
QSpiders - Day1 Network Basics



QSpiders - Day1 Network BasicsQspiders - Software Testing Training Institute The document discusses the OSI model and networking layers. It provides details on the functions of each layer, including physical, data link, network, transport, session, presentation and application layers. Key points covered include how each layer works independently and interfaces with adjacent layers, common protocols and services used at each layer, and how network devices operate at certain layers to enable communication.
Unix Training - 1



Unix Training - 1ankitmehta21 Hi,
This presentation contains history of Unix operating system.
Kindly send me your comments to [email protected] so it will help me to improve future presentations.
Thanks,
Ankit Mehta
[email protected]
Ad
Similar to QSpiders - Unix Operating Systems and Commands (20)
Commands and shell programming (3)



Commands and shell programming (3)christ university The document provides information on various features and commands in the UNIX operating system. It discusses multi-user and multi-tasking capabilities, the building block approach, and the UNIX tool kit. It also describes locating commands, internal and external commands, command structure, general purpose utilities like cal, date, echo, and bc. The document outlines file types, file names, directory commands, file commands, permissions, and vi editor basics.
Unix training session 1



Unix training session 1Anil Kumar Kapil,PMP® Introduction
UNIX Architecture
UNIX file system
Relative & Absolute path
File permission
Directory related commands
Files related commands
Miscellaneous commands
Unix3



Unix3Krishna Prasad The document provides an overview of essential Linux commands and concepts, organized into sections on essential commands, command structure, help, moving around directories, reading and writing files, directories, moving and renaming files, copying and removing files, links, searching, ownership and permissions, switching users, and useful commands. Key commands covered include ls, cd, pwd, touch, mkdir, mv, cp, rm, chmod, and sudo. File permissions are explained using rwx notation and octal representation.
Unit 7



Unit 7siddr The document discusses various types of files in UNIX/Linux systems such as regular files, directory files, device files, FIFO files, and symbolic links. It describes how each file type is created and used. It also covers UNIX file attributes, inodes, and how the kernel manages file access through system calls like open, read, write, and close.
04-1-Linux.ppt



04-1-Linux.pptEidTahir The document provides an introduction to the Linux operating system, explaining that it allows multiple users to be logged in simultaneously and runs processes separately using the kernel. It describes the directory and file system structure, including inodes that contain metadata for each file, and how permissions are assigned to users, groups, and others for access to files based on read, write and execute permissions. Finally, it covers how to view and set file permissions using symbolic modes like chmod and absolute octal modes.
An Introduction to Linux



An Introduction to LinuxDimas Prasetyo This document provides an overview of the Unix operating system and some basic Unix commands. It discusses the kernel and shell architecture of Unix, the multi-user and multi-process capabilities, file and directory structures including important directories like /bin, /home, and /var. It also summarizes common commands for navigating directories, viewing files, copying/moving files, and managing permissions and processes. The document is intended to help users get started with basic Unix concepts and commands.
Lession1 Linux Preview



Lession1 Linux Previewleminhvuong The document discusses Linux file systems and permissions. It describes the Virtual File System (VFS) interface and how it interacts with filesystems, inodes, and open files. It then discusses the EXT2 filesystem in more detail, describing how inodes store file metadata and how hard and soft links work. It also covers common Linux permissions and how to manage users, groups, and permissions using commands like chmod, chown, useradd, and others.
Basic Linux



Basic LinuxTan Huynh Cong The document discusses Linux file systems and permissions. It describes the Virtual File System (VFS) interface and how it interacts with filesystems, inodes, and open files. It then discusses the EXT2 filesystem in more detail, including how inodes store file metadata and pointers to data blocks. It also covers how permissions and ownership are represented, and commands to view and modify permissions like chmod, chown, and umask. Finally, it briefly discusses hard and soft links, and sticky bits.
linux-lecture4.ppt



linux-lecture4.pptLuigysToro The document discusses Linux commands for file management and viewing. It describes commands for navigating directories (cd), changing file permissions (chmod), copying files (cp), finding files (find), listing directory contents (ls), creating and removing directories (mkdir, rmdir), moving and renaming files (mv), viewing file contents (cat, head, tail), comparing files (cmp, diff), searching files (grep), and more. It also covers commands for compressing, archiving, and backing up files like tar, gzip, zip, and commands for counting, sorting, and filtering file contents.
Linux commands and file structure



Linux commands and file structureSreenatha Reddy K R The document discusses Linux commands for file management, viewing and shell programming. It describes common commands like ls, cd, cp, mv, rm, mkdir which allow navigating and manipulating files and directories. It also covers commands for viewing file contents like cat, head, tail, grep. Commands for compression like tar, gzip, zip and decompression like gunzip, unzip are mentioned. The document also has a section on shell programming which explains how to write shell scripts using commands and variables. It provides examples of using pipes, redirections and command options.
2. UNIX OS System Architecture easy.pptx



2. UNIX OS System Architecture easy.pptxPriyadarshini648418 it is a simple and easy presentation on the unix system architecture. v=can be used by the school and colllege students
Karkha unix shell scritping



Karkha unix shell scritpingchockit88 The document provides information about an upcoming UNIX and Shell Scripting workshop, including contact information for the workshop instructor R. Chockalingam, and covers topics that will be discussed such as the architecture and components of the UNIX operating system, basic UNIX commands, text editors, the file system structure, flags and arguments, and more.
various shell commands in unix operating system.pptx



various shell commands in unix operating system.pptxssuserc26f8f this lecture is about various shell commands in unix operating system.
Linuxnishustud



LinuxnishustudVicky Singh Linux has a multi-layered system organization with applications and utilities at the outer layer, a kernel interacting directly with hardware at the inner layer, and a middle layer like desktops and shells facilitating communication. It provides multi-user access with login security and file/folder permissions. Common commands to manage files/folders include ls to list, touch/cat to create/edit, cp to copy, mv to move, rm to delete, and chmod to change permissions. The file system hierarchy has directories like home, bin, lib, etc. Disk space is allocated in blocks and inodes track file attributes.
Basic unix commands_1



Basic unix commands_1thakor bharati This document provides summaries of 30 common Unix commands. It begins with an introduction explaining the purpose and scope of the document. The commands are then listed alphabetically, with each getting a brief 1-2 sentence description. For some commands, simple examples of usage are also provided. The document aims to give beginners a quick overview of the basic usage of important Unix commands.
Ad
More from Qspiders - Software Testing Training Institute (20)
QSpiders - Variable Length-Subnet-Masks



QSpiders - Variable Length-Subnet-MasksQspiders - Software Testing Training Institute The document discusses variable-length subnet masks (VLSM) and route summarization in networking. It provides examples of how a subnet mask can vary in length to further divide a subnet into smaller subnets. It also explains how route summarization works by summarizing addresses of several networks into one address to reduce the size of routing tables. The document includes examples of VLSM implementation and route summarization within an octet and in a VLSM-designed network.
QSpiders - Upper layer-protocols



QSpiders - Upper layer-protocolsQspiders - Software Testing Training Institute A suite of protocols
The DoD & OSI
TCP/IP Protocol Suit at DoD
TCP Segment Format
Application Layer Overview
Subnet Mask with Subnets
QSpiders - Dod Model



QSpiders - Dod ModelQspiders - Software Testing Training Institute The Process / Application Layer
The DoD & OSI
Host-to-Host Layer
Internet Layer
Network Access Layer
LOWER LAYERS PROTOCOLS
Ethernet
QSpiders - Aptitude Assignments



QSpiders - Aptitude AssignmentsQspiders - Software Testing Training Institute Interest Assignments
Partnership Assignments
Percentages Assignment
Profit and Loss
Assignments
Proportion Assignments
Set Theory Assignments
Time and Distance Assignments
Time and Work Assignments
Permutation Assignments
Allegation Assignments
AP,GP Assignments
QSpiders - SQL (Data Base)



QSpiders - SQL (Data Base)Qspiders - Software Testing Training Institute Data is a useful information
Which helps to make a decision
Set of information of any entity is known as data
Databases support storage and manipulation of data
QSpiders - Chapter 7 Debugging



QSpiders - Chapter 7 DebuggingQspiders - Software Testing Training Institute Controlling test runs can help you to identify and eliminate defects in your tests.
The Debug Viewer tabs can display the values of variables or objects in the main script of the current action or in a selected subroutine.
QSpiders - Chapter 4 Checkpoints



QSpiders - Chapter 4 CheckpointsQspiders - Software Testing Training Institute A Checkpoint is a verification point.
QuickTest adds a checkpoint with an icon in the test tree.
Creating Standard Checkpoint.
QSpiders - Simple Recording and Configuration of recording options for HP Loa...



QSpiders - Simple Recording and Configuration of recording options for HP Loa...Qspiders - Software Testing Training Institute Compiles and displays
test results with
graphical and statistical tools.
Generates load
and collects test results.
Creates Scripts as one Single User.
QSpiders - Wonderlic Sample Question



QSpiders - Wonderlic Sample QuestionQspiders - Software Testing Training Institute Assume the first 2 statements are true. Is the final one.
Paper sells for 21 cents per pad.
PRESENT RESERVE
QSpiders - Chapter- 3 Synchronization point



QSpiders - Chapter- 3 Synchronization pointQspiders - Software Testing Training Institute Synchronizing Your Test
Tests can be synchronized either of the ways
Synchronization point
Exist or Wait statements
Increase the default timeout settings
QSpiders - Presentation JMeter



QSpiders - Presentation JMeterQspiders - Software Testing Training Institute JMeter can be used as a unit test tool for JDBC database.
Proxy Server, Organization, Genericity, Assertions.
QSpiders - Memory (JVM architecture)



QSpiders - Memory (JVM architecture)Qspiders - Software Testing Training Institute The JVM architecture has four main memory areas:
1. The method area stores all class files and instance methods.
2. The stack region executes methods and stores local variables.
3. The heap area stores all objects and static variables.
4. The native method area stores code for native languages like C and C++.
QSpiders - Jdk Jvm Jre and Jit



QSpiders - Jdk Jvm Jre and JitQspiders - Software Testing Training Institute JDK stand for java development kit.
JVM stands for Java Virtual Machine.
JRE is the responsible unit to run the java program.
JIT stands for Just In Time compiler.
QSpiders - Simple replay and run time settings Loadrunner



QSpiders - Simple replay and run time settings LoadrunnerQspiders - Software Testing Training Institute The document discusses various runtime settings in HP LoadRunner that define how a script runs, including:
- Emulation settings that configure how users are simulated, such as think time and pacing.
- Logging settings that determine the level of information recorded.
- Network settings that control bandwidth emulation.
- Browser settings that configure aspects like the user agent and cache.
- Error handling settings that specify behavior for errors.
- Multithreading settings that control how VUsers are distributed across machines.
- Transaction settings that determine automatic transaction boundaries.
QSpiders - Major difference



QSpiders - Major differenceQspiders - Software Testing Training Institute The document compares and contrasts several key Java concepts:
1. Constructors are used to initialize objects and are called during object creation, while methods are called externally to perform functionality and can be inherited, overridden, and declared as various modifiers like final or static.
2. Abstract classes can contain both abstract and concrete methods and are used when a common property needs to be shared, while interfaces contain only abstract methods and are used when no common property needs to be shared, allowing multiple inheritance.
3. Collections store objects dynamically while arrays store both primitives and objects with a fixed size; collections provide more object-oriented utility methods than arrays.
QSpiders - Introduction to HP Load Runner



QSpiders - Introduction to HP Load RunnerQspiders - Software Testing Training Institute Performance & Load Testing Basics,
Introduction to Performance Testing,
Throughput, Response Time, Performance Testing.
QSpiders - Interacting with My SQL Database



QSpiders - Interacting with My SQL DatabaseQspiders - Software Testing Training Institute This document provides instructions for interacting with a MySQL database using the MySQL command line client. It explains how to open the client, select a database, create tables, insert and retrieve data, update records, and delete records. The key steps are to open the MySQL client, select a database, connect to it, then use SQL statements like CREATE, INSERT, SELECT, UPDATE, and DELETE to manage tables and data within the selected database.
QSpiders - Server Architecture



QSpiders - Server ArchitectureQspiders - Software Testing Training Institute This document discusses server architecture and different types of server architectures. It defines server architecture as how server layers like the server, network connectivity, and other connected components are arranged. The key points are:
- Server architecture depends on factors like the application type, targeted users, firmware/middleware, and third-party applications.
- Common architectures include client-server, layered, peer-to-peer, and pipes and filters. Client-server architecture involves clients that make requests and servers that satisfy requests.
- Web applications typically use 2-tier, 3-tier, or multitier (n-tier) client-server architectures with specialized tiers for tasks like the user interface, application processing, and
QSpiders - Installation and Brief Dose of Load Runner



QSpiders - Installation and Brief Dose of Load RunnerQspiders - Software Testing Training Institute The document provides information on performance testing processes and tools. It outlines 8 key steps: 1) create scripts, 2) create test scenarios, 3) execute load testing, 4) analyze results, 5) test reporting, 6) performance tuning, 7) communication planning, and 8) troubleshooting. It also discusses tools like LoadRunner, Controller, and Analysis for executing and analyzing tests. The document emphasizes having a thorough test process and communication plan to ensure performance testing is done correctly.
QSpiders - Good to Know Network Concepts



QSpiders - Good to Know Network ConceptsQspiders - Software Testing Training Institute The network layer is concerned with routing packets from the source to the destination across multiple networks. It must understand the topology of connected networks and choose optimal paths while avoiding overloading some lines. The network layer provides either connection-oriented or connectionless services to the transport layer and deals with differences when sources and destinations are in different networks. Dynamic routing algorithms like distance vector routing are used to adaptively route packets based on current network conditions.
QSpiders - Simple Recording and Configuration of recording options for HP Loa...



QSpiders - Simple Recording and Configuration of recording options for HP Loa...Qspiders - Software Testing Training Institute
QSpiders - Simple replay and run time settings Loadrunner



QSpiders - Simple replay and run time settings LoadrunnerQspiders - Software Testing Training Institute
Recently uploaded (20)
How to manage Multiple Warehouses for multiple floors in odoo point of sale



How to manage Multiple Warehouses for multiple floors in odoo point of saleCeline George The need for multiple warehouses and effective inventory management is crucial for companies aiming to optimize their operations, enhance customer satisfaction, and maintain a competitive edge.
Social Problem-Unemployment .pptx notes for Physiotherapy Students



Social Problem-Unemployment .pptx notes for Physiotherapy StudentsDrNidhiAgarwal Unemployment is a major social problem, by which not only rural population have suffered but also urban population are suffered while they are literate having good qualification.The evil consequences like poverty, frustration, revolution
result in crimes and social disorganization. Therefore, it is
necessary that all efforts be made to have maximum.
employment facilities. The Government of India has already
announced that the question of payment of unemployment
allowance cannot be considered in India
The ever evoilving world of science /7th class science curiosity /samyans aca...



The ever evoilving world of science /7th class science curiosity /samyans aca...Sandeep Swamy The Ever-Evolving World of
Science
Welcome to Grade 7 Science4not just a textbook with facts, but an invitation to
question, experiment, and explore the beautiful world we live in. From tiny cells
inside a leaf to the movement of celestial bodies, from household materials to
underground water flows, this journey will challenge your thinking and expand
your knowledge.
Notice something special about this book? The page numbers follow the playful
flight of a butterfly and a soaring paper plane! Just as these objects take flight,
learning soars when curiosity leads the way. Simple observations, like paper
planes, have inspired scientific explorations throughout history.
Ultimate VMware 2V0-11.25 Exam Dumps for Exam Success



Ultimate VMware 2V0-11.25 Exam Dumps for Exam SuccessMark Soia Boost your chances of passing the 2V0-11.25 exam with CertsExpert reliable exam dumps. Prepare effectively and ace the VMware certification on your first try
Quality dumps. Trusted results. — Visit CertsExpert Now: https://www.certsexpert.com/2V0-11.25-pdf-questions.html
Marie Boran Special Collections Librarian Hardiman Library, University of Gal...



Marie Boran Special Collections Librarian Hardiman Library, University of Gal...Library Association of Ireland Phoenix – A Collaborative Renewal of Children’s and Young People’s Services Clare Doyle - Cork City Libraries
World war-1(Causes & impacts at a glance) PPT by Simanchala Sarab(BABed,sem-4...



World war-1(Causes & impacts at a glance) PPT by Simanchala Sarab(BABed,sem-4...larencebapu132 This is short and accurate description of World war-1 (1914-18)
It can give you the perfect factual conceptual clarity on the great war
Regards Simanchala Sarab
Student of BABed(ITEP, Secondary stage)in History at Guru Nanak Dev University Amritsar Punjab 🙏🙏
Odoo Inventory Rules and Routes v17 - Odoo Slides



Odoo Inventory Rules and Routes v17 - Odoo SlidesCeline George Odoo's inventory management system is highly flexible and powerful, allowing businesses to efficiently manage their stock operations through the use of Rules and Routes.
Introduction to Vibe Coding and Vibe Engineering



Introduction to Vibe Coding and Vibe EngineeringDamian T. Gordon Introduction to Vibe Coding and Vibe Engineering
To study the nervous system of insect.pptx



To study the nervous system of insect.pptxArshad Shaikh The *nervous system of insects* is a complex network of nerve cells (neurons) and supporting cells that process and transmit information. Here's an overview:
Structure
1. *Brain*: The insect brain is a complex structure that processes sensory information, controls behavior, and integrates information.
2. *Ventral nerve cord*: A chain of ganglia (nerve clusters) that runs along the insect's body, controlling movement and sensory processing.
3. *Peripheral nervous system*: Nerves that connect the central nervous system to sensory organs and muscles.
Functions
1. *Sensory processing*: Insects can detect and respond to various stimuli, such as light, sound, touch, taste, and smell.
2. *Motor control*: The nervous system controls movement, including walking, flying, and feeding.
3. *Behavioral responThe *nervous system of insects* is a complex network of nerve cells (neurons) and supporting cells that process and transmit information. Here's an overview:
Structure
1. *Brain*: The insect brain is a complex structure that processes sensory information, controls behavior, and integrates information.
2. *Ventral nerve cord*: A chain of ganglia (nerve clusters) that runs along the insect's body, controlling movement and sensory processing.
3. *Peripheral nervous system*: Nerves that connect the central nervous system to sensory organs and muscles.
Functions
1. *Sensory processing*: Insects can detect and respond to various stimuli, such as light, sound, touch, taste, and smell.
2. *Motor control*: The nervous system controls movement, including walking, flying, and feeding.
3. *Behavioral responses*: Insects can exhibit complex behaviors, such as mating, foraging, and social interactions.
Characteristics
1. *Decentralized*: Insect nervous systems have some autonomy in different body parts.
2. *Specialized*: Different parts of the nervous system are specialized for specific functions.
3. *Efficient*: Insect nervous systems are highly efficient, allowing for rapid processing and response to stimuli.
The insect nervous system is a remarkable example of evolutionary adaptation, enabling insects to thrive in diverse environments.
The insect nervous system is a remarkable example of evolutionary adaptation, enabling insects to thrive
YSPH VMOC Special Report - Measles Outbreak Southwest US 5-3-2025.pptx



YSPH VMOC Special Report - Measles Outbreak Southwest US 5-3-2025.pptxYale School of Public Health - The Virtual Medical Operations Center (VMOC) A measles outbreak originating in West Texas has been linked to confirmed cases in New Mexico, with additional cases reported in Oklahoma and Kansas. The current case count is 817 from Texas, New Mexico, Oklahoma, and Kansas. 97 individuals have required hospitalization, and 3 deaths, 2 children in Texas and one adult in New Mexico. These fatalities mark the first measles-related deaths in the United States since 2015 and the first pediatric measles death since 2003.
The YSPH Virtual Medical Operations Center Briefs (VMOC) were created as a service-learning project by faculty and graduate students at the Yale School of Public Health in response to the 2010 Haiti Earthquake. Each year, the VMOC Briefs are produced by students enrolled in Environmental Health Science Course 581 - Public Health Emergencies: Disaster Planning and Response. These briefs compile diverse information sources – including status reports, maps, news articles, and web content– into a single, easily digestible document that can be widely shared and used interactively. Key features of this report include:
- Comprehensive Overview: Provides situation updates, maps, relevant news, and web resources.
- Accessibility: Designed for easy reading, wide distribution, and interactive use.
- Collaboration: The “unlocked" format enables other responders to share, copy, and adapt seamlessly. The students learn by doing, quickly discovering how and where to find critical information and presenting it in an easily understood manner.
CURRENT CASE COUNT: 817 (As of 05/3/2025)
• Texas: 688 (+20)(62% of these cases are in Gaines County).
• New Mexico: 67 (+1 )(92.4% of the cases are from Eddy County)
• Oklahoma: 16 (+1)
• Kansas: 46 (32% of the cases are from Gray County)
HOSPITALIZATIONS: 97 (+2)
• Texas: 89 (+2) - This is 13.02% of all TX cases.
• New Mexico: 7 - This is 10.6% of all NM cases.
• Kansas: 1 - This is 2.7% of all KS cases.
DEATHS: 3
• Texas: 2 – This is 0.31% of all cases
• New Mexico: 1 – This is 1.54% of all cases
US NATIONAL CASE COUNT: 967 (Confirmed and suspected):
INTERNATIONAL SPREAD (As of 4/2/2025)
• Mexico – 865 (+58)
‒Chihuahua, Mexico: 844 (+58) cases, 3 hospitalizations, 1 fatality
• Canada: 1531 (+270) (This reflects Ontario's Outbreak, which began 11/24)
‒Ontario, Canada – 1243 (+223) cases, 84 hospitalizations.
• Europe: 6,814
Multi-currency in odoo accounting and Update exchange rates automatically in ...



Multi-currency in odoo accounting and Update exchange rates automatically in ...Celine George Most business transactions use the currencies of several countries for financial operations. For global transactions, multi-currency management is essential for enabling international trade.
How to track Cost and Revenue using Analytic Accounts in odoo Accounting, App...



How to track Cost and Revenue using Analytic Accounts in odoo Accounting, App...Celine George Analytic accounts are used to track and manage financial transactions related to specific projects, departments, or business units. They provide detailed insights into costs and revenues at a granular level, independent of the main accounting system. This helps to better understand profitability, performance, and resource allocation, making it easier to make informed financial decisions and strategic planning.
SCI BIZ TECH QUIZ (OPEN) PRELIMS XTASY 2025.pptx



SCI BIZ TECH QUIZ (OPEN) PRELIMS XTASY 2025.pptxRonisha Das SCI BIZ TECH QUIZ (OPEN) PRELIMS - XTASY 2025
Political History of Pala dynasty Pala Rulers NEP.pptx



Political History of Pala dynasty Pala Rulers NEP.pptxArya Mahila P. G. College, Banaras Hindu University, Varanasi, India. The Pala kings were people-protectors. In fact, Gopal was elected to the throne only to end Matsya Nyaya. Bhagalpur Abhiledh states that Dharmapala imposed only fair taxes on the people. Rampala abolished the unjust taxes imposed by Bhima. The Pala rulers were lovers of learning. Vikramshila University was established by Dharmapala. He opened 50 other learning centers. A famous Buddhist scholar named Haribhadra was to be present in his court. Devpala appointed another Buddhist scholar named Veerdeva as the vice president of Nalanda Vihar. Among other scholars of this period, Sandhyakar Nandi, Chakrapani Dutta and Vajradatta are especially famous. Sandhyakar Nandi wrote the famous poem of this period 'Ramcharit'.
How to Set warnings for invoicing specific customers in odoo



How to Set warnings for invoicing specific customers in odooCeline George Odoo 16 offers a powerful platform for managing sales documents and invoicing efficiently. One of its standout features is the ability to set warnings and block messages for specific customers during the invoicing process.
pulse ppt.pptx Types of pulse , characteristics of pulse , Alteration of pulse



pulse ppt.pptx Types of pulse , characteristics of pulse , Alteration of pulsesushreesangita003 what is pulse ?
Purpose
physiology and Regulation of pulse
Characteristics of pulse
factors affecting pulse
Sites of pulse
Alteration of pulse
for BSC Nursing 1st semester
for Gnm Nursing 1st year
Students .
vitalsign
How to Subscribe Newsletter From Odoo 18 Website



How to Subscribe Newsletter From Odoo 18 WebsiteCeline George Newsletter is a powerful tool that effectively manage the email marketing . It allows us to send professional looking HTML formatted emails. Under the Mailing Lists in Email Marketing we can find all the Newsletter.
How to Customize Your Financial Reports & Tax Reports With Odoo 17 Accounting



How to Customize Your Financial Reports & Tax Reports With Odoo 17 AccountingCeline George The Accounting module in Odoo 17 is a complete tool designed to manage all financial aspects of a business. Odoo offers a comprehensive set of tools for generating financial and tax reports, which are crucial for managing a company's finances and ensuring compliance with tax regulations.
Marie Boran Special Collections Librarian Hardiman Library, University of Gal...



Marie Boran Special Collections Librarian Hardiman Library, University of Gal...Library Association of Ireland
YSPH VMOC Special Report - Measles Outbreak Southwest US 5-3-2025.pptx



YSPH VMOC Special Report - Measles Outbreak Southwest US 5-3-2025.pptxYale School of Public Health - The Virtual Medical Operations Center (VMOC)
Political History of Pala dynasty Pala Rulers NEP.pptx



Political History of Pala dynasty Pala Rulers NEP.pptxArya Mahila P. G. College, Banaras Hindu University, Varanasi, India.
QSpiders - Unix Operating Systems and Commands
- 2. Introduction • Operating System: It acts as an interface between the user and system. a system that manages the resources of a computer. • Resources: CPUs, Memory, I/O devices, Network etc..
- 3. Unix Architecture Hardware Kernel Shell hardware kernel sh who date ed wc grep as nroff ld cpp Other apps
- 4. Kernel • Three major tasks of kernel: Process Management Device Management File Management
- 5. Shell The shell acts as an interface between the user and the kernel A shell is an environment in which we can run our commands, it is also called as a command-line interpreter
- 6. Basic Linux Commands • File Handling • Text Processing • System Administration • Process Management • Archival • Network • File Systems • Advanced Commands
- 7. Files Everything in unix is considered as a file, including the physical devices like flash device, network cards etc.. Logical collection of files is called as file system or Unix file system(UFS). A UFS(unix file system) contains both inode and contents of the file. Every file as a unique number to identify, this number is called as an inode number.
- 8. Files….. We can classify files into 3 1. Ordinary Files • Text File • Binary File 2. Device Files 3. Directory Files / Special Files
- 9. Unix File Attributes File Permissions 1. Read: ‘r’ If you have read permission of a file, you can see the contents of the file. 2. Write: ‘w’ If you have write permission of a file, you can change the file. This means you can add to a file, or overwrite a file. You can empty a file. 3. Execute: ‘x’ If the file has execute permission, then you can ask the operating system to run the file as if it were a program. If it's a binary file/program, you can execute it like any other program.
- 10. File Attribute… 1. File type/File Permissions 2. Link 3. Owner 4. Group 5. Size 6. Last Modified Time 7. File Name NOTE: ‘ls –l’ command lists the files in the directory along with their attributes.
- 11. 1. File type/ File permissions The first field of ls –l command gives the details of file type and file permission This field as 10 characters. _|_ _ _|_ _ _|_ _ _ FILE TYPE FILE PERMISSIONS 1. FILE TYPE the first character of the first field defines the type of the file. ‘d’ – specifies that the file is a ‘directory file’ or a ‘special file’ ‘-’ – spefies that a file is not a directory file.
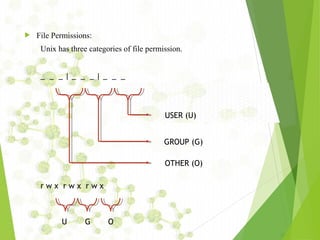
- 12. File Permissions: Unix has three categories of file permission. _ _ _ | _ _ _ | _ _ _ r w x r w x r w x USER (U) GROUP (G) OTHER (O) U G O
- 13. To change file Permission ‘chmod’ command is used to change the permissions of the file. USAGE: chmod [options] mode[,mode] file1 [file2 ...] Unix allows the user to specify modes in two ways. 1. Absolute 2. Relative 1. Absolute: in this we use a series of 3 octal numbers to specify the permission of a file. Ex: chmod 501 demo.txt, chmod 777 demo.txt
- 14. | rwx | 111 | 7 | Read, write and execute | | rw- | 110 | 6 | Read, write | | r-x | 101 | 5 | Read, and execute | | r-- | 100 | 4 | Read, | | -wx | 011 | 3 | Write and execute | | -w- | 010 | 2 | Write | | --x | 001 | 1 | Execute | | --- | 000 | 0 | no permissions | +----------------------------------------------------+
- 15. RELATIVE In this mode ‘=‘ , ‘+’, ‘-’ operators are used to assign, give and remove permissions. On the LHS specify the category u,g,o,a. On the RHS specify the permission r,w,x. Ex: chmod u+r demo.txt chmod u+rw demo.txt chmod ug+rwx demo.txt chmod a+rwx demo.txt chmod u+rw,g+x demo.txt
- 16. INODE Is a data structure and it contains following details of the file: 1. Mode/permission (protection) 2. Owner ID 3. Group ID 4. Size of file 5. Number of hard links to the file 6. Time last accessed 7. Time last modified 8. Time inode last modified ‘-i’ option along with ls command is used to see the inode number of a file.
- 17. 2. Link A link in UNIX is a pointer to a file. Like pointers in any programming languages, links in UNIX are pointers pointing to a file or a directory . Creating links is a kind of shortcuts to access a file. It is similar to creating multiple names of the file to access from different directories. The two different types of links in UNIX are: 1. Soft Links or Symbolic Links 2. Hard links
- 18. ln Command This command is used to create link for a file. USAGE: ln [option] target link_name ex: ln file1 file2 ‘-s’ option is used to provide a soft link. USAGE: ln –s target_file Link_name ex: ln –s file1 file3
- 19. Hard link A hard link is an additional name for an existing file on Unix-like operating systems. Any number of hard links can be created for a file, and thus any number of names, can be created for any file The inode of the hard linked file remains same as the original file. On deleting the original file, hard linked file can still be accessed. By giving the hard link the link count of the file will increase. Hard links do not need any extra data memory to save since it uses links Can be created only on files, not on directories.
- 20. Soft/Symbolic Link In computing, a symbolic link (soft link) is the nickname for any file that contains a reference to another file or directory in the form of an absolute or relative path and that affects pathname resolution. Soft link can be created for non exiting file. oft link has a different inode number than the original file On deleting the original file, soft link cannot be accessed. Soft link needs extra memory to store the original file name as its data. Access to the file is slower due to the overhead to access file.
- 21. 3. Owner Gives the name of the owner of the file. We can change the owner of the file using the command ‘chown’. usage: chown owner file
- 22. 4.Group Gives the name of the group a file belong to. We can change the group of the file using the command ‘chgrp’. Usage: chgrp group file
- 23. Sources to learn commands?? (man) λ Primary – man(manual) pages.1 2 man <command> shows all information about the command ex: man ls <command> help shows the available options for that command ex: ls help
- 24. File Handling commands • • mkdir – is used to create directories Usage: mkdir [OPTION] DIRECTORY... ex: mkdir demo ls – is used to list all the files and subdirectories of the current directory. Usage: ls [OPTION]... [FILE]... eg. ls, ls l, ls l demo
- 25. File Handling(contd...) • pwd - print name of current working directory Usage: pwd • cd change directories Usage: cd [DIRECTORY] eg. cd demo Note: the Directory can be a relative or absolute path of Directory
- 26. cp – copy files and directories Usage: cp [OPTION]... SOURCE DEST Examples: 1. cp file1 file2 cp a.txt b.txt 2. cp file 1 file2…. filen directory cp file1 file2 /home/user/demo
- 27. mv – this command is used to move a file from one directory to another It is also used to rename a file. Usage: mv [OPTION]... SOURCE DEST eg. mv source.txt target_dir mv old.txt new.txt rm remove files or directories Usage: rm [OPTION]... FILE... eg. rm file1.txt , rm rf some_dir
- 28. • find – search for files in a directory hierarchy Usage: find [OPTION] [path] [action] eg. 1. find file1.txt, 2. find name file1.txt • history – prints recently used commands Usage: history
- 29. TO create an USER ‘addusr’ command is used to create a user. To create a new user the user should be logged in as a rootuser. usage: addusr user_name
- 30. TO switch User ‘su’ command is used to switch from one user to another Usage: su User_name It asks for the password to login. ‘exit’ command is used to come out of the logged in user.
- 31. How to login as root ? ‘sudo su’ command is used to login as a root-user. usage: sudo su It will ask for the password. The user should have permission to login as the root-user. All the users having root permissions are stored in a file ‘visudo’.
- 32. To remove User ‘delusr’ command is used to delete a user. usage: delusr user-name You should be log-in as a root-user to delete an user.
- 33. Basic Regular Expression The BRE a{1,2} matches a{1,2} literally, while a{1,2} matches a or aa. As {,},+,?,(,),.. Are treated as a normal symbols and we have to use a ‘’ to give special meaning to them. As ?,+,.. Are not supported by POSIX (Portable Operating system Interface for Unix) BRE. We use grep command for BRE.
- 34. Extended Regular Expression The quantifiers ?, +, {n}, {n,m} and {n,} repea t the preceding token zero or once, once or more, n times, between n and m times, and n or more times, respectively. These above quantifiers are supported by POSIX ERE and we use egrep or grep –E command.
- 35. Metacharacters ^ (Caret)=match expression at the start of a line, as in ^A. $ (Dollar)=match expression at the end of a line, as in A$. (Back Slash)=turn off the special meaning of the next character, as in ^. [ ] (Brackets)=match any one of the enclosed characters, as in [aeiou]. Use Hyphen "-" for a range, as in [0-9]. [^ ]=match any one character except those enclosed in [ ], as in [^0-9].
- 36. . (Period)=match a single character of any value, except end of line. * (Asterisk)=match zero or more of the preceding character or expression. {x,y}=match x to y occurrences of the preceding. {x}=match exactly x occurrences of the preceding. {x,}=match x or more occurrences of the preceding.
- 37. Searching for a pattern in UINIX Unix has a special family of commands for handling search requirements. The main member of this family is the grep command. GREP: (Global Regular Expression Parser) It scans its input for a pattern and displays lines containing the pattern.
- 38. Examples grep '^From: ' demo.txt grep '[a-zA-Z]'{any line with at least one letter} grep '[^a-zA-Z0-9]{anything not a letter or number} grep '[0-9]{3}-[0-9]{4}'{999-9999, like phone numbers} grep '^.$'{lines with exactly one character}
- 39. grep '"smug"'{'smug' within double quotes} grep '"*smug"*'{'smug', with or without quotes} grep '^.'{any line that starts with a Period "."} grep '^.[a-z][a-z]'{line start with "." and 2 letters}







