Real time operating systems (rtos) concepts 5
Download as PPTX, PDF1 like611 views
Task Context. Context Switching between tasks. Shared Data Problem. Non Reentrant Function. Reentrant Function. Gray area of reentrancy. How to protect Shared Data?
1 of 17
Downloaded 121 times
















Ad
Recommended
Real time operating systems (rtos) concepts 4



Real time operating systems (rtos) concepts 4Abu Bakr Ramadan The Scheduler.
What if two tasks have the same priority are ready?
Task object data.
System tasks.
Hello World application using RTOS.
References and Read more
Real time operating systems (rtos) concepts 7



Real time operating systems (rtos) concepts 7Abu Bakr Ramadan Semaphore Types
Binary Semaphore.
Counting Semaphore.
Mutual Exclusion with Binary Semaphore.
Semaphore in µC/OS-II.
Dead Lock.
Avoid Dead Lock
Real time operating systems (rtos) concepts 3



Real time operating systems (rtos) concepts 3Abu Bakr Ramadan Video Content:
RTOS Kernel,
Priority Based Kernel
RTOS Task Status,
Preemptive Kernel,
Non-Preemptive Kernel,
Real time operating systems (rtos) concepts 9



Real time operating systems (rtos) concepts 9Abu Bakr Ramadan Mutex
Mutex vs Binary Semaphore
Determinism vs Responsiveness
Why RTOS,
Why not RTOS,
RTOS Market,
Real time operating systems (rtos) concepts 8



Real time operating systems (rtos) concepts 8Abu Bakr Ramadan This document discusses key concepts in real-time operating systems (RTOS) including resource synchronization, semaphores for task synchronization, priority inversion, priority inheritance, race conditions, CPU starvation. It also provides references and websites for further reading on RTOS concepts, embedded software, and the FreeRTOS open source operating system.
Real-Time Operating Systems



Real-Time Operating SystemsPraveen Penumathsa This document provides an overview of real-time operating systems (RTOS), including their key characteristics, scheduling approaches, and commercial examples. RTOS are used in applications that require tasks to complete work and deliver services on time. They use priority-based and clock-driven scheduling algorithms like rate monotonic analysis and earliest deadline first to ensure real-time constraints are met. Commercial RTOS aim to provide features like priority levels, fast task preemption, and predictable interrupt handling for real-time applications.
Process scheduling



Process schedulingDeepika Balichwal Hello....
Dear views
Scheduling is most important Role in OS..... in this ppt i described very Creatively about Process Scheduling...... I hope you like it..... and easily understand it...... :-) :-)
Context Switching



Context Switchingfranksvalli The document discusses the actions taken by the kernel during a context switch between processes. It explains that a context switch involves suspending the currently running process, storing its context in the Process Control Block (PCB), and loading and resuming the context of another process from its PCB. The PCB contains information about the process state, registers, memory management, and more. Context switching has significant overhead as it involves saving and loading all this process context data.
Real time operating systems (rtos) concepts 1



Real time operating systems (rtos) concepts 1Abu Bakr Ramadan What is The an Operating system (OS).
What is a Real-Time OS?
Hard vs. Soft real-time.
Examples of RTOS applications.
Examples of RTOS in the market.
Real Time Operating Systems



Real Time Operating SystemsMurtadha Alsabbagh This document discusses real-time operating systems (RTOS). It defines an RTOS as a program that schedules execution in a timely manner, manages system resources, and provides a consistent foundation for developing application code. The key components of an RTOS include a scheduler, objects like tasks and semaphores, and services like interrupt management. The scheduler uses algorithms to determine which task executes when and includes important elements like context switching. Objects help with synchronization between tasks. Services perform operations on objects and other kernel functions.
Rtos Concepts



Rtos ConceptsSundaresan Sundar An RTOS differs from a common OS in that it allows direct access to the microprocessor and peripherals, helping to meet deadlines. An RTOS provides mechanisms for multitasking like scheduling, context switching, and IPC. It uses techniques like priority-based preemptive scheduling and memory management with separate stacks and heaps for tasks. Common RTOS services include timing functions, synchronization, resource protection and communication between processes.
Approaches to real time scheduling



Approaches to real time schedulingKamal Acharya This document discusses various approaches to real-time scheduling such as clock-driven, weighted round-robin, and priority-driven approaches. It also covers topics like dynamic versus static systems, effective release times and deadlines, optimality and non-optimality of algorithms, challenges in validating timing constraints, and differences between offline and online scheduling.
FreeRTOS basics (Real time Operating System)



FreeRTOS basics (Real time Operating System)Naren Chandra A presentation that covers all the basics needed to understand and start working with FreeRTOS . FreeRTOS is comparable with more than 20 controller families and 30 plus supporting tools and IDEs.
FreeRTOS is a market-leading real-time operating system (RTOS) for microcontrollers and small microprocessors. Distributed freely under the MIT open source license, FreeRTOS includes a kernel and a growing set of libraries suitable for use across all industry sectors. FreeRTOS is built with an emphasis on reliability and ease of use.
Tiny, power-saving kernel
Scalable size, with usable program memory footprint as low as 9KB. Some architectures include a tick-less power saving mode
Support for 40+ architectures
One code base for 40+ MCU architectures and 15+ toolchains, including the latest RISC-V and ARMv8-M (Arm Cortex-M33) microcontrollers
Modular libraries
A growing number of add-on libraries used across all industries sectors, including secure local or cloud connectivity
IoT Reference Integrations
Take advantage of tested examples that include all the libraries essential to securely connect to the cloud
Multi processor scheduling



Multi processor schedulingShashank Kapoor Operating System: Multi-Processor scheduling, Multi-Core issues, Processor affinity and Load balancing
REAL TIME OPERATING SYSTEM



REAL TIME OPERATING SYSTEMprakrutijsh This document discusses real-time operating systems (RTOS). It defines an RTOS as a multitasking OS that meets time deadlines and functions in real-time constraints. The document outlines RTOS architecture, including the kernel that provides abstraction between software and hardware. It also discusses RTOS features like tasks, scheduling, timers, memory management, and inter-task communication methods. Examples of RTOS applications include medical devices, aircraft control systems, and automotive components.
Interrupts



InterruptsUrwa Shanza The document discusses interrupts in a computer system. It defines an interrupt as a signal that breaks the normal sequence of program execution to handle an event that requires immediate attention, like input from a device. There are two main types of interrupts: hardware interrupts caused by external devices, and software interrupts caused by exceptional conditions in a program like division by zero. The document outlines how interrupts work, including how the processor saves the state of the interrupted program, services the interrupt, and then restores the original program context. It also discusses interrupt priorities and how interrupts can be disabled or deferred based on priority.
Real time-system



Real time-systemysush A real-time system must respond to external stimuli within a finite time period. The correctness of real-time computations depends on both logical results and timeliness. Real-time systems require substantial design effort to ensure task deadlines are met. There are two types of real-time systems: hard where missing deadlines causes damage, and soft where missing deadlines is undesirable. Scheduling algorithms like earliest deadline first (EDF) and rate monotonic analysis (RMA) are used to ensure tasks meet deadlines in real-time systems.
Real Time OS For Embedded Systems



Real Time OS For Embedded SystemsHimanshu Ghetia This document discusses real-time operating systems for embedded systems. It defines embedded systems and real-time constraints. It describes the components of an RTOS including task management, inter-task communication, dynamic memory allocation, timers, and device I/O. It discusses when an RTOS is necessary compared to a general purpose OS and provides examples of common RTOSes.
8086 Interrupts & With DOS and BIOS by vijay



8086 Interrupts & With DOS and BIOS by vijayVijay Kumar This document discusses interrupts in microprocessors and provides examples of their use. It defines an interrupt as an event that temporarily halts normal program execution to service another event, like an I/O device requiring attention. Interrupts provide an alternative to polling that allows a CPU to serve multiple devices simultaneously. The document then gives examples of using interrupts to control a robot's movement in response to sensors as compared to polling, and provides overviews of DOS and BIOS interrupts for I/O functions like reading keyboards, displaying to screens, and communicating with serial ports.
RTOS - Real Time Operating Systems



RTOS - Real Time Operating SystemsEmertxe Information Technologies Pvt Ltd This presentation talks about Real Time Operating Systems (RTOS). Starting with fundamental concepts of OS, this presentation deep dives into Embedded, Real Time and related aspects of an OS. Appropriate examples are referred with Linux as a case-study. Ideal for a beginner to build understanding about RTOS.
Real time-embedded-system-lec-02



Real time-embedded-system-lec-02University of Computer Science and Technology The document discusses real-time embedded systems and real-time operating system (RTOS) scheduling. It introduces key concepts like hard and soft real-time systems, embedded systems, and RTOS scheduling techniques including round robin, function pointer based, and priority-based preemptive scheduling. The document also covers rate monotonic scheduling and static priority driven preemptive scheduling assumptions and theorems.
FreeRTOS introduction



FreeRTOS introductionJegadeesh Vontlin Looking for A Basic Insight on RTOS Introduction from official Guide.
This series of PPT's slides helps you to gain knowledge in FreeRTOS
Interrupts



Interruptsguest2e9811e Interrupts allow external events to suspend and later resume processes running on a computer. They improve processor utilization by allowing the operating system to interrupt running processes to respond to external events like user input or I/O device completion. There are different types of interrupts including program-generated, timer, I/O, and hardware failure interrupts. When an interrupt occurs, the CPU saves its context and executes an interrupt handling routine that calls the appropriate interrupt service routine to handle the interrupt before resuming the original process.
Rtos concepts



Rtos conceptsanishgoel The document discusses real-time operating systems (RTOS). It defines an RTOS as an operating system intended for real-time applications that must respond to events within strict time constraints. An RTOS has two main components - the "real-time" aspect which ensures responses within deadlines, and the "operating system" aspect which manages hardware resources and allows for multitasking. Common features of RTOSes include task scheduling, synchronization between tasks, and communication between tasks. The document outlines several RTOS concepts such as task management, scheduling, and inter-task communication methods like semaphores.
Real Time Operating system (RTOS) - Embedded systems



Real Time Operating system (RTOS) - Embedded systemsHariharan Ganesan A real-time operating system (RTOS) is an operating system designed for embedded systems where responses need to occur within strict time constraints. An RTOS prioritizes tasks and responds immediately to inputs. There are two types - hard RTOS which must meet deadlines to avoid catastrophic failure, and soft RTOS where occasionally missing deadlines does not cause failure. An RTOS manages tasks, schedules tasks and system resources, and handles interrupts to ensure time-critical applications perform as required.
Real Time Operating Systems for Embedded Systems



Real Time Operating Systems for Embedded SystemsAditya Vichare This document discusses real-time operating systems for embedded systems. It defines embedded systems and real-time embedded systems, noting examples like smart home security systems. It then defines real-time operating systems (RTOS) as operating systems intended for real-time applications that process data as it comes in without buffer delay. Key features of RTOS are discussed, including priority-based scheduling, minimal interrupt latency, preemptible kernels, and task-based modular development. Examples of RTOS usage include air traffic control systems and anti-lock braking systems.
Critical section problem in operating system.



Critical section problem in operating system.MOHIT DADU The critical section problem refers to ensuring that at most one process can execute its critical section, a code segment that accesses shared resources, at any given time. There are three requirements for a correct solution: mutual exclusion, meaning no two processes can be in their critical section simultaneously; progress, ensuring a process can enter its critical section if it wants; and bounded waiting, placing a limit on how long a process may wait to enter the critical section. Early attempts to solve this using flags or a turn variable were incorrect as they did not guarantee all three requirements.
evolution of operating system



evolution of operating systemAmir Khan The document discusses the evolution of operating systems from early mainframe systems to modern personal computers. It describes how early operating systems facilitated batch processing on mainframes using punch cards for input/output. Later, developments like multiprogramming, time-sharing, and multiprocessing increased CPU utilization and allowed multiple users/processes. Modern operating systems build on these foundations, with the first PC operating system being DOS and early versions of Windows sitting on top of DOS.
Process management in Operating System_Unit-2



Process management in Operating System_Unit-2mohanaps In this PPT Of operating system it covers:
Process Concept; Process Control Block; Process Scheduling; CPU Scheduling - Basic Concepts; Scheduling Algorithms – FIFO; RR; SJF; Multi- level; Multi-level feedback. Process Synchronization and deadlocks: The Critical Section Problem; Synchronization hardware; Semaphores; Classical problems; Deadlock: System model; Characterization; Deadlock prevention; Avoidance and Detection.
Apache airflow



Apache airflowPurna Chander This document provides an overview of building data pipelines using Apache Airflow. It discusses what a data pipeline is, common components of data pipelines like data ingestion and processing, and issues with traditional data flows. It then introduces Apache Airflow, describing its features like being fault tolerant and supporting Python code. The core components of Airflow including the web server, scheduler, executor, and worker processes are explained. Key concepts like DAGs, operators, tasks, and workflows are defined. Finally, it demonstrates Airflow through an example DAG that extracts and cleanses tweets.
Ad
More Related Content
What's hot (20)
Real time operating systems (rtos) concepts 1



Real time operating systems (rtos) concepts 1Abu Bakr Ramadan What is The an Operating system (OS).
What is a Real-Time OS?
Hard vs. Soft real-time.
Examples of RTOS applications.
Examples of RTOS in the market.
Real Time Operating Systems



Real Time Operating SystemsMurtadha Alsabbagh This document discusses real-time operating systems (RTOS). It defines an RTOS as a program that schedules execution in a timely manner, manages system resources, and provides a consistent foundation for developing application code. The key components of an RTOS include a scheduler, objects like tasks and semaphores, and services like interrupt management. The scheduler uses algorithms to determine which task executes when and includes important elements like context switching. Objects help with synchronization between tasks. Services perform operations on objects and other kernel functions.
Rtos Concepts



Rtos ConceptsSundaresan Sundar An RTOS differs from a common OS in that it allows direct access to the microprocessor and peripherals, helping to meet deadlines. An RTOS provides mechanisms for multitasking like scheduling, context switching, and IPC. It uses techniques like priority-based preemptive scheduling and memory management with separate stacks and heaps for tasks. Common RTOS services include timing functions, synchronization, resource protection and communication between processes.
Approaches to real time scheduling



Approaches to real time schedulingKamal Acharya This document discusses various approaches to real-time scheduling such as clock-driven, weighted round-robin, and priority-driven approaches. It also covers topics like dynamic versus static systems, effective release times and deadlines, optimality and non-optimality of algorithms, challenges in validating timing constraints, and differences between offline and online scheduling.
FreeRTOS basics (Real time Operating System)



FreeRTOS basics (Real time Operating System)Naren Chandra A presentation that covers all the basics needed to understand and start working with FreeRTOS . FreeRTOS is comparable with more than 20 controller families and 30 plus supporting tools and IDEs.
FreeRTOS is a market-leading real-time operating system (RTOS) for microcontrollers and small microprocessors. Distributed freely under the MIT open source license, FreeRTOS includes a kernel and a growing set of libraries suitable for use across all industry sectors. FreeRTOS is built with an emphasis on reliability and ease of use.
Tiny, power-saving kernel
Scalable size, with usable program memory footprint as low as 9KB. Some architectures include a tick-less power saving mode
Support for 40+ architectures
One code base for 40+ MCU architectures and 15+ toolchains, including the latest RISC-V and ARMv8-M (Arm Cortex-M33) microcontrollers
Modular libraries
A growing number of add-on libraries used across all industries sectors, including secure local or cloud connectivity
IoT Reference Integrations
Take advantage of tested examples that include all the libraries essential to securely connect to the cloud
Multi processor scheduling



Multi processor schedulingShashank Kapoor Operating System: Multi-Processor scheduling, Multi-Core issues, Processor affinity and Load balancing
REAL TIME OPERATING SYSTEM



REAL TIME OPERATING SYSTEMprakrutijsh This document discusses real-time operating systems (RTOS). It defines an RTOS as a multitasking OS that meets time deadlines and functions in real-time constraints. The document outlines RTOS architecture, including the kernel that provides abstraction between software and hardware. It also discusses RTOS features like tasks, scheduling, timers, memory management, and inter-task communication methods. Examples of RTOS applications include medical devices, aircraft control systems, and automotive components.
Interrupts



InterruptsUrwa Shanza The document discusses interrupts in a computer system. It defines an interrupt as a signal that breaks the normal sequence of program execution to handle an event that requires immediate attention, like input from a device. There are two main types of interrupts: hardware interrupts caused by external devices, and software interrupts caused by exceptional conditions in a program like division by zero. The document outlines how interrupts work, including how the processor saves the state of the interrupted program, services the interrupt, and then restores the original program context. It also discusses interrupt priorities and how interrupts can be disabled or deferred based on priority.
Real time-system



Real time-systemysush A real-time system must respond to external stimuli within a finite time period. The correctness of real-time computations depends on both logical results and timeliness. Real-time systems require substantial design effort to ensure task deadlines are met. There are two types of real-time systems: hard where missing deadlines causes damage, and soft where missing deadlines is undesirable. Scheduling algorithms like earliest deadline first (EDF) and rate monotonic analysis (RMA) are used to ensure tasks meet deadlines in real-time systems.
Real Time OS For Embedded Systems



Real Time OS For Embedded SystemsHimanshu Ghetia This document discusses real-time operating systems for embedded systems. It defines embedded systems and real-time constraints. It describes the components of an RTOS including task management, inter-task communication, dynamic memory allocation, timers, and device I/O. It discusses when an RTOS is necessary compared to a general purpose OS and provides examples of common RTOSes.
8086 Interrupts & With DOS and BIOS by vijay



8086 Interrupts & With DOS and BIOS by vijayVijay Kumar This document discusses interrupts in microprocessors and provides examples of their use. It defines an interrupt as an event that temporarily halts normal program execution to service another event, like an I/O device requiring attention. Interrupts provide an alternative to polling that allows a CPU to serve multiple devices simultaneously. The document then gives examples of using interrupts to control a robot's movement in response to sensors as compared to polling, and provides overviews of DOS and BIOS interrupts for I/O functions like reading keyboards, displaying to screens, and communicating with serial ports.
RTOS - Real Time Operating Systems



RTOS - Real Time Operating SystemsEmertxe Information Technologies Pvt Ltd This presentation talks about Real Time Operating Systems (RTOS). Starting with fundamental concepts of OS, this presentation deep dives into Embedded, Real Time and related aspects of an OS. Appropriate examples are referred with Linux as a case-study. Ideal for a beginner to build understanding about RTOS.
Real time-embedded-system-lec-02



Real time-embedded-system-lec-02University of Computer Science and Technology The document discusses real-time embedded systems and real-time operating system (RTOS) scheduling. It introduces key concepts like hard and soft real-time systems, embedded systems, and RTOS scheduling techniques including round robin, function pointer based, and priority-based preemptive scheduling. The document also covers rate monotonic scheduling and static priority driven preemptive scheduling assumptions and theorems.
FreeRTOS introduction



FreeRTOS introductionJegadeesh Vontlin Looking for A Basic Insight on RTOS Introduction from official Guide.
This series of PPT's slides helps you to gain knowledge in FreeRTOS
Interrupts



Interruptsguest2e9811e Interrupts allow external events to suspend and later resume processes running on a computer. They improve processor utilization by allowing the operating system to interrupt running processes to respond to external events like user input or I/O device completion. There are different types of interrupts including program-generated, timer, I/O, and hardware failure interrupts. When an interrupt occurs, the CPU saves its context and executes an interrupt handling routine that calls the appropriate interrupt service routine to handle the interrupt before resuming the original process.
Rtos concepts



Rtos conceptsanishgoel The document discusses real-time operating systems (RTOS). It defines an RTOS as an operating system intended for real-time applications that must respond to events within strict time constraints. An RTOS has two main components - the "real-time" aspect which ensures responses within deadlines, and the "operating system" aspect which manages hardware resources and allows for multitasking. Common features of RTOSes include task scheduling, synchronization between tasks, and communication between tasks. The document outlines several RTOS concepts such as task management, scheduling, and inter-task communication methods like semaphores.
Real Time Operating system (RTOS) - Embedded systems



Real Time Operating system (RTOS) - Embedded systemsHariharan Ganesan A real-time operating system (RTOS) is an operating system designed for embedded systems where responses need to occur within strict time constraints. An RTOS prioritizes tasks and responds immediately to inputs. There are two types - hard RTOS which must meet deadlines to avoid catastrophic failure, and soft RTOS where occasionally missing deadlines does not cause failure. An RTOS manages tasks, schedules tasks and system resources, and handles interrupts to ensure time-critical applications perform as required.
Real Time Operating Systems for Embedded Systems



Real Time Operating Systems for Embedded SystemsAditya Vichare This document discusses real-time operating systems for embedded systems. It defines embedded systems and real-time embedded systems, noting examples like smart home security systems. It then defines real-time operating systems (RTOS) as operating systems intended for real-time applications that process data as it comes in without buffer delay. Key features of RTOS are discussed, including priority-based scheduling, minimal interrupt latency, preemptible kernels, and task-based modular development. Examples of RTOS usage include air traffic control systems and anti-lock braking systems.
Critical section problem in operating system.



Critical section problem in operating system.MOHIT DADU The critical section problem refers to ensuring that at most one process can execute its critical section, a code segment that accesses shared resources, at any given time. There are three requirements for a correct solution: mutual exclusion, meaning no two processes can be in their critical section simultaneously; progress, ensuring a process can enter its critical section if it wants; and bounded waiting, placing a limit on how long a process may wait to enter the critical section. Early attempts to solve this using flags or a turn variable were incorrect as they did not guarantee all three requirements.
evolution of operating system



evolution of operating systemAmir Khan The document discusses the evolution of operating systems from early mainframe systems to modern personal computers. It describes how early operating systems facilitated batch processing on mainframes using punch cards for input/output. Later, developments like multiprogramming, time-sharing, and multiprocessing increased CPU utilization and allowed multiple users/processes. Modern operating systems build on these foundations, with the first PC operating system being DOS and early versions of Windows sitting on top of DOS.
Similar to Real time operating systems (rtos) concepts 5 (20)
Process management in Operating System_Unit-2



Process management in Operating System_Unit-2mohanaps In this PPT Of operating system it covers:
Process Concept; Process Control Block; Process Scheduling; CPU Scheduling - Basic Concepts; Scheduling Algorithms – FIFO; RR; SJF; Multi- level; Multi-level feedback. Process Synchronization and deadlocks: The Critical Section Problem; Synchronization hardware; Semaphores; Classical problems; Deadlock: System model; Characterization; Deadlock prevention; Avoidance and Detection.
Apache airflow



Apache airflowPurna Chander This document provides an overview of building data pipelines using Apache Airflow. It discusses what a data pipeline is, common components of data pipelines like data ingestion and processing, and issues with traditional data flows. It then introduces Apache Airflow, describing its features like being fault tolerant and supporting Python code. The core components of Airflow including the web server, scheduler, executor, and worker processes are explained. Key concepts like DAGs, operators, tasks, and workflows are defined. Finally, it demonstrates Airflow through an example DAG that extracts and cleanses tweets.
Stateful streaming and the challenge of state



Stateful streaming and the challenge of stateYoni Farin The different challenges of working with state in a distributed streaming data pipeline and how we solve it with the 3S architecture and Kafka streams stores based on rocksDB
dbms.ppt



dbms.pptThontadharyaThontadh Database management concepts involve managing structured data through database management systems (DBMS). A DBMS allows for efficient data retrieval and manipulation through features like querying, views, indexing and optimization. It also controls access and maintains integrity. Key concepts include the database schema, data independence, transaction processing for concurrent users, and ensuring serializability and atomicity of transactions.
dbms.ppt



dbms.pptKRISHNARAJ207 Database management concepts involve managing structured data through database management systems (DBMS). A DBMS allows for efficient data retrieval and manipulation through features like querying, views, indexing and optimization. It also controls access and maintains integrity. Key concepts include the database schema, data independence, transaction processing for concurrent users, and ensuring serializability and atomicity of transactions.
dbms.ppt



dbms.pptGeorgeSamaan9 Database management concepts involve managing structured data through database management systems (DBMS). A DBMS allows for efficient data retrieval and manipulation through features like querying, views, indexing and optimization. It also controls access and maintains integrity. Key concepts include the database schema, data independence, transaction processing for concurrent users, and ensuring serializability and atomicity of transactions. Distributed databases introduce additional challenges around concurrency control and recovery.
dbms (1).ppt



dbms (1).pptUbaidURRahman78 Database management concepts involve managing structured data through database management systems (DBMS). A DBMS allows for efficient data retrieval and manipulation through features like querying, views, indexing and optimization. It also controls access and maintains integrity. Key concepts include the database schema, data independence, transaction processing for concurrent users, and ensuring serializability and atomicity of transactions.
Dbms



DbmsMaria Stella Solon Database management concepts involve managing structured data through database management systems (DBMS). A DBMS allows for efficient data retrieval and manipulation through features like query processing, database views, and enforcing data integrity. It also provides data independence and supports multiple users accessing and modifying shared data simultaneously through concurrency control and transaction management. Knowledge bases extend databases by adding reasoning capabilities to represent knowledge and allow inference.
Presto At Treasure Data



Presto At Treasure DataTaro L. Saito Presto is used to process 15 trillion rows per day for Treasure Data customers. Treasure Data developed tools to manage Presto performance and optimize queries. They collect Presto query logs to analyze performance bottlenecks and classify queries to set implicit service level objectives. Tools like Prestobase Proxy and Presto Stella storage optimizer were created to improve low-latency access and optimize storage partitioning. Workflows using DigDag and a new tabular data format called MessageFrame are being explored to split huge queries and support incremental processing.
stigbot_beta



stigbot_betaZachary Job The document provides information about Zachary Job - Property of STIGroup, a software project written solely in C for efficiency and portability. It consists of 25,000 lines of code across 360 files and 9 modules. The software acts as an email management system that can process emails and trigger events like ticket creation in under 0.0001 seconds. While feature-complete, the developer notes areas like the GUI and documentation could be improved and some modules made more efficient.
Unit-3.ppt



Unit-3.pptsurajranjankumar1 1) Parallel algorithms divide a problem into sub-problems that can be solved concurrently. This document discusses techniques for decomposing problems into parallel tasks, including recursive decomposition, data decomposition, and partitioning input/output/intermediate data.
2) Data decomposition involves partitioning the data used in computations and assigning each partition to a separate task. This is a common technique that can induce concurrency in algorithms that operate on large data structures.
3) Partitioning can involve dividing input data, output data, or intermediate data among tasks. The goal is to identify independent work that can be done simultaneously while minimizing communication between tasks.
Distributed Model Validation with Epsilon



Distributed Model Validation with EpsilonSina Madani Scalable performance is a major challenge with current model management tools. As the size and complexity of models and model management programs increases and the cost of computing falls, one solution for improving performance of model management programs is to perform computations on multiple computers. The developed prototype demonstrates a low-overhead data-parallel approach for distributed model validation in the context of an OCL-like language. The approach minimises communication costs by exploiting the deterministic structure of programs and can take advantage of multiple cores on each (heterogenous) machine with highly configurable computational granularity. Performance evaluation shows linear improvements with more machines and processor cores, being up to 340x faster than the baseline sequential program with 88 computers.
SE-coupling and cohesion.ppt



SE-coupling and cohesion.pptvishal choudhary High cohesion and low coupling are characteristics of good design that make software components more independent and modular. Cohesion refers to how related the responsibilities of a component are, while coupling refers to interdependencies between components. The document defines and provides examples of different types of cohesion and coupling, from ideal to poor, to help understand their impacts on maintenance and modifiability.
Essential concepts of data architectures



Essential concepts of data architecturesMarco Brambilla The basic concepts that are needed to understand relational and non-relational database architectures
Lecture 5 inter process communication



Lecture 5 inter process communicationKumbirai Junior Muzavazi Inter-process communication (IPC) allows processes to communicate and synchronize actions. There are two main models - shared memory, where processes directly read/write shared memory, and message passing, where processes communicate by sending and receiving messages. Critical sections are parts of code that access shared resources and must be mutually exclusive to avoid race conditions. Semaphores can be used to achieve mutual exclusion, with operations P() and V() that decrement or increment the semaphore value to control access to the critical section. For example, in the producer-consumer problem semaphores can suspend producers if the buffer is full and consumers if empty, allowing only one process at a time in the critical section.
Unit 1- dbms.ppt



Unit 1- dbms.pptminnu41 The document provides an overview of database management concepts including:
- Database Management Systems (DBMS) which manage large structured data through efficient data retrieval and modification while allowing sharing and access control.
- Database schemas define the structure of relations (tables) and attributes (columns).
- Types of DBMS include relational, hierarchical, network, and object-oriented structures.
- Query processing retrieves and manipulates data through operations like joins and projections.
- Transaction management and concurrency control are used to maintain data integrity when multiple users access a database simultaneously.
Module 2 - PPT.pdfModule 2 - PPT.pdfModule 2 - PPT.pdfModule 2 - PPT.pdfModul...



Module 2 - PPT.pdfModule 2 - PPT.pdfModule 2 - PPT.pdfModule 2 - PPT.pdfModul...morganjohn3 This document discusses process management concepts including processes, threads, process scheduling, and inter-process communication. A process is defined as the fundamental unit of work in a system and requires resources like CPU time and memory. Key process concepts covered include process states, process layout in memory, and the process control block. Threads allow a process to execute multiple tasks simultaneously. Process scheduling and context switching are also summarized. Methods of inter-process communication like shared memory and message passing are described along with examples of client-server communication using sockets, remote procedure calls, and remote method invocation.
Ad
Recently uploaded (20)
Exploring Wayland: A Modern Display Server for the Future



Exploring Wayland: A Modern Display Server for the FutureICS Wayland is revolutionizing the way we interact with graphical interfaces, offering a modern alternative to the X Window System. In this webinar, we’ll delve into the architecture and benefits of Wayland, including its streamlined design, enhanced performance, and improved security features.
Designing AI-Powered APIs on Azure: Best Practices& Considerations



Designing AI-Powered APIs on Azure: Best Practices& ConsiderationsDinusha Kumarasiri AI is transforming APIs, enabling smarter automation, enhanced decision-making, and seamless integrations. This presentation explores key design principles for AI-infused APIs on Azure, covering performance optimization, security best practices, scalability strategies, and responsible AI governance. Learn how to leverage Azure API Management, machine learning models, and cloud-native architectures to build robust, efficient, and intelligent API solutions
FL Studio Producer Edition Crack 2025 Full Version



FL Studio Producer Edition Crack 2025 Full Versiontahirabibi60507 Copy & Past Link 👉👉
http://drfiles.net/
FL Studio is a Digital Audio Workstation (DAW) software used for music production. It's developed by the Belgian company Image-Line. FL Studio allows users to create and edit music using a graphical user interface with a pattern-based music sequencer.
Kubernetes_101_Zero_to_Platform_Engineer.pptx



Kubernetes_101_Zero_to_Platform_Engineer.pptxCloudScouts Presentacion de la primera sesion de Zero to Platform Engineer
Maxon CINEMA 4D 2025 Crack FREE Download LINK



Maxon CINEMA 4D 2025 Crack FREE Download LINKyounisnoman75 ⭕️➡️ FOR DOWNLOAD LINK : http://drfiles.net/ ⬅️⭕️
Maxon Cinema 4D 2025 is the latest version of the Maxon's 3D software, released in September 2024, and it builds upon previous versions with new tools for procedural modeling and animation, as well as enhancements to particle, Pyro, and rigid body simulations. CG Channel also mentions that Cinema 4D 2025.2, released in April 2025, focuses on spline tools and unified simulation enhancements.
Key improvements and features of Cinema 4D 2025 include:
Procedural Modeling: New tools and workflows for creating models procedurally, including fabric weave and constellation generators.
Procedural Animation: Field Driver tag for procedural animation.
Simulation Enhancements: Improved particle, Pyro, and rigid body simulations.
Spline Tools: Enhanced spline tools for motion graphics and animation, including spline modifiers from Rocket Lasso now included for all subscribers.
Unified Simulation & Particles: Refined physics-based effects and improved particle systems.
Boolean System: Modernized boolean system for precise 3D modeling.
Particle Node Modifier: New particle node modifier for creating particle scenes.
Learning Panel: Intuitive learning panel for new users.
Redshift Integration: Maxon now includes access to the full power of Redshift rendering for all new subscriptions.
In essence, Cinema 4D 2025 is a major update that provides artists with more powerful tools and workflows for creating 3D content, particularly in the fields of motion graphics, VFX, and visualization.
How to Batch Export Lotus Notes NSF Emails to Outlook PST Easily?



How to Batch Export Lotus Notes NSF Emails to Outlook PST Easily?steaveroggers Migrating from Lotus Notes to Outlook can be a complex and time-consuming task, especially when dealing with large volumes of NSF emails. This presentation provides a complete guide on how to batch export Lotus Notes NSF emails to Outlook PST format quickly and securely. It highlights the challenges of manual methods, the benefits of using an automated tool, and introduces eSoftTools NSF to PST Converter Software — a reliable solution designed to handle bulk email migrations efficiently. Learn about the software’s key features, step-by-step export process, system requirements, and how it ensures 100% data accuracy and folder structure preservation during migration. Make your email transition smoother, safer, and faster with the right approach.
Read More:- https://www.esofttools.com/nsf-to-pst-converter.html
How Valletta helped healthcare SaaS to transform QA and compliance to grow wi...



How Valletta helped healthcare SaaS to transform QA and compliance to grow wi...Egor Kaleynik This case study explores how we partnered with a mid-sized U.S. healthcare SaaS provider to help them scale from a successful pilot phase to supporting over 10,000 users—while meeting strict HIPAA compliance requirements.
Faced with slow, manual testing cycles, frequent regression bugs, and looming audit risks, their growth was at risk. Their existing QA processes couldn’t keep up with the complexity of real-time biometric data handling, and earlier automation attempts had failed due to unreliable tools and fragmented workflows.
We stepped in to deliver a full QA and DevOps transformation. Our team replaced their fragile legacy tests with Testim’s self-healing automation, integrated Postman and OWASP ZAP into Jenkins pipelines for continuous API and security validation, and leveraged AWS Device Farm for real-device, region-specific compliance testing. Custom deployment scripts gave them control over rollouts without relying on heavy CI/CD infrastructure.
The result? Test cycle times were reduced from 3 days to just 8 hours, regression bugs dropped by 40%, and they passed their first HIPAA audit without issue—unlocking faster contract signings and enabling them to expand confidently. More than just a technical upgrade, this project embedded compliance into every phase of development, proving that SaaS providers in regulated industries can scale fast and stay secure.
Adobe Photoshop Lightroom CC 2025 Crack Latest Version



Adobe Photoshop Lightroom CC 2025 Crack Latest Versionusmanhidray Copy & Past Lank 👉👉
http://drfiles.net/
Adobe Photoshop Lightroom is a photo editing and organization software application primarily used by photographers. It's designed to streamline workflows, manage large photo collections, and make adjustments to images in a non-destructive way. Lightroom is available across various platforms, including desktop, mobile (iOS and Android), and web, allowing for consistent editing and organization across devices.
Scaling GraphRAG: Efficient Knowledge Retrieval for Enterprise AI



Scaling GraphRAG: Efficient Knowledge Retrieval for Enterprise AIdanshalev If we were building a GenAI stack today, we'd start with one question: Can your retrieval system handle multi-hop logic?
Trick question, b/c most can’t. They treat retrieval as nearest-neighbor search.
Today, we discussed scaling #GraphRAG at AWS DevOps Day, and the takeaway is clear: VectorRAG is naive, lacks domain awareness, and can’t handle full dataset retrieval.
GraphRAG builds a knowledge graph from source documents, allowing for a deeper understanding of the data + higher accuracy.
Proactive Vulnerability Detection in Source Code Using Graph Neural Networks:...



Proactive Vulnerability Detection in Source Code Using Graph Neural Networks:...Ranjan Baisak As software complexity grows, traditional static analysis tools struggle to detect vulnerabilities with both precision and context—often triggering high false positive rates and developer fatigue. This article explores how Graph Neural Networks (GNNs), when applied to source code representations like Abstract Syntax Trees (ASTs), Control Flow Graphs (CFGs), and Data Flow Graphs (DFGs), can revolutionize vulnerability detection. We break down how GNNs model code semantics more effectively than flat token sequences, and how techniques like attention mechanisms, hybrid graph construction, and feedback loops significantly reduce false positives. With insights from real-world datasets and recent research, this guide shows how to build more reliable, proactive, and interpretable vulnerability detection systems using GNNs.
Avast Premium Security Crack FREE Latest Version 2025



Avast Premium Security Crack FREE Latest Version 2025mu394968 🌍📱👉COPY LINK & PASTE ON GOOGLE https://dr-kain-geera.info/👈🌍
Avast Premium Security is a paid subscription service that provides comprehensive online security and privacy protection for multiple devices. It includes features like antivirus, firewall, ransomware protection, and website scanning, all designed to safeguard against a wide range of online threats, according to Avast.
Key features of Avast Premium Security:
Antivirus: Protects against viruses, malware, and other malicious software, according to Avast.
Firewall: Controls network traffic and blocks unauthorized access to your devices, as noted by All About Cookies.
Ransomware protection: Helps prevent ransomware attacks, which can encrypt your files and hold them hostage.
Website scanning: Checks websites for malicious content before you visit them, according to Avast.
Email Guardian: Scans your emails for suspicious attachments and phishing attempts.
Multi-device protection: Covers up to 10 devices, including Windows, Mac, Android, and iOS, as stated by 2GO Software.
Privacy features: Helps protect your personal data and online privacy.
In essence, Avast Premium Security provides a robust suite of tools to keep your devices and online activity safe and secure, according to Avast.
Adobe Illustrator Crack FREE Download 2025 Latest Version



Adobe Illustrator Crack FREE Download 2025 Latest Versionkashifyounis067 🌍📱👉COPY LINK & PASTE ON GOOGLE http://drfiles.net/ 👈🌍
Adobe Illustrator is a powerful, professional-grade vector graphics software used for creating a wide range of designs, including logos, icons, illustrations, and more. Unlike raster graphics (like photos), which are made of pixels, vector graphics in Illustrator are defined by mathematical equations, allowing them to be scaled up or down infinitely without losing quality.
Here's a more detailed explanation:
Key Features and Capabilities:
Vector-Based Design:
Illustrator's foundation is its use of vector graphics, meaning designs are created using paths, lines, shapes, and curves defined mathematically.
Scalability:
This vector-based approach allows for designs to be resized without any loss of resolution or quality, making it suitable for various print and digital applications.
Design Creation:
Illustrator is used for a wide variety of design purposes, including:
Logos and Brand Identity: Creating logos, icons, and other brand assets.
Illustrations: Designing detailed illustrations for books, magazines, web pages, and more.
Marketing Materials: Creating posters, flyers, banners, and other marketing visuals.
Web Design: Designing web graphics, including icons, buttons, and layouts.
Text Handling:
Illustrator offers sophisticated typography tools for manipulating and designing text within your graphics.
Brushes and Effects:
It provides a range of brushes and effects for adding artistic touches and visual styles to your designs.
Integration with Other Adobe Software:
Illustrator integrates seamlessly with other Adobe Creative Cloud apps like Photoshop, InDesign, and Dreamweaver, facilitating a smooth workflow.
Why Use Illustrator?
Professional-Grade Features:
Illustrator offers a comprehensive set of tools and features for professional design work.
Versatility:
It can be used for a wide range of design tasks and applications, making it a versatile tool for designers.
Industry Standard:
Illustrator is a widely used and recognized software in the graphic design industry.
Creative Freedom:
It empowers designers to create detailed, high-quality graphics with a high degree of control and precision.
Meet the Agents: How AI Is Learning to Think, Plan, and Collaborate



Meet the Agents: How AI Is Learning to Think, Plan, and CollaborateMaxim Salnikov Imagine if apps could think, plan, and team up like humans. Welcome to the world of AI agents and agentic user interfaces (UI)! In this session, we'll explore how AI agents make decisions, collaborate with each other, and create more natural and powerful experiences for users.
Who Watches the Watchmen (SciFiDevCon 2025)



Who Watches the Watchmen (SciFiDevCon 2025)Allon Mureinik Tests, especially unit tests, are the developers’ superheroes. They allow us to mess around with our code and keep us safe.
We often trust them with the safety of our codebase, but how do we know that we should? How do we know that this trust is well-deserved?
Enter mutation testing – by intentionally injecting harmful mutations into our code and seeing if they are caught by the tests, we can evaluate the quality of the safety net they provide. By watching the watchmen, we can make sure our tests really protect us, and we aren’t just green-washing our IDEs to a false sense of security.
Talk from SciFiDevCon 2025
https://www.scifidevcon.com/courses/2025-scifidevcon/contents/680efa43ae4f5
Revolutionizing Residential Wi-Fi PPT.pptx



Revolutionizing Residential Wi-Fi PPT.pptxnidhisingh691197 Discover why Wi-Fi 7 is set to transform wireless networking and how Router Architects is leading the way with next-gen router designs built for speed, reliability, and innovation.
Download Wondershare Filmora Crack [2025] With Latest![Download Wondershare Filmora Crack [2025] With Latest](https://cdn.slidesharecdn.com/ss_thumbnails/neo4j-howkgsareshapingthefutureofgenerativeaiatawssummitlondonapril2024-240426125209-2d9db05d-250419-250428115407-a04afffa-thumbnail.jpg?width=560&fit=bounds)
![Download Wondershare Filmora Crack [2025] With Latest](https://cdn.slidesharecdn.com/ss_thumbnails/neo4j-howkgsareshapingthefutureofgenerativeaiatawssummitlondonapril2024-240426125209-2d9db05d-250419-250428115407-a04afffa-thumbnail.jpg?width=560&fit=bounds)
![Download Wondershare Filmora Crack [2025] With Latest](https://cdn.slidesharecdn.com/ss_thumbnails/neo4j-howkgsareshapingthefutureofgenerativeaiatawssummitlondonapril2024-240426125209-2d9db05d-250419-250428115407-a04afffa-thumbnail.jpg?width=560&fit=bounds)
![Download Wondershare Filmora Crack [2025] With Latest](https://cdn.slidesharecdn.com/ss_thumbnails/neo4j-howkgsareshapingthefutureofgenerativeaiatawssummitlondonapril2024-240426125209-2d9db05d-250419-250428115407-a04afffa-thumbnail.jpg?width=560&fit=bounds)
Download Wondershare Filmora Crack [2025] With Latesttahirabibi60507 Copy & Past Link 👉👉
http://drfiles.net/
Wondershare Filmora is a video editing software and app designed for both beginners and experienced users. It's known for its user-friendly interface, drag-and-drop functionality, and a wide range of tools and features for creating and editing videos. Filmora is available on Windows, macOS, iOS (iPhone/iPad), and Android platforms.
Download YouTube By Click 2025 Free Full Activated



Download YouTube By Click 2025 Free Full Activatedsaniamalik72555 Copy & Past Link 👉👉
https://dr-up-community.info/
"YouTube by Click" likely refers to the ByClick Downloader software, a video downloading and conversion tool, specifically designed to download content from YouTube and other video platforms. It allows users to download YouTube videos for offline viewing and to convert them to different formats.
Adobe Illustrator Crack | Free Download & Install Illustrator



Adobe Illustrator Crack | Free Download & Install Illustratorusmanhidray Copy & Link Here 👉👉
http://drfiles.net/
Adobe Illustrator is a vector graphics editor and design software, developed and marketed by Adobe, used for creating logos, icons, illustrations, and other graphics that can be scaled without loss of quality. It's a powerful tool for graphic designers, web designers, and artists who need to create crisp, scalable artwork for various applications like print, web, and mobile.
Adobe Master Collection CC Crack Advance Version 2025



Adobe Master Collection CC Crack Advance Version 2025kashifyounis067 🌍📱👉COPY LINK & PASTE ON GOOGLE http://drfiles.net/ 👈🌍
Adobe Master Collection CC (Creative Cloud) is a comprehensive subscription-based package that bundles virtually all of Adobe's creative software applications. It provides access to a wide range of tools for graphic design, video editing, web development, photography, and more. Essentially, it's a one-stop-shop for creatives needing a broad set of professional tools.
Key Features and Benefits:
All-in-one access:
The Master Collection includes apps like Photoshop, Illustrator, InDesign, Premiere Pro, After Effects, Audition, and many others.
Subscription-based:
You pay a recurring fee for access to the latest versions of all the software, including new features and updates.
Comprehensive suite:
It offers tools for a wide variety of creative tasks, from photo editing and illustration to video editing and web development.
Cloud integration:
Creative Cloud provides cloud storage, asset sharing, and collaboration features.
Comparison to CS6:
While Adobe Creative Suite 6 (CS6) was a one-time purchase version of the software, Adobe Creative Cloud (CC) is a subscription service. CC offers access to the latest versions, regular updates, and cloud integration, while CS6 is no longer updated.
Examples of included software:
Adobe Photoshop: For image editing and manipulation.
Adobe Illustrator: For vector graphics and illustration.
Adobe InDesign: For page layout and desktop publishing.
Adobe Premiere Pro: For video editing and post-production.
Adobe After Effects: For visual effects and motion graphics.
Adobe Audition: For audio editing and mixing.
Ad
Real time operating systems (rtos) concepts 5
- 1. Real Time Operating systems (RTOS) concepts Abu Bakr Mohamed Ramadan [email protected]
- 2. Content: • Task Context. • Context Switching between tasks. • Shared Data Problem. • Non Reentrant Function. • Reentrant Function. • Gray area of reentrancy. • How to protect Shared Data? • References and Read more
- 3. Task Context • Every task has it’s own context (it’s own Data). • Every Task Created has it’s own data structure called Task Control Block (TCB). • Task saves it’s data like: tasks status, ID , priority, stack pointer, Pointer to function( task itself) ……, in it’s TCB. • Task context also saved in it’s own stack and CPU registers.
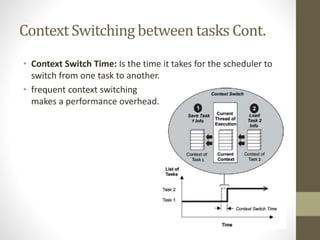
- 4. Context Switching between tasks • Context switching : Is how to switch the processor between the context of one task to the another, so the system must: • Save the state of the old process, • Then load the saved state for the new process, • The new process continues from where it left off just before the context switch. • When the task is not running, its context is frozen within the TCB, to be restored the next time the task runs. • The Dispatcher : • Is the part of the scheduler that performs context switching.
- 5. Context Switching between tasks Cont. • Context Switch Time: Is the time it takes for the scheduler to switch from one task to another. • frequent context switching makes a performance overhead.
- 6. Context Switching between tasks Cont.
- 7. Context Switching between tasks Cont.
- 8. Context Switching between tasks Cont. TCB
- 9. Context Switching between tasks Cont. TCB
- 10. Context Switching between tasks Cont.
- 11. Context Switching between tasks Cont.
- 13. Non Reentrant Function. • Is a function that can’t be used between more than one task. • Can’t be interrupted or a data loss will happen. • Example:
- 14. Reentrant Function. • Is a function that can be used between more than one task with out fear of data corruption. • Can be interrupted at any time and resumed without loss of data. • Reentrant functions either: • Use local variables, Or use protected global variables. • Can’t Call other non reentrant function.
- 15. Gray area of reentrancy • Some Functions and some operation on a shared data are processor and compiler dependent. • Example: • printf() Function Is reentrant or non reentrant? • The answer is it’s depend on the processor and on the compiler. • A++
- 16. How to protect Shared Data? • Using Mutual Exclusion access. • Examples on Mutual Exclusion methods are: • Disable and enable interrupts, • Disabling Scheduling, and • Using Semaphores.
- 17. References and Read more: • Real-Time Concepts for Embedded Systems book by Qing Li and Carolyn. • http://www.e-reading.club/book.php?book=102147 • An Embedded Software Primer by David E. Simon. • http://www.amazon.com/Embedded-Software-Primer-David- Simon/dp/020161569X • Linux Kernel Embedded Systems Building Blocks 2e by Jean J. Labrosse. • http://www.amazon.com/Embedded-Systems-Building-Blocks- Ready/dp/0879306041 • FreeRTOS website. • http://www.freertos.org




