Reverse Engineering for exploit writers
- 1. Nibin Varghese iViZ Security, Kolkata Reverse Engineering for Exploit Writers
- 2. Agenda Exploitation Overview Reverse Engineering Tools Case Study MS08-067
- 3. Exploitation Overview Software vulnerabilities exist Reliable exploitation techniques exist Stack overflow Heap overflow Exploit mitigation Prevent or impede a class of vulnerabilities Patch the vulnerability Disable the service Generic mitigations
- 4. Reverse Engineering Tools IDA Pro Bindiff Plugin for IDA Ollydbg or Immunity Debugger or Windbg Debugging Symbols Sysinternals tool suite Any scripting language to write PoC (Python, Ruby etc)
- 5. MS08-067 Windows Server Service Vulnerability Out of band release Details: Error in netapi32.dll when processing directory traversal character sequence in path names. This can be exploited to corrupt stack memory by example sending RPC requests containing specially crafted path names to the Server service component – secunia.com
- 7. Structure of X86 stack frame Stack grows towards lower addresses Local Variables Saved EBP Saved IP Arguments
- 8. Classical Overflow Return address overwritten with address of shellcode Local Variables Saved EBP Saved IP Arguments
- 9. Reverse engineering the patch Demo
- 10. The Bug Decompiled by Alexander Sotirov Visual demo of the bug
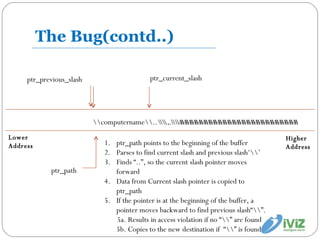
- 11. The Bug(contd..) ptr_path \\computername\\..\\..\\AAAAAAAAAAAAAAAAAAAAAAAAA ptr_previous_slash ptr_current_slash ptr_path points to the beginning of the buffer Parses to find current slash and previous slash‘\\’ Finds “..”, so the current slash pointer moves forward Data from Current slash pointer is copied to ptr_path If the pointer is at the beginning of the buffer, a pointer moves backward to find previous slash“\\”. 5a. Results in access violation if no “\\” are found 5b. Copies to the new destination if “\\” is found \\..\\AAAAAAAAAAAAAAAAAAAAAAAAA Lower Address Higher Address
- 12. path Return Address of vulnerable_function Saved EBP Netapi32!NetpwPathCanonicalize vulnerable_function( wchar *path ) wcscpy(dst,src) Return Address of wcscpy Saved EBP ptr_path points to the beginning of the buffer Parses to find current slash and previous slash‘\\’ Finds “..”, so the current slash pointer moves forward Data from Current slash pointer is copied to ptr_path If the pointer is at the beginning of the buffer, a pointer moves backward to find previous slash“\\”. 5a. Results in access violation if no “\\” are found 5b. Copies to the new destination if “\\” is found \\..\\AAAAAA \\..\\AAAAAAAAAAA (ptr1 – 1) ptr2 ptr1 ptr_path \\c\\..\\.. \\AAAAAAAAAAA AAAA AAAA AAAA Shell Code
- 13. The Bug (contd..) Not a classical buffer overflow The destination buffer is large enough to copy the contents from source The hunt for “\\” if the pointer points to the beginning of the buffer makes it a BUG
- 14. Ready for PoC Identify the vector of exploitation 3 possible ways wcslen of path Predictable location of “\\” in the stack after repeated interaction Metasploit way of calculating the device_length
- 15. Mass Exploitation If no NX, return to stack and execute shellcode If NX enabled, disable DEP/NX by abusing Win32 API NtSetInformationProcess and return to stack and execute shellcode. Refer Skape and Skywing paper on Uninformed Journal “Bypassing Windows Hardware-enforced Data Execution Prevention” In Vista, ASLR makes return addresses unpredictable.
- 16. Thank You Thanks to Research Team@iViZ Security Thanks to Clubhack 08 organizers Thanks to all the attendees
- 17. Ready for Phase 2 ?