Scalable and secure sharing of public health record using attribute based Encryption
- 1. SCALABLE AND SECURE SHARING OF PERSONAL HEALTH RECORDS IN CLOUD COMPUTING USING ATTRIBUTE BASED ENCRYPTION By Shreyank M. Byadagi Email:[email protected]
- 2. AGENDA: 1. Objectives of project. 2. Problem definition. 3. Literature survey. 4. Methodology. 5. Applications. 6. Implementation carried out. 7. References.
- 3. OBJECTIVES: • The main aim of this system is to provide secure patient- centric PHR access and efficient key management at the same time. • The key idea is to divide the system into multiple security domains according to the different users’ data access requirements.
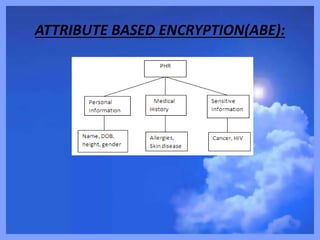
- 4. PROBLEM DEFINITION: Personal health record(PHR) is meant for health information exchange , this data is outsourced for maintenance like cloud providers. CHALLENGES : • PHR data is prone to unauthorized access. • Access needs to be secure. OUR SOLUTION: • Attribute Based Encryption(ABE) techniques are used to encrypt patient’s PHR file. • A high degree of patient privacy guaranteed.
- 5. LITERATURE SURVEY: • J. Benaloh, proposed a scheme “Patient Controlled Encryption: Ensuring Privacy of Electronic Medical Records,” in which a file can be uploaded without key distribution and it is highly efficient. • J. Hur and D. K. Noh proposed a scheme “Attribute-Based Revocation in Data Outsourcing Systems” with immediate capability, instead of periodical revocation.
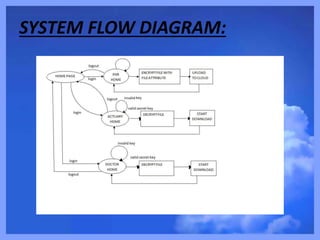
- 8. ER-Diagram:
- 9. EXISTING SYSTEM: • Due to the high cost of building and maintaining specialized data centers, many PHR services are outsourced . • The main concern is about whether the patients could actually control the sharing of their sensitive personal health information (PHI), especially when they are stored on a third- party server which people may not fully trust.
- 10. EXISTING SYSTEM(Contd…): Hey, I got it !! Lets modify & send!!!
- 11. PROPOSED SYSTEM: • It is the promising method to encrypt the PHRs before outsourcing. • Risks of privacy exposure , scalability in key management , flexible access are important challenges towards data access control. • Attribute Based Encryption(ABE) techniques are used to encrypt patient’s PHR file.
- 13. ALGORITHMS: • Advanced Encryption Standard(AES) • Message Digest5(MD5)
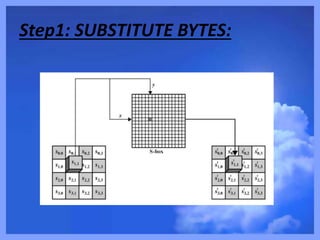
- 14. ADVANCED ENCRYPTION STANDARD: • Step1:Substitute bytes. • Step2. Shift rows. • Step3. Mix Columns. • Step4. Add Round Key
- 16. Contd….
- 20. MESSAGE DIGEST5(MD5): • Step1: Append padding bits: Message is pad so its length is 448 mod 512 • Step2: Append Length Append a 64-bit length value to message Generate a message with 512 bits in length • Step3: Initialize MD buffer Initialize a 4-word (128-bit) MD buffer (A, B, C, D) Word A: 01 23 45 67 Word B: 89 AB CD EF Word C: FE DC BA 98 Word D: 76 54 32 10 • Step4: Process Message in 16-word block Process message in 16- word (512-bit) blocks • Step5: Output
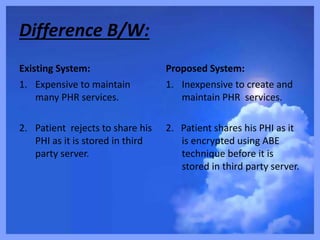
- 21. Difference B/W: Existing System: 1. Expensive to maintain many PHR services. 2. Patient rejects to share his PHI as it is stored in third party server. Proposed System: 1. Inexpensive to create and maintain PHR services. 2. Patient shares his PHI as it is encrypted using ABE technique before it is stored in third party server.
- 23. APPLICATIONS: • Hospital Management. • Health Care Website.
- 24. MODULES: • PHR Owner module • Cloud Server Module • Attribute based Access Policy Module • Data confidentiality Module Front end of our project is prepared with the help of JSP.
- 25. REQUIREMENTS: HARDWARE REQUIREMENTS:- • Processor - Pentium –III • Speed - 1.1 Ghz • RAM - 256 MB(min) • Hard Disk - 20 GB • Floppy Drive - 1.44 MB • Key Board - Standard Windows Keyboard • Mouse - Two or Three Button Mouse • Monitor - SVGA
- 26. REQUIREMENTS(CONTD..) SOFTWARE REQUIREMENTS:- • Operating System : Windows95/98/2000/XP • TOOL USED : ECLIPSE • Front End : JAVA
- 27. REFERENCES: • M. Li, S. Yu, K. Ren, and W. Lou, “Securing personal health records in cloud computing: Patient-centric and fine-grained data access control in multi-owner settings”. • H. Lohr, A.-R. Sadeghi, and M. Winandy, “Securing the e- health cloud”. • “The health insurance portability and accountability act”.
- 29. THANK YOU!!!!