Sdn pres v2-Software-defined networks
- 1. SDN security Supervised by Dr Ashraf Tammam prepared by Mahmoud Fathy
- 2. Outline Introduction Security via SDN Threats Mininet Future work Conclusion
- 3. Outline Introduction Security via SDN Threats Mininet Future work Conclusion
- 4. Software-defined networks Network operators need to configure each individual network device separately using vendor specific commands. Networks are dynamic, and operators have little or no mechanisms to automatically respond to network events. With an SDN, network flows are controlled at the level of the global network abstraction, rather than at the level of the individual devices, usually, but not necessarily, with the aid of the OpenFlow protocol. Network devices become simple forwarding devices. The control logic is implemented in a logical controller. Introduction
- 5. Software-defined networks Separation of the control plane from the data plane that lays the ground to the Software Defined Networking paradigm. Data plane is responsible for packet forwarding and it is widely known by its OSI seven layers. Control plane serves the Data plane, it shapes the traffic that the network exists to carry. Introduction
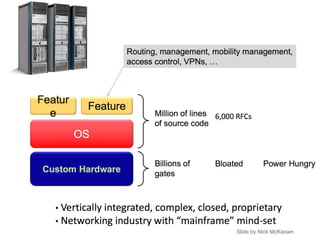
- 6. Software-defined networks Traditional networks Operating system Specialised packet forwarding hardware Operating system Specialised packet forwarding hardware Operating system Specialised packet forwarding hardware Operating system Specialised packet forwarding hardware Operating system Specialised packet forwarding hardware SSH/CLI
- 7. Software-defined networks packet forwarding hardware packet forwarding hardware packet forwarding hardware packet forwarding hardware packet forwarding hardware Network Operating System runs Controller App App App southbound API northbound API
- 8. Slide by Nick McKeown
- 10. Software-defined networks Open Networking Foundation (ONF) is a user-driven organization dedicated to the promotion and adoption of Software-Defined Networking (SDN) through open standards development. Working groups continue to analyze SDN requirements, evolve the OpenFlow Standard to address the needs of commercial deployments, and research new standards to expand SDN benefits. website: opennetworking.org Open networking foundation
- 11. Software-defined networks Open networking foundation Open Networking Foundation (ONF) is a user-driven organization dedicated to the promotion and adoption of Software-Defined Networking (SDN) through open standards development. Working groups continue to analyze SDN requirements, evolve the OpenFlow Standard to address the needs of commercial deployments, and research new standards to expand SDN benefits. website: opennetworking.org
- 12. Software-defined networks An open interface to packet forwarding, not the standard but it is the most widespread used. The origins of OpenFlow, when a PhD student at Stanford University developed something called Ethane, intended as a way of centrally managing global policy. That idea eventually led to what become known as OpenFlow, thanks to more research conducted jointly by teams at Stanford and the University of California, Berkeley. This is how the controller configures the switches’ Flow tables. OpenFlow
- 13. Software-defined networks Network Operating System App features Operating System (Windows, Linux or Mac) CPU (Intel, AMD) OpenFlow Instruction set OpenFlow analogy
- 14. Software-defined networks OpenFlow Header Payload Match Match on any header, or new header Action Forward to port(s), drop, send to controller. Overwrite header. Forward at specific bit-rate.
- 15. Software-defined networks OpenFlow Switch Port MAC src MAC dst Eth type VLAN ID IP src IP dst IP protoco l TCP sport TCP dport Action VLAN switching Switch Port MAC src MAC dst Eth type VLAN ID IP src IP dst IP protoco l TCP sport TCP dport Action Routing Switch Port MAC src MAC dst Eth type VLAN ID IP src IP dst IP protoco l TCP sport TCP dport Action Firewall 00:2f.. vlan1 port6 port61.2.3.4 drop22 X X X X X X X X X X X XX X X XX X X X XX X XX X
- 16. Software-defined networks Network Operating System Control Program OpenFlow IF header = x, forward to port 4 IF header = y, overwrite header with q then forward to port 5 IF header = other, forward to me Flow Tabl e
- 17. Software-defined networks Advantages Greater agility resulting from reduced reliance on switch installation and configuration, and centralised management and control.
- 18. Software-defined networks Advantages An OpenFlow-only switch would be extremely simple and inexpensive to build 10 Gigabit Ethernet OpenFlow switch from IBM
- 19. Software-defined networks Advantages Reduced dependence on vendors’ equipment product cycles.
- 20. Software-defined networks Advantages The centralization of the control logic in a controller with global knowledge of the network state simplifies the development of more sophisticated network functions. http://sourceforge.net/projects/itransformer/
- 21. Software-defined networks Advantages Enabling the introduction of sophisticated network policies simultaneously with the operation (e.g., security, resource control, prioritization). Connect Load balance Secure …
- 22. Software-defined networks Other advantages A control program can automatically react to spurious changes of the network state. Easier to test and deploy newly researched protocols. Facilitates troubleshooting. One advantage of this capability is that it enables the network to dynamically respond to application requirements.
- 26. Software-defined networks Empower network owners/operators. Increase the pace of innovation. Diversify the supply chain. Build a robust foundation. How SDN will shape networking
- 27. Outline Introduction Security via SDN Threats Mininet Future work Conclusion
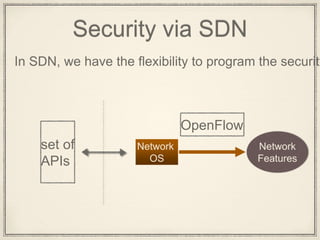
- 28. Security via SDN In SDN, we have the flexibility to program the security set of APIs Network OS Network Features OpenFlow
- 29. Security via SDN This reduces security expenses by limiting the need to purchase new hardware.
- 30. Security via SDN The controller has a full view of the network which gives it an advantage implementing security policies.
- 32. Security via SDN Control of multiple simultaneous security policies thro Authentication IPS Firewall … Controller
- 33. Security via SDN No need to have dedicated tap devices as it can be replaced by openflow instructions. Match any, forward to A A
- 34. Security via SDN It allows us to build vague boundaries make it impossible to determine where security devices, such as firewalls, are deployed. Attacker
- 35. Security via SDN It allows us to build vague boundaries make it impossible to determine where security devices, such as firewalls, are deployed. Attacker Where ?! Firewall functionality is distributed on switches
- 36. Security via SDN A scheme proposed by ONF, Automated Malware Quarantine (AMQ). AMQ detects and isolates insecure network devices. It identifies the problem and automatically downloads the necessary patches to resolve it. After the threat has been contained, AMQ software automatically allows the device to rejoin the network. It has the potential to reduce operating expenses.
- 37. Outline Introduction Security via SDN Threats Mininet Future work Conclusion
- 38. Threats Traditional networks have inherited protections, proprietary nature of network devices, the heterogeneity of software, and the decentralized structure of the control plane represent defences against common threats. A common standard (e.g., OpenFlow) among vendors and clients can also increase the risk. Softwares are always subject to bugs and a score of other vulnerabilities. Centralization of the “network intelligence” in implies that anyone with access to the servers that host the control software can potentially control the entire network. Concerns
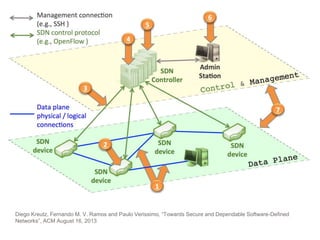
- 39. Diego Kreutz, Fernando M. V. Ramos and Paulo Verissimo, “Towards Secure and Dependable Software-Defined Networks”, ACM August 16, 2013
- 40. Can be used to target switches and controllers This threat can be triggered by faulty (non-malicious) devices or by a malicious user. An attacker can use network elements to launch a DoS attack against OpenFlow switches by exhausting TCAMs or controller resources Faked traffic flows Threats 1 The use of intrusion detection systems could help identify abnormal flows, or enforce a policy to bound the rate for control plane requests.
- 41. One single switch could be used to drop or slow down packets in the network, clone or deviate network traffic. This is mostly performed for data theft purposes. Attacker has the ability inject traffic or forged requests to overload the controller or neighbouring switches. Threats Vulnerabilities in switches2 Mechanisms to monitor and detect abnormal behaviour of network devices can be a useful to defeat this kind of threats.
- 42. Diego Kreutz, Fernando M. V. Ramos and Paulo Verissimo, “Towards Secure and Dependable Software-Defined Networks”, ACM August 16, 2013
- 43. Can be used to generate DoS attacks or for data theft. Control plane communications rely on using TLS/SSL which is considered a non-guarantee for secure communication. Once an attacker gains access to the control plane, it may be capable of aggregating enough power force (in terms of the number of switches under its control) to launch DDoS attacks. Threats Attacks on control plane communications3 The use of automated device association mechanisms may be considered, dedicated to guarantee trust between the control plane and data plane devices.
- 44. The most severe threats to SDNs as a malicious controller could compromise the entire network Use of a common intrusion detection system isn’t a solution, as it is practically hard to find the exact combination of events that trigger a particular behavior to label a controller as malicious Similarly, a malicious application can potentially do anything it pleases in the network. Threats Vulnerabilities in controllers4 Security policies enforcing correct behavior might be mapped onto those techniques, restricting which interfaces an application can use and what kind of rules it can generate to program the network.
- 45. Diego Kreutz, Fernando M. V. Ramos and Paulo Verissimo, “Towards Secure and Dependable Software-Defined Networks”, ACM August 16, 2013
- 46. There is a lack of mechanisms to ensure trust between the controller and management applications. The techniques used to certify network devices are different from those used for applications. . Threats Management applications5 Mechanisms for autonomic trust management could be used to guarantee that the application is trusted during its lifetime.
- 47. Used in SDNs to access the network controller These machines are already an exploitable target in traditional networks, what makes it worse being that the threat surface as seen from a single compromised machine increases dramatically in SDNs. Threats Vulnerabilities in administrative stations6 The use of protocols requiring more than one credential verification.
- 48. Diego Kreutz, Fernando M. V. Ramos and Paulo Verissimo, “Towards Secure and Dependable Software-Defined Networks”, ACM August 16, 2013
- 49. Forensics and remediation would allow to understand the cause of a detected problem and proceed to a fast and secure mode recovery. There is a lack of trusted resources for forensics and remediation in SDN. In order to investigate and establish facts about an incident, we need reliable information from all components of the network This data will only be useful if its trustworthiness (integrity, authenticity, etc.) can be assured. Remediation requires safe and reliable system snapshots to guarantee a fast and correct recovery of network elements to a known working state. Threats Forensics and remediation7 In order to be effective, logging and tracing should be indelible. Furthermore, logs should be stored in remote and secure environments.
- 50. Slide by Nick McKeown
- 51. Future Work Controllers are designed in order that they can be easily replicated, are capable of interoperating and providing support to execute applications across controllers. The switches will also need to be able to dynamically associate with more than one controller. Diversity helps improve the robustness of the system. In summary, replication, diversity, dynamic switch association Security and Dependability
- 52. Conclusion We have been introduced to SDN which is a new paradigm in networking that is needed for today’s applications. OpenFlow made SDN possible but it haven’t been designed with security in mind. SDN is vulnerable to several threats but enough work can be done to mitigate this. A handy tool to emulate SDN and examine new schemes in networks before deployment. There is research trend to design security schemes for SDN before widely deploying it.
- 53. References https://www.opennetworking.org/ An attempt to motivate and clarify Software-Defined Networking (SDN), video by Professor Scott Shenker Diego Kreutz, Fernando M. V. Ramos and Paulo Verissimo, “Towards Secure and Dependable Software-Defined Networks”, ACM August 16, 2013