Secure Code Review 101
14 likes6,862 views
Secure code review is probably the most effective technique to identify security bugs early in the system development lifecycle. When used together with automated and manual penetration testing, code review can significantly increase the cost effectiveness of an application security verification effort. This presentation explain how can we start secure code review effectively.
1 of 25
Downloaded 519 times




















![Review Session Management
● .Net ASPX web.config
<authentication mode=”Forms”>
<forms loginUrl=”member_login.aspx”
cookieless=”UseCookies”
requireSSL=”true”
path=”/MyApplication” />
</authentication>
● Java web.xml
<session-config>
<cookie-config>
<secure>true</secure>
</cookie-config>
</session-config>
● PHP.ini
session.cookie_lifetime=0
session.use_cookies=On
session.use_only_cookies=On
session.use_strict_mode=On
session.cookie_httponly=On
session.cookie_secure=On
session.gc_maxlifetime=[choose smallest possible]
session.use_trans_sid=Off](https://image.slidesharecdn.com/securecodereview101-161119132006/85/Secure-Code-Review-101-23-320.jpg)


Ad
Recommended
Application Security Verification Standard Project



Application Security Verification Standard ProjectNarudom Roongsiriwong, CISSP This presentation is the overview of OWASP Application Security Verification Standard Project (ASVS) V3.0.1, presented in Thailand Cybersecurity Week arranged by ETDA on Jun 26, 2017
Secure coding practices



Secure coding practicesScott Hurrey This document provides an overview of secure coding practices for developers. It discusses secure design principles like defense in depth and least privilege. It also covers secure coding practices such as input validation, escaping, and HTML sanitization. The document provides examples of good and bad code related to reflecting user input, access control, and request authenticity. It also defines key security terms and outlines strategies for handling user input and encoding output.
Secure code practices



Secure code practicesHina Rawal Secure code best practices for developers. And comparison of 2017 and 2021 OWASP top 10 with description of vulnerability and mitigation.
Security risk management



Security risk managementG Prachi The United Nations uses a risk management process that involves assessing the criticality of programs to balance security risks. It uses a risk matrix to determine risk levels and requires a program criticality assessment for activities with high or very high residual risks. The assessment evaluates the contribution of activities to strategic results and their likelihood of implementation against criteria to designate them as Priority 1 activities that are lifesaving or directed by the Secretary-General. Risk level and program criticality are determined separately without consideration of each other.
Secure Coding 101 - OWASP University of Ottawa Workshop



Secure Coding 101 - OWASP University of Ottawa WorkshopPaul Ionescu This presentation introduces students to the concepts of software weakness, attack and secure coding practices.
Secure coding presentation Oct 3 2020



Secure coding presentation Oct 3 2020Moataz Kamel Secure coding is the practice of developing software securely by avoiding security vulnerabilities. It involves understanding the application's attack surface and using techniques like input validation, secure authentication, access control, and encrypting sensitive data. The OWASP organization provides free tools and guidelines to help developers code securely, such as their Top 10 security risks and cheat sheets on issues like injection, authentication, and access control. Developers should use static and dynamic application security testing tools to identify vulnerabilities and continuously learn about secure coding best practices.
Azure Penetration Testing



Azure Penetration TestingCheah Eng Soon The document discusses Azure penetration testing. It provides an agenda that covers an overview of common Azure services attacked, tools used for testing, and guidelines. It describes how Microsoft's blue and red teams work together on testing. Policies prohibit attacks on other customers or social engineering. Encouraged tests include using trial accounts and informing Microsoft of any vulnerabilities found. Steps outlined include identifying attack surfaces, data collection, vulnerability scanning, and penetration testing public-facing Azure services using tools like MicroBurst. Securing databases and using encryption are also addressed. A demo of vulnerability identification is promised.
Static Analysis Security Testing for Dummies... and You



Static Analysis Security Testing for Dummies... and YouKevin Fealey Most enterprise application security teams have at least one Static Analysis Security Testing (SAST) tool in their tool-belt; but for many, the tool never leaves the belt. SAST tools have gotten a reputation for being slow, error-prone, and difficult to use; and out of the box, many of them are – but with a little more knowledge behind how these tools are designed, a SAST tool can be a valuable part of any security program.
In this talk, we’ll help you understand the strengths and weaknesses of SAST tools by illustrating how they trace your code for vulnerabilities. You’ll see out-of-the-box rules for commercial and open-source SAST tools, and learn how to write custom rules for the widely-used open source SAST tool, PMD. We’ll explain the value of customizing tools for your organization; and you’ll learn how to integrate SAST technologies into your existing build and deployment pipelines. Lastly, we’ll describe many of the common challenges organizations face when deploying a new security tool to security or development teams, as well as some helpful hints to resolve these issues
Application Security



Application SecurityReggie Niccolo Santos * Brief timeline on cyber attack history
* Definition
* Foundations of Security
* Definition of Terms
* Threat Modeling
* Application Vulnerability Categories
* Core Security Principles
* Web Application Security
* Risks and Risk Mitigation/Control Measures
Secure coding practices



Secure coding practicesMohammed Danish Amber Secure Coding Practices - PHP.
How to safe gaurd your application from CSRF, Session Hijacking, SQLi
CSSLP & OWASP & WebGoat



CSSLP & OWASP & WebGoatSurachai Chatchalermpun Challenge Web Application Today!!!
Promote CSSLP Certification.
Introduce OWASP 2010 Top 10 Risks?
Practice with Web Goat?
For Education only.
Penetration Testing Basics



Penetration Testing BasicsRick Wanner The document provides an overview of penetration testing basics from a presentation by The Internet Storm Center, SANS Institute, and GIAC Certification Program. It discusses the Internet Storm Center, SANS/GIAC training and certifications, common cyber threats, the methodology for penetration testing, tools used for various stages like reconnaissance, scanning, exploitation, and analysis, and the importance of reporting and mitigation strategies.
Introduction to penetration testing



Introduction to penetration testingNezar Alazzabi this is a simple presentation that will give you a general overview and introduction to penetration testing.
The Security Code Review Guide



The Security Code Review GuideNicola Pietroluongo Is your code secure? Do you know what are the practices in secure code review? In this talk you will see the important aspects of the various controls to build a reference when conducting secure code reviews in PHP.
Introduction to Web Application Penetration Testing



Introduction to Web Application Penetration TestingAnurag Srivastava Web Application Pentesting
* Process to check and penetrate the security of a web application or a website
* process involves an active analysis of the application for any weaknesses, technical flaws, or vulnerabilities
* Any security issues that are found will be presented to the system owner, together with an assessment of the impact, a proposal for mitigation or a technical solution.
Penetration Testing Tutorial | Penetration Testing Tools | Cyber Security Tra...



Penetration Testing Tutorial | Penetration Testing Tools | Cyber Security Tra...Edureka! ( ** Cyber Security Training: https://www.edureka.co/cybersecurity-certification-training ** )
This Edureka PPT on "Penetration Testing" will help you understand all about penetration testing, its methodologies, and tools. Below is the list of topics covered in this session:
What is Penetration Testing?
Phases of Penetration Testing
Penetration Testing Types
Penetration Testing Tools
How to perform Penetration Testing on Kali Linux?
Cyber Security Playlist: https://bit.ly/2N2jlNN
Cyber Security Blog Series: https://bit.ly/2AuULkP
Instagram: https://www.instagram.com/edureka_lea...
Facebook: https://www.facebook.com/edurekaIN/
Twitter: https://twitter.com/edurekain
LinkedIn: https://www.linkedin.com/company/edureka
Security testing fundamentals



Security testing fundamentalsCygnet Infotech Security Testing is deemed successful when the below attributes of an application are intact
- Authentication
- Authorization
- Availability
- Confidentiality
- Integrity
- Non-Repudiation
Testing must start early to minimize defects and cost of quality. Security testing must start right from the Requirements Gathering phase to make sure that the quality of end-product is high.
This is to ensure that any intentional/unintentional unforeseen action does not halt or delay the system.
Understanding Cross-site Request Forgery



Understanding Cross-site Request ForgeryDaniel Miessler This document provides an overview of cross-site request forgery (CSRF) attacks. It discusses how CSRF works, forcing victims to perform actions on a website without their knowledge. Common defenses like using nonces or CAPTCHAs are described. The document also covers how to validate if an issue is truly a CSRF vulnerability and lists some example attack vectors. Key takeaways emphasize the importance of validating any potential CSRF issue affects state, is sensitive, and has non-unique requests.
OWASP Top 10 Web Application Vulnerabilities



OWASP Top 10 Web Application VulnerabilitiesSoftware Guru This document provides an overview of the OWASP Top 10 Risk Rating Methodology. It explains how risks are rated based on four factors: threat agent, attack vector, technical impact, and business impact. Each factor is given a rating of 1-3 (easy to difficult) and these ratings are multiplied together to calculate an overall weighted risk rating. An example of how this methodology would be applied to an SQL injection vulnerability is also provided.
Vulnerability assessment and penetration testing



Vulnerability assessment and penetration testingAbu Sadat Mohammed Yasin This document discusses vulnerability assessment and penetration testing. It defines them as two types of vulnerability testing that search for known vulnerabilities and attempt to exploit vulnerabilities, respectively. Vulnerability assessment uses automated tools to detect known issues, while penetration testing employs hacking techniques to demonstrate how deeply vulnerabilities could be exploited like an actual attacker. Both are important security practices for identifying weaknesses and reducing risks, but require different skills and have different strengths, weaknesses, frequencies, and report outputs. Reasons for vulnerabilities include insecure coding, limited testing, and misconfigurations. The document outlines common vulnerability and attack types as well as how vulnerability assessment and penetration testing are typically conducted.
Application Security - Your Success Depends on it



Application Security - Your Success Depends on itWSO2 Traditional information security mainly revolves around network and operating system (OS) level protection. Regardless of the level of security guarding those aspects, the system can be penetrated and the entire deployment can be brought down if your application's security isn't taken into serious consideration. Information security should ideally start at the application level, before network and OS level security is ensured. To achieve this, security needs to be integrated into the application at the software development phase.
In this session, Dulanja will discuss the following:
The importance of application security - why network and OS security is insufficient.
Challenges in securing your application.
Making security part of the development lifecycle.
API Security Fundamentals



API Security FundamentalsJosé Haro Peralta Slides for my webinar "API Security Fundamentals". They cover
👉 𝐎𝐖𝐀𝐒𝐏’𝐬 𝐭𝐨𝐩 𝟏𝟎 API security vulnerabilities with suggestions on how to avoid them, including the 2019 and the 2023 versions.
👉 API authorization and authentication using 𝐎𝐀𝐮𝐭𝐡 and 𝐎𝐈𝐃𝐂
👉 How certain 𝐀𝐏𝐈 𝐝𝐞𝐬𝐢𝐠𝐧𝐬 expose vulnerabilities and how to prevent them
👉 APIs sit within a wider system and therefore API security requires a 𝐡𝐨𝐥𝐢𝐬𝐭𝐢𝐜 𝐚𝐩𝐩𝐫𝐨𝐚𝐜𝐡. I’ll talk about elements “around the API” that also need to be protected
👉 automating API 𝐬𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐭𝐞𝐬𝐭𝐢𝐧𝐠
What is Penetration Testing?



What is Penetration Testing?btpsec This presentation describes penetration testing with a Who, What, Where, When, and How approach. In the presentation, you may discover the common pitfalls of a bad penetration test and you could identify a better one. You should be able to recognize and differentiate both looking at the methods (attitude) and result.
Simplified Security Code Review Process



Simplified Security Code Review ProcessSherif Koussa This document summarizes a presentation about simplifying secure code reviews. It discusses defining an effective security code review process, including reconnaissance, threat modeling, automation, manual review, confirmation, and reporting. It also discusses using the OWASP Top 10 list to focus code reviews, and defining trust boundaries to identify areas of code to review for specific vulnerabilities. The goal is to introduce a simplified process that can help development teams integrate security code reviews into their workflow.
Security testing



Security testingTabăra de Testare Security Testing involves testing applications and systems to ensure security and proper functionality. It includes testing input validation, internal processing, output validation, and more. Common types of security testing are security auditing, vulnerability scanning, risk assessment, ethical hacking, and penetration testing. The OWASP Top 10 includes SQL injection, cross-site scripting, and broken authentication and session management as common vulnerabilities.
Practical Malware Analysis: Ch 0: Malware Analysis Primer & 1: Basic Static T...



Practical Malware Analysis: Ch 0: Malware Analysis Primer & 1: Basic Static T...Sam Bowne This document provides an overview of basic static malware analysis techniques. It discusses using antivirus scanners, hashing files, and finding strings to identify malware without executing it. It also covers analyzing the Portable Executable (PE) file format used in Windows executables, including examining the PE header, imported and exported functions, linked libraries, and sections like .text and .rsrc. The document demonstrates various tools for these static analysis tasks like HashCalc, strings, PEview, Dependency Walker, and Resource Hacker.
Vulnerability and Assessment Penetration Testing



Vulnerability and Assessment Penetration TestingYvonne Marambanyika VAPT defines a wide range of security testing services to ascertain and address cyber security exposures. It includes vulnerability testing through perimeter scans for missing patches or custom exploits to bypass perimeters, as well as penetration testing by simulating real-world attacks to provide a point-in-time assessment of vulnerabilities and threats to a network infrastructure. Customers can inquire more about these security testing and analysis services by contacting the company.
Application Security Architecture and Threat Modelling



Application Security Architecture and Threat ModellingPriyanka Aash 95% of attacks are against “Web Servers and Web Applications”
Security Architecture and SDLC
3 Tier – Web App Architecture
Would you trust the code?
Traditional SDLC
Secure SDLC
SAST vs. DAST
Shift Left Security



Shift Left Securitygjdevos "Shift Lef Security" What the funk does that mean?
In the agile, lean, DevOps communities people talk about improving security by "shifting left". Patterns and tools are emerging, or re-emerging, that make security less of a pain in the development process while also making applications more secure.
Security in open source projects



Security in open source projectsJose Manuel Ortega Candel The document discusses security in open source projects. It covers vulnerabilities in dependencies, detecting vulnerabilities in code bases, and improving security. Functionality is often prioritized over security. Various coding flaws are described like buffer overflows. Tools for analyzing dependencies, detecting vulnerabilities statically and dynamically are presented, like OWASP Dependency-Check, Snyk, SonarQube, ZAP. Best practices for open source security include following responsible disclosure policies and auditing code bases regularly.
Ad
More Related Content
What's hot (20)
Application Security



Application SecurityReggie Niccolo Santos * Brief timeline on cyber attack history
* Definition
* Foundations of Security
* Definition of Terms
* Threat Modeling
* Application Vulnerability Categories
* Core Security Principles
* Web Application Security
* Risks and Risk Mitigation/Control Measures
Secure coding practices



Secure coding practicesMohammed Danish Amber Secure Coding Practices - PHP.
How to safe gaurd your application from CSRF, Session Hijacking, SQLi
CSSLP & OWASP & WebGoat



CSSLP & OWASP & WebGoatSurachai Chatchalermpun Challenge Web Application Today!!!
Promote CSSLP Certification.
Introduce OWASP 2010 Top 10 Risks?
Practice with Web Goat?
For Education only.
Penetration Testing Basics



Penetration Testing BasicsRick Wanner The document provides an overview of penetration testing basics from a presentation by The Internet Storm Center, SANS Institute, and GIAC Certification Program. It discusses the Internet Storm Center, SANS/GIAC training and certifications, common cyber threats, the methodology for penetration testing, tools used for various stages like reconnaissance, scanning, exploitation, and analysis, and the importance of reporting and mitigation strategies.
Introduction to penetration testing



Introduction to penetration testingNezar Alazzabi this is a simple presentation that will give you a general overview and introduction to penetration testing.
The Security Code Review Guide



The Security Code Review GuideNicola Pietroluongo Is your code secure? Do you know what are the practices in secure code review? In this talk you will see the important aspects of the various controls to build a reference when conducting secure code reviews in PHP.
Introduction to Web Application Penetration Testing



Introduction to Web Application Penetration TestingAnurag Srivastava Web Application Pentesting
* Process to check and penetrate the security of a web application or a website
* process involves an active analysis of the application for any weaknesses, technical flaws, or vulnerabilities
* Any security issues that are found will be presented to the system owner, together with an assessment of the impact, a proposal for mitigation or a technical solution.
Penetration Testing Tutorial | Penetration Testing Tools | Cyber Security Tra...



Penetration Testing Tutorial | Penetration Testing Tools | Cyber Security Tra...Edureka! ( ** Cyber Security Training: https://www.edureka.co/cybersecurity-certification-training ** )
This Edureka PPT on "Penetration Testing" will help you understand all about penetration testing, its methodologies, and tools. Below is the list of topics covered in this session:
What is Penetration Testing?
Phases of Penetration Testing
Penetration Testing Types
Penetration Testing Tools
How to perform Penetration Testing on Kali Linux?
Cyber Security Playlist: https://bit.ly/2N2jlNN
Cyber Security Blog Series: https://bit.ly/2AuULkP
Instagram: https://www.instagram.com/edureka_lea...
Facebook: https://www.facebook.com/edurekaIN/
Twitter: https://twitter.com/edurekain
LinkedIn: https://www.linkedin.com/company/edureka
Security testing fundamentals



Security testing fundamentalsCygnet Infotech Security Testing is deemed successful when the below attributes of an application are intact
- Authentication
- Authorization
- Availability
- Confidentiality
- Integrity
- Non-Repudiation
Testing must start early to minimize defects and cost of quality. Security testing must start right from the Requirements Gathering phase to make sure that the quality of end-product is high.
This is to ensure that any intentional/unintentional unforeseen action does not halt or delay the system.
Understanding Cross-site Request Forgery



Understanding Cross-site Request ForgeryDaniel Miessler This document provides an overview of cross-site request forgery (CSRF) attacks. It discusses how CSRF works, forcing victims to perform actions on a website without their knowledge. Common defenses like using nonces or CAPTCHAs are described. The document also covers how to validate if an issue is truly a CSRF vulnerability and lists some example attack vectors. Key takeaways emphasize the importance of validating any potential CSRF issue affects state, is sensitive, and has non-unique requests.
OWASP Top 10 Web Application Vulnerabilities



OWASP Top 10 Web Application VulnerabilitiesSoftware Guru This document provides an overview of the OWASP Top 10 Risk Rating Methodology. It explains how risks are rated based on four factors: threat agent, attack vector, technical impact, and business impact. Each factor is given a rating of 1-3 (easy to difficult) and these ratings are multiplied together to calculate an overall weighted risk rating. An example of how this methodology would be applied to an SQL injection vulnerability is also provided.
Vulnerability assessment and penetration testing



Vulnerability assessment and penetration testingAbu Sadat Mohammed Yasin This document discusses vulnerability assessment and penetration testing. It defines them as two types of vulnerability testing that search for known vulnerabilities and attempt to exploit vulnerabilities, respectively. Vulnerability assessment uses automated tools to detect known issues, while penetration testing employs hacking techniques to demonstrate how deeply vulnerabilities could be exploited like an actual attacker. Both are important security practices for identifying weaknesses and reducing risks, but require different skills and have different strengths, weaknesses, frequencies, and report outputs. Reasons for vulnerabilities include insecure coding, limited testing, and misconfigurations. The document outlines common vulnerability and attack types as well as how vulnerability assessment and penetration testing are typically conducted.
Application Security - Your Success Depends on it



Application Security - Your Success Depends on itWSO2 Traditional information security mainly revolves around network and operating system (OS) level protection. Regardless of the level of security guarding those aspects, the system can be penetrated and the entire deployment can be brought down if your application's security isn't taken into serious consideration. Information security should ideally start at the application level, before network and OS level security is ensured. To achieve this, security needs to be integrated into the application at the software development phase.
In this session, Dulanja will discuss the following:
The importance of application security - why network and OS security is insufficient.
Challenges in securing your application.
Making security part of the development lifecycle.
API Security Fundamentals



API Security FundamentalsJosé Haro Peralta Slides for my webinar "API Security Fundamentals". They cover
👉 𝐎𝐖𝐀𝐒𝐏’𝐬 𝐭𝐨𝐩 𝟏𝟎 API security vulnerabilities with suggestions on how to avoid them, including the 2019 and the 2023 versions.
👉 API authorization and authentication using 𝐎𝐀𝐮𝐭𝐡 and 𝐎𝐈𝐃𝐂
👉 How certain 𝐀𝐏𝐈 𝐝𝐞𝐬𝐢𝐠𝐧𝐬 expose vulnerabilities and how to prevent them
👉 APIs sit within a wider system and therefore API security requires a 𝐡𝐨𝐥𝐢𝐬𝐭𝐢𝐜 𝐚𝐩𝐩𝐫𝐨𝐚𝐜𝐡. I’ll talk about elements “around the API” that also need to be protected
👉 automating API 𝐬𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐭𝐞𝐬𝐭𝐢𝐧𝐠
What is Penetration Testing?



What is Penetration Testing?btpsec This presentation describes penetration testing with a Who, What, Where, When, and How approach. In the presentation, you may discover the common pitfalls of a bad penetration test and you could identify a better one. You should be able to recognize and differentiate both looking at the methods (attitude) and result.
Simplified Security Code Review Process



Simplified Security Code Review ProcessSherif Koussa This document summarizes a presentation about simplifying secure code reviews. It discusses defining an effective security code review process, including reconnaissance, threat modeling, automation, manual review, confirmation, and reporting. It also discusses using the OWASP Top 10 list to focus code reviews, and defining trust boundaries to identify areas of code to review for specific vulnerabilities. The goal is to introduce a simplified process that can help development teams integrate security code reviews into their workflow.
Security testing



Security testingTabăra de Testare Security Testing involves testing applications and systems to ensure security and proper functionality. It includes testing input validation, internal processing, output validation, and more. Common types of security testing are security auditing, vulnerability scanning, risk assessment, ethical hacking, and penetration testing. The OWASP Top 10 includes SQL injection, cross-site scripting, and broken authentication and session management as common vulnerabilities.
Practical Malware Analysis: Ch 0: Malware Analysis Primer & 1: Basic Static T...



Practical Malware Analysis: Ch 0: Malware Analysis Primer & 1: Basic Static T...Sam Bowne This document provides an overview of basic static malware analysis techniques. It discusses using antivirus scanners, hashing files, and finding strings to identify malware without executing it. It also covers analyzing the Portable Executable (PE) file format used in Windows executables, including examining the PE header, imported and exported functions, linked libraries, and sections like .text and .rsrc. The document demonstrates various tools for these static analysis tasks like HashCalc, strings, PEview, Dependency Walker, and Resource Hacker.
Vulnerability and Assessment Penetration Testing



Vulnerability and Assessment Penetration TestingYvonne Marambanyika VAPT defines a wide range of security testing services to ascertain and address cyber security exposures. It includes vulnerability testing through perimeter scans for missing patches or custom exploits to bypass perimeters, as well as penetration testing by simulating real-world attacks to provide a point-in-time assessment of vulnerabilities and threats to a network infrastructure. Customers can inquire more about these security testing and analysis services by contacting the company.
Application Security Architecture and Threat Modelling



Application Security Architecture and Threat ModellingPriyanka Aash 95% of attacks are against “Web Servers and Web Applications”
Security Architecture and SDLC
3 Tier – Web App Architecture
Would you trust the code?
Traditional SDLC
Secure SDLC
SAST vs. DAST
Similar to Secure Code Review 101 (20)
Shift Left Security



Shift Left Securitygjdevos "Shift Lef Security" What the funk does that mean?
In the agile, lean, DevOps communities people talk about improving security by "shifting left". Patterns and tools are emerging, or re-emerging, that make security less of a pain in the development process while also making applications more secure.
Security in open source projects



Security in open source projectsJose Manuel Ortega Candel The document discusses security in open source projects. It covers vulnerabilities in dependencies, detecting vulnerabilities in code bases, and improving security. Functionality is often prioritized over security. Various coding flaws are described like buffer overflows. Tools for analyzing dependencies, detecting vulnerabilities statically and dynamically are presented, like OWASP Dependency-Check, Snyk, SonarQube, ZAP. Best practices for open source security include following responsible disclosure policies and auditing code bases regularly.
Demystify Information Security & Threats for Data-Driven Platforms With Cheta...



Demystify Information Security & Threats for Data-Driven Platforms With Cheta...Chetan Khatri The document discusses information security for data-driven platforms and open source projects. It motivates the importance of security through examples of data breaches. It covers topics like encryption, authentication, vulnerabilities in open source code, and how to evaluate open source libraries for security issues. The document demonstrates penetration testing tools like Vega and SQLMap to find vulnerabilities like SQL injection in web applications.
DevSecOps: What Why and How : Blackhat 2019



DevSecOps: What Why and How : Blackhat 2019NotSoSecure Global Services This document discusses DevSecOps, including what it is, why it is needed, and how to implement it. DevSecOps aims to integrate security tools and a security-focused culture into the development lifecycle. It allows security to keep pace with rapid development. The document outlines how to incorporate security checks at various stages of the development pipeline from pre-commit hooks to monitoring in production. It provides examples of tools that can be used and discusses cultural and process aspects of DevSecOps implementation.
Agile Secure Development



Agile Secure DevelopmentBosnia Agile How to make the agile team work with security requirements? To get secure coding practices into agile development is often hard work. A security functional requirement might be included in the sprint, but to get secure testing, secure architecture and feedback of security incidents working is not an easy talk for many agile teams. In my role as Scrum Master and security consultant I have developed a recipe of 7 steps that I will present to you. Where we will talk about agile secure development, agile threat modelling, agile security testing and agile workflows with security. Many of the steps can be made without costly tools, and I will present open source alternatives for all steps. This to make a test easier and to get a lower startup of your teams security process.
Shift Left Security



Shift Left Securitygjdevos In the agile, lean, devops communities people talk about improving security by "shifting left". Patterns and tools are emerging, or re-emerging, that make security less of a pain in the development process while also making applications more secure.
Course_Presentation cyber --------------.pptx



Course_Presentation cyber --------------.pptxssuser020436 This document provides an agenda for a web application penetration testing course. The course aims to share cybersecurity knowledge in Arabic and focus on practical application. It will cover Linux basics, Burp Suite, common web vulnerabilities at easy and medium levels, and advanced topics like XSS and CSRF. Students will learn how to find data leaks, analyze protocols and network traffic, exploit vulnerabilities, and earn money through bug bounty programs.
Coding Security: Code Mania 101



Coding Security: Code Mania 101Narudom Roongsiriwong, CISSP The document discusses several coding security practices for developing secure software, including input validation, output handling, parameterizing queries, identity and authentication controls, and access controls. It provides examples and recommendations for implementing each practice to prevent common vulnerabilities like injection and data tampering. The goal is to integrate security at the code level from the beginning to reduce risks.
BroadStrong Software Room Profile



BroadStrong Software Room ProfileHenry Li This document profiles BroadStrong Software Room, a software development company owned by Henry Li. It provides details about:
1. Henry Li's background and experience founding BroadStrong Software Room, which employs about 15 core employees.
2. The various technology platforms and development tools BroadStrong can use for projects, including Windows, Linux, Java, PHP, .NET, and mobile platforms.
3. Contact information is provided at the end for Henry Li and BroadStrong Software Room.
Serverless survival kit



Serverless survival kitSteve Houël This document discusses serverless applications and Ippon Technologies. It provides an overview of what serverless computing is, how a monolith application could be broken into serverless functions, best practices for serverless development including packaging code and continuous deployment, and tools for monitoring serverless applications on AWS like CloudWatch. It also advertises that Ippon Technologies is hiring for cloud-focused roles like Cloud Cost Architect and Site Reliability Engineers.
MongoDB .local Bengaluru 2019: New Encryption Capabilities in MongoDB 4.2: A ...



MongoDB .local Bengaluru 2019: New Encryption Capabilities in MongoDB 4.2: A ...MongoDB New encryption capabilities in MongoDB 4.2 provide client-side field-level encryption that protects sensitive data. The encryption is performed by the client drivers using modern cryptography, keeping encrypted fields opaque to the database server and operators. This allows individual fields to be encrypted per document with customer-managed keys. The presentation provides a history of database security methods and covers the new encryption in terms of design, cryptography used, and developer experience. A code example demonstrates how to configure and use the new encryption capabilities.
OWASP ZAP Workshop for QA Testers



OWASP ZAP Workshop for QA TestersJavan Rasokat The document discusses OWASP Zed Attack Proxy (ZAP), a free and open source web application security scanner. It can be used by pentesters, developers, and testers to detect vulnerabilities. ZAP passively and actively scans applications to find issues. It can be integrated into CI/CD pipelines and automated with APIs, command line tools, and programming libraries. The document provides examples of using ZAP to perform passive scanning, active scanning, and automation for testers.
Resume ram-krishna



Resume ram-krishnaRam Krishna | BitHostIn Ram Krishna Resume | Software Developer | DevOps | Server Admin | Cloud Engineer | AWS | GCP Class.
Introduction to Backend Development (1).pptx



Introduction to Backend Development (1).pptxOsuGodbless Backend development is the behind-the-scenes work that powers websites and applications. It involves storing and managing data, implementing business logic, ensuring security and reliability, and enabling scalability. While the frontend handles what users see, the backend orchestrates their experience through content delivery, response to actions, and personalized experiences based on user data. Programming languages are crucial tools for backend developers, underpinning functionality through code. Popular languages include Python, Java, and Node.js. Key backend processes include user registration, which involves receiving and validating data, database interaction, and response to the user.
Webinar: Scaling MongoDB



Webinar: Scaling MongoDBMongoDB Has your app taken off? Are you thinking about scaling? MongoDB makes it easy to horizontally scale out with built-in automatic sharding, but did you know that sharding isn't the only way to achieve scale with MongoDB?
In this webinar, we'll review three different ways to achieve scale with MongoDB. We'll cover how you can optimize your application design and configure your storage to achieve scale, as well as the basics of horizontal scaling. You'll walk away with a thorough understanding of options to scale your MongoDB application.
Topics covered include:
- Scaling Vertically
- Hardware Considerations
- Index Optimization
- Schema Design
- Sharding
WebGoat.SDWAN.Net in Depth



WebGoat.SDWAN.Net in Depthyalegko This document summarizes a presentation on SD-WAN security given by Denis Kolegov and Oleg Broslavsky. It discusses the results of an SD-WAN internet census that found thousands of exposed SD-WAN devices, many with known vulnerabilities. Common vulnerabilities found in SD-WAN products include XSS, CSRF, insecure authentication, and the use of hardcoded cryptographic keys. Exploits are demonstrated against several commercial SD-WAN products to highlight real-world risks. The presenters advocate for improving SD-WAN security and responsible vulnerability disclosure.
WebGoat.SDWAN.Net in Depth: SD-WAN Security Assessment 



WebGoat.SDWAN.Net in Depth: SD-WAN Security Assessment Sergey Gordeychik Denis Kolegov, Oleg Broslavsky, Power of Community 2018, Seoul, Korea
Today, «SD-WAN» is a very hot and attractive topic. Software-defined WAN (SD-WAN) is a technology based on software-defined network (SDN) approach applied to wide area networks (WAN) in enterprise networks. According to Gartner’s predictions study, more than 50% of routers will be replaced with SD-WAN solutions by 2020.
In this presentation, we disclose a set of vulnerabilities in widespread and most popular SD-WAN products including Citrix NetScaler and Silver Peak EdgeConnect. We present the new results of our research, consider some technical details of the insecure design and found vulnerabilities, and describe different attack scenarios that may allow an attacker to compromise SD-WAN control and data planes.
MongoDB SoCal 2020: Migrate Anything* to MongoDB Atlas



MongoDB SoCal 2020: Migrate Anything* to MongoDB AtlasMongoDB This presentation discusses migrating data from other data stores to MongoDB Atlas. It begins by explaining why MongoDB and Atlas are good choices for data management. Several preparation steps are covered, including sizing the target Atlas cluster, increasing the source oplog, and testing connectivity. Live migration, mongomirror, and dump/restore options are presented for migrating between replicasets or sharded clusters. Post-migration steps like monitoring and backups are also discussed. Finally, migrating from other data stores like AWS DocumentDB, Azure CosmosDB, DynamoDB, and relational databases are briefly covered.
OWASP_Top_Ten_Proactive_Controls_v32.pptx



OWASP_Top_Ten_Proactive_Controls_v32.pptxnmk42194 The OWASP Top Ten Proactive Controls 2.0 document introduces new proactive controls to the Top Ten list and provides more practical examples and contributions from the community. It includes some best practices for building secure mobile apps. The document then describes 10 proactive controls addressing common vulnerabilities like injection, XSS, access control issues etc. It provides details on each control with examples and references.
Ad
More from Narudom Roongsiriwong, CISSP (20)
Biometric Authentication.pdf



Biometric Authentication.pdfNarudom Roongsiriwong, CISSP - NIST guidelines support limited use of biometrics for authentication and recommend it only be used as part of multi-factor authentication along with a physical authenticator. Biometrics have limitations including probabilistic matching and inability to easily revoke templates.
- When biometrics are used, NIST requires a false match rate of 1 in 1000 or better, implementation of liveness detection, and preference for local rather than central matching to mitigate attacks.
- For AAL2 authentication on mobile, NIST recommends using multi-factor cryptographic software authenticators activated by a second factor like biometrics. Examples include FIDO protocols and Android's CryptoObject for authenticating to remote servers.
- Behavioral biometrics analyzing user
Security Shift Leftmost - Secure Architecture.pdf



Security Shift Leftmost - Secure Architecture.pdfNarudom Roongsiriwong, CISSP Security shifting left addressed earlier security concerns in the software development life-cycle (that is, left in a left-to-right schedule diagram). The question is "Are the security concerns in software development life-cycle sufficient?". This presentation will introduce "Shifting Leftmost in Security" which focusing in Security Architecture. Software implementation in medium and large enterprise environments requires well defined architecture especially in security requirements. The scope in this presentation will cover secure application infrastructure and secure application design.
Secure Design: Threat Modeling



Secure Design: Threat ModelingNarudom Roongsiriwong, CISSP Threat modeling is an approach for analyzing the security of an application. It is a structured approach that enables you to identify, quantify, and address the security risks associated with an application.
Security Patterns for Software Development



Security Patterns for Software DevelopmentNarudom Roongsiriwong, CISSP The document summarizes security patterns for software development. It begins with introducing the speaker and their background in information security. It then defines security patterns as design patterns that can achieve security goals like confidentiality, integrity, and availability. The document outlines different approaches to incorporating security like using UML/OCL models, vulnerability analysis, and model-driven security. It discusses the value of patterns and why they are useful for security. The main body provides examples of security patterns, including encrypting messages, microservice access control, federation and assertions, strong authentication, and pinning.
How Good Security Architecture Saves Corporate Workers from COVID-19



How Good Security Architecture Saves Corporate Workers from COVID-19Narudom Roongsiriwong, CISSP During COVID-19 pandemic, staying home is one of the key factors to save lives in the way of Social Distancing. However it is not so easy to move most of the employees in the large enterprise which does not always on the Internet like banking sector to work from home without well-planned architecture. This presentation is talking about security architecture that my company chosen to build on in the environment of multi-cloud architecture and how 60% of employees can work from home with this security architecture.
Secure Software Design for Data Privacy



Secure Software Design for Data PrivacyNarudom Roongsiriwong, CISSP This presentation was presented in OWASP Thailand Chapter Meeting 5/2019 (July 25). It is about how to design data architecture and secure software in order to protect organization from regulation's penalty causes by data breach. However, this slide is still incomplete and need more clarification, so it would be useful for those attended the meeting. Be careful for distribution.
Blockchain and Cryptocurrency for Dummies



Blockchain and Cryptocurrency for DummiesNarudom Roongsiriwong, CISSP Blockchain technology is a distributed ledger platform that provides open and transparent transaction information with integrity and non-repudiation based on modern cryptography. It is also the technology behind many cryptocurrencies. This presentation will give fundamental knowledge on how blockchain works, its cryptography implementation, cryptocurrency definition and related terms and also blockchain use cases.
DevSecOps 101



DevSecOps 101Narudom Roongsiriwong, CISSP Security teams are often seen as roadblocks to rapid development or operations implementations, slowing down production code pushes. As a result, security organizations will likely have to change so they can fully support and facilitate cloud operations.
This presentation will explain how DevOps and information security can co-exist through the application of a new approach referred to as DevSecOps.
National Digital ID Platform Technical Forum



National Digital ID Platform Technical ForumNarudom Roongsiriwong, CISSP Thailand's National Digital ID Platform is an infrastructure for connecting all parties such as Relying Parties, Identity Provider,s Authoritative Sources and users to do authentication, consent, identify or sign electronically. This presentation update the progress of the technical team as of November 27, 2017
IoT Security



IoT SecurityNarudom Roongsiriwong, CISSP The growth of embedded systems connecting to the Internet or "Internet of Things" (IoT) increases year by year. Thus, the IoT ecosystems become new targets of the attackers. This presentation will talk about the basic principle of information security, why we need to secure IoT ecosystems, and also the vulnerabilities and solutions from OWASP.
Embedded System Security: Learning from Banking and Payment Industry



Embedded System Security: Learning from Banking and Payment IndustryNarudom Roongsiriwong, CISSP Nowaday, embedded systems are widely used and connected to networks, especially the Internet. This become the Internet of Things (IoT) era. When a device is on the Internet, it may be attacked or intentionally used by an unauthorized persons. How can we make IoT devices secure under the limited resources?
This presentation will explain the lesson learned from banking and card payment industry how the embedded systems process financial transaction reliably and securely.
Secure Your Encryption with HSM



Secure Your Encryption with HSMNarudom Roongsiriwong, CISSP Hardware Security Modules (HSMs) are widely use for cryptography key management in many areas such as PKI, card payment, trusted platform modules, etc. However they are rarely used in in-house software development.
This presentation will explain about why we need the key management and its fundamental, overview of HSM and how it take parts in key management, HSM selection criterias, and finally, an idea to make a web service wrapper easier to adopt by developers those lack of knowledge in cryptography programming.
Top 10 Bad Coding Practices Lead to Security Problems



Top 10 Bad Coding Practices Lead to Security ProblemsNarudom Roongsiriwong, CISSP This presentation contains the list of top 10 bad practices those lead to security problems in MY opinion according to code reviews. Those practices are
“eval” Function,
Ignore Exception,
Throw Generic Exception,
Expose Sensitive Data or Debug Statement,
Compare Floating Point with Normal Operator,
Not validate Input,
Dereference to Null Object,
Not Use Parameterized Query,
Hard-Coded Credentials,
Back-Door or Secret Page
OWASP Top 10 Proactive Control 2016 (C5-C10)



OWASP Top 10 Proactive Control 2016 (C5-C10)Narudom Roongsiriwong, CISSP The OWASP Top Ten Proactive Controls 2016 is a list of security techniques that should be included in every software development project. They are ordered by order of importance, with control #1 being the most important. This presentation is the second part which contains control #5 to #10 in the following controls
C5: Implement Identity and Authentication Controls
C6: Implement Appropriate Access Controls
C7: Protect Data
C8: Implement Logging and Intrusion Detection
C9: Leverage Security Frameworks and Libraries
C10: Error and Exception Handling
Securing the Internet from Cyber Criminals



Securing the Internet from Cyber CriminalsNarudom Roongsiriwong, CISSP Securing the organization from cyber crimes cannot be done only by the perimeter defense. One of the most important knowledge is to understand the cyber criminal operations. This presentation explain about 2 common operations those can be found all over the internet and how to defense.
Secure Software Development Adoption Strategy



Secure Software Development Adoption StrategyNarudom Roongsiriwong, CISSP This document discusses adopting a secure software development strategy at Kiatnakin Bank. It recommends starting with a goal like the OWASP Top 10 controls, establishing an application security team, processes like code reviews and testing, baseline frameworks and guidelines, introducing security design concepts, and setting security checkpoints. The presentation emphasizes building knowledge, leading change, and getting management support to successfully adopt secure development practices.
Secure PHP Coding



Secure PHP CodingNarudom Roongsiriwong, CISSP PHP is the most commonly used server-side programming and deployed more than 80% in web server all over the world. However, PHP is a 'grown' language rather than deliberately engineered, making writing insecure PHP applications far too easy and common. If you want to use PHP securely, then you should be aware of all its pitfalls.
Application Security: Last Line of Defense



Application Security: Last Line of DefenseNarudom Roongsiriwong, CISSP For more than a decade, organizations trust in network perimeter protection such as firewalls or intrusion prevention systems to protect their IT infrastructures from the internet threats. However, traditional network security protection may not be sufficient to safeguard from the new threats targetting security flaws in web servers and web applications. In order to defend the threats related to these services and applications, it is essential to understand the risks commonly found in web applications.
This presentation explains the needs of application security as the last line of defense, common web application risks and security measures need to be implemented alongside the development of web applications.
AnyID and Privacy



AnyID and PrivacyNarudom Roongsiriwong, CISSP AnyID is the infrastructure of Thailand's National e-Payment Initiative. The presentation explains National e-Payment big picture, AnyID as a payment Infrastructure, AnyID security design & implementation and also privacy comparison between “With” and “Without” AnyID.
OWASP Top 10 A4 – Insecure Direct Object Reference



OWASP Top 10 A4 – Insecure Direct Object ReferenceNarudom Roongsiriwong, CISSP Insecure Direct Object References occur when an application provides direct access to objects based on user-supplied input. As a result of this vulnerability attackers can bypass authorization and access resources in the system directly, for example database records or files.
This presentation explain how to discover this vulnerability in application, how to test and how to mitigate the risk.
Ad
Recently uploaded (20)
Noah Loul Shares 5 Steps to Implement AI Agents for Maximum Business Efficien...



Noah Loul Shares 5 Steps to Implement AI Agents for Maximum Business Efficien...Noah Loul Artificial intelligence is changing how businesses operate. Companies are using AI agents to automate tasks, reduce time spent on repetitive work, and focus more on high-value activities. Noah Loul, an AI strategist and entrepreneur, has helped dozens of companies streamline their operations using smart automation. He believes AI agents aren't just tools—they're workers that take on repeatable tasks so your human team can focus on what matters. If you want to reduce time waste and increase output, AI agents are the next move.
Splunk Security Update | Public Sector Summit Germany 2025



Splunk Security Update | Public Sector Summit Germany 2025Splunk Splunk Security Update
Sprecher: Marcel Tanuatmadja
Role of Data Annotation Services in AI-Powered Manufacturing



Role of Data Annotation Services in AI-Powered ManufacturingAndrew Leo From predictive maintenance to robotic automation, AI is driving the future of manufacturing. But without high-quality annotated data, even the smartest models fall short.
Discover how data annotation services are powering accuracy, safety, and efficiency in AI-driven manufacturing systems.
Precision in data labeling = Precision on the production floor.
Massive Power Outage Hits Spain, Portugal, and France: Causes, Impact, and On...



Massive Power Outage Hits Spain, Portugal, and France: Causes, Impact, and On...Aqusag Technologies In late April 2025, a significant portion of Europe, particularly Spain, Portugal, and parts of southern France, experienced widespread, rolling power outages that continue to affect millions of residents, businesses, and infrastructure systems.
Special Meetup Edition - TDX Bengaluru Meetup #52.pptx



Special Meetup Edition - TDX Bengaluru Meetup #52.pptxshyamraj55 We’re bringing the TDX energy to our community with 2 power-packed sessions:
🛠️ Workshop: MuleSoft for Agentforce
Explore the new version of our hands-on workshop featuring the latest Topic Center and API Catalog updates.
📄 Talk: Power Up Document Processing
Dive into smart automation with MuleSoft IDP, NLP, and Einstein AI for intelligent document workflows.
HCL Nomad Web – Best Practices and Managing Multiuser Environments



HCL Nomad Web – Best Practices and Managing Multiuser Environmentspanagenda Webinar Recording: https://www.panagenda.com/webinars/hcl-nomad-web-best-practices-and-managing-multiuser-environments/
HCL Nomad Web is heralded as the next generation of the HCL Notes client, offering numerous advantages such as eliminating the need for packaging, distribution, and installation. Nomad Web client upgrades will be installed “automatically” in the background. This significantly reduces the administrative footprint compared to traditional HCL Notes clients. However, troubleshooting issues in Nomad Web present unique challenges compared to the Notes client.
Join Christoph and Marc as they demonstrate how to simplify the troubleshooting process in HCL Nomad Web, ensuring a smoother and more efficient user experience.
In this webinar, we will explore effective strategies for diagnosing and resolving common problems in HCL Nomad Web, including
- Accessing the console
- Locating and interpreting log files
- Accessing the data folder within the browser’s cache (using OPFS)
- Understand the difference between single- and multi-user scenarios
- Utilizing Client Clocking
AI Changes Everything – Talk at Cardiff Metropolitan University, 29th April 2...



AI Changes Everything – Talk at Cardiff Metropolitan University, 29th April 2...Alan Dix Talk at the final event of Data Fusion Dynamics: A Collaborative UK-Saudi Initiative in Cybersecurity and Artificial Intelligence funded by the British Council UK-Saudi Challenge Fund 2024, Cardiff Metropolitan University, 29th April 2025
https://alandix.com/academic/talks/CMet2025-AI-Changes-Everything/
Is AI just another technology, or does it fundamentally change the way we live and think?
Every technology has a direct impact with micro-ethical consequences, some good, some bad. However more profound are the ways in which some technologies reshape the very fabric of society with macro-ethical impacts. The invention of the stirrup revolutionised mounted combat, but as a side effect gave rise to the feudal system, which still shapes politics today. The internal combustion engine offers personal freedom and creates pollution, but has also transformed the nature of urban planning and international trade. When we look at AI the micro-ethical issues, such as bias, are most obvious, but the macro-ethical challenges may be greater.
At a micro-ethical level AI has the potential to deepen social, ethnic and gender bias, issues I have warned about since the early 1990s! It is also being used increasingly on the battlefield. However, it also offers amazing opportunities in health and educations, as the recent Nobel prizes for the developers of AlphaFold illustrate. More radically, the need to encode ethics acts as a mirror to surface essential ethical problems and conflicts.
At the macro-ethical level, by the early 2000s digital technology had already begun to undermine sovereignty (e.g. gambling), market economics (through network effects and emergent monopolies), and the very meaning of money. Modern AI is the child of big data, big computation and ultimately big business, intensifying the inherent tendency of digital technology to concentrate power. AI is already unravelling the fundamentals of the social, political and economic world around us, but this is a world that needs radical reimagining to overcome the global environmental and human challenges that confront us. Our challenge is whether to let the threads fall as they may, or to use them to weave a better future.
Generative Artificial Intelligence (GenAI) in Business



Generative Artificial Intelligence (GenAI) in BusinessDr. Tathagat Varma My talk for the Indian School of Business (ISB) Emerging Leaders Program Cohort 9. In this talk, I discussed key issues around adoption of GenAI in business - benefits, opportunities and limitations. I also discussed how my research on Theory of Cognitive Chasms helps address some of these issues
Procurement Insights Cost To Value Guide.pptx



Procurement Insights Cost To Value Guide.pptxJon Hansen Procurement Insights integrated Historic Procurement Industry Archives, serves as a powerful complement — not a competitor — to other procurement industry firms. It fills critical gaps in depth, agility, and contextual insight that most traditional analyst and association models overlook.
Learn more about this value- driven proprietary service offering here.
What is Model Context Protocol(MCP) - The new technology for communication bw...



What is Model Context Protocol(MCP) - The new technology for communication bw...Vishnu Singh Chundawat The MCP (Model Context Protocol) is a framework designed to manage context and interaction within complex systems. This SlideShare presentation will provide a detailed overview of the MCP Model, its applications, and how it plays a crucial role in improving communication and decision-making in distributed systems. We will explore the key concepts behind the protocol, including the importance of context, data management, and how this model enhances system adaptability and responsiveness. Ideal for software developers, system architects, and IT professionals, this presentation will offer valuable insights into how the MCP Model can streamline workflows, improve efficiency, and create more intuitive systems for a wide range of use cases.
Dev Dives: Automate and orchestrate your processes with UiPath Maestro



Dev Dives: Automate and orchestrate your processes with UiPath MaestroUiPathCommunity This session is designed to equip developers with the skills needed to build mission-critical, end-to-end processes that seamlessly orchestrate agents, people, and robots.
📕 Here's what you can expect:
- Modeling: Build end-to-end processes using BPMN.
- Implementing: Integrate agentic tasks, RPA, APIs, and advanced decisioning into processes.
- Operating: Control process instances with rewind, replay, pause, and stop functions.
- Monitoring: Use dashboards and embedded analytics for real-time insights into process instances.
This webinar is a must-attend for developers looking to enhance their agentic automation skills and orchestrate robust, mission-critical processes.
👨🏫 Speaker:
Andrei Vintila, Principal Product Manager @UiPath
This session streamed live on April 29, 2025, 16:00 CET.
Check out all our upcoming Dev Dives sessions at https://community.uipath.com/dev-dives-automation-developer-2025/.
TrsLabs - Fintech Product & Business Consulting



TrsLabs - Fintech Product & Business ConsultingTrs Labs Hybrid Growth Mandate Model with TrsLabs
Strategic Investments, Inorganic Growth, Business Model Pivoting are critical activities that business don't do/change everyday. In cases like this, it may benefit your business to choose a temporary external consultant.
An unbiased plan driven by clearcut deliverables, market dynamics and without the influence of your internal office equations empower business leaders to make right choices.
Getting things done within a budget within a timeframe is key to Growing Business - No matter whether you are a start-up or a big company
Talk to us & Unlock the competitive advantage
tecnologias de las primeras civilizaciones.pdf



tecnologias de las primeras civilizaciones.pdffjgm517 descaripcion detallada del avance de las tecnologias en mesopotamia, egipto, roma y grecia.
UiPath Community Berlin: Orchestrator API, Swagger, and Test Manager API



UiPath Community Berlin: Orchestrator API, Swagger, and Test Manager APIUiPathCommunity Join this UiPath Community Berlin meetup to explore the Orchestrator API, Swagger interface, and the Test Manager API. Learn how to leverage these tools to streamline automation, enhance testing, and integrate more efficiently with UiPath. Perfect for developers, testers, and automation enthusiasts!
📕 Agenda
Welcome & Introductions
Orchestrator API Overview
Exploring the Swagger Interface
Test Manager API Highlights
Streamlining Automation & Testing with APIs (Demo)
Q&A and Open Discussion
Perfect for developers, testers, and automation enthusiasts!
👉 Join our UiPath Community Berlin chapter: https://community.uipath.com/berlin/
This session streamed live on April 29, 2025, 18:00 CET.
Check out all our upcoming UiPath Community sessions at https://community.uipath.com/events/.
Technology Trends in 2025: AI and Big Data Analytics



Technology Trends in 2025: AI and Big Data AnalyticsInData Labs At InData Labs, we have been keeping an ear to the ground, looking out for AI-enabled digital transformation trends coming our way in 2025. Our report will provide a look into the technology landscape of the future, including:
-Artificial Intelligence Market Overview
-Strategies for AI Adoption in 2025
-Anticipated drivers of AI adoption and transformative technologies
-Benefits of AI and Big data for your business
-Tips on how to prepare your business for innovation
-AI and data privacy: Strategies for securing data privacy in AI models, etc.
Download your free copy nowand implement the key findings to improve your business.
How analogue intelligence complements AI



How analogue intelligence complements AIPaul Rowe
Artificial Intelligence is providing benefits in many areas of work within the heritage sector, from image analysis, to ideas generation, and new research tools. However, it is more critical than ever for people, with analogue intelligence, to ensure the integrity and ethical use of AI. Including real people can improve the use of AI by identifying potential biases, cross-checking results, refining workflows, and providing contextual relevance to AI-driven results.
News about the impact of AI often paints a rosy picture. In practice, there are many potential pitfalls. This presentation discusses these issues and looks at the role of analogue intelligence and analogue interfaces in providing the best results to our audiences. How do we deal with factually incorrect results? How do we get content generated that better reflects the diversity of our communities? What roles are there for physical, in-person experiences in the digital world?
HCL Nomad Web – Best Practices und Verwaltung von Multiuser-Umgebungen



HCL Nomad Web – Best Practices und Verwaltung von Multiuser-Umgebungenpanagenda Webinar Recording: https://www.panagenda.com/webinars/hcl-nomad-web-best-practices-und-verwaltung-von-multiuser-umgebungen/
HCL Nomad Web wird als die nächste Generation des HCL Notes-Clients gefeiert und bietet zahlreiche Vorteile, wie die Beseitigung des Bedarfs an Paketierung, Verteilung und Installation. Nomad Web-Client-Updates werden “automatisch” im Hintergrund installiert, was den administrativen Aufwand im Vergleich zu traditionellen HCL Notes-Clients erheblich reduziert. Allerdings stellt die Fehlerbehebung in Nomad Web im Vergleich zum Notes-Client einzigartige Herausforderungen dar.
Begleiten Sie Christoph und Marc, während sie demonstrieren, wie der Fehlerbehebungsprozess in HCL Nomad Web vereinfacht werden kann, um eine reibungslose und effiziente Benutzererfahrung zu gewährleisten.
In diesem Webinar werden wir effektive Strategien zur Diagnose und Lösung häufiger Probleme in HCL Nomad Web untersuchen, einschließlich
- Zugriff auf die Konsole
- Auffinden und Interpretieren von Protokolldateien
- Zugriff auf den Datenordner im Cache des Browsers (unter Verwendung von OPFS)
- Verständnis der Unterschiede zwischen Einzel- und Mehrbenutzerszenarien
- Nutzung der Client Clocking-Funktion
Increasing Retail Store Efficiency How can Planograms Save Time and Money.pptx



Increasing Retail Store Efficiency How can Planograms Save Time and Money.pptxAnoop Ashok In today's fast-paced retail environment, efficiency is key. Every minute counts, and every penny matters. One tool that can significantly boost your store's efficiency is a well-executed planogram. These visual merchandising blueprints not only enhance store layouts but also save time and money in the process.
What is Model Context Protocol(MCP) - The new technology for communication bw...



What is Model Context Protocol(MCP) - The new technology for communication bw...Vishnu Singh Chundawat
Secure Code Review 101
- 1. Secure Code Review 101Secure Code Review 101 Narudom Roongsiriwong, CISSPNarudom Roongsiriwong, CISSP MiSSConf(SP2) Nov 19, 2016MiSSConf(SP2) Nov 19, 2016 Secure Code Review 101Secure Code Review 101 Narudom Roongsiriwong, CISSPNarudom Roongsiriwong, CISSP MiSSConf(SP2) Nov 19, 2016MiSSConf(SP2) Nov 19, 2016
- 2. WhoAmI ● Lazy Blogger – Japan, Security, FOSS, Politics, Christian – http://narudomr.blogspot.com ● Information Security since 1995 ● Web Application Development since 1998 ● Head of IT Security and Solution Architecture, Kiatnakin Bank PLC (KKP) ● Consultant for OWASP Thailand Chapter ● Committee Member of Cloud Security Alliance (CSA), Thailand Chapter ● Consulting Team Member for National e-Payment project ● Contact: [email protected]
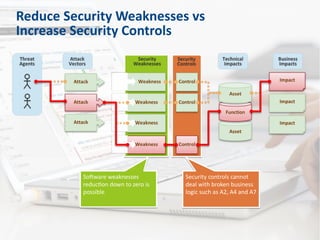
- 3. Security controls cannot deal with broken business logic such as A2, A4 and A7 Security controls cannot deal with broken business logic such as A2, A4 and A7 Software weaknesses reduction down to zero is possible Software weaknesses reduction down to zero is possible Reduce Security Weaknesses vs Increase Security Controls
- 4. What is Secure Code Review? ● Aim to identify security flaws in the application related to its features and design, along with the exact root causes. ● Verify that the proper security and logical controls are present, work as intended, and have been invoked in the right places. ● Assure application developers are following secure development techniques. ● Combine human effort and advanced static analysis tools.
- 5. Code Review and Secure Code Review ● Secure Code Review enhances the standard Code Review practice with security considerations. – Security standards – Security risks in the code base – Security context ● Reviewers must have the necessary skills and secure coding knowledge to effectively evaluate the code.
- 6. Code Review in Secure SDLC Code Review
- 7. How Code Review Reduces Costs on Bug Fixes Relative cost of security fixes, based on time of detection Source: The National Institute of Standards and Technology (NIST) Code Review Penetration Testing
- 8. Method Comparison to Cover High Level Topics Good Some None Source: Code Review Guide 2.0 (Alpha Release)
- 9. Method Comparison Against OWASP Top 10 Risks Good Some None Source: Code Review Guide 2.0 (Alpha Release)
- 10. Factors to Consider in Code Review Process ● Risks ● Purpose & Context – A payment web application will have higher security standards than a promotional website. ● Lines of Code: the more lines, the more bugs ● Programming Language – Unmanaged code → Chances of buffer overflow – PHP → Remote code execution ● Resources, Time & Deadlines
- 11. Code Review Preparation ● Application Features and Business Rules – BR, SRS, etc ● Context ● Sensitive Data ● User Roles and Access Rights ● Application Type – Web, Desktop, Web Service, Mobile, Hybrid ● Language and Its Security Features and Issues ● Design / Framework – MVC, Strut, Spring, Hibernate, YII, CakePHP ● Company Standards and Guidelines
- 12. Code Review Checklist ● Data Validation ● Authentication ● Session Management ● Authorization ● Cryptography ● Error Handling ● Logging ● Security Configuration ● Network Architecture
- 13. Advantage & Disadvantage of Source Code Scanner ● Advantage – Reduction in manual efforts – Find all the instances of the vulnerabilities – Source to sink analysis – Elaborate reporting format ● Disadvantage – Business logic flaws remain untouched – Limited scope – Design flaws – False positives
- 14. Name Programming Language Support OS Java PHP .NET C C++ Python Other CodePro X W L M FindBugs X W L FxCop X W Flawfinder X X L Milk X X W L MOPS X L OWASP Code Crawler X X W OWASP ORIZON X X X L OWASP O2 Platform X X Javascript W OWASP LAPSE X W L M PMD X X X Javascript, XML, XSL W L PREfast X X W L RIPS-Scanner X SonarQube X X X X Delphi, Javascript, XML W L M Sprint X W L StypeCop X W Yasca X X X X X HTML, , Javascript, Cobol, Coldfusion W L Free Source Code Scanners
- 15. Example: SonarQube with OWASP Plugin
- 16. Let’s Go Back to Basic without Code Scanner ● Use your favorite text editor or IDE. ● “Find in Files” feature with RegEx is recommended. ● In this presentation will show you “Geany”, cross platform text editor. https://www.geany.org
- 17. Review SQL Injection ● Cause of SQL injection vulnerability is from an SQL command that constructs from the untrusted input. ● Common actions to interact with data are Create (INSERT), Read (SELECT), Update, Delete. ● SELECT/UPDATE/DELETE are usually filtered only some records, using WHERE. ● Some bad code use dynamic fields or tables, it’s also able to be injected. Sting custQuery = “SELECT custName, address1, address2, city, postalCode WHERE custID= ‘“ + request.GetParameter(“id”) + “’“ Code Data
- 18. Example: Find in Files for INSERT or WHERE
- 19. Example: Find in Files for INSERT or WHERE 1) Suspect 2) Is this an input parameter? 3) Vulnerable from calling?
- 20. Review Remote Code Injection ● Both client side (JavaScript) and server side (ex. PHP) scripting ● Search for data from untrusted sources could be inputs of – eval (most of scripting language) – include, require (PHP) eva1
- 21. Review Hard-Coded Password/Encryption Key ● Hard-coded passwords or key may compromise system security in a way that cannot be easily remedied. ● Developers may create a backdoor with hard-coded username and password for special credential. ● Forms of password for databases and application are likely to be “password”, “pass”, “passwd” or “pwd”. → RegEx: pass|pwd ● Borland Interbase 4.0, 5.0, 6.0 was discovered a special credentials, username “politically” and password “correct”, were inserted into the credential table at program startup. dpb = dpb_string; *dpb++ = gds__dpb_version1; *dpb++ = gds__dpb_user_name; *dpb++ = strlen (LOCKSMITH_USER); q = LOCKSMITH_USER; while (*q) *dpb++ = *q++; *dpb++ = gds__dpb_password_enc; strcpy (password_enc, (char *)ENC_crypt(LOCKSMITH_PASSWORD, PASSWORD_SALT)); q = password_enc + 2; *dpb++ = strlen (q); while (*q) *dpb++ = *q++; dpb_length = dpb – dpb_string; isc_attach_database (status_vector, 0, GDS_VAL(name), &DB, dpb_length, dpb_string);
- 22. Review Poor Logging Practices ● Use of a System Output Stream – Using System.out or System.err rather than a dedicated logging. – Log messages may accidentally be returned to the end users and expose sensitive information public class MyClass public void debug(Object message) { System.out.println(message); } } ● Logger Not Declared Static Final – Loggers should be declared to be static and final. – Use the same logger for the duration of the program. – The following statement errantly declares a non-static logger. private final Logger logger = Logger.getLogger(MyClass.class);
- 23. Review Session Management ● .Net ASPX web.config <authentication mode=”Forms”> <forms loginUrl=”member_login.aspx” cookieless=”UseCookies” requireSSL=”true” path=”/MyApplication” /> </authentication> ● Java web.xml <session-config> <cookie-config> <secure>true</secure> </cookie-config> </session-config> ● PHP.ini session.cookie_lifetime=0 session.use_cookies=On session.use_only_cookies=On session.use_strict_mode=On session.cookie_httponly=On session.cookie_secure=On session.gc_maxlifetime=[choose smallest possible] session.use_trans_sid=Off
- 24. Conclusion ● Code scanner absolutely helps code reviewers but they are lacks of capabilities and usually create false positive. ● Code reviewers should know the specific language and framework of codes they reviews ● The justification must rely on the context and requirements of the application together with standards and guidelines



